On September 1st, Jaguar Land Rover’s global production came to a halt. Assembly lines froze. Supply chains rippled. Losses soared past $1.5 billion as factories remained offline for weeks.
But what truly alarmed security teams around the world wasn’t the scale of the damage; it was the precision of the attack. This wasn’t a smash-and-grab. It was a patient, surgical operation that unfolded over months.
Let’s walk through how the breach evolved and how ORDR could have stopped it at every stage.
Phase 1: Initial Compromise — The Laptop That Opened the Door
What Happened
The attack began with a single click. A phishing email led an employee to install infostealer malware that harvested Jira credentials. Suddenly, a trusted laptop inside the network was under attacker control.
From there, they:
- Installed remote access tools and credential stealers
- Disabled endpoint protection and MDM controls
- Tampered with firewall configurations
All of it happened on what was supposed to be a “managed” device
The Billion-Dollar Blind Spot
If you can’t see every connected device—contractor laptops, IoT sensors, legacy PLCs—you’re operating in the dark. Most manufacturing networks contain thousands of endpoints, many of which are invisible to security tools.
How ORDR Stops It
ORDR automatically discovers and profiles every device the moment it connects—no agents required. It knows who’s using it, what it’s running, and whether it’s behaving normally. Integrations with CMDB, Active Directory, and procurement systems validate asset legitimacy and highlight devices missing EDR, outdated via MDM, or misconfigured.
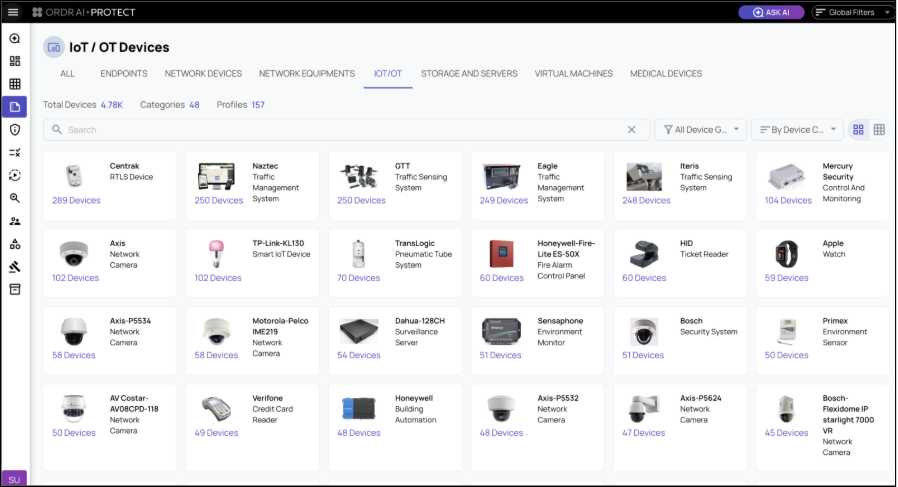
When that compromised laptop started behaving abnormally—talking to systems it never had before—ORDR would have detected it instantly and isolated the threat before it spread.
Phase 2: Reconnaissance — The Quiet Mapping of Your Network
What Happened
Once inside, the attackers didn’t rush. They mapped the network, cataloged devices, and identified high-value systems:
- Manufacturing control systems
- Engineering workstations
- Legacy equipment with known vulnerabilities
- Pathways between IT and OT
The Hidden Risk
Legacy devices (unpatchable, agentless, and critical to production) are perfect reconnaissance targets. Many environments still rely on systems from 2008 and older, which traditional security tools can’t see.
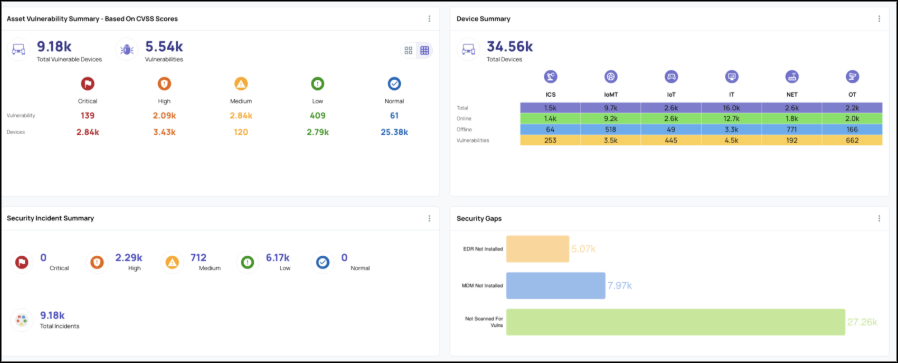
How ORDR Stops It
ORDR combines passive and active discovery with integrations to tools like Rapid7, Tenable, and Qualys to build a risk-prioritized map of every connected asset.
It identifies
- Legacy devices with linked CVEs
- High-risk assets exposed to the internet
- Devices from prohibited manufacturers (Huawei, ZTE, Dahua, Hikvision) for Section 889 compliance
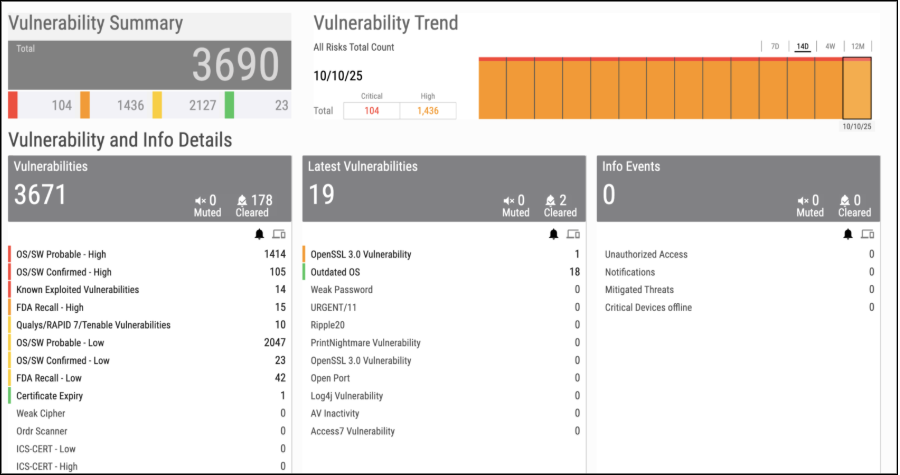
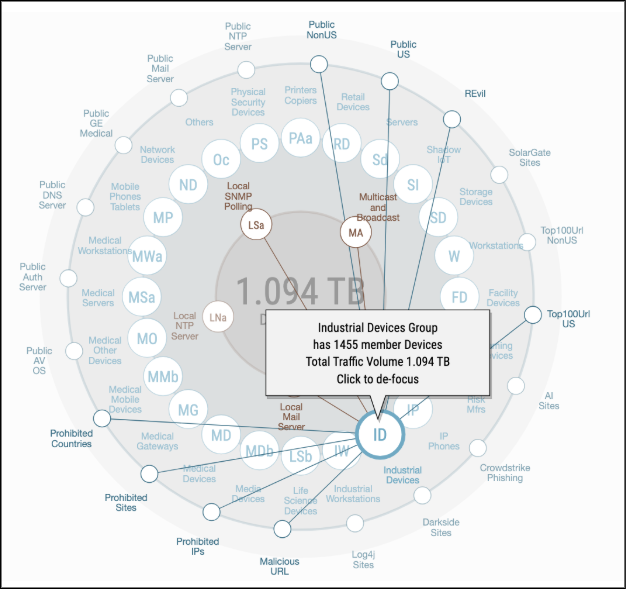
Example: That 15-year-old PLC controlling your assembly line? knows it’s there, knows it has 23 critical CVEs, knows it’s talking to the internet, and automatically helps you create a remediation ticket.

ORDR’s Asset Graph shows each device’s blast radius—revealing what else would be at risk if it were compromised.
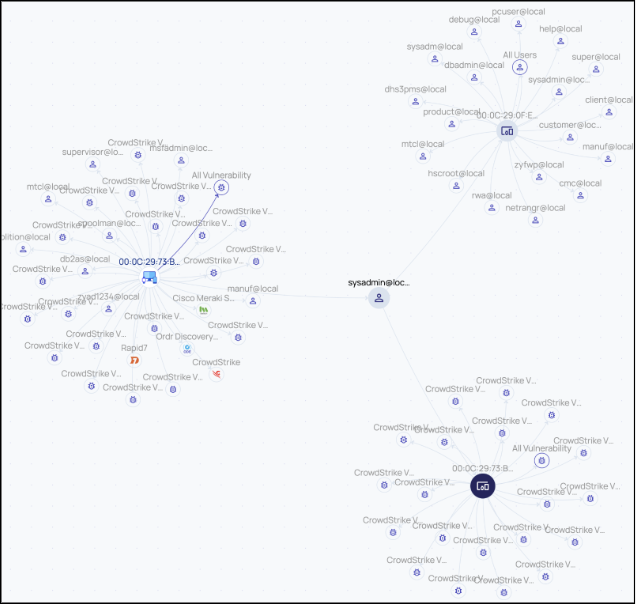
Key Takeaway: ORDR helps you see what attackers see, but sooner, deeper, and with context that drives immediate action.
Phase 3: Lateral Movement — When the Attack Spreads Sideways
What Happened
With credentials and a network map, the attackers moved laterally, quietly hopping between:
- Engineering workstations
- Manufacturing execution systems
- Production control networks
- File servers with proprietary data
Poor segmentation lets them move freely between IT and OT, turning one compromised device into a full-scale outage.
The Overlooked Danger
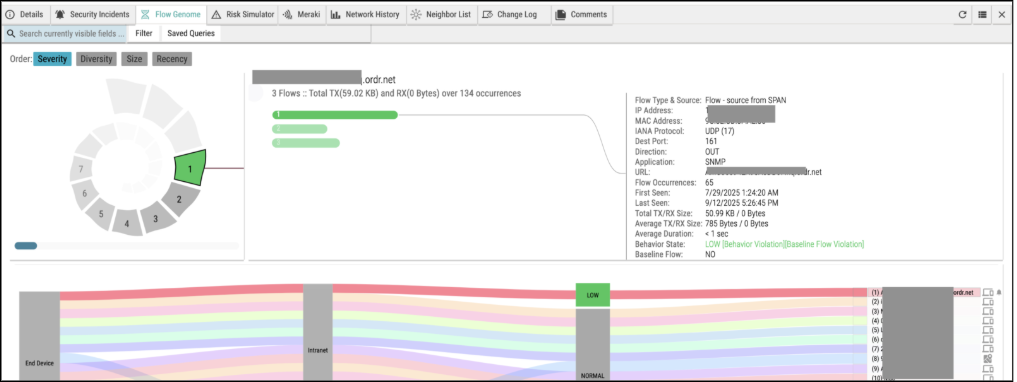
Most tools monitor north-south traffic (in and out). But east-west traffic (device-to-device communication) is where attackers thrive. When a laptop suddenly talks to an industrial controller, that’s not business as usual.
How ORDR Stops It
ORDR continuously learns what “normal” looks like for every device, its connections, timing, and traffic patterns. When attackers begin lateral movement, ORDR detects:
- Unusual internal communications
- Unauthorized access to restricted VLANs
- IT devices crossing into OT zones
- Violations of expected communication baselines
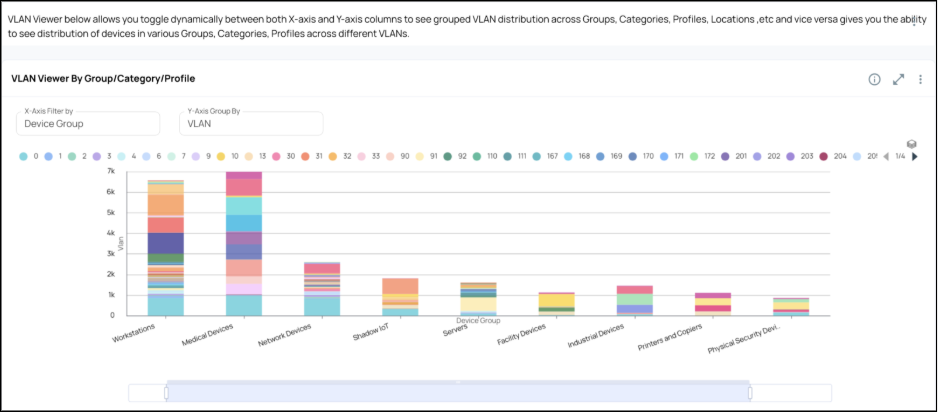
ORDR doesn’t just alert; it acts. Integrations with switches, firewalls, and NAC systems allow automated containment: quarantining devices, reassigning VLANs, or shutting down ports in seconds.
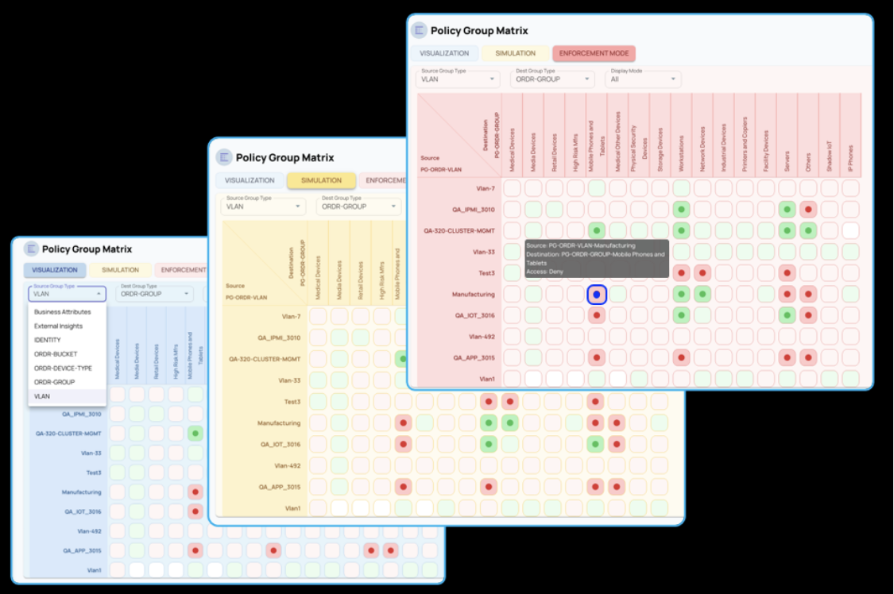
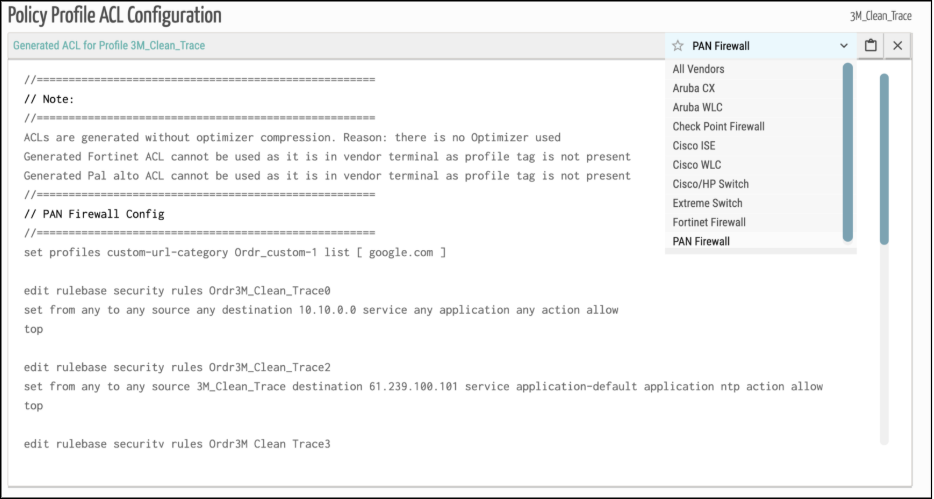
Key Takeaway: ORDR eliminates blind spots between IT and OT, turning east-west traffic into an early warning system that can respond automatically.
Phase 4: Exfiltration — The Data That Walked Out the Door
What Happened
The attackers stole over 700 internal documents, source code, and employee data, roughly 350 GB of sensitive information, without triggering alarms. They:
- Encrypted transfers
- Used legitimate cloud services
- Trickle-exfiltrated data to stay below thresholds
- Made it all look like ordinary business traffic
The Problem You Face:
95% of modern attacks involve data exfiltration, and attackers increasingly focus on silent data theft rather than noisy ransomware. When exfiltration hides within normal traffic patterns, traditional DLP and perimeter defenses can’t see it. The danger isn’t just losing data—it’s not knowing what left or when.
How ORDR Stops It
ORDR uses behavioral analytics and continuous traffic monitoring to expose stealthy exfiltration:
- Detects new destinations, suspicious IPs, and unfamiliar protocols
- Flags traffic to prohibited geographies
- Identifies deviations from normal outbound patterns
- Integrates with DLP and SIEM to prioritize true incidents
- Can automatically block or isolate devices attempting data theft
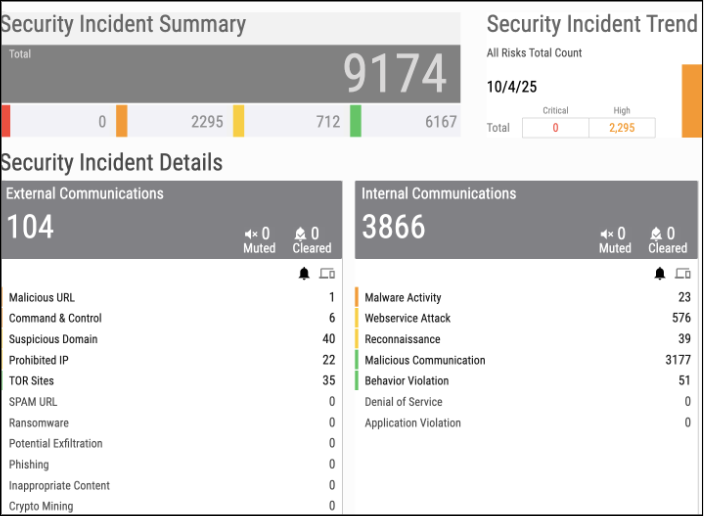
When a manufacturing controller that’s never sent data abroad suddenly starts communicating with a foreign server, ORDR detects the anomaly and stops it before any data leaves your network.
Back to Basics: Strengthen Your Controls
The attackers didn’t use some magical exploits. They used compromised credentials, moved laterally through a flat network, and exfiltrated data through encrypted channels. In other words, they exploited gaps in visibility and control that exist in most manufacturing networks.
100% Asset Visibility, zero blind spots, and Seconds to contain a threat
- Know What You Have — You can’t protect what you can’t see. Complete device visibility isn’t optional anymore.
- Know What’s Broken — Risk and Vulnerability management that prioritizes based on risk, not just CVSS scores.
- Know When Things Get Weird — Behavioral analytics that understand device-to-device communication patterns.
- Know How to Contain It Fast — Network response capabilities that quarantine threats in seconds, not hours.
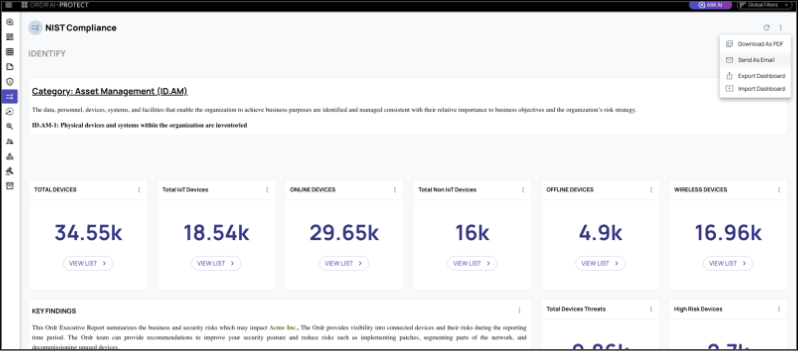
- Know It’s Working — Schedulable dashboards and compliance reporting (NIST, CIS 20, etc.) with advanced AI search capabilities that prove your controls are present and functioning.
The Bigger Picture: Lessons From a Modern Breach
This attack didn’t rely on exotic zero days. It exploited the same weaknesses most organizations struggle with every day:
- Incomplete device visibility
- Flat, unsegmented networks
- Unmonitored east-west traffic
- Legacy systems that can’t be patched
- Data moving undetected through trusted channels
Every one of these weaknesses is preventable with continuous visibility and automated response.
The ORDR Advantage: Visibility, Control, and Speed
ORDR delivers:
- 100% Device Visibility: Every connected asset, IT, IoT, BMS, and IoMT. identified and classified instantly.
- Real-Time Risk Insights: Vulnerabilities prioritized by exposure and business impact.
- Behavioral Intelligence: Detection of abnormal communication patterns that signal compromise.
- Automated Containment: Integrated response that isolates threats in seconds, not hours.
- Proven Compliance: Simplified reporting for NIST, CIS 20, and Section 889 with AI-powered dashboards.
The Bottom Line
This wasn’t an isolated incident. It’s a preview of how modern cyber operations work. Attackers exploit the unseen, move quietly, and aim to disrupt production before you even know they’re inside.
ORDR gives you the power to see everything connected to your network, understand how it behaves, and act the moment something goes wrong.
Because the real question isn’t “Can you prevent every attack?”
It’s “How fast can you see it—and stop it—before it stops you?”
Ready to see what’s actually happening in your network?
Learn more in our Rise of the Machines Report, or request a demo to see ORDR in action.

Interested in
Learning More?
Subscribe today to stay informed and get
regular updates from ORDR Cloud


