Challenges with IT/OT Convergence
Critical infrastructure and manufacturing organizations have evolved from airgapped networks to converged IT and OT environments.
Cyber-physical systems including operational technology (OT) and Internet of Things (IOT), connect physical processes with digital technology, and underpin critical infrastructure. The more connected they are, the more the attack surface expands and the more they need to be protected from cyberattacks.
Security teams are realizing that they need comprehensive visibility and security across their entire network and for every connected asset – IT, IOT, OT and cyber-physical systems. There are several challenges here.
- IOT, OT and cyber-physical systems aren’t always designed with security in mind, and cannot be discovered via traditional approaches
- IOT, OT and cyber-physical systems are often deployed without consultation with the security team.
- Most organizations still focus mainly on IT-security-centric risk management.
- Limited collaboration across siloed teams running systems such as IT, OT and IoT impact security
- Critical infrastructure environments — power grid, water treatment, healthcare, pipeline, transportation and logistics, telecommunications are increasingly being targeted.
“China’s hackers are positioning on American infrastructure in preparation to wreak havoc and cause real-world harm to American citizens and communities, if or when China decides the time has come to strike.”
Christopher Wray, FBI Director
What is Cyber-Physical Systems (CPS) Security?
In many organizations, production assets were initially deployed to perform specific custom tasks, and security was not central to their design. Most assets were fully “air gapped” and therefore thought to be resilient against cyberattacks. As OT systems started connecting to each other and then to IT systems, a network-centric security discipline emerged, anchored around the Purdue model.
As the complexity and variety of old and new assets have become a reality for most organizations, so has the recognition that an asset-centric approach to security is needed. Security teams now recognize that in a converged environment, they need to secure not only IT, but also IOT, OT and every other cyber-physical system that connects the cyber and physical worlds.
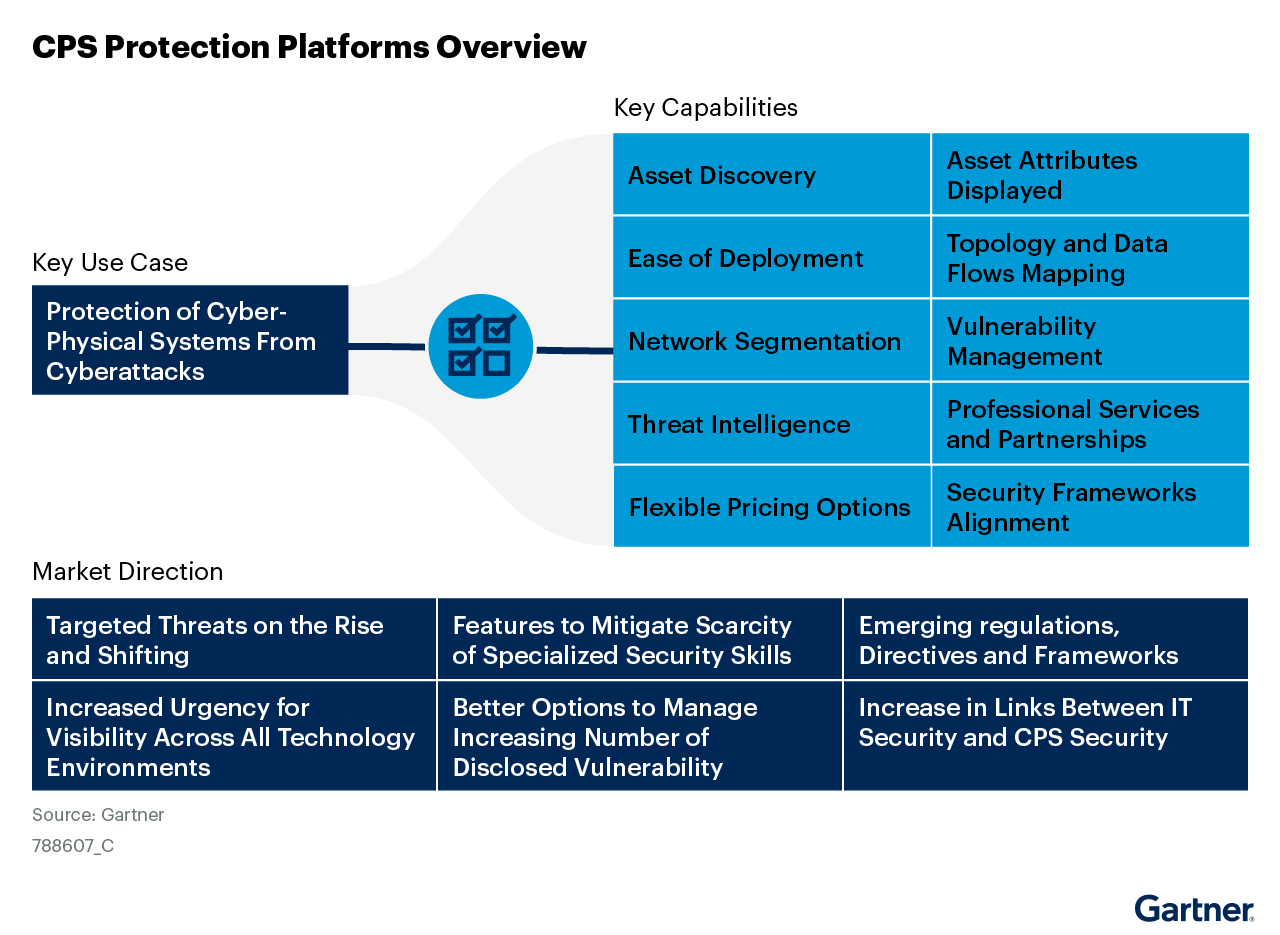
Cyber-physical systems (CPS) security ensures that every mission-critical asset — IT, IOT, OT and CPS — is secure and cyber resilient in the face of growing threats
Industry’s Most Accurate CAASM Solution
Asset Visibility (IT, IOT, OT and Cyber-Physical Systems)
Automated hardware and software asset inventory across IT, IoT, IoMT, OT
Vulnerability Prioritization and Management
Identify and prioritize vulnerabilities for the entire converged network – IT, IOT, OT, and cyber-physical systems
Connectivity and Communications Mapping
Visualize asset connections and communications with detailed mapping, providing clarity on network interactions, segmentation issues, and potential risks
Network Segmentation
Automatically generate segmentation policies to isolate parts of the network to stop lateral movement, and to secure vulnerable, mission-critical devices
Threat intelligence
Gain understanding of threats targeting your specific verticals, and better understand exposure
Security Framework Alignment
Address compliance frameworks such as NIST-CSF, CIS Controls Cyber Essentials, CMMC, NHS DSP Toolkit, and more with customized reporting and dashboards
Considerations For Securing Converged IT and OT Environments
There are many factors to consider when selecting a Cyber-Physical Systems (CPS) security product to secure converged IT and OT environments. Consider the following:
- What teams are involved in this initiative? Does it include both security and OT teams?
- Which assets in your environment are critical and need to be secured?
- Does the vendor support visibility and security for all assets including IT, IOT and OT?
- Can the vendor support prioritization of vulnerabilities based on your organizational risk?
- Can the vendor detect all types of known and unknown threats targeting assets?
- What automation is available to accelerate incident response?
- Can the vendor enable segmentation of mission-critical assets?