The world seems upside down at the moment, and it is difficult not to be anxious and stressed. There were times in my past when during stressful moments, I would take a welcomed trip to the Bronx Zoo. The escape from the hustle and noise of the city was a welcome reprieve. I quite enjoyed the simplicity of a walk to visit the animals and wildlife. My personal favorite was the rhinos, healthy and fit yet calm and proud.
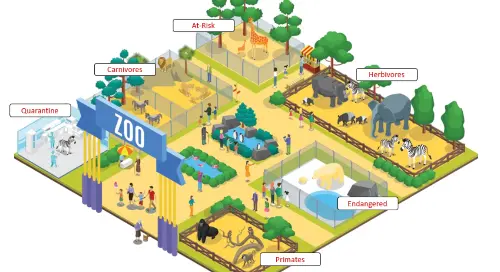
Keeping the Animals Separate
When you enter the Bronx Zoo in New York City, you will notice that the animals are separate in particular areas. At the southern end of the park, there is the African Plains section with the giraffes and wild dogs, and it’s also where you can see the fierce lions basking in the sun. Over by the Himalayan highlands is where visitors can observe the snow leopard and the red panda. So awesome those little red pandas. Between the mountains and the plains, you will find playful characters in the baboon reserve.
There is, of course, a separate world of reptiles, the birds of prey, even Madagascar! Where ring-tailed lemurs roam playfully. At the north section of the zoo by the fountain, the circle is the aquatic birdhouse, the sea bird aviary and the birds of prey. To the east of the main foundation at the Fordham Road gate is where you whisk away to the high plains and see the Bison grazing. Everything in the animal kingdom in its place, everything in order.
Covering over 265 acres, the Bronx zoo is one of the largest in the US and first opened its doors in 1899. Sections and regions are well organized, and every animal, reptile, bird, you name it, is grouped logically together: kingdom, phylum, class, order, family, genus, and species. The ordering makes sense, everything is in their natural habitat, and you won’t find an antelope sharing a snack with the penguins. The order of things is intuitive, and the segmentation implemented adds a layer of protection.
Segmentation Keeps Threats at Bay
Segmentation can also help mitigate risk. At the zoo, you can have external threats, bad actors coming from the outside, and causing damage and internal risk when you can have havoc from the inside. In 2001, an otherwise normal man climbed a 20-foot wall entered the gorilla enclosure, and stripped down to his boxer shorts, telling the NYPD later that he wanted to be “one with the gorillas.” In 2007 Javan langurs (an old-world monkey form the colobinae subfamily) was placed together with Oriental small-clawed otters. The monkeys proceeded with well, monkey business, and it didn’t end well for one of them, a tragic example of internal risk.
Likewise, there are external and internal risks that large enterprises deal with every day. From hospitals to banks to retail operations, information is valuable, and hackers will do anything to attack from the outside to get access to valuable information. An example of internal risk is when compromised employees or vendors go after sensitive information, or if an employee unknowingly grants access to an attacker by clicking on a phishing link in an email.
Similar to the order of things at the zoo, we help organizations segment their networks in a manner that makes sense. We can divide networks granularly down to the workload level and define specific security policies for these specific segments and workloads. So instead of just using gates and fences seen at some local animal farm, it’s a more secure process where movement can be monitored, communications can be traced, and all the animals can roam but stay in their respective regions.
If and when a deviation occurs (a crocodile gets out, or a device in the ER room talks to the finance department), our system can take remedial action right away. If a green peafowl escapes, there is no need to close the entire zoo. Our system is smart enough to contain the bird in the right area.
Segmentation Keeps Red Pandas and Networks Safe
With Ordr, we can help reduce the number of alerts and alarms and act fast when something unexpected happens. We proactively protect the enterprise network, and traffic is analyzed at multiple layers. Our SCE system creates a conversation map called the flow genome for every connected device. We can identify all communications between the various segment and VLANs, and we leverage AI to baseline normal communication behavior and then translates these behaviors into a device-specific security policy. The red panda will be proud.

Interested in
Learning More?
Subscribe today to stay informed and get
regular updates from ORDR Cloud