organizations have segmented just one of the six mission-critical areas
organizations have segmented two or more mission critical areas
organizations have successfully segmented all six mission-critical areas
Source: Vanson Bourne
FROM MANUAL PAIN TO AI PRECISION
Segmentation Without Headaches.
Most segmentation projects stall under the weight of complexity — patching blind spots, manual inventories, endless ACLs, and flat networks that weren’t built for security. ORDR clears the path with AI that automates what used to take months of manual work. From instant discovery to safe, simulation-first enforcement, ORDR helps you move fast — without breaking things.
No Patching blind spots
Identify devices that are critical to your operations and yet cannot be patched and isolate them without disruption.
No Manual inventory
Our AI-powered discovery instantly classifies every asset — no agents, no spreadsheets.
No ACL nightmares
Let machine learning write the policies for you — based on real-world behavior.
No Flat networks
AI-driven enforcement applies least privilege segmentation without changing your infrastructure.
No Guesswork enforcement
Simulate and validate AI-generated policies before a single change is made.
No Policy handoffs
Translate policy across your stack automatically — AI knows the syntax of your infrastructure.
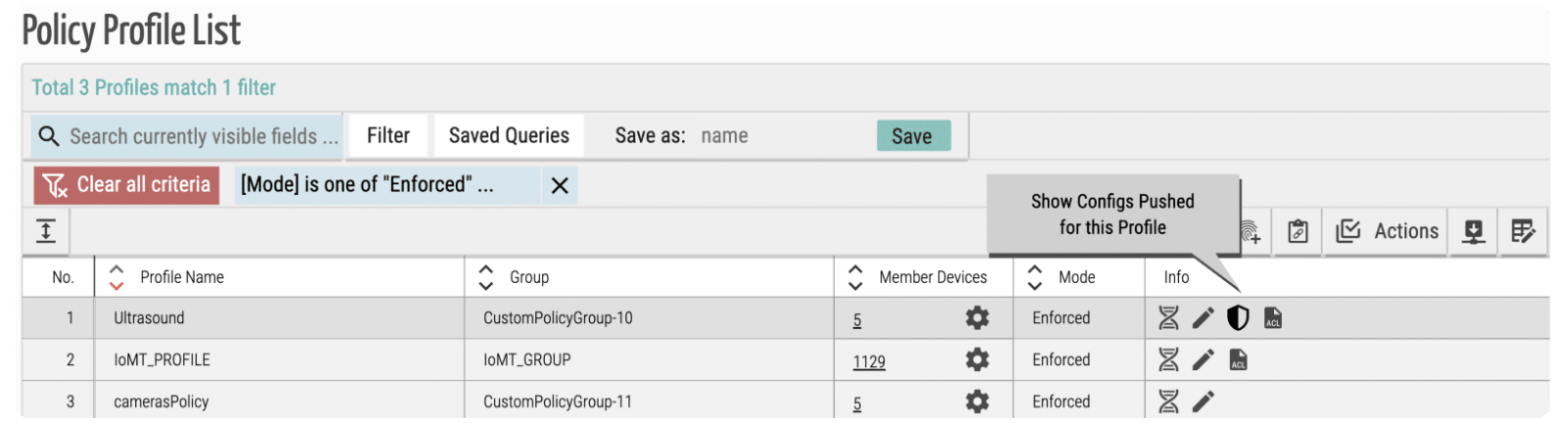
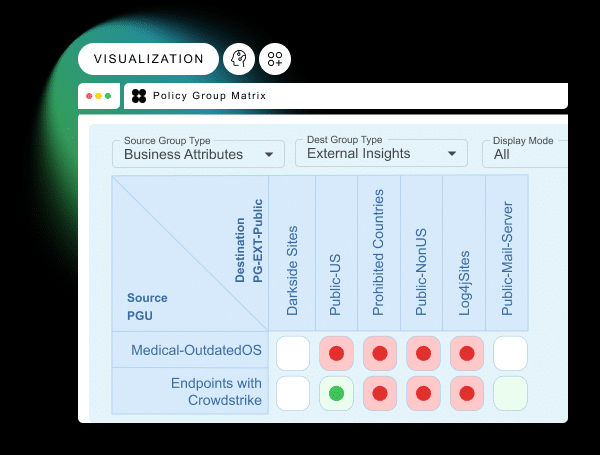
INTELLIGENCE TO ACTION
AI That Understands Your Environment Before It Acts
Before you can take action, you need to know what you’re dealing with. ORDR uses AI to quickly profile devices, baseline their behavior, and simulate policy outcomes — so you can move with confidence, not guesswork.
- Detect and Classify
- Dynamically Group Devices
- Baseline Behavior
- Simulate Policies Before You Enforce
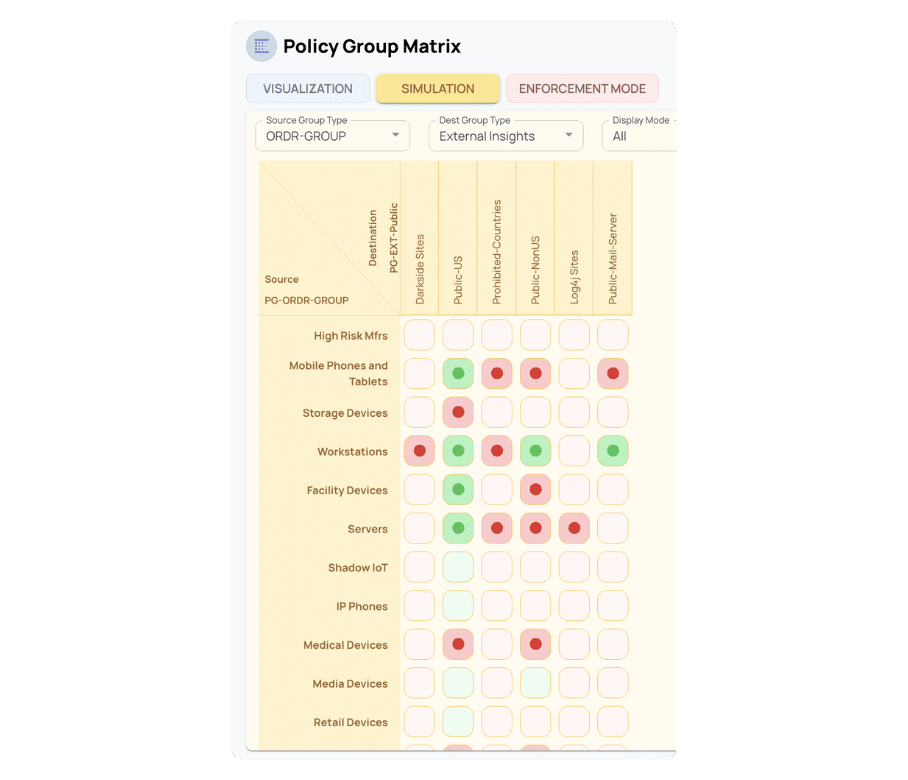
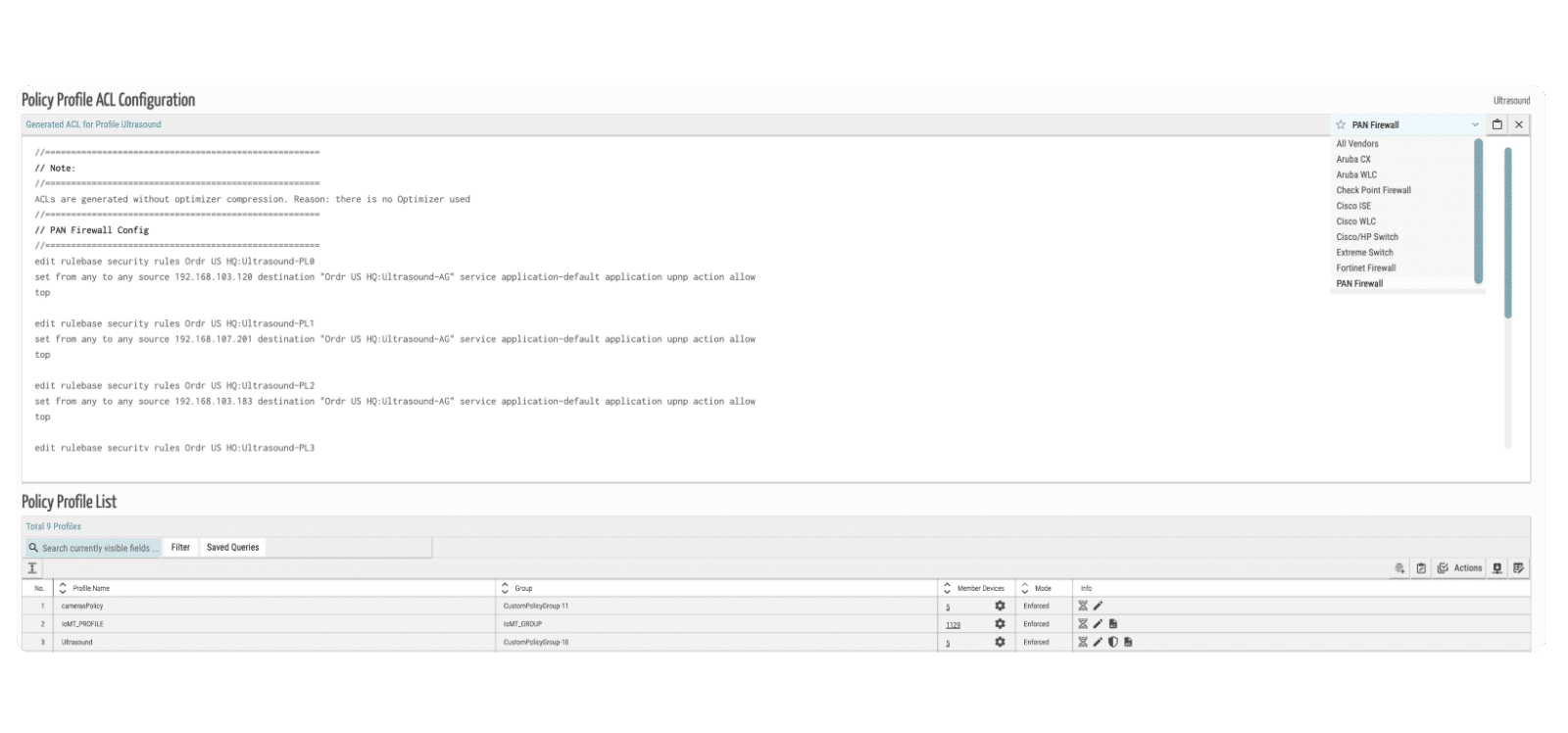
FROM INSIGHTS TO ACTIONS WITHOUT REWRITES
Enforce Instantly. Adapt Automatically. Stay Ahead.
Once your policies are defined, ORDR turns them into real-world enforcement — mapped to your infrastructure and optimized for performance. And as your environment changes, ORDR keeps up.
- Map Policies to Enforcement Zones
- Optimize for Scale and Performance
- Deploy in Real Time
- Continuously Learn and Adjust
Try the Fastest Path to Real Segmentation
Customer Case Studies

The visibility that we now have into our networked devices and their software inventory gives us greater assurance that we are properly maintaining and securing our systems to ensure that we can continue to provide excellent service and patient care.
Stacy Estrada
Information Security Manager, Montage Health

Using ORDR’s device-centric threat and anomaly detection, Veritex Bank has also been able to detect and quickly address issues, even before being notified by our virtual SOC. This has helped the team accelerate response.
Bob Ludecke
CISO, Veritex Bank

ORDR automatically discovers all our managed and unmanaged devices and delivers critical insights through a real-time dashboard. ORDR also generates policies by type and enforces them to support microsegmentation, zero trust, and other network access controls.
Director of Information Security
Automotive Manufacturer
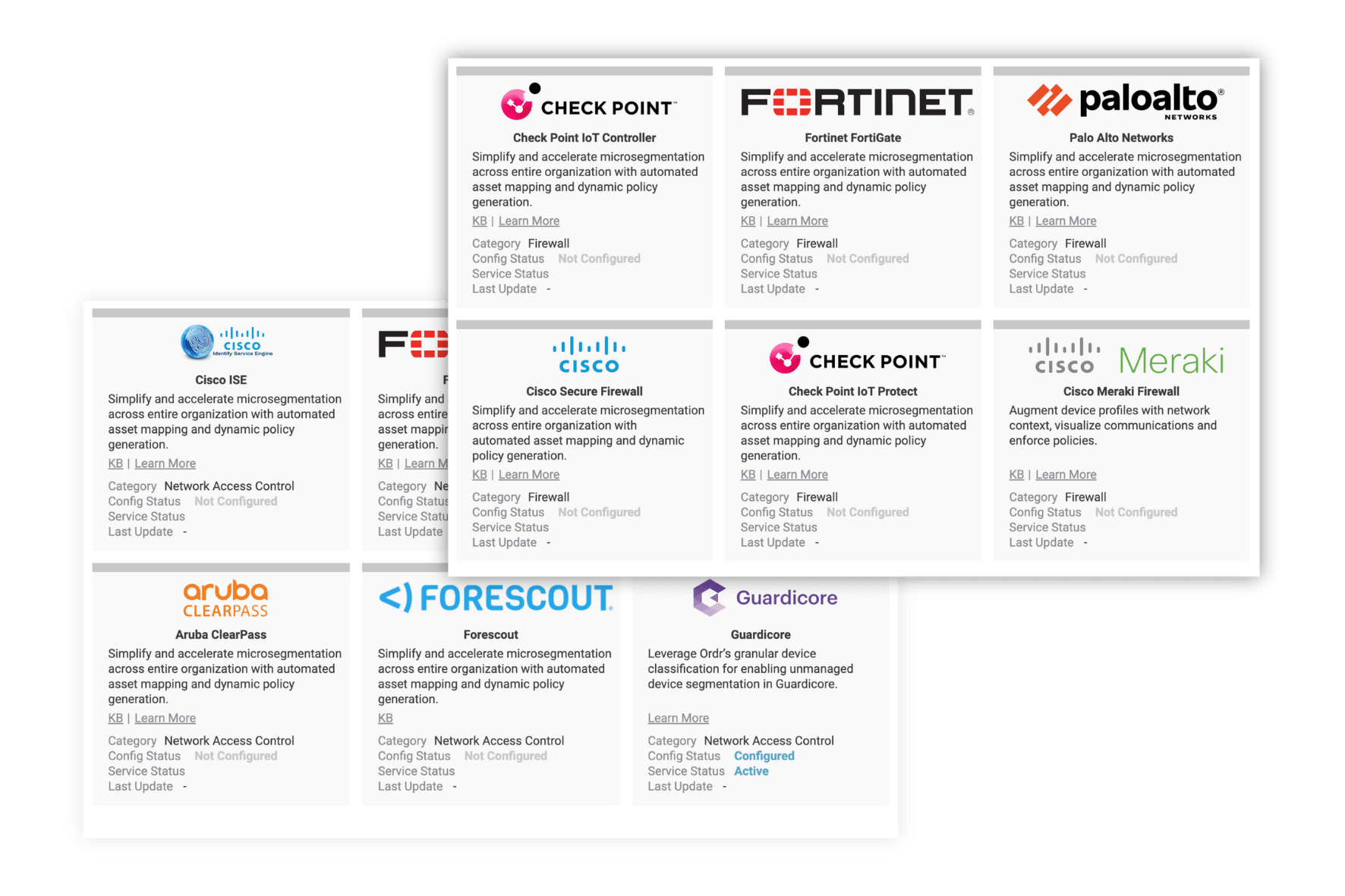
BUILT FOR THE STACK YOU ALREADY HAVE
No Rip and Replace. Just Results.
ORDR doesn’t ask you to start over. It makes what you already have smarter. From Cisco to Aruba, Palo Alto to Fortinet, ORDR works with your existing switches, firewalls, and platforms — no forklift upgrades, no new hardware.
- AI translates intent into enforcement — automatically.
- Enforce on 3,500+ infrastructure types without scripting.
- Push quarantines, tags, and remediations with AI-driven speed.
- One UI, one control plane, powered by real-time insight.
Learn how ORDR supercharges your existing infrastructure.
THE BOTTOM LINE
Segmentation Isn’t Just Possible. It’s Finally Practical.
ORDR doesn’t give you another dashboard. It gives you segmentation that finally works — with AI that handles the complexity, and enforcement that fits your world. And it takes the pain out of your job.
- No manual inventory
- No more brittle ACLs
- No broken ops
- No waiting on NACs to get fixed
Just real segmentation, built for your world – the real world.
ORDR AI Protect for Segmentation