On Friday, May 7, 2021, Colonial Pipeline confirmed that a cyberattack forced the company to proactively close down operations and freeze IT systems after becoming the victim of a ransomware attack. Even though the specifics of how the attack was carried out and its impact have not been disclosed, Colonial confirmed that operations is only partially restored even after three days. On May 10, 2021, the FBI confirmed that DarkSide ransomware was responsible for this attack on Colonial Pipeline.
What is Ransomware?
Ransomware is a form of malware designed to encrypt files on a device, rendering any files and the systems unusable. This is usually carried out by malicious actors who then demand ransom in exchange for decryption. Ransomware actors often target and threaten to sell or leak exfiltrated data if the ransom is not paid. According to the latest industry trends, ransomware activity increased by close to 150% in 2020, with each event resulting in an average downtime of 18 days. The report also mentions an increase of financial loss for each event by 200% from 2019.
What is DarkSide?
DarkSide is a group that has used ransomware to attack various companies in the U.S. and Europe. They have attempted to extort companies with threats and claims to give part of the money it makes to charity organizations. DarkSide follows a growing trend by ransomware gangs called “double extortion,” where the hackers not only encrypt and lock the data but threaten to release the data if ransomware is not paid.
FBI Flash Announcement of Indicators of Compromise (IOCs)
On May 10, 2021, the FBI announced IOCs for the DarkSide ransomware. The list included a set of IP addresses and URLs that are associated with this ransomware. Our security team has incorporated these IOCs into the ORDR platform.
IP addresses associated with DarkSide
176.123.2.216 51.210.138.71 185.105.109.19 192.3.141.157 213.252.247.18 23.95.85.176 159.65.225.72 80.209.241.4 46.166.128.144 108.62.118.232 185.203.116.7 185.203.117.159 104.21.69.79 172.67.206.76 185.203.116.28 198.54.117.197 198.54.117.199 185.243.214.107 45.61.138.171 45.84.0.127 212.109.221.205
URLs associated with DarkSide
catsdegree.com fotoeuropa.ro 7cats.ch securebestapp20.com gosleepaddict.com kgtwiakkdooplnihvali.com yeeterracing.com/gate ironnetworks.xyz lagrom.com openmsdn.xyz ctxinit.azureedge.net
Tracking DarkSide using ORDR
There are a number of challenges when tracking ransomware typically:
- Security controls might not have complete visibility to track Patient 0. Most ransomware is targeted
- Lateral movement of malware is widespread. Security teams need complete visualization of East-West traffic to detect lateral movement
- Ransomware typically uses standard protocols like HTTPS to communicate to C&C servers, so the traffic may appear benign.
Here are best practices using your ORDR deployment to track a potential DarkSide ransomware infection within your organization.
1. Identify and understand risks for every device
ORDR uses DPI and AI, along with enrichment from a variety of different security and threat intelligence feeds to calculate the risk and security posture of every device. Device context including static attributes like O/S of the device, hotfixes deployed, installed software deployed, and the behavioral patterns of the device provides a unique view of the risks of a device. ORDR uses industry-leading threat intelligence to detect close to 25 critical event types to identify vulnerable devices in the network, and offers an actionable risk score.
2. Track East-West lateral movement with ORDR Threat Detection Engine
ORDR sensors deployed across the network support the full stack L7 threat detection capabilities. Most organizations focus on north-south threat detection, but east-west traffic analysis is critical to lateral movement and is a major blind spot for enterprises as this analysis is outside the realm of perimeter firewall.
3. Monitor Communications to DarkSide C2
ORDR’s multi-dimensional threat intelligence (URL reputation, IP reputation, IDS, weak passwords/certificates, etc.) has been updated to track all future communications to the malicious entities associated with the DarkSide ransomware in real-time. ORDR SCE also supports capabilities to analyze traffic retrospectively for these communications.
Currently, in the ORDR SCE 7.4.2 R1 release this can be accomplished by working with the ORDR Customer Support team. In the upcoming ORDR 7.4.2 R2 release this can be done via YAML and ORDR will support a simple customized YAML file to track these entities. Users can simply edit the YAML file and add the above list of IOCs to the file. This will update the system in real-time and will analyze all new and retrospective communications against the list and mark them accordingly.
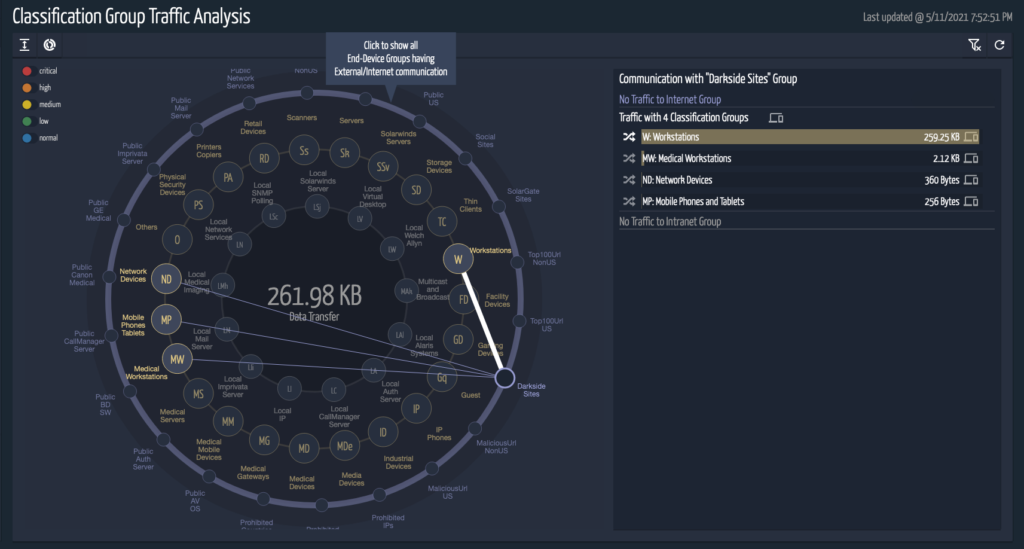
All the IP addresses communications will be captured under Prohibited IP, and the URL communications will be captured as part of suspicious domains in the security page of SCE. The risk score for the devices with these communications will increase accordingly. This information is also available on the traffic analysis tool, where you can drill down on the data based on the classification type, VLAN or Subnet.
4. Customized Security Event Monitoring
One other feature added to the upcoming 7.4.2 R2 release is the ability to create a special event that track customized IP addresses and suspicious domains. Users can configure the event by simply editing the YAML file named “monitoring-groups.yaml”.
Users can follow steps to create a new event called DarkSide and add associated URLs and IPs given in the list to the file. This will create a new entry in the ORDR Group Traffic Analysis constellation view which, provides users with a complete overview of network communications. The user will have an option to drill down the communication patterns of each device associated with the event. This could give some pointers to other devices that should be analyzed for potential infections. Multiple events can be created if needed.

Interested in
Learning More?
Subscribe today to stay informed and get
regular updates from ORDR Cloud




