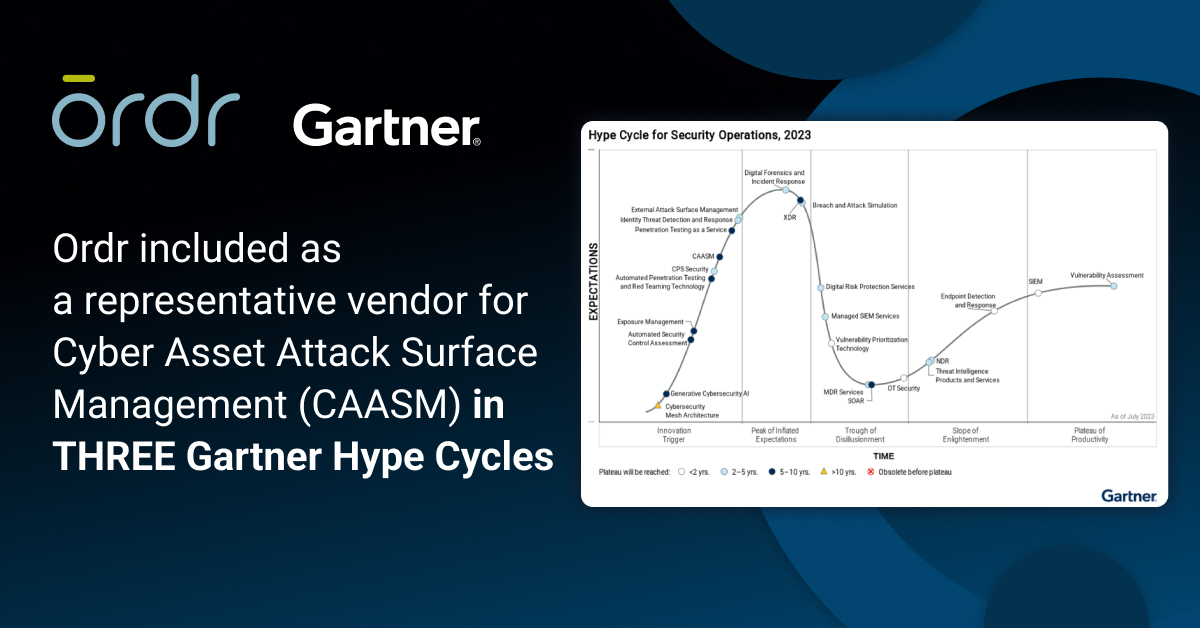
Gartner analysts have been busy publishing several Hype Cycles recently. If you’re not familiar with the Gartner Hype Cycle, it is a graphic representation of the maturity lifecycle of new technologies, and there are several key reports to help security leaders with their strategy and investments. We are thrilled to be included as a representative vendor for Cyber Asset Attack Surface Management (CAASM) category in three Gartner Hype Cycles:
- Hype Cycle for Security Operations, 2023
- Hype Cycle for Cyber Risk Management, 2023
- Hype Cycle for Workload and Network Security, 2023
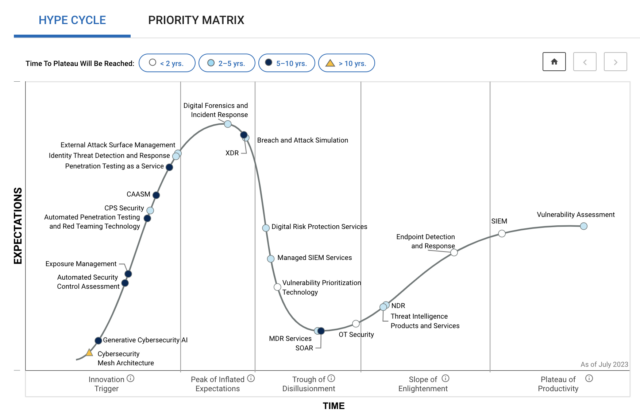
What is Cyber Asset and Attack Surface Management (CAASM)?
As described by Gartner, “Cyber Asset Attack Surface Management (CAASM) is an emerging technology that is focused on presenting a unified view of cyber assets to an IT and security team. These assets can serve as an attack vector for unauthorized users to gain access to a system to steal information or launch a cyber attack. In order to detect assets containing outdated software, misconfigurations, and other vulnerabilities, CAASM tools use API integrations to connect with existing data sources of the organization. These tools then continuously monitor and analyze detected vulnerabilities to drill down the most critical threats to the business and prioritize necessary remediation and mitigation actions for improved cyber security.”
In ORDR deployments, we don’t just aggregate data via API. We also perform our own asset discovery, via ORDR Discovery Engine and ORDR Software Inventory Collector for the most comprehensive visibility into every asset on the network.
Use Cases for Cyber Asset and Attack Surface Management
There are a number of use cases for cyber asset and attack surface management for security teams:
- Asset management – provide granular visibility across all devices (IT, Internet of Things (IoT) and operational technology (OT) assets), installed applications, SaaS and cloud workloads including detailed information about device type, manufacturer, OS version, vulnerabilities.
- Compliance assessment – during an audit, the process to provide details of assets, and the software, antivirus or applications that are running on them, can be very cumbersome if done manually. CAASM can simplify this process.
- Security gaps – identify security gaps across the network, for example, assets that should have a security endpoint agent but do not or assets that are running outdated operating systems.
- IT governance – identify shadow IT devices or assets that should not be on the network, such as gaming devices. ORDR goes a step further and can help with asset reconciliation, for example, comparing what assets we see on the network versus what is actually in the CMDB or vice versa. We can also identify devices that we discover on the network or are missing on the network in the last 24 hours.
- Vulnerability management – identify vulnerabilities associated with assets. Most CAASMs only ingest vulnerabilities from various source systems. ORDR goes further with asset risk scores and vulnerability management details from our ecosystem of integrations (via API), along with ORDR Software Inventory Collector details. ORDR delivers visibility into vulnerabilities on IoT and OT devices that are are typically blind spots for other CAASM vendors.
These use cases are all fundamental CAASM use cases. But, they are just scratching the surface of what’s possible with ORDR. Enterprise security teams deploying ORDR can also expand to deep behavioral intelligence, threat detection and segmentation for mission-critical IoT and OT assets. Because ORDR also maps communications flows for every asset, we can also support the following use cases:
- Baseline flows – the ability to baseline normal communications patterns for every device is critical to identify malicious and anomalous traffic. This can include devices communicating to the Internet, manufacturing or medical devices in the guest VLAN, or devices that are communicating to a malicious command and control domain.
- Bidirectional integrations – Any asset details that we aggregate and correlate is shared with more than 80 networking and security integrations. For example, granular asset and vulnerability details can be shared with CMMS, CMDB, SIEM and traditional vulnerability management solutions like Rapid7, Qualys and Tenable. This ensures a consistent source of truth on all assets and risks across the entire organization.
- Automated policies – Finally, with ORDR, because we have details on assets, connectivity and communications flows, we can dynamically generate proactive Zero Trust segmentation policies to secure devices (to allow only sanctioned, normal communications) or dynamically generate reactive policies to block ports, terminate sessions or move devices to different VLANs during an incident.
Check out a recent Demo Forum panel hosted by Richard Stiennon on Cyber Asset and Attack Surface Management. ORDR’s own Jeremy Haltom participated, and summarizes our value proposition.
In summary, there are many benefits to CAASM, primarily with optimizing resources via automated inventory of what’s on the network. Additionally, with the granular details on risks for every device, organizations can reduce their attack surface, improve operational efficiencies, and streamline compliance assessments. ORDR extends these benefits to even more comprehensive security capabilities, and actionable policies on existing infrastructure that can accelerate incident response by hours.
For more information on the ORDR platform, contact us.

Interested in
Learning More?
Subscribe today to stay informed and get
regular updates from ORDR Cloud