In April 2025, an alerting story emerged from a major U.S. hospital: a pharmacist had allegedly spent nearly a decade spying on coworkers by exploiting hospital systems — including connected security cameras.
The case isn’t just about insider abuse. It’s about how agentless, unmanaged devices like security cameras can be quietly manipulated without detection.
What happened
According to multiple sources, the attacker used legitimate badge access to enter restricted areas and install keylogger software on more than 400 hospital computers. These tools quietly captured credentials, enabling unauthorized access to both hospital systems and victims’ personal accounts — including home surveillance cameras.
A central element of the scheme involved network-connected cameras. The attacker reportedly manipulated them to stream footage to personal devices. This raises a critical question: Why was a hospital camera permitted to send data to an unauthorized destination in the first place?
The breach only came to light after an FBI investigation. By that point, significant damage had already been done.
Where security broke down
This wasn’t a zero-day exploit or a ransomware gang operation. It was a long-running campaign rooted in overlooked devices, weak controls, and poor visibility.
Key security gaps included:
- Lack of visibility into connected cameras and other agentless devices. The attacker could repurpose them without raising alarms.
- Insufficient access controls failed to flag or prevent inappropriate physical access.
- No software inventory to detect keylogger installations on hospital workstations.
- No behavioral monitoring to catch devices streaming data externally or communicating with unauthorized endpoints.
- Default or weak credentials that made cameras and other devices easy targets.
This case serves as a real-world example of what happens when agentless and unmanaged devices are treated as out of scope for enterprise security.
How ORDR helps you take control
Best practices like strong access control, credential hygiene, and behavioral monitoring are essential—but extremely difficult to enforce consistently across a dynamic, distributed enterprise. Especially when you’re dealing with thousands of devices that don’t support agents.
ORDR is built specifically to bring visibility, intelligence, and enforcement to these blind spots. Below are key areas where ORDR closes the gaps—with [screenshot] placeholders to show platform examples.
Full camera and device visibility
ORDR automatically discovers and inventories all connected devices in your environment, including those never formally onboarded by IT. It enriches that inventory with deep context, allowing teams to quickly identify risk.
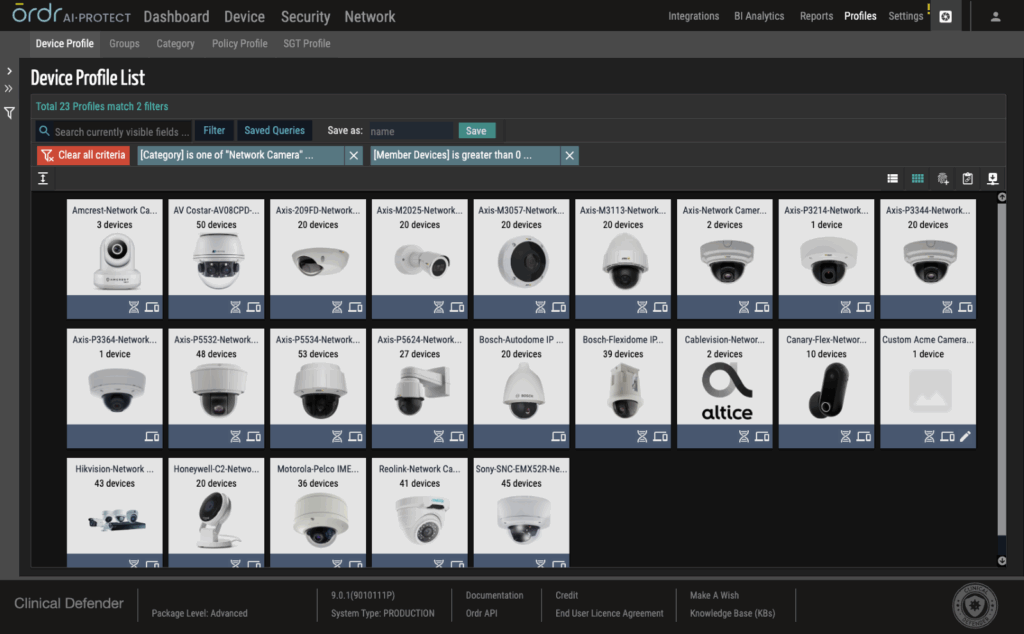
Behavioral profiling and segmentation
ORDR builds a behavioral baseline for every device — what protocols it uses, where it communicates, and what’s normal for its role. This makes it easy to identify deviations and take action.

Risk and vulnerability insights
ORDR continuously evaluates devices for security hygiene and vulnerabilities, prioritizing what matters most based on exposure and criticality.
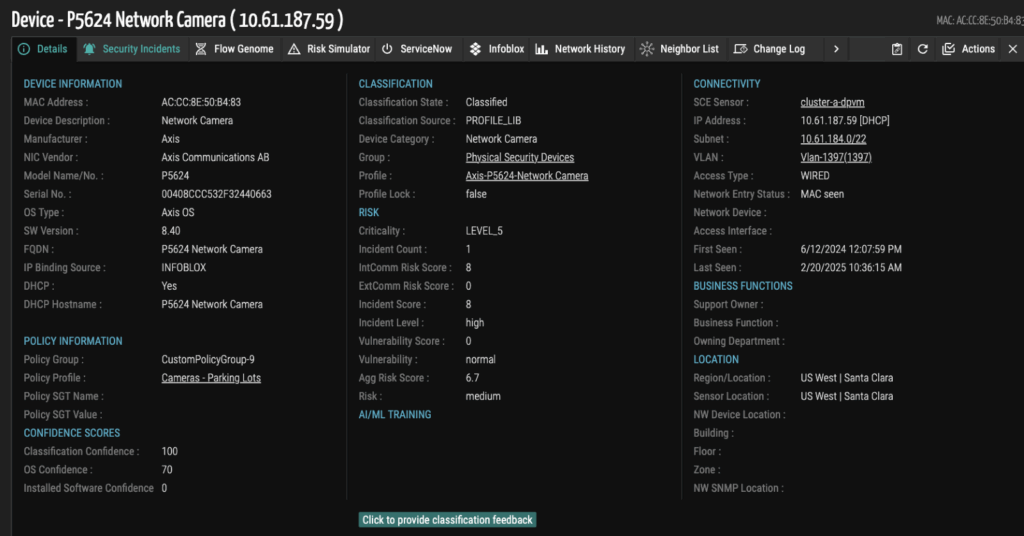
Dashboards for visibility and operations
A centralized command center provides both high-level insights and deep operational detail, supporting everything from compliance reporting to incident investigations.
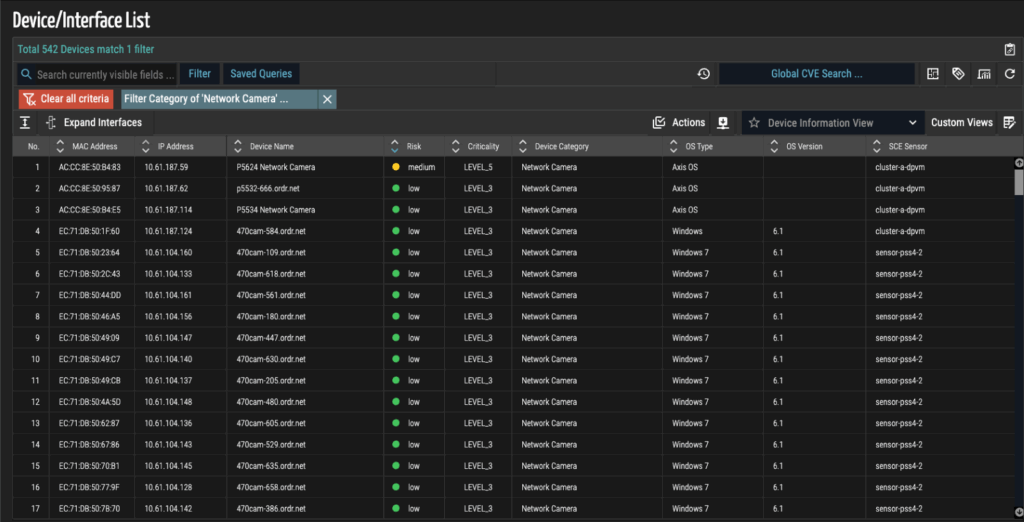
Real-time alerting and enforcement
ORDR enables immediate response when something risky or malicious occurs — whether that’s a new rogue device, an unauthorized connection, or malware being installed.

Why this matters now
As hospitals, manufacturers, and enterprises expand their digital infrastructure, the number of agentless and unmanaged devices continues to grow. From security cameras to smart displays, these assets are often invisible to traditional security tools.
When these blind spots are left unchecked, they become footholds for attackers — whether internal or external. The breach earlier this year is just one example of how agentless devices can be exploited without ever triggering traditional defenses.
Next steps
To learn more about the growing risks posed by unmanaged and agentless devices, explore our Rise of the Machines Report. If you’re ready to see how ORDR brings visibility, control, and security to these blind spots, request a demo today to experience the platform in action.

Interested in
Learning More?
Subscribe today to stay informed and get
regular updates from ORDR Cloud



