Just for a minute, pretend you’re playing the villain in a game and you want to be the innocent civilians of Metropolis to your will. Your weapon: a special chemical that, when swallowed, will cause a person to do whatever you command. You have two ways to achieve your objective:
- Go house to house throughout the city and slip the chemical into each residence’s plumbing
- Penetrate the municipal water headquarters and dump the chemical into the city’s water tower, which also happens to be largely unguarded
Not a tough choice, is it?
Now you can understand the appeal to cybercriminals who want to do maximum damage — all at once — to corporations and their customers by attacking their software supply chains.
Let’s switch your role again. You now are no longer the villain — now you’re the hero, defending potential victims. And rather than a made-up game, you’re in charge of cyber security for a major corporation and you need to stop the bad guys before they infiltrate your company through a third-party software partner. What do you do?
In this blog, we’ll examine the methodology of the attackers, the status of corporations and suppliers in being aware of and combating the threat, and finally, best practices you can follow to help your company stay safe.
The Soft Underbelly: Software Vendors
Real-life bad guys increasingly like to target software supply chains to reach their ultimate destinations. Their common methodology is to infiltrate a software vendor’s network and employ malicious code to compromise the software, which is sent to the vendor’s customers. It then compromises the customer’s data or system.
The infiltration can come when a company first acquires the vendor’s software or in subsequent actions, such as through a software patch or hotfix. In these cases, the compromise still occurs before the patch or hotfix enters the customer’s network. This is referred to as going “upstream” in the supply chain to compromise systems earlier in the software distribution process.
These types of attacks affect all users of the compromised software and can have widespread consequences for all software customers. As we suggested in the water supply comparison, attacks on software supply chains act as “force multipliers” in gaining access to hundreds or thousands of companies with a single compromise. What looks initially like a minor ripple on the attack surface can almost instantly become a cyber attack tidal wave, damaging organizations near and far.
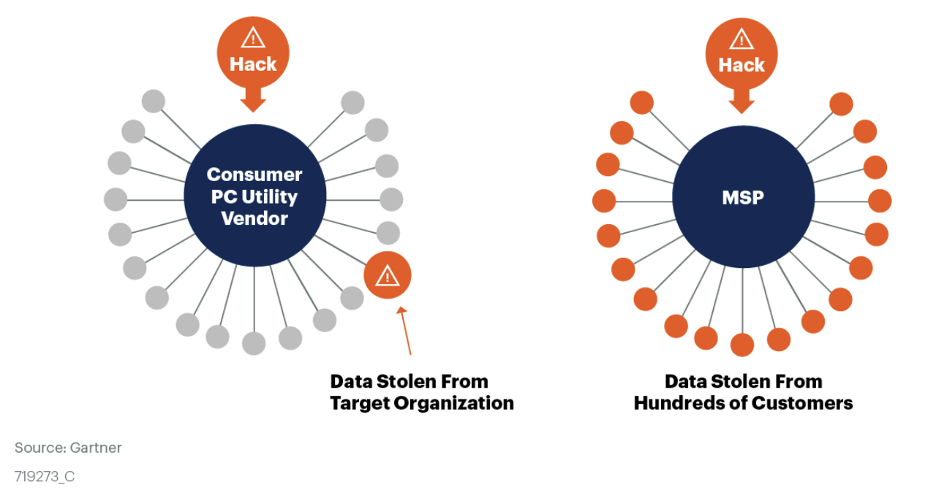
Source: Gartner
Flying Blind on Software Supply Chain Dangers
Overall, organizations don’t have great visibility into risks posed by third parties, especially when it comes to complex software supply chain ecosystems. A full third of organizations are clueless about their software supply chain risk exposure. Only 22.5% monitor their entire supply chain, and 32% perform vendor risk assessments no more than once every six months (BlueVoyant).
Increasingly Complex Attack Methodologies
So how are these attacks being executed? There are three common techniques:
- Compromising software updates
- Undermining code signing
- Exploiting open-source code
The three are not executed in isolation. Rather, they’re often leveraged in combination or with other, less common techniques.
Compromising Software Updates
Software vendors typically continuously distribute updates from centralized servers through cloud infrastructure to their customers. This is part of routine product maintenance. Threat actors can compromise an update by infiltrating the vendor’s network and either inserting malware into the outgoing update or altering the update to grant the threat actor control over the software’s normal functionality. A well-known example of this method is NotPetya, which caused major global disruptions across the financial, healthcare, and industrial sectors.
Undermining Code Signing
Code signing is used to validate the identity of the code’s author and the integrity of the code. Attackers undermine code signing by self-signing certificates, breaking signing systems or exploiting misconfigured account access controls. By undermining code signing, threat actors are able to successfully compromise software updates. They impersonate a trusted vendor and insert malicious code into an update. For example, APT 41, a China-based threat actor, routinely undermines code signing while conducting sophisticated software supply chain compromises against the United States and other countries.
Exploiting Open-Source Code
Open-source code exploitation occurs when threat actors insert malicious code into publicly accessible code libraries, which unsuspecting developers—looking for free blocks of code to perform specific functions—then add to their own third-party code.
These compromised malicious libraries will often contain the same code and functionality of those they are impersonating, but they also include additional functionality that can be used for malicious purposes. This allows the threat actors to obtain boot persistence, open a reverse shell on remote devices, or deploy a remote code execution (RCE) attack. Open-source code compromises affect privately owned software because developers of proprietary code routinely leverage blocks of open-source code in their products.
It Will Get Worse Before It Gets Better
Attackers look to infiltrate and disturb supply chain systems in order to disrupt business and harm a company’s production system. Because there are multiple means of pervading the supply chain, it is difficult to secure all means and prevent an event from happening.
Especially with organizational supply chains and third-party relationships continuing to grow, there is an increasing opportunity for attackers to strike. Nobelium, the Russia-based threat actor behind the supply chain attack on SolarWinds, is targeting cloud service providers and IT services organizations in a large-scale and ongoing campaign designed to infiltrate systems belonging to downstream customers of these companies. “Since May, Nobelium has attacked at least 140 cloud service providers and compromised 14 of them, according to Microsoft, which has been tracking the campaign. Between July 1 and mid-October of 2021, Microsoft security researchers observed some 22,868 Nobelium attacks on organizations in the US and elsewhere (Source: Microsoft).”
Best Practices for Protecting Your Organization
To protect a business from supply chain attacks, we need to identify the areas that pose a risk and maintain a system to safeguard them. The best practices that result from this understanding boil down to these:
- Know what devices and systems are on your network: the first rule of cybersecurity is know what you have. You need to be monitoring devices and systems for anomalous behavior that may have been compromised as part of a supply chain attack.
- Ensure suppliers implement security practices: You’ll need everyone in the supply chain to implement their best housekeeping to secure your business from the very beginning of the supply chain.
- Limit access to data: Prioritize who should be given access, restricting it to only those who need it.
- Implement effective auditing and reporting practices: Collect data and log it for review to understand the methods that work and those that don’t, then only employ the effective practices.
- Test your own security measures: Put your practices to the test and note how they hold up to various threats you may want to emulate.
- Work in collaboration: Communication is key to keeping a good relationship and prioritizing a smooth supply chain exchange of goods.
In Summary
While software supply chains are critical for businesses, attacks on the chains are growing in part due to the multiple alleys of access and the “force multiplier” effect we described at the beginning. It is simple to attack a single network within the supply chain and gain access to several companies at one time.
Therefore businesses must take extra measures to stop supply-chain attackers by emphasizing good relationships, necessary security practices, and routine cleaning and testing. The more these are implemented, the better shape business will be in to nullify the attackers from the onset.
Read More on how ORDR can help with supply chain attacks like Solarwinds.

Interested in
Learning More?
Subscribe today to stay informed and get
regular updates from ORDR Cloud




