It’s one thing to hear about theoretical security vulnerabilities that could impact IoT devices. It’s another to know that serious security flaws have existed for decades in a software library that is widely used in the IoT ecosystem.
That’s exactly what happened in the case of Ripple20, a series of security vulnerabilities that impact hundreds of millions of IoT devices. This article explains what Ripple20 is, why it’s dangerous and how companies can help mitigate threats like Ripple20 within their network.
What is Ripple20?
Ripple20 is the name that security researchers at JSOF gave to a collection of vulnerabilities that they discovered within a software library first developed in the 1990s by a company called Treck. The library is a lightweight implementation of a TCP/IP stack, meaning that it provides the core functionality that devices need to connect to networks.
Researchers at the cybersecurity firm JSOF discovered the vulnerabilities in 2020. They named the vulnerabilities Ripple20 because of their potential to cause a “ripple effect” across supply chains of which IoT devices are a part. In other words, the vulnerabilities impact not just end-user devices (like printers or home security systems), but entire operational networks that include IoT hardware at any layer. For example, IoT sensors that help manage environmental conditions on a manufacturing floor and are affected by Ripple20 could have a ripple effect that compromises the security of “downstream” participants in the supply chain of which the facility is a part.
Although the Ripple20 vulnerabilities did not come to light until 2020, researchers believe that they have existed for at least twenty years.
What is Treck?
Treck is a nearly ubiquitous embedded TCP/IP that works well on devices with limited hardware resources. That feature made it a very popular solution for IoT devices, which typically lack the resources to run the more demanding types of software that are common on PCs or servers.
The library is consequently in widespread use, and likely places “hundreds of millions” of devices at risk, according to JSOF. Those devices represent a broad category of IoT use cases, from home and enterprise printers, to Industrial Control Systems (ICS), to healthcare equipment and beyond.
What are the effects of Ripple20?
As noted above, the Treck library impacted by Ripple20 powers the network communications of devices that use it. Because networking is at the core of device operations, Ripple20 vulnerabilities expose devices—and users who depend on them—to a range of potential attacks.
Perhaps one of the most serious is remote-code execution attacks, in which threat actors take control of an affected device in order to harvest private data from it or run malicious software on it. Making matters worse from a security standpoint, remote-code attacks can be executed from external networks, which means attackers need not have breached a company’s network perimeter or firewalls in order to exploit Ripple20 vulnerabilities.
The following table displays a number of common vulnerabilities and exposures (CVE) that correspond to specific types of attacks and risks that have emerged from Ripple20.
CVEs that correspond to active Ripple20 attacks
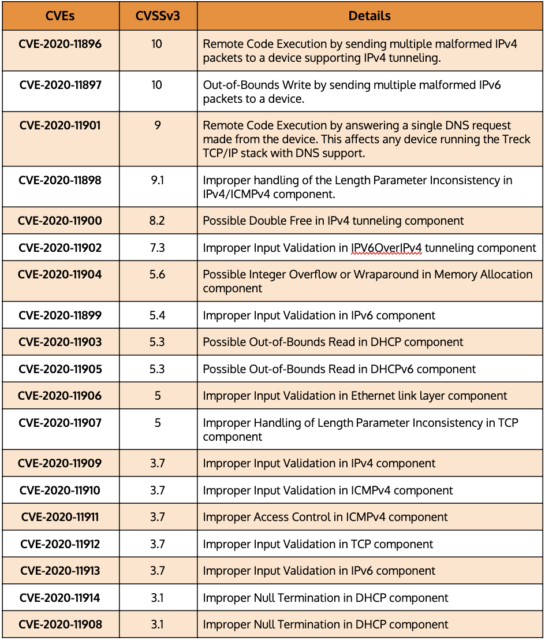
In practice, Ripple20’s effects could include attacks such as the theft of personal data from Internet of Medical Things (IoMT) devices, or the interference with dosage levels distributed by such devices to patients. Or, if attackers use Ripple20 to take control of a manufacturer’s network, it could disrupt operations, leading to downtime and significant financial loss.
The list of potential attack scenarios could go on. The takeaway is that Ripple20 creates an unusually large and serious set of vulnerabilities that impact virtually every niche within the IoT ecosystem. JSOF has confirmed that Ripple20 affects IoT devices manufactured by fifteen specific vendors, including Baxter, Intel, Caterpillar, Cisco, Aruba, HP, and Xerox, but many others manufacturers’ products are likely to be at risk as well.
Identifying devices vulnerable to Ripple20
Because Ripple20 became publicly known only in 2020, many organizations are still in the process of assessing their exposure and risk. To do so, they must start by building an asset inventory within their infrastructure. Then, they must determine which devices are impacted by Ripple20.
There are two main ways to identify affected devices. One is to consult advisories from device manufacturers who have determined that their devices are impacted. But because not all manufacturers have issued advisories yet, equally important is proactive monitoring of devices in order to discover whether they are using the Treck TCP/IP stack and appear vulnerable to Ripple20. Ordr has developed novel techniques to discover devices that have Ripple20 vulnerabilities regardless of whether advisories from device manufacturers exist.
Once companies identify vulnerable devices, they can typically address the Ripple20 vulnerabilities by installing patches provided by device manufacturers. If a patch does not yet exist, the vulnerable devices can be taken offline until one becomes available or, at a minimum, segmented from other devices in order to mitigate the potential impact.
How to detect Ripple20
Because attackers can execute Ripple20 exploits from external networks, traditional firewalls and Network Access Controls (NACs), which filter traffic only along the boundary between the public Internet and a company’s internal network, provide little protection.
This is why novel Ripple20-detection techniques like those developed by Ordr are so important. In addition to looking for the presence of impacted Treck software on devices themselves, Ordr also baselines device behavior to determine malicious or suspicious patterns and will flag this activity. Ordr provides a level of protection against Ripple20 that a firewall and NAC solutions alone cannot deliver.
How to protect vulnerable devices from Ripple20
Although identifying devices that are impacted by Ripple20 and patching them is an obvious step for responding to the Ripple20 vulnerabilities, organizations must take broader steps to ensure that their networks are hardened against threats like Ripple20. That includes embracing the principles of Zero Trust security. It’s a safe bet that similar vulnerabilities exist in the wild but have not yet been discovered. Zero Trust helps ensure that your network will be resilient against such attacks, regardless of which form they take.
Zero Trust means that networks are configured in such a way that, whenever a new device appears on a network, or an existing device’s configuration changes, the device has no access to the network or the hosted resources until a security administrator has verified that the device should be granted access.
In addition, network administrators should adhere to several other best practices associated with Zero Trust:
- Do not rely on firewalls or private IP addresses to establish which devices are “safe.” Instead, identify each device that exists on a network and ensure that it can be trusted before you grant it access to network resources.
- Implement least-privilege access. Grant devices only the minimal access privileges they need to operate.
- Use Multi-Factor Authentication (MFA). MFA is a security enhancement that requires a user to present two or more pieces of evidence when logging in to an account.
- Implement microsegmentation. Grant access privileges to each device on a highly granular basis, rather than assigning broad access rights. Policies are tailored to the individual needs of each device on the network.
Proactive protection of IoT devices with Ordr
The Ripple20 vulnerabilities highlight just how much risk IoT and unmanaged devices face, even when they run software that has been used and trusted for decades. They demonstrate the need for proactive protection and deep visibility.
Ordr Systems Control Engine (SCE) is a solution for organizations that need to protect their network and devices from Ripple20 and other vulnerabilities. Ordr SCE can:
- Discover all network-connected devices.
- Identify vulnerable assets impacted by Ripple20.
- Detect and flag anomalous behavior using a built-in intrusion detection engine.
- Proactively protect devices from Ripple20 attacks by dynamically generating policies and enforcing them on next-generation firewalls or NAC solutions.

Interested in
Learning More?
Subscribe today to stay informed and get
regular updates from ORDR Cloud