See, Know, Secure Every Asset in Your Enterprise
Incomplete Asset Inventory
Security teams find themselves investing considerable time and manual efforts in correlating data from various sources to answer questions about their security posture. Most asset management solutions cannot identify IoT and OT, leading to cybersecurity blind spots. ORDR unifies API, DPI and proprietary ORDR Discovery methods to deliver comprehensive and accurate asset insights on devices, users, applications, SaaS and cloud.
Attack Surface Reduction
Enterprise organizations face challenges in identifying and prioritizing vulnerabilities, exposures, and security gaps. ORDR provides a solution by automating the identification and providing context needed for remediation of critical risks, high-risk vulnerabilities, shadow IT, security coverage gaps, and non-compliant controls, allowing organizations to secure their attack surface effectively.
Identifying and Responding to Threats
Identifying not only known threats, but when an asset deviates from its normal behavior is crucial for early threat detection and response. During a security incident, swift response is essential. With ORDR, you can effectively detect anomalies, identify exploits or active threats, and automate your incident response process, ensuring the security and resilience of your enterprise.
SEE
Discover and Classify Every Asset
Utilizing API integrations and ORDR’s Discovery Engine, CAASM+ delivers real-time visibility into all devices, cloud assets, applications, SaaS apps, and users—critical to deliver efficient, modern enterprise customer experiences and maintain business operations:
- Gain real-time, accurate asset data and insights for devices, users, applications, SaaS and cloud, including hard-to-discover IoT and OT
- See granular device details like manufacturer, model, serial number, OS, support owner, connectivity and more.
- Identify issues like rogue or banned devices, and devices with outdated operating systems
- Pinpoint security coverage gaps such as endpoints missing MDM/EDR agents
- Map and analyze risky communications between assets and to the Internet
- Enrich CMDB with real-time asset visibility
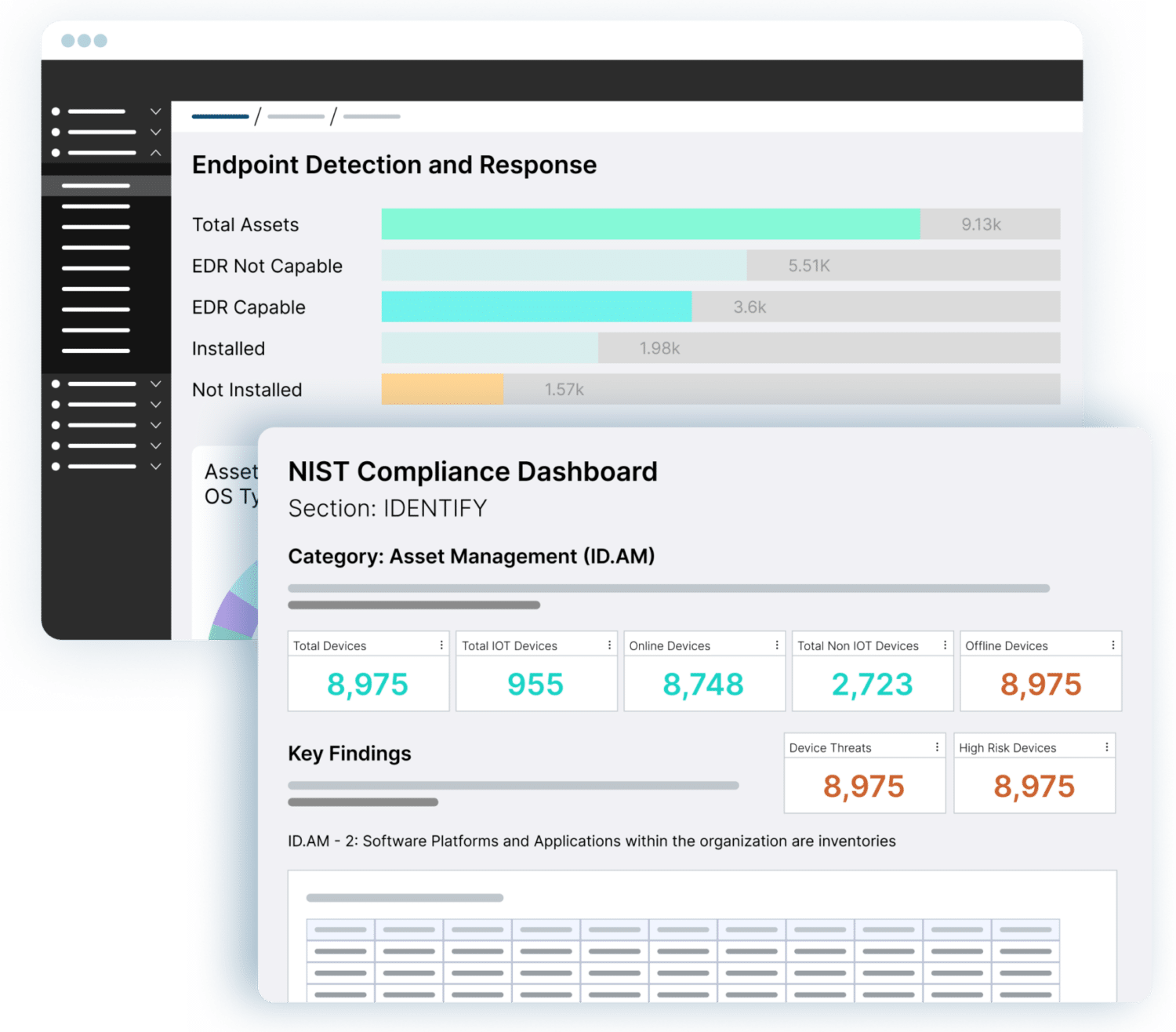
KNOW
Reduce Risks and Exposures and Accelerate Incident Response
ORDR provides enterprise organizations with comprehensive visibility into the vulnerability landscape for both managed and unmanaged devices. Translate vulnerabilities into a prioritized action plan with risk scores and automated workflows assigned to the correct device owner, enabling efficient response actions. Detect cyberthreats that can pose significant risks to profitability and essential business operations, ensuring proactive threat mitigation.
- Gain comprehensive coverage of all vulnerabilities, including those on IoT and OT devices
- Prioritize vulnerabilities based on multiple asset and organizational risk factors and automate remediation for the right owners
- Detect active exploits and risky communications with an integrated IDS and threat intelligence feeds
- Identify devices behaving abnormally, based on baseline known-good communications
SECURE
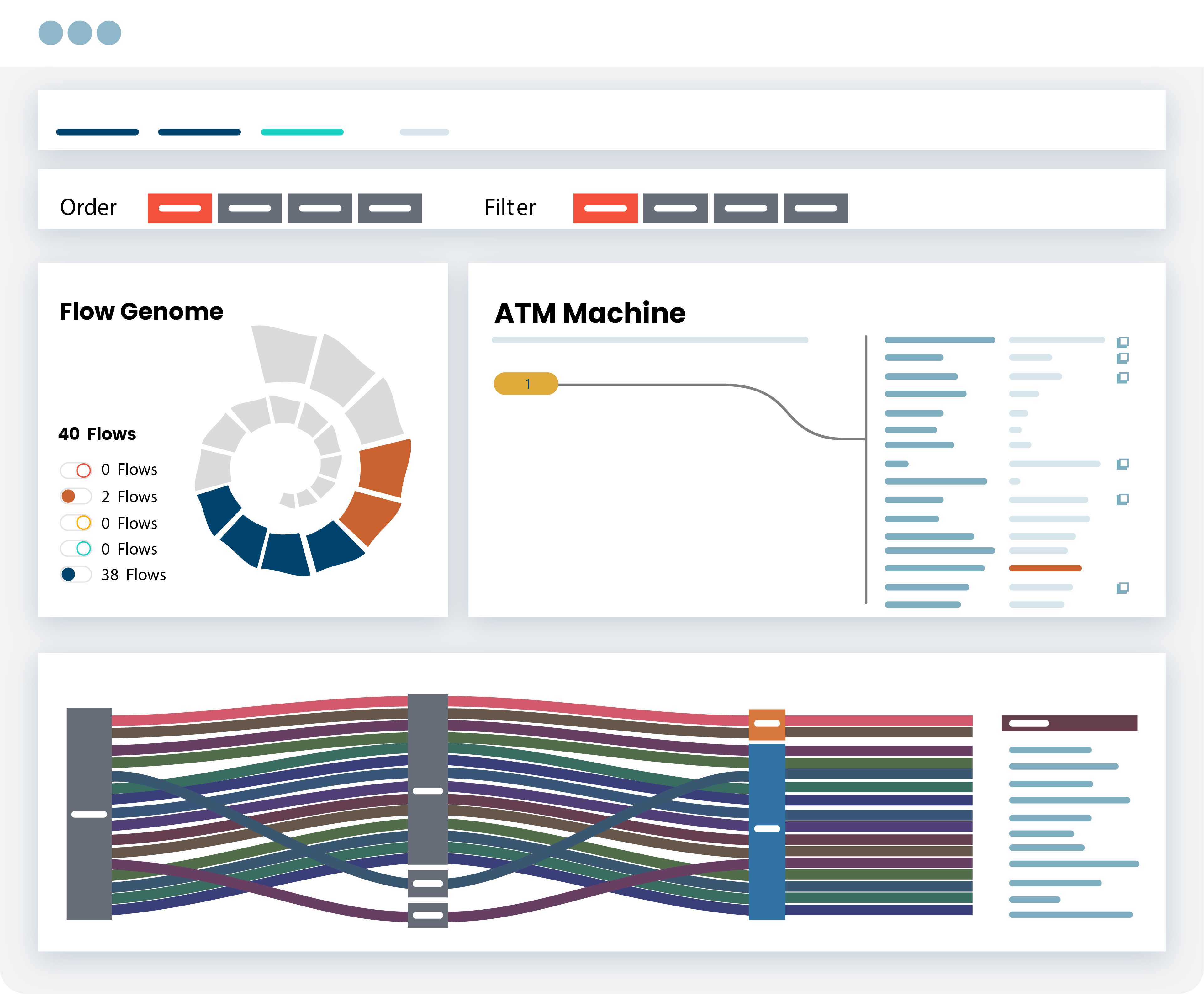
Segmentation To Manage Risks
Segmentation is a cybersecurity best practice. Accelerate NAC and Zero Trust initiatives. Deploy ORDR to create segmentation policies that align to business needs – macro segmentation to isolate specific types of assets, and Zero Trust segmentation to limit vulnerable devices to baseline communications. Optimize policies based on enforcement points – firewalls, NAC or switches.
SECURE
Easily Address Compliance Regulations
Compliance can be a challenge for businesses, especially collecting data and evidence for board meetings and audits. With limited resources, automation is key to efficiently managing security controls and coverage gaps. Simplify compliance across various frameworks, such as NIST, CIS, Cyber Essentials, and other standards with ORDR’s comprehensive reporting tools designed to streamline the compliance process. Dashboards and reports can be customized based on the business’s specific needs.