Studies show that close to 50% of ransomware attacks result from unpatched vulnerabilities, including weaknesses in an organization’s information systems, system processes, or internal controls. Prioritizing vulnerabilities presents a significant challenge for enterprises as security teams often must sift through thousands of vulnerabilities, each presenting different dangers to the organization based on the associated asset risk. Yet this must be done because unaddressed vulnerabilities increase the likelihood of a breach or cybersecurity incident.
To effectively manage vulnerability risks, enterprises must therefore develop a strategy that prioritizes vulnerabilities based on its specific risk and impact to their business. In general, assets can be categorized into three broad categories:
- Assets with known vulnerabilities that can be patched once a patch is available.
- Assets with known vulnerabilities that may have a recommended patch, but validation by the manufacturer is necessary before patching.
- Assets with an outdated operating system (OS) that typically cannot be patched. (In such cases, security teams must find alternate methods to prevent the exploitation of these vulnerabilities.)
To help organizations simplify and tackle the task of risk prioritization and vulnerability management, ORDR’s Cyber Asset Attack Surface Management (CAASM) product offers enterprises end-to-end vulnerability management, enabling their security teams to identify, investigate, and prioritize vulnerabilities efficiently. Below we will share how ORDR enables enterprise security teams to reduce alert fatigue and get a prioritized list of top risks.
Automatically Discover and Assign Vulnerabilities to All Assets
ORDR uses multiple methods to collect and de-duplicate vulnerability data from multiple sources, offering a streamlined approach to managing vulnerabilities on a single platform. Utilizing the following methods ensures security teams can discover and understand the full vulnerability landscape across all assets, including IT, IoT, IoMT, and OT.
1. For regularly scanned assets, integrations with vulnerability assessment systems, such as Rapid7, Tenable, and Qualys, collect vulnerability data. ORDR then deduplicates this data to ensure teams have an accurate list of vulnerabilities.

2. For assets that cannot be scanned or are not updated regularly, ORDR’s lightweight script, Software Inventory Collector, detects vulnerabilities based on KB/HF correlation instead of scanning the asset. This approach ensures comprehensive vulnerability coverage is collected for assets that cannot undergo traditional scanning.
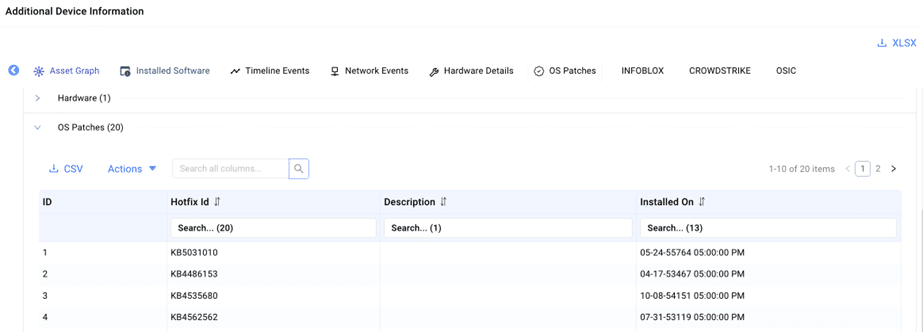
3. For assets with outdated operating systems, ORDR uses both passive and active scanning techniques to collect detailed asset context, including make, model, manufacturer, and OS. This data is then used to accurately assign vulnerabilities to these assets.
Enhancing Vulnerability Data & Context for Risk-Based Prioritization
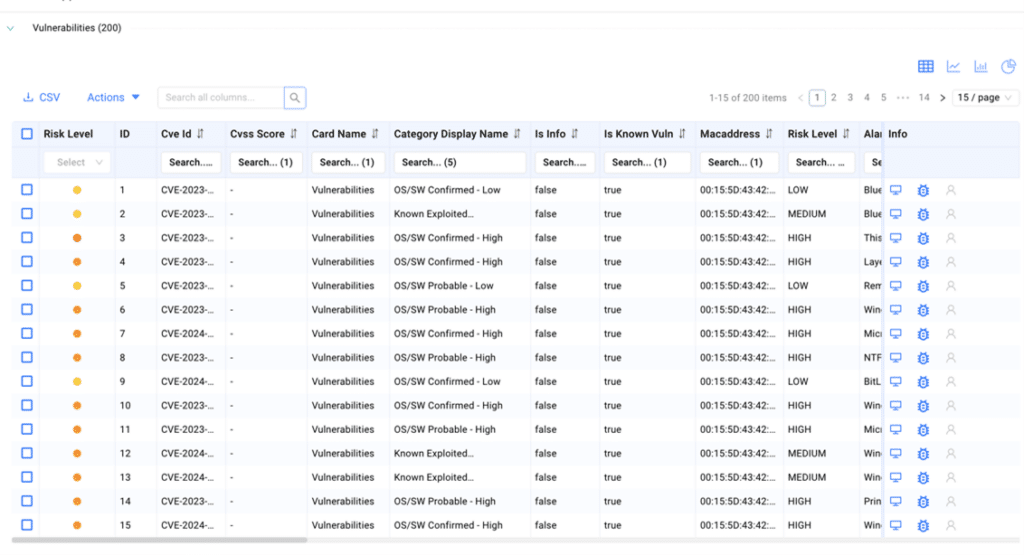
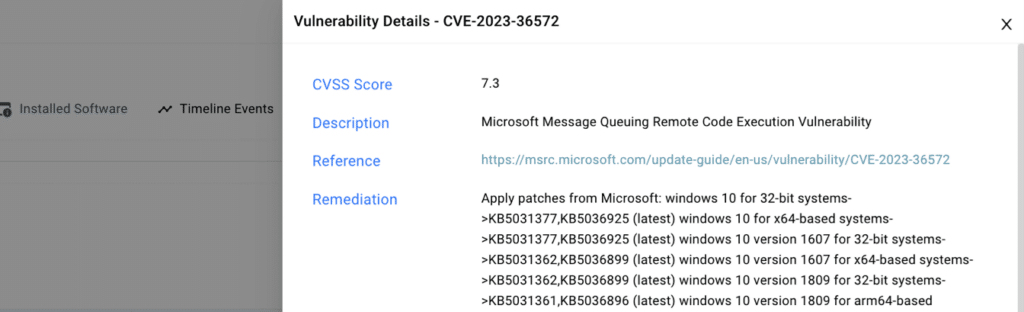
After identifying all assets with vulnerabilities, ORDR enriches the data by providing additional business context for each asset. This empowers security teams to prioritize vulnerabilities based on the criticality of assets to the business, enabling them to focus on addressing the most significant risks. ORDR’s Asset Risk Score considers multiple factors such as asset context, CVSS scores, vulnerability exploitability, type of data (encrypted), location, and more. To obtain detailed asset data and business context, ORDR utilizes:
- AI/ML technology to classify assets and assign business context. Customers can also add additional context to customize the risk score to further align with their specific business needs.
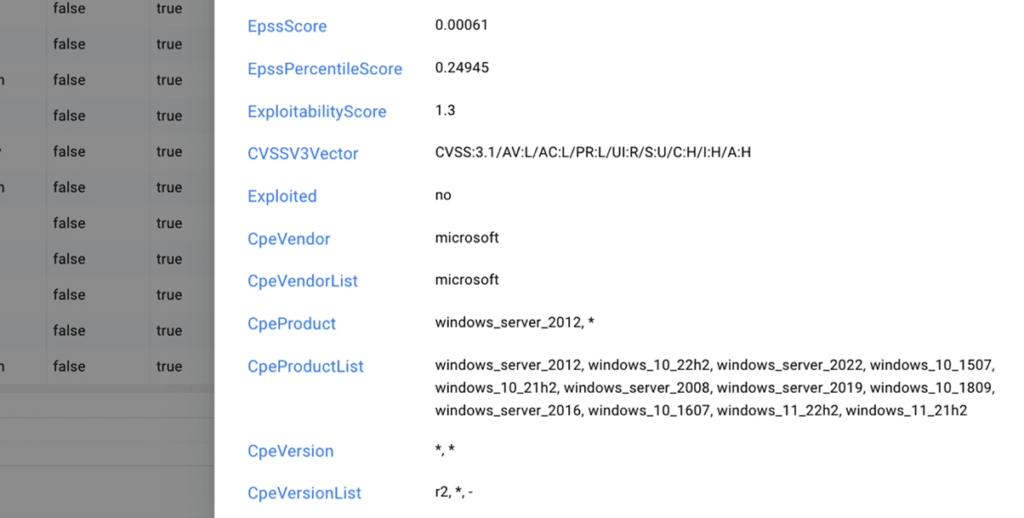
- Known Exploited Vulnerabilities (KEV) and Exploit Prediction Scoring System (EPSS) data to gain additional visibility into vulnerabilities posing the greatest risk.
After gathering asset context utilizing AI/ML technology, the data is standardized into a score, prioritizing assets based on numerical risk. Each asset is assigned a risk-based score ranging from Level 1 to Level 5, with mission-critical assets designated as Level 5.
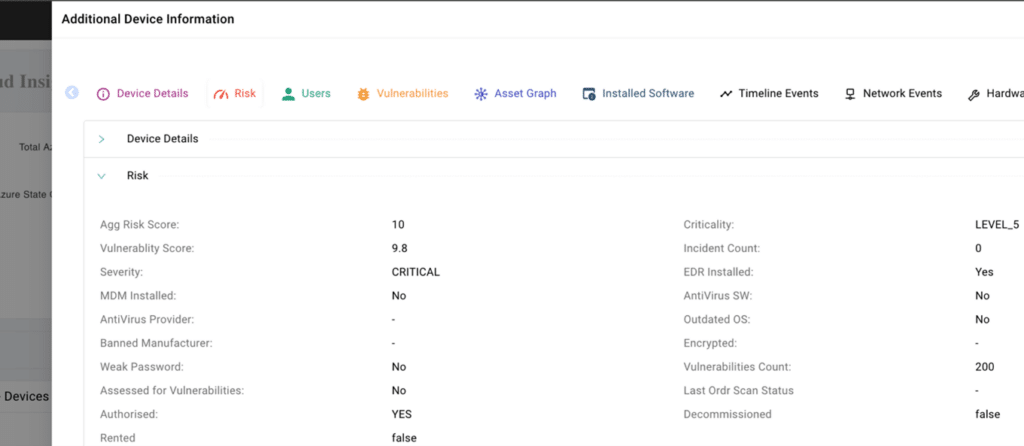
Streamlining End-to-End Vulnerability Management
ORDR streamlines end-to-end risk and vulnerability management to cover everything from associating vulnerabilities with assets, to assigning remediation tasks to the appropriate asset owner and monitoring vulnerability status. ORDR’s comprehensive approach includes:
- Building integrations with vulnerability management tools, such as the ServiceNow VR module and others, to deliver real-time status updates based on reconciled data.
- Providing the capability to mute a vulnerability, allowing teams to temporarily hide the vulnerability from dashboards while still tracking the vulnerability until a patch is available.
- Enabling teams to assign vulnerability remediation tasks to individual users, complete with priority and due date specifications.
- Providing visualization of trending analysis based on newly discovered, open, and closed vulnerabilities.
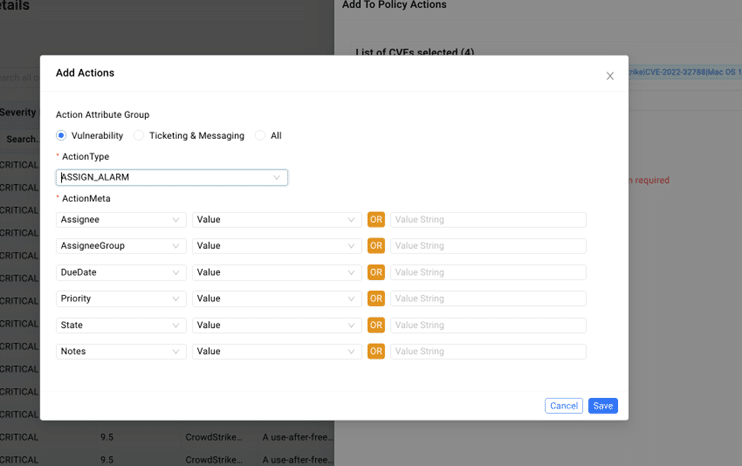
Intuitive Vulnerability Data Search
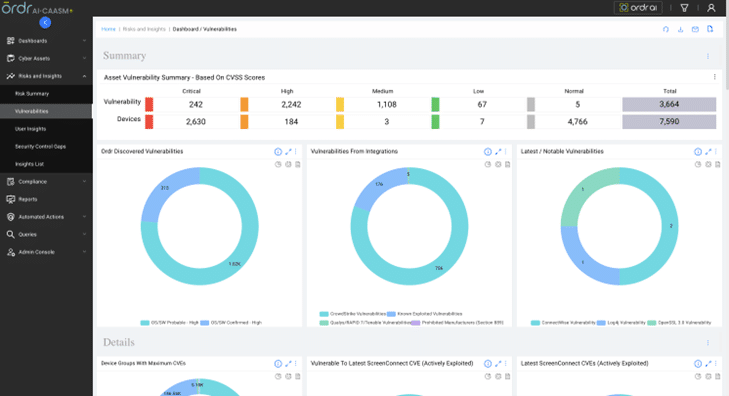
ORDR’s AI/ML mapping and correlation engine, along with the Software Inventory Collector, align technical and business priorities, mitigating alert fatigue and delivering a prioritized list of top risks. With features like the Vulnerability Dashboard for comprehensive insights, Query Builder for customized dashboards, and Ask ORDRAI for instant vulnerability information, CAASM+ simplifies risk and vulnerability management on a single platform.
Vulnerability Dashboard provides a complete “state of the union” on vulnerabilities.
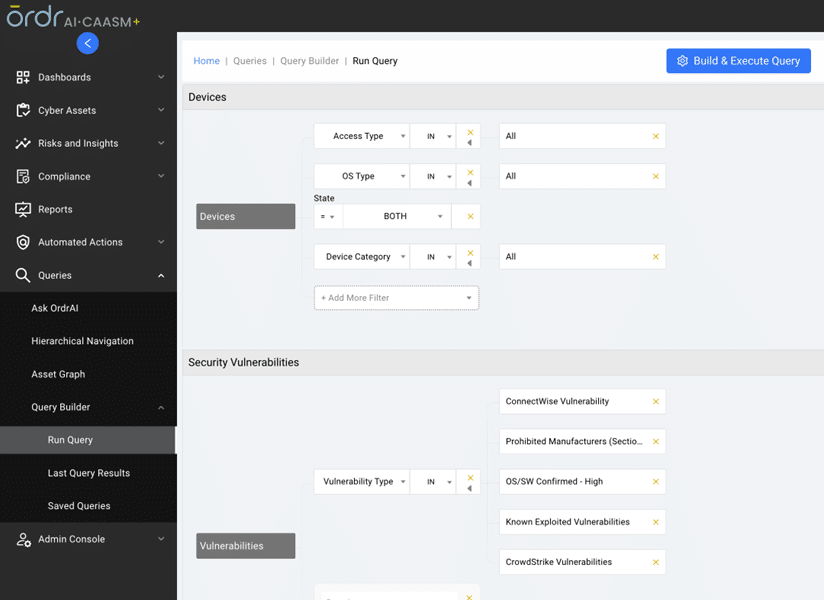
Query Builder for creating a custom dashboard based on the customer’s needs.
Ask ORDRAI gives security teams a natural language search option to get information on vulnerabilities, eliminating the need for technical expertise or coding.

ORDR integrates with industry-leading security solutions to share data and insights when assets have vulnerabilities or remediation is needed. Recommended data sources for ORDR to integrate with for end-to-end vulnerability management include:
- EDR
- MDM
- CMDB
- Cloud Assets
- Vulnerability Assessment Systems
- ORDR Discovery Engine
ORDR provides a framework for remediation with multiple enforcement options. These enforcement actions include:
- Network based enforcement (changed VLAN, shutdown port, integrate with firewall)
- Integrations with ticketing systems
- Integrations with messaging/collaboration tools
- Integration with vulnerability management tools
Watch the video to see how CAASM+ empowers security teams to efficiently identify, investigate, and prioritize vulnerabilities.
Learn more about ORDR’s risk-based vulnerability prioritization and management and connect with one of our experts for a personalized demo.
Thanks for joining us for another blog in our series on CAASM+ use cases. Stay tuned as we explore more of these critical use cases in the coming weeks and discuss how ORDR addresses them.

Interested in
Learning More?
Subscribe today to stay informed and get
regular updates from ORDR Cloud



