Respondents on asset visibility issues
%
45% of professionals agree that lack of common view of assets across security and IT teams causes vulnerability patching delays.
Respondents say vulnerability prioritization is an issue
%
Failure to prioritize vulnerabilities is an issue. Risk-based prioritization help teams focus on the right ones for the business
percent fewer breaches with risk-based vulnerability
%
80% of organizations observe fewer breaches when they use a risk-based vulnerability management approach.
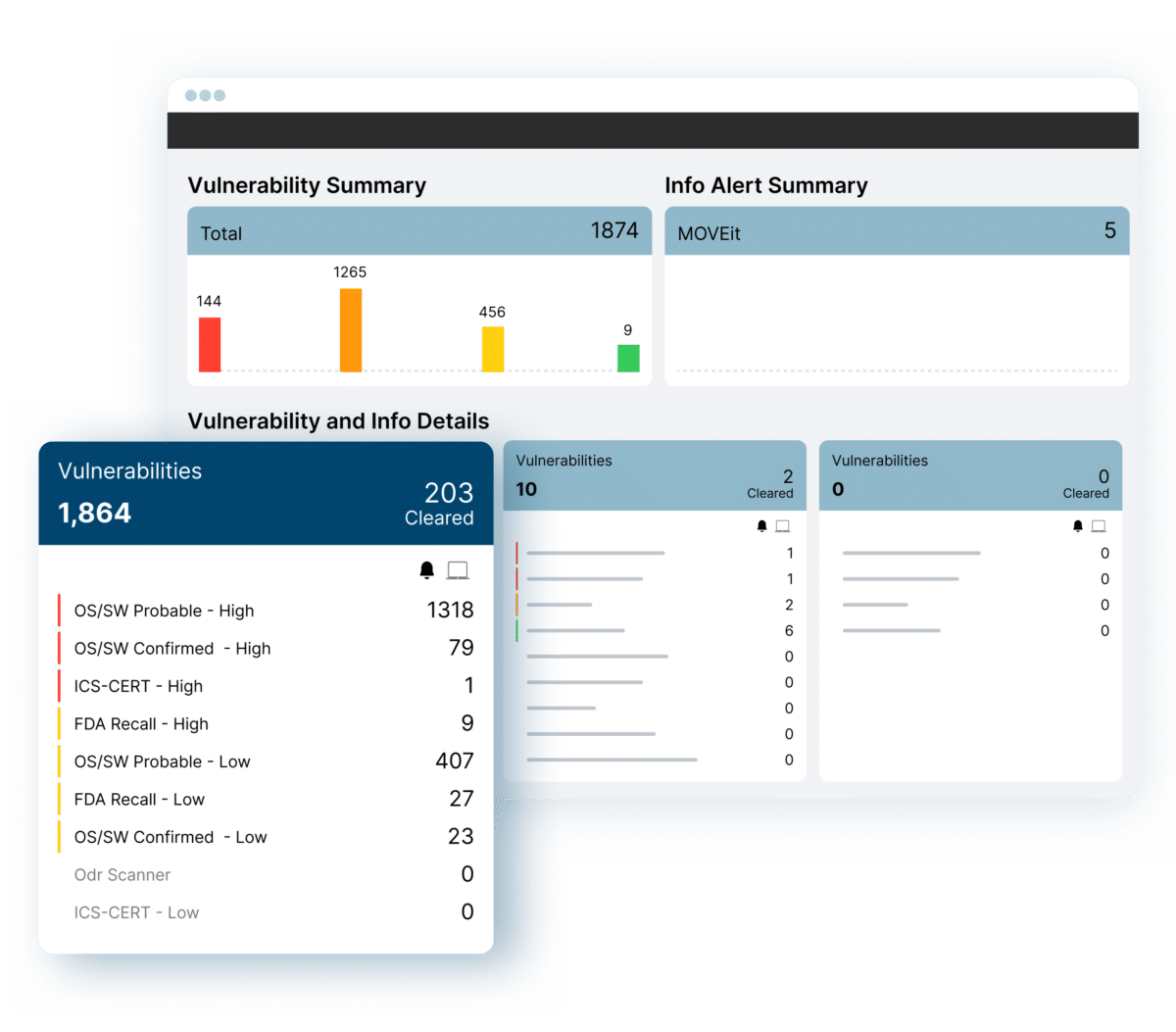
VULNERABILITY DETECTION
Discover and Understand the Complete Vulnerability Landscape
ORDR uses a combination of API data collection, proprietary discovery methods, and AI/ML classification to deliver accurate asset visibility and context. This asset data, mapped with vulnerability databases, provides a holistic and up-to-date view of your entire attack surface:
- Comprehensive vulnerability mapping via NVD, MITRE, ICS-CERT, FDA, Recall DB, OpenVAS
- No blind spots. Detect vulnerabilities on IOT, IOMT and OT devices without impacting operations
- Know if you’re vulnerable to a Zero Day. ORDR Scanner identifies zero days like Log4J, PrintNightmare, Ripple20
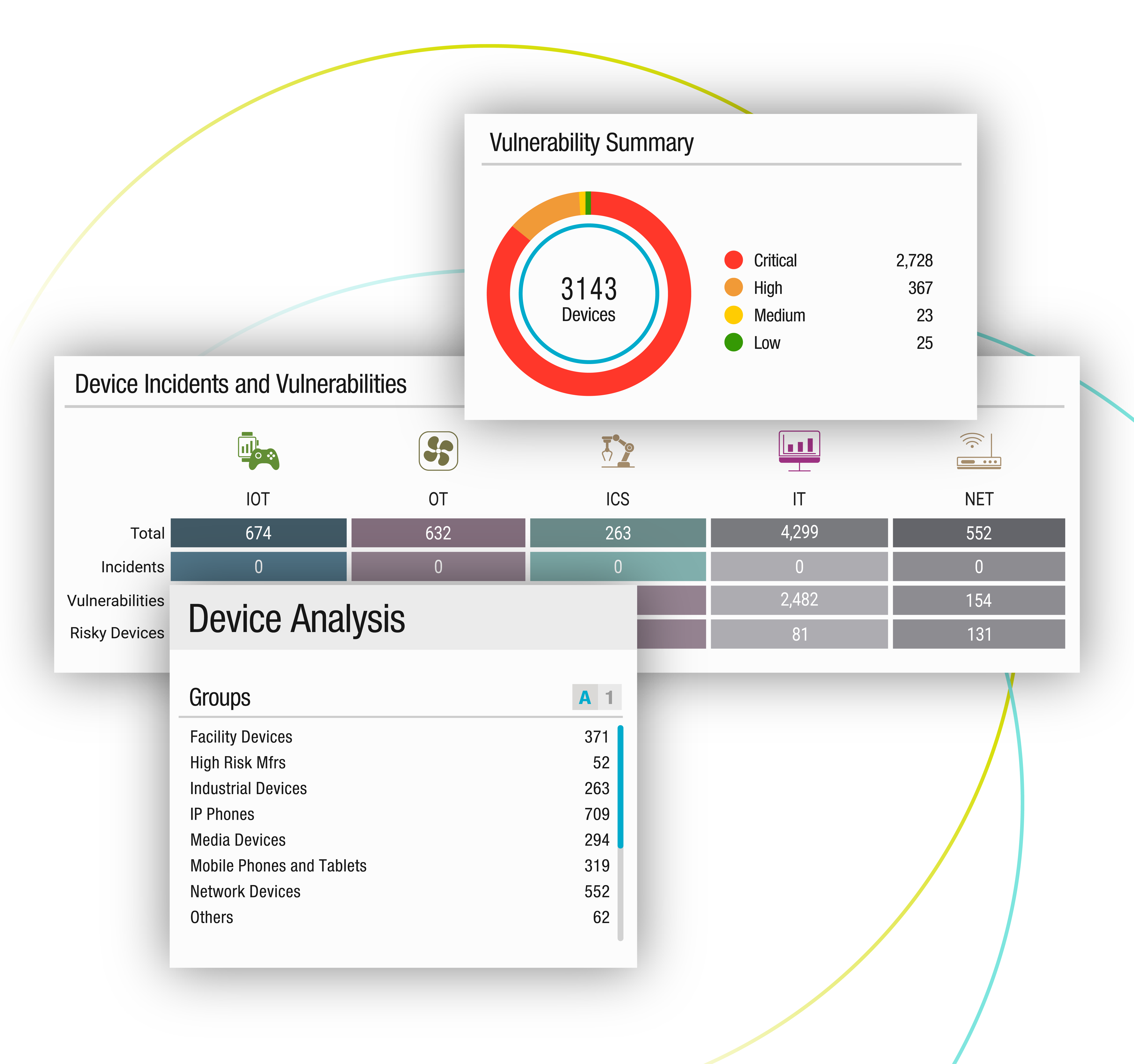
RISK-BASED PRIORITIZATION
Simplify Vulnerability Prioritization and Management
CVSS scores aren’t enough! Security teams need to focus on the vulnerabilities that bring the biggest risks to the business. ORDR empowers teams with asset risk scores for a risk-based approach to vulnerability management:
- ORDR Asset Risk Score considers factors like asset context, CVSS scores, vulnerability exploitability, type of data (encrypted), location and more
- ORDR Software Inventory Collector delivers accurate OS, application and patching details
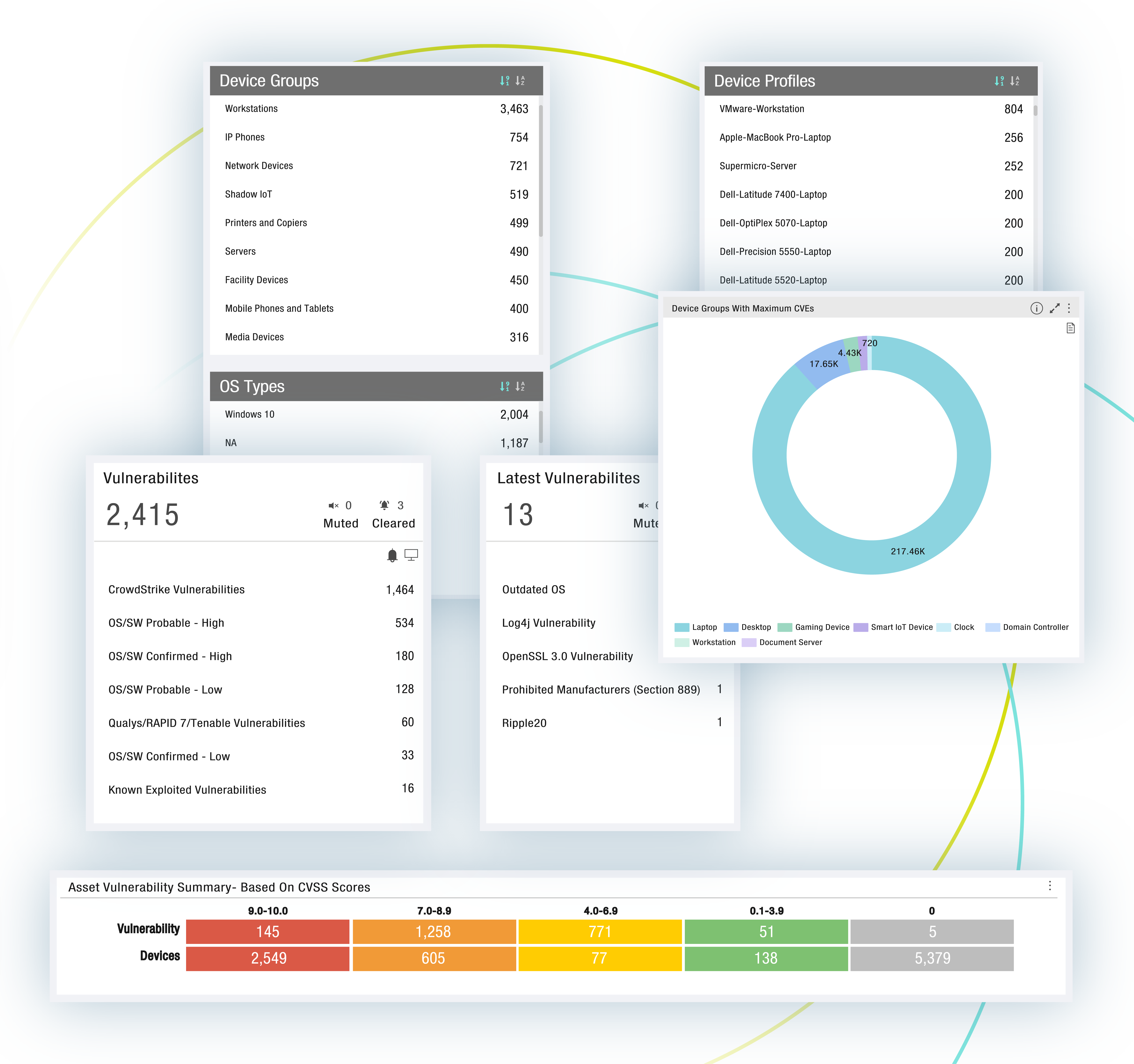
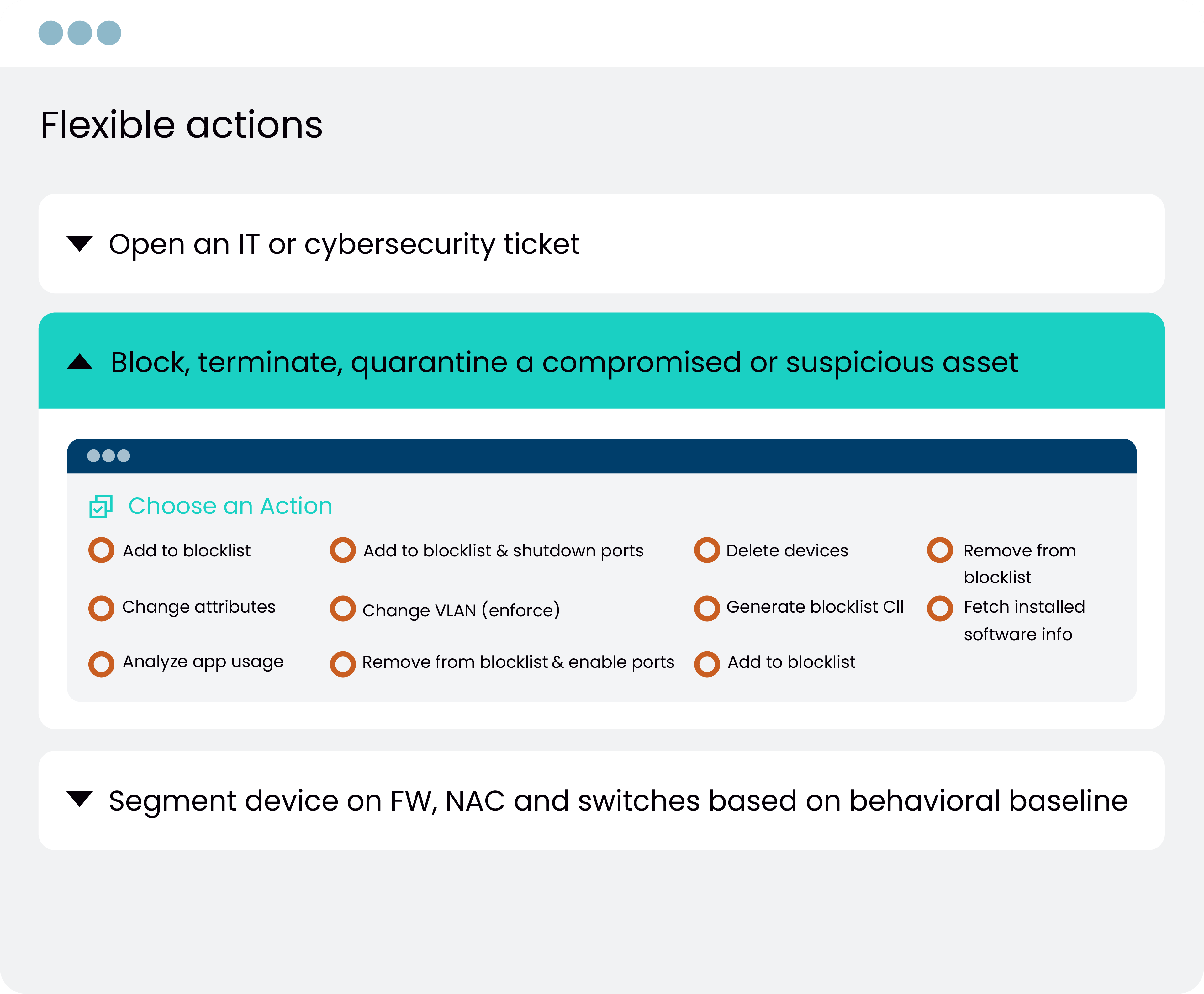
VULNERABILITY REMEDIATION
Automate Remediation And Segmentation
Every unpatched vulnerability is a potential threat vector. Accelerate vulnerability remediation or mitigation with automated workflows and policies, assigned to the right owner.
- Integrate with ITSM workflows and assign remediation to the right device owner
- Create Zero Trust segmentation policies for assets running outdated operating systems that cannot be patched, limiting to baseline communications
- Create segmentation policies for vulnerable assets until patches or resources are available
Customer Case Studies

The Ordr SCE gives us visibility into a breadth of devices that we didn’t have before. Before Ordr, we didn’t have a full view of any devices outside of printers and laptops. Now we have complete visibility into every device, across the enterprise
Clint Perkinson
Director of Information Systems

We liked the simplicity of the ORDR solution coupled with its forensiclevel insight. It’s very intuitive and quick to install—even on a network
of this size—and it instantly started cataloging and risk profiling every
single device on our network.
Darran Lebas
Network & IT Security Manager

Working with Ordr has been a really positive experience where the
system was installed quickly, giving us results from day one. We were
a little surprised at what we found on the network, but I suspect
we’re not alone on that front!
Stephen Hacon
IT Manager