Did you know that Windows 7 end of life is on January 14, 2020? This is only 300 days away, and today over 40% of the desktops deployed are still running this 10 year old OS. I can’t even imagine the number of imbedded IoT, OT, and Medical Devices where this OS is still used. This is going to be a big issue for the security community in 2019 to get their arms around this Windows 7 End of Life, the impact it will have on their security posture, and in medical and industrial fields – the safety risks it will expose to their patients and workers.
Here is a great article highlighting the EOL in more detail.
3 Ways Ordr Can Help You Take Control of Windows 7
- Ordr Discovery | Inventory | Categorization: Ordr captures the OS detail on devices as we do our automated Discovery, Inventory, Categorization and analysis of the traffic flows (Flow Genome).
Here is an example of a GE Ultrasound Machine, but the same would apply to other systems:
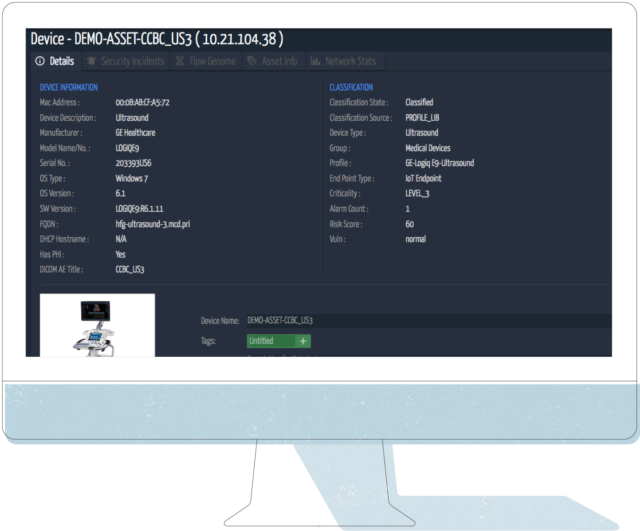
- Ordr integrates with CMDB / ITAM / CMMS Systems: If you integrate Ordr with your CMDB / IT Asset Management / CMMS system – say ServiceNow, Nuvolo, etc – you can further improve your visibility by leveraging the real-time always on view of the Ordr solution, to then update your records as you work to identify systems that need to be updated, who the device owners are, location of the equipment, where it is in its lifecycle, and perform post upgrade validation to close out the update work and document the remediation.
Here is a view of the same Ultrasound Machine as above, with the integrated asset detail from a CMMS system:
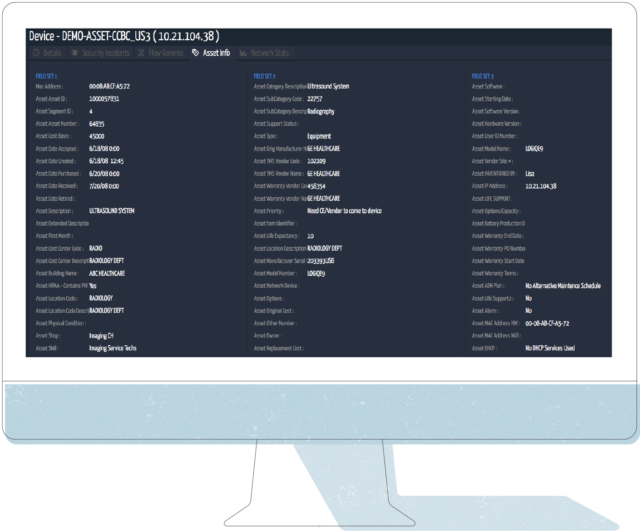
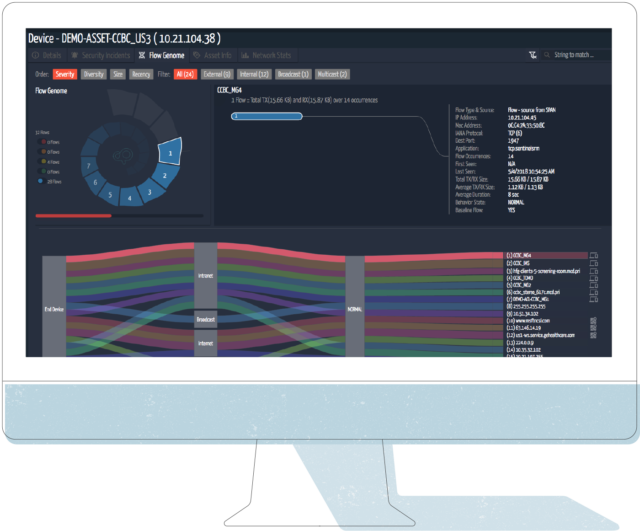
- Asset Info to Action: Armed with all this detail, Security and Network teams can start working with the appropriate lines of business (HTM in my example case), to figure out a plan to either upgrade the system, replace the system, or if can’t replace it and you are stuck with it on your network – build security controls around the device. This is where Ordr helps close the loop. One key area we can help is our capabilities around the behavior of the device in the network, the Flow Genome. Below you can see the 24 baselined normal flows Ordr has detected during this devices time on the network under monitoring.
See below, we will use this information in step 4:
Time to Take Control! OK, so you are stuck with the Windows 7 device on your network beyond 1/14/2020. You are armed with the information in steps 1 – 3. What do you do about it? How do you build in the right controls? This does depend on the environment, where there are firewall systems, NAC, network infrastructure that supports ACLs, etc. I will give you the most common actions I have seen, that should fit most of the customer environments you are working in.
Common controls Ordr can help you achieve
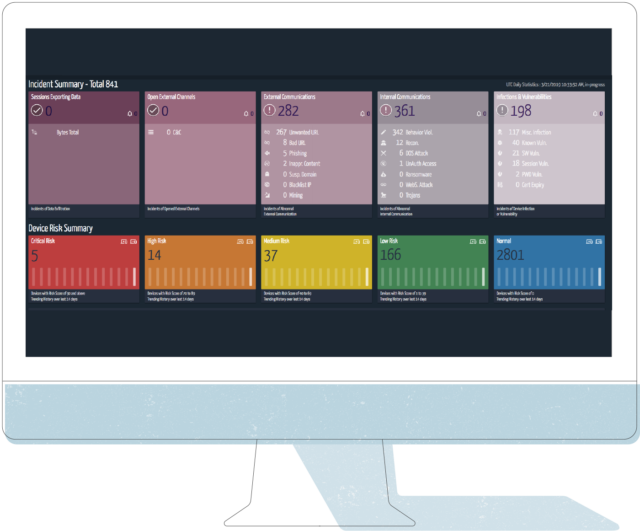
- Leave the device as is, but monitor it: This is probably the most common control. Monitor the device and respond to any alerts, change in behavior. There is concern especially with OT and Medical Devices around putting limiting controls in place. The good news is Ordr can alert on Behavior Violations, meaning if the device starts communicating outside of its Normal Baseline Flow. Ordr can be integrated into a workflow management system, send out email alerts on its own, fire off events to a SIEM or other Orchestration tool, or have a screen like the one below up in your SOC for human monitoring.
Below is a screen shot of our Incident Summary & Device Risk Dashboard: The Behavior Viol. count under Internal Communications is where we highlight behavior anomalies detected by the Flow Genome. All of this is linked to the events to quickly see and understand the reason for the alarm.
- Build a specific VLAN with ACLs for this Device Type: One approach to segmentation is with a custom VLAN for a device type, in this case GE Ultrasound Devices. The good part about Medical IoT, and IoT in general, is there is usually a consistent communication pattern for how it behaves on the network. In the case of a VLAN configuration with Access Control Lists for communication, the Security, HTM, and Network team could build the rule set for this ACL and limit the communication behavior. Or, you could let Ordr generate the ACL for you, that you apply in the environment. Here is an ACL based on the example system above:
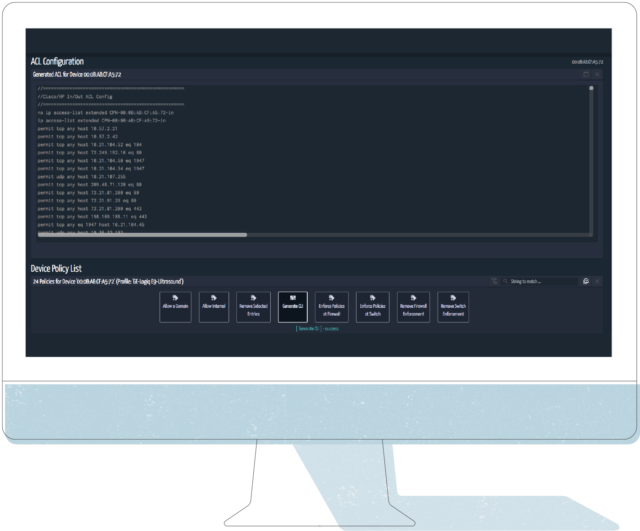
- Integrate with your Network Access Control (NAC) solution: In this case Ordr can talk with your NAC system to put this device in a specific group (TAG), where there are ACL and/or TrustSec TAGs to identify and control access of this device. All of the attributes shown above can be shared, and the NAC solution can handle the controls around this device.
- Integrate with your Firewall system: Many customers are leveraging firewalls as part of their segmentation approach. Beyond the normal Internal to External (North / South) traffic control / protections from a firewall, they are putting more Firewall systems in the internal network (East / West) to segment the network. This helps with controlling the traffic flow, gives inspection points, and also gives the chance to apply other security tools of an Advanced Firewall feature set and the audit logging of the communication internally. Ordr integrates with firewall systems to either apply Firewall ACL’s to the traffic discovered by the Flow Genome, or to apply a Security TAG to the firewall. Many of these firewalls support Tagging as well for device groups, so you don’t have to build individual policies for each device. Ordr can give information to North/South and East/West firewall systems, to help with segmentation control.
What other strategies and ideas do you have to Take Control of the Windows 7 End of Life? Let us know.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud




