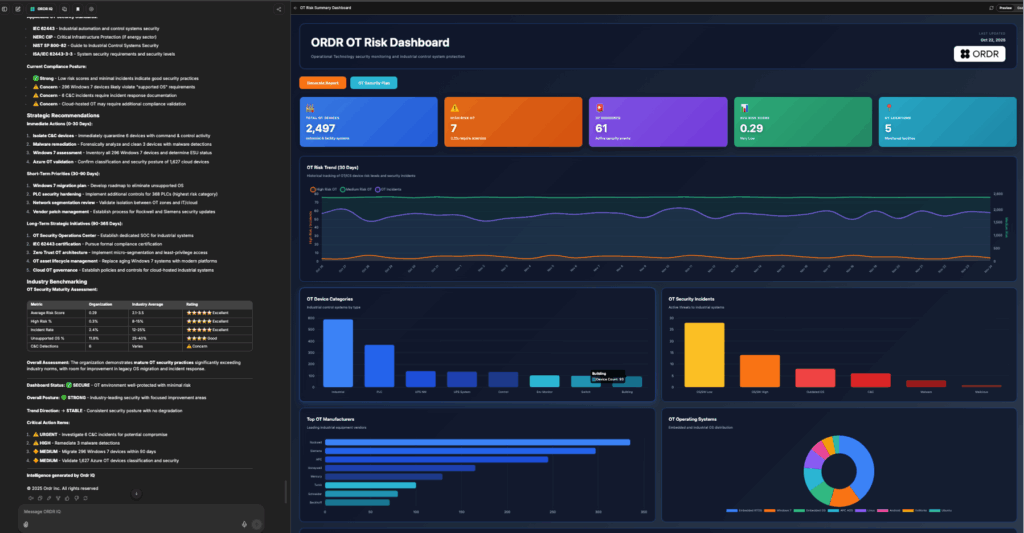
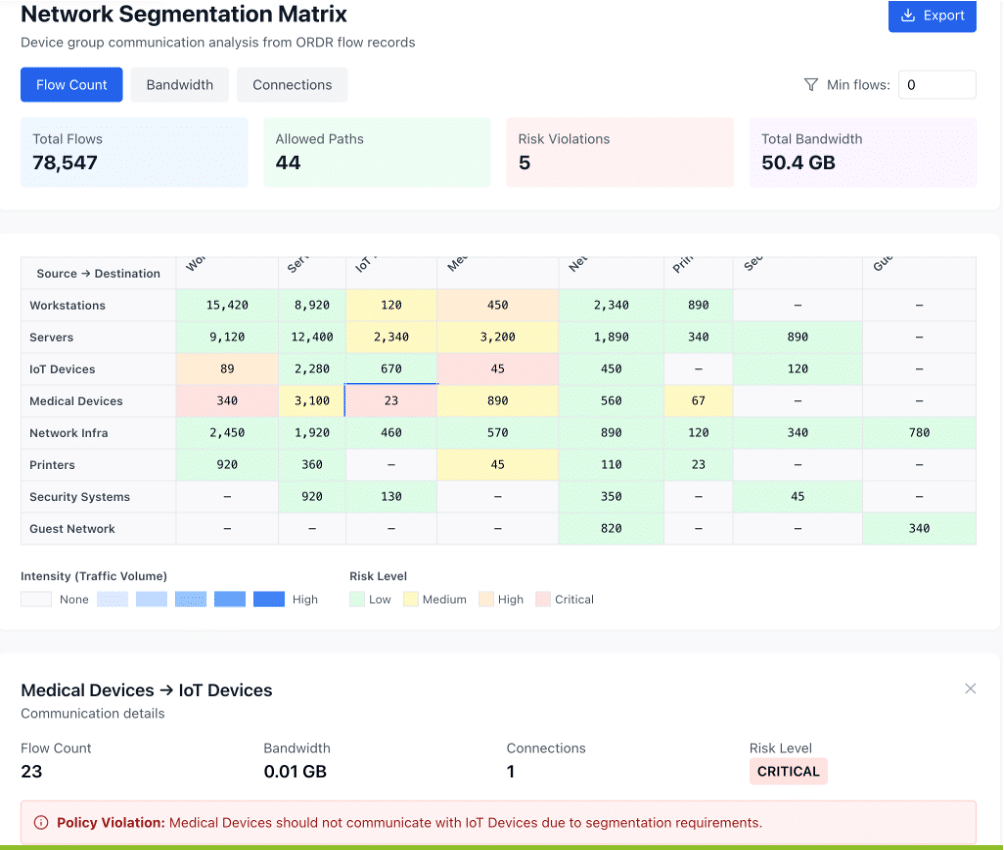
The visibility that we now have into our networked devices and their software inventory gives us greater assurance that we are properly maintaining and securing our systems to ensure that we can continue to provide excellent service and patient care.
Stacy Estrada Information Security Manager, Montage Health