person hours spent on asset Inventory
On average, security teams spend 90 person hours per week on manual asset collection.
Devices are blind spots
%
Most asset management solutions are blind to IOT, OT, IOMT devices that make up 40% of assets in a network.
Investigation Hours
It can take 24 hours and more to investigate an alert without accurate asset insights.
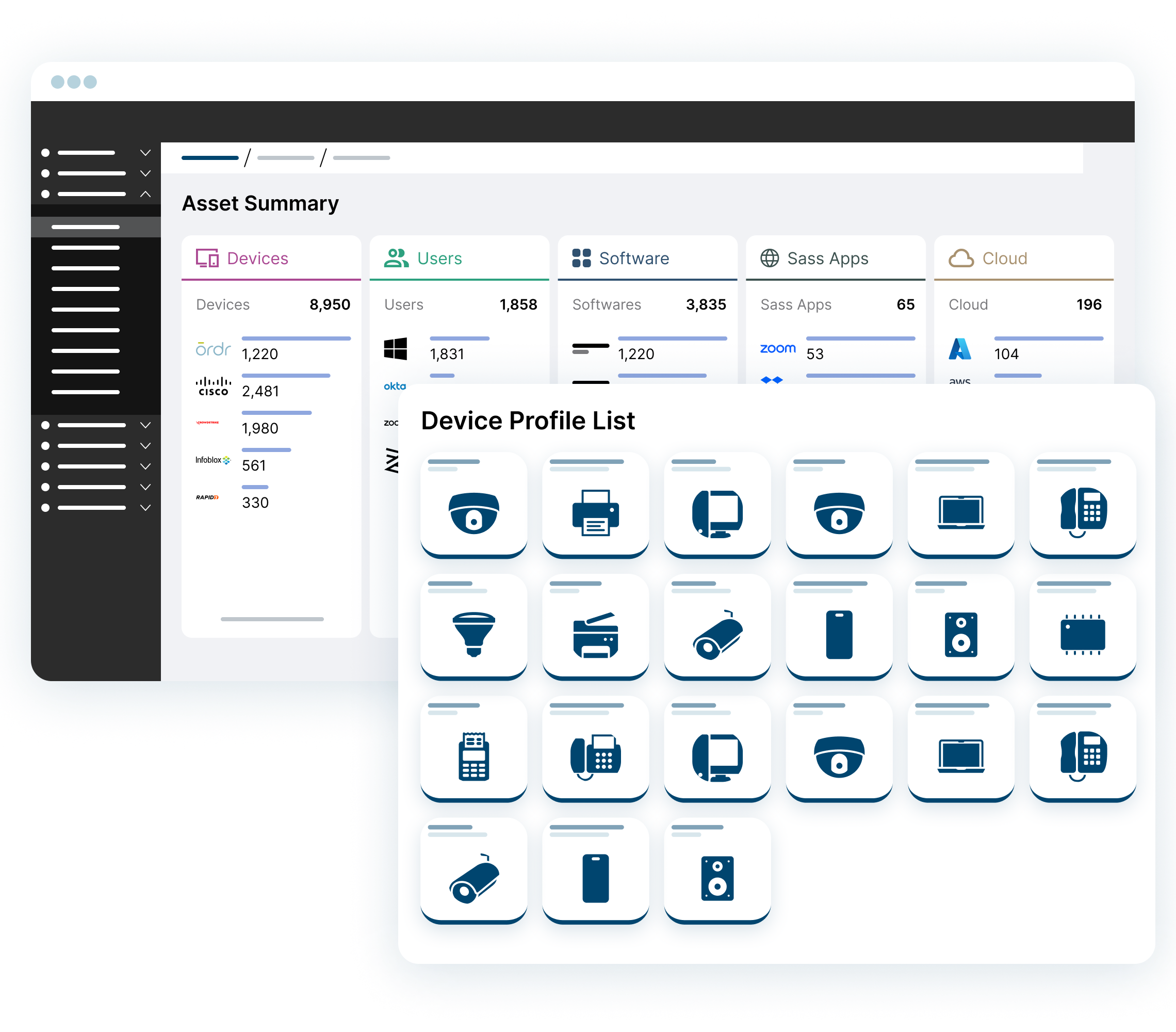
AUTOMATED ASSET INVENTORY
Comprehensive Asset Visibility
Reduce manual efforts to collect and reconcile asset information. Enable automated, accurate asset inventory using API data collection and Ordr’s proprietary Discovery Engine, complete with deduping and correlation to eliminate noise.
- Deep context including make, model, OS, serial number, connectivity and more
- Automated asset classification using AI/ML
- Eliminate blind spots with IOT, OT, IOMT devices
- Identify security gaps like assets missing EDR or MDM agents
SINGLE SOURCE OF TRUTH
CMDB Asset Reconciliation
Enrich CMDB and other IT tools with the most comprehensive, accurate, and trusted insights for all assets. Ensure asset management databases are accurate and reflect the current state of your network.
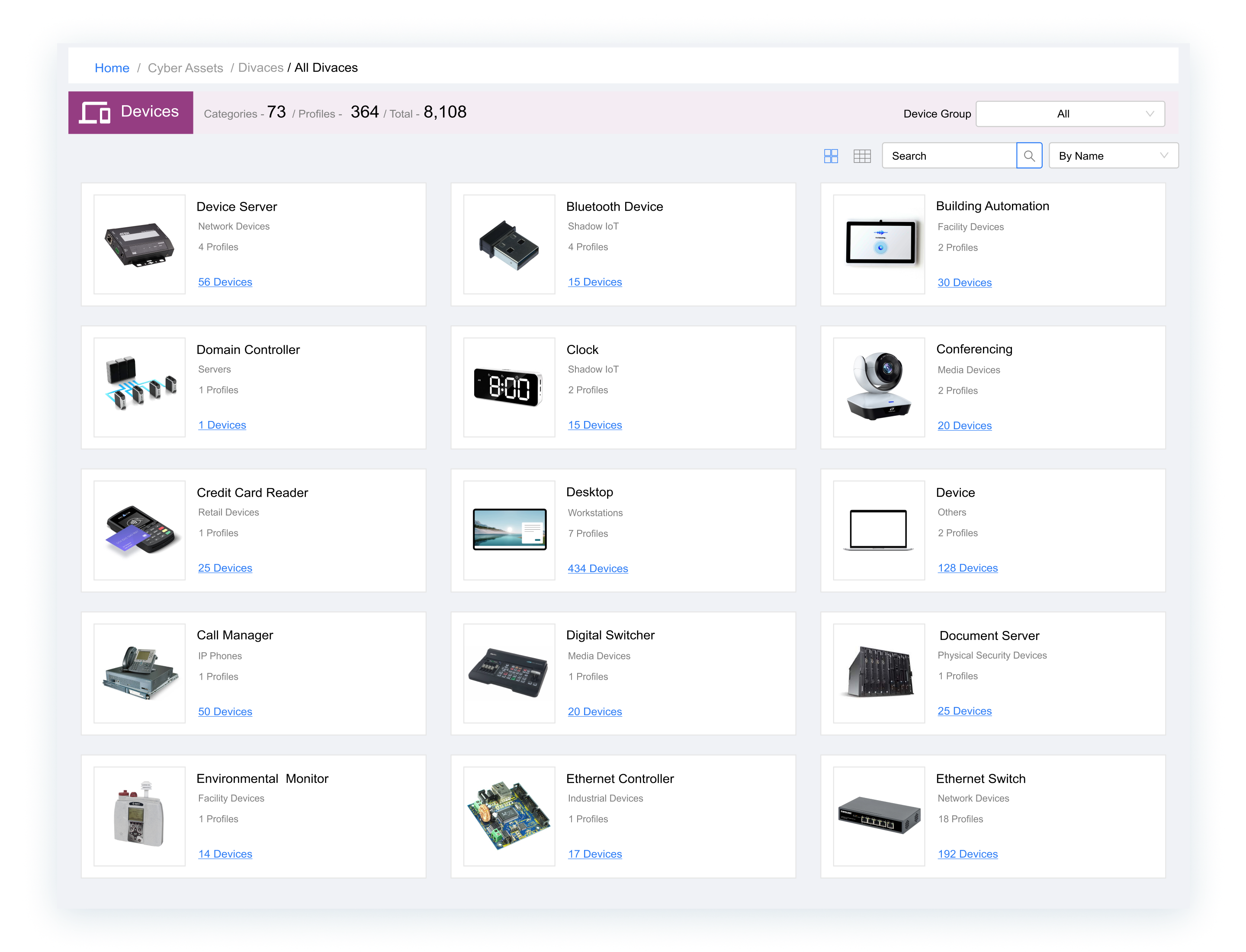
SIMPLIFY VULNERABILITY PRIORITIZATION
Vulnerability Prioritization and Management
Streamline vulnerability management with risk scores based on their organization impact, allowing for targeted, effective resolution.
- Comprehensive vulnerability management across every asset
- Automate remediation workflows with ITSM, SIEM, SOC integrations
- Assign remediation to the correct device owners
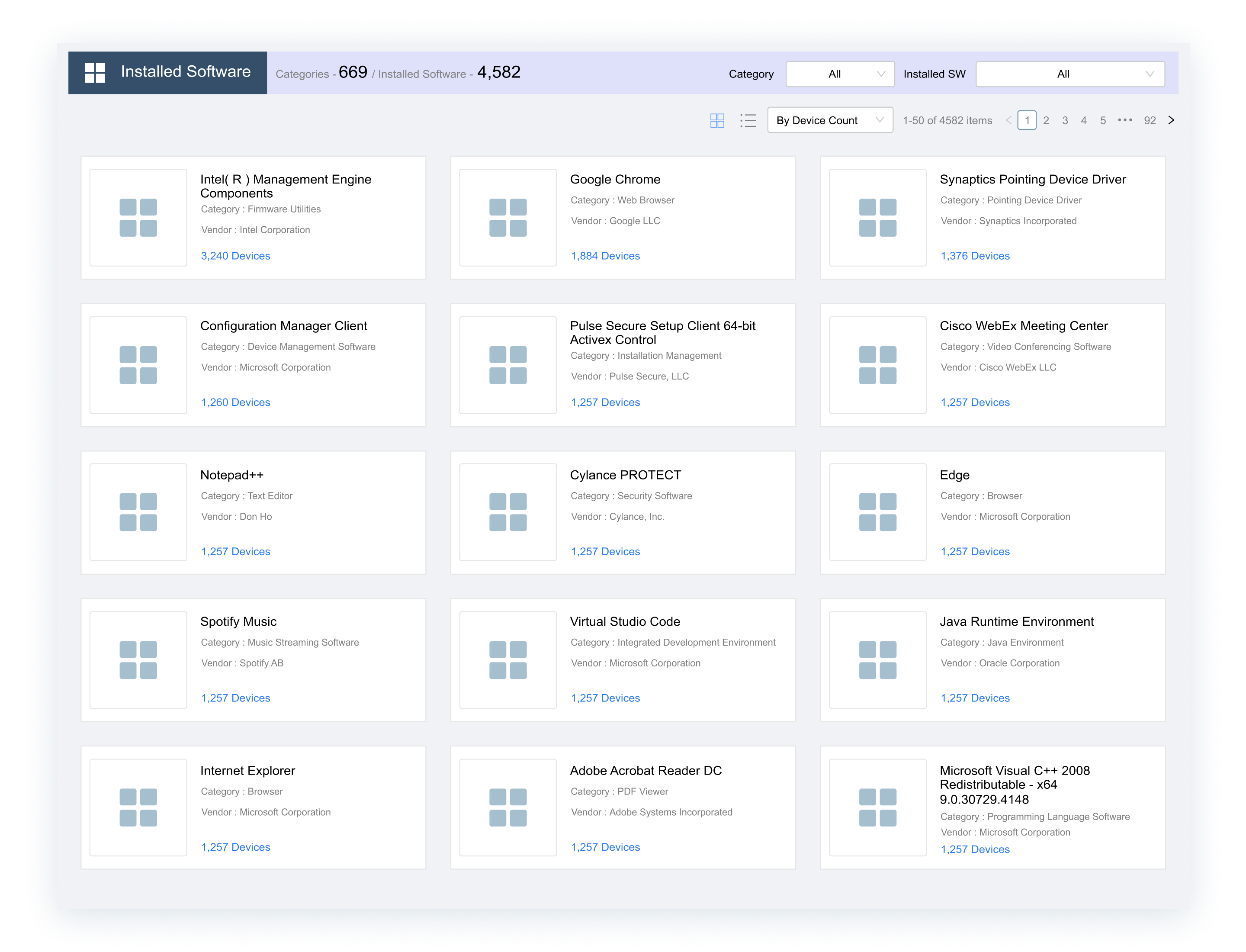
REAL-TIME VISIBILITY
SBOM Reporting
Gain insights into the software components of your assets with Ordr Software Inventory Collector. Asset insights from Ordr Software Inventory Collector informs vulnerability management prioritization and identifies impact from Zero Days.
- See details like OS patches, 3rd party software installed, anti-virus software status, disk encryption, BIOS password status
- Understand impact from Zero Days like OpenSSL, MoveIT, Log4J
- Support compliance and regulatory framework requirements
Customer Case Studies

The visibility that we now have into our networked devices and their software inventory gives us greater assurance that we are properly maintaining and securing our systems to ensure that we can continue to provide excellent service and patient care.
Stacy Estrada
Information Security Manager, Montage Health

Using Ordr’s device-centric threat and anomaly detection, Veritex Bank has also been able to detect and quickly address issues, even before being notified by our virtual SOC. This has helped the team accelerate response.
Bob Ludecke
CISO, Veritex Bank

Ordr automatically discovers all our managed and unmanaged devices and delivers critical insights through a real-time dashboard. Ordr also generates policies by type and enforces them to support microsegmentation, zero trust, and other network access controls.
Director of Information Security
Automotive Manufacturer