Background
ConnectWise ScreenConnect software is a comprehensive remote desktop access software solution that enables secure, flexible, and efficient technical support for its customers. Part of ConnectWise’s suite of IT service delivery and support products, ScreenConnect is commonly used by managed service providers (MSPs) to gain remote access to customer endpoints for services such as IT support.
ConnectWise recently announced it discovered that flaws in ScreenConnect were being actively exploited and issued a security advisory. The ConnectWise advisory reported that all versions of ScreenConnect prior to 23.9.8 contained two vulnerabilities.
Vulnerability Details
| CVE-2024-1709 | CVE-2024-1708 | |
| Severity | Critical CVSS: 10 | High CVSS: 8.4 |
| Products affected | ConnectWise ScreenConnect Software. | ConnectWise ScreenConnect Software. |
| Versions affected | Up to (excluding) 23.9.8 | Up to (excluding) 23.9.8 |
| Details | Authentication bypass using an alternate path or channel to gain unauthorized access to confidential information or critical systems. | Improper limitation of a pathname to a restricted directory (“path traversal”) via a Zip Slip attack. |
| Exploitability Score | 3.9 | 1.7 |
| Vector | CVSS:3.1/AV:N/AC:L/PR:N/UI:N/S:C/C:H/I:H/A:H | CVSS:3.1/AV:N/AC:L/PR:H/UI:R/S:C/C:H/I:H/A:H |
| Impact Score | 6.0 | 6.0 |
| NVD Published Date | 02/21/2024 | 02/21/2024 |
| NVD Last Modified | 02/22/2024 | 02/22/2024 |
| Reference | CVE-2024-1709 Detail | CVE-2024-1708 Detail |
Have these vulnerabilities been exploited?
Yes. CVE-2024-1708 and CVE-2024-1709 have been exploited and, due to that evidence, have been added to the Known Exploited Vulnerabilities Catalog by CISA. Trend Micro says that multiple cybercrime groups, including the Black Basta and B100dy ransomware groups, have started exploiting the flaws.
CISA has directed that all federal civilian Executive Branch agencies must address vulnerabilities identified in this catalog by a specified due date, which for CVE-2024-1709 is Feb 29, 2024.
For detailed information and updates on CVE-2024-1709 and CVE-2024-1708, refer to the official CVE database and the advisories provided by ConnectWise and CISA.
How to use ORDR to detect and respond to this threat
- ORDR updated its vulnerability database for all customer instances with these latest ConnectWise ScreenConnect CVEs for early identification and patching.
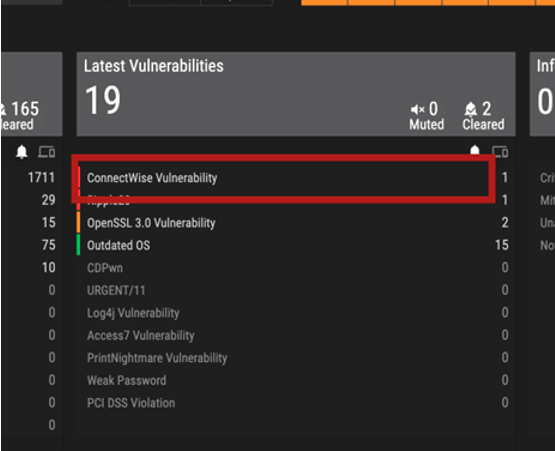
- ORDR added a new alert type in the “Latest Vulnerabilities” threat card as an easy visual indicator. ORDR analyzes the total software installed on all devices, checks for this specific version and matches with this vulnerability after a quick lookup of affected devices.
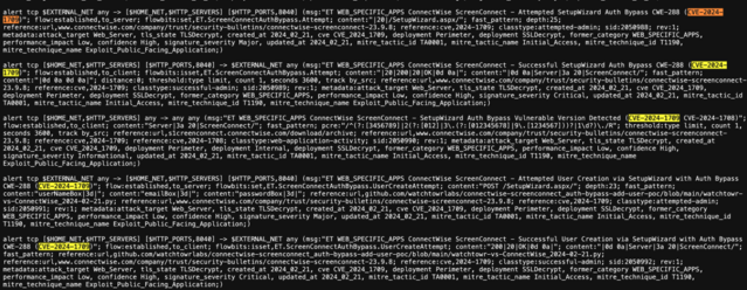
- ORDR updated its IDS rules corresponding to the exploitation of these vulnerabilities for real-time detection. As a result of this update, ORDR’s IDS engine will automatically look for relevant signatures and add a visual indication in the ORDR security page incident card if there is a match with the signature on the packet stream.
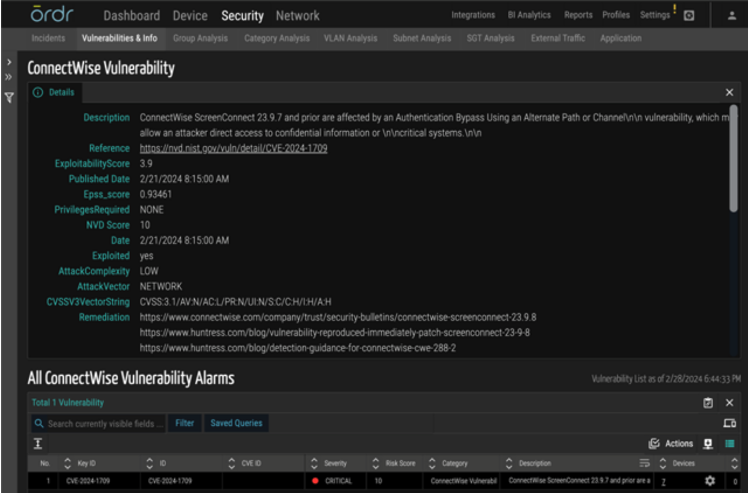
ORDR detection details and CVE lookup
The following are ways to identify if your organization has been exposed to these vulnerabilities and how to mitigate them.
Vulnerability mapping of impacted devices:
- ORDR provides visibility into all the devices running ConnectWise applications by mapping applications collected via ORDR Software Inventory Collector or 3rd party integrations like EDR, MDM, MSFT-AD, and others.
- ORDR also maintains a list of all the software packages installed on the endpoints with exact version numbers and a time stamp on which it was installed and last updated.
- ORDR matches the software version number against the various vulnerability databases to identify vulnerable versions of ConnectWise ScreenConnect applications.

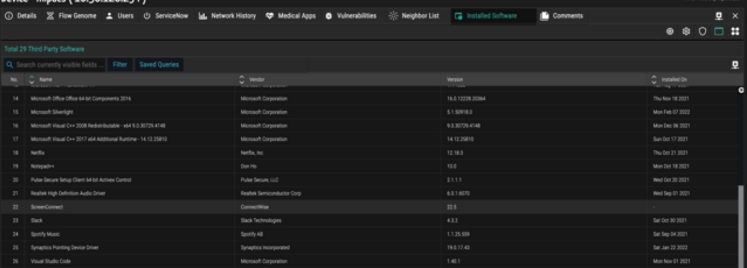
This information can be looked up easily in the following ways:
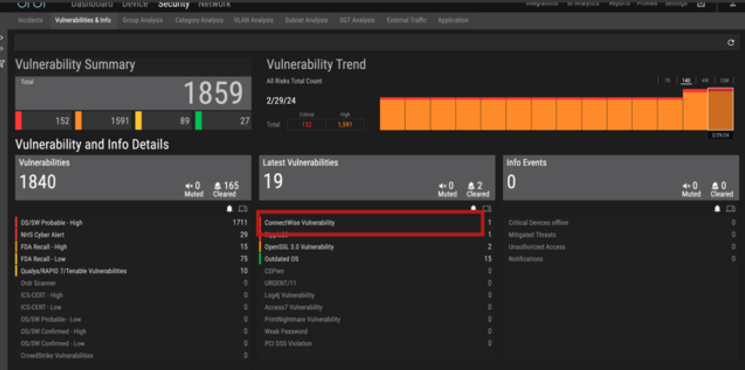
- Latest Vulnerabilities Card: All devices running a vulnerable version of the software are highlighted in the ORDR Vulnerabilities and Info page in the Latest Vulnerabilities card.
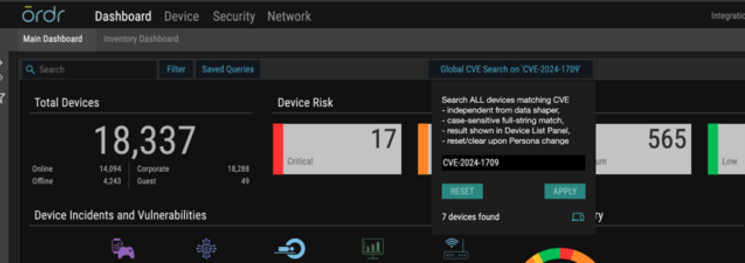
- Global CVE Search: For easy lookup in just a click, customers can search for the CVE ID corresponding to ScreenConnect vulnerabilities directly from the global CVE search in the ORDR main dashboard page.
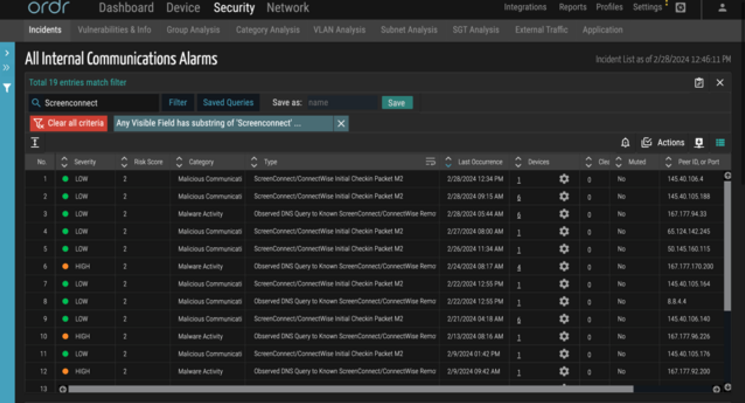
Real-time detection of exploits using IDS, behavioral violation, and threat correlation:
The ORDR IDS engine detects this specific vulnerability using analysis of packets transacting over the wire. ORDR IDS signatures have been updated to detect ConnectWise ScreenConnect software exploitations.
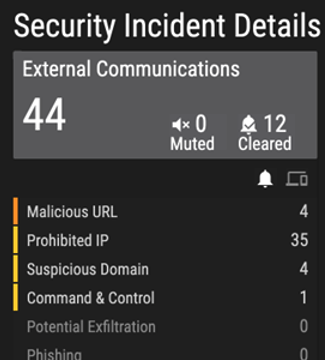
Generate alerts based on communication malicious IPs/URLs: ORDR’s external IP/IOC tracks every communication to prohibited IP/URLs in real-time. ORDR uses a continuously updated, cloud-based threat intelligence platform and all malicious communications alerts are marked accordingly in the ORDR Security Threat Card.
Mitigation actions to perform if detected:
To mitigate the risks associated with CVE-2024-1708 and CVE-2024-1709, several strategies are recommended:
- Update ConnectWise ScreenConnect software: Ensure that you are using the latest version of ConnectWise ScreenConnect above version 23.9.8. Updates often include patches for known vulnerabilities, which can prevent exploitation.
- Reactive rapid threat containment: ORDR has the capability to rapidly isolate the affected devices if it is deemed to have this vulnerability by putting the device in a quarantine VLAN, or denying its connection to the network using automation with a single click. This automation works with almost any networking, switch, or wireless controller vendor.
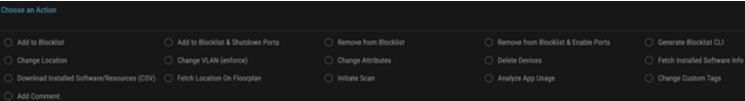
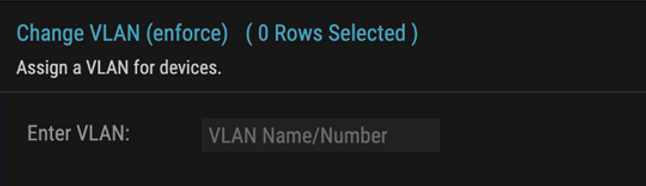
- Pro-active protection: Even if a breach happens, mission-critical assets (medical devices, industrial controls, etc.) can be protected using ORDR-enabled policies such as quarantining, or limiting communications to specific assets over certain protocols.
ORDR supports integration with multiple industry-leading NAC vendors.
- Stay Informed and Respond Quickly: Regularly check for updates from ConnectWise and security advisories from cybersecurity researchers and organizations like CISA. Responding quickly to vulnerabilities by patching can significantly reduce the risk of exploitation.
ORDR’s Call to Action for Customers
Customers are requested to monitor their environment and quickly identify the presence of the ConnectWise ScreenConnect CVEs mentioned using ORDR’s easy lookup methods, then Patch/Remediate them promptly to safeguard their organization against this rapidly known and exploited vulnerability.
Please get in touch with ORDR customer support for any queries or guidance.

Interested in
Learning More?
Subscribe today to stay informed and get
regular updates from ORDR Cloud



