- PARTNERS
- TECHNOLOGY
Strategic Partnerships That Maximize Your Tech Investments
ORDR partners with leading technology providers across security, networking, IT, and clinical domains — powering 200+ integrations that unify visibility, enrich intelligence, and extend the value of your existing tools.
BigFix
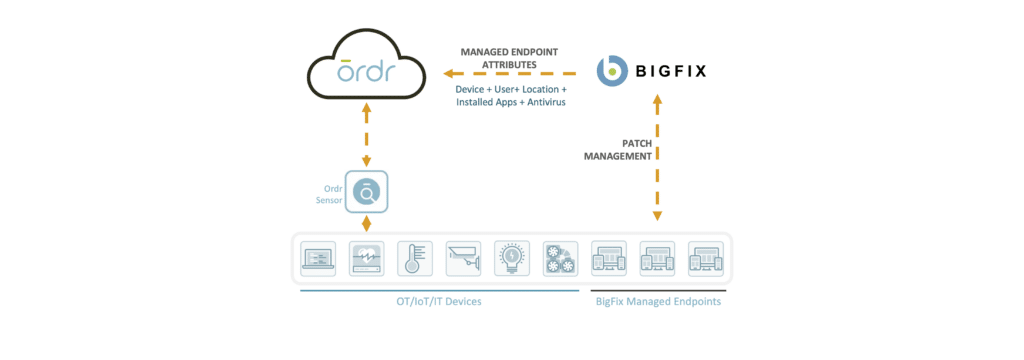
Ordr integrates with BigFix, an endpoint management platform built to discover, manage, and remediate all endpoints whether on-premises, mobile, virtual, or in the cloud – regardless of the operating system, location, or connectivity.
How it works
Ordr collects attributes for all BigFix managed devices and enables you to see and know more about all your devices, their connections, and vulnerabilities.
Benefits
- See Every Connected Device: Automate and centralize discovery of all managed, unmanaged and newly connected devices.
- Advanced Endpoint Profiling: Know more about devices by combining granular Ordr insights with BigFix endpoint data.
- Security Posture Compliance: Gain a comprehensive understanding of risk and generate compliance reports for all managed and unmanaged devices.
Arista
Ordr integrates with wired and wireless infrastructure solutions to combine network details with granular device insights and ensure accurate device classification, location details, and anomaly detection.
How it works
Ordr analyzes collected data to enhance insights through passive discovery, accurately classifying each asset. By analyzing data from Arista switches, it maps communication flows, establishing normal behavior baselines for each device. These baselines are automatically fine-tuned, updated, and compared to historical behavior and similar devices. Ordr identifies anomalies in device behavior, comparing them to global deployments. This analysis enables incident response teams to swiftly pinpoint specific devices, locations, connections, and communication details, facilitating rapid threat response.
Benefits
- See every device connecting to the network
- Identify anomalous behavior
- Accelerate response to threats
Anomali
Ordr’s ability to consume STIX and TAXII – and incorporate these threat feeds into the Ordr Data Lake – now extends this security strategy to the critical realm of agentless devices such as IoT, medical devices, smart office appliances, and operational technology, and more for deep understanding of devices, behaviors, and network intelligence to identify assets, alert on threats, and automate response actions.
Amazon Web Services
The increasing growth of cloud adoption adds a visibility black hole, making it difficult to fully understand how devices are connecting – and what those devices are actually communicating with in the cloud. This increases the risk factors of connected devices exponentially.
Gaining visibility and control across an organization’s entire attack surface of connected assets is one of the most fundamentally important – yet challenging – tasks facing IT and security teams today.
How it works
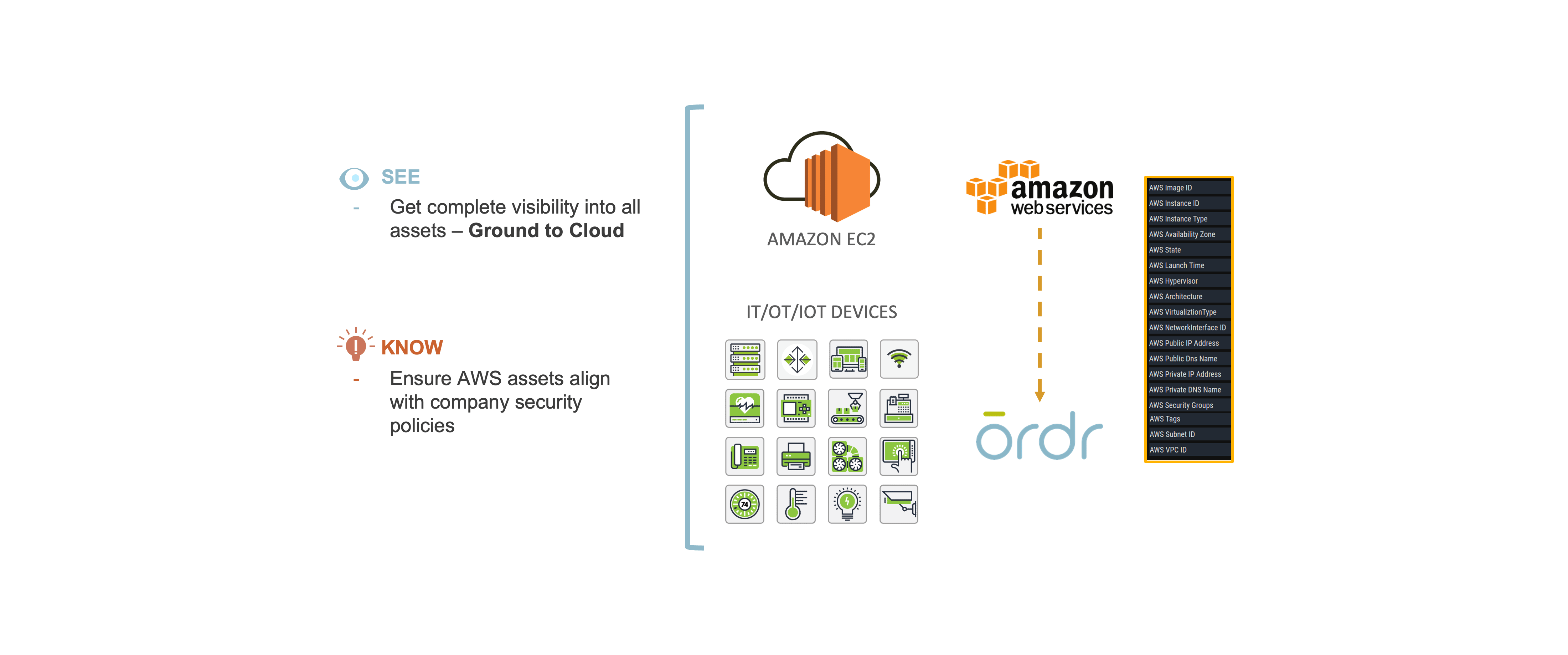
Ordr gathers cloud asset information by collecting attributes from Amazon Elastic Compute Cloud (EC2), the AWS service used to create and run virtual machines.
Benefits
Ordr integrates with Amazon Web Services (AWS) to deliver complete ground to cloud visibility– from assets in remote sites and campus devices, all the way to assets in the cloud.
- See: Get complete visibility into all assets- Ground to cloud
- Know: Ensure AWS assets align with company security policies
Oracle
Enable Single Sign On (SSO) for Ordr with Oracle IDCS.
Symantec
Ordr integration with Symantec allows you to leverage Ordr’s rich device data to create alerts, reports, and custom analyses. Ordr transmits security alerts, device information, and other critical information via the Syslog output format. Symantec ingests the feed, parses the data into proper fields for better event management.
Pulsedive
Ordr integration with Pulsedive automates threat detection and risk assessment for external traffic from all connected devices. Ordr collects details on malicious URLs, IP addresses, and files from Pulsedive.
Ping Identity
Enable Single Sign On (SSO) for Ordr with Ping Identity.
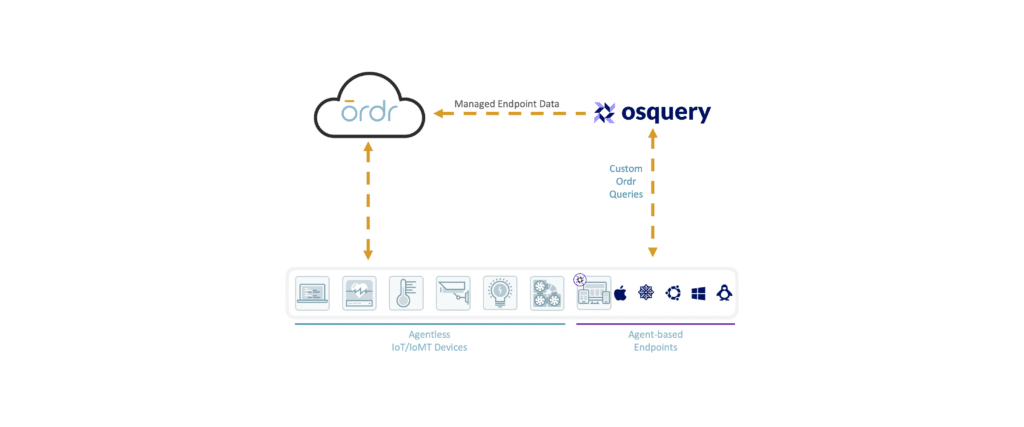
Osquery
Ordr integrates with Osquery by providing a custom query pack for collecting granular device data from devices running the open-source agent.
Gain visibility into all devices independent of operating system with support for Windows, macOS, CentOS, FreeBSD, and almost every Linux distribution.
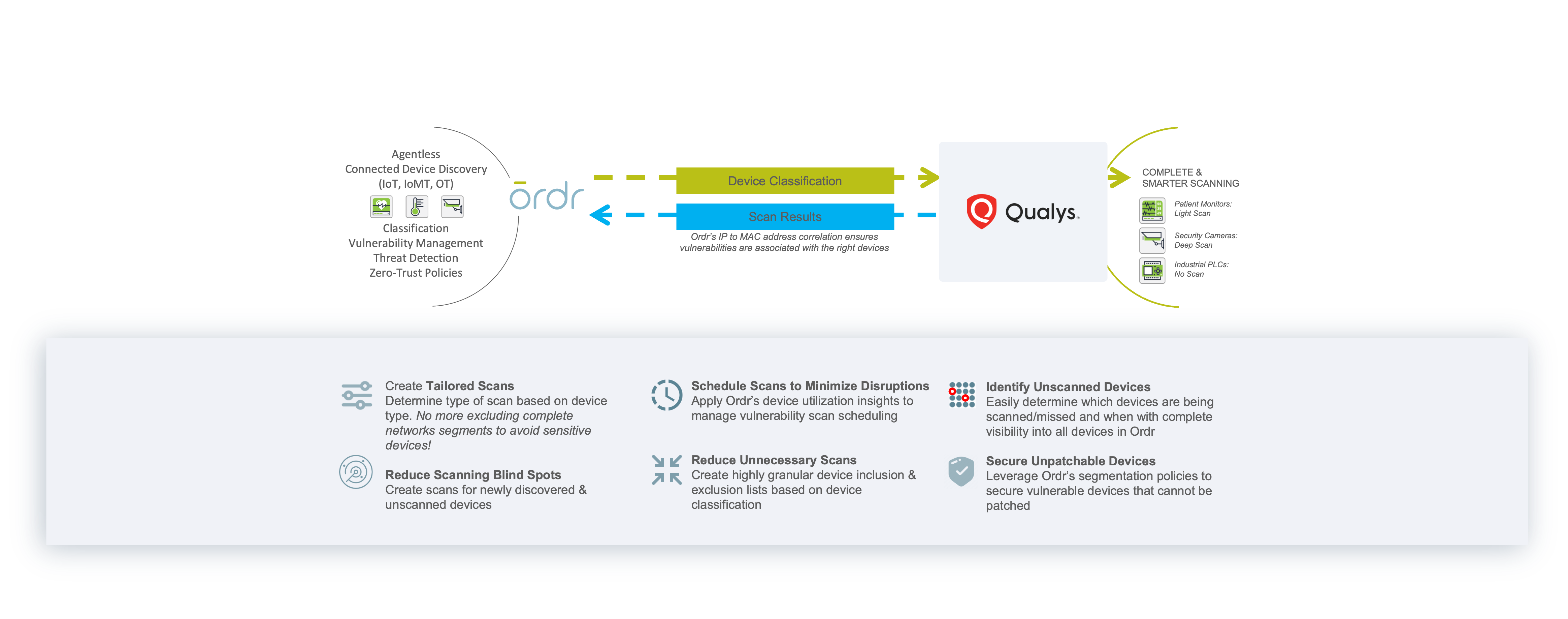
Qualys
Ordr’s bidirectional integration with Qualys enables comprehensive vulnerability scanning without gaps or disruptions. Qualys uses Ordr device insights to determine when and how devices are scanned and if they have been excluded. Ordr uses Qualys scan results in the calculation of device risk scores and other security analytics.
How it works
Ordr integrates with the Qualys Cloud Platform to seamlessly send device insights and enable organizations to identify devices to scan with the appropriate type of scan for each device. Ordr also incorporates Qualys scan results with security and risk analysis to calculate a risk score for every connected device for an accurate and comprehensive view of risk.
Benefits
- Comprehensive Coverage – Gain complete visibility of all devices with Ordr to easily determine which devices are scanned, which are missed, and when scanning occurred. Additionally, Ordr’s identification and classification of lightweight, agentless devices allows administrators to quickly exclude specific connected devices or device categories from active scans, opening network segments to vulnerability scanning that had previously been excluded.
- Optimized Scanning – Easily Identify devices to exclude and apply the right scan type for each device category using detailed Ordr insight on device types, scan sensitivity, and device role within the organization.
- Proactive Protection – Automate segmentation policies with Ordr and enforce with existing security and network infrastructure to secure vulnerable devices rather than block or quarantine critical devices that cannot be patched or updated.
- Smart Scheduling – Leverage device utilization patterns from Ordr to schedule vulnerability scans for times when devices are not in use to minimize disruption and operational risk
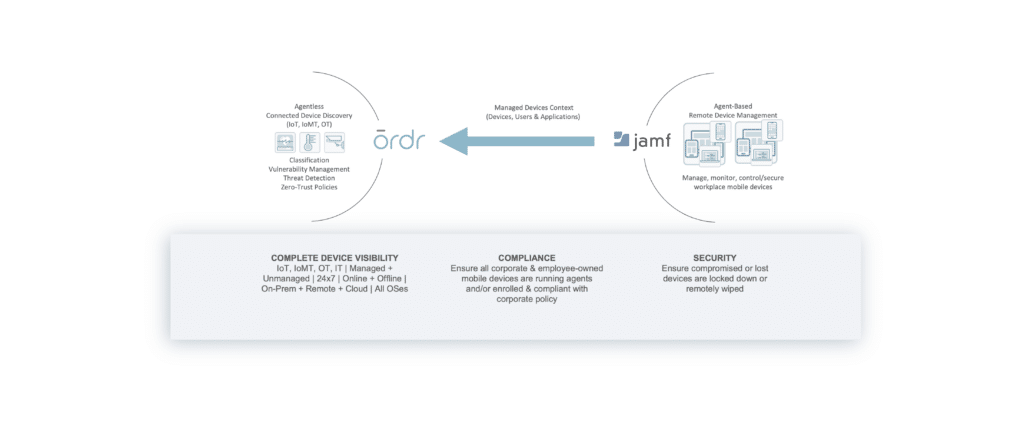
Jamf
Ordr integrates with Jamf to extend visibility to all managed Apple endpoints and enrich the Ordr Data Lake with rich device context from the Jamf platform.
How it works
Ordr integration with Jamf enables organizations to extend visibility to all Jamf managed Apple devices. Ordr collects device, user, and installed application details to enrich the Ordr Data Lake and enhance the view of all devices, connections, and vulnerabilities.
Benefits
- Real-time visibility of all connected devices across all operating systems, on-prem, remote, managed, and unmanaged.
- Comprehensive insights into vulnerabilities and risk prioritized to align with your organization.
- Centralization of the view for your connected device attack surface and risk posture.
- Acceleration of threat response and proactive Zero Trust security efforts with automated policy.
- Accurate and up-to-date device details to meet compliance and cyber insurance requirements.
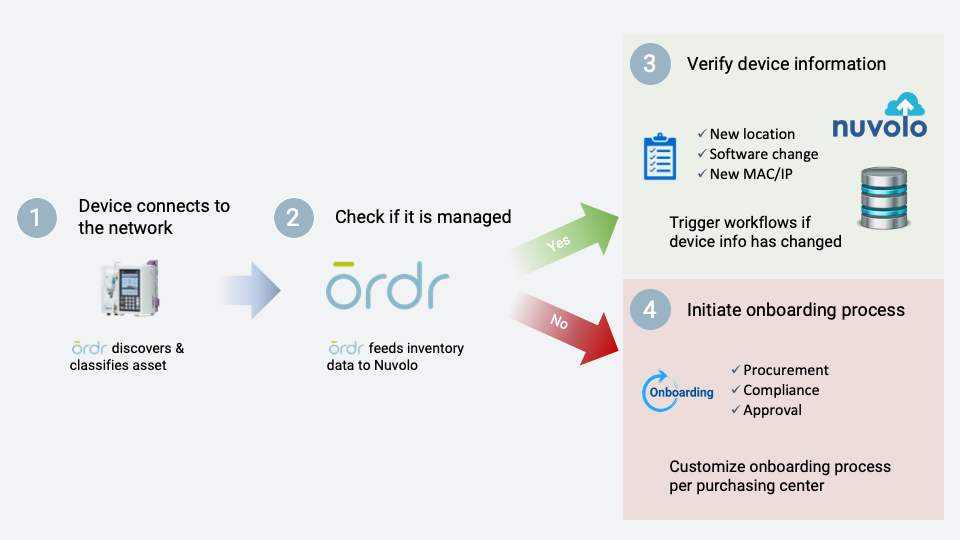
Nuvolo
Ordr and Nuvolo have teamed up to create a healthcare partnership to reduce device cyber security risk. The solution combines Ordr’s superior IoT Security Platform to discover and profile connected devices in healthcare organizations with Nuvolo’s workplace management platform for healthcare.
The joint solution enables organizations to optimize their device utilization while significantly reducing risk and improving operational efficiency.
How it works
Ordr’s bidirectional integration with Nuvolo allows you to simplify inventory management and proactively mitigate risk. Ordr collects inventory data from Nuvolo and sends Ordr-discovered device data along with risk and utilization details for all devices.
Benefits
- Streamline inventory management: automatically build and maintain a complete and accurate inventory of connected medical devices and eliminate the manual inspection and software version record-keeping
- Optimize device utilization: monitor core components of the medical device fleet to efficiently manage and understand medical device utilization data, right-size inventories, lower costs, and optimize placement.
- Risk management: inform security operations on the precise nature of a vulnerability or threat, quickly identify any at-risk medical devices, and take proactive measures to mitigate risk including implementing granular segmentation to protect devices











