Search Results:
”Role of Huawei H19-431_V1.0 Exam Questions in Getting the Highest-Paid Job 💆 Search for { H19-431_V1.0 } and download exam materials for free through [ www.pdfvce.com ] 🏸Premium H19-431_V1.0 Files”
-
 BlogCISA Alert (AA20-302A) Ransomware Activity
BlogCISA Alert (AA20-302A) Ransomware Activity…of Investigations (FBI) and Health and Human Services (HHS) announced an increased and imminent cyberthreat to the Healthcare and Public Health Sector. This warning comes on the heels of increased…
Security Bulletin
CISA Alert (AA20-302A) Ransomware Activity
Targeting the Healthcare and Public Health Sector
5Min ReadBy Prasanna Rajendiran

On Oct 28, 2020, the Cybersecurity and Infrastructure Security Agency (CISA) along with the Federal Bureau of Investigations (FBI) and Health and Human Services (HHS) announced an increased and imminent cyberthreat to the Healthcare and Public Health Sector. This warning comes on the heels of increased ransomware incidents in the last few months and includes information on Conti, TrickBot, BazarLoader and new Indicators of Compromise (IOCs). As healthcare continues to grow as a reliable source of income for threat actors because of the necessity to protect patient care, ransomware campaigns will continue to proliferate.
Jeff Horne, Chief Security Officer at Ordr, provides insight into the latest wave of ransomware with a series of articles:- Ransomware in Healthcare Providers and Healthcare Delivery Organizations – Tactics, Techniques, and Procedures and Recommendations of How to Triage
- A Primer on Preparing for and Responding to Ransomware for Users of IoT and IoMT
Threat Summary
Ransomware has been around for decades and while the recent evolution in the past few years has transformed into more of a service – yes, Ransomware-as-a-Service (RaaS), it can be attributed to one of the reasons there is a 25 percent increase in attacks from Q4 2019 to Q1 2020 and a 715% year-over-year increase in detected – and blocked – ransomware attacks and the average payment increased by 33%.
The distributed nature of the ransomware developer and the affiliates makes it more lethal than ever.
Ransomware developer: Who creates custom malicious code, and capabilities like lateral movement tools and scripts, and including exploit code that is sold to a ransomware affiliate for a fee or share in eventual ransom after a successful attack.
Ransomware affiliate: Starts a hosting site with custom exploit code. Identify targets and send the exploit code typically by phishing email or as an attachment.
Victim: Falls victim to the exploit code.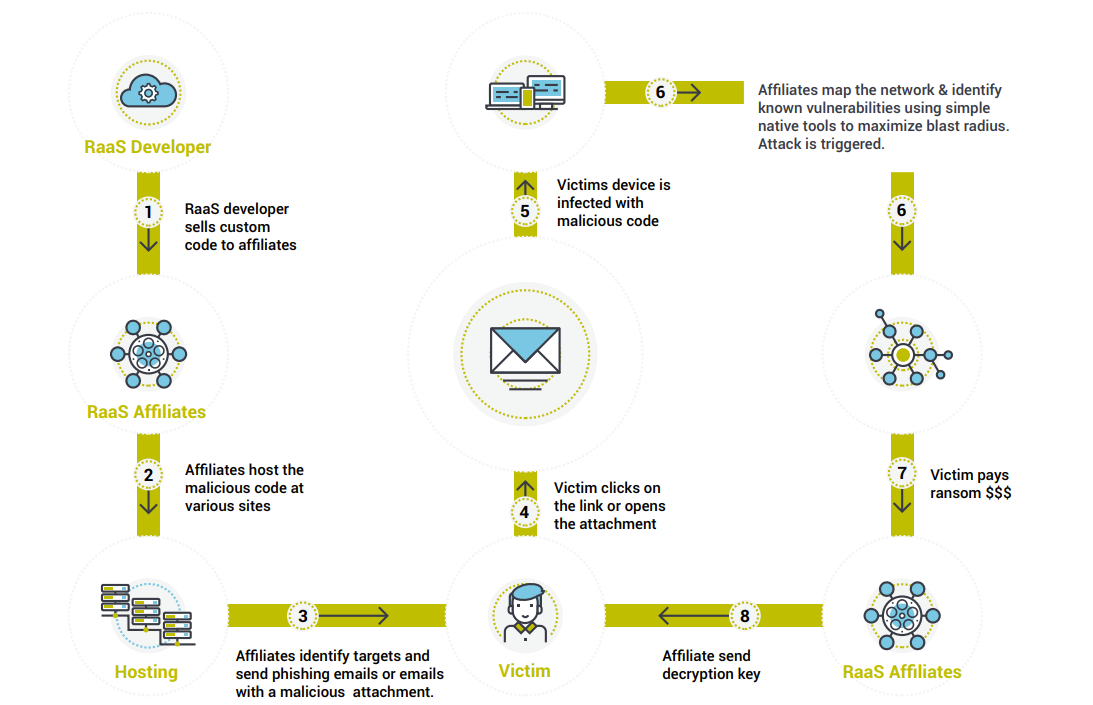
RaaS Infection Lifecycle There are several RaaS types identified by security experts. Some examples are Sodinokibi, Ryuk, Mamba, Phobos, Dharma, Snatch, etc. It is worth noting that in the actual ransomware code is usually the last piece dropped in the infection life cycle giving hope that this can be prevented. The infection usually starts with Trojans like Trickbot, will go through the baking process where the RaaS affiliates monitor and map out the network and any existing vulnerabilities and then drop the actual ransomware code.
Ordr recommendation for defense against RaaS:
There are several recommendations given by security experts. Ordr compiled the Mitigation plans and policies from the CISA advisory and others, mapped it to the NIST cybersecurity framework.
Fig-2: NIST cybersecurity framework Identify
Insightful asset management: Asset management of all the network connected assets is the first step towards defense against any threats. Insightful asset management is not about maintaining a list of IP addresses or serial numbers but a very detailed inventory containing – What the device is, where it is located, Operating System details etc. Ordr passively detects all the network connected devices creates a database with make, model, OS, location and other detailed information.
Continuous monitoring: Continuous monitoring is key for any good asset management and security programs. With the proliferation of IoT devices continuous monitoring is key to the protection of the entire Organization. A device that is not supposed to be in the network need to be detected right away and appropriate action need to be taken. Ordr detects a device the moment it is active in the network and records the same. Ordr can quarantine or disconnect a device from the network with a click of a button.
Knowledge of what is in your control and more importantly what is not: Organizations usually maintain the inventory of the assets that they control. What is largely missed are the assets that are not “owned” by the organization but still uses the critical resources of the organization – third-party managed network, vendor devices, devices and software under vendor qualification etc. Ordr detects all these devices and gives a very easy way to identify these unmanaged devices with ease.
Asset criticality: Knowing and protecting critical assets is a critical part of the security program. For healthcare Ordr provides Clinical risk metrics that helps prioritize and secure the most critical assets.Protect
Security awareness: Awareness is key to any security program. This process should cover topics from identifying malicious emails to social engineering risks. Make sure that Security awareness campaign is an ongoing process.
Understand vulnerability threat posture: Understand the existing vulnerabilities of all the devices and software in the network. Most of the ransomware damage is done using the existing vulnerabilities. One of the vulnerabilities identified as a major exploitation vector is CVE-2020-1472. Ordr identifies devices that are impacted by this vulnerability. Ordr in combination with any popular vulnerability detection software like Tenable or Rapid7 provide a complete picture of IoT specific and application vulnerabilities. With the combination of critical infrastructure score, organization knows how to prioritize the never-ending patching programs.
Bring unmanaged devices under compliance: In almost all deployments Ordr found devices that the security teams never knew existed. These range from someone plugging in some device into the corporate network, contractor/vendor devices to third party managed networks. Ordr can easily identify these devices so that appropriate action can be taken to bring these devices in compliance.
Understand active threat posture: Active threats are different from vulnerabilities. Ordr has an inbuilt IDS engine that can detect East to West threat propagation. Understanding the criticality of the device along with the evidence of vulnerability exploitation is very critical. Typical Firewalls don’t catch East to West threat propagation. Ordr detects and reports the East to West threat propagation that reduces the threat response time.
Monitor active communications: No one wants their device to talk to the bad websites. Ordr detects these activities right away and triggers an alarm.
Backup and encryption: As a standard practice, perform regular backup and encryption.
Be proactive: These new attacks try to understand the network and the connectivity details to cause maximum damage. Microsegmentation is a sure way to protect the network from the ransomware attacks as the threat exposure is minimized. Ordr makes microsegmentation easier and a reality.Detect
Make sure standard security practices are up-to-date: Make sure that all the security measures you have in place like end-point protection software and threat feed information are up-to-date. Provide continuous security education to all the users including vendors and contractors.
Logging: Make sure that you have the logs of all transactions. Ordr records all network transactions over the network. This will help immensely for any forensic activities.
User to device mapping: Its critical to understand who is using what devices and what they are doing with those devices. Ordr helps map user to device mapping and device communication mapping.
Communication patterns: Understanding device to device communication patterns and blocking unnecessary or unexpected communication is another step towards protecting the infrastructure. One of the exploitation vectors for the recent ransomware attacks is the open RDP port 3389. Ordr provides an easy way to identify devices that are communicating over port-3389. User can then decide if this communication is expected or not and if the RDP port itself need to be changed.Respond
Incident response: Develop a plan to respond to an incident. Ordr helps identify the blast radius, understand the impacted applications and users to come up with an effective threat incident response plan.
Recover
Restore: With the backup and encryption mechanisms in place, restore the data.
Verify: Make sure that the suspect hardware software is not used in the future. Ordr continuous monitors the network for the devices and will let the user know about any vulnerable devices coming back into the network.
Report: Report the incident to appropriate authorities as designated by response and discloser policies.
In summary RaaS has no prescriptive solutions. This can be prevented by following the recommendations by Ordr and other authoritative sources. In the battle between good and evil always good triumphs – We just need to know the exploitation vectors, vulnerability posture of the organization and the active threat posture of the organization. We hope our recommendation will help organizations to continue their business and discourage bad actors from doing malicious activities.
For more information on how Ordr can help you identify and manage vulnerabilities for any connected device, please contact info@ordr.net.Prasanna Rajendiran
Prasanna Rajendiran has more than 20 years of experience in various engineering, solutions architect, product management and customer success roles with a focus in telecommunications and security. At Ordr, Prasanna serves as a Principal where he is responsible for working with customers in their complex environments and internally to develop cutting edge solutions.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogOrdr Included in Forrester Microsegmentation Landscape Report
BlogOrdr Included in Forrester Microsegmentation Landscape Report…cybersecurity incidents since they involve fewer systems and get access to less data. [In Ordr deployments, critical infrastructure and industrial operators often have deep investments in supervisory control and data…
Blog
Ordr Included in Forrester Microsegmentation Landscape Report
4Min Read
By Danelle Au
From the start, one of the key features of the Ordr platform has been our ability to discover and classify assets at a granular level, pinpoint asset risks and threats, and accelerate segmentation. That is an important part of establishing a Zero Trust architecture for any organization serious about maximizing security and operational resilience. Because today’s enterprise IT infrastructures are sprawling, comprising diverse systems and devices, and always in flux, network segmentation—and microsegmentation—is vital to protecting the full spectrum of assets that an organization relies on to carry out its mission.
A Maturing Market
As more cybersecurity tools are evolved and developed to address microsegmentation, the market is attracting the attention of users who need those capabilities, and analysts whose expertise is sought to help guide the market. One analyst group leading the way is Forrester Research, and we are thrilled to be included in the Q2 Forrester Research Microsegmentation Solutions Landscape research report as a representative vendor.
The number of tools available for addressing the need for microsegmentation is growing, as you’d expect when a critical need is identified, and pioneering vendors like Ordr show the way. We work hard to provide the best possible solution for microsegmentation through our OrdrAI asset intelligence platform and OrdrAI Protect, and so it is gratifying to be recognized by a respected technology analyst firm like Forrester.
Addressing Core Needs
Authored by principal research analyst David Holmes with contributions from VP and research director Joseph Blankenship, associate project manager Lok Sze Sung, and practice director Michael Belden, the Microsegmentation Solutions Landscape report defines the core value of microsegmentation as helping organizations with the following
- Secure critical and important resources. The best way to quantify microsegmentation as a business benefit is to accept that some level of resource isolation is a cybersecurity requirement, and then compare the cost of a microsegmentation solution to the cost of resegmenting a network or architecture. Limiting lateral movement reduces the impact of cybersecurity incidents since they involve fewer systems and get access to less data.
[In Ordr deployments, critical infrastructure and industrial operators often have deep investments in supervisory control and data acquisition (SCADA), industrial control systems (ICS), and other operational technologies (OT) with service lives that may be measured in decades. Likewise, modern healthcare facility networks are an amalgam of medical technologies, building controls, traditional IT, and even consumer devices. Keeping those systems in service—while protecting them from imperiling threats—is essential.]
- Defend against ransomware. While many organizations are proactive about Zero Trust, an enterprise typically seeks a microsegmentation solution after a cybersecurity incident like ransomware has already done its damage. These organizations are looking to prevent future attacks from being as destructive. Quantifying the benefit for ransomware victims is as easy as subtracting the cost of the solution from the cost of the actual breach, including the ransom.
[Ordr helps defend against ransomware attacks by identifying assets behaving outside of normal baselines, or by identifying those with vulnerabilities that can be exploited. Ordr also can generate proactive segmentation policies based on business needs to stop lateral movement, enforced on existing infrastructure like switches, wireless LAN controllers, firewalls and NAC. And should an attack succeed in getting through, Ordr can also quarantine a compromised device, keeping it isolated until the threat can be remediated.]
- Achieve compliance imperatives. Occasionally, microsegmentation can be used to meet a specific business imperative or compliance mandate separate from Zero Trust. For instance, it can assist in identifying data for GDPR. Customers with strict security requirements can insist that you use microsegmentation to protect their data within your systems.
[By providing a complete asset inventory, Ordr can accelerate compliance initiatives. Ordr pre-defined reports like NIST can help accelerate compliance initiatives, while segmentation limits the scope of compliance.
Our asset risk scores are based on what the asset is, the most up-to-date data and threat intelligence, vulnerabilities, hotfixes and more , Ordr enables security teams to close risk gaps that could result in security incidents triggering enforcement under regulations like HIPAA, GDPR, and other data security and privacy regimes.]
Addressing Zero Trust
Forrester says that microsegmentation tools emerged as one of the first technologies to address Zero Trust security architectures when that philosophy was defined (by Forrester) more than 15 years ago. According to Forrester, one of the most important Zero Trust implementation trends involving microsegmentation is:
Main Trend: Organizations are finally getting serious about Zero Trust. Some, proactively, are implementing microsegmentation as part of a Zero Trust strategy or initiative. Others are implementing it because they got hit by ransomware and are trying to avoid it again. But all of them are doing Zero Trust with microsegmentation.
Ordr Microsegmentation Benefits
Importantly, Forrester has highlighted how Ordr demonstrates key abilities like the capacity to discover assets across the full enterprise, including on-premises legacy technologies, cloud and hybrid infrastructure, industrial environments populated with operational technologies, and other enterprises with heterogeneous network configurations.
Holmes says, “You can use microsegmentation solutions to secure critical and important resources, defend against ransomware, and achieve compliance imperatives. But to realize these benefits, you’ll first have to select from a diverse set of vendors that vary by size, type of offering, geography, and use case differentiation.”
Ordr Takes Microsegmentation Further
That is true, but Ordr goes a step further. To gain the full potential of microsegmentation requires a platform that can discover assets, ingest data, and deliver precise risk analysis in real-time. That is the power of OrdrAI–and the advantage of the Ordr Data Lake, which is unrivaled in its scope and rich detail, containing in-depth profiles of millions of individual asset types. With OrdrAI organizations can assign an accurate risk score to every asset in the network, baseline normal operations and accurately identify risky behavior, then automatically enforce security policies, including microsegmentation, to prevent, contain, and limit the damage of cyberattacks.
The good news is that you don’t have to wait for that future to arrive if you are struggling with complex networks, visibility gaps, and technologies that are impossible to discover and monitor using traditional tools. OrdrAI has already established a stellar record and reputation with a growing client list that includes top organizations in healthcare, manufacturing, critical infrastructure, financial services, education, and government and smart cities. You can find more information about the OrdrAI asset intelligence platform here, and learn more about our segmentation capabilities here, or contact us directly with questions about the OrdrAI platform, or your specific challenges.
Want to learn more about how Ordr helps you simplify segmentation? Attend our webinar on May 14th with our expert Craig Hyps.
Danelle Au
Danelle Au has more than 20 years of experience bringing new technologies to market. Prior to Ordr, she was CMO at Blue Hexagon, a deep learning for malware protection company, and CMO at SafeBreach where she helped build the marketing organization and and define the Breach and Attack Simulation category. Previously, she led strategy and marketing at Adallom, a cloud security company acquired by Microsoft. She was also Director, Security Solutions at Palo Alto Networks, driving growth in critical IT initiatives like virtualization, network segmentation and mobility. Danelle was co-founder of a high-speed networking chipset startup, co-author of an IP Communications Book and holds 2 U.S. Patents. She has an MSEE from UC Berkeley
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogPowering ServiceNow Vulnerability Response
BlogPowering ServiceNow Vulnerability Response…profile and to recognizing when conditions change that put the device and the enterprise in danger of exploitation. The value of the information Ordr has in the Ordr Data Lake,…
Integration
Powering ServiceNow Vulnerability Response
With Complete and Accurate Data for All Devices
5Min Read
By Chris Westphal

Learn how the ServiceNow vulnerability response integration with Ordr closes visibility gaps and provides insights for all connected devices. Overview
Enterprises are a complex mix of devices, applications, and data, and the speed at which they are changing is growing exponentially. Look just about anywhere in the modern technology estate and you’re bound to find connected devices that either didn’t exist or weren’t designed to connect to the network even five years ago. Modernization and digital transformation are major factors that have driven the demand to connect more things to networks in an effort to collect and exchange data and enable new services. And as innovation continues apace, we can expect to see further escalation in the numbers and kinds of devices that connect to the network.
With all the benefits of connected devices comes a slew of new challenges when it comes to managing and securing them, especially when you consider that many operate undetected by IT operations. Ordr’s own analysis of environments in which our technology has been deployed shows that as many as 15% of devices discovered were previously unknown by the enterprise. That is a significant visibility gap that equates to a significant risk gap. As we hear over and over again from CISOs, “I can’t protect what I can’t see, but I’m still responsible for it.”
One Big Challenge
What can IT and security leaders do to meet the challenges and keep their enterprises safe from cyberthreats? Automation is key to keeping pace with the speed of growth and change because automation helps organizations scale and keep up with demands. The key is not just in maintaining scale, however, but in collecting and analyzing quality data in real time. This is especially true when it comes to security. Without complete and accurate data, automation is arguably useless. Rather than paving the way to precise and timely action, bad data creates speed bumps and even roadblocks that require manual verification and thus impede rapid decision making.
I can’t protect what I can’t see, but I’m still responsible for it.
Every CISO, Every EnterpriseOne big challenge to ingesting accurate, timely data is in discovering and keeping track of everything that’s connected to the network. In a self-serve IT paradigm, many devices connect outside the view of IT management. Many devices are not capable of being monitored and managed with traditional methods such as active scanning and agents. Sometimes devices can get lost when changes or updates render their agents obsolete or ineffective. And as organizations grow, these issues compound.
Legacy monitoring and tools are not designed to meet today’s challenges because you can’t take advantage of automation if you can’t trust your data. Therefore, it is essential to acquire the means to see, know, and secure every connected device, collect the data associated with each device’s operations, and use that data to generate the security and operational intelligence needed to maintain fast, safe, and efficient operations.
How Ordr Helps
IT and security leaders require a purpose built tool to ensure they have the complete and accurate operational data they need to fill in the blanks left by legacy tools that depend on agents or active scanning. This all starts with the ability to discover the millions of unmanageable network-connected devices in operation in today’s industrial, medical, retail, financial, and other environments. That’s where Ordr comes into play. The Ordr Connected Device Security Platform is engineered to automatically discover, identify, classify, monitor, identify vulnerabilities and assess the risk of every device connected to the network. Here’s how.

Connected device discovery starts by analyzing network traffic. If it connects to the network Ordr will find it, and once we do, we keep it in view. But it’s not enough to simply know a device is there. You need to know what it is going beyond merely collecting its MAC and IP address and instead gain detailed information about the device, the role it plays, and how it is expected to operate under normal conditions to deliver services. Ordr maintains an extensive library of millions of different device types–the Ordr Data Lake–with detailed information on each. That information includes deep insights into known vulnerabilities, FDA recalls, and other data critical to understanding the device’s risk profile and to recognizing when conditions change that put the device and the enterprise in danger of exploitation.
The value of the information Ordr has in the Ordr Data Lake, and that we collect from devices in real-time, is maximized by our extensive list of technology integrations that enable bi-directional data feeds to support other critical security and operational functions. That includes our tight integration with ServiceNow’s Service Graph Connector, configuration management database (CMDB), IT service management (ITSM), and our latest integration with Vulnerability Response. The real-time operational data we collect is used to populate the ServiceNow CMDB and enable workflows in ITSM and Vulnerability Response platforms to ensure the most accurate IT operations automations possible. And from a cybersecurity perspective, maintaining a closed loop of data flow with ServiceNow Vulnerability Response ensures an organization’s security team maintains visibility and status of the attack surface, including any vulnerabilities associated with devices operating in the network.
Closing Visibility Gaps
The bidirectional Vulnerability Response Integration with Ordr, certified by ServiceNow Engineering and available in the ServiceNow Store, closes visibility gaps and provides vulnerability insights for all connected devices including those not supported by endpoint agents or active scanning. Using passive methods, Ordr collects operating system and software details, and vulnerability details including severity for all devices. This information is sent to ServiceNow Vulnerability Response so teams can leverage accurate data to optimize and accelerate vulnerability management tasks and reduce risk.
Combined with Ordr collected device context and vulnerability data from multiple industry and threat intelligence sources, the Ordr-ServiceNow integration delivers a complete, rich, and single view of device vulnerabilities and risk, while providing the data needed to automate dynamic policy creation and efficient enforcement of mitigations as well as rapid incident response actions. Here’s how it works:
- Ordr automatically identifies and gathers granular details including vulnerabilities for every managed and unmanaged device connected to the network.
- Ordr uses passive methods and does not impact device services to identify every device and collect granular details including vulnerability information for every connected device.
- Ordr Software Inventory Collector, gathers details of applications and application patch levels for all devices including unmanaged devices.
- ServiceNow Vulnerability response pulls vulnerability information from Ordr for all managed and unmanaged devices.
- Vulnerability status is maintained across both platforms leveraging bidirectional integration.
This complements other Ordr integrations with ServiceNow to provide ServiceNow customers with comprehensive and accurate details of all managed and unmanaged devices in their environment to enable organizations to take full advantage of ServiceNow automation and orchestration capabilities.
- ServiceNow Service Graph Connector – to enable the exchange of granular and accurate device data at scale between the Ordr and ServiceNow platforms.
- ServiceNow CMDB – for a centralized, comprehensive, accurate, and up-to-date asset inventory.
- ServiceNow ITSM – to enrich and accelerate IT workflows with accurate and up-to-date asset details.

ServiceNow VR + Ordr Means Less Risk
Because the Ordr integration with ServiceNow Vulnerability Response enables organizations to fill in visibility gaps with comprehensive device vulnerability details and combine device data from multiple sources, enterprises are safer from threat actors actively working to exploit weaknesses in enterprise security. And because we use passive methods, device performance is not affected, meaning even an organization’s most sensitive and critical devices are protected with no impact to services or patient safety.
To learn more about Ordr’s integration with ServiceNow Vulnerability Response, Service Graph Connector, CMDB, and ITSM solutions, check out ServiceNow on our partners page.
Chris Westphal
Head of Product Marketing
Chris is the Head of Product Marketing at Ordr where he helps drive awareness for connected device security and the value of the Ordr solution. Chris brings more than two decades of experience to his role with a background in enterprise security, cloud, and data center technologies. Most recently, Chris was head of product marketing at Salt Security, the leader in API protection, and has held product marketing leadership roles at companies including VMware, Illumio, and Adallom (acquired by Microsoft).
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
You Might Also Be Interested in
Ready to Get Started?
-
Knowledge BaseWhat is network access control (NAC)?
…registering them under the terms of your company’s BYOD policy, for example. Or, an IT team might set up devices for testing purposes and then forget about them, even though…
What is network access control (NAC)?
6Min ReadAN INTRODUCTION TO NETWORK ACCESS CONTROL (NAC)
For decades, network access control (NAC) standards such as IEEE 802.1X (which defines resources that can be shared over a network using ports) and WPA (which enforces access control and data encryption for wireless networks) have helped to protect devices and users. But organizations face a new set of challenges today, and traditional NAC strategies are not always well-suited to handle.
Unfortunately, devices comprising the Internet of Things (IoT) are not always supported by traditional NAC protocols, and the proliferation of “shadow” devices requires new approaches to NAC. This article defines NAC, explains the benefits and limitations of NAC, and discusses best-practices for optimizing NAC strategies on modern networks.
What is network access control?
Network access control, or NAC, is the set of tools, processes and protocols that govern access to network-connected resources. It is a multifaceted discipline that involves access control solutions for different types of resources, including conventional PCs and servers, and also network routers, IoT devices and more.
NAC also applies to data that travels over the network, and the resources it helps to secure may be physical (as in the case of hardware routers or servers) or software-defined, virtual resources (such as a software firewall or a virtual machine).
In addition, NAC extends beyond access control narrowly defined to include device identification, threat monitoring and policy-based management of access control for networked resources. It also addresses the security requirements of both wired and wireless networks, although, as we discuss below, NAC considerations sometimes vary between these two contexts.
When/why do you need network access control?
Whether you have a small network with just a handful of devices or a sprawling enterprise network that includes thousands of devices, you need NAC for IoT security. Why? NAC is a critical component of your overall security strategy, and for several reasons.
Unauthorized devices
It’s easy to add devices to a network, but not always so easy to track them. As a result, organizations run a high risk of having unauthorized devices on their networks.
Employees may bring personal computers or phones to work and connect them to the network without properly registering them under the terms of your company’s BYOD policy, for example. Or, an IT team might set up devices for testing purposes and then forget about them, even though they are still running. Resources like these become “shadow” IoT devices that are connected to your network but not properly managed.
NAC helps to prevent unauthorized devices from being joined to your network in the first place, while also identifying those that exist so that you can take them offline or make sure they are secured properly.
Outsider access
Large organizations regularly work with contractors, partners and third-party suppliers, and must sometimes grant these external stakeholders access to their network. Without an effective NAC strategy, it’s very difficult to guarantee that these outside devices are properly secured and don’t become a vector for attack into your network. It’s also difficult to ensure that the devices are disconnected when they are no longer needed.
Data privacy laws
Government agencies and industry groups have introduced increasingly strict regulations and data privacy laws that govern which types of data are collected and stored by an organization. Without NAC, companies lack visibility into the types of resources that exist on their network and whether special compliance rules may apply to them.
For these reasons and more, organizations seeking to stay ahead of security challenges and regulatory issues must develop an effective NAC strategy.
NAC capabilities and limitations
NAC is a powerful component within a broader cybersecurity strategy. However, NAC is not a panacea. It’s important to understand which security risks NAC can and cannot address.
NAC capabilities
NAC excels at addressing several traditional types of security needs:
- Conventional network visibility: NAC can help identify which devices exist on your network, who has access to them and how they can share resources with each other.
- Endpoint security technology: NAC helps ensure that network endpoints—meaning physical or virtual resources that can send or receive data over the network—are secured against known vulnerabilities.
- Authentication: NAC policies ensure that users and devices authenticate properly before they are allowed to use a network by, for example, preventing a computer from joining a wireless network unless its user enters the right passphrase.
- Network security enforcement: NAC can identify instances where devices are not compliant with authentication or security policies.
NAC limitations
Despite these strengths when it comes to managing authentication for users and known devices, NAC is subject to several limitations in other respects.
Low visibility into IoT and unmanaged devices
One of the major limitations of NAC is that it is effective in managing security risks only for known devices, and devices that are associated with human users (like a PC or server). A device that is joined to the network and has no specific user or group of users associated with it, such as an IoT sensor, is more difficult to manage via NAC. These devices may not support traditional authentication protocols or security certificates due to hardware capacity limitations or a lack of user input.
As a result, organizations often default to trusting these devices blindly and excepting them from standard NAC rules.
Network access control for wired networks
While access to wireless networks is typically secured using protocols like WPA, wired networks often have no such controls in place. They often assign an IP address via DHCP and give full connectivity to any device that is plugged in (and even if they don’t assign an IP address automatically, the device or user can configure one manually).
This approach is convenient because it eliminates the need to manage access credentials for wired devices and users. Organizations sometimes assume that the security risks are low because only users with physical access to their infrastructure can plug in devices. The reality, however, is that unsecured wired networks are prime vectors for shadow devices to enter an organization’s infrastructure.
Monitoring for threats post-access
Because NAC focuses on controlling access to networks, it is effective only for protecting against threats that are external to a network. It doesn’t detect breaches after they occur, or protect against “insider” threats that originate on an already-authenticated device.
Ability to establish policies for devices
Unmanaged, non-user devices, such as IoT hardware, often rely on special communications protocols that are not supported by standard NAC authentication policies or tools. Faced with this challenge, organizations end up choosing between granting these devices an exception from NAC rules, or building very complex policies to accommodate them. Both approaches are far from ideal.
NAC use cases
Although traditional NAC is subject to certain limitations, NAC strategies can effectively support security needs for modern networks and workloads by taking advantage of next-generation tools or processes. Following are some examples of how NAC can address common challenges faced by organizations today.
NAC for incident response
Although NAC doesn’t detect threats post-access, NAC data can be incorporated into security monitoring platforms that use artificial intelligence (AI) or machine learning (ML) to detect threats. For example, by collecting data about normal access request patterns and analyzing it for anomalies, security monitoring tools can discover unauthorized devices that were mistakenly granted access to the network. In turn, the tools can generate alerts so that engineers can react.
NAC for BYOD
NAC can mitigate risks associated with BYOD policies—which allow users to bring their own devices onto a company’s network—by using a mix of policy management, profiling, and access control to safeguard networks from unmanaged devices. For instance, an NAC tool could require users of new devices to complete a form in order to register their device before it is granted access to the network. A major limitation here, however, is that this approach won’t work for non-user devices.
NAC for IoT
On IoT networks that include hundreds or thousands of devices, NAC helps to manage inventory so that organizations have continuous visibility into which IoT devices exist and when they go online and offline. In addition, NAC tools allow teams to “lock down” IoT devices by enforcing a policy of least privilege or blocking devices from the internal network until they meet the criteria of the organization’s security policy.
NAC for medical devices
Medical devices that collect data about patients or, in some cases, are implanted inside them, can be used as gateways to collect sensitive data, such as protected health information or financial systems. NAC can mitigate these threats by segmenting medical devices from the rest of the network in order to minimize the attack surface. It can also ensure that medical devices are connected only when necessary, which also helps to minimize opportunity for attack.
In short, NAC can play a powerful role in a cybersecurity strategy, but it should never be the be-all, end-all of your cybersecurity strategy. You must instead understand and prepare for its limitations, especially when it comes to unmanaged devices and devices that don’t have human users.
Optimize your NAC deployment with Ordr
NAC is one effective tool in your cybersecurity toolbox, but to get the most out of it, you need to plug the visibility holes in your network. You must be able to identify and address risks such as shadow devices that are connected to the network without authorization, devices that are intermittently connected and therefore not always visible through conventional management tools, and IoT devices that can’t be secured using traditional authentication protocols.
Ordr Systems Control Engine (SCE) provides the visibility you need to achieve these goals. Ordr SCE complements NAC by continuously identifying unmanaged, non-user and IoT devices. It fully maps every microscopic device detail and its context at massive scale, using machine learning to inspect and baseline the behavior of every device on your network on a continuous basis. Ordr also detects exposed vulnerabilities and delivers intricate risk scores for priority attention and mitigation.
These features empower organizations to address the security risks that their NAC solutions don’t detect or can’t manage. In a world where BYOD practices and IoT networks are on the rise, Ordr SCE helps to plug critical gaps in your security strategy.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogA Tree is Worth a Thousand Leaves
BlogA Tree is Worth a Thousand Leaves…the same type and class of device. It filters out irrelevant details and focus on important attributes. Instead of creating a new profile for each of these devices and each variant…

There’s an explosion of new devices connecting to the enterprise today. We look at how the growth of cyber assets and their operational data complicates cybersecurity, the challenges they create, and what a CISO can do to protect the network. The Numbers Game
Today, virtually every device connects to the enterprise network. From simple function IoT devices to multi-million-dollar operational systems, modern devices utilize data connectivity to perform highly specialized tasks much more intelligently. The sheer heterogeneity of these devices is growing exponentially.
Effectively regulating these devices, in terms of what it can and cannot do inside the enterprise, requires a significant amount of knowledge on each, since you simply cannot control what you don’t know. In an effort to build the necessary repositories of device intelligence, vendors create – with varying levels of detail – device profile libraries. At Ordr we see these libraries as a starting point, a base on which to deliver a comprehensive suite of control capabilities that effectively protect devices and relevant business critical information. We believe that developing a large profile library is nice – organizing in a way to keep it relevant and up to date is crucial.
There are enormous challenges in organizing the library relevant and up to date. A set of printers that are classified as a set of profiles in an enterprise installation will look slightly different in another customer installation – perhaps because of configuration, operational behavior, network connectivity – and will result in an entirely new set of device profiles. Any firmware or software update will necessitate a new profile in order to keep it up to date. At the same time, just like a traditional library, there are too much material that are irrelevant since nobody can ever use them. Profiles with irrelevant information will do more harm than good. To search through all the myriad of uncorrelated and out of date information in a library to get what you need is a difficult task.
Profile Library vs Profile Generator
At Ordr, we believe that the only way to keep the device profiles relevant and up to date is to develop a profile generator. Being able to report millions of device profiles in a library is fundamentally unimportant. What is important is the efficiency with which the profiles can be used in an underlying multi-vendor networking and security infrastructure – and automate such infrastructure to control these devices in terms of access control and policy enforcement. We need a real-time Profile Generator for those devices actually deployed in an enterprise and produces the relevant parameters for automated control.
In order to achieve this goal, we deploy a number of sophisticated Machine Learning (ML) techniques for our Profile Generator. Our Deep Neural Network (DNN)model ingests all the relevant attributes identified to create a sophisticated machine learning engine for comprehensive device classification. Each unique set of device attributes are collected and fed into the engine, which learns and organizes it. When new devices are added to the network or when their software is updated, the learning engine can add or update the device profile. Moreover, it has the intelligence to determine that multiple devices, while they may have slight differences in individual attributes, are essentially the same type and class of device. It filters out irrelevant details and focus on important attributes.
Instead of creating a new profile for each of these devices and each variant of it, the DNN enhances the main device profile to better predict the behavior of the device regardless of its enterprise-specific attributes. When we feed a set of attributes of a device, DNN engine models the non-linear relationship on data for more generalized learning. This way we arrive at an “inference engine” that can predict the classification the devices of that it has never seen before.
Along with DNN, we also use carefully crafted ensembles of Random Forest and SVM algorithms to influence prediction performance. Such techniques have a significant positive impact on the classification accuracy of our inference engine.
For instance, with Ordr, a printer profile hierarchy would be organized as a logical tree beginning for example with manufacturer, make, model, firmware, and other attributes which may vary from enterprise to enterprise. Ordr intentionally organizes this structure in a way that enables increasing granularity of detail with each tier, while other approaches would create a different profile for each variation in any level of attribute. Not only is it an efficient way to store the profiles, the hierarchical method delivers an ever-increasing level of intelligence and accuracy, while maintaining the relationship among the devices in an efficient manner. As the number of devices identified to be within a group increases, the predictive engine becomes increasingly efficient in future classifications, all without the need for any manual intervention or personnel resources. The Profile Generator is a Learning Tree that continues to produce new branches and grow new leaves, while shedding dead branches and dropping dry leaves.
Our ultimate goal is to effectively offer automated protection to the myriad of connected devices that access the enterprise network. To do this, we generate and enforce granular policies that utilize the existing network and security infrastructure. It is absolutely essential to scale profiling efficiency to many hundreds of thousands of devices in a single enterprise, and finish this process within hours. Without understanding the relevant details of the relationship among these profiles properly organized in a hierarchical way – this policy generation would be untenable, if not impossible.
Taking Control with Actionable Profiles
In summary, we use the most sophisticated data extraction techniques to collect data using methods like DPI (Deep Packet Inspection) and application level transaction analysis. The inference engine from the learning model gives us an enormous advantage to classify the unseen devices in the customer setup without additional interventions. Our AI/ML models make it possible to not only detect anomalies but also come up with actionable auto-generated policies ready to apply in the existing networking and security infrastructure. Our real-time Profile Generator can keep the information relevant and up to date, with continuous improvement in coverage and accuracy.
It may sound impressive and exciting to hear about many millions of device profiles. Big numbers get attention. But growing a tree is more than collecting thousands of leaves.
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogClosing the Door to Cyber Vulnerabilities at Hospitals
BlogClosing the Door to Cyber Vulnerabilities at Hospitals…with the increase in threats and the potential risk of information breaches at these hospitals. Sensitive patient information is what cyber attackers are often after. Just recently in October, the FBI issued…
Healthcare Security
Closing the Door to Cyber Vulnerabilities at Hospitals
5Min Read
By Pandian Gnanaprakasam

Healthcare’s recent and profound digital transformation, with new medical devices, digital services, and applications comes with a high cost of increased cyber risk as networks and attack surfaces become larger and more complex. The health sector has been undergoing a profound digital transformation in recent years. New digital technologies have allowed for important improvements in all the processes of the sector, from medical follow-ups and preventive care to improved diagnosis and patient services. The sector has also seen major improvements to its connected network, administrative and financial systems. The day-to-day life of hospitals is increasingly punctuated by digital technology and more devices are becoming smart and connected. Consider the MRI scanner, insulin pumps or other important assets that are all digitally interconnected. These devices can communicate information on their operating status, provide detailed information on patients and in some devices can even be operated remotely.
Digital transformation affects all sectors, all organizations, both public and private. Healthcare facilities are no exception, especially in terms of cyber security. This transformation of connectivity in hospitals has unfortunately been accompanied by a sharp increase in threats and risks on all the processes involved. Hackers often favor health care institutions because they know that their security investments are not necessarily prioritized and remain lower than for other industries. With hacks at hospitals, the sector can be impacted as a whole as patient confidence decreases and regulatory fines increase. We focus on vulnerabilities in this article, what it is, and how the medical industry should think about risk and some potential ways to isolate, measure and reduce vulnerabilities.
In hospitals, connected objects are everywhere while confidential patient data is becoming digitized across the board. While the rapid development of digitization and connectivity provides for improved efficiency and quality of care, the industry is now wrestling with the increase in threats and the potential risk of information breaches at these hospitals. Sensitive patient information is what cyber attackers are often after. Just recently in October, the FBI issued a warning that ransomware attacks are becoming “more targeted, sophisticated and costly, even as the overall frequency of attacks remains consistent.”
Framing Vulnerabilities at Hospitals
A vulnerability is essentially a fault or a weakness in an environment that can make the collective system unstable. This amounts to leaving, for example, a house unlocked, a door left open, a checklist incomplete. As a result, this “door” can potentially be used by hackers to access the system.
We often find vulnerabilities on computers but the weakness of vulnerabilities can be increasingly found in many other connected devices. In essence, anything that is “coded” can potentially contain vulnerabilities: including firmware, hypervisors, operating systems, libraries, and software. Vulnerabilities may also appear in the way a network or system has been configured. Once a vulnerability exists, a hacker can exploit this weakness for malicious purposes, causing damage to an organization. Every organization today faces attacks from multiple vectors and overall protection and risk management include thoroughly understanding a system’s vulnerabilities.
At hospitals, medical devices themselves can often be the source of vulnerabilities. A study of 24 hospitals in nine countries (EMEA) found that more than half of the hospitals surveyed used standard passwords (ie default settings) to secure their valuable assets. Data is what is often the target for hackers at hospitals and it’s a constant battle to close opened doors and to risk manage vulnerabilities.
What are hackers after? Patient data can be quite valuable and a medical record can sell for $20 to $300 on the darknet, fetching multiples more than credit card data. Hackers also want to create harm and demand ransom in return. Some hospitals have seen had their patient schedule pirated. Scammers in one instance contacted patients to tell them that their consultation was canceled and showed them a different contact number to reschedule an appointment. It can get worse. In 2016, 114,000 patients by a pharmaceutical company were contacted following the detection of a cyber security breach on an insulin pump model. The control box had a vulnerability that, if it had been exploited, could have allowed the patient to inject a potentially lethal dose of insulin.
Vigilance is Needed
Hospitals have to deal with many security issues and if anything the the number of incidents seem to be on the rise. This is happening while devices being connected to the hospital network is growing at +20% per year.
- Theft of scanned records containing medical history, test results, and ongoing treatments.
- Misuse of social security and financial data of patients.
- Partial or total interruption of access to databases.
- Partial or total destruction of the information contained in the databases.
Not Easy for Hospitals
It can be particularly difficult for hospitals to close the door on vulnerabilities. Oftentimes, hospitals are working under regulatory constraints, too many disparate systems and limited overall security and network visibility. Hospitals also have to deal with the lack of resources, training, multiple remote site, and branches. While the headquarters and data centers can be fortified, hackers are all too aware that a remote, unprotected connected site can be an easy on-ramp to the overall healthcare system, exposing yet another key vulnerability.
Cyber Risks and the Consequences Doth Direct and Indirect
Cyber criminals are ingenious and use many methods: phishing, hacking passwords, to get into hospital networks to reach sensitive and profitable data held by hospitals and major healthcare systems. Our next article dives deeper into specific methods of how the bad guys can get in a hospital system. What is alarming is that often times, the bad buys are already in, patiently waiting to exploit vulnerabilities.
Lost Time and Asset Utilization
The goal of hackers is to slow down or paralyze the health facility’s activities until ransom payment and these cyber-extortions can provide considerable financial gains. Think not just of WannaCry but even PetyaWrap which caused Princeton Community Hospital to stop functioning. Doctors were unable to review patients’ medical history or transmit laboratory and pharmacy orders. Unable to restore services and unable to pay a ransom, Princeton Hospital resorted to using paper records. And with little choice left the hospital subsequently scrapped and rebuilt its entire network.
Cyber criminals benefit from the fact that medical equipment such as MRI, X-ray machines, scanners and other diagnostic equipment do not always benefit from optimal security, even though they are almost always connected and used often. This oversight can create security loopholes and encourages intrusions into the systems. Taking a system offline can be a big issue as oftentimes hospitals lease expensive equipment to maximize their usage.
Hidden in the Dark
Highly targeted and sophisticated, the focused on hospitals are often the result of structured groups. These attackers are patient, often lurking undetected waiting to exploit a vulnerability. The goal of the attacker is to discreetly maintain access for as long as possible in order to capture strategic information in a timely manner. In some instances it can be years before an attacker surfaces.
Thinking about Proactive Protection
Businesses need cost-effective, easy-to-deploy solutions that can continually show them who and what is connected to all parts of their networks. The other critical element to consider is the ability to identify any vulnerabilities and apply remedial action proactively. Ideally, the security system will be able to regulate flow and behavior by device type, group, location, function, application, the control is yours.
Many products today will ring the alarm that something is wrong, adding to a whole list of alarms that go off in a day at a hospital. A few will take the next necessary step forward providing automated remediation and loop learning. What we recommend is a system that can quickly provide holistic visibility and the ability to detect exposed vulnerabilities and delivers intricate risk scores for priority attention and mitigation.
Increasingly threats will become sophisticated and automated smart enough to find the key vulnerabilities in a network. Remediation should likewise follow suit and will need to be more sophisticated and automated while leveraging machine learning and AI. The goal of this intelligent system is to deal proactively with any type of vulnerability and limit the damage before it occurs, protecting the hospital’s important business critical assets and closing the door on cyber vulnerabilities.
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogAmerica’s National Cybersecurity Strategy: We’re in This Together
BlogAmerica’s National Cybersecurity Strategy: We’re in This Together…reduce risk.” “[Reduce] systemic technical vulnerabilities in the foundation of the Internet and across the digital ecosystem.” “[Prioritize] cybersecurity R&D for next-generation technologies;” and, “[Develop] a diverse and robust national…
Security Strategy
America’s National Cybersecurity Strategy: We’re in This Together
4Min Read
By Jim Hyman

In an age of digital supply chains and infrastructure, no organization operates in isolation. So when Ordr’s cybersecurity experts studied the U.S.’s new National Cybersecurity Strategy there we reached one conclusion: we’re all in this together. When the Biden-Harris Administration issued its National Cybersecurity Strategy on March 2, I was thrilled to see the high profile focus on this topic. Social media was quickly buzzing as bloggers, influencers, and just about everyone with an opinion to share were in a rush to be first out of the gate with their hot takes. There was a lot of energy surrounding the announcement, and that’s a good thing. The cybersecurity community benefits from the attention when the White House lays out a vision for cyberdefense that highlights many of the issues that have plagued industry for years.
From within the team here at Ordr there is consensus that one of the biggest takeaways from the document is the “we’re in this together” message that pervaded the memo accompanying the strategy. Although that has been true for nearly fifty years—since the advent of the first computer virus in the early 1970s–cooperation among private enterprises and government has not been the way the industry has operated.
That has to change if we are to make meaningful progress toward a stouter national cybersecurity posture. As the president said, “to be able to trust that the underlying digital ecosystem is safe, reliable, and secure” requires “robust collaboration, particularly between the public and private sectors.” That means going beyond merely trying to protect individual enterprises, but striving for greater cooperation in areas like sharing threat intelligence, greater interoperability of tools and platforms, and building technology products with a security-first philosophy.
A Cohesive Vision
After reading through the National Cybersecurity Strategy, it struck me that at its core the strategy is about accountability. The emphasis of its content was on consolidating a number of policies that have been announced previously, and expressing them in a single, cohesive document that lets everyone affected by these policies know what is expected of them. Accountability and simplicity are important for public and private organizations that need to draft their own cybersecurity strategies; and it is important for technology innovators and service providers who must develop the tools we will rely on to meet the goals of this ambitious strategy, namely increased security and resilience for, and trust in, the infrastructure of our digital economy.
Complementing the National Cybersecurity Strategy, the White House also released a Fact Sheet to summarize and reiterate the Strategy’s goals, describing five pillars on which the plan will be built, including:
- Defend Critical Infrastructure
- Disrupt and Dismantle Threat Actors
- Shape Market Forces to Drive Security and Resilience
- Invest in a Resilient Future
- Forge International Partnerships to Pursue Shared Goals
To achieve these ambitious goals demands an acknowledgment that business-as-usual cannot continue, and that cybersecurity must be elevated as a priority for all organizations from small companies to large enterprises. This requires making greater investments in effective security programs and calls for a seat at the table for CIOs and CISOs to advocate for such programs at the board level. Some key points from the Fact Sheet that stand out as vital to doing this are:
- “[Expand] the use of minimum cybersecurity requirements in critical sectors.”
- “[Enable] public-private collaboration at the speed and scale necessary to defend critical infrastructure and essential services.”
- “[Address] the ransomware threat through a comprehensive Federal approach and in lockstep with our international partners.”
- “Place responsibility on those within our digital ecosystem that are best positioned to reduce risk.”
- “[Reduce] systemic technical vulnerabilities in the foundation of the Internet and across the digital ecosystem.”
- “[Prioritize] cybersecurity R&D for next-generation technologies;” and,
- “[Develop] a diverse and robust national cyber workforce.”
A Plan for Today and Tomorrow
The Cybersecurity memo demonstrates a vision that takes into account both current needs and reliance on connected devices comprising the Internet of Things (IoT)–an issue near and dear to our hearts here at Ordr. In Strategic Objective 3.2: Drive the Development of Secure IoT Devices, the National Cybersecurity Strategy accurately observes that “many of the IoT devices deployed today are not sufficiently protected against cybersecurity threats. Too often they have been deployed with inadequate default settings, can be difficult or impossible to patch or upgrade, or come equipped with advanced—and sometimes unnecessary—capabilities that enable malicious cyber activities on critical physical and digital systems.”
No Time to Waste
Establishing regulations that address the weaknesses of IoT devices are necessary, but they will take years to draft, enact, and enforce. In the meantime, there are tens of billions of connected devices in operation today, many of which fit the description defined by the White House. These risks need to be addressed today whether or not there is a law compelling compliance.
We must ensure the Internet remains open, free, global, interoperable, reliable, and secure—anchored in universal values that respect human rights and fundamental freedoms.”
Fortunately, the methodologies and applications to close the IoT security gap are available now, and embodied in the Ordr platform and our See, Know, Secure approach to connected device security. Ordr’s platform has been built to discover every connected device operating in a network while profiling and monitoring each device for known risks and risky behavior. Then, taking that information and automating the segmentation and policy enforcement necessary to prevent threats targeting IoT and stop active threats from moving laterally within an environment. This philosophy is one the federal government already acknowledges as effective, and was mandated for all executive branch agencies by the Cybersecurity and Infrastructure Security Agency (CISA) in its recent Binding Operational Directive 23-01 (BOD 23-01), issued last October and going into effect next month.
As we have with previous policy announcements such as Strengthening America’s Cybersecurity, the IoT Cybersecurity Improvement Act, the PATCH Act, and Zero-Trust initiatives, Ordr supports–in word and action–the White House’s efforts to advance the protection of cybersecurity. We agree wholeheartedly with President Biden when he said, “We must ensure the Internet remains open, free, global, interoperable, reliable, and secure—anchored in universal values that respect human rights and fundamental freedoms. Digital connectivity should be a tool that uplifts and empowers people everywhere, not one used for repression and coercion.”
Jim Hyman
CEO
Jim Hyman brings more than 30 years of experience building and managing world-class teams in enterprise software and SaaS businesses with a specific expertise in cybersecurity. Prior to taking the helm as Ordr’s CEO, Jim was Chief Operating Officer at Synack, the leader in crowdsourced security testing. Jim has successfully driven revenue generation at high growth start-ups and mid-market companies through innovative go-to-market strategies. Previously, Jim was at Trusteer (acquired by IBM in 2013), Z-Scaler (IPO in 2018), and Ironport Systems (acquired by Cisco in 2007). Jim’s experience spans sales, alliances, M&A, finance, venture capital and operations working in the US and internationally. Jim received his B.A. from The University of Pennsylvania and his M.B.A. in finance from The University of Southern California.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
Knowledge BaseWhat is IoMT?
…notably when deploying IoMT in-home, on-body, in the community, and in-hospital: In-Hospital IoMT Hospitals must manage the quality and supply of their medical assets over time, and they also need…
What is IoMT?
4Min ReadThe Internet of Medical Things (IoMT) is the network of Internet-connected medical devices, hardware infrastructure, and software applications used to connect healthcare information technology. Sometimes referred to as IoT in healthcare, IoMT allows wireless and remote devices to securely communicate over the Internet to allow rapid and flexible analysis of medical data.
IoMT’s impact on the healthcare market is undeniable and irreversible. Some healthcare technology market analysts expect the IoMT market is expected to reach $861.3 billion by 2030.
The broader Internet of Things (IoT) includes the network of all Internet-connected devices, including: internet connected factory equipment, biometric cybersecurity scanners, and autonomous farming equipment. IoMT is focused specifically on healthcare and medical applications. Given the sensitivity and strict regulations around healthcare data, IoMT requires a more comprehensive security infrastructure than other IoT systems.
How is IoMT impacting healthcare?
IoMT impacts the healthcare industry in myriad ways. These changes can be seen most notably when deploying IoMT in-home, on-body, in the community, and in-hospital:
In-Hospital IoMT
Hospitals must manage the quality and supply of their medical assets over time, and they also need to understand how personnel and patients are moving throughout the premises. Healthcare professionals use IoMT sensors and other tracking systems to track all of these interactions so that administrators can get a comprehensive understanding of what is going on.
In-home IoMT
In-home IoMT allows people to transmit medical data from their home to other locations such as their primary care provider or a hospital. For instance, remote patient monitoring (RPM) is the use of medical devices to transmit metrics such as blood pressure or oxygen saturation from recently discharged patients to their hospital for review by their doctors. This can reduce hospital readmissions by catching issues before they become serious.
Telehealth—the use of communication technologies for remote healthcare services—provides further flexibility by allowing recently discharged patients to resolve minor issues by remotely connecting with their doctors.
The use of IoMT devices along with telehealth can also be useful for ongoing care outside of the patient setting. For example, personal emergency response systems (PERS) can track events—such as a fall or heart attack—to automatically call for help. PERS can provide security to at-risk people such as seniors that want to live at home without compromising their safety.
On-body IoMT
On-body IoMT is the use of wearable medical devices that are connected to remote tracking or monitoring systems. Unlike in-home IoMT, on-body IoMT can often be used outside of the home as people live their normal lives.
Consumer on-body IoMT devices are wearable devices that anyone can buy to track health metrics for both personal use and for sharing with healthcare providers. In addition to tracking a standard metric, such as heart rate, these devices can be early warning signs for more serious health conditions. For example, the Apple Watch can warn users about irregular heart rhythms.
Clinical on-body IoMT devices are like the consumer devices but afford a wider array of sensor options. For instance, glucose sensors can be worn by diabetic patients to alert them to fluctuations in glucose levels. Many of these devices can share data directly with a patient’s doctors to ensure they get fast and accurate treatment.
Community IoMT
Community IoMT is the use of IoMT devices throughout a broader town or geographic area. For example, mobility services are devices used to track patients while in transit in a vehicle. Similarly, emergency response intelligence systems are used by paramedics and first responders to track patient metrics outside of the hospital setting.
In addition to mobile and emergency care, community IoMT also involves technologies that enable remote services. For example, point of care devices can be used by healthcare providers in non-traditional medical settings such as a field hospital, and kiosks can be used to dispense medicines to people in areas with limited or no access to traditional infrastructure.
Suppliers may also use IoMT devices in logistics to help in the transport of healthcare goods or medical equipment. For instance, sensors can monitor temperature- or pressure-sensitive shipping containers to ensure that quality is maintained throughout the shipping process.
IoMT Challenges
IoMT comes with some unique legal, regulatory, technical, and privacy challenges, mainly because the IoMT ecosystem has so many stakeholders, including:
- Medical device providers
- Connectivity providers
- Original equipment manufacturers (OEM)
- Systems/software providers
- System integrators
- End users
Legal challenges
When IoMT devices generate and share data, it is not always clear who legally owns that data. For example, if a city-owned medical device captures data from a patient, stores the data in a third-party cloud application, and shares the data with a private healthcare organization … who owns the data? The city? The patient? The software provider? The healthcare organization?
There are many ways the different parties can use and share the data. The owner may have the right to destroy the data, which can be complicated in a distributed network where data is potentially replicated many times.
Regulatory challenges
Due to the sensitivity of medical data, there is significant regulation about how and where it can be used, along with specifications about how the technology should be secured. For instance, the FDA released comprehensive guidance about the Management of Cybersecurity in Medical Devices.
The European Union, the United Kingdom, and organizations such as the Association for the Advancement of Medical Instrumentation and the European Commission, released additional guidance and regulation around these devices.
However, even with all the regulations and guidance issued, 66% of respondents in the Deloitte study said they believe that the regulatory framework will not catch up with what is possible today for another five years.
Technical challenges
Given the distributed nature of IoMT infrastructure, the devices and software systems must be able to communicate securely with one another. However, the protocols and security standards for these types of integrations change constantly. This can cause compatibility issues as new technologies are introduced if older systems cannot keep up to date with these changes.
Privacy and security challenges
IoMT data typically flows through the public Internet and is exposed to more security threats than are present in a firewalled private network. This threat is compounded by the fact that the data is shared among many systems, providing multiple attack vectors.
OEMs must use industry best practices around security, and administrators should use the latest encryption protocols, using unique and complex passwords for access and validating the SSL certificates of remote systems.
Getting it right: How to secure IoMT devices
There are many variables at play in IoMT security, and there is no simple way to secure all medical devices against all types of threats. However, a basic first step is to ensure that you know which medical devices exist on your network, and the types of threats that may impact them.
Ordr recommends a zero trust network security model, in which communication among devices is controlled by strict access control and authentication to ensure traffic is coming from where you think it is. Ordr Systems Control Engine (SCE) can enable visibility and security of all your connected medical devices. Try a demo of Ordr to learn how to keep your IoMT devices—and the data they collect and share—safe and secure.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogThe Importance of Accurate Device and Flow Context
BlogThe Importance of Accurate Device and Flow Context…are intended to impress upon the reader the magnitude of the problem and to convey the impressive effort involved in producing the report year-after-year. But they reveal a much bigger…
Risk Management
The Importance of Accurate Device and Flow Context
Threat Detection and Response
4Min Read
By Pandian Gnanaprakasam

Looking closely at security trend studies like Verizon’s Data Breach Investigation Report, you find the need for and value of accurate threat data. Good asset insights and operational flow data is essential to detecting and preventing threats to the enterprise. When the 2022 Verizon Data Breach Investigations Report (VDBIR) came out at the end of May, I was preoccupied with closing Ordr’s $40 million Series C investments and, while I gave it a quick read at the time, I didn’t get around to taking a close look until this past weekend. The VDBIR always contains a wealth of information, and like most people in the information security industry, I read through many studies to keep abreast of trends and look for clues that point to what’s next.
I especially look forward to seeing what is new in the VDBIR. Over the last 15 years the team at Verizon has done yeoman’s work quantifying the way threats have played out, tracking things like ransomware and digital supply chain attacks, helping to raise awareness of the need to improve the ways enterprises secure their networks, data, and people. It is incredibly useful and has the advantage of its deep history.
Reading Between the Numbers
After skimming the 108-page 2022 report, and examining more closely the sections calling out healthcare, manufacturing, finance services, and other industries that call on Ordr to protect them from the threats to their extensive connected device inventories, something caught my attention. At first I couldn’t quite figure out what it was that made the numbers stand out to me, but then it hit me.
In the introduction, the scope of the report is quantified as “23,896 security incidents, of which, 5,212 were confirmed data breaches.” Those numbers are intended to impress upon the reader the magnitude of the problem and to convey the impressive effort involved in producing the report year-after-year. But they reveal a much bigger problem for those organizations that depend on our industry to protect them from the schemes of cyber criminals: the critical importance of accurate data in cybersecurity detection and response. Let me explain what I mean.
Bad Data is Costly
Bad data–whether inaccurate, incomplete, or obsolete–is the root of many persistent problems vexing cybersecurity, including false positive security events. Each of those nearly 24,000 incidents took time and resources away from the organization whose security team had to investigate and determine whether or not an attack had taken place. And when you consider that data in light of a recent article in CSO Magazine reported that reported security teams waste thousands of hours and hundreds-of-thousands of dollars each year chasing their tails because of false positive incidents, the impact of bad data gets worse.
False positive security incidents may account for as many as 45% of all security events.
According to CSO Magazine, false positive security incidents may account for as many as 45% of all security events. That means that of the 23,896 security events used in Verizon report, there were nearly as many incidents that also had to be evaluated before determining whether they were actual indicators of compromise (IoC) or false positive events, wasting time and resources, but also causing signal fatigue through the boy who cried wolf effect, making organizations less secure because security teams become conditioned to expect to find no threat. When security evaluations and decisions are based on bad data, the natural response is to adjust the systems designed to detect anomalies to be less sensitive. This reduces the workload for human analysts, but it also increases the chance that actual IoCs will go unnoticed.
Imprecise data begets imprecise results, and imprecise results increase risks to the enterprise. The remedy, therefore, is more data–and more precise data.
Building on a Foundation of Excellent Data
When we set out to develop the technology that became the Ordr platform, we knew we had to build something that was engineered from the start to address the problem of false positive signals. We also knew we needed to focus on discovering and protecting connected devices, so we created an Ordr Data Lake populated with data specific to millions of devices; then we applied artificial intelligence and machine learning to run behavioral analytics to develop security models for each device.
That combination of Ordr Data Lake, our behavioral analytics engine, and comprehensive, real-time discovery of devices is powerful. Deep packet inspection of network traffic along with granular device context (including properties like operating systems, patches, and software installed and network connectivity) flows to our Ordr Data Lake along with all of the flow data that the device transacts. Using this rich data, our AI-powered behavioral analytics engine along with standard threat detection methods, like intrusion detection signatures, URL/IP reputations, and other unique techniques forms a very accurate profile of a device, and identifies ones with vulnerabilities, risks and anomalies.
Deep and Unrivaled Device Data
Today, the Ordr platform is informed by a body of threat intelligence and device-specific data that is unrivaled in its scope and scale. What’s more, Ordr is constantly enriched with an influx of new data, including real-time packet capture and analysis across each customer environment. That feeds our platform with an accurate, continuous, and correlated input of data from every connection, flow, and change.
The Ordr Data Lake collects close to 1000 attributes for every device and models are updated regularly with new data to scale classification of newer devices introduced in the network
Non-correlated data can’t be used to distinguish false positive signals from actual indicators of compromise at the speed required to quickly and efficiently detect and contain–or even prevent–attacks. That level of detail and resulting accuracy means that, when the Ordr platform detects an anomaly, we can apply automated policy enforcement with a high degree of confidence to exactly isolate the offending device.
Ordr uses that depth of detailed intelligence to perform multidimensional contextual analytics centered on individual devices that can quickly detect and contain a threat, not merely track an attack’s progress. It’s the difference between eliminating the detrimental effects of false positive signals and taking decisive action that minimizes the threat of a breach while allowing business critical operations to continue.
Ordr Covers your Large Threat Surface
There are more than 35 billion internet of things (IoT), internet of medical things (IoMT), and operational technology (OT) devices connected to enterprise networks today. By 2025 that number is expected to more than double to 75 billion. When you consider that the average hospital operates an enterprise with more than 100,000 connected devices, including as many as 15,000 dedicated to clinical care, the importance of device security is easy to understand. Each device contributes to an expanding threat surface that would be impossible to protect without a purpose-built solution.
The power of device and flow context, along with building behavioral models using historical observations world wide for each device, is critical in reducing false positives and confidently thwarting attacks on an organization. This is even more pertinent for devices that do not have an inert security agent installed.
If you want to put that power and precision of the device data lake to work protecting your enterprise, get in touch.
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogThree-Time KLAS Market Leader in Healthcare IoT Security
BlogThree-Time KLAS Market Leader in Healthcare IoT Security…Helpful training and education offerings, including the Masterclass webinar series; User interface enhancements; and, Strong technical background of the Ordr team in security, healthcare and networking. There are several aspects…
Company News
Three-Time KLAS Market Leader in Healthcare IoT Security
4Min Read
By Danelle Au

KLAS Research’s “Healthcare IoT Security 2022: Moving Beyond Device Visibility” makes Ordr only three-time healthcare IoT cybersecurity leader. Read what the report has to say and why our customers continue to put their trust in us for improved cybersecurity and attack surface management. It’s not often that, in a high-tech industry like security, a company can pioneer an emerging market, and then continue to lead that market for the next five years. This is why our recognition as a Healthcare IoT Security market leader—for the third straight year—by KLAS Research in its latest report, “Healthcare IoT Security 2022: Moving beyond Device Visibility,” is such a milestone achievement for us.
We are so grateful to our customers who engaged with KLAS and provided feedback to them. We couldn’t have done it without you! Ordr received high marks from customers in the KLAS report for:
- Breadth of functionality beyond just visibility, including abnormal activity identification, traffic monitoring, and device utilization tracking;
- High customer satisfaction rates;
- High value across multiple stakeholders including Security, Clinical/Biomed and IT;
- Helpful training and education offerings, including the Masterclass webinar series;
- User interface enhancements; and,
- Strong technical background of the Ordr team in security, healthcare and networking.
There are several aspects of the report that are important to highlight.
1. 3-Time Leader with High Customer Satisfaction Rates
In 2019, when we first appeared in the KLAS report, the market was just emerging. In November 2020, we were named a market leader for the 2nd time. In 2022 again, we’re named a market leader. In the same report, KLAS highlighted our client list transparency.
For healthcare organizations, we emphasize the value of working with a partner with a consistent track record of leadership in healthcare. That consistency and focus is something we’re really proud of.
2. Evolution of Our Customers from Visibility to Risk Insights and Security
Customers interviewed celebrated Ordr’s ability to provide value beyond device visibility. In its report, KLAS noted that, “Ordr customers (often very large health systems) use the platform to do more than simply see what devices are connected to their network—they also track device utilization, identify abnormal device activity, and monitor traffic.”
“Ordr customers (often very large health systems) use the platform to do more than simply see what devices are connected to their network—they also track device utilization, identify abnormal device activity, and monitor traffic.”
This is an important distinction.
As an early vendor in this market, working with so many large healthcare system customers over the last couple of years, our customers have moved beyond visibility (“See”) towards the “Know” and “Secure” part of their connected device security lifecycle. Many healthcare customers utilize Ordr as the source of truth for both device and network context as well as flow level analytics for policy generation. Our customers depend on us for critical risk and clinical insights, and we’ve successfully implemented Zero Trust policies to support their initiatives.
The KLAS report also celebrated our ability to deliver high value across the domains of different stakeholders. Observe the broad range of ways different users within a healthcare organization – Clinical/biomed engineering, security and networking– are using Ordr in these KLAS customer insights, and the outcomes we’ve delivered:
“On the clinical engineering side, the value of the product comes from utilizing the product. We look at whether things are performing as expected or whether the system requires patching. We can get patches from the vendor, but we may miss something, and that makes things very difficult. With Ordr’s system, we can identify which things have been patched and which haven’t. We are also feeding the data into the asset management tool so that we know exactly which systems are involved in our work. The data is very rich and useful.”
“I would definitely recommend the system. The major strength is complete visibility into the endpoints for the traffic that we send through the solution. That will assist us when we get into a more stringent RADIUS authentication requirement for our wired network. Another strength is the ability to see exactly what a device has talked to from either a profile view or a specific device view. We can see what ports were used, how many times the communication happened, and what the date and time were. We can get a rather slick visual representation of that and easily export it.”
“The biggest outcome is a significant decrease in the amount of incident response time. We have used Ordr Platform as a part of our incident response with ransomware. Because we couldn’t run our antivirus on our machines, we were able to go in and identify the specific machines in Ordr Platform and provide a picture to the field support. The network engineers had already logged in to Ordr Platform, saw the traffic, and then killed the port so that it couldn’t communicate. That was very handy so that when a field support person walked into the room, they knew exactly where they were going. We were able to get the medical devices back up and running on our network and segmented really quickly. Ordr made that quick turnaround happen. We have factored the utilization of Ordr Platform into our incident response plans. We have been able to reduce our response time by hours. We already had a really robust response time and plan, and the system sped things up significantly.”
3. Preferred by the Top Healthcare Delivery Organizations (HDOs)
Top healthcare organizations, including 3 of the top 6 HDOs in the world use Ordr. Addressing the needs of these large and sophisticated healthcare organizations is NOT easy and requires a mature product that can meet requirements of accuracy, scale, resiliency and reliability. Our customers have higher levels of expectations with Ordr and we are a critical part of their mission critical security journey. Designing a system to discover 15,000 connected devices for asset inventory in a single hospital is far different than designing a solution for 500,000 devices across an entire healthcare system, delivering granular profiling, device flow mapping, clinical and security risk insights, and segmentation policies.
We are proud of the fact that as we continue to evolve our product and through our many years in the market, we continue to receive some of the highest ratings and deliver the highest levels of transparency to KLAS.
And when it comes to delivering value for healthcare providers, we are just getting started. Stay tuned to this space to see what’s coming next from Ordr.
Danelle Au
Danelle Au has more than 20 years of experience bringing new technologies to market. Prior to Ordr, she was CMO at Blue Hexagon, a deep learning for malware protection company, and CMO at SafeBreach where she helped build the marketing organization and and define the Breach and Attack Simulation category. Previously, she led strategy and marketing at Adallom, a cloud security company acquired by Microsoft. She was also Director, Security Solutions at Palo Alto Networks, driving growth in critical IT initiatives like virtualization, network segmentation and mobility. Danelle was co-founder of a high-speed networking chipset startup, co-author of an IP Communications Book and holds 2 U.S. Patents. She has an MSEE from UC Berkeley
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?