As enterprise environments become more complex, the responsibilities of Incident Response (IR) teams have become equally complex. With the rapid growth of IoT, OT, IoMT, container, ephemeral cloud, and various other asset types, the task of identifying assets and effectively responding to cybersecurity incidents has become more difficult and time-consuming than ever. OrdrAI CAASM+ provides a centralized platform for cyber asset attack surface management (CAASM) with accurate asset data and actionable business insights for IR teams to protect their assets and accelerate response times during incidents.
Preparation: Handling an incident more effectively with complete, accurate asset inventory and in-depth data
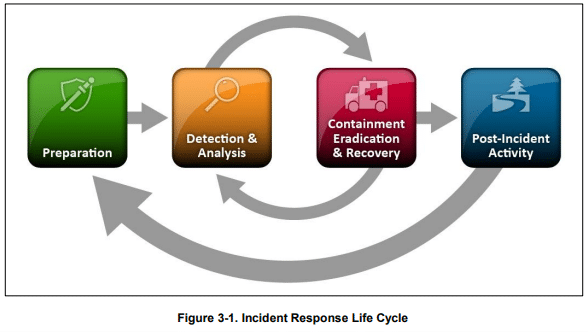
NIST 800-61 R2, Computer Security Incident Handling Guide, outlines a framework for incident response. OrdrAI CAASM+ empowers IR teams to effectively prepare for the “preparation phase” by equipping them with a complete, accurate, and centralized source of asset inventory and data. This eliminates the need for manual data gathering and correlation from siloed sources.
Ordr’s methodology combines 170+ IT and security ecosystem integrations and proprietary discovery technology with AI/ML correlation and classification. The result is a complete, deduplicated inventory of all assets, including devices (IT, IoT, IoMT, OT), SaaS, applications, cloud, and users. This approach also delivers deep asset context, including device owners, software, security tool posture, assigned policies, open ports, running services, vulnerabilities, and more.
With this asset context and data, IR teams can efficiently respond to incidents, reducing mean-time-to-remediation (MTTR). Additionally, Ordr’s proprietary AI/ML asset profiling and classification provides teams with a visual representation of all devices, including IoT and OT. This is invaluable for on-site personnel seeking to locate—and potentially disconnect—a device from the network.

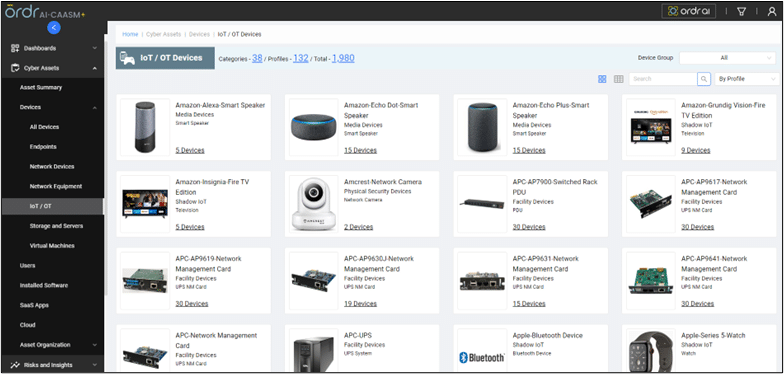
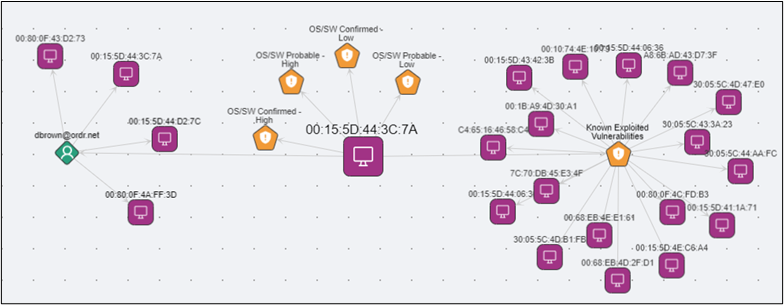
Ordr also provides teams with user-to-device relationships, alongside vulnerabilities, SaaS applications, installed software, and more, through the OrdrAI Asset Graph.
In the screenshot below, you can quickly see that user “dbrown” has been active on four devices. Focusing on a specific device, we see the known exploited vulnerabilities (KEV) associated with it. We can further extend this analysis to understand every device in the environment affected by the same known exploitation. With this information, IR teams can efficiently assess, prioritize, and assign remediation actions to the most critical devices.
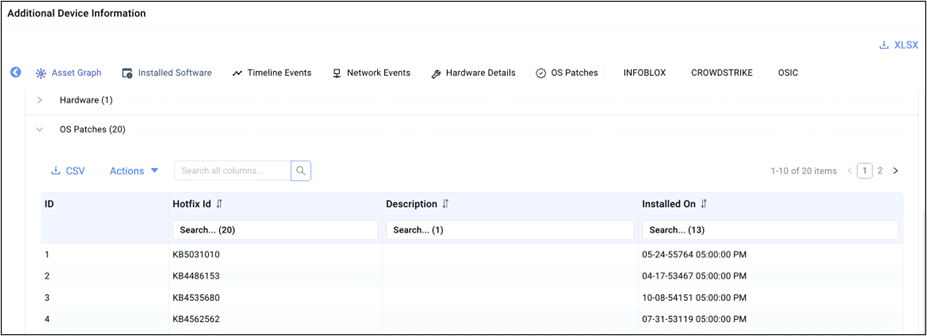
Ordr uses a variety of techniques to identify vulnerabilities, ensuring organizations achieve a comprehensive understanding of all vulnerabilities in their network. For assets unable to undergo scans or those not regularly updated, Ordr utilizes our Software Inventory Collector, a lightweight script that detects vulnerabilities based on KB/HF correlation instead of scanning the asset directly.
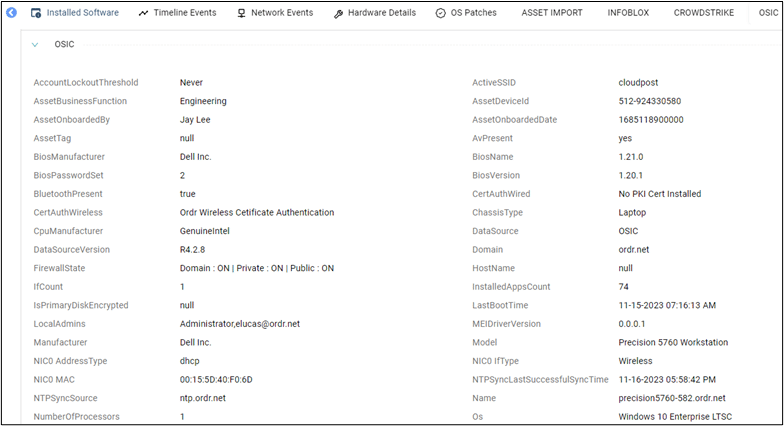
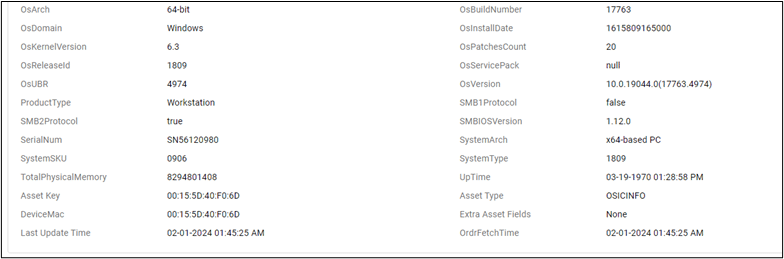
Ordr utilizes asset data (including things like make, model, manufacturer, and operating system) collected through passive and active techniques, to identify vulnerabilities associated with assets running outdated operating systems.
Detection & Analysis: Optimizing incident response with comprehensive asset data and business insights with GenAI Search
Traditional methods and initial analysis of an incident may only identify suspicious activity from a specific IP or user. Ordr’s ability to understand and visualize asset relationships is crucial for incident response teams to easily access asset data and deliver the context needed to efficiently contain and recover from an incident.
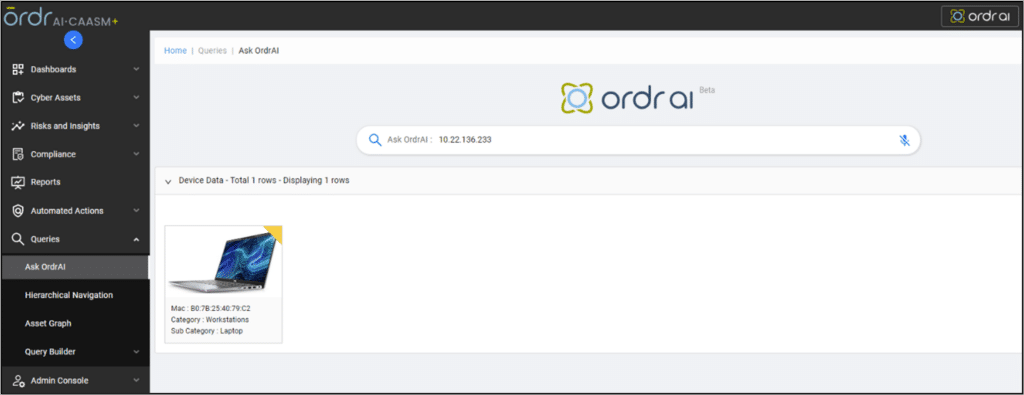
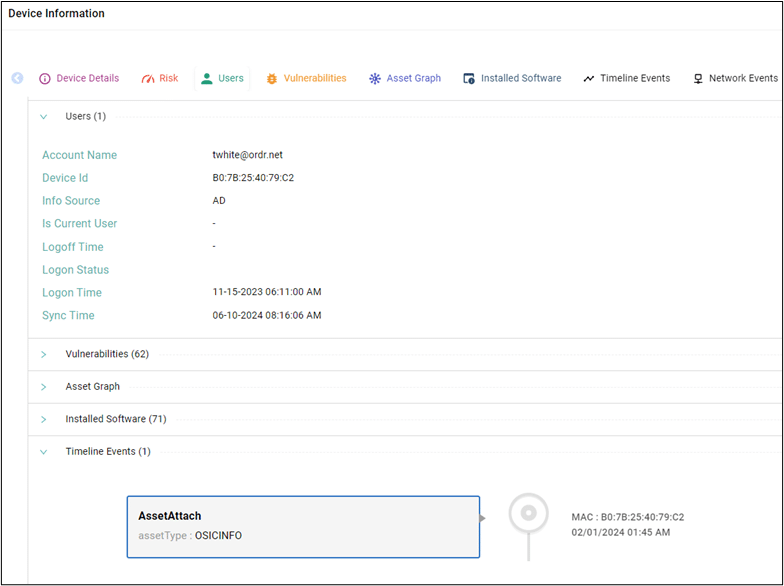
Ordr’s Generative AI search enables security and IR teams to quickly initiate their investigation with a single data point. For example, in the screenshot below, the team begins their investigation by inputting the flagged IP address associated with suspicious activity. After inputting the IP address, teams gain access to the necessary data for analysis and incident containment, including the make and model of the device (Dell Latitude 7420 laptop), device user, and a timeline of events.
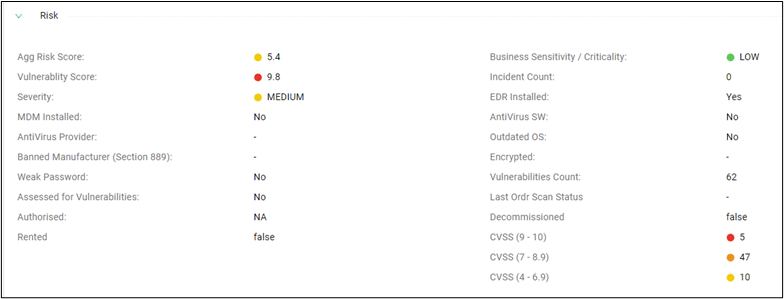
Additionally, OrdrAI CAASM+ provides an out-of-the-box risk analysis, including customizable risk and vulnerability scores, assessment of device compatibility with endpoint detection and response (EDR) and mobile device management (MDM) technologies, and more. This risk analysis empowers teams with the context needed to prioritize vulnerabilities based on the criticality of assets to the business, enabling them to concentrate on addressing the most significant risks.
Contain, Eradicate & Recover: Improve Time-to-Remediation with OrdrAI CAASM+
OrdrAI CAASM+ is a game changer for incident response teams, providing them with the data and business insights needed for prompt and decisive action throughout NIST’s incident handling process. Additionally, OrdrAI CAASM+ empowers teams with streamlined workflows that strengthen their incident response capabilities while reducing response times. Ordr also provides a framework for remediation with multiple enforcement options, including:
- Add to Blocklist
- Add to Blocklist & Shutdown Ports
- Generate Blocklist CLI
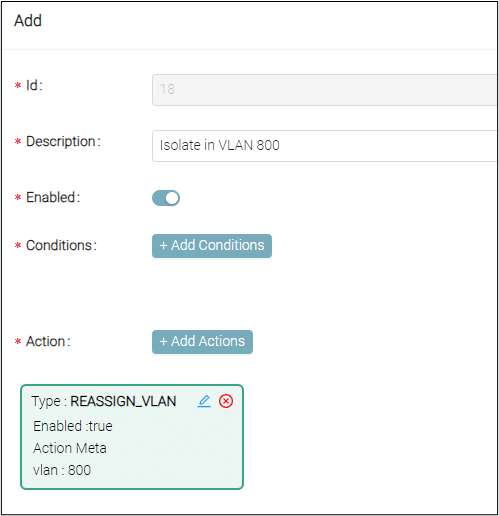
- Change VLAN (enforce)
- Initiate Scan
- Analyze App Usage
- Open a Ticket
- Send SMS
- Send Email
Furthermore, Ordr integrates with industry-leading security solutions to share risk and vulnerability data and automate remediation. Recommended data sources for Ordr to integrate with to accelerate incident response include:
- EDR
- MDM
- CMDB
- Cloud Assets
- Vulnerability Assessment Systems
- Ordr Discovery Engine
Check out this video for a deeper dive, or you can also learn how OrdrAI CAASM+ can help your security and IR teams reduce their response times with a live demo.
Thanks for joining us for another blog in our series on cyber asset and attack surface management use cases. We will continue to explore more asset and attack surface management use cases in the coming weeks and discuss how Ordr addresses them.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud