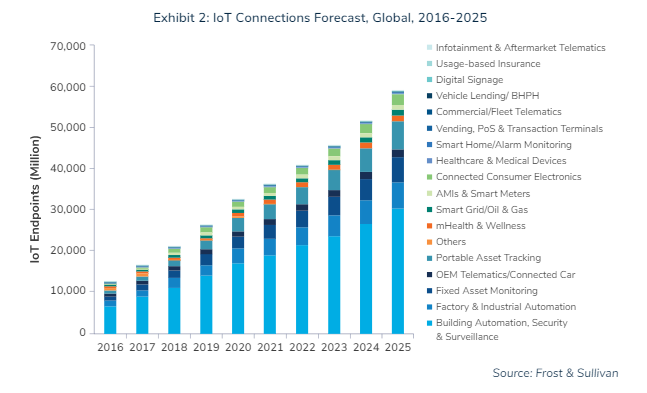
Internet of Things (IoT) are now in every aspect of enterprises. As businesses grow, adding more and more devices to their networks, they face unique challenges in securing IoT. Frost and Sullivan, in their most recent report “Strategic Assessment of the IoT Security market” expects the number of IoT devices to grow from around 34 billion devices in 2020 to over 60 billion by 2025″:
As IoT adoption increases, IoT security is becoming critical. Many IoT devices lack basic security features, cannot be easily patched, and run obsolete operating systems. The ideal scenario is to build security into these devices, which some states and the Federal government are advocating via legislation such as the California SB327 or the IoT Cybersecurity Improvement Act. But with billions of insecure IoT devices already deployed, organizations need cybersecurity solutions that can address IoT security today.
In this report, Frost and Sullivan also calls out the need for an IoT security solution that offers the following:
- Network Monitoring: Network monitoring, or network detection and response solutions that incorporate deep packet inspection technologies can extract granular insights about devices. This can be combined with artificial intelligence (AI) and machine learning (ML) technologies to map and baseline every device communications.
- Integrated IT, IoT, and OT Cybersecurity: As IT and IoT/OT networks, the need for multifunction platform that offer the “whole enterprise” approach is important.
- IoT Risk Management: A solution that can help identify risks and defines anomalous behavior is important
- Network Segmentation: A good best practice to protect connected devices is via segmentation. Zero Trust segmentation ensures devices have appropriate access required for its role, while limiting access, and can be enforced on next-generation firewalls or in the network (switches, network access control)
In fact, these are the key building blocks of the Ordr platform – a whole organization approach to device security that combines DPI with AI to classify devices, profile risks and behavior and automate response including Zero Trust segmentation. Our capabilities include:
- Device discovery: Within a few hours of deployment, Ordr discovers high-fidelity context on every connected device, including make, OS, location and application/port usage
- Device flow analytics and baselining: Ordr passively monitors network communications and creates a conversation map, called the Ordr Flow Genome, for every connected device.
- Security response: Ordr automates device identification and uses AI to baseline normal communication behavior, then translates these behaviors into a device-specific security policy
- Detection of internal reconnaissance and lateral movement: For reconnaissance and sniffing, the Ordr behavioral baseline of the compromised devices can spot these activities as soon as the flow starts to a destination from a device that has the malware infection to a device to which it has never had any flows
- Comprehensive device insights for businesses: Ordr sees the device the moment it becomes active in the network, records operational activity and records the time it goes offline
Learn more about Ordr’s IoT security solutions.

Interested in
Learning More?
Subscribe today to stay informed and get
regular updates from ORDR Cloud



