The definition of a cyber asset has evolved significantly, expanding beyond network devices to encompass a wide array of elements such as users, applications, SaaS, and cloud resources. The shift to a distributed, hybrid workforce further complicates matters as administrators need visibility into assets that traditional, on-premises security controls do not protect. As a result, security and IT teams are now tasked with managing hundreds, thousands, and even millions of cyber assets to protect their organizations from cybersecurity threats. Unfortunately for CISOs and their teams, this broadening definition has expanded the cyber asset attack surface, making it larger and more diverse, creating new challenges for enterprise security teams, including:
- Incomplete asset inventory leading to network blind spots, particularly with IoT, OT, and IoMT devices.
- Duplicate asset entries and inaccurate inventories due to reliance on tracking assets using IP addresses.
These challenges hinder incident response and make it difficult to understand—and limit—an attack’s blast radius. They also complicate the task of identifying security gaps, vulnerabilities, and prioritizing cyber risk management. And when incidents do occur, it is challenging for security and IT teams to quickly identify which assets are impacted and understand the connections to other devices on the network, leaving them to rely more on guesswork than data-driven analysis.
OrdrAI CAASM+ Enables Enterprise Teams to Improve Their Security Posture and Reduce the Attack Surface
Going beyond API-only solutions, OrdrAI CAASM+ provides security teams with complete visibility and data for all assets, including devices (IT, IoT, OT, IoMT), cloud, installed software, SaaS, and users. Then, utilizing a combination of over 180 security and IT ecosystem integrations a proprietary discovery technology and AI/ML classification, Ordr empowers security teams with a unified platform to address critical asset management questions such as:
- How many cyber assets do I have?
- What software is running on my devices?
- What is the blast radius of a compromised cyber asset?
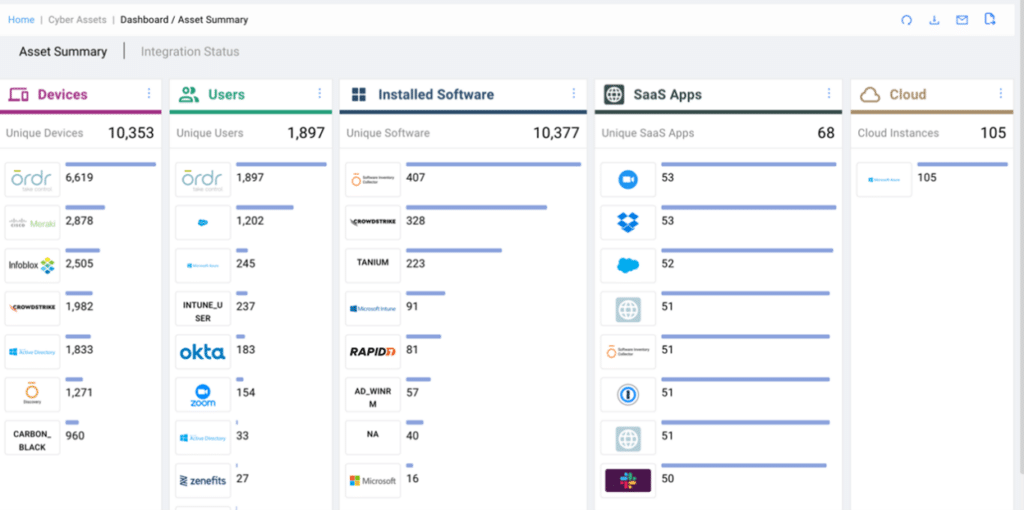
To help enterprise organizations maintain up-to-date asset information and enhance overall security posture, Ordr recommends integrating with a variety of data sources, including:
- CMDB
- IPAM
- EDR
- MDM
- AWS for cloud assets
- Network infra integration (SNMP)
- Active querying from Ordr
OrdrAI CAASM+ Deduplicates, Normalizes, and Aggregates Asset Data and Correlates it into a Single Source of Asset Intelligence
Merely seeing an organization’s entire asset inventory is not enough. What enterprise organizations need is comprehensive, accurate asset visibility coupled with in-depth asset context to tackle critical security and IT use cases head-on. To provide this data, Ordr uses a multi-level de-duplication technique to consolidate and compress the asset data based on the set of attributes to provide an accurate asset count. This eliminates issues with duplicate assets such as when data is collected from EDR using MAC addresses and VA using IP addresses, resulting in duplicate entries.
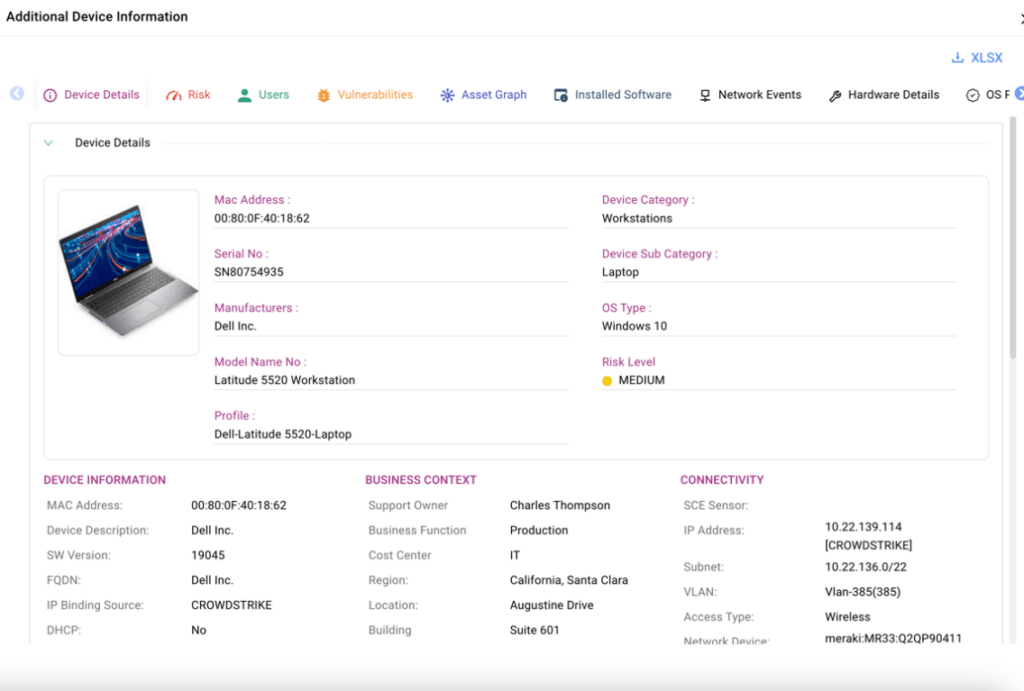
Tracking all assets independently and displaying this data within the platform, CAASM+ provides teams with the necessary asset insights to determine the blast radius of an exposed asset. The information is readily available in the user interface, as shown below, and can be accessed for any type of asset with a simple click of a button.

Using AI/ML Classification, Ordr Provides In-Depth Asset Context to Reveal Security Issues and Coverage Gaps in Asset Management
Over the last six years, Ordr has built a crowd-sourced asset repository—the Ordr Data Lake—comprising data from over 1.5 million different assets across networks from all industries. Leveraging our proprietary AI/ML technology, Ordr classifies and assigns a three-level hierarchy for every asset. This classification enables Ordr to assign a risk score based on business context and asset criticality. Additionally, it allows the enterprise security admins to easily find and identify security infrastructure gaps, eliminating guesswork by clearly defining security control boundaries. This allows teams to distinguish which devices require Endpoint Detection and Response (EDR) and which already have it installed. This differentiation is crucial, as it ensures that teams do not waste time on devices that cannot support EDR installation.
When starting from a foundation of comprehensive, accurate asset inventory, enriched with in-depth context and business insights, security teams can better address critical challenges in cyber asset visibility and management. OrdrAI CAASM+ empowers organizations by providing:
- Actionable asset data and detailed business insights, such as make, model, OS, serial number, connectivity and more. This data can be easily share with CMDBs and other IT tools to reconcile asset data and easily identify missing assets, update records, and remove outdated information.
- Generative-AI powered natural language search to easily obtain answers about your security posture and identifying security issues.
- Asset risk scores to prioritize and remediate risks and exposures based on asset context, CVSS scores, vulnerability exploitability, type of data (encrypted), location, and more.
- Streamlined remediation through automated workflows integrated with ITSM, SIEM, and SOC, ensuring actions are assigned to the appropriate device owner.
Do these challenges sound familiar? Schedule a meeting with our team of security experts to learn how you can leverage Ordr’s automated, accurate asset inventory management solution to proactively prioritize and reduce risks and exposures, streamline incident response, and enhance your overall security posture.
Thanks for joining us for another blog in our series on CAASM+ use cases. Stay tuned as we explore more of these critical use cases in the coming weeks and discuss how Ordr addresses them.

Interested in
Learning More?
Subscribe today to stay informed and get
regular updates from ORDR Cloud