Search Results:
”Role of Huawei H19-431_V1.0 Exam Questions in Getting the Highest-Paid Job 💆 Search for { H19-431_V1.0 } and download exam materials for free through [ www.pdfvce.com ] 🏸Premium H19-431_V1.0 Files”
-
Knowledge BaseThe Increasing Importance of Cybersecurity Asset Management
…may come and go as application instances spin up and down in response to fluctuations in demand, for instance, and cloud services may change their configurations continuously as they scale….
The Increasing Importance of Cybersecurity Asset Management
5Min ReadIn the world of cybersecurity, you can’t secure something if you don’t know it exists. That’s why cybersecurity asset management is a critical component to the foundation of cybersecurity operations across businesses of all types. By allowing your security team to maintain a real-time directory of IT assets—as well as the associated security risks—cybersecurity asset management is foundational to achieving a “whole enterprise” approach to a proactive, end-to-end, security strategy.
What is cybersecurity asset management?
Cybersecurity asset management is the process of identifying, on a continuous, real-time basis, the IT assets that your organization owns and the potential security risks or gaps that affect each one.
In this context, assets take many forms. They could be traditional devices, like PCs and servers. Or, they could be specialized IoT, IoMT, IIoT, or OT devices or software-defined resources, like a cloud-based database or a company-owned domain.
Any device, resource or service that exists within your IT estate could be subject to risks or vulnerabilities that lead to a breach of the individual resource and your network as a whole, in the event that attackers use one compromised resource as a beachhead to launch a broader attack.
Why is cybersecurity asset management important?
Cybersecurity asset management empowers your security team, as well as the overall business, with the visibility it needs to build a comprehensive security strategy that mitigates threats quickly and proactively. Such an approach delivers several key benefits:
- Cybersecurity is not a distraction: With a strong cybersecurity asset management process in place, businesses can deploy new IT services or resources without letting security become a distraction or hindrance. They can make decisions based on business priorities, confident that whichever changes they make, their cybersecurity asset management process will catch potential vulnerabilities.
- Proactive response: Cybersecurity asset management helps ensure that security teams detect threats before they evolve into serious problems. By continuously monitoring the IT estate for new deployments and risks, teams don’t have to wait until they detect an active attack in order to respond.
- Security visibility: If an attack does occur, cybersecurity asset management provides the security team with an inventory of assets and risks that it can use to gain context on what went wrong and when. Instead of having to reconstruct the state of resource deployments and configurations in order to research the origins of a breach or vulnerability, teams have an up-to-date record that they can refer to immediately.
In all of these ways, cybersecurity asset management places businesses in a stronger position to identify and react to security risks. Although cybersecurity asset management is only one component of an effective cybersecurity strategy, it’s impossible in most cases to maintain proactive security operations without cybersecurity asset management in place.
Risks associated with poor cybersecurity asset management
Lack of cybersecurity asset management, or poor implementation of it, does not merely make security operations more challenging. It creates critical risks for the overall business.
Chief among them is a higher risk of business disruptions. If essential data or systems are made unavailable by a breach, the business may not be able to operate. Not only will such disruptions harm the business’s reputation, but they also have serious financial consequences: IT downtime costs businesses $9,000 per minute on average.
Poor cybersecurity asset management also makes it difficult to maintain an continuous and accurate inventory of IT resources. Without knowing what exists where within your business’s IT estate, you are left guessing about where the most serious risks lie. Lack of certainty makes it difficult to deploy security resources efficiently or respond to issues when they arise.
Along similar lines, ineffective cybersecurity asset management undercuts security teams’ ability to operate efficiently. It’s difficult to automate security operations when you lack an accurate listing of which resources and risks exist. Instead, your team is left to find and secure devices manually, which is a poor use of time and money.
Examples of cybersecurity asset management
Because IT resources and security risks come in so many forms, cybersecurity asset management is a process that involves a variety of activities. The exact nature of cybersecurity asset management will vary from one organization to another depending on the types of resources at stake, but following are the cornerstones of the process for the typical business:
- Device discovery and protection: By identifying network endpoints and assessing each one for security vulnerabilities, teams can take immediate steps to address problems by, for example, segmenting insecure endpoints from the rest of the network.
- Vulnerability management: Cybersecurity asset management helps detect and address active vulnerabilities, such as unpatched software running on a device.
- Cloud security: Modern clouds are complex, multilayered environments that consist of a range of services and resource types. Cybersecurity asset management includes the identification of cloud resources that are vulnerable due to insecure software or lack of access control.
- Incident response: When an incident warrants further investigation, cybersecurity asset management plays a role in providing the incident response (IR) team with the information it needs to determine the root cause and remediate.
- Continuous policy enforcement: In the event that a resource violates security policies that your team has defined, cybersecurity asset management enables the rapid discovery and remediation of the problem. When new devices are added to the network that match a particular device profile with an active policy, they are automatically protected.
Remember that many of the resources described above change constantly. Network devices may come and go as application instances spin up and down in response to fluctuations in demand, for instance, and cloud services may change their configurations continuously as they scale. This is why cybersecurity asset management processes must be performed continuously and in real-time, in order to keep up to date with rapidly evolving environments.
Why prioritize cybersecurity asset management?
Historically, organizations placed little priority on cybersecurity asset management simply because the tools necessary to automate cybersecurity asset management processes didn’t exist. It wasn’t practical to maintain real-time and continuous inventories manually.
Thanks to the advent of automated resource discovery and threat identification tools, however, cybersecurity asset management now plays a major role in security operations across a variety of verticals. It’s critical not just for software and IT businesses, but for any organization that relies on software and hardware to power its operations—which virtually every business does today, given that every company is now a technology company.
In manufacturing, for instance, cybersecurity asset management helps ensure that high-value equipment, such as plant control systems, diagnostics and monitoring systems, and machine sensors, remain secure and free of threats that could disrupt operations.
Likewise, cybersecurity asset management protects healthcare organizations, which face high rates of ransomware attacks as well as vulnerabilities that may exist within specialized devices deployed as part of the Internet of Medical Things, or IoMT.
More generally, any enterprise that deploys connected devices to help manage or monitor physical infrastructure, collect business data or extend networks into spaces where conventional infrastructure can’t reach needs cybersecurity asset management to keep those devices—and, by extension, the business as a whole—secure.
How to capitalize on cybersecurity asset management
To deliver fully on its promise, cybersecurity asset management requires the implementation of multiple processes. Businesses must be able to identify, assess and address the security risks posed by devices and assets of all types while taking proactive steps to protect their devices, networks and data. They must also discover and track assets in real time, perform continuous risk assessment and immediately segment untrusted assets from the rest of the network.
The Ordr Systems Control Engine (SCE) gives organizations the tooling they need to automate cybersecurity asset management at scale. Ordr SCE provides holistic visibility and security into network-connected devices, offering a powerful solution to identify, classify and evaluate every network-connected device, then automates steps to remediate risks.
What’s more, Ordr SCE allows security and IT teams to create proactive microsegmentation policies for every class of device in order to control communications and mitigate potential risks.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogA Closer Look at Ordr’s Commitment to Security: The SOC 2 Journey
BlogA Closer Look at Ordr’s Commitment to Security: The SOC 2 Journey…gaps and understanding the context of data flows and device operations that allow us to deliver the highest level of security possible. Ordr takes pride in providing these services and…
Company News
A Closer Look at Ordr’s Commitment to Security: The SOC 2 Journey
4Min Read
By Pandian Gnanaprakasam

It is important that our organization is as secure as the products we make. That’s why we value SOC2 certification. Take a Closer Look at Ordr’s Commitment to Security, SOC 2 implementation journey, and why it validates our commitment to data security and provides benefits to all enterprises. A special blog for October Cybersecurity Awareness Month
In an era where data security is paramount, we at Ordr, specializing in comprehensive security solutions for connected devices, prioritize safeguarding customer information as a core mission. One pivotal step Ordr has taken in securing data is earning SOC 2 compliance with a specific focus on Organizational Governance and Structure. I want to use this blog to delve into what our SOC 2 implementation journey means, how we steadfastly uphold our commitment to data security, and the significant benefits this provides to both our internal operations and customers.
Why is SOC2 Critical?
Service Organization Control 2, or SOC 2, is a widely recognized framework designed to assess and report on customer data’s security, availability, processing integrity, confidentiality, and privacy. It is a rigorous set of standards that validate an organization’s dedication to safeguarding sensitive information. By going through the process, SOC 2 certification validates:
- Ordr’s ability to connect people, process, and technology to provide the services continuously.
- Ordr’s ability to provide response during a critical security event.
- Ordr’s ability to provide services in case of failure to the hosted data center with no impact to customers.
Those validations are important to us and for those organizations that put their trust in us. Ordr allows its customers to gain visibility into their complete attack surface. We do this by collecting a wealth of information from the infrastructures where Ordr is deployed. That data is critical for closing visibility gaps and understanding the context of data flows and device operations that allow us to deliver the highest level of security possible. Ordr takes pride in providing these services and makes data security a paramount requirement. We at believe these are core components to any SaaS solution and should be tested once a year to make sure all the above-mentioned factors are in sync.
[SOC 2] validations are important to us and for those organizations that put their trust in us.“
Our SOC2 Journey
Our SOC 2 compliance journey has been ongoing for the last several years, and each year the scope has expanded. Our commitment is not limited to specific aspects of our operations; it encompasses the entire development process, our entire employee population from onboarding to continuous training, and our customer onboarding and training processes. This comprehensive approach demonstrates our unwavering dedication to protecting our customers’ sensitive information.
- Change Management: Our meticulous change management processes translate to a reduced risk of service disruptions, ensuring the uninterrupted operation of critical services for our customers.
- Risk Management: By systematically identifying and mitigating potential security threats and vulnerabilities using a risk registry, we enhance the safety of our customer’s data and services.
- Vendor Management: Customers benefit from our rigorous vendor management practices, which assure them of the security standards upheld by third-party vendors, going above and beyond merely reviewing vendor certifications like SOC 2.
- User Access Management: Enhanced user access controls mean customer data remains accessible only to authorized personnel, minimizing the risk of unauthorized access.
- Data Storage: Secure data storage practices give our customers confidence in protecting their sensitive information, safeguarding it from breaches and unauthorized access.
- Hiring, Onboarding, and Employee Training: Customers benefit from a workforce that is not only vetted but also continuously trained to uphold the highest standards of security, thus reducing the risk of insider threats.
- Incident Management: Well-documented and tested incident response plans mean that potential security incidents are swiftly and effectively handled, minimizing the impact on customer operations.
- Logical Access: Enhanced logical access controls reduce the risk of data breaches or unauthorized access to customer systems and data.
- Endpoint Security: The bolstered endpoint security ensures that our devices and endpoints are safeguarded against malware, viruses, and other security threats, reducing the risk of service disruptions or data compromise.
- Data Resiliency: This allows Ordr’s service to run from another data center in case of failure to the primary data center and it means we are able to maintain SLA commitments provided in customer contracts.
Our commitment to SOC 2 compliance extends to additional rigorous controls. Every code commit undergoes a security review by an expert separate from the developer and code reviewer, ensuring that security considerations are meticulously addressed. We regularly test data resiliency between cloud locations for seamless failover, and we scrutinize every laptop for compliance with policies like firewall, encryption, and the presence of endpoint detection and response (EDR) and mobile device management (MDM) solutions.
When done right, with a diligent auditor that is allowed go through every employee, every customer, every line of code, every vendor, the SOC 2 process is more than worthwhile.”
Our auditor, Geels Norton (BTW, highly recommended), is renowned for their diligence in auditing. Instead of reducing scope, we have consistently accepted a broader scope and higher standards by Geels Norton and actively strive to achieve and maintain these elevated security levels.
SOC 2 Does Matter
I am very aware of the ongoing and vigorous debate about the value of earning SOC 2 certification, that it is a waste of time, that organizations are finding ways to water-down the process and that, as a result, the process has become little more than window dressing. We take the opposite view. When done right, with a diligent auditor that is allowed go through every employee, every customer, every line of code, every vendor, the (painful) process is more than worthwhile. It gives an organization the information it needs to beef up controls and quantify its performance. Done right, SOC 2 demonstrates a top-to-bottom commitment to security.
Ordr’s achievement of SOC 2 compliance in Organizational Governance and Structure underscores our enduring commitment to security. We continue to vigilantly monitor our systems and processes, ensuring they comply with SOC 2 standards. Furthermore, we remain steadfast in our commitment to optimizing our security posture, proactively staying ahead of emerging threats, and ensuring that our customers can trust us with the highest level of data protection.
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogConnected Devices Conspicuously Absent
BlogConnected Devices Conspicuously Absent…68% of breaches,” and that financial gain was the motive in 98% of attacks on the industry. In manufacturing we learned that “system intrusion, social engineering, [and] basic web application…
General
Connected Devices Conspicuously Absent
2023 Verizon Data Breach Investigations Report (DBIR)
4Min Read
By Danelle Au

The 2023 Verizon Data Breach Investigations Report (VDBIR) is notable because of the lack of references to the risks associated with connected devices (IoT, OT, etc.) despite the role they play as attack vector, path, or target. The 2023 Verizon Data Breach Investigations Report is out. Like most folks in the cybersecurity industry, we downloaded it and pored over the contents to see what was new and relevant and surprising. As always, there’s a lot of data that quantifies the issues we see everyday: ransomware attacks, social engineering, underlying factors, threat types, etc. For example, the summary of findings identified external actors as the top threat involved in 83% of breaches; said that human error plays a role in 74% of all breaches; and reported that 24% of attacks involve ransomware; and broke down credential theft, phishing, and exploitation of vulnerabilities as the three primary means of attack.
Digging Deeper
Then we gravitated toward findings specific to the industries that Ordr is focused on and that have embraced our technology as a part of their cybersecurity strategies.
- In financial services and insurance, we learned that “basic web application attacks, miscellaneous errors, and system intrusion represent 77% of breaches,” and that financial gain was the motive in 97% of attacks on the industry.
- In healthcare we learned that “system intrusion, basic web application attacks, and miscellaneous errors represent 68% of breaches,” and that financial gain was the motive in 98% of attacks on the industry.
- In manufacturing we learned that “system intrusion, social engineering, [and] basic web application attacks represent 83% of breaches,” and that financial gain was the motive in 96% of attacks on the industry.
Similar results were reported down the line in accommodation and food services, education services, government, IT and so on. Threat actors want money, they are good at finding ways into networks where they aren’t welcome, and whether by their intent, neglect, or error, people inside of breached organizations are a reliable source of help. Each data point illuminates and confirms issues we all intuitively recognize as true.
Threat actors want money, they are good at finding ways into networks where they aren’t welcome, and whether by their intent, neglect, or error, people inside of breached organizations are a reliable source of help.”
Then we started looking deeper. Our focus at Ordr is on protecting enterprises by securing the growing number of connected devices at work in enterprises across the globe, in every industry. These include categories like the Internet of Things (IoT), Internet of Medical Things (IoMT), Industrial Internet of Things (IIoT), Operational Technology (OT), and the many devices connecting to networks to perform new and exciting tasks in a variety of niche roles (XIoT).
A Threat to Health and Safety
The risks that unsecured devices present to the organizations that own them are well known, and the implications of attacks affecting them are troubling. In healthcare, for example, attacks may have financial motives, as the VDBIR says. But recent research by the Ponemon Institute found that cyberattacks on hospitals correlated to an increase in negative outcomes for patients in 57% of hospitals affected due to delays in performing needed tests and procedures. The problem is so severe that hospitals with no means of protecting the medical devices integral to the delivery of patient care are training staff in “code dark” response, which is the physical unplugging and disconnecting of at-risk systems.
The problem is so severe that hospitals with no means of protecting the medical devices are training staff in ‘code dark’ response, which is the physical unplugging and disconnecting of at-risk systems.”
The dangers associated with vulnerable IoT, IoMT, and OT devices, and the risks they pose to not only critical infrastructure but financial services, manufacturing, and smart cities, are so concerning to our economic and physical security that connected devices are a part of the White House’s National Cybersecurity Strategy, called out in “Strategic Objective 3.2: Drive the Development of Secure IoT Devices.” The FDA has also issued a mandate to ensure new devices entering the market are built to be secure. And over in the UK connected device security is called out as part of that country’s new National Health Services cybersecurity strategy.
Despite the real and troubling issues associated with IoT security, there is no mention of them in the 2023 VDBIR. And OT security is dismissed with the explanation that “we continue to see [a] very small numbers of incidents involving Operational Technology (OT), where the computers interface with heavy machinery and critical infrastructure,” in contrast to the volume of attacks on traditional IT systems.
Vector, Path, or Target
It is worth pointing out that even if IoT, IoMT, and OT are not the initial vector of attack, such systems may be the target of an attack, or used as a path of attack as threat actors, once inside a network, move laterally to their intended destination. It could also be that, because the VDBIR takes a broad and high-level view of the data they collect, the presence of IoT in the report is simply buried in the data. Or maybe it is not known that connected devices are involved. Our analysis following the discovery of devices connected and operating on customer networks shows that as many as 15% of those devices were unknown to IT security and management prior to deployment of Ordr. You can’t secure what you can’t see, and so an attack in which an unknown, vulnerable, and unsecured connected device was the primary vector would also be invisible to security analysts.
More likely is that attacks involving IoT, IoMT, or OT devices are probably too granular a detail to be called out specifically in any report based on broad security analysis. But that doesn’t mean the risk isn’t real, and that the potential effects of an attack involving connected devices are not dire. They are, and that is why we built the Ordr platform to see, know, and secure every device in any network.
Danelle Au
Danelle Au has more than 20 years of experience bringing new technologies to market. Prior to Ordr, she was CMO at Blue Hexagon, a deep learning for malware protection company, and CMO at SafeBreach where she helped build the marketing organization and and define the Breach and Attack Simulation category. Previously, she led strategy and marketing at Adallom, a cloud security company acquired by Microsoft. She was also Director, Security Solutions at Palo Alto Networks, driving growth in critical IT initiatives like virtualization, network segmentation and mobility. Danelle was co-founder of a high-speed networking chipset startup, co-author of an IP Communications Book and holds 2 U.S. Patents. She has an MSEE from UC Berkeley
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 NewsOrdr Improves Visibility, Security & Management of Connected Devices
NewsOrdr Improves Visibility, Security & Management of Connected Devices…integrations announced in Ordr 8.1 enable the following: Asset discovery and visibility in public and private clouds – Completely understand how on premise devices are communicating with assets in cloud…
Ordr Improves Visibility, Security & Management of Connected Devices
From Ground To Cloud
5Min ReadSanta Clara, CA – September 21, 2022 – Ordr, the leader in connected device security, today announced new capabilities and enhancements to its AI-powered platform to help organizations discover, gain essential context, and secure their connected devices everywhere.
New integrations expand the more than 80 integrations within the Ordr Data Lake, to empower organizations with a single source of truth about connected devices and assets in their on-prem, remote, data center, private, public, and hybrid cloud environments. In addition, enhancements have been made to Ordr’s automated segmentation capabilities that help organizations accelerate and scale adoption of a true Zero Trust security posture to protect every connected device.
“Gaining visibility and control across an organization’s entire attack surface of connected assets, is one of the most fundamentally important – yet challenging – tasks facing IT and security teams today,” said Pandian Gnanaprakasam, Chief Product Officer and co-founder of Ordr. “The latest additions to our industry-leading platform will deliver complete ground to cloud visibility – from assets in remote sites, and campus devices, all the way to assets in the cloud. This “whole hospital” or “whole enterprise” approach to security, ensures that no device or connection remains unknown. We’ve also added the ability to more efficiently define and enforce segmentation to accelerate Zero Trust initiatives.”
New Ordr Ecosystem Integrations and Partnerships
The increasing growth of cloud adoption adds a visibility black hole, making it difficult to fully understand how devices are connecting – and what those devices are actually communicating with in the cloud. This increases the risk factors of connected devices exponentially. Ordr 8.1 gives organizations comprehensive visibility into their entire attack surface, from ground to cloud.“Ordr’s coverage from day one has been excellent, being able to see all connected devices with their whole enterprise and whole hospital approach. Cloud coverage adds a critical new layer of visibility and protection for all organizations,” said Michael Grall, president and CEO, Talus Solutions. “Ordr works closely with its customers, who are some of the largest enterprises and healthcare providers in the country, so you know this solves a real problem. The new integrations are a good leading indicator of challenges organizations face, and Ordr is defining how connected device security needs to continue to evolve.”
Ordr now supports more than 80 integrations. New partnerships and technology integrations announced in Ordr 8.1 enable the following:
- Asset discovery and visibility in public and private clouds – Completely understand how on premise devices are communicating with assets in cloud environments.
- AWS – Workloads running in Amazon Web Services (AWS) environments are now visible to organizations using Ordr. Ordr AMI sensor support is also available as part of this release to provide additional insights into AWS workloads.
- VMware – Extend visibility to VMware workloads running in public, private, and hybrid cloud environments.
- Network discovery – Automatically discover, classify, and gain context for every connected device on the network. Granular device insights are combined with network details to ensure every discovered device is accurately identified, mapped to its current location, and properly secured.
- Arista – Collect connectivity data from Arista devices, adding to an already broad portfolio of network infrastructure integrations.
- Cisco Prime – Expand Cisco Prime integration with multi-instance support to gain connected device details such as physical location, device name, and network.
- ERSPAN – Extend and optimize Ordr to discover and secure devices in remote sites.
- Ordr Data Lake enrichment – Integrate with more than 80 tools across the IT infrastructure to gather and enrich connected device details, establishing a single source of truth. Gain a much more complete picture of networks, devices, and the context required to identify risk, quickly respond to threats, and stop attacks. Ordr 8.1 integrations include:
- BigFix – Improve device insights with additional context such as location, users, vulnerabilities, and the patch state of endpoints.
- Microsoft DHCP/DNS – Track DHCP assignments to devices for an accurate view of IP address bindings, increasing the fidelity and accuracy of Ordr insights.
- Osquery – Enable organizations adopting open-source Osquery endpoint agents to collect details from Linux, Windows, and macOS devices using custom query packs.
- CrowdStrike – See every managed connected device, identify unmanaged devices, and know more about device vulnerabilities and risk combining Ordr insights with CrowdStrike security data.
- Service Integration page – Manage all Ordr integrations from a new simplified and informative central page in the Ordr Dashboard.
Other recently announced capabilities that enrich the Ordr Data Lake includes Ordr’s own Software Inventory Collector, that simplifies device context collection, particularly installed software and patch data.
“Software Inventory Collector gives us a view of devices and potential threats that has been nearly impossible to keep current,” said Christina Cucchetti, IS&P Operations Specialist from Nexteer Automotive. “We now have a centralized, real-time view of risk for devices across all our sites, while team members that previously spent hours manually collecting device details can focus on patching critical vulnerabilities and protecting our operations.”
Enhanced Automated Segmentation Capabilities
Organizations have struggled to achieve a true Zero Trust security posture because they lack insights needed to understand their connected devices and create appropriate security policies. Many connected devices are unmanaged or un-agentable, and have unique communication requirements. To truly achieve Zero Trust, organizations need deep visibility into connected devices – to understand how and what they’re communicating with – in order to to define, manage, and enforce segmentation.Ordr collects and learns details needed to provide insights and automate policy creation in support of Zero Trust efforts. This includes discovering and automatically classifying each connected device – and analyzing device communications to establish a baseline for normal activity. With these insights, Ordr automatically creates reactive policies to stop attacks – as well as proactive segmentation policies to improve security.
“Ordr provides the visibility and context into all connected devices to advance our segmentation journey with Cisco ISE,” said Shawn Fletcher, Senior Systems Administrator, St. Joseph’s Healthcare Hamilton. “Ordr greatly simplifies policy administration by providing accurate device baselines that can be generated, tuned, and enforced on groups or individual devices. Ordr responded to our compliance needs with the enhanced Policy Editor and new capabilities such as the Ordr Policy Optimizer which are making it easier to automate and expand Zero Trust across our environment.”
“The power of the Ordr platform has always been its ability to automate device classification and behavioral modeling using AI. This is foundational to our Zero Trust and segmentation strategy. The feature enhancements in Ordr 8.1 will further simplify and optimize how we create and enforce segmentation policies for every connected device,” said Larry Smith, Manager, Cybersecurity Architecture and Engineering, El Camino Health.
Key segmentation features of Ordr 8.1 include:
- Automated policy creation and customization – Some device communications are infrequent, such as those related to backups or disaster recovery, and need to be accounted for when defining policies – or risk being blocked outright. Additionally, administrative requirements, common services, and other allowed activity must be taken into consideration when creating policies. With new tools such as Ordr Policy Editor, Ordr automated policies can be customized to meet business needs or account for unique requirements.
- Segmentation policy optimization – Segmentation policies must be reviewed and adjusted to ensure they provide the intended result in an optimized way and can be adapted to new requirements as needed. At the same time, overly complex policies can impact resources such as enforcement and management. New features such as the Ordr Policy Optimizer automatically compress policies, reducing policy size and complexity and making it easier to create, maintain, and enforce.
- Enforcement scaling – Enforcement points have finite resources – and must process every line of a policy – impacting performance and restricting the number of rules that can be supported. In addition, in large, complex environments, it can be challenging to support enforcement points from different vendors. With Ordr Policy Sharding, policies are automatically separated based on where enforcement or segmentation occurs, making them easier to manage and deploy. With support for enforcement point APIs or other enforcement point mechanisms, Ordr simplifies the distribution and enforcement of policies optimized for your infrastructure.
For more information about how Ordr can help security and IT teams deliver visibility and security for their connected devices, from ground to cloud, please visit www.ordr.net.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
- Asset discovery and visibility in public and private clouds – Completely understand how on premise devices are communicating with assets in cloud environments.
-
 BlogActionable Asset Insights: The Missing Piece In XDR
BlogActionable Asset Insights: The Missing Piece In XDR…the value of XDR and for organizations to embrace the means of seeing across IT infrastructure to take a complete inventory of all network assets and gain a deep understanding…
Blog
Actionable Asset Insights: The Missing Piece In XDR
Visibility Alone is Not Enough
4Min Read
By Srinivas Loke
Extended detection and response (XDR) is not a new concept in cybersecurity even if the category name was recently coined. The renewed focus means XDR gets a lot of attention, and that’s a good thing for the industry. Good data and analytics have long been known to be vital to assessing risks, identifying threats, and repelling attacks; but the challenge lies in collecting, analyzing, and using the resulting insights in a timely manner. Things move fast in today’s technology enterprises and so anything less than real-time is obsolete. Fortunately, capability has caught up with need in recent years and further cybersecurity innovation drives continued progress.
Gartner describes XDR as an approach to security that “focuses on detecting and responding to threats through increased visibility on networks, cloud, endpoints and other components.” The key phrase in that definition is “increased visibility,” because to know what’s happening in the network requires seeing every nook and cranny of the network. I’ll add to that and argue that visibility has to be “actionable,” meaning it isn’t just about seeing that something is lurking around, but about gaining a deep understanding of where threat actors can hide, move, and do their dirty work undetected.
Gaining Actionable Asset Visibility
As Gartner’s definition implies, when an organization’s IT infrastructure extends from a physical main campus to include facilities distributed across wide geographies and interconnected via the cloud, things get complicated. Then there are many systems comprising the IT estate, including a proliferation of connected assets like Internet of Things (IoT) and Operational Technology (OT). Those assets come with increased risk since they may be installed and managed by teams outside of cybersecurity, and are unknown or operate undetected.
Our analysis of enterprise IT environments shows that the average attack surface comprises about 40% connected assets, and that as many as 20% of those devices are unmanaged or unknown assets. That creates a challenge for security teams because unknown devices represent a potential attack vector or path. Even devices that can be detected may only show up as a nondescript user device because they run a common operating system and can’t be fully identified using software agents or by a simple scan of the network. But even gaining more visibility isn’t much good if you don’t have a precise understanding of all devices. Without that rich, actionable device intelligence you can’t identify vulnerabilities and adequately protect the enterprise.
Threat actors know this, and they eagerly exploit the gaps in an organization’s asset visibility and intelligence. In fact, Microsoft uncovered a “a sophisticated attack campaign” targeting IoT devices that allows “attackers to hijack SSH credentials, move laterally within networks and conceal malicious SSH connections.” This is the type of activity that XDR could potentially detect and prevent, but only when the data used in XDR analysis is gathered from all assets connected to the network, including those operating in the shadows. That data must include things like device location, business purpose, normal operational parameters, industry-specific threat intelligence, known vulnerabilities, and other in-depth information that can’t be gleaned from typical discovery and monitoring methods.
Averting Hidden Threats
Another threat that has been in the headlines recently, and that capabilities consistent with an XDR approach to security could help to avert, is that of assets and systems that are at risk of exploitation because of vulnerabilities in their software makeup or improper installation.
Last year it was revealed that the cl0p ransomware gang began an attack campaign against Progress Software’s popular managed file transfer (MFT) platform MOVEit, exploiting a weakness that made the product vulnerable to attacks and allowing unauthenticated parties to control its installation, potentially leading to data alteration or theft, malicious software installation, and server configuration changes.
The situation was discovered in late May of 2023 when someone noticed anomalous activity involving their organization’s MOVEit instance and alerted Progress. A fix was issued within a few days, but despite the rapid patch release, the attack—two years in the making—was quick to unfold and breach disclosures soon followed. Today independent GRC analyst and research firm KonResearch says the attack breached more than 2,600 organizations affecting nearly 90 million people.
It’s worth pointing out that the attack was revealed because a customer happened to notice operational anomalies and, digging deeper, discovered suspicious activity. This illustrates the importance of maximizing contextual visibility into all enterprise assets. When the MOVEit instance acted in a way that was unexpected, it prompted an investigation and that led to the discovery of an attack. MOVEit’s primary function is to send and receive data, usually large amounts of important, regulated data. If a threat actor manages to gain control of a product like that, it can be devastating, transforming MFT software into an ideal platform for data theft and exfiltration.
Accelerating Detection and Response
The objective of XDR is to enable better detection and response. Integrating assets and context visibility into an XDR tool accelerates the process identifying anomalies within the network. Most network assets operate within a determinative range and this baseline “normal activity or communications pattern” can be identified and analyzed by using artificial intelligence. If an organization detects abnormal device activity straying beyond the range of expected behavior, it may be an early indicator of a compromise. This means policies and responses can be automated to quickly quarantine the device. This is the value of XDR, but it can only function at a high level when there is complete visibility into assets and their context.
There is a trend toward increasing asset visibility and enabling capabilities consistent with extended detection and response. When the U.S. Cybersecurity Infrastructure & Security Agency (CISA) issued Binding Operational Directive 23-01: Improving Asset Visibility and Vulnerability Detection on Federal Networks in October 2022, it stated, “Continuous and comprehensive asset visibility is a basic precondition for any organization to effectively manage cybersecurity risk.” That is a strong endorsement for the value of XDR and for organizations to embrace the means of seeing across IT infrastructure to take a complete inventory of all network assets and gain a deep understanding of context and communications flows that can lead to vastly improved security.
Maximizing XDR Efficacy
To maximize the efficacy of your organization’s XDR implementation, you must feed your XDR platform with rich, accurate, and relevant data from trusted sources, including:
- Rich device data from all connected assets
- Real-time device communications flows
- Threat intelligence feeds
- Security monitoring tools
- Up-to-date CMDB
Ordr can discover and identify all connected assets in the enterprise inventory, providing unmatched detail on millions of devices through the Ordr Data Lake, monitoring and analyzing their communications flows in the context of your specific business risk profile. Contact us to learn how the integration across all security and IT operations tools offers an ideal complement to any XDR platform to support the best possible threat detection and response.
Srinivas Loke
Srinivas Loke is Vice President of Product Management at Ordr. Srinivas has a passion for cybersecurity with a deep understanding of network, end point, cloud and IoT security. Prior to Ordr, he led product teams at Aruba, Pulse Secure, FireEye and McAfee. He loves taking 1.0 products to the market and furthering cutting edge technologies that are solving customer problems.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogThe Six Levels of Enterprise Asset Control
BlogThe Six Levels of Enterprise Asset Control…equipment and devices oftentimes might not really have full visibility into all their assets. Some medical systems go through mergers or divestitures and its often difficult to find all the…

There are 6 levels of control for managing network security. Device control, vulnerability control, network control, behavior control, external communications control, and application and user control. Knowing them is essential for cybersecurity. The Six Levels of Control
Aristotle, born in 384 BC, had some specific thoughts on how to formulate dramatic stories that have lasted to this day. Screenwriters still rely on its basic framework. In “Poetics”, Aristotle wrote that drama has to include a simple structure where there is always a beginning, a middle, and an end tied together with a unity of theme and purpose. Aristotle’s “Poetics” discusses further how there are six elements for a drama to be cohesive and coherent. There is a plot, character, thought, diction, music, and spectacle. A compelling story, an interesting hero, a theme, the tone, clear music and something memorable to tie it all together, it’s a formula that has stood the test of time.
Similarly, we see security in a proactive and holistic framework with six elements, in this case, six levels of control. It’s a cohesive framework which ties everything together it’s comprehensive and it ties everything together. Our six levels of control include Devices, Vulnerability, Network, Behavior, External Communications, and Application & User Control. Taken by each element alone there is some value but it’s the overall cohesiveness that makes for unity when it comes to proactive protection. Here’s our take on the six elements of control:
Device Control
First off is device control. Before we implement any security measure it helps to know exactly what we have. Hospitals with all the equipment and devices oftentimes might not really have full visibility into all their assets. Some medical systems go through mergers or divestitures and its often difficult to find all the equipment, let alone which infusion pump or MRI machine is being utilized or not.
At Ordr we do device visibility comprehensively, getting all the nitty-gritty details such as the make, model, serial number and modalities of all the assets connected to the network. Once the data is collected, it’s important to know where the devices are actually connected and we can pinpoint the exact location and even the port to where something is plugged in.
Vulnerability Control
Unpatched software and outdated operating systems can leave you vulnerable and we can tell you exactly what device needs upgrading or patching. Sometimes equipment or devices may be hiding somewhere but if it does end up being connected and starts communicating with the network, we will see it and let you know.
The problem with software versions is that there are so many upgrades to keep track of. Lingering old Windows 7 machines can be a problem since its no longer supported and we can tell you exactly which machines you need to keep track of. When we find these Windows 7 devices, we can segment it and keep its traffic within its own zone away from the regular traffic.
Network Control
The boundaries for many hospital networks are now blurred and stationary perimeter firewall protecting us from all attacks is no longer the rule. Malware can be downloaded to many devices often unintentionally by remote or telecommuting workers and damage can occur when someone reconnects to the corporate network.
Malware, once it gets in, is often programmed to perform reconnaissance and to understand devices that are near its proximity so that it can spread. This unusual side to side movement in the network is what you need to stop and contain right away before it does any harm.
Behavior Control
I’m not a psychiatrist but I know abnormal behavior when I see it. Likewise in a hospital, we know what each and every medical device should be doing and how they should act. Whether its sending images and video streams to the video servers at the data center for a camera for example or an MRI machine being accessed by lab technicians at specific times.
If there is any deviation from normal behavior, we can sound the alert. And it’s not just the changes from the daily routine that we can see, our engine can monitor how each device acts in a normal setting relative to its peer group. A thermostat talking to the finance department, that should not happen. Some traffic flow trying to disable security controls or install rootkits? We will shut it down.
External Communications Control
Traffic to certain countries should raise alarms. If someone clicks a URL and there is traffic flow to Iran, Syria, or North Korea, there could be trouble brewing and it’s something you need to know about right away. Even within the U.S., there might be well-intended sites but it can be a trap for ransomware. Now going to a different country, that is fine its just specific suspicious ones that we block proactively.
A fortified firewall is one thing but with so many RDP sessions, many of which are not closed after a remote session, and with no one actively monitoring all these sessions, a corporation can be left unprotected. As a remedy, we work hand in hand with existing firewalls as we make the firewall even smarter by providing the context behind each IP traffic, understanding what the device is and what it is doing when it ventures out to an external website. Policy updates are written automatically to that firewall, providing security managers the added peace of mind.
Application and User control
There are supervisory command applications such as Telnet, FTP, SSH, SNMP, and others. As an example, SSH works by enabling secure system administration and file transfers over insecure networks. Uses encryption to secure the connection between a client and a server. All user authentication, commands, outputs, and file transfers are encrypted to protect against attacks in the network. SSH and other command applications are used to operate and debug and fix things and we can help you keep track of all these sessions.
Understanding applications is one thing but what’s also important is to understand the flow and what is actually happening within the session. If there is a regular port 22 session with a known device that is fine but we proactively ring the alarm if the SSH session is coming from a different or even worse an unknown un-authorized person. Since plain text authentication can be readily stolen and be used to extricate massive amounts of sensitive data, we can alert you right away if there is any use of an insecure protocol and/or any extraction of any data. We can further add controls to only those who are allowed to access the data.
Proactive and Comprehensive Security, Aristotle will be Proud
At Ordr we take a holistic view of security understanding the granular details of control and having a system that learns and adapts. “We are what we repeatedly do. Excellence, then, is not an act, but a habit” said, Aristotle. Devices, Vulnerability, Network, Behavior, External Communications, and Application & User Control it all fits together with the Ordr framework and this is what we do.
Thoughtful details of traffic sessions and flow genome are factored in our engine and we ingest more information every day repeatedly to make our system smarter as we strive for excellence. Take control with Ordr.
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogMaking the Friendly Skies Safe
BlogMaking the Friendly Skies Safe…information including private passport and credit card data-valuable information for cyber-criminals. The other issue is that the airlines often connect disparate systems and networks together which can open the door for…

It’s not that commercial airlines don’t have enough trouble keeping planes on schedule and passengers happy. Now they must also worry about cybersecurity. How can they (and you) protect their networks as attack surfaces grow larger and more complex? The winter weather, high fuel prices, customer complaints, and bad publicity for dragging a passenger off an overbooked flight are some of the worries that can keep an airline executive up at night. Add to this list the rising concern of cyber-attacks and many CSOs of airlines wish they were vacationing instead in an overwater bungalow in Bora Bora.
Why are airlines being attacked by cyber-criminals? For one, Airlines have a treasure trove of sensitive customer information including private passport and credit card data-valuable information for cyber-criminals. The other issue is that the airlines often connect disparate systems and networks together which can open the door for increased vulnerabilities. Reservation systems, baggage system, logistical data and partner networks are all connected and we’re now adding IoT to the mix providing more potential entry gateways for criminals.
This is all happening while people are flying more than ever. By the end of 2019, the airline industry will set a new record in terms of the number of scheduled passengers, almost 4.6 billion which is up 130% from 2004. The International Air Transport Association (IATA) revealed that present trends in air transport suggest passenger numbers could double to 8.2 billion in 2037.
Problem for Airlines Around the World
A little while back, British Airways was in the embarrassing situation of announcing that 500,000 customers visiting its website were redirected to a fraudulent site where sensitive data was subsequently stolen. It was an expensive problem to fix not to mention the huge $230M fine which British authorities asked the airline to pay for not safeguarding people’s personal data.
And then there was the big headline shared globally involving Cathay Pacific. A little over a year ago, Cathay Pacific was hit hard by hackers and passport numbers, credit card data and other sensitive information such as nationalities, dates of birth, addresses of up to 9.4 million people were illegally accessed. Over at Delta Airlines, the chat software was to blame for the cybersecurity breach exposing customer data. And for our friends in the North, Air Canada said that a data breach occurred on its mobile app, effecting about 20,000 people.
Numerous Connections Make it More Confounding
For busy airlines, the risk of a major security breach can increase with the number of third party vendors involved with a company’s operational process and the number of connected devices. At SFO for example, over 30 airlines connect to the airport systems, the baggage systems, the maintenance network, the FAA, various business partners, all tied together to make the system work seamlessly and get passengers to their destinations.
When a breach occurs, it can be a flurry of activity to contain the damage and find a remedy. Air Alaska for example right after it closed its deal with Virgin America was hacked when cybercriminals gained access to Virgin airline’s systems. When hackers used a remote access toolkit to exploit an Apache Struts vulnerability they were able to move laterally inside the network environment, basically jumping to other systems where more desirable information and data were stored. It was all hands on deck to contain the damage and the good news was that Alaska Airline at that point, and even now for that matter had Virgins network environment separate from the core Alaska Airline’s network.
Segmentation, Sort of, Kind of
This segmentation of sorts helped contain the damage and limited the negative impact to the parent brand. The bad news, however, was that that vulnerability point of ingress was a vendor controlled system that had to remain online as required by the FAA so the system could not simply be switched off and even worse so Alaska had to wait for the vendor to provide a patch update.
Thinking the Problem Through
Having sensitive customer information, unfortunately, means Airlines are subject to cyber-attacks. And the cost and fines related to compliance can be a big deal in addition to the negative publicity and consumer loss of confidence when a breach occurs. The number of devices will continue to be connected to the network for major airlines exposing carriers from international all the way down to regional to security risks.
Segmentation the Ordr Way
The airline industry has been consolidating in North America and its understandable and prudent to keep networks separate after a merger. Cost savings nonetheless can be limited by keeping multiple systems and different networks running vs combining things together. Keeping things separate can keep help contain and limit the expansion of damage yet we like to think a better approach is via micro-segmentation, keeping things separate not just physically but logically as well.
Micro-segmentation gives network administrators more granular control over the traffic that travels up and down and across a network. If and when a breach occurs, micro-segmentation limits the potential spreading and helps prevent potential business disruption. At Ordr, we can help companies segment their network and make sure that traffic within one subnet is carefully monitored and that any anomaly is quickly detected and contained. For Ordr, segmentation applies to the detection and isolation side and just importantly the protection and prevention side.
The Control Tower…Be in Control
The airport control tower is where key operations such as flight data, clearance delivery, and ground control are orchestrated. Ground control makes sure airplanes that have landed can taxi to the right terminal while airplanes ready to take off are sequenced correctly and in order. Even if there was an incident or emergency, there is a segmented and orderly way to contain an issue and keep it from spreading throughout the airport. Likewise, Ordr’s system sees all the elements in a network, keeps things orderly while also making sure operations flow smoothly throughout.
Beyond classification and visualization, our security vision is to provide proactive protection and automate and streamline what can be labor-intensive and time-consuming tasks similar to how things are performed within an air traffic control tower. It all starts with doing segmentation the right way so that things are orderly, even considering the 100,000 flights a day or the millions of bags traversing every day. As an added benefit at Ordr, we have supported multi-vendor heterogeneous networks and our approach is not limited to how and where we can instantiate policy enforcement but rather across the entire airline’s network system.
For airlines we can help implement policies dynamically automate remedial actions and policies across different segments or disparate subnet of a network, helping to keep the friendly skies safe.
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogDetecting DarkSide Ransomware Used in the Colonial Pipeline Attack
BlogDetecting DarkSide Ransomware Used in the Colonial Pipeline Attack…to the file. This will update the system in real-time and will analyze all new and retrospective communications against the list and mark them accordingly. All the IP addresses communications…
Security Bulletin
Detecting DarkSide Ransomware Used in the Colonial Pipeline Attack
4Min Read
By Srinivas Loke

On Friday, May 7, 2021, Colonial Pipeline confirmed that a cyberattack forced the company to proactively close down operations and freeze IT systems after becoming the victim of a ransomware attack. Even though the specifics of how the attack was carried out and its impact have not been disclosed, Colonial confirmed that operations is only partially restored even after three days. On May 10, 2021, the FBI confirmed that DarkSide ransomware was responsible for this attack on Colonial Pipeline.
What is Ransomware?
Ransomware is a form of malware designed to encrypt files on a device, rendering any files and the systems unusable. This is usually carried out by malicious actors who then demand ransom in exchange for decryption. Ransomware actors often target and threaten to sell or leak exfiltrated data if the ransom is not paid. According to the latest industry trends, ransomware activity increased by close to 150% in 2020, with each event resulting in an average downtime of 18 days. The report also mentions an increase of financial loss for each event by 200% from 2019.
What is DarkSide?
DarkSide is a group that has used ransomware to attack various companies in the U.S. and Europe. They have attempted to extort companies with threats and claims to give part of the money it makes to charity organizations. DarkSide follows a growing trend by ransomware gangs called “double extortion,” where the hackers not only encrypt and lock the data but threaten to release the data if ransomware is not paid.
FBI Flash Announcement of Indicators of Compromise (IOCs)
On May 10, 2021, the FBI announced IOCs for the DarkSide ransomware. The list included a set of IP addresses and URLs that are associated with this ransomware. Our security team has incorporated these IOCs into the Ordr platform.
IP addresses associated with DarkSide
176.123.2.216 51.210.138.71 185.105.109.19 192.3.141.157 213.252.247.18 23.95.85.176 159.65.225.72 80.209.241.4 46.166.128.144 108.62.118.232 185.203.116.7 185.203.117.159 104.21.69.79 172.67.206.76 185.203.116.28 198.54.117.197 198.54.117.199 185.243.214.107 45.61.138.171 45.84.0.127 212.109.221.205
URLs associated with DarkSide
catsdegree.com fotoeuropa.ro 7cats.ch securebestapp20.com gosleepaddict.com kgtwiakkdooplnihvali.com yeeterracing.com/gate ironnetworks.xyz lagrom.com openmsdn.xyz ctxinit.azureedge.net
Tracking DarkSide using Ordr
There are a number of challenges when tracking ransomware typically:
- Security controls might not have complete visibility to track Patient 0. Most ransomware is targeted
- Lateral movement of malware is widespread. Security teams need complete visualization of East-West traffic to detect lateral movement
- Ransomware typically uses standard protocols like HTTPS to communicate to C&C servers, so the traffic may appear benign.
Here are best practices using your Ordr deployment to track a potential DarkSide ransomware infection within your organization.
1. Identify and understand risks for every device
Ordr uses DPI and AI, along with enrichment from a variety of different security and threat intelligence feeds to calculate the risk and security posture of every device. Device context including static attributes like O/S of the device, hotfixes deployed, installed software deployed, and the behavioral patterns of the device provides a unique view of the risks of a device. Ordr uses industry-leading threat intelligence to detect close to 25 critical event types to identify vulnerable devices in the network, and offers an actionable risk score.
2. Track East-West lateral movement with Ordr Threat Detection Engine
Ordr sensors deployed across the network support the full stack L7 threat detection capabilities. Most organizations focus on north-south threat detection, but east-west traffic analysis is critical to lateral movement and is a major blind spot for enterprises as this analysis is outside the realm of perimeter firewall.
3. Monitor Communications to DarkSide C2
Ordr’s multi-dimensional threat intelligence (URL reputation, IP reputation, IDS, weak passwords/certificates, etc.) has been updated to track all future communications to the malicious entities associated with the DarkSide ransomware in real-time. Ordr SCE also supports capabilities to analyze traffic retrospectively for these communications.
Currently, in the Ordr SCE 7.4.2 R1 release this can be accomplished by working with the Ordr Customer Support team. In the upcoming Ordr 7.4.2 R2 release this can be done via YAML and Ordr will support a simple customized YAML file to track these entities. Users can simply edit the YAML file and add the above list of IOCs to the file. This will update the system in real-time and will analyze all new and retrospective communications against the list and mark them accordingly.
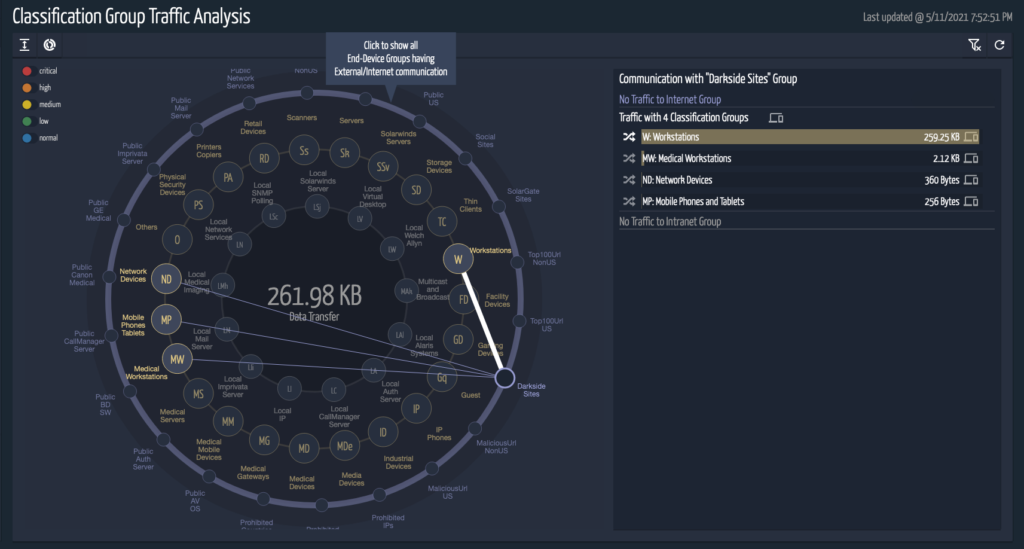
All the IP addresses communications will be captured under Prohibited IP, and the URL communications will be captured as part of suspicious domains in the security page of SCE. The risk score for the devices with these communications will increase accordingly. This information is also available on the traffic analysis tool, where you can drill down on the data based on the classification type, VLAN or Subnet.
4. Customized Security Event Monitoring
One other feature added to the upcoming 7.4.2 R2 release is the ability to create a special event that track customized IP addresses and suspicious domains. Users can configure the event by simply editing the YAML file named “monitoring-groups.yaml”.
Users can follow steps to create a new event called DarkSide and add associated URLs and IPs given in the list to the file. This will create a new entry in the Ordr Group Traffic Analysis constellation view which, provides users with a complete overview of network communications. The user will have an option to drill down the communication patterns of each device associated with the event. This could give some pointers to other devices that should be analyzed for potential infections. Multiple events can be created if needed.
Srinivas Loke
Srinivas Loke is Vice President of Product Management at Ordr. Srinivas has a passion for cybersecurity with a deep understanding of network, end point, cloud and IoT security. Prior to Ordr, he led product teams at Aruba, Pulse Secure, FireEye and McAfee. He loves taking 1.0 products to the market and furthering cutting edge technologies that are solving customer problems.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogCarousel Industries and Ordr: Uncovering the IoT Surprises
BlogCarousel Industries and Ordr: Uncovering the IoT Surprises…of services and solutions and ensuring client satisfaction through the company’s engineering talent and masterfully designed solutions. Jason is the driving force behind the launch of Carousel’s Office of the…
Security Strategy
Carousel Industries and Ordr: Uncovering the IoT Surprises
Hiding Within Your Network
3Min ReadBy Jason Viera

First, some straight-up pragmatism: IoT devices probably won’t get much more secure as time goes on. There’s just not enough impetus for manufacturers to add security capabilities. Couple that lack of onboard security with the fact that IoT usage is rapidly increasing, and the onus falls on IT to address the shortcomings of this evolving Internet of (Insecure) Things so new connections don’t introduce vulnerabilities.
Tools already exist to monitor and manage IoT devices but few follow Leonardo da Vinci’s time-tested premise, “Simplicity is the ultimate sophistication.” Instead, most require too much administration time and in-the-weeds configuration to make them truly effective. That leaves organizations with haphazard deployments, misconfigurations, diminished value from their tech investments, and countless IoT devices prowling the network without proper oversight.
By contrast, Ordr helps enterprises solve IoT risks with a solution that’s refreshingly sophisticated in its simplicity. Powerful and quick to deploy, Ordr hunts down IoT devices on the network, categorizes them and shows you what they are, who they’re talking to, and what they’re doing. To test its usability – its power to deliver insight into IoT activities as well as the ability to launch it quickly and use it effectively – I tried Ordr myself through their IoT Discovery Program.
Simple? Check. Deploying the Ordr sensor on my home network couldn’t have been simpler. I removed it from the box, plugged it into my network, and set up a SPAN session to send all my traffic to it. Then I grabbed some food from the kitchen. Back at my desk, sandwich in hand, I saw the sensor was already hitting security solution pay dirt.
Powerful? Definitely. Along with discovering traditional Windows devices, Ordr showed me the Raspberry Pi that I forgot was on the network and my Garmin watch, which I didn’t realize had wireless enabled. Then things got really interesting as Ordr presented information about what was happening on my network, automatically categorizing my devices and displaying flows. It revealed that my son’s machine was talking to places overseas it shouldn’t have been – and with command and control (C2) traffic, no less! I immediately remediated that issue, something I would never have known about if I hadn’t plugged Ordr into my network.
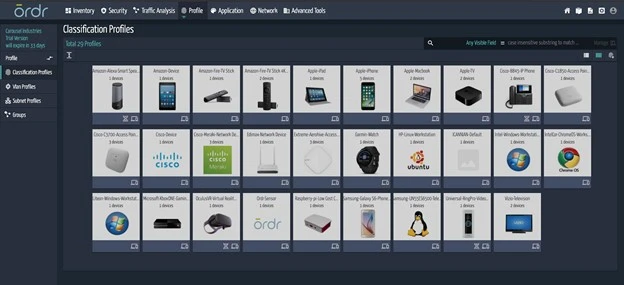
Quick? Ordr’s value became apparent right away. I didn’t fiddle around with configurations. I didn’t even have to impact my network traffic. Watching the sensor do its work was simplicity in motion and the insight I gained after just a few minutes was eye opening. Things had been happening on my network for how long without me knowing about it?
What IT organization wouldn’t want that level of visibility into their own IoT frontier?
Having real-time insight into your network is particularly important because other departments might deploy IoT devices without IT’s knowledge, often referred to as “shadow IoT.” The concept of shadow IoT isn’t about rogue employees with malicious intent. Instead, IoT – along with Operational Technology (OT) and Internet of Medical Things (IoMT) devices such as patient heart monitors, indoor air quality sensors, and automated equipment controllers – enable desirable outcomes for so many functional areas that they’re bound to wind up in your enterprise because employees think they’re doing something good. Unfortunately, the need for security never crosses their radar.
A real-world example illustrates how quickly unmanaged IoT access can turn messy. A highly secure organization working with the Department of Defense (DoD) hired a third party to conduct penetration testing. The pen test vendor was granted physical access to the building and noticed digital signage in the hallway outside the conference room reserved for their work. They got the IP address of that IoT device, discovered it was running an old, unpatched version of Linux, and obtained Microsoft Active Directory credentials into the environment. The digital signage was innocuous, intended to benefit the organization’s users, but it hadn’t been secured against intrusion.
And so, we come back to da Vinci and his penchant for simplicity. Ordr’s effectiveness is built on simplicity. You don’t have to manually sift through and categorize hundreds or thousands of IoT devices, some of which you probably didn’t expect to find. The platform does the work for you, using easily-deployed out-of-band sensors and Ordr’s powerful AI-driven database of devices, well beyond traditional Network Access Control (NAC) device discovery. Its speed stems from the ability to monitor the network in real-time, automatically assigning categories when it spots something new. Ordr solves a big Day Two challenge for enterprises struggling to keep pace with an IoT device list that’s constantly growing. In businesses where shadow IoT is hard at work, this task is even more overwhelming – and more critical.
The time to take control of your IoT environment is now. To help you get started, Carousel and Ordr are offering a free 30-day trial with the IoT Discovery Program. You’ll receive access to the Ordr dashboard and a zero-touch sensor that’s quick and simple to deploy. Ordr’s powerful solution and Carousel’s deep expertise will be behind at every step to simplify the complexities of IoT device security, and at the end of your trial you’ll receive a complete IoT Discovery Report.
What will you see when you add Ordr to your network?
Jason Viera
Jason Viera is Chief Technology Officer for Carousel Industries. As CTO, he is responsible for spearheading and shaping the vision of Carousel’s technology strategy to help innovate and cultivate new opportunities for its more than 6,000 clients. As CTO, Jason is laser-focused on continuously strengthening Carousel’s range of services and solutions and ensuring client satisfaction through the company’s engineering talent and masterfully designed solutions. Jason is the driving force behind the launch of Carousel’s Office of the CTO whose mission is to align the company’s engineering talent with customers to advance their business outcomes. Through client engagement activities, The Office is responsible for driving unbiased strategic innovation for both Carousel and its customers. Additionally, The Office vets and adds new technology solutions to its portfolio to provide further value to customers as they continue their digital transformation journey. Before serving as CTO, Jason was previously Senior Director of Infrastructure Solutions for Carousel. In this role, he worked with customers across multiple verticals to address their challenges with end-to-end architectures to meet their business and technical requirements. Prior to Carousel, he served in several engineering and leadership positions for Cisco Systems, Amgen, and Proctor & Gamble. Jason is a Tech10 Award winner, a member of the Forbes Tech Council, and is a frequent contributor to Network World, CRN, Channel Futures, and several other leading IT and business publications. Jason has over two decades of industry experience and more than a dozen industry certifications.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogAchieving a Zero Trust Posture with its Device Inventory
BlogAchieving a Zero Trust Posture with its Device Inventory…within federal agencies, some of which operate the largest IT operations in the world. And, examining the second pillar—device inventory, management, and security—we already know that there are many connected…
Security Strategy
Achieving a Zero Trust Posture with its Device Inventory
The White House’s Ambitious Goals
4Min Read
By Pandian Gnanaprakasam

The White House has announced a new and ambitious plan to achieve a Zero Trust cybersecurity posture for cyber assets operating in U.S. federal networks. With the right tech capable of seeing, knowing, and securing each device, the goal is already achievable. On January 26th the White House Office of Management and Budget (OMB) issued a memo outlining a “Federal strategy to move the U.S. Government toward a ‘zero trust’ approach to cybersecurity.” The memo is a follow-up to last year’s Executive Order on Improving the Nation’s Cybersecurity in which President Joe Biden outlined a set of priorities to improve the security posture of networks operated by U.S. federal agencies.

The White House has announced a new and ambitious plan to achieve a Zero Trust cybersecurity posture for cyber assets operating in U.S. federal networks. With the right tech capable of seeing, knowing, and securing each device, the goal is already achievable. (You can read our original response to the Executive Order here, and to the subsequent NIST memo regarding defining OT as critical infrastructure.)
The gears of change turn slowly in a bureaucracy as large as the U.S. federal government, and urgency to harden government networks is long overdue, especially with the discovery and exploitation of of zero-day vulnerabilities like Log4j. And as tensions rise in Eastern Europe, including the implied threat of cyberattacks against our national IT infrastructure and politically motivated “hacktivist” attacks against other governments disrupting services, the potential consequences of a lack of readiness are all too real.
Five Pillars of Federal Cybersecurity
The OMB strategy to “achieve specific zero trust security goals by the end of Fiscal Year (FY) 2024” was developed with cooperation from senior administration officials from the OMB, NSA, CISA, and key federal IT organizations. Those goals, which CISA refers to as “five pillars,” are identified in the OMB strategy memo as:
1. Identity: Agency staff use enterprise-managed identities to access the applications they use in their work. Phishing-resistant MFA protects those personnel from sophisticated online attacks.
2. Devices: The Federal Government has a complete inventory of every device it operates and authorizes for Government use, and can prevent, detect, and respond to incidents on those devices.
3. Networks: Agencies encrypt all DNS requests and HTTP traffic within their environment, and begin executing a plan to break down their perimeters into isolated environments.
4. Applications and Workloads: Agencies treat all applications as internet-connected, routinely subject their applications to rigorous empirical testing, and welcome external vulnerability reports.
5. Data: Agencies are on a clear, shared path to deploy protections that make use of thorough data categorization. Agencies are taking advantage of cloud security services to monitor access to their sensitive data, and have implemented enterprise-wide logging and information sharing.
These are ambitious goals for any organization to achieve, let alone those within federal agencies, some of which operate the largest IT operations in the world. And, examining the second pillar—device inventory, management, and security—we already know that there are many connected devices operating within federal networks that are beyond the visibility of IT operations. This was made clear following the discovery of security cameras made in China and connected to networks within the Department of Defense that were found to be sending data back to their manufacturers.
Managing and Securing a Vast Device Inventory
How can the U.S. government achieve their Zero Trust objective for its vast device inventory? Many federal agencies have already deployed Ordr to look across their IT infrastructure to discover and identify each device—including those that are currently unaccounted for and operating in the shadows.
We’ve proven time and time again how the following best practices and five-step approach can get you to Zero Trust.
- Step 1: Passively detect and identify all known, unknown, and prohibited devices without disruption or adverse effects to operations. Ordr’s agentless deployment delivers device inventory and categorization within hours of deployment, and augments device context with additional network data and threat intelligence
- Step 2: Identify devices at-risk to reduce the attack surface. Ordr offers an integrated intrusion detection engine and integration with threat intelligence services, vulnerability management tools, and manufacturing databases to pinpoint the devices that are most likely to be targeted by attackers. By addressing known vulnerabilities, taking prohibited devices offline, or segmenting mission-critical devices, federal agencies can start to reduce their attack surface.
- Step 3: Map and baseline communications patterns for every device. Every device has deterministic functions. Ordr can profile and baseline device behavior using machine learning to reveal and alert to the presence of anomalous communications.
- Step 4: Apply appropriate Zero Trust security policies on devices. Ordr offers proactive, reactive, and retrospective policies. Ordr Zero Trust segmentation policies can be proactively and automatically (yes this means with a push of a button and without manual effort) created for devices, to only allow communications required for their functions. Ordr reactive policies applied on firewalls, NACs, and switches immediately limit exposure and mitigate risks by blocking traffic, terminating sessions, or isolating compromised devices. Finally, Ordr retrospective policies enable a time-machine view of infected devices communicating to newly announced indicators of compromise.
- Step 5: Finally, federal agencies need to continuously monitor the network to identify new devices that connect, detect indicators of compromise in operation, and automatically enforce security policies when risks are detected.
(For more details, check out our whitepaper “5 Steps to Zero Trust”.)
Success Within Reach
Given the size and scope of the U.S. federal government’s combined IT infrastructure, it may seem that the goals articulated by the White House and CISA are unrealistic within the given timeline. In fact, where accounting for and reining-in a massive device inventory is concerned, success is well within reach. Ordr is already deployed within many federal agencies where a Zero Trust device posture is in effect. We’ve proven ourselves in many environments—such as healthcare, financial services, retail, manufacturing, and more—where device security is a priority for protecting critical infrastructure and maintaining operations.
Ordr is proud to be leading the way in this priority initiative to improve national cybersecurity. And with a simple demonstration we can show your agency or organization how you can identify, inventory, assess, and protect your connected devices within minutes. Contact us at info@ordr.net.
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?