exposed records every year
M
The process of identifying non-compliance and security control gaps is complex, with 156M records exposed annually due to security gaps.
average lifecycle of a breach
Days
The average lifecycle of a breach from identification to containment is long. On average, it is 277 days.
of companies expect increases
%
Manual processes for demonstrating compliance already burden teams. Companies expect requirements to increase.
Automate Security Coverage Gap Discovery
AUTOMATED INVENTORY
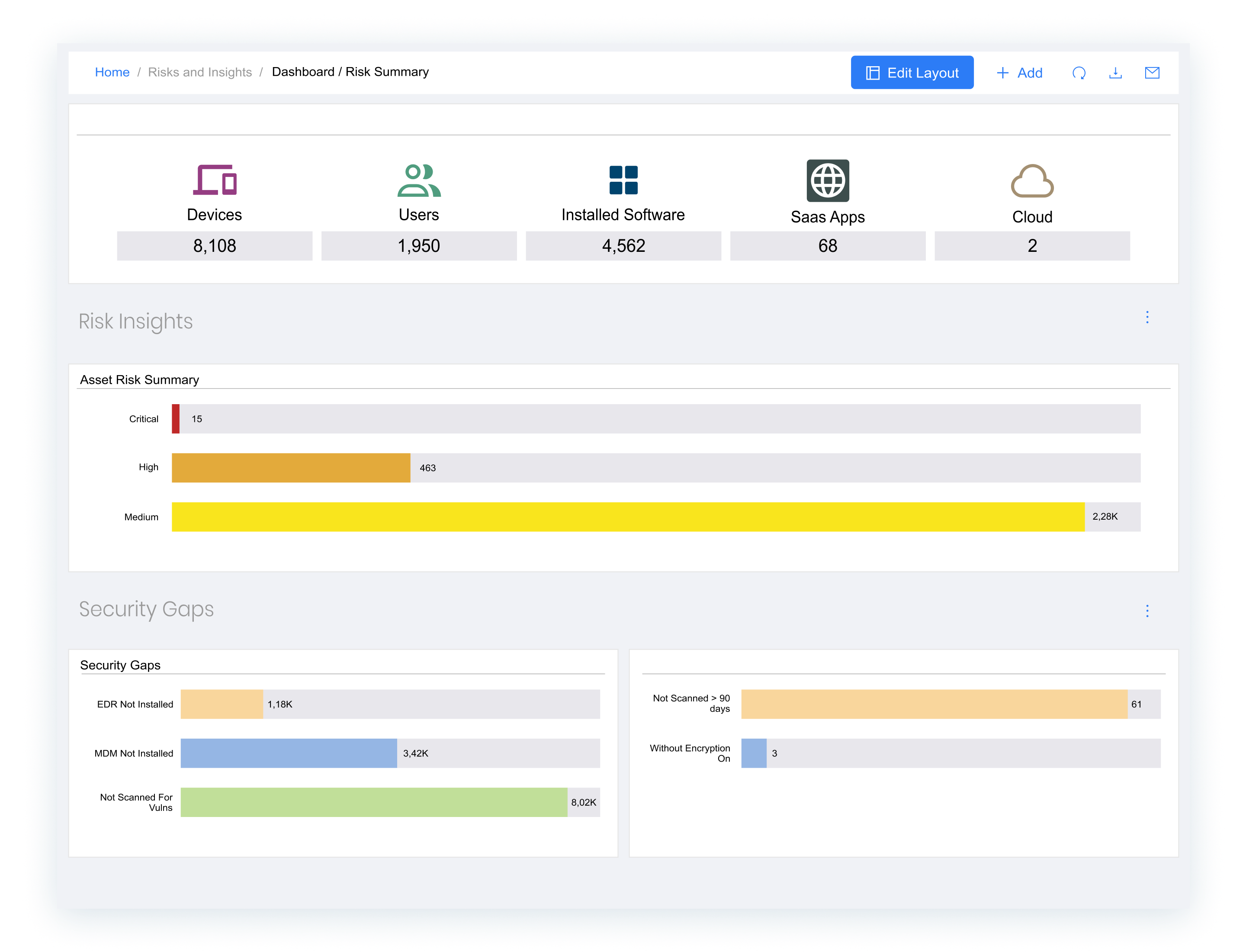
Real-Time, Accurate Asset Inventory
Ensure comprehensive asset oversight with automated inventory capabilities, eliminating the need for manual methods and fine-tuning, and uncover hidden gaps in asset management. Visualize relationships and dependencies with an intuitive UI, customizable dashboards, and advanced RBAC capabilities.
- Answer questions about your security posture with Generative-AI powered Natural Language search
- Generate compliance reports on risks and issues
- Observe trends on exposure – are risks being mitigated and improving overall security posture
SURFACE ISSUES
Communications And Connectivity
Visualize and map asset communications internally to other assets, and to the Internet. Surface communications and connectivity non-compliance such as:
- Assets located in the wrong VLAN
- Users with access to unapproved assets
- Assets communicating to the Internet
SECURITY HYGIENE
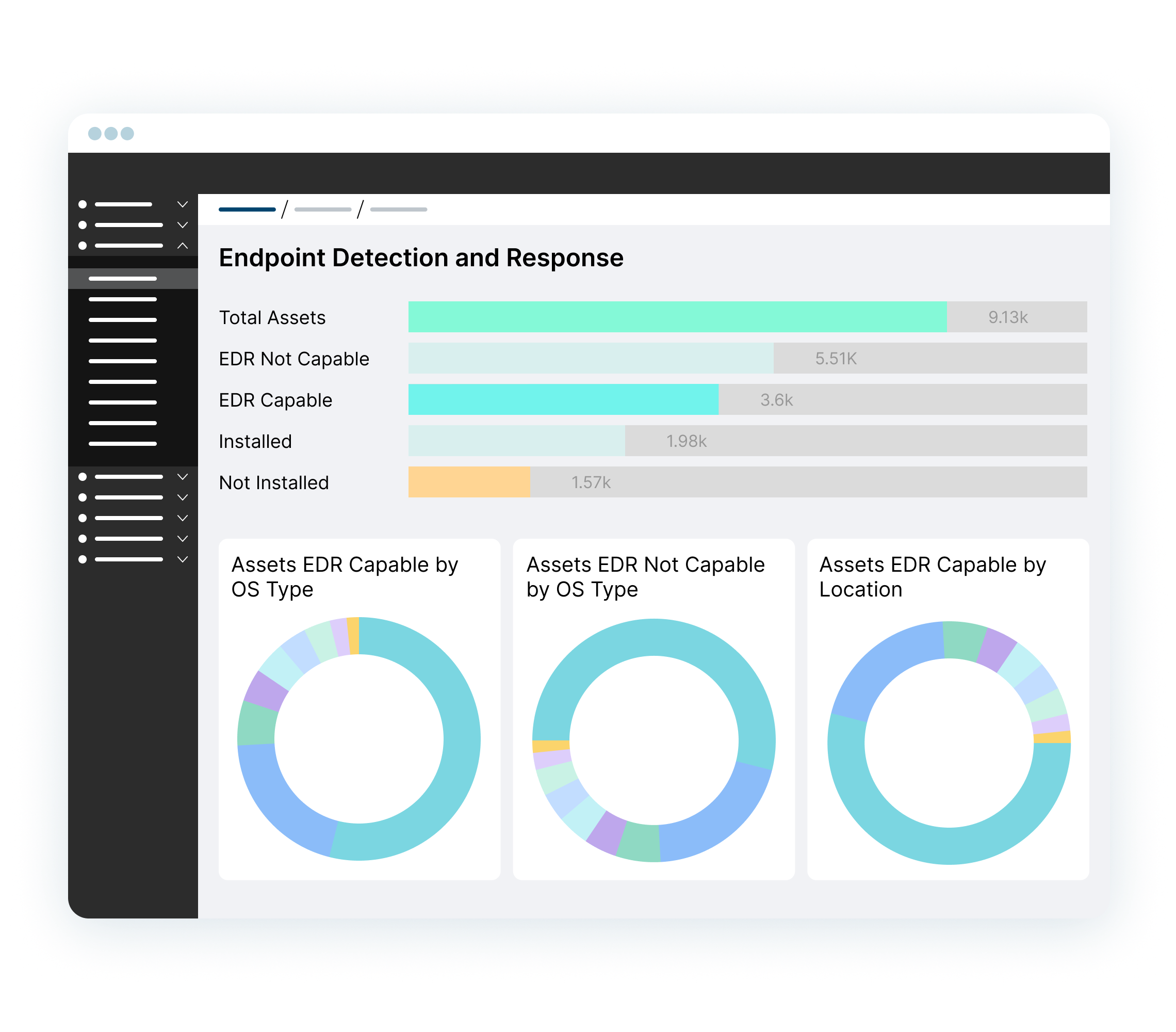
Improve Security Hygiene
Ordr’s powerful mapping and correlation engine align technical and business priorities, reducing alert fatigue, identifying security gaps, delivering a prioritized list of top risks. This ensures teams know when
- endpoints are missing critical security controls like EDR or MDM
- assets banned by the Federal Government
- assets are running out-of-date software
- assets have weak passwords
- when misconfigurations create security gaps
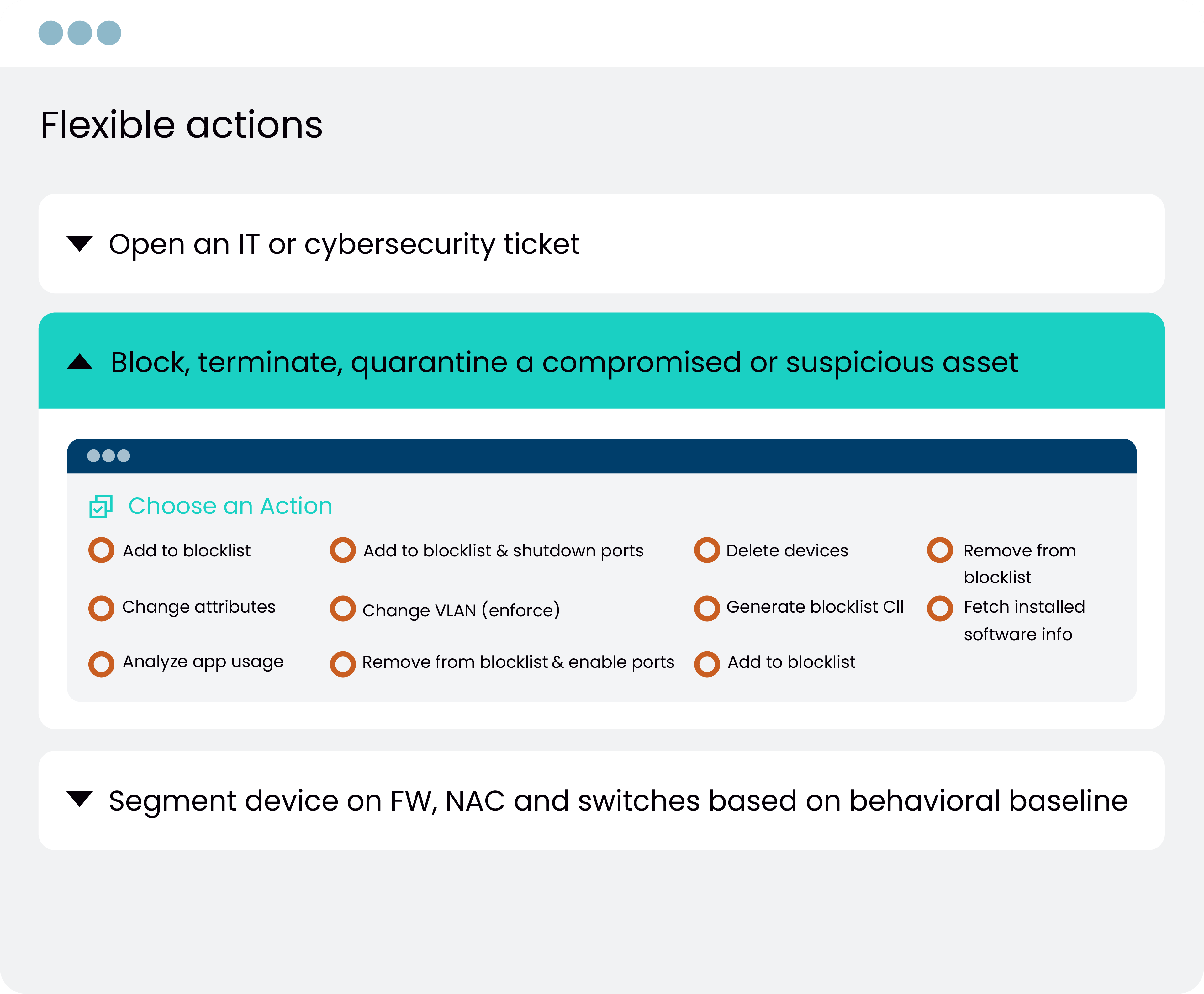
AUTOMATE REMEDIATION WORKFLOWS
Accelerate Remediation and Improve Collaboration
Share deep asset context with SIEM/SOC, create ITSM tickets, facilitating faster and more informed incident response. Utilize automated workflows using ITSM, SIEM, and SOC integrations. Enrich your IT tools with the most comprehensive, accurate, and trusted insights for all assets.