Coauthors: Srinivas Loke, Gowri Sunder Ravi
Progress Software, which makes the MOVEit Transfer app, first disclosed a vulnerability for the MOVEit application on May 31st, 2023. The MOVEit application is a managed file transfer software produced by IPSwitch (acquired by Progress Software Corporation). It encrypts and uses secure FTP to transfer data with automation. MOVEit is used by thousands of enterprises, including 1700 software companies and 3.5 million developers. MOVEit is also used significantly within the healthcare industry, with HHS recently issuing an alert on this.
1. What Are The MOVEit Vulnerabilities?
CVE-2023-34362, with a CVSS score of 9. 8, is a critical SQL injection vulnerability affecting MOVEit Transfer and MOVEit Cloud. The vulnerability allows unauthenticated attackers to control a MOVEit installation completely, potentially leading to data alteration or theft, malicious software installation, and server configuration changes. The MOVEit Transfer versions affected are:
- before 2021.0.6 (13.0.6), 2021.1.4 (13.1.4), 2022.0.4 (14.0.4), 2022.1.5 (14.1.5),
- and 2023.0.1 (15.0.1)
Following this disclosure, two additional vulnerabilities were disclosed for a total of three to date:
- CVE-2023-35708 (June 15, 2023) with patching recommendations here:
- CVE-2023-35036 (June 9, 2023) with patching recommendations here:
- CVE-2023-34362 (May 31, 2023) with patching recommendations here:
2. Has this vulnerability been exploited?
Exploits of the vulnerability have been discovered in the wild, and have been attributed to the Cl0p ransomware group (also known as FIN11 or Lace Tempest). It has been reported that attacks against this vulnerability were “zero-day attacks” and may have begun as early as May 27, 2023, before a patch was available or the vulnerability was publicly disclosed or discussed.
3. Recommendations by Progress Software
- Disable all HTTP and HTTPs traffic to your MOVEit Transfer environment
- More specifically, modify firewall rules to deny HTTP and HTTPs traffic to MOVEit Transfer on ports 80 and 443 until the patch can be applied.
- Review, Delete, and Reset
- Delete Unauthorized Files and User Accounts (Particularly looks for an event associated with human2.aspx)
- Delete any instances of the human2: aspx (or any files with the human2 prefix) and .cmdline script files.
- On the MOVEit Transfer server, look for any new files created in the C:\MOVEitTransfer\wwwroot\ directory.
- On the MOVEit Transfer server, look for new files created in the C:\Windows\TEMP\[random]\ directory with a file extension of [.]cmdline
- On the MOVEit Transfer server, look for new APP_WEB_[random].dll files created in the C:\Windows\Microsoft. NET\Framework64\[version]\Temporary ASP .NET Files\root\[random]\[random]\ directory:
- Stop IIS (iisreset /stop)
- Delete all APP_WEB_[random].dll files located in C:\Windows\Microsoft. NET\Framework64\[version]\Temporary ASP. NET Files\root\[random]\[random]\
- Start IIS (iisreset /start). Note:The next time the web application is accessed, it will be rebuilt correctly. It is normal to have 1 APP_WEB_[random].dll file located in this directory.
- Apply the Patch
4. How Ordr Can Help
Detection
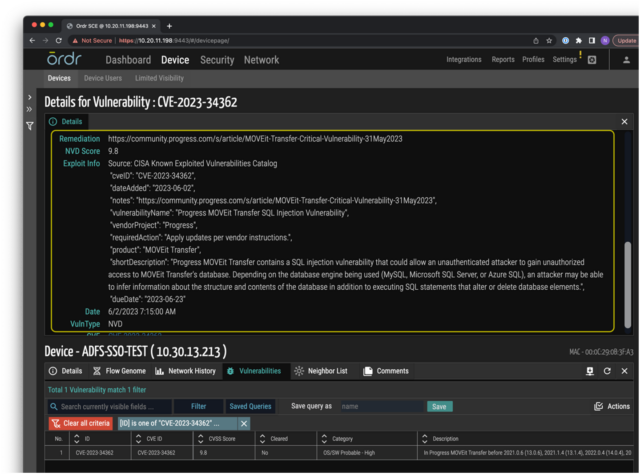
Vulnerability mapping of impacted devices:
- Ordr provides application mapping via its Software inventory Collector to detect MOVEit applications in the network and uses its Vulnerability Matching engine to identify whether the organization is impacted:
- Using its Software Inventory Collector, Ordr provides visibility into all the apps installed on all enterprise or health system devices, workstations, and servers.
- Ordr maintains a list of all the software packages installed on the endpoints with version numbers and a time stamp on when it was installed/last updated etc.,
- Ordr vulnerability mapping engine assigns vulnerabilities based on the SW version collected from the endpoint. The installed application list is updated daily, and vulnerabilities are recalculated based on the new info.
Real-time detection of exploits using IDS, behavioral violation, and threat correlation:
- Ordr has an IDS engine that can detect this specific vulnerability using analysis of packets transacting over the wire.
- Ordr IDS signatures have been updated to detect exploits of the MOVEit vulnerability
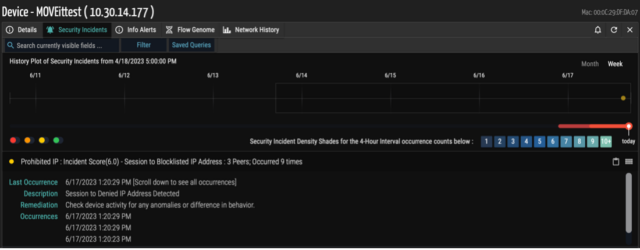
Track communications to compromised IP/URLs:
- In real-time, Ordr’s external IP/IOC tracks every communication to prohibited IP/URLs. Ordr uses a cloud-based threat intelligence platform where the list is continuously updated, and all communications are marked accordingly in the Ordr Security Threat Card.
- Ordr scoured the internet to establish a list of MOVEit IPs/URLs and tracks all communications associated with this vulnerability with a “group” within the Ordr Traffic Analysis Tool outer ring. Ordr has named it “MOVEIT” in the classification analysis. All the lookups done using this method are retrospective in nature and map every communication to these IoCs.
- Users can easily track and tag every device communicating with malicious IPs for remediation purposes.
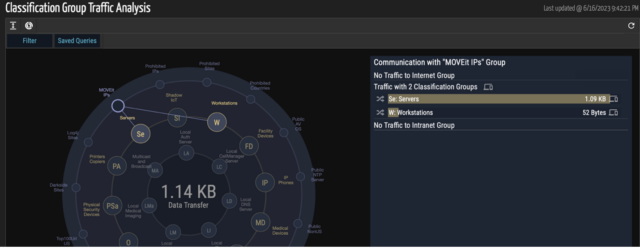
Baseline communications to surface anomalies:
- Ordr also provides the capability to baseline all the communications based on profile, location, business function, or any customized entity using our AI/ML techniques. Ordr can trigger anomalies based on any deviations observed for this traffic. Ordr recommends using our behavioral anomaly and threat detection capabilities to identify anomalies while performing any incident response or remediation.
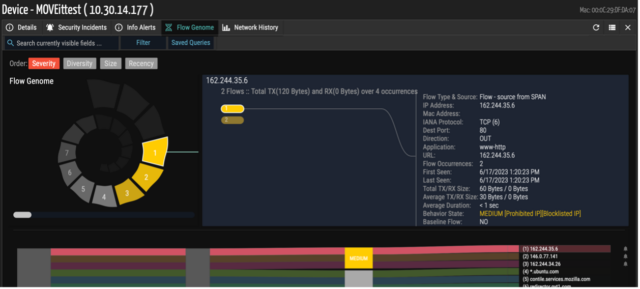
- Ordr adjusts the risk score of the device based on the events detected for the device along with the asset criticality. For example, Ordr assigns a higher risk score for devices with vulnerability and exploits vs. devices only with vulnerability. All of the risk scores are normalized based on the criticality.
Mitigation
- M1051 (ATT&CK) – Update Software
- Patch immediately. Refer to the Progress Software Knowledge Base above and apply the fixed versions of MOVEit Transfer.
- M1040 (ATT&CK) – Behavior Protection on Endpoint – Rapid threat containment if a breach is detected.
- Ordr tracks every device’s connectivity and keeps real-time data on where the device is connected to in the enterprise network – wired switch, wireless AP, VPN, and so on.
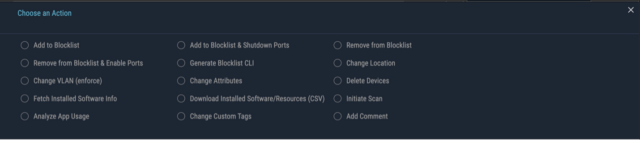
- When an alarm of a breach comes into the SOC team, the Ordr platform provides a one-click action to immediately get the device isolated or segmented into a quarantine VLAN.
- Ordr supports a variety of threat containment actions, as shown below:
- M1037(ATT&CK) Proactive firewall policies:
- Disabling HTTP (port 80) and HTTPS traffic (port 443) to MOVEit Transfer in the interim is recommended to prevent exploitation.
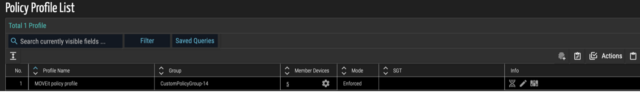
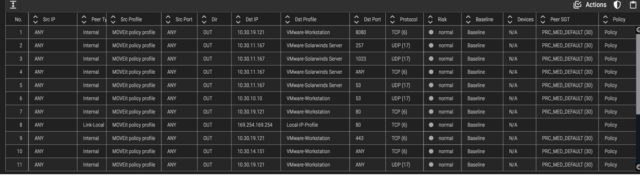
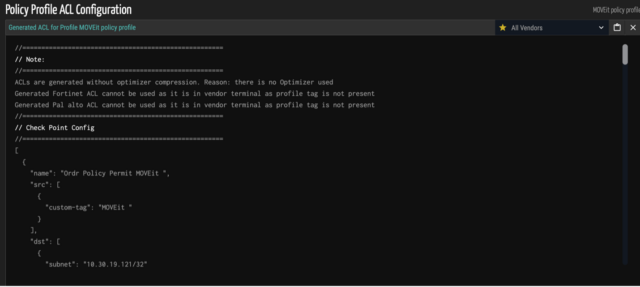
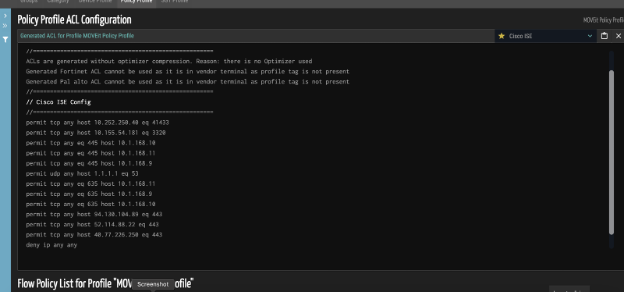
- Create a policy profile with all the MOVEit servers, then build a firewall policy to block ports 80 and 443 inbounds from an external address.
- Ordr supports integration with multiple industry-leading firewall vendors. Below is a sample screenshot of one vendor.
- M1030(ATT&CK) – Network Segmentation:
- Ordr’s segmentation policies can protect the mission-critical devices
- Even if a breach happens, mission-critical devices, for example, medical or devices in ER/OR, can be protected using Ordr policies. Only specific devices over certain protocols can communicate with these mission-critical devices.
- Ordr supports integration with multiple industry-leading NAC vendors.
6. Ordr Customer Updates
Ordr has prepared the following software configuration rules package (no software change required) and is working with customers on pushing them to their separate instances with utmost priority:
- Ordr Vulnerability Database to match against devices vulnerable to MOVEit.
- Ordr IDS engine to detect exploits related to MOVEit vulnerability.
- IoCs associated with MOVEit vulnerabilities are constantly updated and all the existing and new communications are mapped against these IoCs and are updated in the Ordr’s traffic analytics diagrams.
- All the indicators of compromise will be flagged on the Ordr’s security page and added to the alerts. Ordr constantly streams to the SOC/SIEM and sends emails to the admin if configured.
7. Helpful Links

Interested in
Learning More?
Subscribe today to stay informed and get
regular updates from ORDR Cloud



