Search Results:
”Role of Huawei H19-431_V1.0 Exam Questions in Getting the Highest-Paid Job 💆 Search for { H19-431_V1.0 } and download exam materials for free through [ www.pdfvce.com ] 🏸Premium H19-431_V1.0 Files”
-
 BlogHow Ordr Customers Are Identifying Account Misuse Through Employee Access
BlogHow Ordr Customers Are Identifying Account Misuse Through Employee Access…off, and to which system. What specific resources were accessed. The amount and direction of data transacted (in malware terms, the identification of the data that was exfiltrated. Former employee…
Security Strategy
How Ordr Customers Are Identifying Account Misuse Through Employee Access
3Min Read
By Pandian Gnanaprakasam

Any computer security policy is founded on the concept of identifying users and establishing their credentials to authorize them to access system networked resources. Managing usernames and passwords might seem like a trivial task but when a network grows to have many resources and correspondingly many users, the potential for security breaches multiplies.
Integration with Windows Active Directory (AD) provides flexibility for network administrators to adopt a wide range of security policies.
In the most extreme form of “least privilege” access, administrators can lock down each user to allow access only to very specific resources, at specific times, and with specified permissions for specific resources such as file systems, individual files, servers, VPNs, medical workstations, medical and industrial equipment, printers and copiers, and phones.
In practice, this ideal level of control is rarely achieved, and compromises are made to make managing the operation more practical. As a result, many organizations face the following user access challenges:
- User accounts often grant more access than the employee needs.
- Sometimes user accounts survive an employee’s termination – for one reason or another they aren’t disabled.
- In some cases, a user can create “local” user accounts with access privileges. This is often allowed in systems managed with Windows Active Directory.
- There can be some systems in the network that do not use the network administrator’s security protocol.
- IoT Devices (both wired and wireless) and various off the shelf software packages with default passwords (for example: “admin/admin”) appear in corporate network. Most of the time, account management with passwords can become tedious when thousands of IoT devices are deployed in the network, because these devices are typically configured by the manufacturer with default credentials.
While these challenges vary, the end result is the same: an un-authorized user gains access, typically via a VPN or SSH session to some system or device, and from there accesses other privileged resources in the system. In this type of security breach, malware need not be involved, although this may turn out to be a vector for malware. Given the numerous ways in which phishing attacks can install malware agents on an employee-owned corporate laptop, jumping to other devices with weak credentials becomes easier for attackers.
Ordr and Active Directory, RADIUS and wireless Integration
Ordr provides very robust tracking of users using AD/RADIUS and wireless integration, enabling security teams to monitor which user is accessing what device at what time. Ordr provides two key perspective:
- User tracking – analysis of all devices accessed by a user, including IoT and OT
- Device tracking – analysis of which users were logged into a specific device, at what time, duration and more.
Ordr also monitors all devices that use supervisory protocols like SSH, telnet, ftp, etc., associates them with user names, correlates them with the network they logged in from (corporate or guest), and maintains an accurate access record for each and every device as well as each and every user.
We also track and monitor corporate and guest network users. Corporate resources need to be accessed by corporate users with the right credentials from the corporate network. Ordr can alert or trigger the appropriate incident response workflow when a guest network user crosses over to the corporate network.
Finally, organizations can take advantage of all this rich user authentication during a security incident to provide qualifying details such as which network was the entry point, which device the “user” used to get into the network and what authentication methods they used, in addition to detailed Ordr Flow Genome flows.
Account Misuse Use Cases
Our customers have used the Ordr platform in many cases where one or more misuse of user accounts have occurred.
- Unauthorized user accessing accounts – Based on the network data collected in the Ordr Data LakeTM, we were able to reconstruct extensive and specific activities conducted by a person with an unauthorized-yet-active account, specifically:
- When the user account was logged on and off, and to which system.
- What specific resources were accessed.
- The amount and direction of data transacted (in malware terms, the identification of the data that was exfiltrated.
- Former employee accesses records – In one healthcare environment, we identified that a former nurse used their login credentials at a medical facility to access more than 600 data records. With the information gathered from Ordr, the response and mitigation of the security breach was initiated in a few minutes. Similar incidents have been documented publicly.
- Security cameras with default passwords – Another case involved access to security cameras whose default passwords had not been changed. This can happen not only on new installations but also where a failed unit is replaced by a worker not familiar with the organization’s security requirements. After the initial incident the security team was able to make necessary operational changes to avoid a reoccurrence of this specific problem.
To find out more about how Ordr is helping organizations today, you can view our case studies, webinars and white papers here.
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogCISA Mitigation Guide for Healthcare Organizations: Part One
BlogCISA Mitigation Guide for Healthcare Organizations: Part One…segment I’ll discuss CISA’s Mitigation Strategy #2: Identity Management and Device Security and offer some insights and approaches for achieving the goals of that portion of the Guide. The good…
Healthcare Security
CISA Mitigation Guide for Healthcare Organizations: Part One
4Min Read
By Wes Wright

A lack of medical device and cyber asset visibility puts hospitals and healthcare organizations at risk. Our experts break down the recently published CISA threat mitigation guide to show how Ordr helps follow the recommendations. Build your cybersecurity strategy on a solid foundation of asset visibility and segmentation
On November 20, 2023, the Cybersecurity Infrastructure and Security Agency (CISA) issued guidance for healthcare delivery organizations (HDOs) struggling to secure their data and systems against a growing and pernicious onslaught of attacks from threat actors across the globe. The purpose of CISA’s Mitigation Guide: Healthcare and Public Health (HPH) Sector is to articulate “best practices to combat pervasive cyber threats affecting the Healthcare and Public Health (HPH) Sector.”
The Mitigation Guide follows on the heels of CISA’s Cyber Risk Summary: Healthcare and Public Health (HPH) Sector Calendar Year 2022 in which the agency identified six common weaknesses in healthcare cybersecurity, including:
- Web application vulnerabilities
- Encryption weaknesses
- Unsupported software
- Unsupported Windows operating systems (OS)
- Known exploited vulnerabilities (KEVs)
- Vulnerable services
To help HDOs and other healthcare enterprises create and execute more effective cybersecurity strategies to address these weaknesses, the Mitigation Guide calls out strategies for improving security, with focus areas for each. We’ll be analyzing each of the guidelines provided by CISA in a series of blogs, starting with the first Mitigation Strategy: Asset Management and Security.
Mitigation Strategy #1: Asset Management and Security
Focus Area 1: Asset inventory
At the top of CISA’s list is an issue that is at the core of Ordr’s mission, namely gaining visibility across the enterprise for identifying, inventorying, and securing all of an organization’s assets. Without real-time visibility and complete, accurate details, of every asset on the network (including Internet of Medical Things (IoMT), operational technologies (OT), Internet of Things (IoT) devices, you are building your security program on a foundation of sand. The Mitigation Guide highlights the reason gaining visibility across the IT estate and compiling a thorough asset inventory is vital to improving cybersecurity when it says:
Organizations that have not implemented or maintained an asset management policy risk exposing vulnerabilities or services that could be exploited by threat actors to gain unauthorized access, steal sensitive data, disrupt critical services, or deploy ransomware, causing significant harm to patients and the organization’s reputation.”
Establishing a complete and accurate asset inventory has been a major challenge for HDOs because of the highly varied nature of the technologies that connect to and operate within healthcare networks. HDOs not only have all the traditional systems and devices of other enterprises: servers, routers, desktop and laptop computers, tablets and handheld devices, and the like, but they also have a wide array of Internet of Medical Things (IoMT), operational technologies (OT), Internet of Things (IoT) devices that are critical to patient care services. These can include devices like patient monitors, respirators, imaging and surgical equipment, and therapeutic devices as well as HVAC, security, communications, environmental control, and other equipment.
CISA recommends utilizing active scans, passive processes, or both to discover these devices, but we believe organizations should use a passive approach in order to not impact the operations of sensitive medical devices, IoT and OT. This is consistent with the medical profession’s “do no harm” philosophy, as active scanning can be detrimental to the performance of some equipment. In fact, one organization I’m familiar with experienced a catastrophic failure of its telephone system after active scanning was applied that interfered with the telephony/IP interface.
Furthermore, many systems are either incompatible with active scanning, or may have prohibitions in place due to FDA rules. For these reasons it is best to avoid active scanning. Ordr’s passive scanning approach has proven effective at discovering and identifying all connected assets, has no negative effect on performance or communications, and enables real-time tracking and monitoring of all devices on the network.
Focus Area 2: Securing your assets
CISA recommends that, once a complete and accurate device inventory is compiled, healthcare organizations segment their networks to keep medical devices separate from other technologies. This prevents attackers that succeed in compromising traditional IT from using IoMT to move laterally to their target destination.
I was happy to see that CISA ranked segmentation so high as a priority action. Too often organizations will try to tackle tasks like risk evaluation first, but for every minute the healthcare organization operates with a flat network, those critical devices are vulnerable to attack. By segmenting medical equipment as a second step after compiling a complete inventory, you’ve already increased network security and improved patient safety by disassociating those assets from traditional IT and OT.
Although network segmentation is a great best practice, the reason most organizations put it off–or avoid it completely–is that (as CISA’s schematic and description implies), it can be difficult to do using traditional approaches. Ordr simplifies segmentation. You can start off with macrosegmentation based on asset type, and then evolve to microsegmentation by enabling the creation and automation of Zero Trust segmentation policies to control what devices can connect and communicate with across the network. Segmentation policies created with Ordr can be enforced through integrations with NAC, switches and firewalls.
Stay Tuned for Part Two
In my next segment I’ll discuss CISA’s Mitigation Strategy #2: Identity Management and Device Security and offer some insights and approaches for achieving the goals of that portion of the Guide. The good news is, with the right tools, healthcare organizations can do what is needed with less trouble than they might think.
In the meantime, you might want to check out our new white paper, Mapping Ordr Capabilities to CISA Mitigation Guide: Healthcare and Public Health (HPH) Sector. It goes into much greater detail of how the Ordr platform can be used to quickly and easily do what the CISA Mitigation Guide suggests, while serving as a roadmap for formulating a strategy to align organization policy with CISA guidelines.
Wes Wright
Chief Healthcare Officer
Wes is responsible for driving Ordr’s engagements in healthcare. Previously he was the CTO for Imprivata, and prior to that VP and CTO at Sutter Health, a 26 hospital network in Northern California. Prior to Sutter, Wes was CTO and then CIO at Seattle Childrens’, which, to this day, he says was his most gratifying work experience.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogSee, Know, and Secure Your Asset Attack Surface
BlogSee, Know, and Secure Your Asset Attack Surface…growing larger, more complex, and more diverse; and the mix of hardware, software, and innovative new tools used to manage and secure those enterprises are pushing aside the legacy systems…
Security Strategy
See, Know, and Secure Your Asset Attack Surface
3Min Read
By Danelle Au

Learn about the new cyber asset attack surface management (CAASM) market category emerging in the cybersecurity industry and what it means to you. Then learn how Ordr helps you to see, know, and secure your enterprise’s unique and expanding attack surface to minimize cyber risk. Things move fast in tech. Enterprise infrastructure is growing larger, more complex, and more diverse; and the mix of hardware, software, and innovative new tools used to manage and secure those enterprises are pushing aside the legacy systems that have failed to keep up. The old saying, “You need a scorecard to keep track of the players” would apply but for the fact that the scorecard is probably out-of-date, too.
The CAASM is Growing
Just in case you weren’t paying attention, there’s a new market category—and associated acronym—that has emerged to describe a fast-evolving corner of the cybersecurity industry. Gartner, which coins terms faster than the Franklin Mint, saw activity reaching critical mass in addressing the need to track, secure, and manage the growing number of devices connecting to and comprising the modern enterprise, and defined a new category: cyber asset attack surface management, or CAASM (which you’ll probably want to pronounce like “chasm”).
Richard Stiennon, cybersecurity author and analyst, recently moderated a panel on CAASM as part of the Demo Forum, participated by Ordr’s VP Systems Engineering, Jeremy Haltom.
It’s good to see this space getting attention. Ordr’s mantra, “See. Know. Secure.” is a simple description of the CAASM approach needed to rein-in complexity to make it easier to secure. As enterprises get populated with devices, known and unknown, managed and unmanaged, the attack surface is also growing. That makes it harder for IT security and operations teams to do their jobs. You can’t protect what you can’t see, and it’s hard to know if the things you can see are compromised unless you have a clear understanding of what it is, what risks it brings, and how it is supposed to behave.
Without Visibility You’re Flying Blind
Absent a way to effect complete asset discovery, track the ephemeral nature of the attack surface in real-time, and manage those assets based on actual data that can tell indicators of compromise from a baseline of normal behavior, you are flying blind. And that’s not where a CTO, CISO, or CSO wants to be.
What’s interesting to us is that the Ordr System Control Engine was conceived as a solution to the challenges inherent with protecting connected systems and the networks they were connecting to. This was a big problem for healthcare organizations that rely on a mix of medical devices—the internet of medical things or IoMT—that defy traditional approaches to IT security and management. If a certain piece of equipment is operating with obsolete, unsupported software that makes it vulnerable to attack, there may be restrictions keeping IT from making any needed modifications. And if a device is in active use, it may be impossible to turn off.
Ordr SCE and the Power of Data
That was the challenge we set out to solve when Ordr was founded. But as Ordr gained traction in healthcare and other industries, our customers found that our platform was excellent at discovering and tracking assets wherever they were in the organization. We heard stories of hospitals that found equipment that had been missing for years, while others took the business intelligence they’d gathered from Ordr SCE to support asset requisition and allocation management decisions. That’s the power of data when it is complete, accurate, and in granular, contextual detail.
We know that the challenges associated with seeing, knowing, and securing cyber-assets are not going to diminish. At last count, devices were being acquired and attached to networks and the internet at more than 125 per second, with an expected 75 billion “things” connected by 2025. That’s a lot of devices, and for those organizations driving that growth through the adoption of IoT, IoMT, OT, and other connected devices, that’s a lot of attack surface to monitor, manage, and secure.
With Ordr You Aren’t Alone
So, whether you were aware of CAASM specifically or intuitively, you already know it has to be a part of an effective cybersecurity strategy. The good news is you don’t have to face the challenge alone. Get in touch with us and we’ll show you how you can see, know, and secure your cyber-asset attack surface with OrdrAI CAASM+.
Danelle Au
Danelle Au has more than 20 years of experience bringing new technologies to market. Prior to Ordr, she was CMO at Blue Hexagon, a deep learning for malware protection company, and CMO at SafeBreach where she helped build the marketing organization and and define the Breach and Attack Simulation category. Previously, she led strategy and marketing at Adallom, a cloud security company acquired by Microsoft. She was also Director, Security Solutions at Palo Alto Networks, driving growth in critical IT initiatives like virtualization, network segmentation and mobility. Danelle was co-founder of a high-speed networking chipset startup, co-author of an IP Communications Book and holds 2 U.S. Patents. She has an MSEE from UC Berkeley
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogOpen SSL Security Advisory on Critical Vulnerability
BlogOpen SSL Security Advisory on Critical Vulnerability…proprietary information. The chances of these vulnerabilities getting abused are low because one of the conditions is a malformed certificate signed by a trusted CA. The issue lies in the…
Risk Management
Open SSL Security Advisory on Critical Vulnerability
4Min Read
By Pandian Gnanaprakasam

OpenSSL is an open-source cryptography utility used to generate public and private keys, install SSL/TLS certificates, verify certificate information, and provide encryption. Vulnerabilities discovered in OpenSSL put organizations at risk. Ordr helps to find and mitigate the threat. (Updated on November 10th with new Ordr capabilities)
On October 26th, OpenSSL Project a critical vulnerability associated with OpenSSL versions 3.0 and higher. The version released on November 1st — OpenSSL version 3.0.7 —addresses this vulnerability.
- CVE-2022-3602 is an arbitrary 4-byte stack buffer overflow that could trigger crashes or lead to remote code execution (RCE).
- CVE-2022-3786 can be exploited by attackers via malicious email addresses to trigger a denial-of-service state via a buffer overflow.
-
These vulnerabilities were downgraded from critical to as high (CVSS score 8.8 from 9.0) on November 1st.
Here is what you need to know about this critical vulnerability:
What is OpenSSL?
OpenSSL is a widely used open-source cryptography utility implemented to keep secure the web traffic exchange between a client and server. It is used to generate public and private keys, install SSL/TLS certificates, verify certificate information, and provide encryption.
Most web servers across the internet and within Intranets use SSL certificates to secure connections and the website being browsed. These certificates are traditionally generated by OpenSSL.
How concerned should we be about this vulnerability?
OpenSSL can be misused if the vulnerable version is in use. The good news is that this vulnerability impacts a very specific version of OpenSSL and patching quickly will address any associated risks.
A flaw in OpenSSL has previously affected businesses. In April 2014, OpenSSL’s Heartbleed flaw was discovered. Numerous web servers, including those running popular websites like Yahoo, included it. Security teams rushed to apply updates because the vulnerability was simple to exploit.
How is this OpenSSL vulnerability exploited?
Both CVE-2022-3602 and CVE-2022-3786 vulnerabilities are prone to buffer overflow attacks that can perform RCE (Remote Code Execution) or expose contents of the memory that contains private keys or proprietary information.
The chances of these vulnerabilities getting abused are low because one of the conditions is a malformed certificate signed by a trusted CA.
The issue lies in the verification process of certificates that OpenSSL performs for certificate-based authentication. The exploitation of the vulnerabilities could allow an attacker to launch a Denial of Service (DoS) or even a Remote Code Execution attack.
Patches for the two weaknesses found in OpenSSL v3.0.0 to v3.06 have now been released.
Which OpenSSL versions are vulnerable?
- OpenSSL versions 3.0 and above are vulnerable.
- OpenSSL 3.0.0, the first stable version of OpenSSL 3.0, was released in September 2021, about one year ago. Any older operating systems prior to 3.0.0 are not impacted by this vulnerability.
- Open SSL version 3.0.0 to 3.0.6 are affected by this vulnerability.
- OpenSSL version 3.0.7 includes the fix for the critical vulnerability.
CRITICAL Severity: This affects common configurations, which are also likely to be exploitable. Among these are significant disclosures of server memory (potentially revealing user information), vulnerabilities that are easily exploitable to compromise server private keys remotely, or situations where remote code execution is possible. We will keep these issues private and release a new version of all supported versions as soon as possible.
HIGH Severity: This includes issues that are of a lower risk than critical, perhaps due to affecting fewer common configurations or which are less likely to be exploitable. These issues will be kept private and will trigger a new release of all supported versions. We will attempt to keep the time these issues are private to a minimum; our aim would be no longer than a month, where this is something under our control.
Is the Ordr platform impacted by the OpenSSL vulnerability?
Ordr has reviewed our usage of OpenSSL. This vulnerability does not impact Ordr as we do not use the impacted version.
How Ordr can help?
Ordr has added two new capabilities:
-
A new scanner that will detect versions of the OpenSSL that are vulnerable.
-
New IPS signatures that can detect exploits of this OpenSSL vulnerability
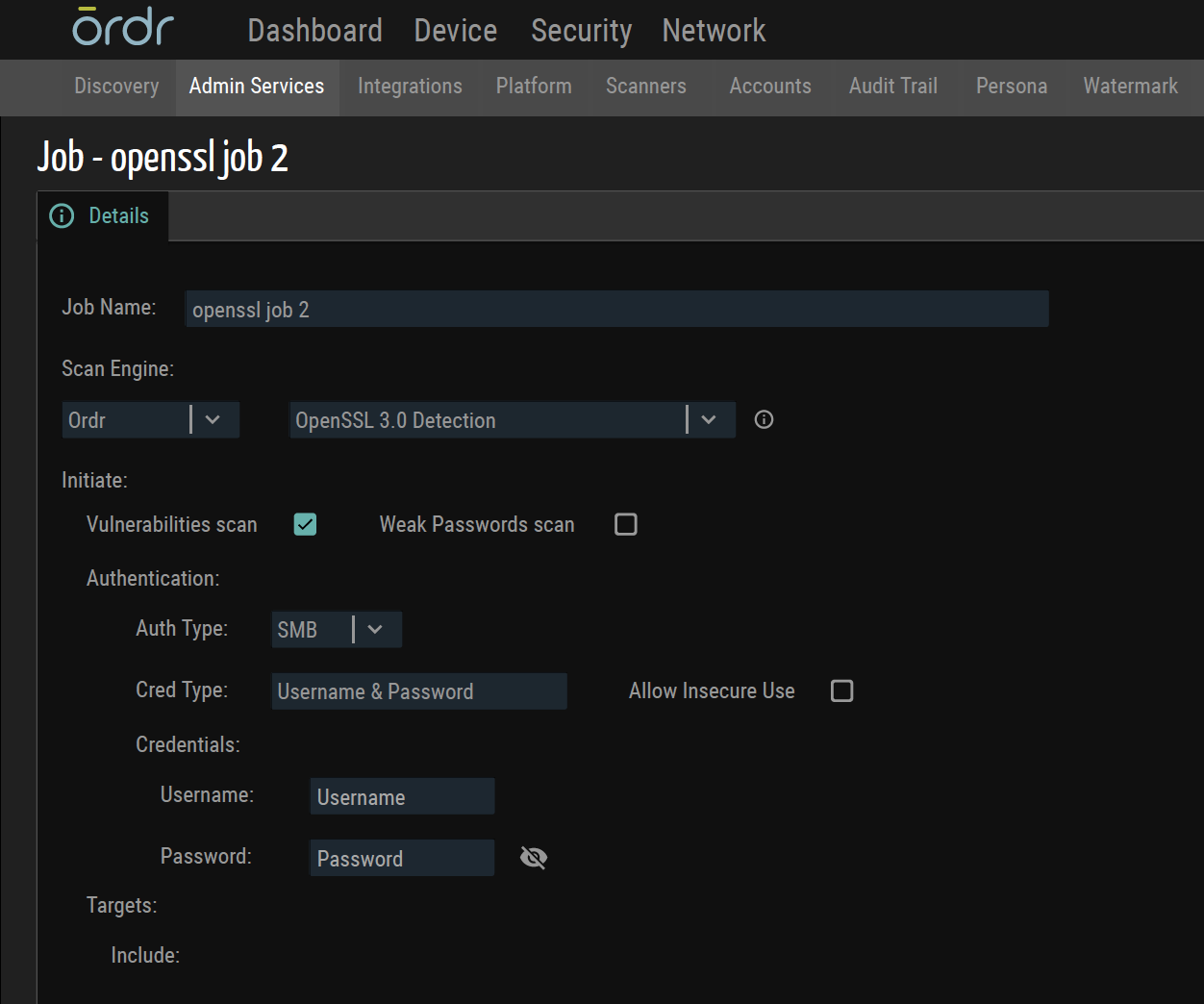
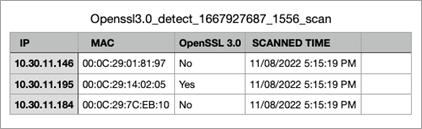
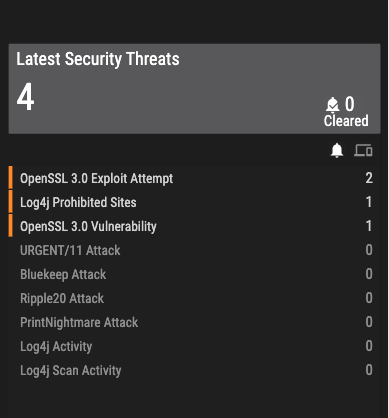
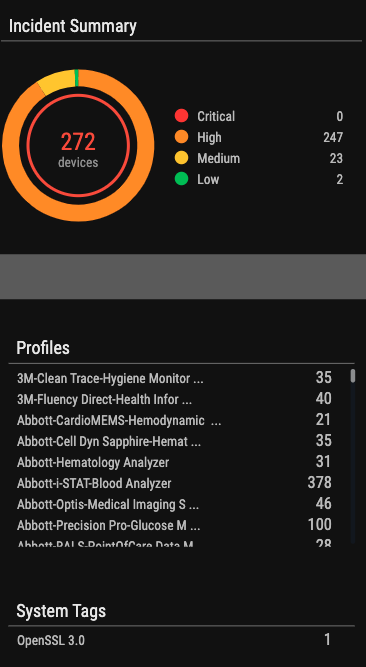
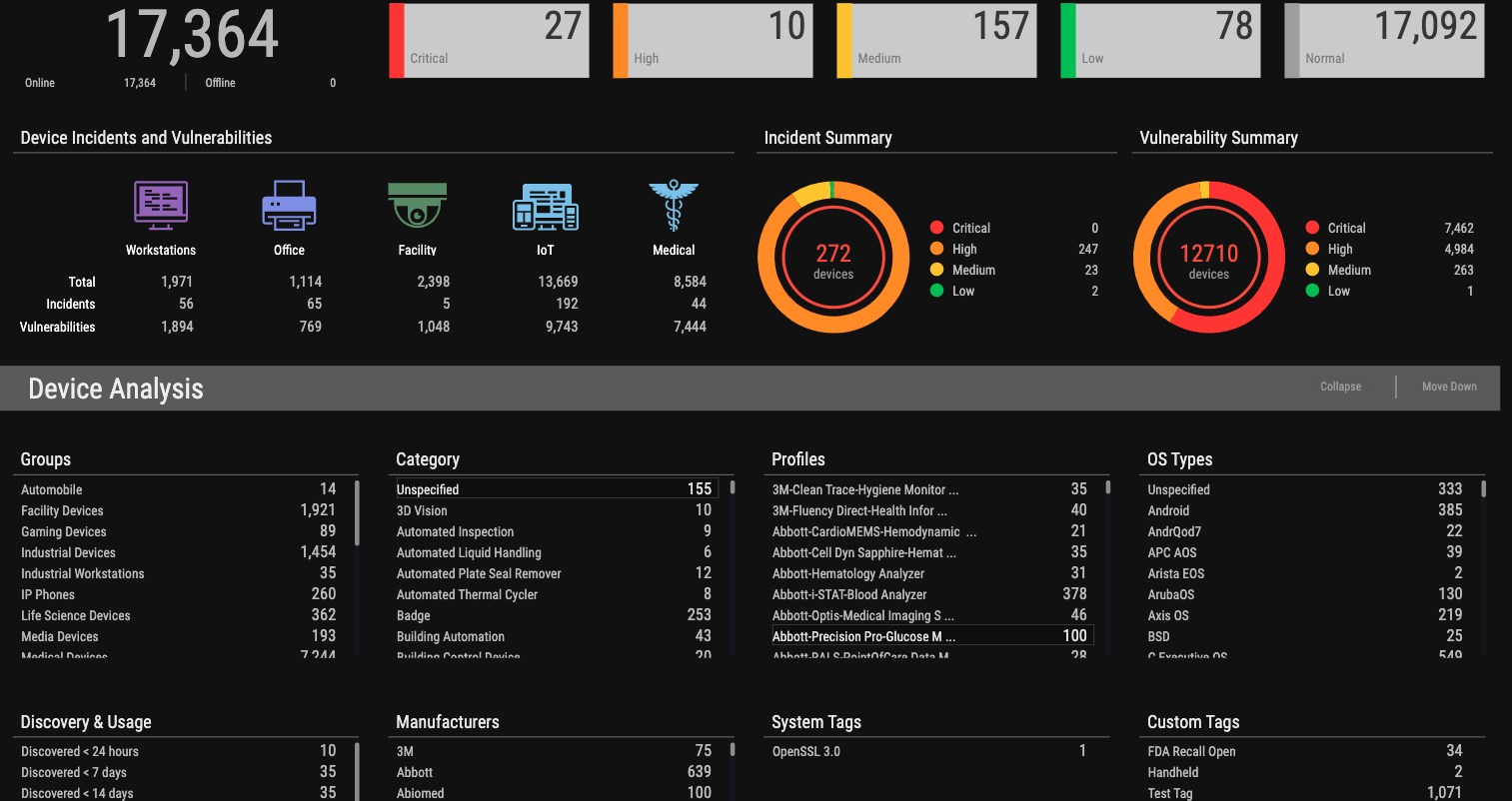
New Ordr Scanner to Detect Vulnerable Versions of OpenSSL
- Ordr scanner uses the following command-line Options:
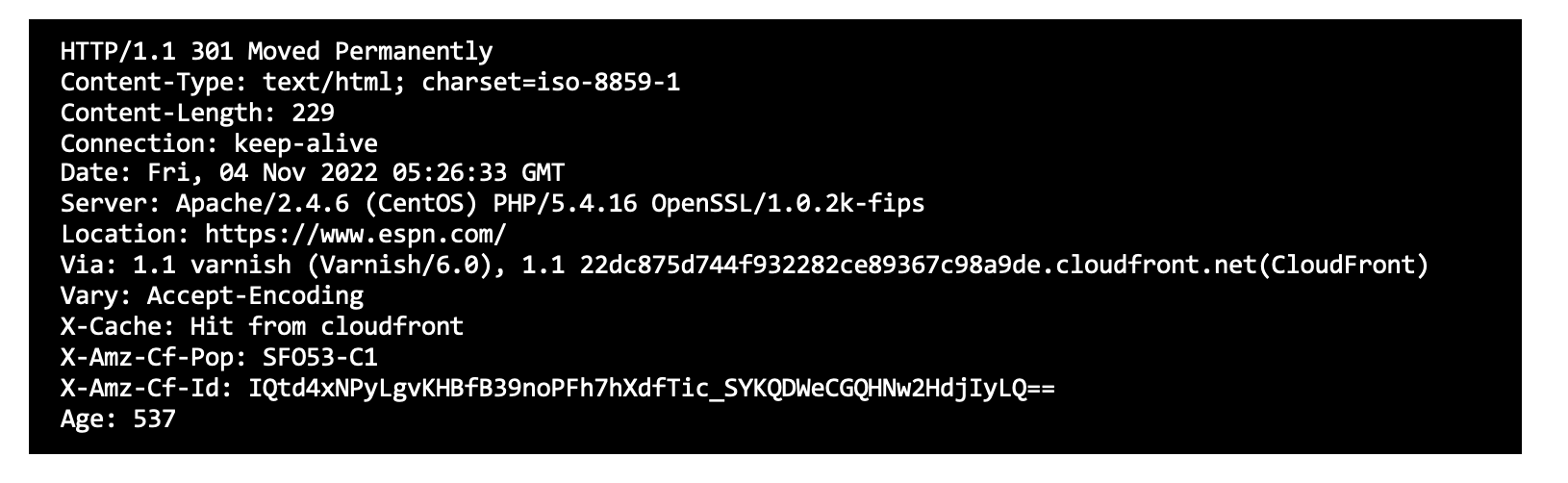
- As servers have an open HTTP port; A curl command is used to connect to them to find the SSL version
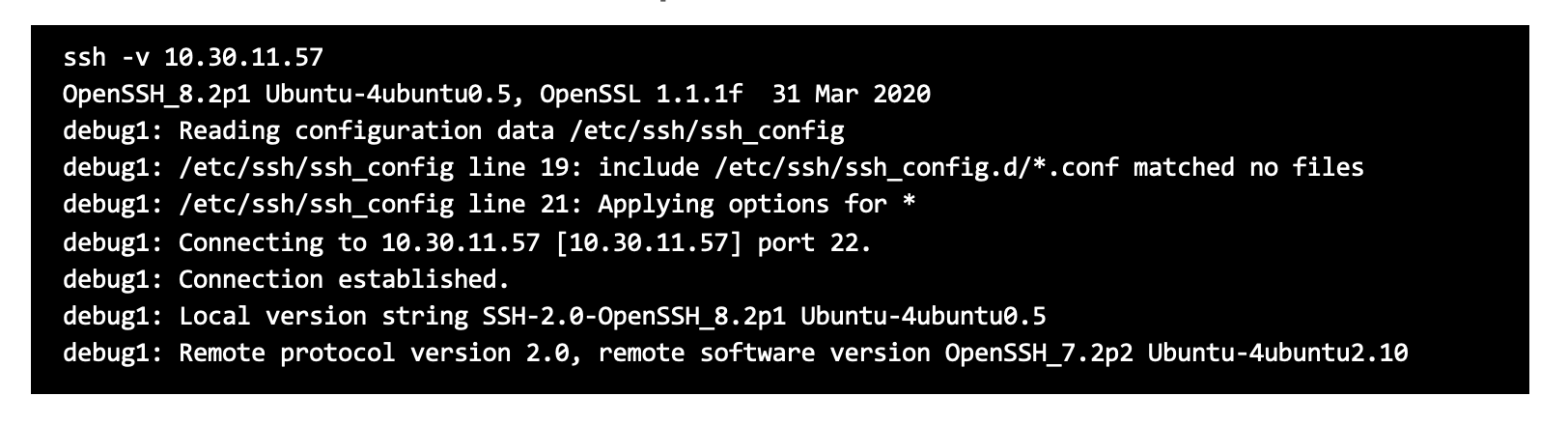
- In cases where clients do not usually have web services, the “ssh” command can be used instead.
- As for a detection method, we use HTTPS headers, SSH headers, and credentialed scans to get the information.
- Some scanners use only authenticated approach that requires full credentials, but Ordr uses an unauthenticated way to get information about Open SSL versions.
- Ordr scanner also uses tools like Nmap to find open ports as a precursor before finding out about the OpenSSL version.
- Example screenshots of detecting Open SSL that is built into the Ordr scanner.
Sample SSL command
Sample SSH command
Packet Parser with IDS Signatures to Detect Exploit Attempts
- While the Ordr scanner detects all the machines that have this vulnerability, the next step is to see if any exploits are exploting this vulnerability.
- There is a parser on the wire that we need to enhance with rules to get versions of TLS, certs, and cryptography.
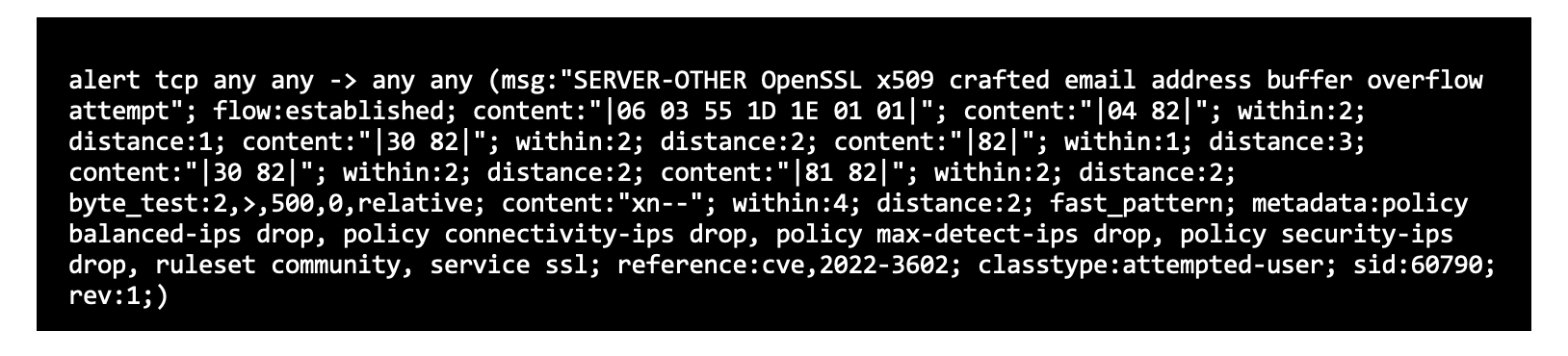
- Ordr has an intrusion detection engine that scans for exploits of this vulnerability with the correct signatures. For example, given below is a signature that would help identify the exploit of this vulnerability.
- CVS-2022-3602 Detection – Detection of this pattern was done using IDS Signatures.
- A buffer overflow can be triggered by sending an X.509 certificate with a specially crafted email address in the “id-on-SmtpUTF8Mailbox” field (OID 1.3.6.1.5.5.7.8.9), resulting in a crash (Denial of Service – DoS) or potentially remote code execution on a vulnerable client or server. Potential opportunities for exploitation can occur if a server requests authentication information after a malicious client connects or if a client connects to a malicious server, which would then make the client vulnerable.
- “OpenSSL x509 crafted email address buffer overflow attempt” is detected with the following signature.
- In the event that there is a malicious activity involving OpenSSL, Ordr has pushed the latest signature to all its customers, and the alarms will be raised.
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogConnected Device Security – Zero Trust is a Journey, not a Destination
BlogConnected Device Security – Zero Trust is a Journey, not a Destination…within the domains of the Internet of things (IoT), Internet of medical things (IoMT), and operational technology (OT) are, by their nature, dynamic. They connect to and disconnect from networks…
Security Strategy
Connected Device Security – Zero Trust is a Journey, not a Destination
Ordr Use Case Series
3Min Read
By Chris Westphal

Hospitals and other healthcare delivery organizations are under constant assault from cybercriminals and other threat actors. In response, Ordr offers a framework for healthcare cybersecurity with A Practical Guide: Implementing Connected Device Security for Healthcare Organizations. If Ralph Waldo Emerson had been a CISO and not a poet, he might have said, “Like life, Zero Trust is not a destination, but a journey.” And he’d be right, of course. For all the love Zero Trust has gotten from zealous marketers who promise that an investment in their cybersecurity product will deliver Zero Trust, the fact is that enterprises are far too dynamic for any one product to achieve that state. In fact, Zero Trust is not a static state, but an ideal that must be as dynamic as the environment in which it prevails.
Dynamic Environment, Dynamic Tool
When Ordr talks about Zero Trust, it is within the context of the challenges of protecting organizations that are increasingly reliant on connected devices to manage and run their operations. Devices within the domains of the Internet of things (IoT), Internet of medical things (IoMT), and operational technology (OT) are, by their nature, dynamic. They connect to and disconnect from networks often, finding a home where they are needed. They move around and increase an enterprise’s attack surface as they aggregate and grow in number. That kind of changeability and complexity requires a security platform like Ordr that has the speed and intelligence to discover, identify, and secure every device operating in the network.
According to the FBI, healthcare was the industry most targeted by ransomware gangs in 2021.
This is especially important for healthcare organizations that rely on IoT, IoMT, and OT devices to manage their facilities and provide a high level of care to patients. These devices gather data, provide diagnostics and therapeutic functions, and automate activity at all levels. But those devices also expand the attack surface of the organizations that deploy them, and threat actors have been taking advantage. According to the FBI, healthcare was the industry most targeted by ransomware gangs in 2021, affecting more than 550 organizations, compromising the protected health information (PHI) of more than 40 million people, and inflicting financial losses of $6.9 billion.
Wisdom of Old CISOs
Standing up to the threat requires thoughtful investments in security tools that address the specific needs of each organization, backed by a deliberate and strategic plan that maximizes the efficacy of those tools to achieve and maintain a continuous Zero Trust posture. And as Emerson said Zero Trust is a journey, another famous CISO, philosopher Lao Tzu said the journey of a thousand miles to Zero Trust begins with a single step. Fortunately for healthcare organizations looking to protect their IoT, IoMT, and OT assets, that single step is one of five in a connected device security maturity model that Ordr has outlined in a new ebook entitled A Practical Guide: Implementing Connected Device Security for Healthcare Organizations.
Five Easy Pieces
Authored by Gartner veteran and Ordr strategic advisor Brad LaPorte, with close consultation by many of our own subject matter experts, “A Practical Guide” includes recommended actions, technical considerations, and helpful insights that complement each of the five steps of maturity for connected device security, which are:
- Step One – Asset Visibility: a foundational exercise that must be launched and operationalized to discover and classify every device, and map its flows.
- Step Two – Vulnerability and Risk Management: used to extend the capabilities of the organization to effectively see and know about all the devices present in the environment.
- Step Three – Reactive Security: prioritization of activities necessary, such as blocking specific inbound and outbound communications to mitigate risks, risks.
- Step Four – Proactive Security: establish automated policies to ensure rapid threat detection and prevention, and begin to implement proactive Zero Trust segmentation policies.
- Step Five – Optimized Security: use of real time analysis and micro-segmentation to automate dynamic policy changes, scale protections reflective of an environment’s current state, and enable continuous improvement.
As you can see, each step in the maturity model builds on the previous step in sequence; there are no shortcuts. And the speed with which an organization progresses from Step One to Step Five will differ. It’s also important to recognize that, when starting from a place of no or incomplete connected device visibility, each step of the journey represents a significant improvement toward Zero Trust. And when a connected device security strategy is implemented and fully matured, it can be applied holistically across an entire organization or focused on multiple critical areas, in sequence or in parallel.
When starting from a place of no or incomplete connected device visibility, each step of the journey represents a significant improvement toward Zero Trust.
If you want to read A Practical Guide: Implementing Connected Device Security for Healthcare Organizations, you can download it here with our compliments.
Chris Westphal
Head of Product Marketing
Chris is the Head of Product Marketing at Ordr where he helps drive awareness for connected device security and the value of the Ordr solution. Chris brings more than two decades of experience to his role with a background in enterprise security, cloud, and data center technologies. Most recently, Chris was head of product marketing at Salt Security, the leader in API protection, and has held product marketing leadership roles at companies including VMware, Illumio, and Adallom (acquired by Microsoft).
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogWhat is Cyber Asset and Attack Surface Management?
BlogWhat is Cyber Asset and Attack Surface Management?…normal communications patterns for every device is critical to identify malicious and anomalous traffic. This can include devices communicating to the Internet, manufacturing or medical devices in the guest VLAN,…
General
What is Cyber Asset and Attack Surface Management?
3Min Read
By Danelle Au

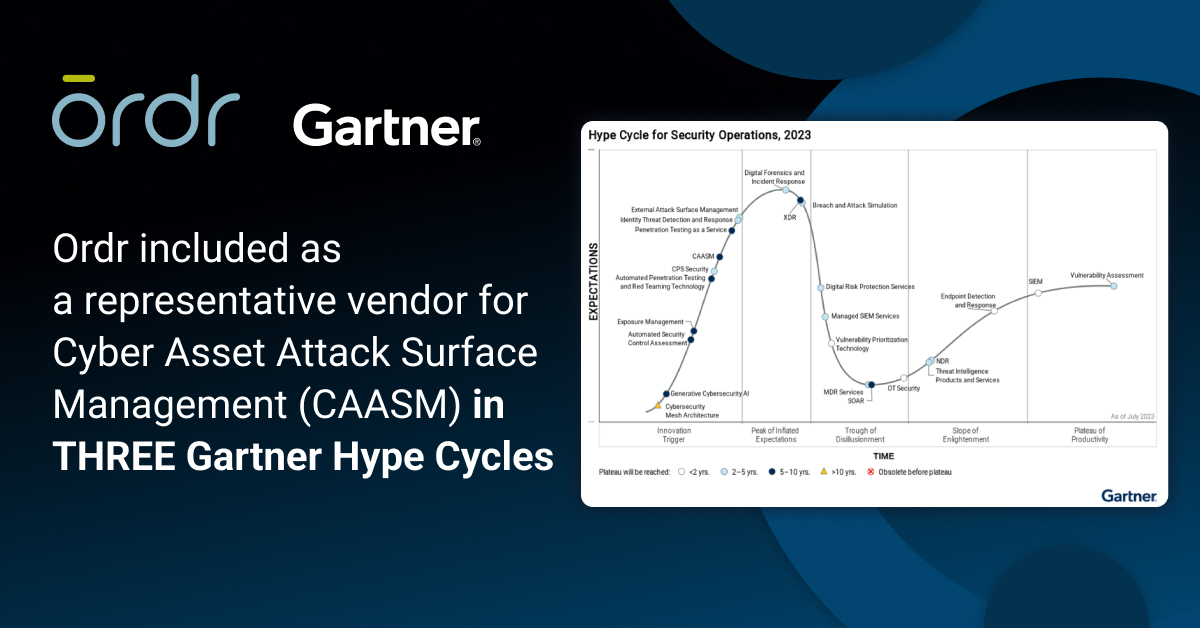
Ordr named a representative vendor for cyber asset attack surface management (CAASM) in 3 Gartner Hype Cycle reports including Hype Cycle for Security Operations, Hype Cycle for Cyber Risk Management, and Hype Cycle for Workload and Network Security. Gartner analysts have been busy publishing several Hype Cycles recently. If you’re not familiar with the Gartner Hype Cycle, it is a graphic representation of the maturity lifecycle of new technologies, and there are several key reports to help security leaders with their strategy and investments. We are thrilled to be included as a representative vendor for Cyber Asset Attack Surface Management (CAASM) category in three Gartner Hype Cycles:
- Hype Cycle for Security Operations, 2023
- Hype Cycle for Cyber Risk Management, 2023
- Hype Cycle for Workload and Network Security, 2023
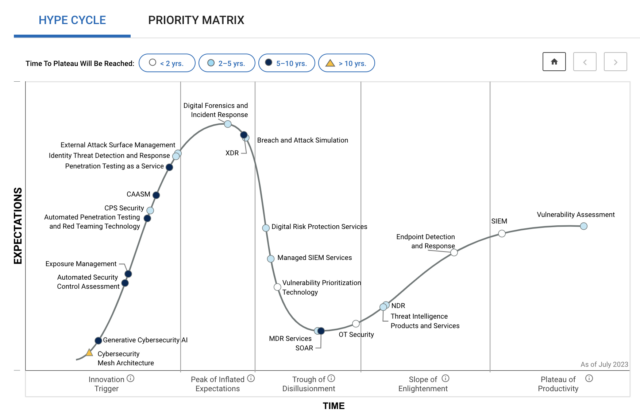
Figure 1: Gartner Hype Cycle for Security Operations, 2023 What is Cyber Asset and Attack Surface Management (CAASM)?
As described by Gartner, “Cyber Asset Attack Surface Management (CAASM) is an emerging technology that is focused on presenting a unified view of cyber assets to an IT and security team. These assets can serve as an attack vector for unauthorized users to gain access to a system to steal information or launch a cyber attack. In order to detect assets containing outdated software, misconfigurations, and other vulnerabilities, CAASM tools use API integrations to connect with existing data sources of the organization. These tools then continuously monitor and analyze detected vulnerabilities to drill down the most critical threats to the business and prioritize necessary remediation and mitigation actions for improved cyber security.”
In Ordr deployments, we don’t just aggregate data via API. We also perform our own asset discovery, via Ordr Discovery Engine and Ordr Software Inventory Collector for the most comprehensive visibility into every asset on the network.
Use Cases for Cyber Asset and Attack Surface Management
There are a number of use cases for cyber asset and attack surface management for security teams:
- Asset management – provide granular visibility across all devices (IT, Internet of Things (IoT) and operational technology (OT) assets), installed applications, SaaS and cloud workloads including detailed information about device type, manufacturer, OS version, vulnerabilities.
- Compliance assessment – during an audit, the process to provide details of assets, and the software, antivirus or applications that are running on them, can be very cumbersome if done manually. CAASM can simplify this process.
- Security gaps – identify security gaps across the network, for example, assets that should have a security endpoint agent but do not or assets that are running outdated operating systems.
- IT governance – identify shadow IT devices or assets that should not be on the network, such as gaming devices. Ordr goes a step further and can help with asset reconciliation, for example, comparing what assets we see on the network versus what is actually in the CMDB or vice versa. We can also identify devices that we discover on the network or are missing on the network in the last 24 hours.
- Vulnerability management – identify vulnerabilities associated with assets. Most CAASMs only ingest vulnerabilities from various source systems. Ordr goes further with asset risk scores and vulnerability management details from our ecosystem of integrations (via API), along with Ordr Software Inventory Collector details. Ordr delivers visibility into vulnerabilities on IoT and OT devices that are are typically blind spots for other CAASM vendors.
These use cases are all fundamental CAASM use cases. But, they are just scratching the surface of what’s possible with Ordr. Enterprise security teams deploying Ordr can also expand to deep behavioral intelligence, threat detection and segmentation for mission-critical IoT and OT assets. Because Ordr also maps communications flows for every asset, we can also support the following use cases:
- Baseline flows – the ability to baseline normal communications patterns for every device is critical to identify malicious and anomalous traffic. This can include devices communicating to the Internet, manufacturing or medical devices in the guest VLAN, or devices that are communicating to a malicious command and control domain.
- Bidirectional integrations – Any asset details that we aggregate and correlate is shared with more than 80 networking and security integrations. For example, granular asset and vulnerability details can be shared with CMMS, CMDB, SIEM and traditional vulnerability management solutions like Rapid7, Qualys and Tenable. This ensures a consistent source of truth on all assets and risks across the entire organization.
- Automated policies – Finally, with Ordr, because we have details on assets, connectivity and communications flows, we can dynamically generate proactive Zero Trust segmentation policies to secure devices (to allow only sanctioned, normal communications) or dynamically generate reactive policies to block ports, terminate sessions or move devices to different VLANs during an incident.
Check out a recent Demo Forum panel hosted by Richard Stiennon on Cyber Asset and Attack Surface Management. Ordr’s own Jeremy Haltom participated, and summarizes our value proposition.
In summary, there are many benefits to CAASM, primarily with optimizing resources via automated inventory of what’s on the network. Additionally, with the granular details on risks for every device, organizations can reduce their attack surface, improve operational efficiencies, and streamline compliance assessments. Ordr extends these benefits to even more comprehensive security capabilities, and actionable policies on existing infrastructure that can accelerate incident response by hours.
For more information on the Ordr platform, contact us.
Danelle Au
Danelle Au has more than 20 years of experience bringing new technologies to market. Prior to Ordr, she was CMO at Blue Hexagon, a deep learning for malware protection company, and CMO at SafeBreach where she helped build the marketing organization and and define the Breach and Attack Simulation category. Previously, she led strategy and marketing at Adallom, a cloud security company acquired by Microsoft. She was also Director, Security Solutions at Palo Alto Networks, driving growth in critical IT initiatives like virtualization, network segmentation and mobility. Danelle was co-founder of a high-speed networking chipset startup, co-author of an IP Communications Book and holds 2 U.S. Patents. She has an MSEE from UC Berkeley
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogProtecting Casinos from Heists…The Cyber Kind
BlogProtecting Casinos from Heists…The Cyber Kind…in that hackers were able to get into the fish tank, into the database, back across the network, and then out of the thermostat into the cloud. With more devices connected,…
Risk Management
Protecting Casinos from Heists…The Cyber Kind
3Min Read
By Pandian Gnanaprakasam

Cybercriminals probably don’t resemble George Clooney or Brad Pitt, but they have exploited connected device vulnerabilities to pull off cyber-heists and steal billions from casinos without any of the Oceans 11 glamor or intrigue. George Clooney and Brad Pitt in Ocean’s 11 looked pretty dapper en route to a $150M heist at three major casinos. Cyber-criminals may lack the handsome dapper look of the original Hollywood cast but some of them are having even better success attacking these gambling enterprises. It’s not just the fancy casinos on the strip either, online establishments are also feeling the sting of cyber attacks.
Casinos can make easy targets for cyber attacks because of the myriad of connected devices. Think about the networking infrastructure, the security cameras and then think about all the public-facing ATMs, card readers, slot machines. You name it, if it’s connected to the network it’s an entry path for cyber criminals. Proper patching and having a vulnerability system can prevent some of these attacks yet it’s a constant battle against well-armed foes.
Add up the impact of the two big casinos such as the Las Vegas Sands and The Hard Rock Hotel & Casino and the total was about $1Billion due to cyber attacks on both the gaming and internal networks. The FBI concluded that the attackers were Iranian hackers that were behind the Las Vegas Sands attack. Not only did they get into the network but they ended up with a lot of personal data on hotel customers as well. Down the strip, Bloomberg estimated that the attack on the Venetian and Palazzo which had their network taken down and private information leaked, the cost of the damage was about $40M. This doesn’t include the hidden cost of reputation damage and the loss of confidence of customers.
There are no hidden headphones or special vans parked outside when it comes to an online gaming enterprise, a market estimated at over $40 Billion. DoS or other methods are being used to get into online sites where the damage can be more severe than at a brick and mortar counterpart. Hack into a game and you are likely to lose gamblers in a hurry, creating very rapid losses for online gambling operators.
Within DDoS, Advanced Persistent Threats (APT) is when co-ordinated DDoS attempts with other web-based attacks are used in a multi-phase lengthy campaign persisting over weeks or even months at a time. Short, single vector attacks go straight at it and typically is the work of very focused individuals who pay a nominal fee at any of the many botnets for hire services.
The smart thermometer attack in the fish tank hack at a casino was ingenious in that hackers were able to get into the fish tank, into the database, back across the network, and then out of the thermostat into the cloud. With more devices connected, it’s going to be increasingly challenging for casinos to keep their networks safe from the onslaught of attacks.
Protecting the slot machines and every valuable asset is a necessity when it comes to keeping a network safe. The first order of business when it comes to protecting a casino is to get full visibility of what’s actually connected. A systematic approach to applying patches can help reduce vulnerabilities at casinos and should be part of an overall security and protection plan as well. Monitoring the traffic is important and making sure that certain devices communicate within their respective separate zones (or segments) can also help casinos protect their networks and contain the damage if a breach occurs.
At Ordr, segmentation applies to both ends of the spectrum of detection/isolation and protection/prevention. On the side of detection, reaction and remediation we rate risk by levels when we see unusual activity such as a device unnecessarily scanning a network, or injecting unwanted packets. While setting off an alarm is one thing at a casino, we don’t think its enough to say “hey this machine is bad”. At Ordr, our system sends the alert but also we send all the remediation procedures with it. For example, the notice will be this Slot Machine which is connected to this particular Cisco switch on this port number 27 needs to be shut down or we need to quarantine this machine using VLANs. Another productive message can be “this HVAC controller on the main casino floor with this particular MAC address connected to this AP/wireless controller needs to be blacklisted.”
The damage at a casino can be very high, and hackers attack casinos because simply, that’s where the money is. We’re building and deploying a smart system that can isolate bad actors quickly when something suspicious comes up in a casino’s network. The proactive protection that we provide takes it a step further as we understand the flows and we whitelist certain transactions such as the application, protocols, and destination. The system is constantly learning and observing flows and noticing deviations if any. George Clooney will be impressed.
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogCybersecurity Asset Management for Modern Organizations
BlogCybersecurity Asset Management for Modern Organizations…including configuration, communications patterns, and expected, unusual behavior, and more; and, Automated policy generation and enforcement to support the protection of devices that are at risk of compromise, or that…
Use Case
Cybersecurity Asset Management for Modern Organizations
Ordr Use Case Series
3Min Read
By Danelle Au

IT asset management is the process of inventorying every piece of hardware, software, service, and application asset in the technology estate from acquisition and deployment to retirement. Doing it right can pay major dividends for improving enterprise security. In IT (information technology), asset management is the process of inventorying every asset that makes up the technology estate. Every piece of hardware and software, every service and application in use has to be tracked from the moment it is acquired until it is retired. Asset management is vital to keeping track of things like licenses, software updates, maintenance, depreciation, and other administrative aspects of enterprise technology ownership.
Asset management plays an essential, if unheralded role in cybersecurity. When you have an accurate and real-time accounting of all the assets that make up your IT environment, you can minimize the chances of an adversary finding a weak spot, or of an error that puts your systems and data at risk of a breach. That’s because cybersecurity asset management also involves things like patch management, access control, and assignment of user privileges.
The Challenges of Unmanaged and Hyperconnected Devices
One area that is difficult for traditional approaches to cybersecurity asset management is unmanaged and hyperconnected devices like IoT (internet of things). Many devices that are within the realm of IoT and that are connected to the enterprise are not traditional IT gear. This can range from devices that cannot be actively scanned to devices that slip through the cracks of NAC systems. (network access controller). Traditionally, whether the equipment is added with the knowledge of IT management, or whether it connects outside of the view of IT, it has to be monitored and tracked manually—and that is an impossible task given the number of devices in use today. And the problem is only going to get worse given predictions of increased deployment use. Juniper Research estimates IoT deployments will go from 36 billion devices today, to more than 83 billion by 2024.
When devices are undiscovered and unmanaged, they represent a potential point of entry for threat actors. And because the number of devices deployed in today’s sophisticated enterprises can reach five- and six-figures, organizations can’t afford to overlook them as a part of an IT security and management program. That is why a connected device security platform that foundationally performs cybersecurity asset inventory and management is an essential tool for the modern enterprise.
Three Keys to Success
To be effective at the task of cybersecurity asset management, organizations require a platform that is engineered for massive environments and is able to synthesize a significant amount of device data via machine learning and automation. That is because accurate device classification and behavioral baselining of device behavior inherently is made for machine learning.
The keys to successful cybersecurity asset management are:
- Complete device discovery to ensure total visibility and accountability into your entire managed and unmanaged device inventory;
- Real-time device monitoring and profiling to ensure you know the status of every connected asset, including configuration, communications patterns, and expected, unusual behavior, and more; and,
- Automated policy generation and enforcement to support the protection of devices that are at risk of compromise, or that cannot be managed and secured by legacy or manual processes.
These are baseline capabilities that can close the security gaps that exist in enterprises that are struggling to manage their expanding connected device inventories. Many devices were never meant to be accessible to the public internet, but are now connected to online supply chain networks; many devices were made by companies that no longer exist, and are now unsupported; many devices operate on obsolete software and operating systems and are vulnerable to well-know exploits; many medical devices are prohibited from needed updates because of FDA mandates.
Discover ALL Your Devices with Ordr
Ordr discovers all managed and unmanaged devices connected to your network, monitors and profiles device use and behavior, and assesses security risks in real time, and automatically generates and enforces security and management policies, ensuring complete coverage across your entire inventory.
If you’re struggling with cybersecurity asset management, Ordr can help. For quick visibility and assessment of your connected devices, request a demo with one of our experts.
Danelle Au
Danelle Au has more than 20 years of experience bringing new technologies to market. Prior to Ordr, she was CMO at Blue Hexagon, a deep learning for malware protection company, and CMO at SafeBreach where she helped build the marketing organization and and define the Breach and Attack Simulation category. Previously, she led strategy and marketing at Adallom, a cloud security company acquired by Microsoft. She was also Director, Security Solutions at Palo Alto Networks, driving growth in critical IT initiatives like virtualization, network segmentation and mobility. Danelle was co-founder of a high-speed networking chipset startup, co-author of an IP Communications Book and holds 2 U.S. Patents. She has an MSEE from UC Berkeley
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogPublic-Private Partnerships to Secure Medical Devices
BlogPublic-Private Partnerships to Secure Medical Devices…at the NTIA. An SBOM is the list of “ingredients,” or the individual components of which a device’s software is composed. Explained by Mr. Jacobson, the task group has been…
Risk Management
Public-Private Partnerships to Secure Medical Devices
3Min ReadBy Ty Greenhalgh

Cyber Tygr’s Ty Greenhalgh writes of the value of establishing public-private initiatives to help address some of the pressing needs in protecting healthcare technology ecosystems by securing medical devices (IoMT) to minimize hospital risk and exposure to cyberattacks. In episode three of the seven-part CHIME webinar series, Public-Private Partnerships to Secure Medical Devices, I am joined by five guest speakers representing three public-private initiatives addressing current issues in the healthcare ecosystem.
- Mike Powers, MBA: Representing the Legacy Devices task group within the Healthcare Sector Coordinating Council (HSCC) Joint Cybersecurity Working Group. Mr. Powers is a Clinical Engineering Director at Intermountain Healthcare and a member of the AAMI Healthcare Technology Leadership Committee.
- Samantha Jacques, PhD: Dr. Jacques is also from the HSCC Joint Cybersecurity Working Group and is the Vice President of Clinical Engineering at McLaren Health Care, vice-chair of the AAMI Healthcare Technology Leadership Council, and a fellow of the American College of Healthcare Executives.
- Alex Wolf: Another representative of the HSCC Joint Cybersecurity Working Group as the Model Contract Language task group leader, Mr. Wolf is a Cybersecurity Specialist at Cleveland Clinic.
- Jim Jacobson: From the National Telecommunications and Information Administration (NTIA) Software Component Transparency work group, Mr. Jacobson is the Chief Product and Solution Security Officer of Siemens Healthineers, and Mr. Amusan is a Principal Cybersecurity Analyst at Mayo Clinic.
- Tola Amusan, MBA: Mr. Amusan is a Principal Cybersecurity Analyst at Mayo Clinic and also a member of NTIA.
Our first topic was addressed by Mr. Powers and Dr. Jacques on their projects at the HSCC’s Legacy Device work group. Officially, legacy devices are defined by the International Medical Device Regulators Forum as simply those that cannot be protected against current cybersecurity threats. In contrast to this vague description, Dr. Jacques elaborated on how clinical engineers of Health Delivery Organizations (HDOs) alternatively define them as devices no longer supported by the manufacturer, necessitating reactive strategies like microsegmentation and network monitoring to keep them secure. The task group’s upcoming publication will provide guidance on the core practices, challenges, recommendations, and HDO and Medical Device Manufacturers (MDM) perspectives. One critical area of contention it aims to resolve is the difference between “end of life” and “end of support.” To an MDM, “end of life” may potentially be initiated to justify terminating post-sale technical support, instructional material, and/or patch availability to incentivize replacement. From an HDO perspective, an unsupported device may still function perfectly, and prematurely relegating it to end-of-life status is often infeasible or cost prohibitive. As Mr. Powers concisely summarizes the distinction, “It’s end-of-life when I push the ‘ON’ button and it doesn’t turn on.”
It’s end-of-life when I push the ‘ON’ button and it doesn’t turn on.”
Mike Powers MBA, Clinical Engineering Director at Intermountain Healthcare
Next, Mr. Jacobson and Mr. Amusan presented their work on Software Bills of Materials (SBOMs) at the NTIA. An SBOM is the list of “ingredients,” or the individual components of which a device’s software is composed. Explained by Mr. Jacobson, the task group has been creating a proof-of-concept SBOM since 2018. Their goal is to provide standardized and automated formats for use by manufacturers. Mr. Amusan highlighted the various use cases of how HDOs may utilize SBOMs across Healthcare Technology Management (HTM) functions ranging from procurement, asset management, risk management, vulnerability and patch management, and device life-cycle management.
In the final segment of the webinar, Mr. Wolf presented an overview of the HSCC’s Model Contract Language task group. Its foremost objective is establishing shared cooperation between MDMs and HDOs in regard to security, compliance, management, operation, and security of MDM-managed medical devices. The task group has been working a contract template for organizations of any size, which simplifies cybersecurity requirements and expectations between parties, and aligns with existing standards like NIST and the FDA Post-Market Guidance. A point of particular emphasis in the delegation of compliance responsibility and liability between parties. Security breaches to devices are an inevitability, so clearly establishing the duties and obligations ensures the HDO and MDM are prepared to recover, and to prevent. To quote Mr. Wolf, “In the event that something goes wrong, both parties are aware of those expectations and have a good understanding how to work through those issues.”
Ty Greenhalgh
For the last 4 years, Ty has been the CEO of Cyber Tygr, a company dedicated to improving and protecting the privacy, cybersecurity and compliance of our nation’s Health Industry by operationalizing advanced technologies. As a result of his intensive efforts in supporting the cybersecurity posture of healthcare medical devices and facility equipment, Nuvolo has brought him on board to spearhead their new Cyber OT module. Mr. Greenhalgh is an active member in several groups and associations, such as Healthcare and Public Health Sector Coordinating Council’s Joint Cybersecurity Workgroup, the Department of Health and Human Services 405(d) Workgroup and the Department of Commerce National Information and Telecommunications Agency.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogBehave You: Network Control
BlogBehave You: Network Control…of every stripe. Each device increases the attack surface and must be protected. Part 4 of 6 in our Series You and I See an Innocuous Camera… Step into a…

The modern manufacturing floor relies on network-attached devices of all kinds. Cameras, sensors, controllers, actuators and IoT, OT, IT, and other cyber assets of every stripe. Each device increases the attack surface and must be protected. Part 4 of 6 in our Series
You and I See an Innocuous Camera…
Step into a major contract manufacturer and the machines are buzzing and whirling with activity. Production lines are busy cranking out the latest consumer electronics and cameras are everywhere making sure the quality process and controls are in ship-shape order. Major facilities here and overseas can have thousands of cameras installed along a production line.
All-day long these digital cameras stream images and video to the data center maintaining diligent logs to track production line quality. The problem is of course that cameras have been an easily exploitable weakness for cyber attacks. It gets more confounding since oftentimes, cameras come configured with default passwords. Alarmingly, it is very easy to hack into a camera and instruct the camera to send its recording to a remote suspicious site. Upgrade the password across all these hundreds of cameras? It won’t accomplish much asides give you a list of new passwords. Furthermore, industrial cameras are embedded systems so you cant even upgrade the OS or install any anti-virus even if you wanted to.
Dealing with Anomalies
Firewalls, anti-virus, and vulnerability detection tools are all available to help us deal with the constant ongoing threats but how do you deal with sophisticated malware attacks which can infiltrate a camera of all things? Much can be accomplished with signature detection and we at Ordr work closely with well-known sources to identify and see deep into signatures for anything that might provide clues of ill intent. We rely on signatures to identify what we consider “known” malware.
There are numerous anti-malware solution providers that identify objects, adding new signatures to its known database and we work them as well. These repositories grow each day and hold data on hundreds of millions of signatures that identify and classify malicious objects. Signature protection against malware works, it is relatively easy to use and it’s a tried and true method of catching the millions of older but still persistent threats that are roaming out there.
But Signatures Only Get You So Far
The problem in this sophisticated age of cyber attacks is that some versions of code may not always be recognized by this mapping approach of signatures. New versions of nasty code can appear that are not readily recognized by traditional signature-based technologies. A study by Cisco found that 95% of malware files analyzed weren’t even 24 hours old.
Worse yet, sometimes signatures can morph and hide. Think about that for a second, malware changing to avoid detection. It’s actually not that hard, some code permutation change here, a register renamed there or code shrunk or expanded and malware can avoid the traditional signature detection.
NotPetya: The Dangers of Hidden Signatures
When NotPetya surfaced, it was originally thought that it was another annoying resurfacing as it had a similar code structure and signature to that of the original Petya ransomware.
NotPetya, however, was way worse and way more sinister. NotPetya got its name from Petya but alarmingly, though it looked similar to Petya, the ransomware message was only a disguise. There was no real money demanded, no real unlocking code at all. The intention of NotPetya was all destructive and to irreversibly encrypt a computer master boot record.
NotPetya was designed to not just encrypt the master boot record (MBR) but to overwrite it with the attacker’s own MBR and with no access to MBR, the user can not access the OS on the computer leaving it inoperable. The signature told security managers that NotPetya was ransomware but NotPetya was actually a highly descriptive data wiper disguised as Petya. Identifying signatures is a start but to really understand what’s happening in your network, one needs to understand the behaviors of the devices with respect to its peer group, history, and context.
Ensuring the Camera is in its best Behavior
If we go back to the example of the cameras at the factory floor, we know what the device should be doing, sending images and video streams to the video servers at the data center. If there is any deviation from this behavior, we will see it right away and we can shut things down immediately.
It’s not just the changes from the daily routine that we can see, our engine can monitor how each device acts in a normal setting relative to its peer group. Time series is also factored in that we can see if a camera’s behavior is deviating or is different from what its behavior was in the prior weeks.
If there is some strange communication between a camera and remote suspicious site, our proactive system can prevent this since it’s smart enough to know that a particular camera never had this session in the past. Even if there is a request going into the camera from an external site, we will sound the alarm. An attempt to extract a video without permission? This is a behavior violation. Unusual communications, we catch that too. If it’s a behavior violation, Ordr will prevent it right away. A thermostat talking to the finance department, that should not happen. Some traffic flow trying to disable security controls or install rootkits? We will shut it down.
Ordr Keeps Learning
Threats are dynamic and constantly evolving. Having a system that understands signature can help in a hyperconnected environment but to have real proactive protection a system must contextually be aware and have the insight to understand behaviors. Diving deeper into historic patterns can also help capture baseline deviations that might fly under the radar.
At Ordr our system is constantly expanding its behavior library, understanding what is normal and what is out of character for each and every device type. We complement your current tools and we work with what you already have. Ordr helps you quickly identify all the friends, eliminate all the foes and ensure all your devices behave the way they should.
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?