Cisco
Ordr’s deep integrations across the Cisco portfolio adds visibility and insights needed to manage and secure the wide range of connected devices in today’s environments.
See, know and secure every managed and unmanaged asset, from IT, IoT, IoMT, OT, to users, applications, SaaS and cloud, in any environment.
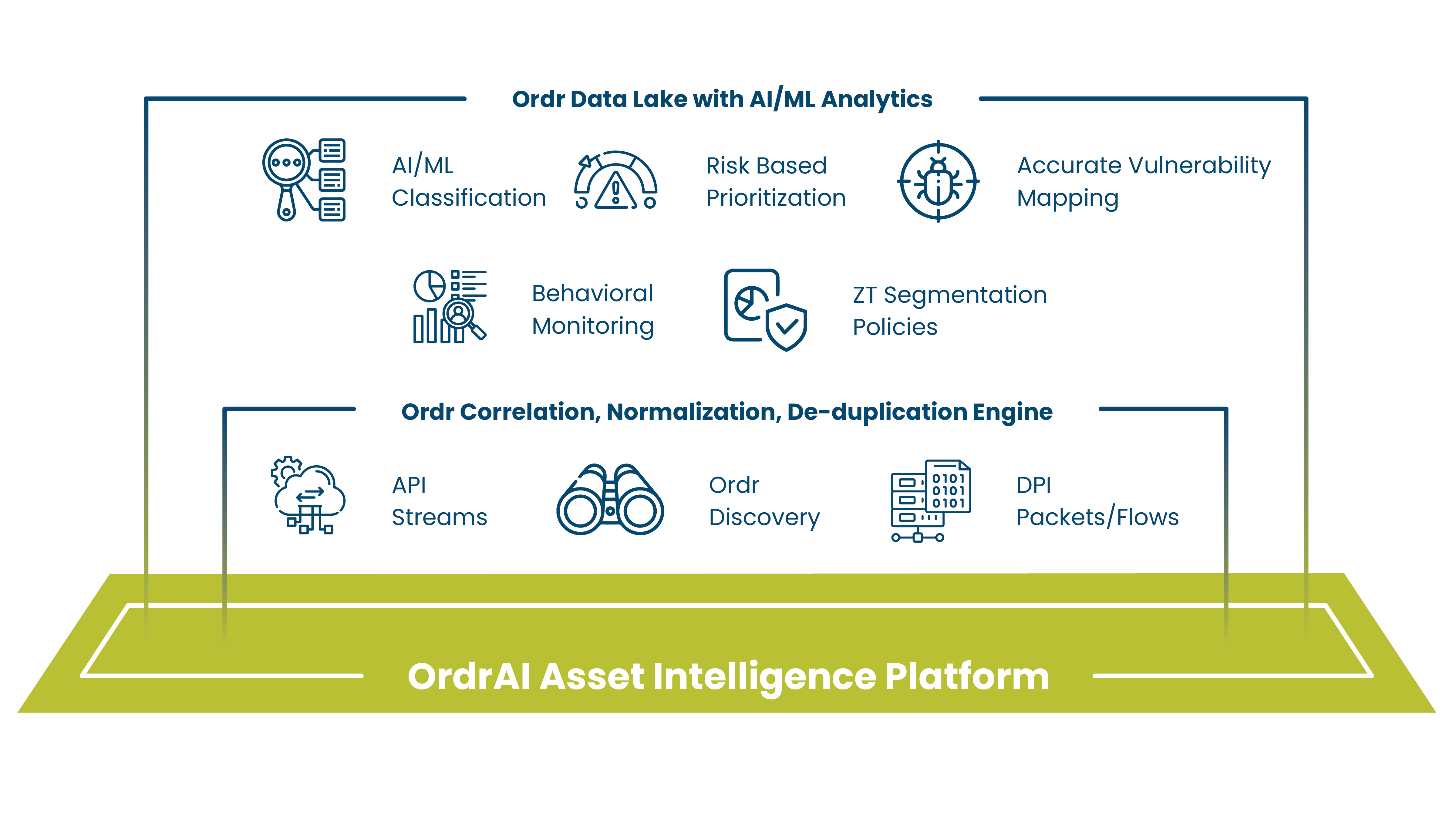
The OrdrAI Asset Intelligence Platform has been designed to be modular, and enable a building block approach to address your cybersecurity maturity – from asset visiblity all the way to Zero Trust.
Gain visibility for your entire asset attack surface. Prioritize vulnerabilities, identify gaps and reduce your exposure.
LEARN MOREAdvanced threat detection, behavioral intelligence and segmentation for mission-critical IT, IOT, OT, IOMT assets.
LEARN MOREAddress your entire asset management journey
EXPLORE WHY ORDRAsset Visibility and Management
Security Issues and Coverage Gaps
Vulnerability Prioritization and Management
Threat And Anomaly Detection
Segmentation and NAC Acceleration
Regulatory Frameworks
Enrich CMDB and security operations with real-time, automated hardware and software inventory, granular asset details, connectivity, device flows and more.
LEARN MORE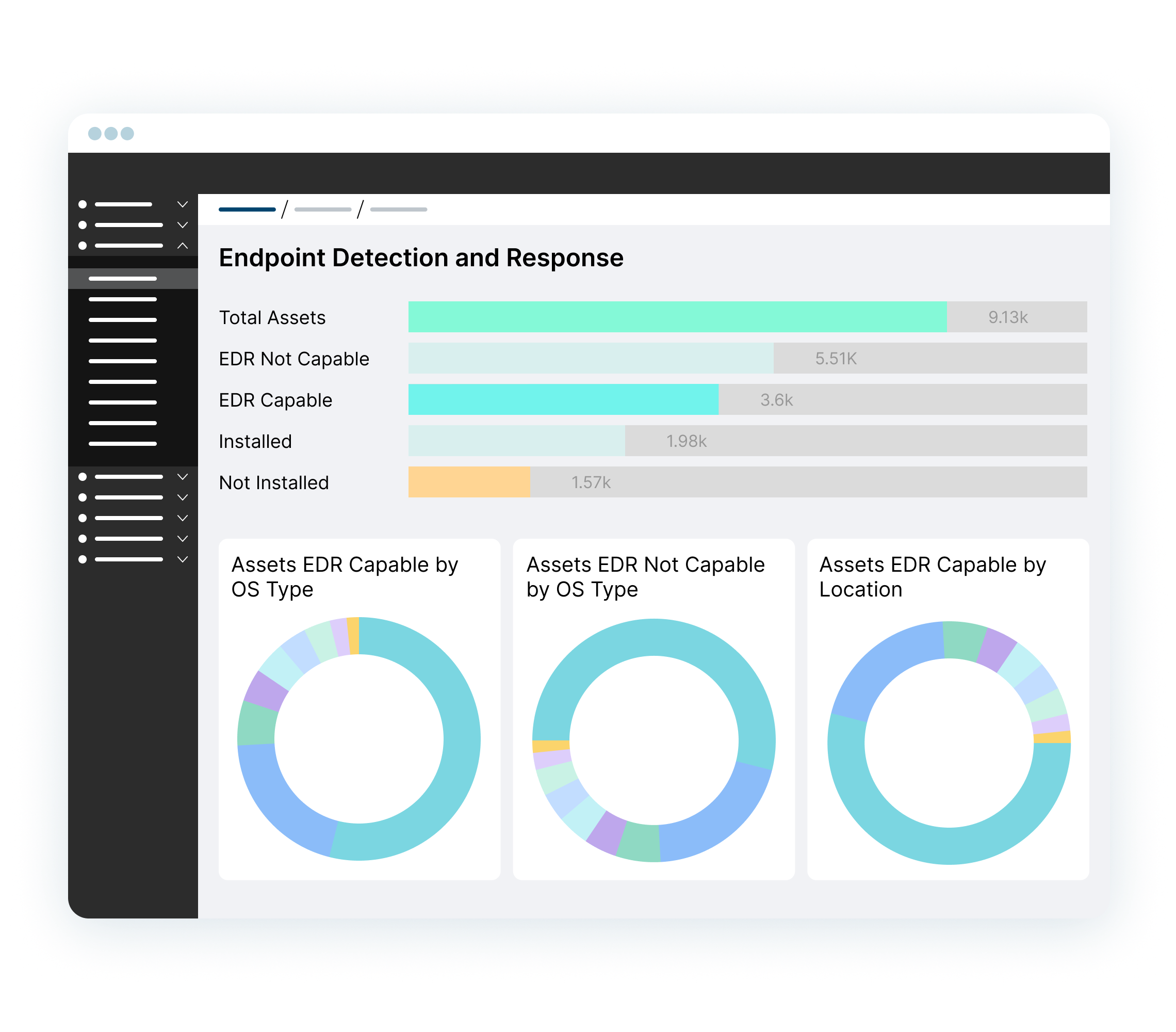
Improve your security hygiene by surfacing security gaps such as devices with outdated OS, or missing EDR/MDM agents.
LEARN MOREReduce risks by prioritizing vulnerabilities based on organizational impact. Automate remediation, assign to the right owner and track progress.
LEARN MOREReduce dwell time. Detect and quarantine devices with exploits, risky communications, anomalous behavior.
LEARN MOREAccelerate NAC projects with asset context and automated policies. Implement Zero Trust segmentation for mission-critical devices.
LEARN MORE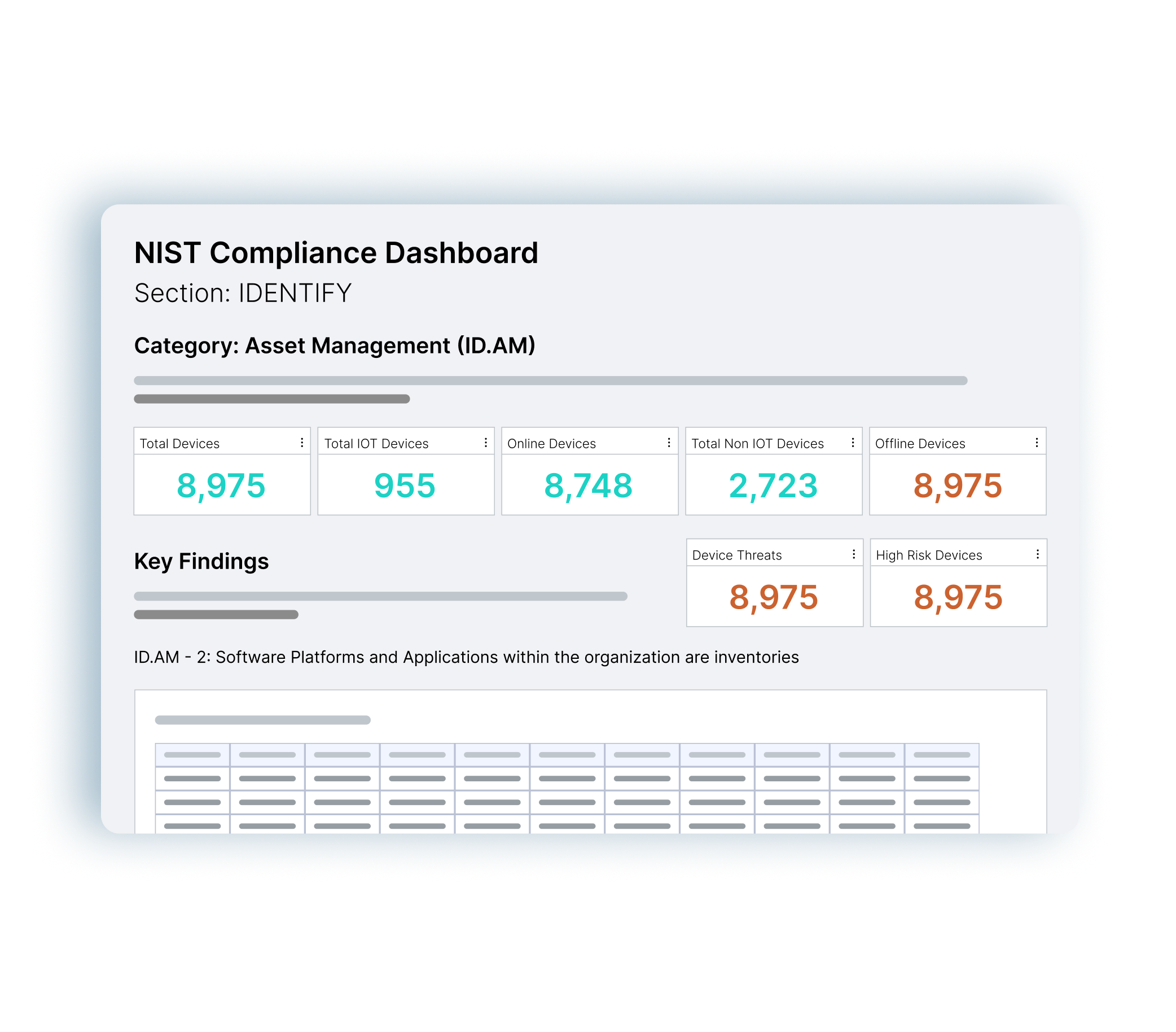
Simplify NIST, CIS Controls, CMMC, Cyber Essentials and NHS DSP Toolkit audits with asset data and reporting at your fingertips.
LEARN MORESeamlessly connect to hundreds of networking and security tools via API. Enrich your security tools with Ordr asset data, and automate response and segmentation policies on firewalls, switches, NAC.
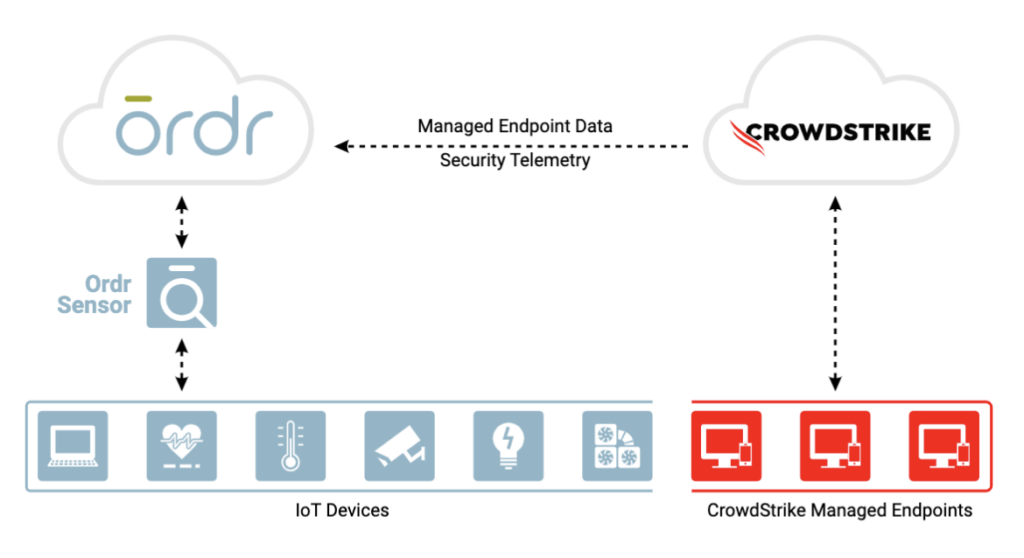
SEE ALL TECHNOLOGY PARTNERSIntegration between Ordr and CrowdStrike ensures the security of all managed and unmanaged devices with comprehensive device visibility, detailed vulnerability insights, an understanding of risk, and the ability to enforce policy to mitigate active threats and improve security across all connected devices
Ordr analyzes network flow data to automatically discover and classify every connected device, profile behavior, and identify active threats. Security telemetry from the CrowdStrike Falcon platform, is shared with Ordr to enhance device insights, and provide a centralized, deep understanding of each device and its associated risk. Ordr uses multiple factors to calculate risk for each device based on business context, asset criticality, vulnerabilities, and overall threat details. With additional device data from the Falcon platform, Ordr provides a highly accurate risk score for each device. By continuously synchronizing device risk scores with CrowdStrike’s enriched security data, Ordr enables teams with an up-to-date view of risk to help them focus on the most critical devices.
Gain complete device visibility
Minimize risk with better insights
Remediate faster
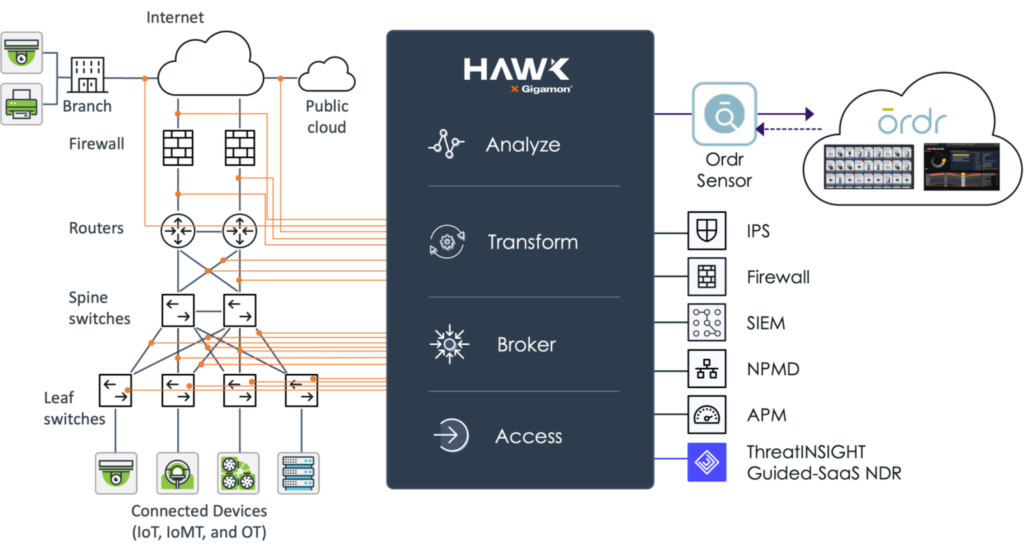
A basic tenet of network security and regulatory compliance is that “You cannot secure what you cannot see.” Gigamon and Ordr have teamed to deliver unsurpassed visibility and control into every thing connected to your network.
The Gigamon Visibility and Analytics Fabric (VAF) optimizes data collection of all north-south and east-west traffic across branch, campus, data center and cloud. Collected data is delivered to Ordr for analysis to ensure comprehensive device classification and visibility into all device communications. Integration with Gigamon VAF also eliminates concerns of SPAN security and potential impact to network infrastructure with “yet another SPAN port or session.”
By integrating with Gigamon VAF, customers can significantly reduce the number of Ordr sensors required to comprehensively discover and monitor every network-connected device, simplifying your network and security monitoring architecture.
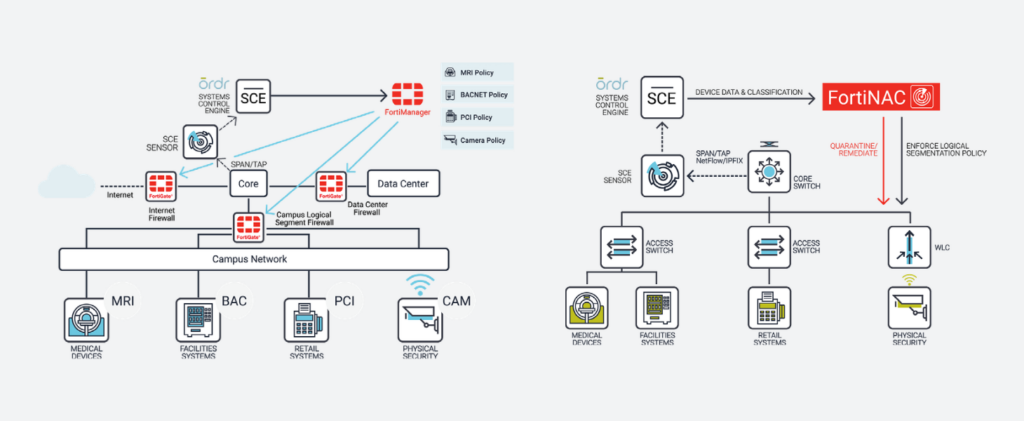
Fortinet and Ordr have partnered to deliver an industry-leading IoT and unmanaged device security solution by integrating FortiManager, FortiGate and FortiNAC with Ordr Systems Control Engine (SCE)
Automated Visibility and Security of All Connected Devices
Ordr SCE automatically creates a complete asset inventory, identifies and prioritizes asset risk, and tracks and risk-rates asset communications patterns. Ordr transmits this critical security context to Fortinet FortiGate, FortiManager, and FortiNAC, allowing administrators to create and apply firewall and NAC policies using business-relevant groups, classifications, and device names, while understanding the full risk profile and impact of each change. Ordr further reduces administrative costs by automatically updating asset groupings as devices join and leave the network, as well as by creating and transmitting security policies directly to FortiGate and FortiManager for enforcement.
With the integration, joint customers can now:
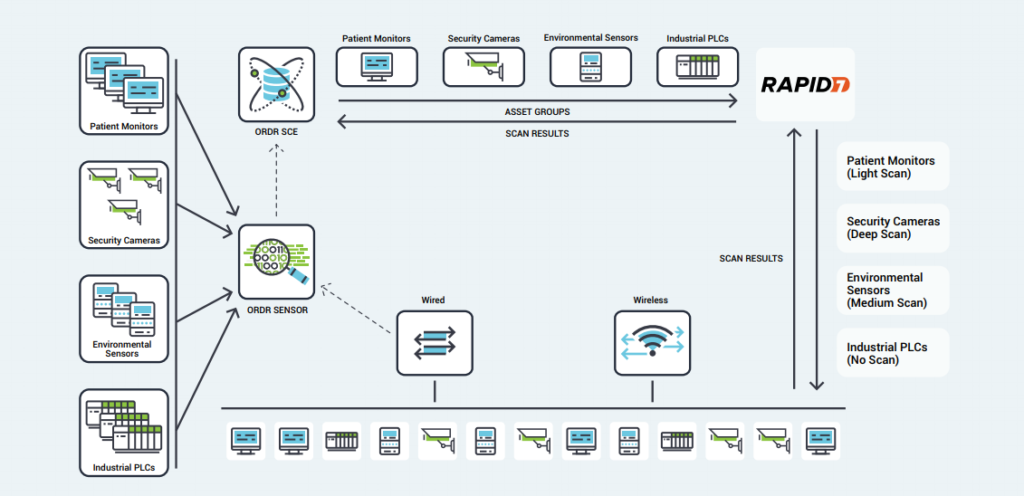
Ordr works with Rapid7 to seamlessly discover all connected assets including IoT, IoMT, and OT devices. The joint solution enables Rapid7 to perform the right scan at the right time regardless of the device type, location, criticality or role within the organization. Many vulnerable IoT/OT devices discovered by Rapid7 cannot be patched or updated. Ordr automates the application of compensating controls to safeguard these devices by sending protection policies directly to firewalls, switches, wireless, or NAC systems. Similarly, infected devices can be quickly isolated through existing network and security devices.
The integration with Ordr and Rapid7 InsightVM provide ongoing bi-directional synchronization for managing vulnerabilities with rich device context. Ordr discovers every connected device, profiles device behaviors and risks, and automates remediation responses. Rapid7 InsightVM provides visibility into the vulnerabilities and clarity on how those vulnerabilities translate into business risk. Combining Ordr’s unique device intelligence with Rapid7’s advanced vulnerability intelligence provides organizations with the ultimate solution to efficiently manage risks while reducing service disruption and time to remediate.
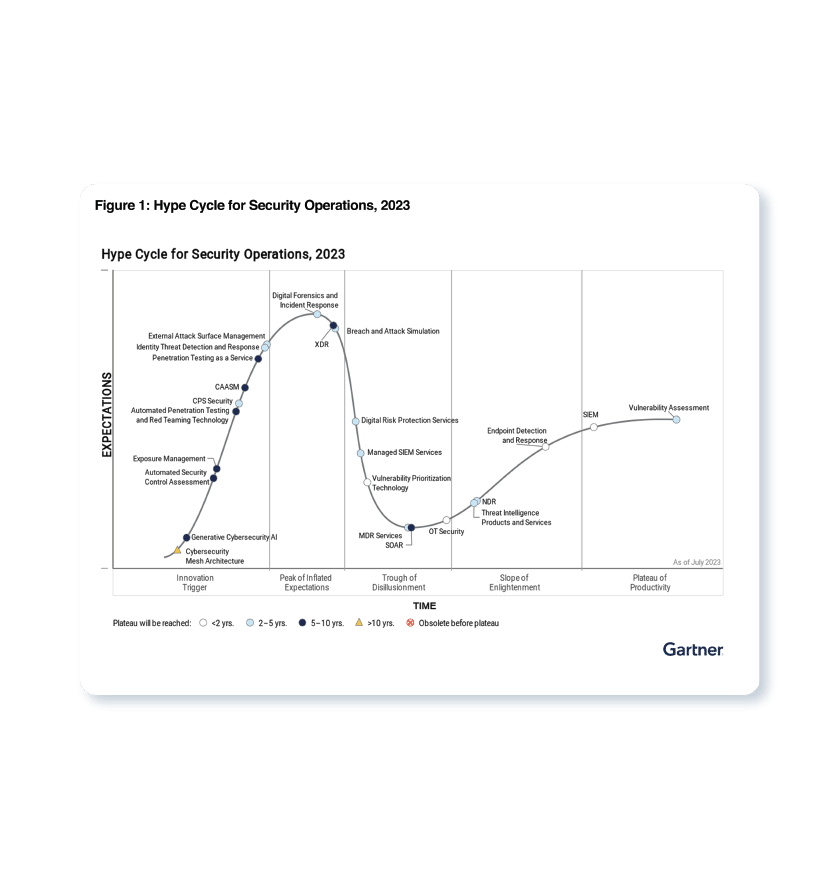
Download the report to learn more about how CAASM improves basic security hygiene by finding security controls gaps, security posture, and asset exposures across all digital assets.
DOWNLOAD