There has been a lot of confusion about the future of cyber insurance following recent statements by market makers Lloyd’s of London and Zurich Insurance Group. In late 2022, Lloyd’s informed underwriters in its syndicate that they would be required to explicitly exclude coverage for damages related to state sponsored cyberattacks. More recently Zurich CEO Mario Greco told the Financial Times, “What will become uninsurable is going to be cyber,” adding that if a threat actor “takes control of vital parts of our infrastructure” the results may be uninsurable.
Those statements, coupled with well publicized policy price increases for 2023 that are as much as three times higher than what many customers paid the year before, have fueled concerns that cyber insurance coverage may be unavailable in the near future and that many underwriters may simply get out of the business. In many ways what we are seeing is the maturation of what remains a relatively new market trying to find its footing in a dynamic threat and risk landscape. Because of that, questions and confusion are rampant, and rational answers from seasoned experts are needed. That is why Ordr recently convened the Cybertrends and the Impact on Cyberinsurance webinar with Marc Schein, national co-chair, cybersecurity center of excellence, Marsh McLennan Agency, and Jim Brady, vice president cybersecurity and risk management, and CISO at Fairview Health.
A Little History
For context, the first cyber insurance policy was written in 1997 by AIG and, according to The Insurance Journal, “Covered only third party suits arising from breaches originating from outside the company.” Optimism for the insurance industry’s first new product category in decades was high, but as underwriters began entering the market in the early 2000s, the challenges associated with an increasingly difficult threat landscape became evident. The number of threat actors, including lone wolf hackers, criminal syndicates, and state-sponsored adversaries, was growing quickly, and the tools available to them were becoming more effective. As new threats emerged, the insurance industry struggled to keep current.
Fast-forward to 2020 and, with the outbreak of Covid-19, things got bad. In the chaos of a global pandemic threat actors took advantage and began focusing on the use of ransomware. Few organizations were prepared for the attacks, and the insurance industry’s risk calculations were turned upside down. Schein said many “underwriters were paying out more in claims than they were collecting in premiums because they were unprepared for the rise in ransomware.”
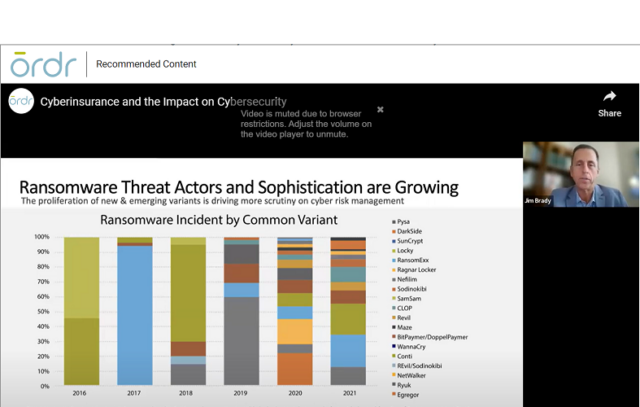
Ransomware Disruption
According to Marsh, there were 4,000 ransomware attacks per day in the U.S., and the cost to the insurance industry was $20 billion in 2021. Then, in 2022 with the outbreak of hostilities between Russia and Ukraine there was another sudden shift in the industry’s risk calculus. The potential for acts of cyberwar targeting critical infrastructure and industry, coupled with continued escalating risks for industries like healthcare, forced the insurance industry to make numerous adjustments to its risk assessments, culminating in steep premium increases along with policies and exclusions written with greater specificity.
In hindsight these changes shouldn’t come as a surprise. If anything, organizations that used cyber insurance as a major part of their risk management strategy had been getting a great deal. But as the industry has become more educated on the risks, that experience is now forcing organizations to (finally) take their own cybersecurity programs more seriously. No more cutting corners. Instead, to qualify for coverage, savvy insurers are demanding that organizations be able to demonstrate that they have complete visibility and understanding of their IT estates, and have implemented controls sufficient to protect their assets.
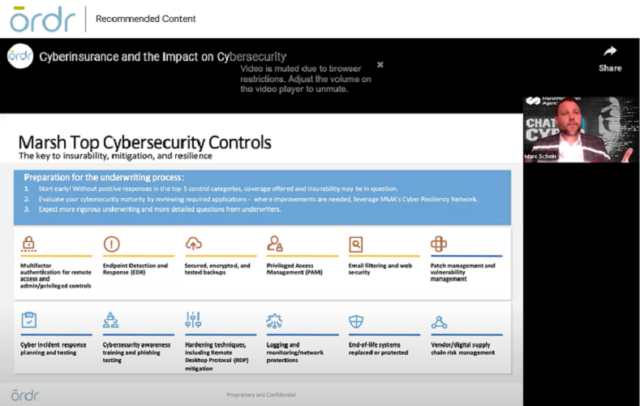
Gain Control
As an early player in cyber insurance, brokerage, risk management, and reinsurance services firm, Marsh McLennan has been a leader in its industry with a deep understanding of what it takes for customers to protect themselves from cyberthreats. The firm offers a list of twelve security controls it requires of its customers that Schein shared during the webinar–along with the caveat that a failure to demonstrate use of the first five is likely to disqualify the organization for coverage. Those twelve controls are:
- Multifactor authentication (MFA) for remote access and admin/privileged controls
- Endpoint detection and response (EDR)
- Secured, encrypted, and tested backups
- Privileged access management (PAM)
- Email filtering and web security
- Patch management and vulnerability management
- Cyber incident response planning and testing
- Cybersecurity awareness training and phishing testing
- Hardening techniques, including remote desktop protocol (RDP) mitigation
- Logging and monitoring/network protections
- End-of-life systems replaced or protected
- Vendor/digital supply chain risk management
The Marsh checklist signals a growing savvy within the industry that knows more information means more accurate risk assessments. As Robert Parisi, North American head of cyber solutions for Munich Re recently told the Wall Street Journal, “The underwriting is aggressively moving toward, ‘How can we get a deeper, more insightful look.’”
What’s missing on this checklist? In the webinar, we raised the question of why asset visibility, security, and segmentation were not included in the list of controls. In fact, the broad “endpoint detection and response”, “patch management and vulnerability management,” and “end-of-life systems replaced or protected” all require visibility into assets and the risks they bring.
Deeper Insight
That requirement for deeper insights into the customer’s risk posture can translate to an advantage for some organizations when shopping for a cyber insurance policy. The ability to provide proof of asset visibility across their entire enterprise can mean a stronger position when shopping for a policy and negotiating with potential underwriters. Brady discussed the advantages Fairview has enjoyed by “coming to the table ready to roll” with necessary controls fully documented. This includes proof the organization has gone beyond an insurer’s requirements by implementing complete asset inventory management and network segmentation to ensure the organization’s ability to quickly detect and effectively mitigate risks.
How can you even detect something bad going on [with a device] if you don’t even know you have it?”
Jim Brady Fairview Health
“How can you even detect something bad going on [with a device] if you don’t even know you have it?” Brady asked, highlighting the strategic advantage of having complete device visibility across the entire network.
Good News
Schein agreed, and delivered surprisingly good news when he said, “If you are engaging better controls and you do improve your security posture, the marketplace is getting significantly better.” He then shared that, even as sharp premium increases grab headlines, 14% of Marsh’s customers enjoyed a price decrease by aggressively improving their overall security posture.
If you are engaging better controls and you do improve your security posture, the marketplace is getting significantly better.”
Marc Schein Marsh McLennan Agency
Clearly, security leaders that have invested in maturing their cybersecurity program with asset management, and excellent controls at the core are reaping the benefits by not only hardening their enterprises against attacks, but by reducing their overall risk profile. Many security leaders recognize that Ordr can play a key role in that equation by giving its customers the ability to see across the entire enterprise to continuously discover and classify an organization’s complete connected device inventory. What’s more, the Ordr Data Lake ensures deep insight into every device’s risk profile with a real-time understanding of communications and operational behavior that could signal an indicator of compromise. Those insights can trigger dynamically created security policies that can be quickly enforced to prevent or contain an attack, and also give insurers confidence that they are working with a customer that takes the concept of Zero Trust seriously and employs strong risk reduction practices.

Interested in
Learning More?
Subscribe today to stay informed and get
regular updates from ORDR Cloud