Why Is CAASM Important?
With digital transformation and adoption of hybrid business models, enterprises are rapidly deploying assets to enhance efficiency. However, the explosive growth of these assets – devices, users, applications, SaaS and cloud workloads – not only significantly expands the attack surface, but also introduces asset management challenges:
- Security teams find themselves investing considerable time and manual efforts in correlating data from various sources to try to answer questions about their security posture
- Most asset management solutions cannot identify IoT and OT, leading to cybersecurity blind spots
- The difficulty in getting granular details about assets, risks and business context can make it challenging to prioritize vulnerabilities and remediation
- The lack of business context becomes even more critical during incidents and can noticeably slow response times.
- Without real-time asset context, addressing compliance requirements require time-consuming and manual processes.
What is Cyber Asset Attack Surface Management (CAASM)?
Cyber asset attack surface management (CAASM) is focused on enabling security teams to overcome asset visibility and exposure challenges.
According to Gartner, CAASM “enables organizations to see all assets (internal and external), primarily through API integrations with existing tools”. With the consolidated view of all assets, security teams can then initiate queries to find security coverage gaps, misconfiguration issues, and prioritize vulnerabilities and risks.
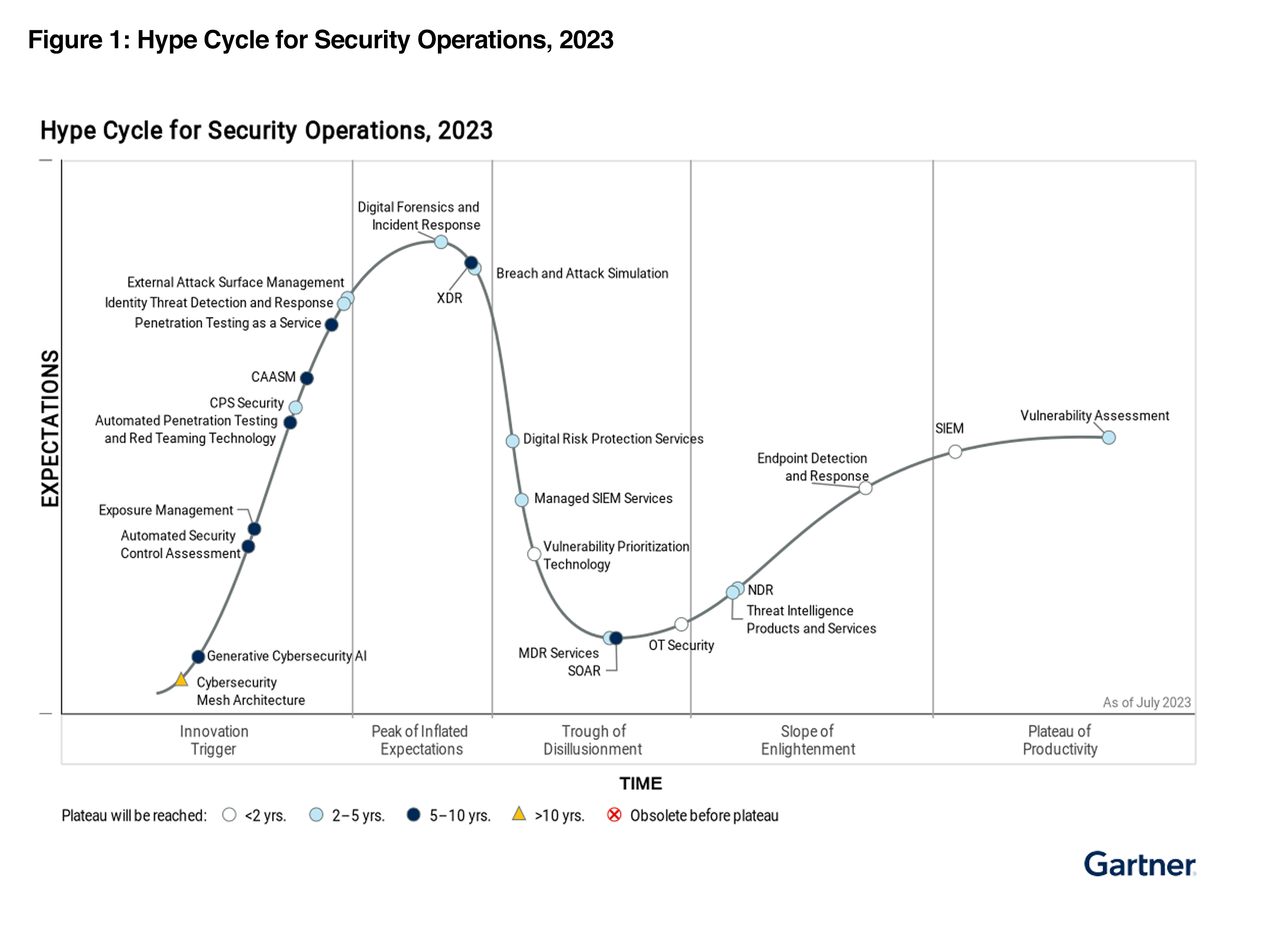
In the Gartner 2023 Hype Cycle for Security Operations, Gartner has stressed for security teams to adopt a continuous exposure-based approach to operations, with an emphasis on being more agile, and emphasizing a business-relevant focused. Gartner identifies CAASM as one of the technologies to continuously discover, assess, prioritize, validate and reduce exposure across digital estates. CAASM is a key component for any organization that is embracing the Continuous Threat Exposure Management (CTEM) framework.
Industry’s Most Accurate CAASM Solution
Automate Asset Inventory
Gain a unified asset inventory of every asset on the network, from devices, users, SaaS, cloud and installed applications.
Security Control and Coverage Reporting
Automatically identify security coverage gaps or misconfigurations, for example endpoints that are missing EDR or MDM agents
Audit/Compliance Reporting
Address compliance and regulatory compliance with accurate and real-time asset data for NIST, CIS Controls and other cybersecurity frameworks
Visibility Gap Analysis
Identify unknown, shadow IT or rogue assets in the network. Identify risks such as weak passwords or assets running outdated operating systems.
Vulnerability Prioritization and Management
Map vulnerabilities across every asset in the network and enable security teams to prioritize the top ones to focus on.
Accelerate Incident Response
Significantly accelerate investigation and response times. Integrate with ITSM, SIEM and SOC, and map the blast radius with asset relationship mapping.
How Does CAASM Differ From CMDB
CAASM is often confused with CMDB because both support asset management. The difference is that CAASM focuses on asset visibility and security use cases for security teams rather than IT service management (ITSM) use cases. CAASM does not support the CDMBs ITSM functions such as tracking asset life cycle, managing workflows associated with these assets and performing financial costing analysis.
- CAASM is primarily built for security teams that want to have a complete visibility of all the organization’s assets, map asset dependencies, surface security gaps and perform prioritization and remediation.
- CAASM provides visibility of all assets. In contrast, CMDBs focus on assets that are important to the IT teams, and miss assets like IOT, IOMT and OT.
- CMDB does not collect and correlate vulnerabilities against assets.
- CAASM can bidirectionally integrate with a CMDB as a data source and be used to enrich CMDB data, or enable asset reconciliation with CMDB data.
Considerations For Selecting a CAASM
There are many factors to consider when selecting a CAASM solution for your enterprise. Below are a few to get you started:
- What does your environment look like today and what visibility should CAASM address?
- How many security tools are deployed today? What teams will be involved to enable ingestion of data from these tools?
- Does the vendor only support asset discovery via API ingestion, or do they supplement with their own discovery methods?
- Is the vendor able to deliver asset inventory beyond traditional asset categories such as granular software inventory, users, and IOT, IOMT or OT systems?
- Beyond just visibility into assets and risks, can the vendor initiate action to reduce the exposure?
- Beyond just visibility into assets and risks, can the vendor extend to more advanced use cases like threat detection?
- Is there an easy way to surface insights about your environment, or do you need to learn a new programming language
- Are there easy reports to facilitate compliance and audit reporting
- Which teams will be involved in this CAASM project? What security outcomes are most important to the users