Overview:
On July 23, the National Security Agency (NSA) along with the Cybersecurity and Infrastructure Security Agency (CISA) urged all DoD, NSS, DIB, and U.S. critical infrastructure facilities take immediate actions to secure their Operational Technologies (OT) assets. The alert was issued because in the past few months, threat actors have leveraged internet connected devices to exploit critical infrastructure. OT and IoT devices and systems are designed for ease-of-use rather than with security in mind and thus don’t have the means to detect or mitigate malicious activity. The design of these devices and systems combined with the data that they transmit and share via the internet, make them easily exploitable.
“…civilian infrastructure makes attractive targets for foreign powers attempting to do harm to US interests”
Some of the observed Tactics, Techniques, and Procedures (TTPs) as defined by the MITRE ATT&CK framework are:
- Spearphishing [T1192] to obtain initial access to the organization’s information technology (IT) network before pivoting to the OT network.
- Deployment of commodity ransomware to Encrypt Data for Impact [T1486] on both networks.
- Connecting to Internet Accessible PLCs [T883] requiring no authentication for initial access.
- Utilizing Commonly Used Ports [T885] and Standard Application Layer Protocols [T869], to communicate with controllers and download modified control logic.
- Use of vendor engineering software and Program Downloads [T843].
- Modifying Control Logic [T833] and Parameters [T836] on PLCs.
While Alert AA20-205A discusses OT specifically, IoT is also relevant in this alert, because the alert tackles the 16 “critical infrastructure” sectors as defined by CISA:
Bolded below are the 9 critical infrastructure sectors that are largely impacted by IoT
- Chemical
- Commercial Facilities
- Communications
- Critical Manufacturing
- Dams
- Defense Industrial Base
- Emergency Services
- Energy
- Financial Services
- Food and Agriculture
- Government Facilities
- Healthcare and Public Health
- Information Technology
- Nuclear Reactors, Materials, and Waste
- Transportation Systems
- Water and Wastewater Systems
How Ordr can help:
“At this time of heightened tensions, it is critical that asset owners and operators of critical infrastructure take the following immediate steps to ensure resilience and safety of US systems should a time of crisis emerge in the near term.”
With our comprehensive IoT security platform, Ordr can help organizations address the following recommended steps as outlined in NSA & CISA Alert AA20-205A:
- Harden Your Network
- Create and Accurate “As-operated” Network Map Immediately
- Understand and Evaluate Cyber-risk on “As-operated” Assets
- Implement a Continuous and Vigilant System Monitoring Program
- Exercise your Incident Response Plan
Harden Your Network
Hardening your network starts with visibility into what is actually on your network. With the most comprehensive platform for discovering, profiling, and automating action for connected devices, we passively discover high-fidelity context on every connected device, including; make, model, operating system, firmware, version, location, and application/port usage. This device context is enriched with threat intelligence, vulnerability data, FDA/device manufacturer alerts, and incorporated into our data lake. Organizations then have granular, high-fidelity classification into every device in their network for identification of outdated operating systems, FDA recalls, and devices banned by the U.S Commerce Department. This device context can be integrated with asset management systems.
Using Ordr Flow Genome, we leverage real-time machine learning to profile every device, and visualize and baseline every device’s communications. This allows organizations to have a deep understanding of behavior insights like identifying anomalous or suspicious behaviors, such as communications to external malicious domains, lateral movement of malware/trojans and more. We do this through our security engines that scan for activity on infected machines.
This allows organizations to address the following hardening requirements:
- Identify devices using weak passwords and ciphers – clear text transfer of passwords, default or manufacturer passwords, shared drives, weak ciphers, etc.
- Identify devices that connect to business, telecommunications, or wireless networks – clearly separate devices into managed, unmanaged, and how devices enter the network.
- Closely scrutinize and track devices that are internet-accessible – closely scrutinize outbound connections to internet especially from mission critical devices like PLCs etc., and rate those connections with respect to the reputation of the sites they are reaching out to.
- Closely scrutinize and track devices that have remote management services – extract all administrative protocol interactions like SSH, rlogin, and more to closely monitor manufacturer based remote debugging sessions using protocols like RDP.
Create and Accurate “As-operated” Network Map Immediately
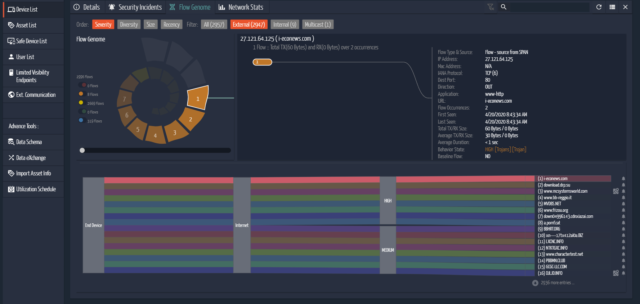
Ordr Flow Genome provides the most comprehensive profiling of every device communications patterns. We are also able to extract the latest authentication information via Active Directory/LDAP, WinRM/WMI and Kerberos to identify device users so organizations can locate devices associated with a specific owner, or identify the most recent authenticated login to a device. Our constellation map also provides a visual network topology view of where these devices are relative to network VLANs and subnets, allowing organizations to quickly address the “network map” requirement,
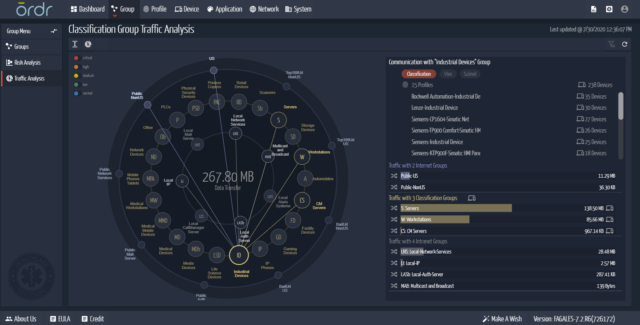
Understand and Evaluate Cyber-risk on “As-operated” Assets
The Ordr dashboard provides flexibility in searching for and investigating the risks outlined by NSA and CISA. This includes using our device inventory and context to identify devices that have been called out by:
- Vendor or technical advisories
- CISA advisories
- CVE vulnerabilities databases
- National vulnerability databases
More importantly, Ordr has the capability to automatically segment and isolate any device that is impacted by vulnerabilities, with one touch of a button. These policies can be enforced on any security or networking infrastructure.
Implement a Continuous and Vigilant System Monitoring Program
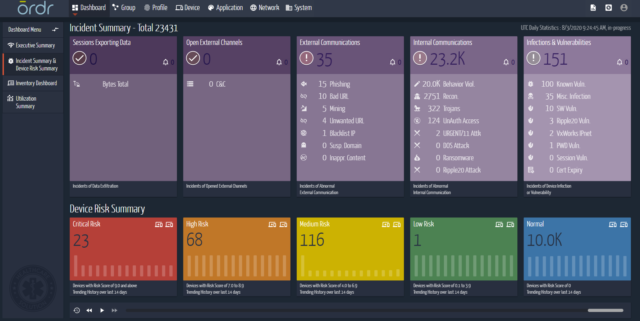
Through the Ordr Incident Summary & Device Risk Summary, we can visually show the continuous discovery and monitoring of devices, highlight any new risks to those devices (ie. Ripple20), alert based on severity, and create action for segmentation.
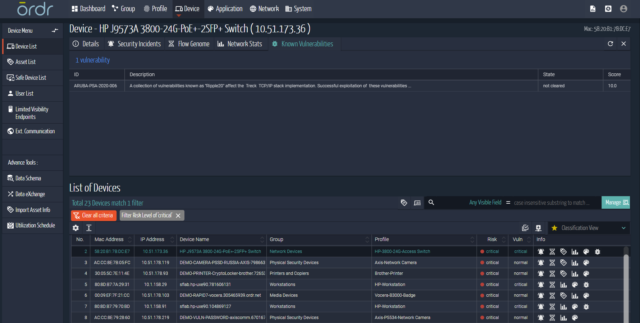
Exercise your Incident Response Plan
We automate the appropriate responses for security and networking teams. These include the automated creation and enforcement of segmentation policies or alerting and triggering a specific security or operational workflow. We also integrate with enforcement points (like switches, CISCO ISE, CPPM, controllers, etc.) to quarantine, blacklist, shutdown or enforce an ACL.
- Proactive Segmentation – Unlike users, devices should only communicate with specific systems. Ordr dynamically create policies to allow only appropriate device communications. These policies can be automatically enforced on existing infrastructure — firewalls, switches, NAC and wireless LAN controllers.
- Operational Actions – when a new or unknown device is discovered, we can trigger a centralized workflow with a CMMS or CMDB to ensure proper inventory, authentication, and routing to the right device owners.
- Security and Incident Response Actions – in the event of a security incident, or if devices have triggered an alert (known vulnerability, weak cipher, weak certificate, active threat, or malicious/suspicious behaviors) we can initiate an incident response workflow in a SIEM or SOAR, or automatically segment the impacted device.
To learn more about how Ordr can help your organization, schedule a demo.

Interested in
Learning More?
Subscribe today to stay informed and get
regular updates from ORDR Cloud




