DETECT MORE THREATS
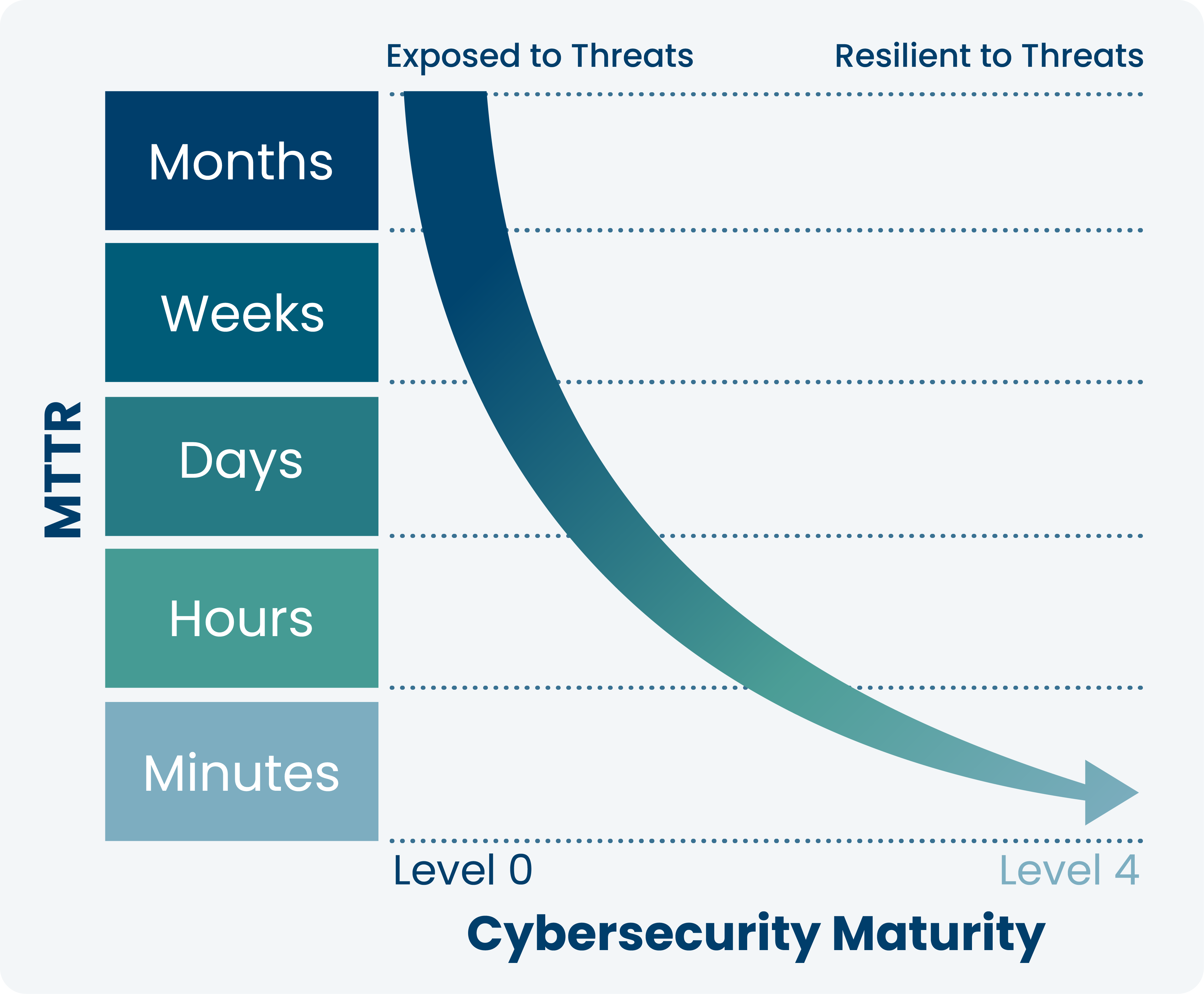
Reduce Dwell Time With Comprehensive Threat Detection
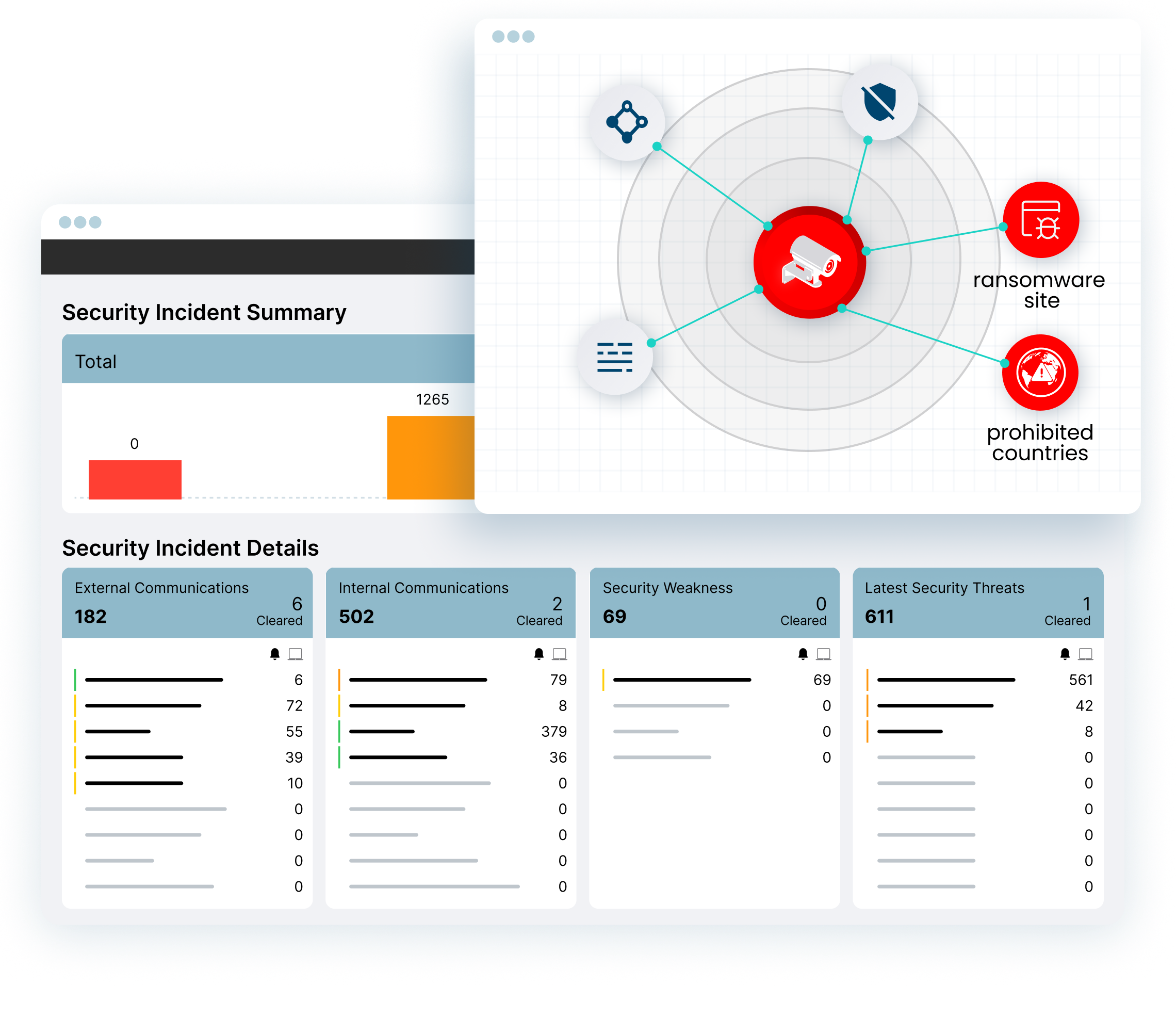
Today’s cyber criminals use a variety of attacks and techniques. Ordr reduces dwell time and mean-time-to-detect with an integrated IDS, threat intelligence, AI/ML behavioral analytics to detect threats, anomalies and risky communications.
- Identify exploits, attacker tools, malware in East West traffic and external communications
- Identify assets behaving abnormally from known-good profile
- Retrospectively identify infected assets when new indicators of compromise are discovered
- Accelerate response with automated policies, enforced on existing security infrastructure.