
ORDR AI Protect Platform Datasheet
Every decision is smarter because AI is behind it all.
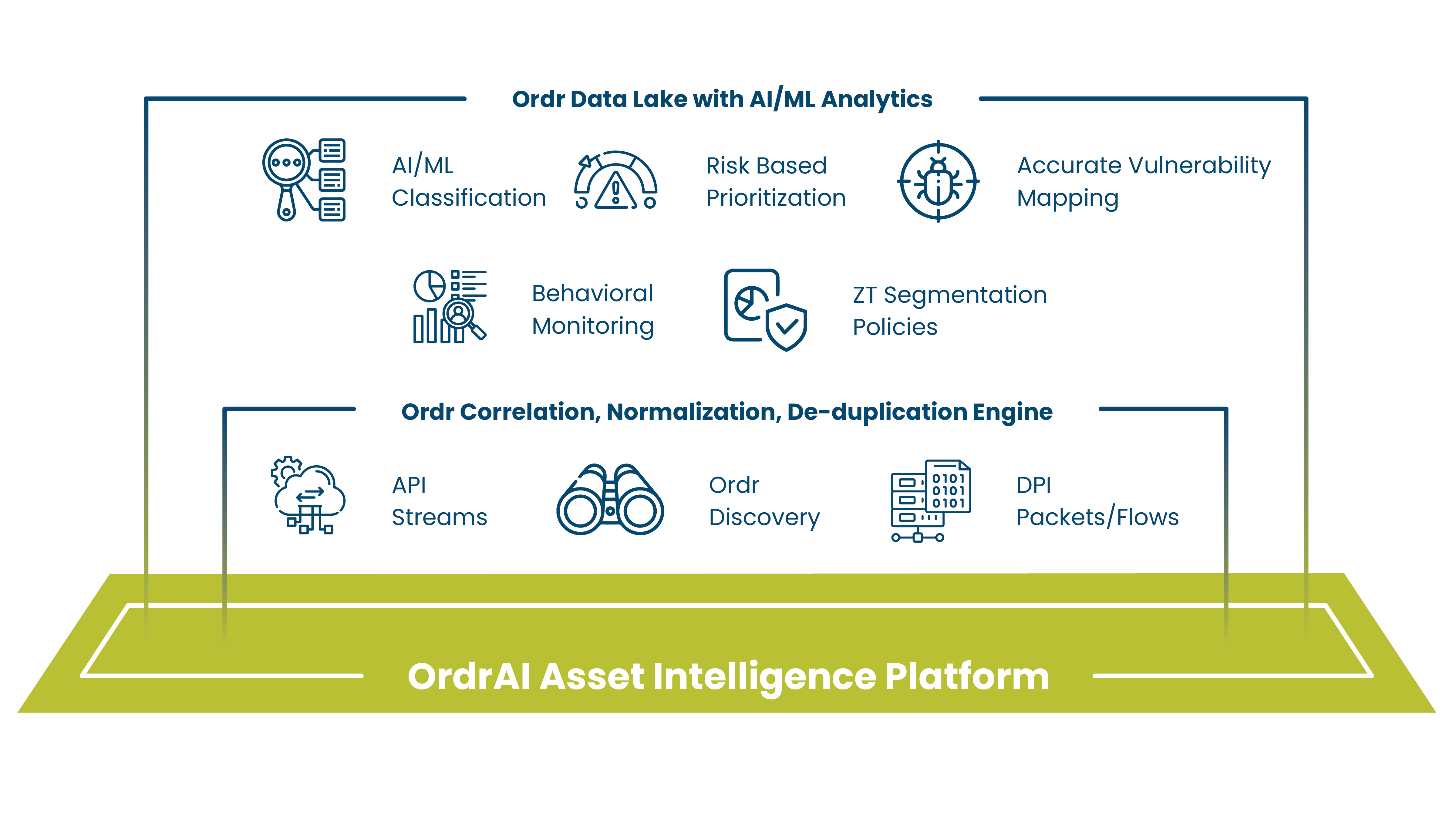
Discovery pulls from real signals — SNMP, DPI, APIs — to identify every asset. Then AI takes over, correlating hundreds of attributes to group devices based on what matters to your business: roles, ownership, function, and risk. Policies are simulated, compressed, and tailored to your infrastructure — no templates, no rewrites, just action that’s ready to enforce – instantly.
Use Cases
Contain ransomware. Isolate high-risk devices. Protect what matters—without taking critical systems offline. ORDR AI Protect segments your network with real-time context, automated policies, and continuous enforcement across switches, firewalls, and NACs. Purpose-built for IoT, OT, and IoMT environments where patching isn’t an option.
ORDR groups devices by function, behavior, VLAN, and risk — not just labels. That’s how it builds policies that reflect your real environment — and enforces them without gaps.
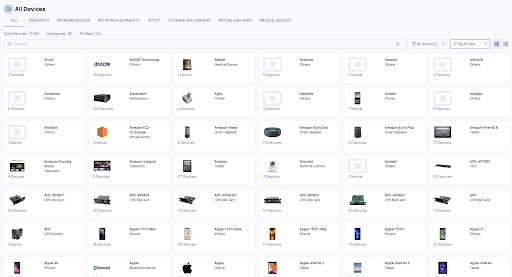
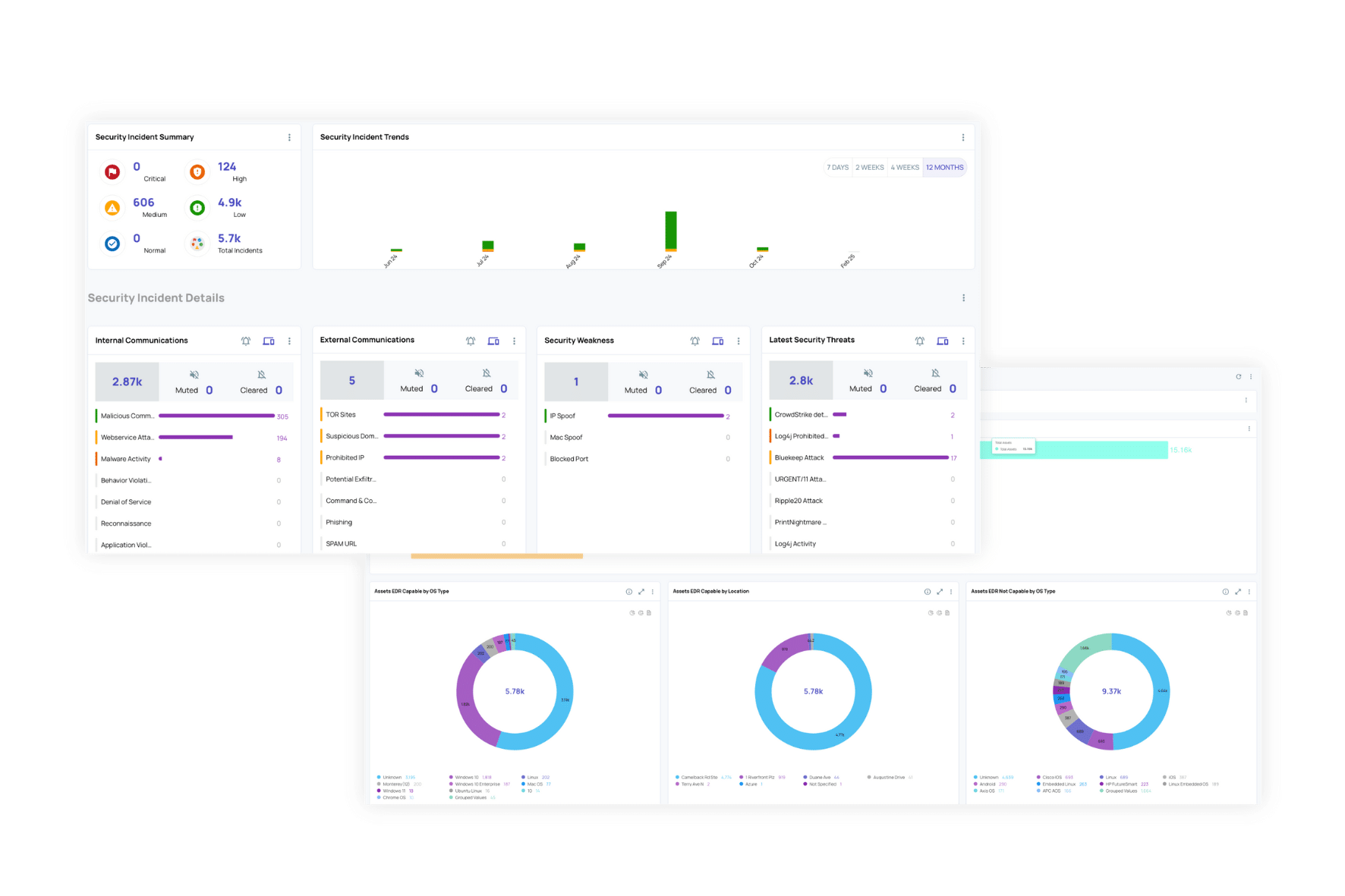
ORDR pinpoints blind spots in your network — from unmanaged devices to missing controls — and brings them to life in intuitive dashboards. So you can see, understand, and secure what others miss
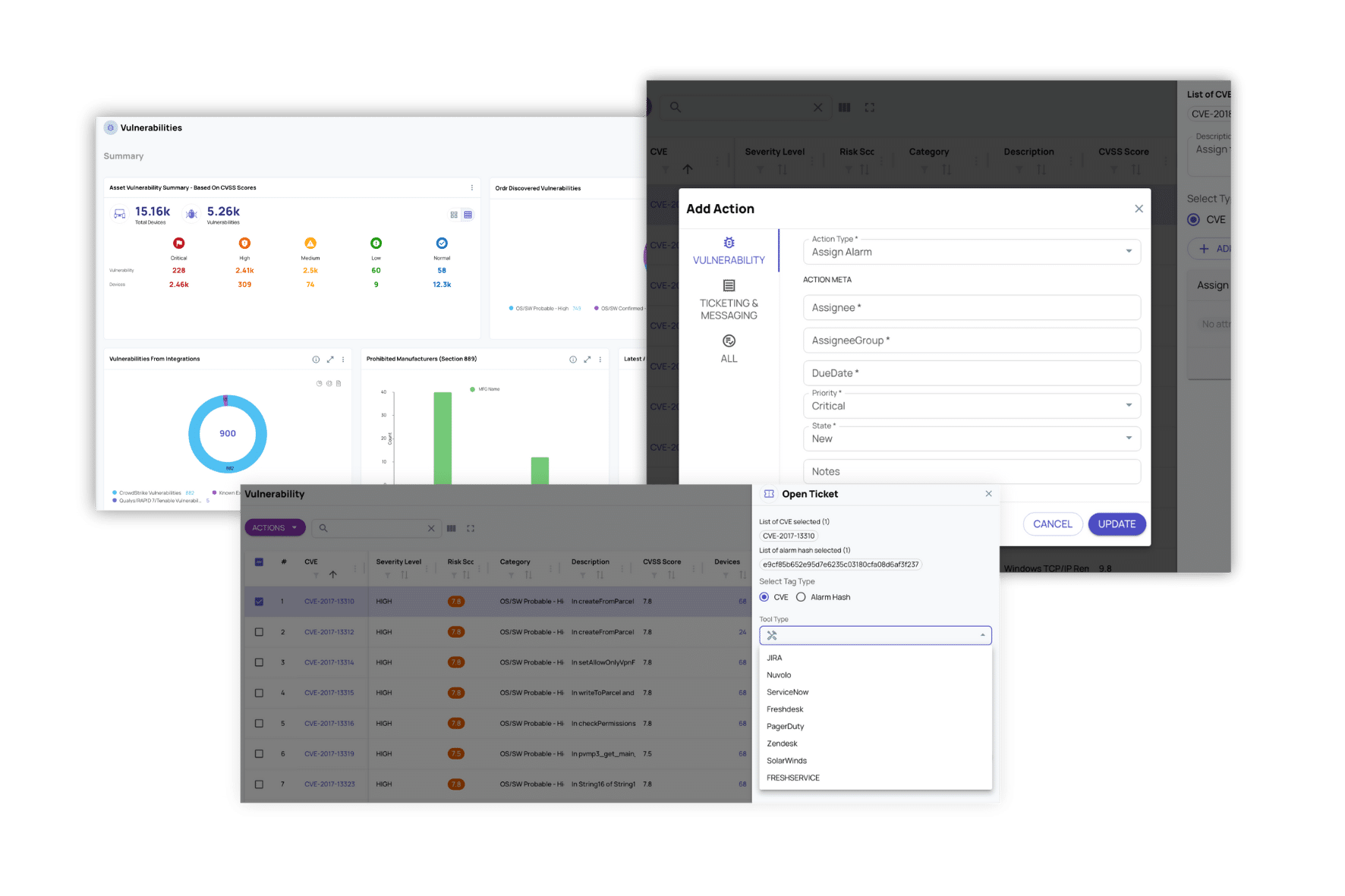
ORDR identifies vulnerabilities in context, ranks them by real risk, and maps them to enforcement — then integrates directly into your ticketing workflows to drive action faster.
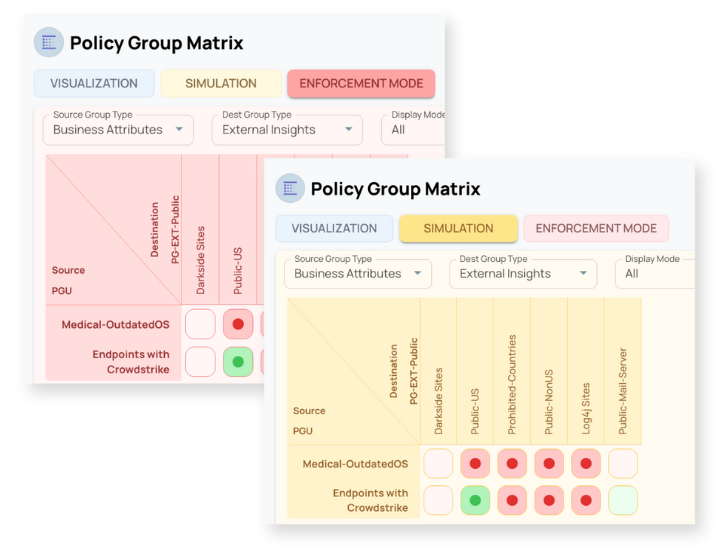
ORDR’s Matrix UI shows every connection — with AI-suggested policies and built-in simulation — so you see the impact before enforcing, and act with total confidence.
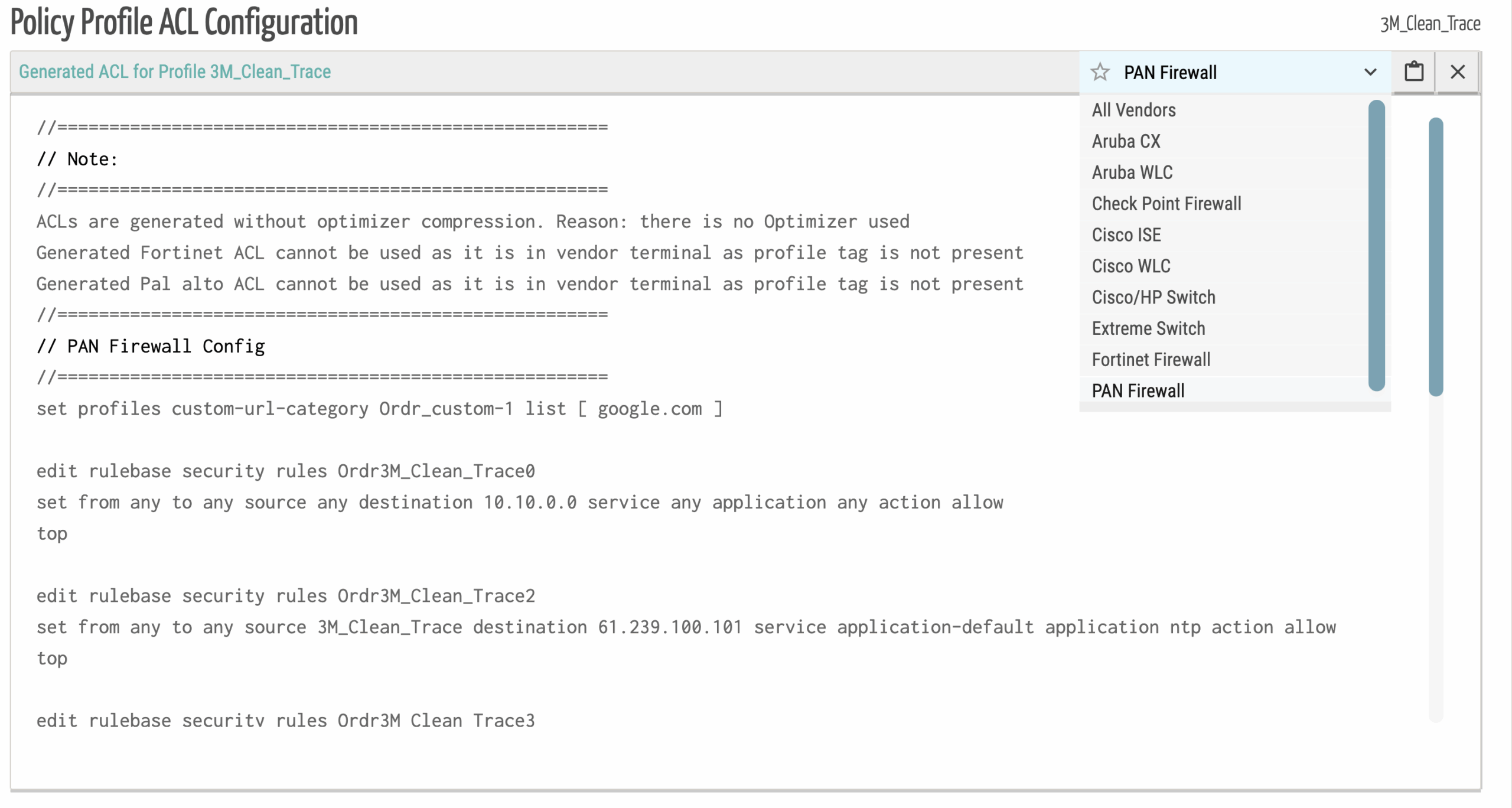
ORDR auto-generates least-privilege policies from real-traffic and behavior – then compresses and customizes them to fit your environment. No guesswork. No overhead. Just policies your switches can handle.
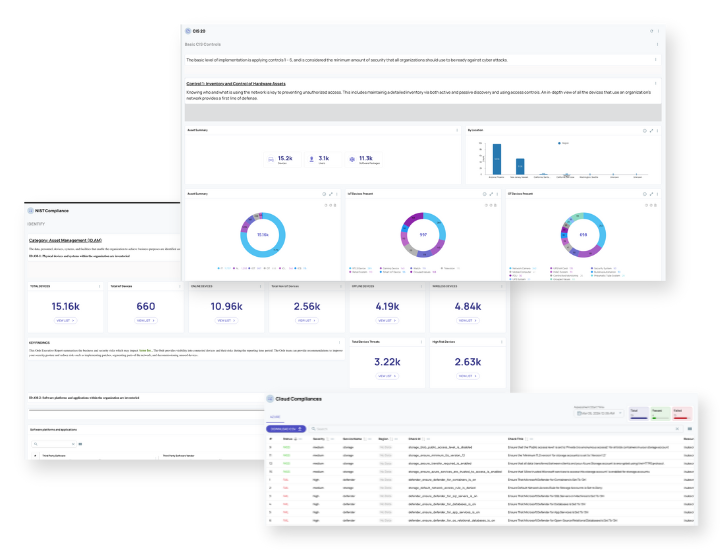
Whether NIST, CIS Controls, CMMC, Cyber Essentials, or NHS DSP, ORDR gives you the asset data and reporting you need — instantly, and effortlessly.