Today’s tech-dependent enterprises are no strangers to change. Our customers’ experiences demonstrate that familiarity daily. Whether they operate in healthcare, financial services, manufacturing, education, or government, they must contend with a constantly evolving infrastructure within their organizations, and constantly evolving threats from the outside. On top of that are the regulations and evolving business standards and practices that influence day-to-day operations.
Embracing digital transformation for all its benefits means buckling in for a bumpy ride—bumpier for some industries than others. Digital transformation expands an organization’s capabilities and opportunities, but it takes effort. In healthcare, for example, I recently stumbled on an interesting digital transformation report stating that only 16% of healthcare providers are in the “win zone,” meeting their transformation goals and driving sustainable change. The average across other industries is over 30%. That figure may be discouraging, but it is absolutely understandable, and organizations in healthcare as well as other industries can learn a lot from the experiences of their peers.
High Risks, Big Rewards
Using technology to improve patient care and operations sounds simple, but it is a complex endeavor that takes herculean effort. The pandemic briefly diverted attention away from long-term planning, but most health delivery organizations (HDOs) and other enterprises are back to addressing their plans and priorities. They are beginning to switch back from being reactive to a proactive mode. And with good reason.
Although high stakes, high costs, and risk aversion have discouraged many in the healthcare industry and beyond from fully embracing digital transformation, the rewards are too great to ignore. And the threats, expectations and competition all organizations face are not standing still. Done well, digital transformation delivers benefits that outweigh the risks and so, for those that have been reluctant to act, the time to embrace digital transformation is now.
What’s Fueling this New Wave of Transformation?
Over the years, every organization I have worked with—no matter how big or small—boils down their core priorities to three essential goals:
- Protecting people and the network
- Preserving service availability
- Improving operational efficiency
Those goals never change, even when the tools and strategies for achieving them do. And what’s more, they are transferable to other contexts as well: keeping manufacturing equipment operational and staff safe on the shop floor, preserving service availability for financial transactions, maintaining the operational efficiency of constituent services, etc. Consistent with these goals, here are some key initiatives and capabilities that are driving this new wave of transformation and pushing the boundaries of operational potential.
- Remote workforce support (i.e., work from home);
- Remote facility, branch, and clinic operations;
- Contractor and equipment maintenance support and outsourcing;
- Data center transformation and migration to hybrid cloud;
- Digital supply chain enablement; and,
- Mergers and acquisitions.
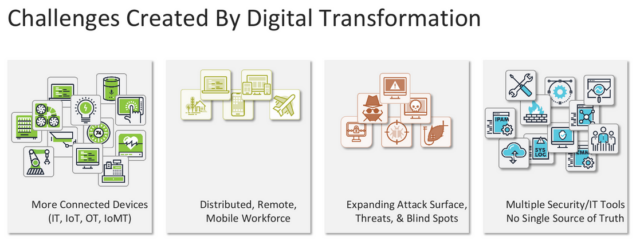
These use cases show how, more and more, connected devices are integral to fulfilling an organization’s mission. And as the inventory of connected devices expands—including the Internet of Things (IoT), Internet of Medical Things (IoMT), operational technologies (OT), mobile, and other devices—those deployments reflect the evolution of the technology. Assets that were once under tight control, on-premises and behind the firewall, are now expanding and connecting beyond traditional boundaries, across multiple network dimensions, and outside of the view and control of IT.
Here are some examples:
- Access from Any Device – IT, IoT, IoMT, OT, IoXT.
- Access from Anywhere – remote sites, remote workers, telemedicine.
- Deployed Anywhere – private and public cloud, virtualized data centers.
- Modern Apps/Mobile Apps – XaaS, training, collaboration, any device-anywhere-any deployment support.
- Ecosystem – third party apps, supply chain access, mergers and acquisitions.
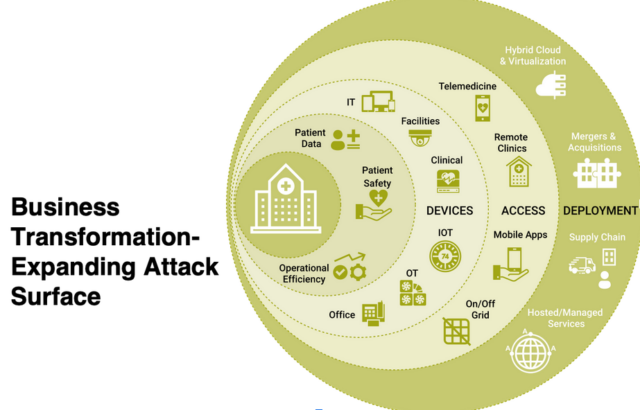
What Keeps the CXOs Up at Night?
IT leaders tasked with driving new digital transformation initiatives understand that success goes well beyond merely integrating new technologies and getting them up and running. Enjoying the multitude of benefits that can follow the completion of a technology refresh comes with many elements contributing to the pucker factor that keeps a CXO awake at night. An expanded and expanding attack surface is at the heart of this unease. Acknowledging that fact, and the factors that play into those concerns, is the first step in planning for and addressing them during the transformation process, rather than promising yourself that you’ll “get to it eventually.” Some pucker factors are reflected in several troubling trends.
Surge in Ransomware Attacks
Ransomware attacks are now more frequent, sophisticated, and severe than ever—and getting worse. Attackers know that many organizations will pay huge ransoms because costs associated with downtime and operational disruption may be even higher than what attackers demand. In healthcare, disruptions caused by ransomware can have life and death consequences.
Prevention is the best way to deal with the ransomware threat, but old school methods simply don’t work. Prevention demands accurate and timely detection, and response automation that can block an attack from progressing to its target destination. You need a way to detect ransomware early, before it has encrypted your organization’s files, because then it’s too late to take effective action.
State-Sponsored Attacks
Adversarial nation states have become adept at using the ambiguity of cyberwarfare to launch attacks on critical infrastructure and economic targets, as well as organizations that hold valuable intellectual property. The tools and methods developed for these campaigns are rarely confined to a limited set of organizations either, as sowing chaos is part of the strategy.
For example, the U.S. Cybersecurity and Infrastructure Security Agency (CISA), along with the FBI and Treasury Department issued a joint advisory about North Korean Maui ransomware targeting the healthcare industry. Similarly, Russian threat actors have been hard at work compromising connected devices and using them as a platform for attacks, including data exfiltration after establishing communications with command-and-control servers in Russia.
Digital Supply Chain Security
Digital supply chains that allow for remote and automated service between organizations have been a boon for operational efficiency—and for threat actors able to compromise those connections for their own ends. The SolarWinds Orion attack targeting U.S. federal agencies and commercial enterprises illustrated how damaging supply chain attacks can be.
Vulnerable SolarWinds servers sitting inside agency and corporate networks, operating with privileged access to IT systems, proved to be a gold mine for hackers to exploit and get whatever data they need, including high level state and military secrets.
Shadow IoT
One big security challenge faced by enterprises today is the presence of connected devices on their networks operating outside the view of IT security and operations. Known as “shadow IoT,” these devices epitomize the mantra you can’t protect what you can’t see. A recent Five Fifty report by McKinsey highlights the risk of the proliferation of devices connecting to the network as shadow IoT (such as the infamous hack of a casino using a connected aquarium thermometer as the vector of attack) and lack of readiness for most organizations.
Often these systems operate with outdated OSes, are unpatched, and unmanaged. Without proper onboarding—or a security platform able to detect, identify, profile, and monitor any device that connects to the network—any organization with shadow IoT operating within its IT estate is at risk of an attack.
How Ordr Helps Enable Secure Digital Transformation
Ordr’s mantra from the beginning has been to enable our customers to SEE, KNOW, and SECURE every device that is connected to their organization. To do this, we establish the most comprehensive and accurate single source of connected device truth in the Ordr Data Lake for each of our customers. This starts with automatically discovering and accurately classifying every connected device because you can’t secure what you can’t see.
From this foundation of visibility Ordr provides a complete view of the connected device attack surface including how devices are connected and communicating, which devices are vulnerable, and the unique risk each device represents in the environment.
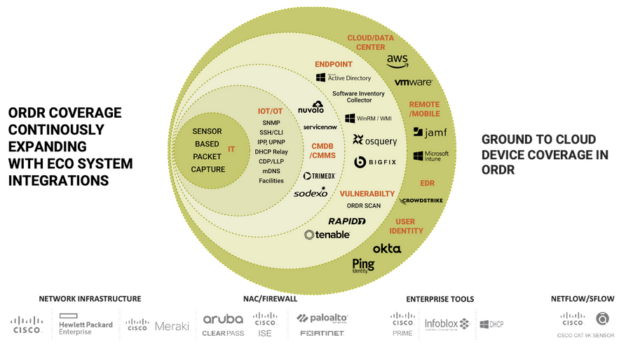
Integrations across the security, networking, and IT ecosystem are integral to the Ordr solution. These integrations enhance the already rich view Ordr has of connected devices by centralizing additional data points and device details. A good example of this are the recent integrations with Mobile Device Management (MDM) and Endpoint Detection and Response (EDR) platforms in the recent Ordr 8.2 release.
Integrations also enable Ordr to enrich the tools and workflows used every day and improve how teams manage and secure devices. An example here is the recent integration with the ServiceNow Service Graph Connector to help customers ensure the data in their CMDB is complete, up to date, and accurate. Another example is how Ordr device insights are used to optimize vulnerability scanning with Qualys.
Integrations also help teams take action to address vulnerabilities, respond to active threats, proactively improve protections, and ultimately reduce risk. Ordr automates the creation of security policies and enforces those policies by integrating with a customer’s existing security and network infrastructure. With this approach Ordr customers are able to quickly block attacks, quarantine compromises devices, segment vulnerable devices, and accelerate Zero Trust projects to proactively improve security.
We continue to drive innovations across the Ordr platform and expand with integrations across the security, networking, and IT ecosystem to provide our customers with a single source of truth for all their connected devices. Reach out for a demo and to learn how Ordr can help you SEE, KNOW, and SECURE, all your connected devices.

Interested in
Learning More?
Subscribe today to stay informed and get
regular updates from ORDR Cloud