Medical Device Security Challenges
Internet of medical things (IOMT) create tremendous opportunities for healthcare providers to monitor and treat patients more effectively. But they also create opportunities for cyber threat actors.
The scale and variety of medical devices create a large and complex attack surface:
- IoMT devices have minimal internal computing resources, with limited ability to install antivirus, encryption and other forms of protection.
- Medical devices are not always designed with security in mind
- Most healthcare professionals who manage medical devices are not cybersecurity experts
- Medical devices often run outdated operating systems because of the longer lifecycles compared to IT systems.
- Due to their sensitive medical functions, medical devices cannot be discovered via traditional approaches or undergo vulnerability scans
At the same time, cyberattacks especially ransomware, are actively targeting healthcare delivery organizations. Effective delivery of care depends on the security and uptime of these medical devices.
Medical device security solutions are meant to address these challenges.
What Is Healthcare and Medical Device Security?
While IOMT devices are a critical part of hospital operations, there are many other assets and devices in the network. Security teams need to consider not only the security of medical devices but every other IOT and OT assets that play a role in hospital operations. This can include elevator control systems, HVAC systems, lighting devices, ATMs, video surveillance cameras and vending machines.
Clinical engineering, and Healthcare Technology management (HTM) will benefit from granular medical device inventory and context as well. Medical device visibility can enrich CMMS systems, make it easier to locate assets for patching, and optimize operations.
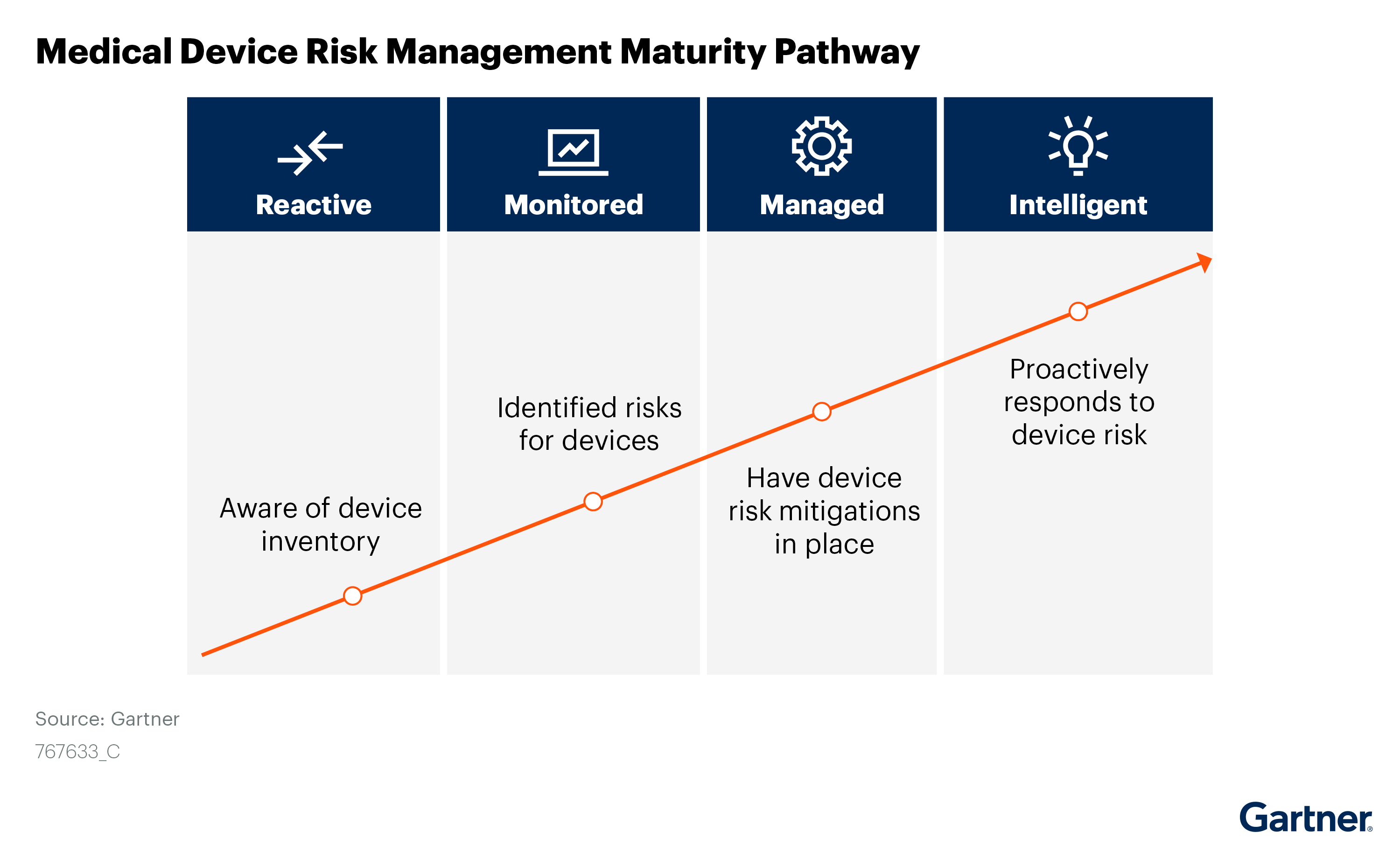
Considerations For Securing Medical, IOT and OT Devices
There are many factors to consider when selecting a healthcare and medical device security solution:
- What teams are involved? Ensure cybersecurity teams are leading medical device security initiatives
- Is the discovery and security of medical and IOT devices done in a way that doesn’t impact sensitive operations?
- Does the vendor support visibility and security for all assets in the hospital including IT, IOMT, IOT and OT?
- Can the vendor integrate with key healthcare tools like CMMS and ITSM
- Can the vendor detect all types of known and unknown threats targeting healthcare assets?
- What automation is available to accelerate incident response?
- Can the vendor enable segmentation of mission-critical assets?