When it comes to file compression, 7-Zip is one of the most widely trusted tools in the world. Whether for personal use or enterprise applications, it has become a go-to for handling large amounts of data efficiently. But even trusted tools aren’t immune to vulnerabilities.
CVE-2024-11477 has turned 7-Zip into an entry point for attackers. This critical flaw, discovered in the Zstandard decompression implementation, allows remote attackers to execute arbitrary code. For organizations relying on 7-Zip across distributed systems, the implications are significant — this isn’t just about fixing a bug; it’s about addressing a critical risk in your environment before it becomes a security breach.
Understanding CVE-2024-11477
The vulnerability exists in all versions of 7-Zip prior to 24.07 and stems from improper validation of user-supplied data during Zstandard decompression. An integer underflow occurs before writing to memory, creating the potential for remote code execution. Classified as a high-severity issue with a CVSS score of 7.8, this vulnerability requires immediate attention, especially in environments where 7-Zip is widely deployed.
What makes CVE-2024-11477 particularly dangerous is its ease of exploitation. Attackers can craft a malicious archive that triggers the vulnerability upon decompression, turning a routine file-handling task into a serious threat. Without automated updates in 7-Zip, organizations must manually patch affected systems, adding another layer of complexity.
A Familiar Pattern: Vulnerabilities in Trusted Tools
This isn’t the first time a critical vulnerability has been uncovered in 7-Zip. Previous flaws, like CVE-2022-29072 and CVE-2023-31102, demonstrate a recurring challenge: securing legacy codebases while maintaining usability and performance. These vulnerabilities underscore the importance of proactive risk management, especially in environments where compressed files are part of critical workflows.
For instance, in healthcare, outdated software can put sensitive patient records at risk. In finance, it might expose transaction histories. In every sector, these vulnerabilities highlight the tension between operational efficiency and security.
How ORDR Secures Against CVE-2024-11477
Addressing CVE-2024-11477 starts with figuring out where the vulnerable versions of 7-Zip live in your environment. That’s already a tough challenge when enterprise assets are managed by so many different tools—and let’s be honest, some devices might not be tracked at all.
This is where ORDR shines. Identifying assets, uncovering vulnerabilities, prioritizing risks, and managing remediation are our core expertise. For our customers, this is how you can use the ORDRAI Asset Intelligence Platform, including ORDRAI CAASM+ and ORDRAI Protect, to tackle CVE-2024-11477 or similar vulnerabilities step by step. And if you’re new to ORDR, these insights will help you understand how to get ahead of vulnerabilities like this.
Comprehensive Asset Inventory
ORDR’s products integrates with existing infrastructure to provide a detailed inventory of software and devices. Using a feature called the ORDR Software Inventory Collector (OSIC), we can quickly identify instances of vulnerable 7-Zip versions without requiring manual scans.
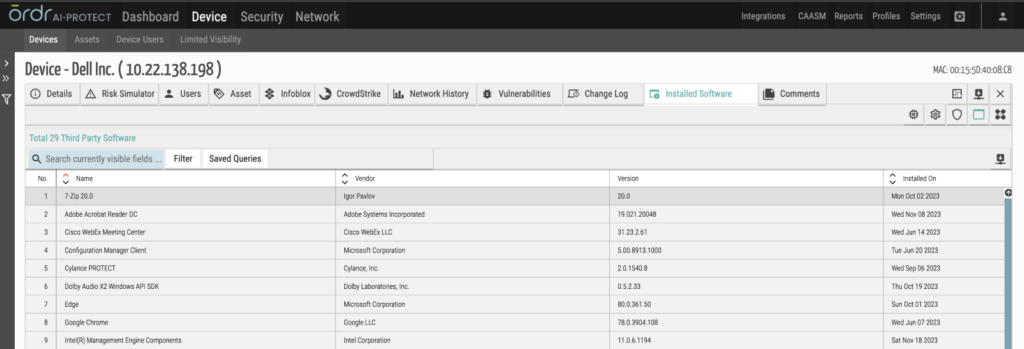
ORDRAI Protect: Installed software details for a device (Figure 1).
ORDR’s inventory view, available via CAASM, allows for an easy lookup of installed software by navigating through “Cyber Assets -> Installed Software.” This streamlined process provides granular details, including version history and installation timestamps.
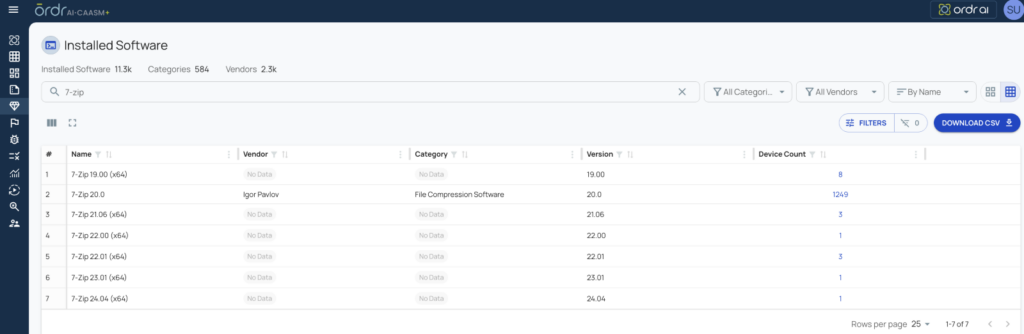
ORDRAI CAASM+: Easy lookup via “Cyber Assets -> Installed Software” page (Figure 2).
Real-Time Vulnerability Detection
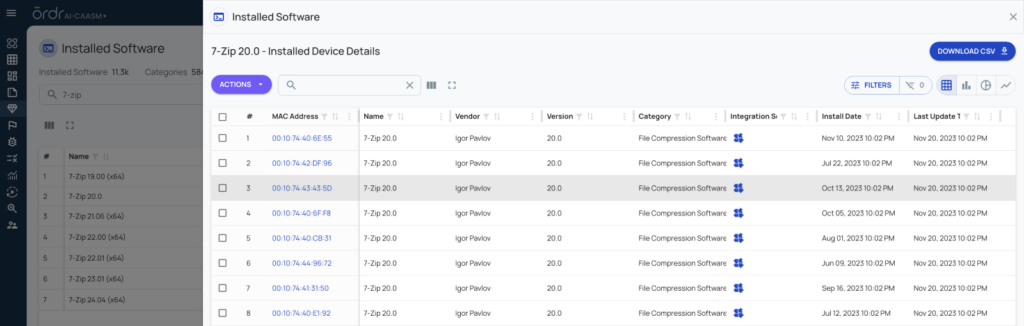
One of our Platform’s most powerful features is its natural language processing (NLP) search capability, which lets security teams instantly locate vulnerable 7-Zip instances. By simply typing a query, users can identify the presence of affected versions and prioritize remediation tasks with ease.
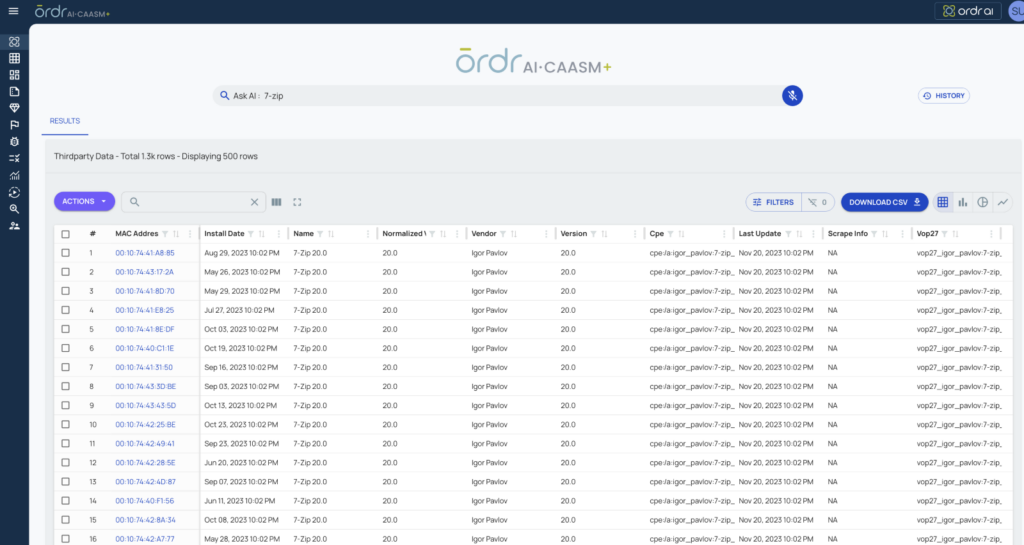
ORDRAI CAASM+: NLP search for instant look up for presence of 7-Zip with versions (Figure 3).
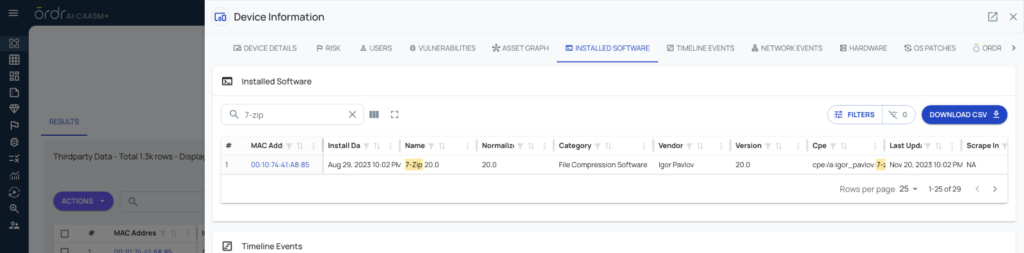
ORDR also enables the creation of custom widgets that allow for continuous monitoring of 7-Zip vulnerabilities. These widgets provide a real-time snapshot of at-risk devices and simplify tracking as updates are deployed across the environment.
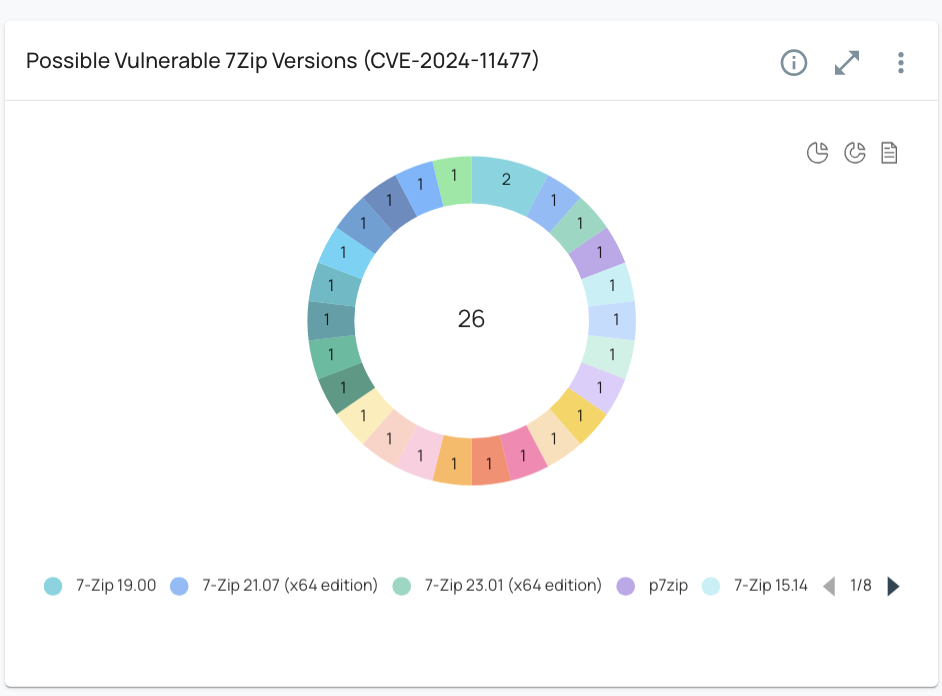
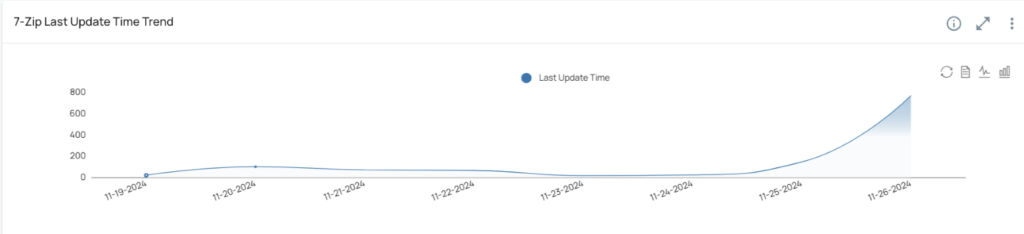
Sample widgets that can be added to track the presence of 7-Zip using ORDRAI CAASM+’s query builder (Figure 4).
Accelerated Remediation
Time is critical when addressing vulnerabilities like CVE-2024-11477. ORDR’s platform accelerates time-to-remediation by integrating with popular messaging, collaboration, and ticketing systems. This allows teams to assign patching tasks, track progress, and manage updates without disrupting workflows.
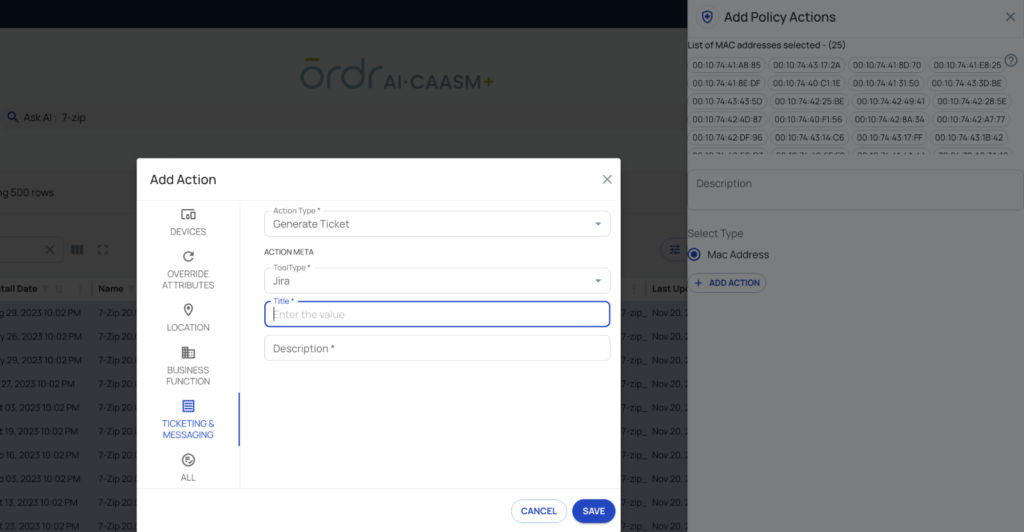
ORDRAI CAASM+: Admins can choose from a wide variety of actions to create quick remediation workflows (figure 5).
Proactive Risk Monitoring
In addition to detecting vulnerabilities, our platform baselines traffic patterns and monitors for anomalies. This capability allows security teams to identify unusual behavior linked to vulnerabilities like CVE-2024-11477, ensuring proactive protection.
By combining these insights with its comprehensive asset inventory, real-time detection, and integration capabilities, we enable organizations to minimize risk and stay ahead of potential threats.
What You Can Do Today to mitigate CVE-2024-1147
Mitigating CVE-2024-11477 begins with patching affected versions of 7-Zip. Upgrading to version 24.07 is critical, and tools like ORDRAI CAASM+ and ORDRAI Protect can streamline this process. Beyond updates, organizations should:
- Audit their software inventory to ensure compliance.
- Monitor for unusual activity on devices using 7-Zip.
- Establish regular patching protocols to stay ahead of future vulnerabilities.
The discovery of CVE-2024-11477 underscores the importance of a proactive approach to cybersecurity. It’s not just about reacting to vulnerabilities — it’s about anticipating them. Our Platform equips security teams with the insights and tools needed to stay ahead, turning potential weaknesses into opportunities for improvement.
The path to better security begins with visibility. Learn more about ORDRAI and schedule time to chat with one of our experts to learn more.
As more details become available, it’s crucial to stay informed through official sources like the CVE database, Zero Day Initiative, and SUSE Security. uick remeidation workflows (figure 5).

Interested in
Learning More?
Subscribe today to stay informed and get
regular updates from ORDR Cloud



