ORDR has one of the most robust channel partner programs in the market, and I often meet with our partners to understand not only what opportunities they’re working on, but also address any questions they have about our products.
In a conversation with Steven Dastoor of CITON recently, we spoke about the convergence of IT and OT environments, and how it was important to have visibility and security for IT (IoT) and OT devices. The Colonial Pipeline attack demonstrated that the security of IT systems is just as important as OT, because when your billing system goes down, your business operations are impacted even if the ransomware did not hit the OT systems.
We discussed best practices and specifically the recommendations outlined in the September 2020 Microsoft Digital Defense Report on securing IoT/OT Networks.
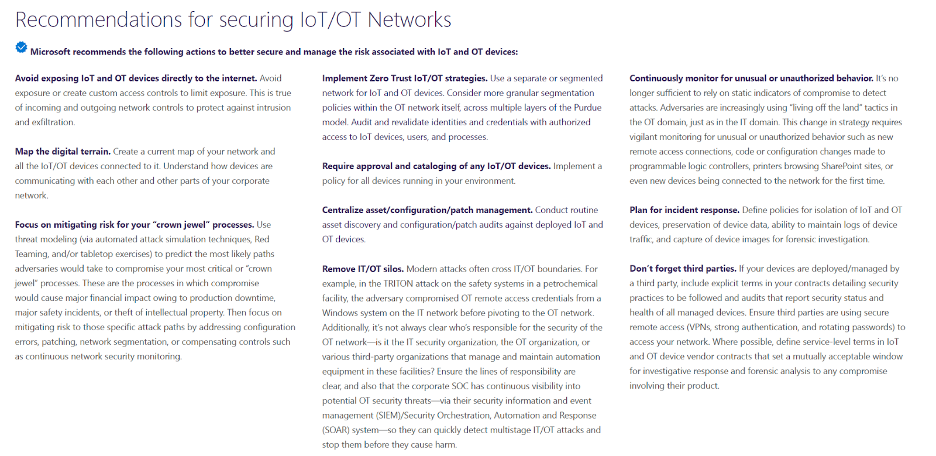
These were great recommendations by Microsoft. Here’s how ORDR maps to them:
Reducing exposure of IoT/OT devices
Beyond discovering and classifying all connected devices– from traditional servers, workstations and PCs to IoT, IoMT and OT devices. ORDR profiles device behavior and risks, and then automates appropriate action. In addition, there are visual representations of your network and associated risk. You can view this at the device group level easily to see all devices with communications to the internet in our ORDR Traffic Analysis connectivity map, or at the individual device level in our ORDR Flow Genome. We also integrate threat intelligence from multiple sources, enriching the ORDR Data Lake with data on emerging threats, domains associated with phishing sites, Command and Control (C2) infrastructure etc. We can also map “good behavior,” and flag and alert on any anomalies or new traffic patterns we have never seen before. This good behavior can be shared with other tools like the firewalls, switch infrastructure too, to create zero trust policies that only allow a device access and communication flows it needs. Anything else is automatically blocked based on the dynamically generated policies.
Mitigating risks
ORDR has a number of capabilities to first identify devices that are high-risks. These include devices with weak passwords and certificates, running outdated operating systems, or with vulnerabilities. ORDR also includes an integrated Threat Detection Engine that detects exploits and active threats, in addition to machine-learning models that alerts on anomalous traffic. ORDR helps validate security-based workflows like red teaming.
In addition, once vulnerable or compromised devices are identified, we can deliver rapid response to remediate and mitigate risks. We dynamically generate policies to save security teams time on manually writing policies individually for VLANs, SGTs, internal Firewall rules. In addition, organizations globally, use ORDR to triage events during the incident response (IR) process, often through enriching their Security Information Event Management (SIEM) solution.
Implement Zero Trust IoT/OT strategies
In order to create the appropriate Zero Trust policies, it is important to not only identify devices but also what they are doing in the network, and be able to create policies that align to business needs. This is one of ORDR’s biggest differentiators– creation of Zero Trust policies and the ability to be able to enforce them across existing networking and security infrastructure such as Aruba ClearPass, Cisco ISE, FortiManager/FortiGate, FortiNAC, CheckPoint, etc…
Centralize asset/configuration/patch management (IT, IoT, and OT)
ORDR delivers real-time asset inventory of every device. As we discover devices on the network, we can push and pull information from tools like ServiceNow or other CMDB/IT Asset Management tools to ensure the devices we see are cataloged by the business. We can keep asset management systems continuously up-to-date about systems that are not being tracked. We see this a lot where ORDR detects devices on the network that do not exist in the Asset Management tool, and also devices that are still in the Asset Management system as Active, but not deployed or online in the environment.
ORDR also works with vulnerability management tools like Tenable and Rapid7 to deliver vulnerability insights into devices that may not previously have been scanned for CVEs.
Convergence of IT and OT
We are a bridge between these teams, as we give them a data set they can both work with, from their unique perspective. I am working with a manufacturer right now where we are delivering visibility and security of their OT and IT networks. Because there aren’t “air-gapped” networks anymore, the IT security team was concerned about exactly what was connected. We found a number of OT Workstations running Windows XP, not part of IT as they are Siemens control systems, But the IT team was using Remote Access (RDP) to connect to them remotely for work. This is similar to how threat actors infiltrated the water treatment plant in Florida. ORDR was able to map out what specific devices are allowed to be part of remote work and remote access, limiting the attack surface. It is a great story of IT and OT coming together to ensure the security and availability of these systems.
Continuously monitor for unusual or unauthorized behavior
The ORDR platform includes a machine learning engine that baselines and maps every single device communications. This baseline allows us to understand what is “normal behavior” and alert on unusual behavior.
ORDR also monitors all devices that use supervisory protocols like SSH, telnet, ftp, etc., associates them with user names, correlates them with the network they logged in from (corporate or guest), and maintains an accurate access record for each and every device as well as each and every user.
Plan for Incident response
We are a critical product for Security Operations Centers (SOCs) and Cyber Security Incident Response Teams (CSIRTs) and should be a tool used in diagnostics. When an incident occurs, ORDR provides the context for the device and details about what it is communicating with. We can also provide insights on communications to C2 sites retrospectively. Finally, we empower SOCs and incident response teams by creating security policies to quickly lock down or isolate a device, block threats through NGFW policies, ACL blocks, quarantine VLAN assignment, port shutdown, or session termination–either directly to firewalls, existing switches, wireless controllers, or via NAC platform.
For example, when the SolarWinds vulnerability hit, we had a customer reach out and ask: “Can you give me an inventory of all of my SolarWinds devices, and where they are in the network”? We did it in two clicks. We also monitored the customer’s environment to see if there were any communications to SolarWinds domains.
Remember third parties
We can monitor third party connections. We see this all the time in healthcare where a third party, like Siemens, is connecting to do remote support on a device, like an MRI. We see the communications coming in from the Netherlands, generally over traditional management protocols like Telnet, SSH, HTTPS, and RDP. We can track the source/destination of this traffic, as well as have the time stamps for when it is occurring. We can then create Zero Trust policies to lock down these management ports, but still allow the third party access that is needed.
Ready to achieve total visibility into what’s on your network? Request a free ORDR sensor today and you’ll be able to see what connected devices are on your network in minutes!

Interested in
Learning More?
Subscribe today to stay informed and get
regular updates from ORDR Cloud




