Average dwell time
Days
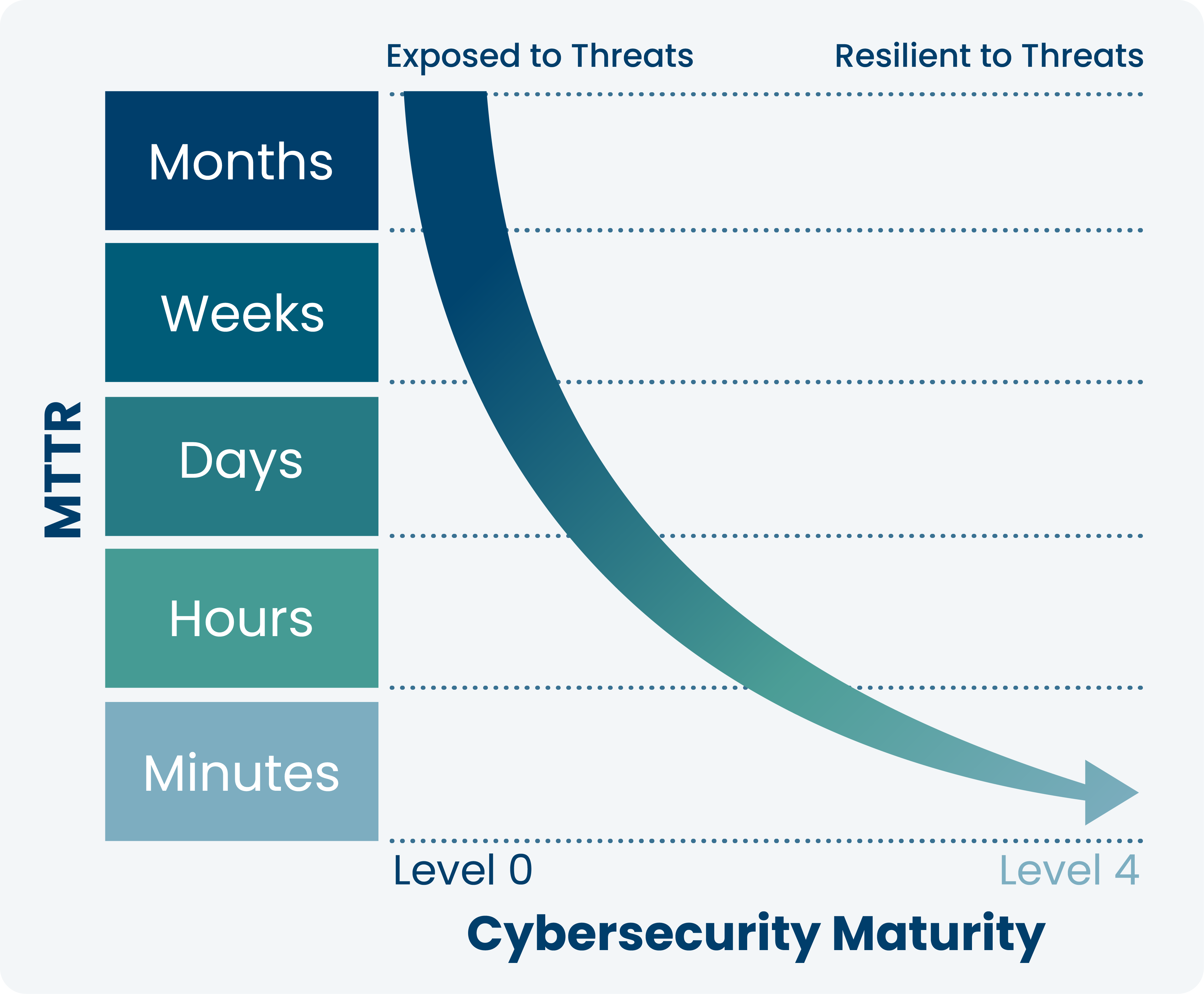
Dwell time, the time between when an attack begins and when it is detected is about 16 days
Investigation hours needed
Hours
Without accurate asset data, it takes at least a day to gather information to investigate an alert or incident
Is how often ransomware strikes
Seconds
There is a ransomware attack on a business every 11 seconds. Rapid detection and containment matters
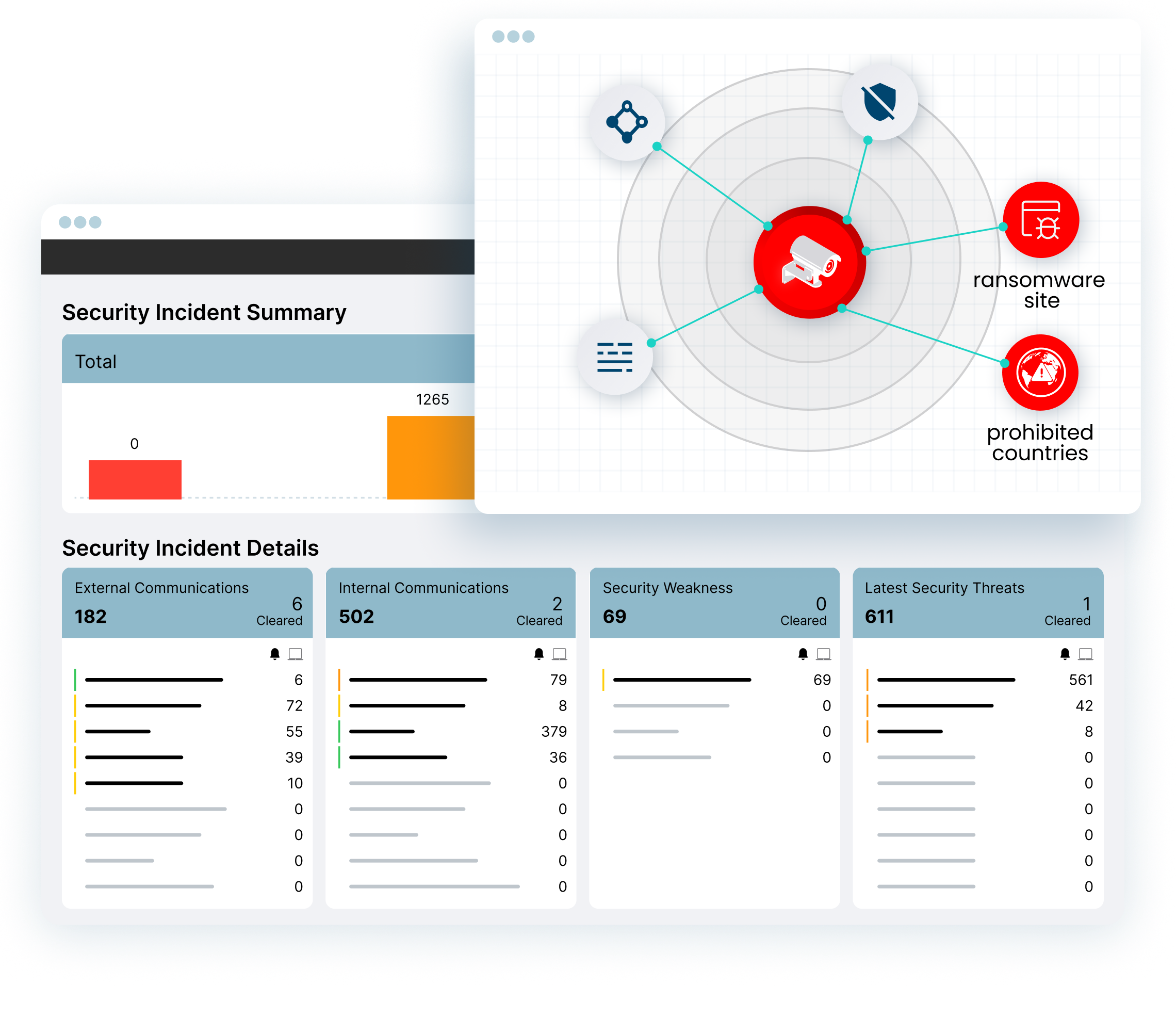
DETECT MORE THREATS
Reduce Dwell Time With Comprehensive Threat Detection
Today’s cyber criminals use a variety of attacks and techniques. Ordr reduces dwell time and mean-time-to-detect with an integrated IDS, threat intelligence, AI/ML behavioral analytics to detect threats, anomalies and risky communications
- Identify exploits, attacker tools, malware in East West traffic and external communications
- Identify assets behaving abnormally from known-good profile
- Retrospectively identify infected assets when new indicators of compromise are discovered
- Accelerate response with automated policies, enforced on existing security infrastructure.
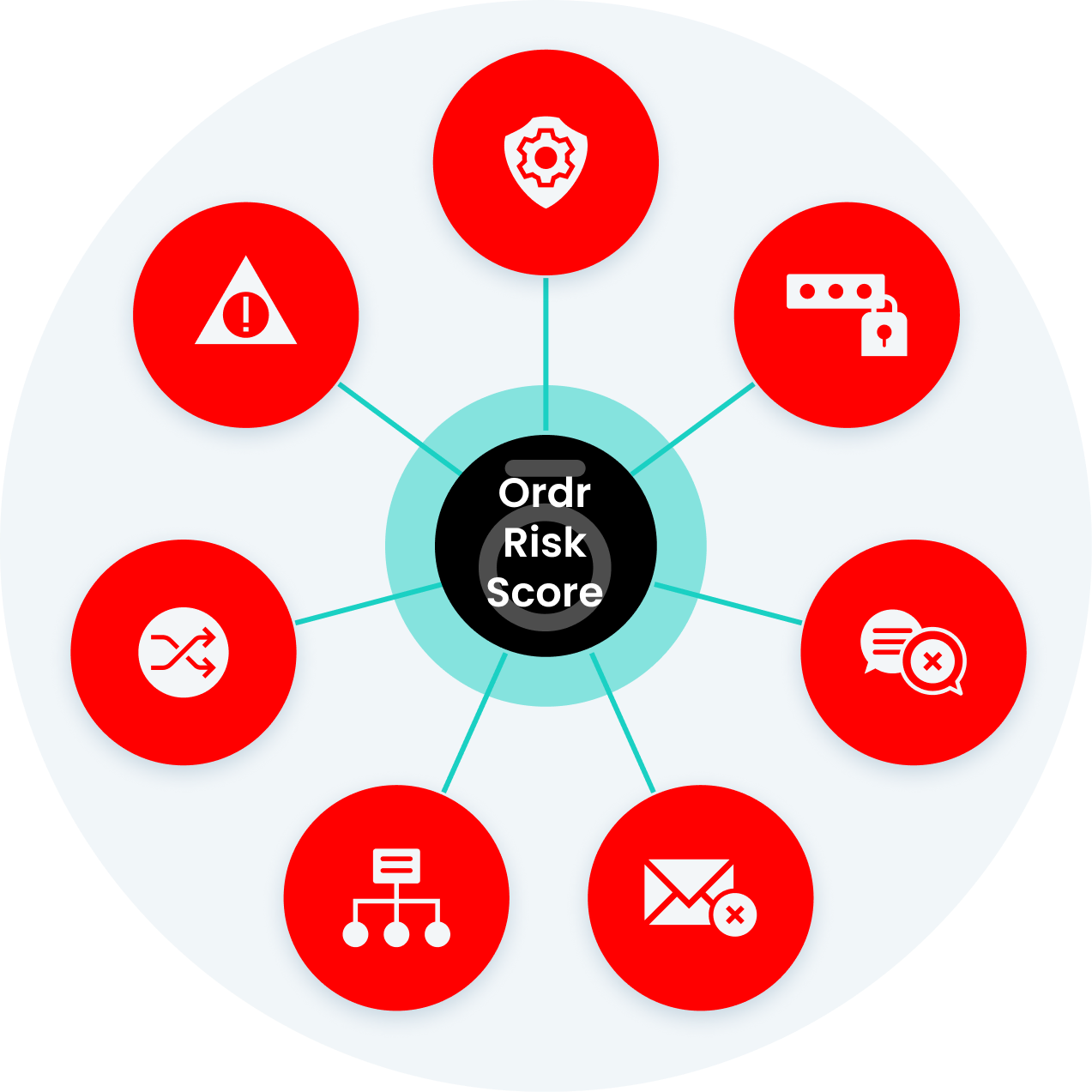
UNDERSTAND ISSUES FASTER
Reduce Investigation Time on Alerts
Security operations teams need accurate asset insights to determine exposure and response. Ordr reduces investigation time and dwell time with real-time asset insights and asset relationship mapping:
- What is this asset? Where is it connected? Who owns it?
- What application is running on this endpoint?
- Was the data encrypted at rest?
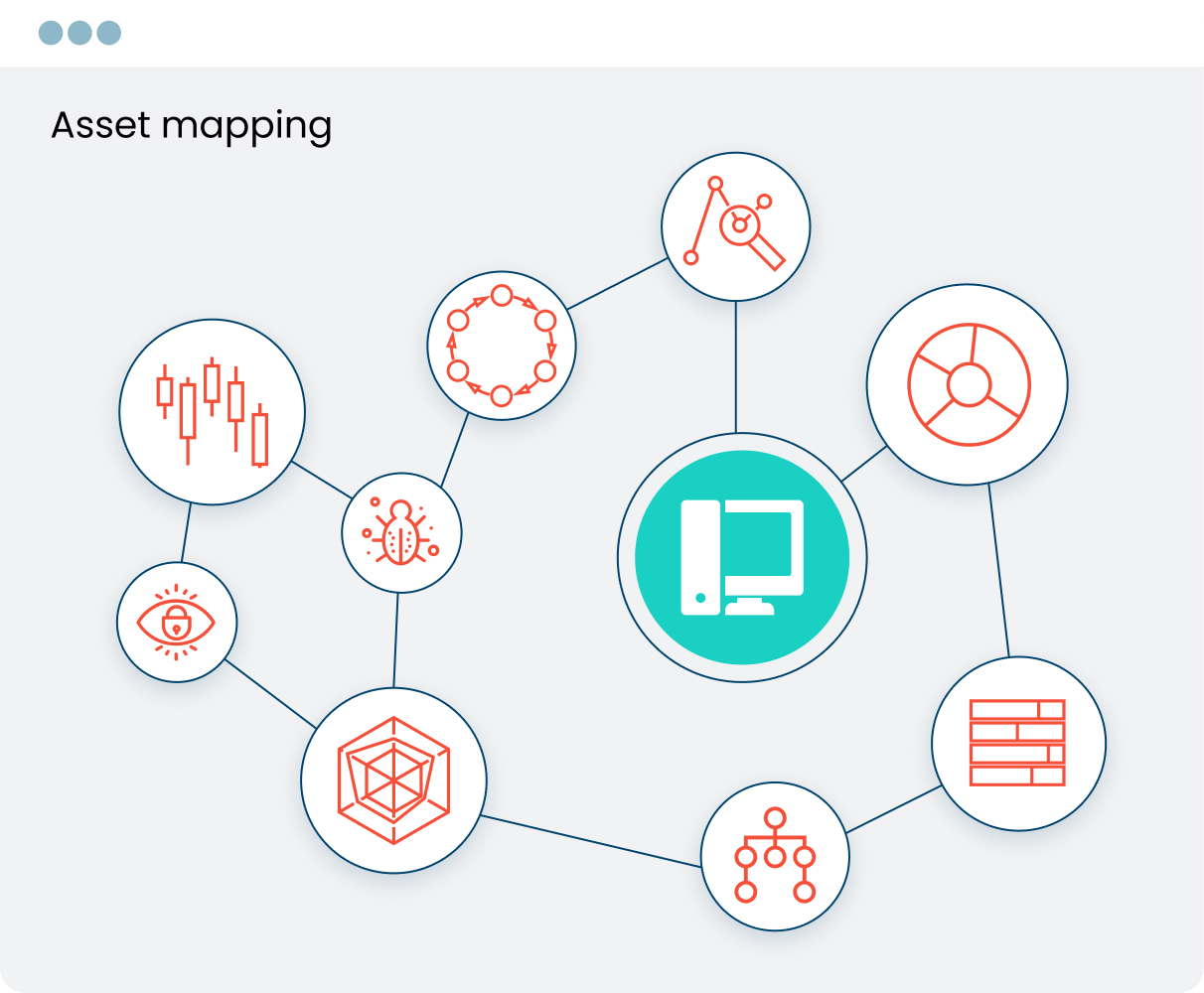
ACCELERATE RESPONSE
Automate Policies and Workflows To Contain A Threat
Once security operations teams have identified that an alert is real, they need to accelerate response. Ordr reduces mean-time-to- response by automating a variety of security policies – proactive and reactive.
- Create tasks and workflows in ITSM
- Automatically generate policies to block ports, terminate sessions or isolate a compromised asset
- Automate policies across multiple enforcement points like firewalls, switches and NAC to accelerate response
Customer Case Studies

The visibility that we now have into our networked devices and their software inventory gives us greater assurance that we are properly maintaining and securing our systems to ensure that we can continue to provide excellent service and patient care.
Stacy Estrada
Information Security Manager, Montage Health

Using Ordr’s device-centric threat and anomaly detection, Veritex Bank has also been able to detect and quickly address issues, even before being notified by our virtual SOC. This has helped the team accelerate response.
Bob Ludecke
CISO, Veritex Bank

Ordr automatically discovers all our managed and unmanaged devices and delivers critical insights through a real-time dashboard. Ordr also generates policies by type and enforces them to support microsegmentation, zero trust, and other network access controls.
Director of Information Security
Automotive Manufacturer