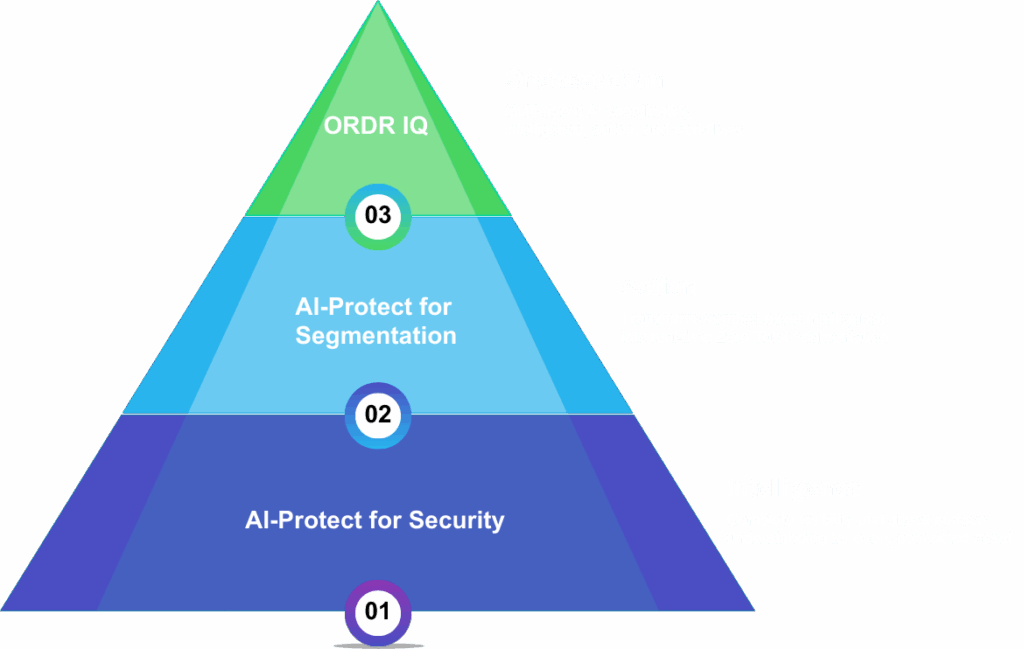
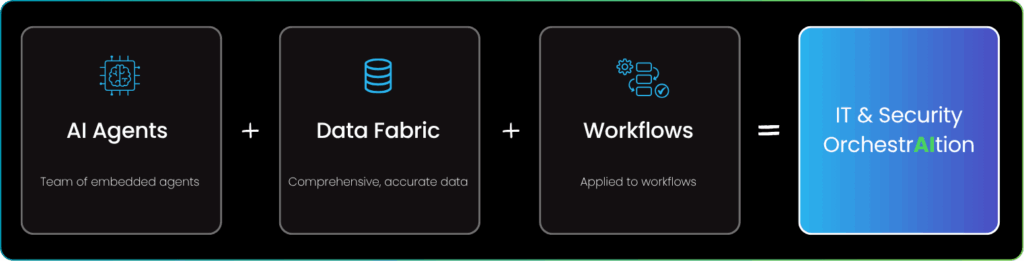
The problem: insight without action
Healthcare, manufacturing, and enterprise environments are flooded with security data: alerts, dashboards, and recommendations.
But when it’s time to respond, teams face:
- Unverified device and asset data
- Disconnected tools and workflows
- Manual decisions that slow response
- Policies that exist on paper, not in the network
Insight alone doesn’t reduce risk. Action does.
Outcomes that matter
When security is built to act, everything changes:
- Risk is reduced earlier—before alerts become incidents
- Response is faster—without manual bottlenecks
- Operations stay resilient—even in complex environments
- Trust is strengthened—with clinicians, operators, and leadership
This is proactive security, designed for real-world conditions.