Search Results:
”Role of Huawei H19-431_V1.0 Exam Questions in Getting the Highest-Paid Job 💆 Search for { H19-431_V1.0 } and download exam materials for free through [ www.pdfvce.com ] 🏸Premium H19-431_V1.0 Files”
-
 NewsNHS Data Security And Protection Toolkit
NewsNHS Data Security And Protection Toolkit…remain in operation for a number of years and cannot be easily replaced for cost reasons. Ordr in its recent Rise of the Machines report found 19% of deployments with devices running…
Ordr Helps Healthcare Organizations Meet Key Criteria
NHS Data Security And Protection Toolkit
4Min ReadMEDIA ALERT
What is Being Announced?
NHS Digital has recently amended the NHS Digital’s Data Security and Protection Toolkit (DSPT) making it mandatory for NHS organizations to now keep an up-to-date inventory of all medical devices including security vulnerabilities and data security. All organizations that have access to NHS patient data and systems must adhere to the requirements in this toolkit to provide assurance that they are practising good data security and that personal information is handled correctly.
Ordr, the leader in agentless security for all connected devices, is today launching a guide to assist healthcare organizations to meet the new DSPT criteria. Healthcare organizations are particularly vulnerable to cyber-attacks such as ransomware, due to outdated operating systems running on medical, Internet of Things (IoT) and Operational Technology (OT) devices. This is due to the fact that many of these devices, in particular medical devices, remain in operation for a number of years and cannot be easily replaced for cost reasons.
Ordr in its recent Rise of the Machines report found 19% of deployments with devices running outdated operating systems Windows 7 and older, and almost 34% of deployments with devices running Windows 8 and Windows 10, which are expected to end-of-life in 2023 and 2025 respectively. Organizations need an automated way to identify these devices-at-risk and segment them to ensure security of these devices, keep them in operation and avoid the costs of replacing devices early.
What Is DSPT?
NHS Digital’s Data Security and Protection Toolkit (DSPT) is an online self-assessment tool that enables organizations to measure their performance against the National Data Guardian’s 10 data security standards. All organizations that have access to NHS patient data and systems must use this toolkit to provide assurance that they are practicing good data security and that personal information is handled correctly. This system is subject to ongoing development.
What Does It Mean for Healthcare Organizations?
DSPT compliance will force many organizations to take a fresh look at their cybersecurity programme and make changes to align with NHS Digital requirements. Core security functions such as inventory, risk management, and threat detection will be essential to maintaining compliance, and organizations should look for efficient, automated systems that can help provide coverage for all connected devices — from traditional servers, workstations, and PCs to IoT, IoMT and OT devices.
Bob Vickers, Head of UKI at Ordr commented:
“Even though data security standards ask healthcare organizations to ensure technology is secure and up to date with no unsupported operating systems, this is actually a global medical challenge for most. Connected medical devices can range widely, and often ran on outdated systems, even though they are a critical part of business operations.
We need to remember that securing medical devices will define the future of healthcare. Security teams need the right tools to increase visibility into risks, bring devices into compliance, optimize utilization and protect them from cyberattacks. spend. Here at Ordr, healthcare organizations can not only gain complete visibility into devices and risks, they can also keep track of NHS Cyber Alerts as a data feed into the Ordr Systems Control Engine (SCE) and address cyber threats such as ransomware on their network. By leveraging automation to drive efficiencies, they can ensure the highest standards of security for patient safety.”
How Can Ordr Help?
Ordr SCE can arm organizations with a powerful platform to gain visibility into their network-connected devices, automatically expose potential risk, and automatically enforce policies for rapid mitigation during cyber attacks or segment high-risk devices to only “allowed” communications, passively and without agents. Ordr is already working with the University Hospital Southampton NHS Foundation Trust (UHS) and the University Hospitals of North Midlands NHS Trust (UHNM Trust) to tackle these challenges, and to improve healthcare cybersecurity and patient safety.
Some of the key criteria that Ordr can help healthcare organizations with are: Personal Confidential Data, Managing Data Access, Responding to Incidents, Continuity Planning,
Unsupported Operating Systems and IT Protection.
The Ordr system has the following key functionality to help meet the above criteria:
- Real-time Asset Inventory: Ordr brings together a unique combination of traffic analysis and AI to automatically discover and classify every device on the network. This includes high-fidelity information such as make, classification, location, and application/port usage.
- Vulnerability Management: Ordr delivers a variety of unique capabilities in the area of vulnerability management. The platform includes a built-in vulnerability scanner to identify devices affected by a variety of industry-specific security alerts or recalls.
- Behaviour and Risk Profiling: Ordr includes a built-in IDS engine to detect threats and devices that are under active attack. Ordr also automatically learns every device’s unique communication patterns, known as its Ordr Flow Genome. This provides a baseline that can be used to find suspicious and anomalous behaviours that could be the sign of an unknown threat.
- Automated Response: Ordr can can automate the creation of NGFW policies, ACL blocks, quarantine VLAN assignment, port shutdown, or session termination with one click of a button– enforced on existing switches, wireless controllers, and firewalls, or via NAC platforms—to mitigate risks. By baselining device behaviour, Ordr can also dynamically create segmentation policies such as firewall rules that provide devices with necessary access while limiting unnecessary exposure.
Prepare today
The Data Security and Protection Toolkit is an annual self-assessment. The deadline for the 2021-22 publication is 30 June 2022. See how Ordr maps to the “Data Security And Protection Toolkit (DSPT)”.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 NewsOrdr Announces a Milestone Release of Ordr Systems Control Engine
NewsOrdr Announces a Milestone Release of Ordr Systems Control Engine…and includes more than 160 new features, integrations, and enhancements to provide unparalleled visibility and protection to companies and their connected devices. As the number of connected devices — including…
Ordr Announces a Milestone Release of Ordr Systems Control Engine
3Min ReadSANTA CLARA, Calif., January 21, 2021 — Ordr, the leader in visibility and security of all connected devices, today announced a significant release of the Ordr Systems Control Engine (SCE), a platform that discovers every connected device, profiles device behavior and risks, and automates response. Ordr SCE 7.4.2 is the largest product launch for the company to date and includes more than 160 new features, integrations, and enhancements to provide unparalleled visibility and protection to companies and their connected devices.
As the number of connected devices — including unmanaged IoT, IoMT, and OT devices — continues to rise exponentially, so do the number of vulnerabilities and attack vectors. Organizations are struggling to maintain a real-time accurate inventory of all connected devices, not to mention the device intelligence to quickly make informed decisions.
“Ordr provides the most robust, time-to-value security solution for organizations that want to reap the benefits of network-connected devices, yet curtail increased global incidents of ransomware, phishing, credit card, and personal data breaches,” said Gnanaprakasam Pandian, co-founder and Chief Product Officer of Ordr. “We are so excited to offer extensive new integrations from dozens of security and network vendors, as well as enhanced features to our customers in healthcare, manufacturing, financial services, life sciences, retail and beyond.”
Ordr not only identifies devices with vulnerabilities, weak ciphers and certificates, and active threats, but also those that exhibit malicious or suspicious behaviors. Ordr automates responses for security and networking teams by dynamically generating policies and enforcing them on existing infrastructure, or by alerting and triggering a specific security or operational workflow.
Highlighted features and benefits of Ordr SCE 7.4.2 include:
- Reduced infrastructure footprint with “sensor-less” visibility via telemetry data from supported switches, routers, firewalls, and wireless LAN controllers. Overnight, customers can leverage key technologies that are already in place and begin the Ordr journey.
- Increased efficiency with workflow-based dashboards to help customers quickly lookup devices that match specific conditions, including manufacturer, category, and profile as well as devices with sensitive data, devices with custom tags, devices communicating with administrative protocols, devices running outdated operating systems, and more.
- Security enhancements to enable our customers in the wake of high-profile ransomware as well as espionage-like activity seen in the SolarWinds attack with access to enhanced security components, focusing on optimized detection and tracking within the platform. Customers will have the ability to visually track antivirus software activity, URLs associated with phishing, malicious communications, user-defined prohibited country communications, and quickly see devices with admin protocols and a snapshot of criticality level for devices with known vulnerabilities.
- Empowered Healthcare Technology Management (HTM) teams with actionable clinical data like medical device data from the FDA, clinical and patient risk associated with a device(s), and security risk from Manufacturer Disclosure Statement for Medical Device Security (MDS2) forms to help make informed decisions and initiate the appropriate workflows within a matter of minutes.
- New security integrations for efficient incorporation into a customer’s existing security workflows. This includes the ability to detect and track ransomware with signature improvements for expedited incident response (IR) processes. In addition, Anomali, Exabeam, Fortinet, IBM QRadar, and Ping Identity join existing partners such as Check Point, Splunk, ServiceNow, and many others, in Ordr’s integration portfolio — the most comprehensive ecosystem of integration partners in the market.
- Enhanced analytics and use case-based policy generation so customers can quickly address scenarios such as controlling access for all physical security cameras used in a retail location, segment patient care devices by hospital and healthcare division, or tag all manufacturing devices that are still running Windows XP or Windows 7.
- Acceleration of Cisco TrustSec and Cisco Software-Defined Access (SD-Access) as Cisco’s leading IoT solution partner for Cisco Identity Services Engine (ISE). Ordr is the only product on the market to provide total IoT and OT visibility to Cisco ISE and the rich device context required to dynamically define Scalable Group Tags (SGTs), automate the provisioning of group-based segmentation policies and provide SGT visualization and traffic analysis that greatly accelerates the time to value and increases strategic adoption of Cisco TrustSec and SDA.
About Ordr
Ordr makes it easy to secure every connected device, from traditional IT devices to newer and more vulnerable IoT, IoMT, and OT. Ordr Systems Control Engine uses deep packet inspection and advanced machine learning to discover every device, profile its risk and behavior, map all communications and protect it with automated policies. Organizations worldwide trust Ordr to provide real-time asset inventory, address risk and compliance and accelerate IT initiatives. Ordr is backed by top investors including Battery Ventures, Wing, and TenEleven Ventures. For more information, visit www.ordr.net and follow Ordr on Twitter and LinkedIn.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogUnderstanding IoT Adoption and Risks
BlogUnderstanding IoT Adoption and Risks…data with the global security communitiy to better understand IoT risks and secure their organization. Among the report’s most interesting findings were the frequent discovery of consumer-grade shadow IoT devices…

The first step to gaining the upper hand on cyberthreats is understanding IoT adoption trends and the security risks they pose. The second step? Acquiring the tools needed to discover, monitor, and protect your connected devices in real-time. In 2015, former Cisco research David Evans calculated how many devices were being added every second. At the time, an average of 127 new things were being connected to the Internet every second. 328 million things were being connected every month, approximately one for each person in the U.S.
Fast forward to 2020 and the IoT market has exploded. From connected cars and video cameras to smart virtual assistants and HVAC systems, the IoT market is now expected to grow to 31 billion connected devices by 2020 and 75 billion devices by 2025.
With so many devices proliferating, security and risk professionals need to be much more aware of the expansion of their attack surface. Each device represents a new attack vector for cyber attackers. The recent spate of vulnerabilities that impact IoT recently, from Ripple20 to SIGRed, demonstrates the importance of securing these devices.
But what types of risks should enterprises expect to find in their environment? How best should they protect themselves?
Today, we’re excited to release the inaugural Rise of the Machines: 2020 Enterprise Adoption and Risk Report. We examined more than 5 million unmanaged, IoT, and IoMT devices in Ordr customer deployments across a variety of verticals including healthcare, life sciences, retail and manufacturing, between June 2019 and June 2020. Ordr strongly believes in the importance of sharing this type of data with the global security communitiy to better understand IoT risks and secure their organization.
Among the report’s most interesting findings were the frequent discovery of consumer-grade shadow IoT devices on the network such as Amazon Alexas and Echos.
We love the perspective that Zeus Kerravala, founder and Principal Analyst at ZK Research provided, “In some of my recent research around enterprise IoT security I’ve found that more than 51% of IT teams are unaware of what types of devices are touching their network. But perhaps what is more disconcerting is that the other 49% often times find themselves guessing or using a ‘Frankenstein’d’ solution to provide visibility into their network security, which will almost always create security issues. Shadow IoT is becoming a real security challenge, as It’s not enough to have the visibility into what is touching your network, but you need a solution like Ordr’s that allows for you to resolve the issues in a scalable automated fashion.”
Highlights from Ordr deployments include the following:
- 15-19 percent of deployments had IoT devices running on legacy operating systems Windows 7 (or older). Since it is often not economical to take these critical systems out of service, these devices need to be properly segmented.
- 20 percent of deployments had PCI-DSS violations where IoT devices with credit card information were on the same subnet or VLAN as a tablet, printer, copier, or video surveillance camera.
- 86 percent of healthcare deployments had more than 10 FDA recalls against their medical IoT devices, meaning the medical device is defective, poses a health risk, or both.
- 95 percent of healthcare deployments had Amazon Alexa and Echo devices active in their environment alongside other hospital surveillance equipment. Voice assistants can unknowingly eavesdrop and record conversations and may put the organization at risk of a HIPAA violation.
- 75 percent of healthcare deployments had VLAN violations where medical devices were connected to the same VLAN and subnet as other non-medical devices.
There are real risks and threats posed by IoT, IoMT, and other connected devices if not accounted for and properly managed. One cannot fix what one cannot see, and with IoT, the discovery and classification is the very first step. Once security and networking have high fidelity visibility into unmanaged and IoT devices, then they need to understand device behavior, perform risk assessment and segment vulnerable and mission-critical devices.
Danelle Au
Danelle Au has more than 20 years of experience bringing new technologies to market. Prior to Ordr, she was CMO at Blue Hexagon, a deep learning for malware protection company, and CMO at SafeBreach where she helped build the marketing organization and and define the Breach and Attack Simulation category. Previously, she led strategy and marketing at Adallom, a cloud security company acquired by Microsoft. She was also Director, Security Solutions at Palo Alto Networks, driving growth in critical IT initiatives like virtualization, network segmentation and mobility. Danelle was co-founder of a high-speed networking chipset startup, co-author of an IP Communications Book and holds 2 U.S. Patents. She has an MSEE from UC Berkeley
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 NewsOrdr Releases 2021 Rise of Machines Report
NewsOrdr Releases 2021 Rise of Machines Report…cybersecurity challenges, including the growth of connected devices and related increase of security risks from these devices as threat actors took advantage of chaos to launch attacks. The research incorporates…
Ordr Releases 2021 Rise of Machines Report
Highlighting Connected Device Security Trends and Threats During COVID
3Min ReadSANTA CLARA, Calif, 11 August 2021 — Ordr, the leader in agentless security for all connected devices, today released its annual report on the state of connected devices, titled “Rise of the Machines 2021: State of Connected devices — IT, IoT, IoMT and OT.” The 2021 report addresses pandemic-related cybersecurity challenges, including the growth of connected devices and related increase of security risks from these devices as threat actors took advantage of chaos to launch attacks.
The research incorporates security risk and trend analysis of anonymized data for 12 months (June 2020 through June 2021) across the company’s 500+ deployments in healthcare, life sciences, retail, and manufacturing verticals.
42% of connected devices were agentless or un-agentable devices
The number of agentless and un-agentable devices increased to 42% in this year’s report (compared to 32% of agentless or un-agentable devices in 2020). These devices include medical and manufacturing devices that are critical to business operations along with network devices, IP phones, video surveillance cameras and facility devices (such as badge readers) that are not designed with security in mind, cannot be patched, and cannot support endpoint security agents. With almost half of devices in the network that are either agentless or un-agentable, organizations need to complement their endpoint security strategy with a network-based security approach to discover and secure these devices.
Pelotons, Sonos, Alexas and Teslas discovered in the network
As a sign of the times, Ordr also discovered that popular consumer “devices” are often connected to the enterprise network, including Pelotons, Sonos speakers, gaming machines, Alexas and Teslas. While the usage of unsanctioned shadow IoT devices was highlighted in the 2020 Rise of the Machines report, there are 2 times more personal devices this year increasing the threat landscape and delivering a wealth of data for threat actors to use to profile targets.
Outdated operating systems present the greatest risks especially in healthcare
Ordr identified about 19% of deployments with devices running outdated operating systems Windows 7 and older, and almost 34% of deployments with devices running Windows 8 and Windows 10, which are expected to end-of-life in 2023 and 2025 respectively. Among the report’s most troubling findings was the discovery that 15% of medical devices and 32% of medical imaging devices run on outdated operating systems. This is because many medical devices remain in operation for a number of years and cannot be easily replaced for cost reasons. Segmentation is the only way to ensure security of these devices, keep them in operation and avoid the costs of replacing devices early.
“Once again, we found an astonishing and worrisome number of vulnerabilities and risks in connected devices, which is a crucial reminder that organizations must have comprehensive visibility as well as security for everything connecting to their networks,” said Ordr CEO Greg Murphy. “As the number of connected devices climbs, the number and sophistication of attacks targeting them will grow.”
Additional findings include:
- 46% of all connected devices are vulnerable to medium and high severity attacks. Top attacks included external communications to malicious URLs such as Darkside and Conti ransomware sites, followed by attacks due to vulnerable operating systems and finally lateral movement such as exploits and active threats/tools like Cobalt Strike or Eternal Blue.
- 55% of deployments have devices with orphaned user access. Devices with orphan accounts retain the same access rights as when they were associated with an active user. These orphaned user accounts provide a gateway to privilege escalation and lateral movement.
The report also includes a helpful set of steps organizations should take to implement Zero Trust for connected devices.
For additional findings and details, download the full report “Rise of the Machines 2021: State of Connected devices — IT, IoT, IoMT and OT”.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogStrategic Risk Prioritization and Vulnerability Management
BlogStrategic Risk Prioritization and Vulnerability Management…mitigating alert fatigue and delivering a prioritized list of top risks. With features like the Vulnerability Dashboard for comprehensive insights, Query Builder for customized dashboards, and Ask OrdrAI for instant…
Blog
Strategic Risk Prioritization and Vulnerability Management
Across the Cyber Attack Surface
< 1Min Read
By Srinivas Loke
Studies show that close to 50% of ransomware attacks result from unpatched vulnerabilities, including weaknesses in an organization’s information systems, system processes, or internal controls. Prioritizing vulnerabilities presents a significant challenge for enterprises as security teams often must sift through thousands of vulnerabilities, each presenting different dangers to the organization based on the associated asset risk. Yet this must be done because unaddressed vulnerabilities increase the likelihood of a breach or cybersecurity incident.
To effectively manage vulnerability risks, enterprises must therefore develop a strategy that prioritizes vulnerabilities based on its specific risk and impact to their business. In general, assets can be categorized into three broad categories:
- Assets with known vulnerabilities that can be patched once a patch is available.
- Assets with known vulnerabilities that may have a recommended patch, but validation by the manufacturer is necessary before patching.
- Assets with an outdated operating system (OS) that typically cannot be patched. (In such cases, security teams must find alternate methods to prevent the exploitation of these vulnerabilities.)
To help organizations simplify and tackle the task of risk prioritization and vulnerability management, Ordr’s Cyber Asset Attack Surface Management (CAASM) product offers enterprises end-to-end vulnerability management, enabling their security teams to identify, investigate, and prioritize vulnerabilities efficiently. Below we will share how Ordr enables enterprise security teams to reduce alert fatigue and get a prioritized list of top risks.
Automatically Discover and Assign Vulnerabilities to All Assets
Ordr uses multiple methods to collect and de-duplicate vulnerability data from multiple sources, offering a streamlined approach to managing vulnerabilities on a single platform. Utilizing the following methods ensures security teams can discover and understand the full vulnerability landscape across all assets, including IT, IoT, IoMT, and OT.
1. For regularly scanned assets, integrations with vulnerability assessment systems, such as Rapid7, Tenable, and Qualys, collect vulnerability data. Ordr then deduplicates this data to ensure teams have an accurate list of vulnerabilities.

2. For assets that cannot be scanned or are not updated regularly, Ordr’s lightweight script, Software Inventory Collector, detects vulnerabilities based on KB/HF correlation instead of scanning the asset. This approach ensures comprehensive vulnerability coverage is collected for assets that cannot undergo traditional scanning.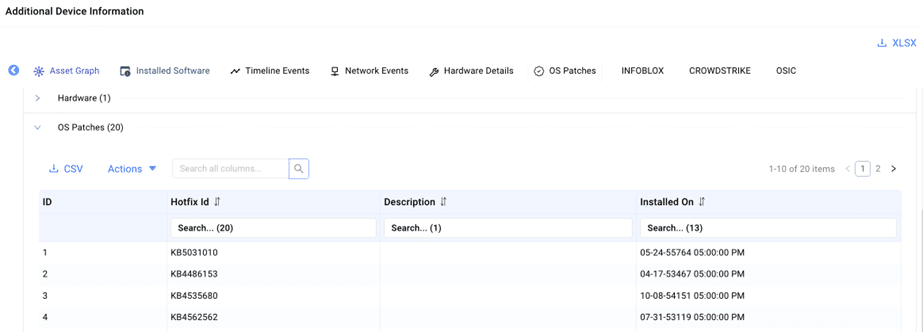
3. For assets with outdated operating systems, Ordr uses both passive and active scanning techniques to collect detailed asset context, including make, model, manufacturer, and OS. This data is then used to accurately assign vulnerabilities to these assets.Enhancing Vulnerability Data & Context for Risk-Based Prioritization
After identifying all assets with vulnerabilities, Ordr enriches the data by providing additional business context for each asset. This empowers security teams to prioritize vulnerabilities based on the criticality of assets to the business, enabling them to focus on addressing the most significant risks. Ordr’s Asset Risk Score considers multiple factors such as asset context, CVSS scores, vulnerability exploitability, type of data (encrypted), location, and more. To obtain detailed asset data and business context, Ordr utilizes:
- AI/ML technology to classify assets and assign business context. Customers can also add additional context to customize the risk score to further align with their specific business needs.
- Known Exploited Vulnerabilities (KEV) and Exploit Prediction Scoring System (EPSS) data to gain additional visibility into vulnerabilities posing the greatest risk.
After gathering asset context utilizing AI/ML technology, the data is standardized into a score, prioritizing assets based on numerical risk. Each asset is assigned a risk-based score ranging from Level 1 to Level 5, with mission-critical assets designated as Level 5.
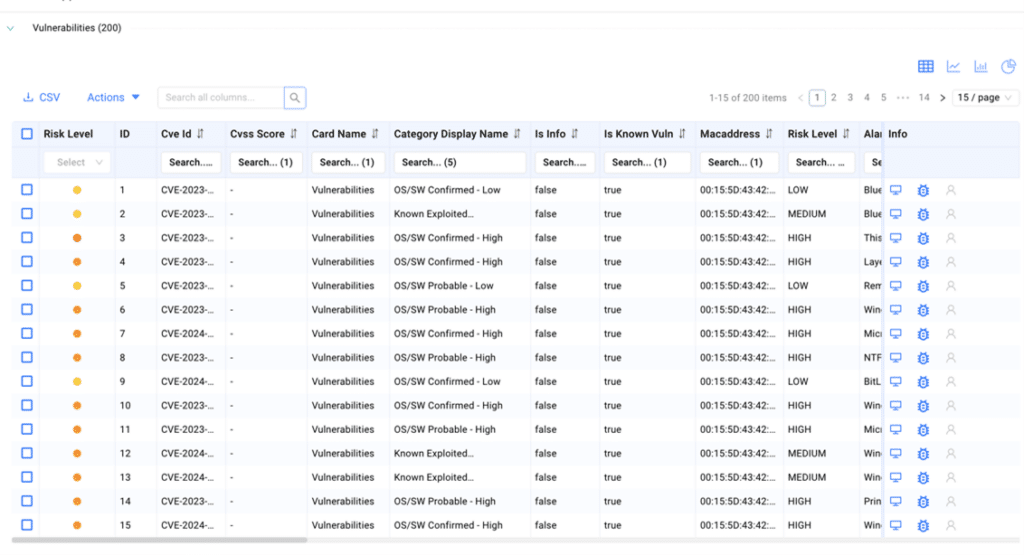
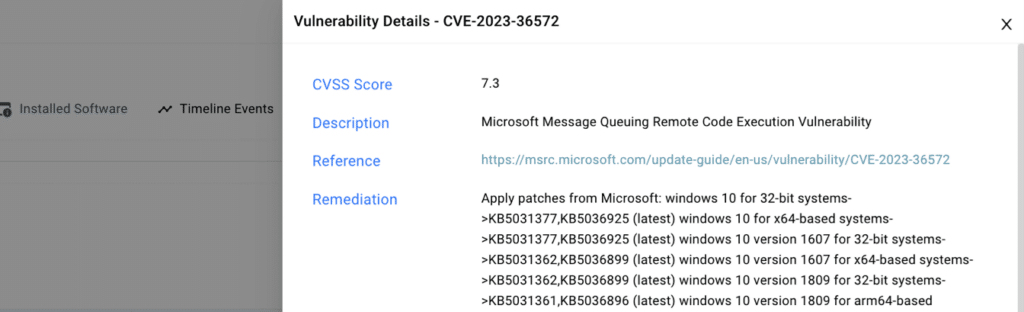
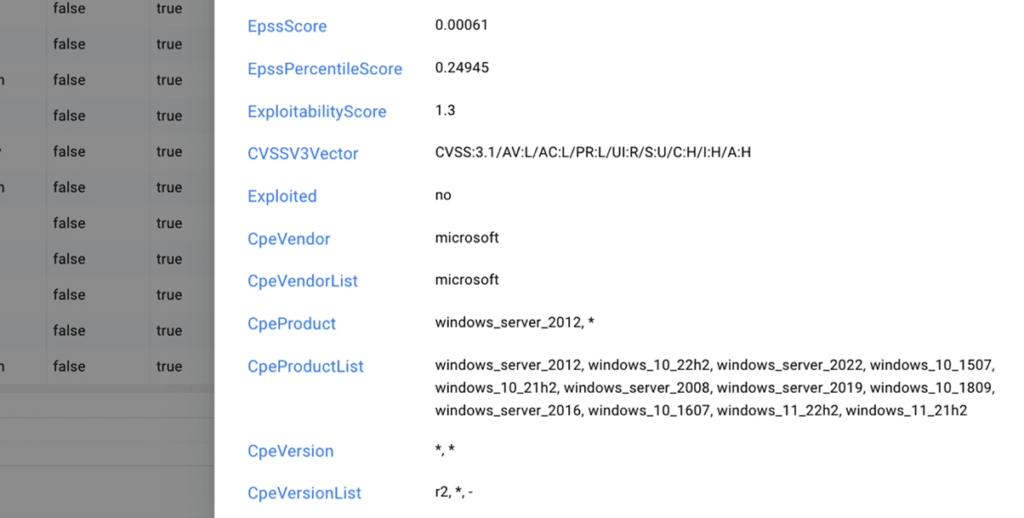
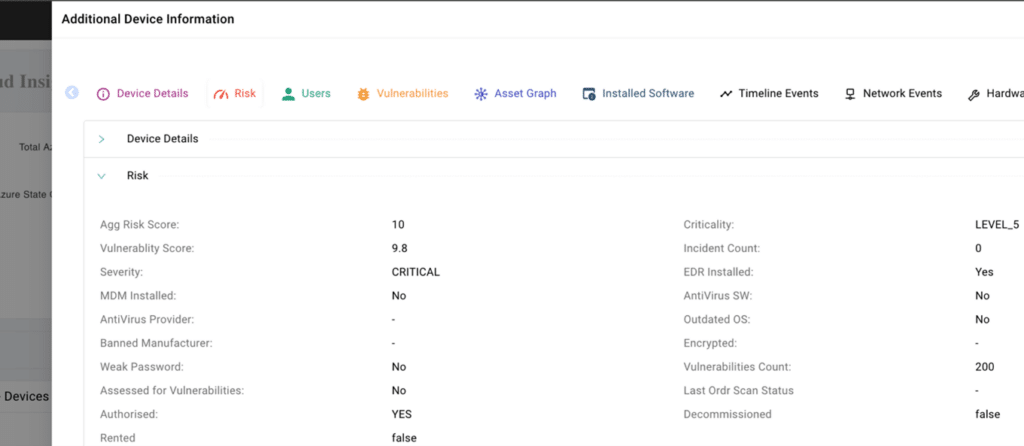
Streamlining End-to-End Vulnerability Management
Ordr streamlines end-to-end risk and vulnerability management to cover everything from associating vulnerabilities with assets, to assigning remediation tasks to the appropriate asset owner and monitoring vulnerability status. Ordr’s comprehensive approach includes:
- Building integrations with vulnerability management tools, such as the ServiceNow VR module and others, to deliver real-time status updates based on reconciled data.
- Providing the capability to mute a vulnerability, allowing teams to temporarily hide the vulnerability from dashboards while still tracking the vulnerability until a patch is available.
- Enabling teams to assign vulnerability remediation tasks to individual users, complete with priority and due date specifications.
- Providing visualization of trending analysis based on newly discovered, open, and closed vulnerabilities.
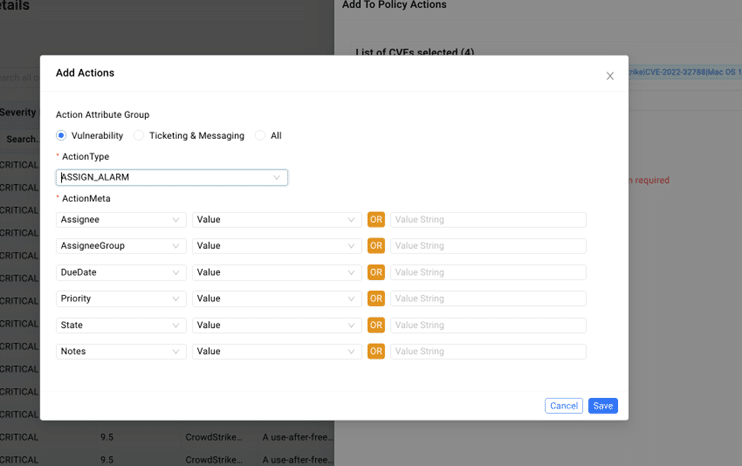
Intuitive Vulnerability Data Search
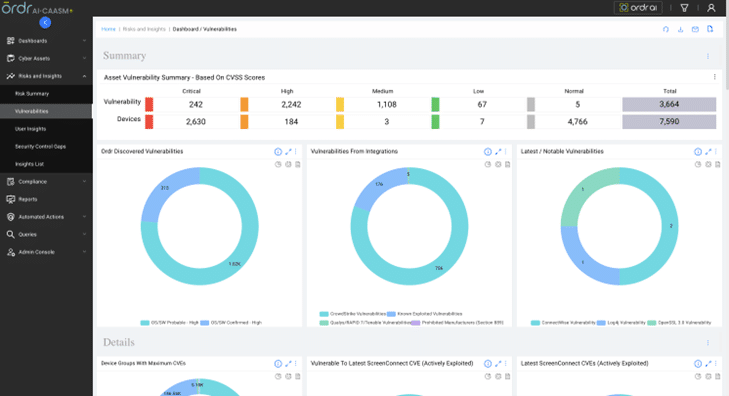
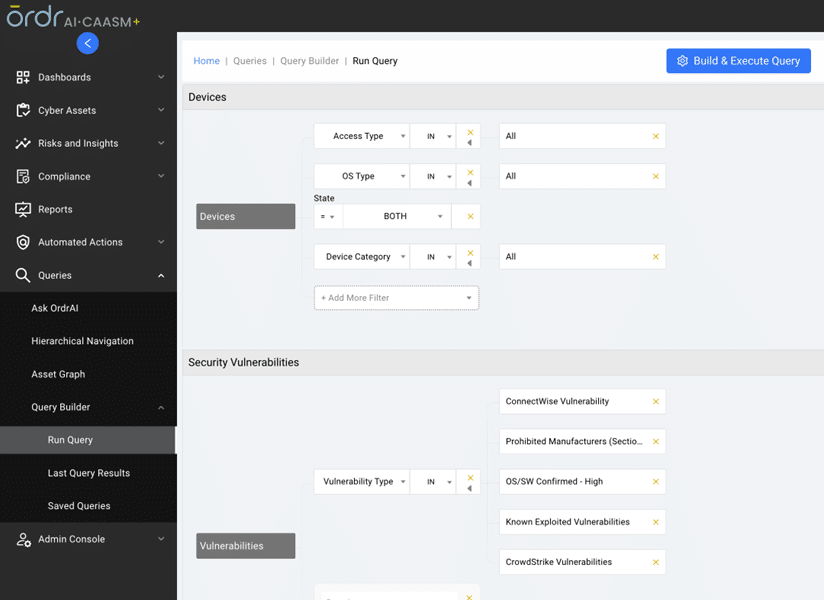
Ordr’s AI/ML mapping and correlation engine, along with the Software Inventory Collector, align technical and business priorities, mitigating alert fatigue and delivering a prioritized list of top risks. With features like the Vulnerability Dashboard for comprehensive insights, Query Builder for customized dashboards, and Ask OrdrAI for instant vulnerability information, CAASM+ simplifies risk and vulnerability management on a single platform.
Vulnerability Dashboard provides a complete “state of the union” on vulnerabilities.
Query Builder for creating a custom dashboard based on the customer’s needs.
Ask OrdrAI gives security teams a natural language search option to get information on vulnerabilities, eliminating the need for technical expertise or coding.
Ordr integrates with industry-leading security solutions to share data and insights when assets have vulnerabilities or remediation is needed. Recommended data sources for Ordr to integrate with for end-to-end vulnerability management include:
- EDR
- MDM
- CMDB
- Cloud Assets
- Vulnerability Assessment Systems
- Ordr Discovery Engine
Ordr provides a framework for remediation with multiple enforcement options. These enforcement actions include:
- Network based enforcement (changed VLAN, shutdown port, integrate with firewall)
- Integrations with ticketing systems
- Integrations with messaging/collaboration tools
- Integration with vulnerability management tools
Watch the video to see how CAASM+ empowers security teams to efficiently identify, investigate, and prioritize vulnerabilities.
https://www.youtube.com/watch?v=7fhFem5YqRcLearn more about Ordr’s risk-based vulnerability prioritization and management and connect with one of our experts for a personalized demo.
Thanks for joining us for another blog in our series on CAASM+ use cases. Stay tuned as we explore more of these critical use cases in the coming weeks and discuss how Ordr addresses them.
Srinivas Loke
Srinivas Loke is Vice President of Product Management at Ordr. Srinivas has a passion for cybersecurity with a deep understanding of network, end point, cloud and IoT security. Prior to Ordr, he led product teams at Aruba, Pulse Secure, FireEye and McAfee. He loves taking 1.0 products to the market and furthering cutting edge technologies that are solving customer problems.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogCISA Mitigation Guide for Healthcare Organizations: Part Two
BlogCISA Mitigation Guide for Healthcare Organizations: Part Two…for Part Three In our next segment we’ll discuss CISA’s Mitigation Strategy #3 Vulnerability, Patch, and Configuration Management, and offer insights and approaches for achieving the goals of that portion…
Healthcare Security
CISA Mitigation Guide for Healthcare Organizations: Part Two
3Min Read
By Wes Wright

Threat actors targeting identity management systems and medical devices put hospitals and healthcare organizations at risk. Our experts break down the recently published CISA threat mitigation guide to show how Ordr helps follow the recommendations. Whole hospital security means knowing every cyber asset in real-time detail
On November 20, 2023, the Cybersecurity Infrastructure and Security Agency (CISA) issued guidance for healthcare delivery organizations (HDOs) struggling to secure their data and systems against a growing and pernicious onslaught of attacks from threat actors across the globe. The purpose of CISA’s Mitigation Guide: Healthcare and Public Health (HPH) Sector is to articulate “best practices to combat pervasive cyber threats affecting the Healthcare and Public Health (HPH) Sector.”
We recently published our first blog that touched on Mitigation Strategy #1: Asset Management and Security, with important best practices around gaining visibility into what assets are actually on your network, and proactively implementing segmentation policies. In this installation of our three-part series, we look at CISA’s second Mitigation Strategy: Identity Management and Device Security and how Ordr helps healthcare organizations raise their security posture to meet the identified objectives.
Mitigation Strategy #2: Identity Management and Device Security
CISA observes that, “As the HPH Sector continues to transition more of its assets and systems online, CISA recommends entities secure their devices and digital accounts and manage their online access to protect sensitive data and PHI from compromise.” For many healthcare organizations that may seem like a daunting task. A typical mix of traditional IT, connected medical devices, building controls, and cloud-based services and applications can be difficult to inventory, manage, and secure–especially with traditional tools.
As the HPH Sector continues to transition more of its assets and systems online, CISA recommends entities secure their devices and digital accounts and manage their online access to protect sensitive data and PHI from compromise.”
To protect the network–and patient health–means first, discovery and classification of every asset, identifying vulnerabilities and threats, and profiling behavior and communications, and then securing every device. Ordr calls this the See, Know, Secure approach to “whole hospital” security . Let’s take a look at the focus areas CISA has identified in this section.
Focus Area 1: Email security and phishing prevention
CISA’s Mitigation Guide shifts focus from the importance of identifying and inventorying all of an enterprise’s assets, to executing against specific policies that in total, represent common attack vectors. CISA reports that more than 90% of all cyberattacks originate with email, so it makes sense that prioritizing email security would be at the top of this list. Whether a spray-and-pray approach to spamming an organization with messages containing weaponized links and attachments, or more targeted phishing campaigns, this is a first-line defense. Ordr can complement email security by identifying devices communicating to known malicious “phishing” sites, or identifying suspicious device behavior that may be an early indication of a compromised device.
Focus Area 2: Access management
Because users are one of the assets that Ordr tracks, we are able to help organizations with access management through robust tracking using AD/RADIUS and wireless integration, enabling security teams to monitor who is accessing what assets and when. That provides two key perspectives, including the time an asset was accessed and the session’s duration. This can help healthcare organizations recognize risks associated with poor cyber-hygiene such as password sharing, or leaving access to an asset open after a task is completed. The level of detail Ordr tracks and records can also prove invaluable during forensic investigations after an incident occurs.
Focus Area 3: Password policies
Too often assets are deployed with weak, default, or no passwords, leaving them vulnerable to threat actors. CISA recommends healthcare organizations observe a 15-character (minimum) password and to change factory defaults. Ordr customers benefit from our ability to identify and report assets operating with default or weak passwords so that security teams can change them in accordance with policy.
Focus Area 4: Data protection and loss prevention
Because Ordr provides granular details on every asset operating in the enterprise (make, model, serial number, operating system, and software version), we are able to help healthcare organizations identify–and apply appropriate policies–those assets that can store and/or transmit sensitive data like protected health information (PHI). What’s more, Ordr can track patching and disk encryption to maximize protection.
Focus Area 5: Device logs and monitoring solutions
Ordr Software Inventory Collector helps healthcare organizations comply with CISA recommendations on tracking assets and log data. By delivering granular asset details, including EDR installation status, version number, and active/inactive state, Ordr helps teams identify assets with out of date, disabled or missing EDR software while confirming whether devices are patched and communicating with the appropriate servers. This helps healthcare security teams to identify and close security gaps,and more quickly detect and respond to threats before they can succeed.
Stay Tuned for Part Three
In our next segment we’ll discuss CISA’s Mitigation Strategy #3 Vulnerability, Patch, and Configuration Management, and offer insights and approaches for achieving the goals of that portion of the Guide. The good news is, with the right tools, healthcare organizations can do what is needed with less trouble, cost, and complexity than they might think.
In the meantime, check out our new white paper, Mapping Ordr Capabilities to CISA Mitigation Guide: Healthcare and Public Health (HPH) Sector. It goes into greater detail of how the Ordr platform can be used to quickly and easily do what the CISA Mitigation Guide suggests, while serving as a roadmap for formulating a strategy to align organization policy with CISA guidelines.
Wes Wright
Chief Healthcare Officer
Wes is responsible for driving Ordr’s engagements in healthcare. Previously he was the CTO for Imprivata, and prior to that VP and CTO at Sutter Health, a 26 hospital network in Northern California. Prior to Sutter, Wes was CTO and then CIO at Seattle Childrens’, which, to this day, he says was his most gratifying work experience.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogGartner Names Ordr a Representative Vendor
BlogGartner Names Ordr a Representative Vendor…none of these devices were created with security in mind. With ubiquitous connectivity comes the increase in ways to exploit them to gain access to sensitive data. The convergence of…
Company News
Gartner Names Ordr a Representative Vendor
2021 Market Guide for Operational Technology Security
3Min Read
By Corin Imai

Read why Gartner Named Ordr Representative Vendor 2021 Market Guide for Operational Technology Security. More than a decade ago, operational technology (OT) was d only used in manufacturing and industrial environments and airgapped from the rest of the organization. Today, the convergence of information technology (IT) and OT, and the growth of the internet of things (IoT) is revolutionizing the way organizations monitor systems, share and analyze data, and efficiently make decisions based on near real-time information. While this transformation brought about a modernization of how IT, IoT, and OT systems share invaluable data to empower business operations, it also brought about the alarming realization that none of these devices were created with security in mind. With ubiquitous connectivity comes the increase in ways to exploit them to gain access to sensitive data.
The convergence of IT and OT calls for the need to address identifying all network connected devices, how they are communicating and properly assess the risk associated. This is why Gartner named Ordr as a Representative Vendor in the Market Guide for OT Security.
As described in the Gartner report, the OT/CPS (Cyber Physical Systems) security journey for organizations aligns with six key phases. “Once they enter the “Oh Wow!” Phase [3], organizations realize that security — whether IT, OT, physical or supply chain — needs a whole-of-enterprise focus. Historical IT and OT functional differences are becoming a liability when security is involved. Due to design, age or function, the unique requirements of OT systems now add to IT security concerns in ways that can no longer be ignored. Modernization efforts bring risk, reliability and safety discussions to the forefront. As a result, leading organizations are starting to elevate OT security requirements into their enterprise risk management (ERM) efforts by adopting an integrated security strategy across IT, OT, CPS, physical security and supply chain security.”
Phase 3. The “Oh Wow!” Moment: Invariably, proof of concepts (POCs) become eye openers. For example:
- Unmanaged assets are connected everywhere.
- OT networks that were initially designed to be highly segregated have become flatter than realized.
- Ports on all kinds of systems in all kinds of remote locations are wide open.
- OEMs are accessing the machines they sold remotely and no one is managing it.
- Disclosed vulnerabilities on old OSs have never been evaluated for possible patching.
- The functional silos between separate security disciplines (e.g., cybersecurity, physical security, supply chain security, product security, health and safety) are creating seams that bad actors can exploit.
- The realization sets in that operational environments where security is lacking are centers of value creation for most organizations; however, no centralized governance exists to start making sense of it all. Recognition develops that roles and responsibilities for a wide variety of (security related) processes and decisions have never been clear, let alone agreed on.
At Ordr we’ve helped top global organizations address visibility and security with a whole-enterprise approach — from traditional servers, workstations and PCs to IoT, IoMT and OT devices. We have created a solution that passively and in real-time discovers what devices are on the network, profiles device behavior and risks, and then automates the appropriate action. Our relationship with our customers has been one of mutual benefit, we have worked together to evolve our solution and address new use cases. As a result, we’re grateful and proud to serve our customers and be been named in the Market Guide for OT Security as a solution addressing device visibility and security.
Gartner Market Guide for Operational Technology Security, Katell Thielemann, Wam Voster, Barika Pace, Ruggero Contu,13th January 2021
Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner’s research organization and should not be construed as statements of fact. Gartner disclaims all warranties, express or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogLess is More – Not all Data is Equal
BlogLess is More – Not all Data is Equal…what they really want is information and knowledge that they can use within their current workflows. Connect Anything and Everything I like to talk about living in the era of…

Welcome to my first blog post with Ordr, which is hopefully the first of many. Here at Ordr we’re all about network-connected device information and providing insightful knowledge, however this comes in many forms. At its simplest form it could be data, binary, Boolean or it could even be a string, but what’s most important is its fidelity, accuracy and relevance. Globally, organizations are starting to truly embrace data, especially big-data, but they are starting to realize that they don’t want just data, what they really want is information and knowledge that they can use within their current workflows.
Connect Anything and Everything
I like to talk about living in the era of ‘connect anything and everything’; these connected devices across any wired or wireless infrastructure come in all shapes, sizes, flavors. More importantly there is a high variance historically in IT’s ability to correctly identify them and understand their risk and compliance status. In my first few months at Ordr, I had the opportunity to sit down with many customers to understand their needs. In short, our customers look to Ordr to provide valuable insights as to what is connected to their network, what exactly is that device, how it is behaving individually or compared to its peers and be able to identify those devices/endpoints that are misbehaving or perhaps possess vulnerabilities again, this is critical information and knowledge, not just data.
Ordr Data Lake for Device Enrichment
We pride ourselves on our foundational ability to identify all network-connected devices with a high degree of fidelity using deep packet inspection (DPI) to provide the insights that matter. Using the raw packet data from your network, we are able to classify all devices at-scale, then enrich that data in our Data Lake with various third-party data sources to turn it into the context that you need to help secure your infrastructure.
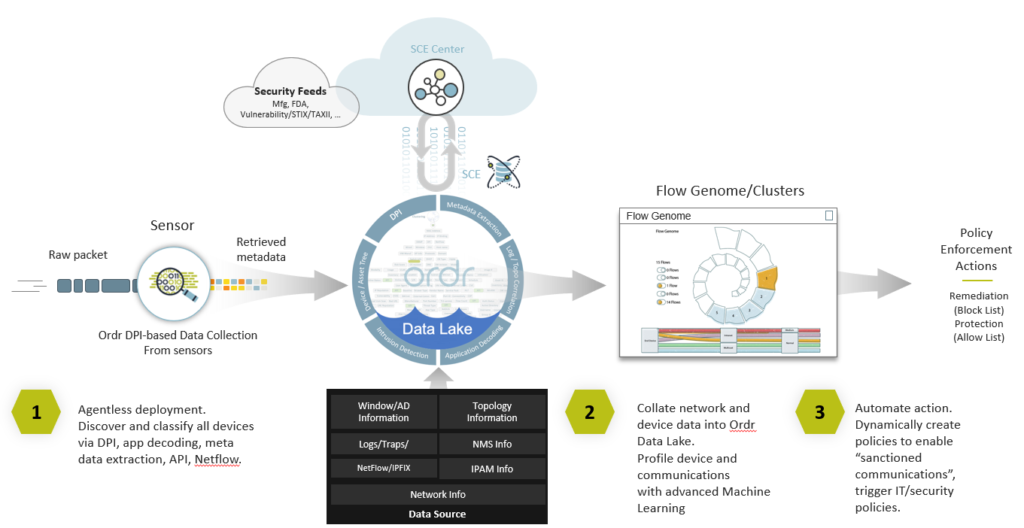
Part of my core responsibilities at Ordr is to expand the eco-system of integration partners. As we support more customer workflows, it is essential to allow more data into the Ordr Data-lLake for enrichment, but that data has to be of high trust and fidelity. That’s why we are embarking on adding a number of additional new integrations that provide us with unique contextual data to enrich our analysis and provide more insightful information and knowledge to our customers.
Integrations
In early 2021, we announced Ordr SCE 7.4.2, delivering more than 160 new features, integrations, and enhancements to provide unparalleled visibility and protection to organizations globally for security, IT, and HTM teams and their connected devices. In this release, we announced our integrations with Anomali, Exabeam, Fortinet, IBM QRadar, and Ping Identity. In this blog, I want to highlight the Anomali and Fortinet integrations, to give you an idea of the openness of our technology and the agnostic approach we are taking within the industry to ingest data or to use our device context to enrich or enforce policies in existing solutions:
- Anomali – Let’s start with Anomali, we worked with Anomali to ingest their STIX/TAXII 2.0 feed. Anomali consolidates various Cyber Threat Information (CTI) feeds and normalizes the data. Then, via a STIX/TAXII pull, Ordr is able to pull in the normalized data and enrich it with device context. The key to this is that we have built this using the very latest STIX/TAXII 2.1 standards. STIX/TAXII allows the sharing of CTI data. The CTI feed of data provides indicators of compromise, generally referred to as IOCs that allow Ordr SCE to find the needle in the haystack. The IOCs provide the bread-crumb-trail such that a vendor like Ordr can identify activity on the network that matches the signature of an IoC. This type of data is very targeted and is a true case of less is more.
- Fortinet – In contrast to the Anomali integration, which is very much an inbound ingest integration, our recent Fortinet integrations is primarily an outbound enforcement integration. We use AI and advanced machine learning, along with the Ordr Data Lake device context to create a complete Ordr Flow Genome profile of every device and its behavior. This baseline forms the foundation of segmentation policies to allow devices access while limiting exposure. We are leveraging the open API’s from FortiManager and FortiGate to enable Ordr to dynamically create and push out these enforcement policies. This can be to FortiGate firewalls or FortiNAC as an enforcement point. l said above it is primarily an outbound-based integration, but we also have the ability to consume basic traffic flow information from FortiGate to enhance and embellish the threat information we already have.
In the coming year, we are planning to implement additional inbound/outbound/bi-directional integrations for the benefit of our customers. As part of that process, we are constantly reviewing the integration use-cases developed to see where we can leverage more context to enable better device context.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogDiscovery and Segmentation: Keys to IoT Strategy Success
BlogDiscovery and Segmentation: Keys to IoT Strategy Success…inspires. Internet of Things Recently we’ve been using a lot of connected devices in the solutions we’re designing for our customers. The internet of things (IoT) includes a lot of…
Security Strategy
Discovery and Segmentation: Keys to IoT Strategy Success
3Min ReadBy Jason Malacko

Guest blog by Jason Malacko, Director Architecture – Security at Logicalis US
When you’re in the business of helping companies integrate and consume sophisticated technology, you learn that, behind all the questions related to how it works, there are two primary concerns: that it will be simple to use, and that it will deliver its promised value… fast.
At Logicalis we strive to make the complex simple. We recognize that our customers are too busy using technology and don’t want to worry about whether a service or application will be reliable or difficult. That’s why they hire us, after all. So, whether it’s a healthcare organization, manufacturer, state or local government agency, or whatever it is that your organization does, we approach every project as though we are architects of change for our customers, building a technology solution that doesn’t befuddle, but that inspires.
Internet of Things
Recently we’ve been using a lot of connected devices in the solutions we’re designing for our customers. The internet of things (IoT) includes a lot of wonderful tools that make operating a business more efficient and effective.
Think about a typical hospital, for example, and you get a sense of the ways IoT supports a mission of healing. Environmental controls keep temperatures where they need to be in every setting, and that air quality is always excellent. Building and security controls make sure people can get to where they need to go quickly, and that only authorized people are allowed in sensitive spaces; that video cameras keep a constant watch on the premises; and that lighting is on at the right level when it needs to be, and off when a space is vacant. There are devices that facilitate communications, IT operations, administrative duties. And, of course, there are a host of medical devices used to treat and monitor patients, provide therapy, and otherwise support medical staff as they care for the sick and injured.
All of these devices have important roles, but from a security and management perspective, they have to be treated very differently. Ordr has proven to be a valuable member of our partner network, supporting our top-down approach to IoT utilization in pursuit of this ideal.
When beginning a customer engagement, we’ve found that about ten percent of an organization’s devices are out of view of IT operations management. That means there are dozens or possibly hundreds of attack vectors somewhere in the network. It also helps to explain why only 26 percent of companies have launched an IoT initiative they consider to have been a success. That makes device discovery a critical first step in understanding, managing, and protecting the network, and to ensuring your IoT initiative does what you want it to do—with no unpleasant surprises.
Ordr Core
Ordr Core gives us the ability to open a customer’s eyes to the level of risk they didn’t realize they had, but it’s only the first step. Complete device discovery means we can begin the process of assessing risk, identifying device behavior, and categorizing each device’s purpose in the network. From there we can reconcile each device’s role, and implement policy automation to ensure proper device use as well as to implement a critical part of the IoT strategy: segmentation.
Device segmentation is an underappreciated aspect of IoT management and security. Done right, segmentation is about more than simply making sure certain categories of devices are on the right VLAN; it’s about aligning IoT use with security and business objectives. If all you’re doing to put segmentation into effect is grouping like assets—say, keeping medical devices, environmental controls, and facilities management equipment on their own VLANs—you may still be leaving your network vulnerable to attack and, once inside, allowing adversarial elements to quickly move laterally within the network.
Ordr Core excels as a tool that give our engineers the ability to work closely with our customers, show them their level of risk, and bring complex technical solutions with a reliance on IoT into alignment with their needs. When we’re able to do that, it gives our team and the customer confidence that our design will be simple to use, and that it will deliver its promised value… fast.
Want to experience Ordr in your network, request a free sensor here.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogIoT Sprawl – Tackling the Inevitable Tsunami of Cyber Threats
BlogIoT Sprawl – Tackling the Inevitable Tsunami of Cyber Threats…adoption of enterprise edge computing and 5G technology are key catalysts for organizations to optimize their businesses and create a competitive advantage. Additionally, COVID-19 has forced the hand of most…
Security Strategy
IoT Sprawl – Tackling the Inevitable Tsunami of Cyber Threats
2Min Read
By Harris Sussman

Corporate adoption of IoT has been under way for some time, but things are about to accelerate in a big way. The rapid adoption of enterprise edge computing and 5G technology are key catalysts for organizations to optimize their businesses and create a competitive advantage. Additionally, COVID-19 has forced the hand of most mid and large enterprises to further extend their network perimeters. This is being accomplished by rolling out secure teleworker solutions ensuring hundreds of millions of employees can remain productive during the pandemic.
As enterprise landscapes evolve, companies are grappling with how to adapt to the growing reality of new threat vectors. If past cyber-attacks are any indication, these exploits are merely a glimpse of what’s to come. Most businesses were already deficient in having a thorough cybersecurity posture, and the increasing number of IoT and unmanaged devices is further exacerbating that issue. Some of the most common vulnerabilities include weak passwords, outdated devices and unpatched software, misconfiguration of network devices, and a lack of device management to name a few.
Customers are demanding that cybersecurity vendors reduce complexity, incorporate existing vendors into new solutions and partner to attain maximum benefit. Ordr, the leader in visibility and security of all connected devices and Fortinet, a global leader in broad, integrated and automated cybersecurity solutions are partnering to deliver exactly what customers are seeking to accommodate the IoT device growth being predicted.
The combined integration of Ordr Systems Control Engine (SCE) with Fortinet’s Security Fabric delivers granular visibility and the automated control and response needed to thwart new threats resulting from the massive number of IoT devices emerging. Ordr is a vital member of the Fortinet Open Fabric Ecosystem, the premier technology partnering program in cyber security.
Evolving network architectures should incorporate the following key elements listed below, which are paramount in helping practitioners combat the onslaught of threats posed by new devices being added to the network.
The integrated solutions offered by Ordr and Fortinet are highly differentiated to deliver these critical features;- ML or machine learning is being used in network monitoring, gathering threat intel and remediation, while it is also being leveraged for identifying anomalous behavior and flagging these patterns in real time.
- ZTNA or Zero Trust Network Access has existed for more than 10 years, but has been perpetually modified. NIST (National Institute of Standards and Technology) continues to refine the ZTNA architecture. Three major components should exist in ZTNA including
- Continual visibility of devices and users connected to the network,
- Ability to enforce security policies despite devices type, location or method of access
- Ability to maintain enforcement and visibility when device goes off line
- Micro-segmentation is a security method that isolates security zones that are associated with workloads, applications and certain devices. By creating these zones, you can prevent lateral movement of threats from being propagated in east/west traffic and providing isolation and being able to prevent an attack.
Assessing your threat landscape for vulnerabilities must be an iterative process. The speed at which disruptive technologies are being adopted and the addition of billions of IoT connected devices to the internet, will warrant stronger “cyber-hygiene” including frequent cyber assessments and leveraging key partnership and tools for simplification. This endless battle warrants businesses to continuously refine how they address granular device visibility, control and how to appropriately respond to emerging threats.
Harris Sussman
Harris Sussman is the Director of Technology Alliances for Fortinet. Harris began his career in Network Engineering at Raytheon. With more than 20 year of experience at Cisco, Dell EMC, Akami and more, Harris has an amazing technical foundation. At Fortinet, Harris is responsible for Fortinet’s technology alliance relationships with OT (Operational Technology) and IoT (Internet of Things) partners.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?