Search Results:
”Role of Huawei H19-431_V1.0 Exam Questions in Getting the Highest-Paid Job 💆 Search for { H19-431_V1.0 } and download exam materials for free through [ www.pdfvce.com ] 🏸Premium H19-431_V1.0 Files”
-
Knowledge BaseThe complete guide to cybersecurity frameworks
…companies in the supply chain. There are five levels to the CMMC certification paradigm. Each reflects the reliability of a company’s cybersecurity infrastructure to safeguard sensitive government information like federal…
The Complete Guide To Cybersecurity Frameworks
7Min ReadProtecting data from cyber attacks has only grown more complicated over the years: the number of cyber crimes committed per year has massively grown. In 2021, the number of security breaches reached 1,862. How do organizations prevent the risk of cyber attack?
Many countries and industries have devised their own sets of cybersecurity best practices for organizations to follow to manage that risk. These frameworks consist of assessment, monitoring, preventative, and response activities to help security teams identify and resolve current issues and constantly scan for new threats. In some cases, these frameworks have even been signed into law.
In this article, you’ll learn what those cybersecurity frameworks are, how they are categorized, and determine which of the most common frameworks might help your organization achieve its security goals.
What are cybersecurity frameworks?
Cybersecurity frameworks are systems and standards that guide security programs and help leaders mitigate cyber risks in their organizations. These frameworks act as a shared language across regions and industries, allowing consumers and businesses to make informed decisions about the companies they place their trust in. No matter the industry, organizations that adopt cyber security frameworks have committed to maintaining a high degree of security around the data they gather and store, as well as the services they provide. Likewise, when a threat arises, they should have a clear plan to take action.
In many cases, implementing certain cybersecurity frameworks is necessary to comply with state, national, and international regulations. Abiding by accepted frameworks shows that organizations are taking concrete steps to decrease their exposure to vulnerabilities that hackers can exploit on their networks, applications, or devices. In practice, cybersecurity frameworks can take on several different forms.
Types of cybersecurity frameworks
There are three types of cybersecurity frameworks distinguished by their function:
Control frameworks
Control frameworks are foundational security strategies. They help teams:
- Evaluate the current state of their overall tech stack (including devices, networks, and applications)
- Create a baseline set of controls
- Plan and prioritize other control implementation
Program frameworks
Program frameworks strengthen an organization’s overarching security practices by:
- Establishing a comprehensive security program
- Continuously assessing the efficacy of that program
- Streamlining communication between the security team and business leaders
Risk frameworks
As the name implies, risk frameworks are designed specifically to minimize risks. They include:
- Processes to help security teams manage existing risk and improve security posture
- Steps to identify and quantify risk
- Methods to triage and implement new security measures
Together, control, program, and risk frameworks serve as a comprehensive barrier — not only to current cyber threats but risks that may arise in the future as well.
8 Cybersecurity framework examples
Since there isn’t any one “right” framework to follow, implementing cybersecurity frameworks can be daunting. Let’s explore eight of the most common frameworks to give you inspiration for the types of frameworks that could fit your organization’s security goals.
1. The NIST Cybersecurity Framework
The NIST Framework for Improving Critical Infrastructure Cybersecurity, known as the “NIST Cybersecurity Framework,” or “NIST CSF” was created to safeguard commercial, energy, and defense utilities. However, its core principles can help any organization follow the basic pattern of cyber defense: identify, protect, detect, respond, and recover.
The NIST framework consists of a series of steps to protect an organization’s data (in transit and at rest), detect risks, respond to threats, and recover assets if needed. It also prompts security teams to conduct root cause analysis of any vulnerabilities they uncover in the process. Originally, the NIST framework was designed to cover traditional IT-managed systems. But organizations are applying the NIST framework to any IoT, IoMT, OT or other connected devices under their purview.
While NIST compliance is voluntary, it’s required for any organization doing business with federal government agencies. For that reason, many enterprise-level organizations in the U.S. have adopted the NIST framework in conjunction with the Cybersecurity Enhancement Act of 2014.
2. The Center for Internet Security (CIS) Critical Security Controls
The Center for Internet Security (CIS) Critical Security Controls framework is best for organizations wanting to ease into a cybersecurity framework. The 20 CIS controls are constantly updated by volunteer experts who hold various industrial, academic, and government roles. Controls are divided into three groups: basics, foundational, and organizational. Security teams should implement the basics first and then move on to the foundational and organizational controls.
CIS also has benchmarks that work in conjunction with its controls. They are set according to other existing standards like NIST or HIPAA, and are split into two levels: security essentials that don’t affect performance, and advanced protocols that may affect performance. Again, this distinction enables security teams to break up their work into more manageable chunks, getting controls implemented faster and more efficiently.
CIS frameworks are meant to calibrate IT services, products, and devices, as well as prepare organizations to tackle other, more complex and demanding frameworks.
3. The International Standards Organization (ISO) frameworks ISO/IEC 27001 and 27002
International Standards Organization (ISO) frameworks are international standards for cybersecurity. As part of the 27K ISO framework, organizations must design and implement an information security (InfoSec) management program dedicated to mitigating identified threats and patching vulnerabilities.
27001 and 27002 ISO frameworks are notoriously demanding. They have over 100 coherent and comprehensive controls that organizations struggle to follow without an ongoing risk management process.
But many organizations need to adopt at least ISO 27001 for legal reasons. To be considered ISO 27001-compliant, organizations must demonstrate that they adhere to the “PDCA Cycle” to an external auditor. The PDCA Cycle is a business management method that focuses on four steps: Plan, Do, Check, and Act:
- Plan – objectives, processes, and procedures for risk management
- Do – implementing InfoSec policies
- Check – regularly evaluating and updating InfoSec policies relative to performance and emerging InfoSec best practices
- Act – enhancing and adjusting InfoSec policies per internal audits
Any organization that has a financial services arm or handles particularly sensitive data, such as medical records, should consider implementing the ISO 27001 protocol.
4. SOC 2 (Systems and Organization Controls 2)
Systems and Organization Controls 2 dictates how organizations protect their data from unauthorized access, security incidents, and other vulnerabilities. Today, most organizations store this information on the cloud, so SOC 2 was formed specifically to protect sensitive data used in cloud-based applications and connected devices.
The SOC 2 framework requires that customer data is managed and stored based on 5 Trust Services criteria:
- Security – protection against unauthorized access, disposal, modification, or disclosure of confidential data, software misuse, or any other system abuse
- Availability – assurance that a device or software works as it’s supposed to when it’s supposed to and there are plans in place to alleviate any delays in performance
- Processing integrity – ensures organizations communicate the way they process data to their clients and uphold their own standards
- Confidentiality – keeps confidential data encrypted and restricted
- Privacy – organizations follow Generally Accepted Privacy Principles (GAAP) to mask PII and other personal data regarding race, sexuality, religion, and health.
Unlike other frameworks, SOC 2 has some flexibility — organizations can determine attestation reports and controls on their own. These reports and controls are then distributed to and evaluated by independent CPA auditors.
While achieving SOC 2 compliance isn’t necessary, it establishes trust with service providers and their customers. Modern procurement teams often look for SOC 2 compliance when evaluating new vendors. Any B2B SaaS organization should strongly consider achieving compliance with this framework.
5. GDPR (General Data Protection Regulations)
The European Union’s GDPR is consumer and data privacy legislation, not a cybersecurity framework. However, this law requires that organizations use “appropriate technical and organizational measures” to secure processed personal data — something that applies to many organizations, especially those in the healthcare sector.
All organizations with patients in the EU must prove that they are GDPR-compliant under the accountability principle. That means they’ve instituted technical measures to adhere to the GDPR law, can explain how those measures work, and demonstrate their effectiveness whenever requested. Examples of those measures include:
- Documenting what data is kept and how long it will be stored for
- Establishing concrete security and response processes for preventing and containing data breaches
- Noting how data is originally collected and whether it can be shared with third parties
The goal of GDPR is to provide consumers with more control over how their personal data is handled and disseminated by companies, particularly in a marketing context. Putting consumers in the driver’s seat makes it more difficult for organizations to mislead consumers with deliberately confusing or vague information.
The EU takes GDPR rules very seriously and will fine organizations that fail to comply with GDPR up to 4% of their global revenue.
6. CMMC (Cybersecurity Maturity Model Certification)
The Cybersecurity Maturity Model Certification (CCMC) is a unified standard for implementing cybersecurity across defense industrial base contractors. The CMMC model was built to prevent U.S. Department of Defense (DoD) information leakage.
Before a contractor can start any government contracts, they must pass certain CMMC certifications. Currently, this applies to over 300,000 companies in the supply chain.
There are five levels to the CMMC certification paradigm. Each reflects the reliability of a company’s cybersecurity infrastructure to safeguard sensitive government information like federal contact information and unclassified documents. Contractors must pass an audit conducted by third-party assessors to achieve each certification.
Organizations that abide by the NIST framework will be in good shape, as submitting an NIST 800-171 assessment to the DoD’s Supplier Performance Risk System is the first step in achieving CMMC certification. Post- NIST assessment, many enterprises enlist the help of an accredited third-party auditor to perform a gap analysis. They can pinpoint any major missing protocols prior to taking the full CMMC assessment.
Organizations also have a chance to remedy any issues that are spotted in a CMMC assessment 90 days after the evaluation is complete. If your organization is successful, it will be awarded a 3-year CMMC certification.
7. FISMA (Federal Information Security Management Act)
Like GDPR, FISMA is U.S. legislation that defines a framework of guidelines and standards to protect government information and operations. FISMA was signed into law in 2002 and requires compliance from state agencies that administer federal programs or organizations that hold a contract with the U.S. government. FISMA compliance is especially crucial for healthcare organizations: many patients receive care through Medicare and Medicaid programs, which are government programs that must be protected. Non-compliance with FISMA can lead to a loss of federal funding, reputational damage, and even indictment for potential government hearings.
FISMA has similar controls to the NIST framework, requiring federal contractors to:
- Track information system inventory
- Continuously categorize risk
- Design a system security plan
- Implement security controls
- Conduct risk assessments
- Achieve certification and accreditation
Organizations that work with the federal government, and even those in the private sector, should stay up to date with FISMA standards and keep a record of the ways in which they comply with the law. Data should be classified according to the level of sensitivity whenever it’s created or stored. Organizations should also take steps to encrypt that data automatically.
8. UK Cyber Essentials sections
The Cyber Essentials scheme is designed to show an organization has a minimum level of protection in cyber security through annual assessments to maintain certification. The Cyber Essentials and Cyber Essentials Plus certifications help organizations avoid weaknesses and address vulnerabilities to prevent exploits.
Both assessments are rooted in five major controls that show organizations are committed to preventing cyber crime. Those controls include:
- Firewalls
- Secure configurations
- User access control
- Malware protection
- Patch management
Organizations that want to bid for UK central government contracts must have the Cyber Essentials certification at minimum.
Get a jumpstart on your cyber security today
Cyber security is of utmost concern to all organizations: hospitals, IP-enabled manufacturing systems, and Interactive Teller Machines are collecting more data than ever before, making rock-solid security protocols a necessity — not a nice to have.
Implementing cyber security frameworks can seem daunting, especially without the right tools. Organizations need a security solution particularly designed for their unique security needs, and that’s where Ordr comes into play. Ordr makes connected device security simple through automated asset discovery, identification of vulnerabilities and risk, and dynamically created policy to improve protection.
Organizations that use Ordr get visibility into what is connected to their network in real time, allowing security teams to find and eliminate vulnerabilities proactively. Plus, Ordr can dynamically create policy to respond to active threats or proactively improve security to protect your organization, data, and patients.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogVerizon Data Breach Investigations Report 2021
BlogVerizon Data Breach Investigations Report 2021…for an incident and a breach: Incident: A security event that compromises the integrity, confidentiality or availability of an information asset. Breach: An incident that results in the confirmed disclosure—not…
Security Strategy
Verizon Data Breach Investigations Report 2021
What We Found Fascinating
6Min Read
By Corin Imai

Each year, Verizon releases their Data Breach Investigations Report (DBIR) for the year prior. In this year’s report, they examine 2020 incident data and non-incident data (ie. malware, patching, DDos, and other data types). It is always good to note, with any research that it does not speak for all data sets and there are still variables that any research team cannot account for. Verizon clearly states that when talking about their Methodology:
We would like to reiterate that we make no claim that the findings of this report are representative of all data breaches in all organizations at all times. Even though the combined records from all our contributors more closely reflect reality than any of them in isolation, it is still a sample. And although we believe many of the findings presented in this report to be appropriate for generalization (and our confidence in this grows as we gather more data and compare it to that of others), bias undoubtedly exists.”
They also follow a standard Vocabulary and Event Recording and Incident Sharing (VERIS) framework with three basic methods:
- Direct recording of paid external forensic investigations and related intelligence operations conducted by Verizon using the VERIS Webapp
- Direct recording by partners using VERIS
- Converting partners’ existing schema into VERIS
The data processing and analysis takes roughly two months and they clearly acknowledge that their data is non-exclusively multinomial, meaning a single feature can have multiple values and there is random bias, sampling bias, and confirmation bias.
Just to clarify before we dive in, here are the definitions for an incident and a breach:
Incident: A security event that compromises the integrity, confidentiality or availability of an information asset.
Breach: An incident that results in the confirmed disclosure—not just potential exposure—of data to an unauthorized party.
Okay, so let’s dive into the areas that we (Jeff, Ben, Jamison and I) found fascinating from the Verizon DBIR:
Security Trends
While we don’t believe that any of these trends are going to shock the industry, we do think some of these are great for those tricky board meetings where you have to discuss why you want budget to protect your organization. So, we pulled out a few of the security trends we thought were cool:
- Social Engineering – while we love a good table top exercise (TTX) around social engineering and trying to see if we can craft a great phishing email to our favorite C-Level executive for credentials. This year’s report validates that, “A lot of Social Engineering breaches steal Credentials and once you have them, what better thing to do than to put those stolen creds to good use, which falls under Hacking. On the other hand, that Phishing email may have also been dropping Malware, which tends to be a Trojan or Backdoor of some type, a trap just waiting to be sprung.” Basically, not only do you have to worry about your infrastructure, but you have to worry about the people your organization is hiring and if they are able to spot a suspicious email or Social tactics. Get them on a good KnowBe4 training and refresh that frequently. Also, just share information or good phishing emails that your organization encounters so employees know what to look for.
- Ransomware Breaches Over Time – well what can we say here. Ransomware as we know well before reading the Verizon DBIR is a crime of passion (as the true crime podcasts say) and now 10% of all breaches now involve ransomware. Since it has been around for more than 30 years, and its entry is usually completely opportunistic, a spam/phishing attack, or vulnerable service on the edge of networks that is easily compromised with very little skill. In addition, most ransomware as a service (RaaS) groups use opportunistic and low skill initial installation techniques like; spam/phishing campaigns, unpatched and vulnerable services exposed on the network, and previously compromised usernames/passwords that remain unchanged. From a mitigation perspective protecting your organization from these opportunistic attacks is the fundamental security best practice around knowing what you have, identifying their risks and monitoring for anomalous behavior.
Some other cool stats that the Verizon DBIR pointed out:
- The rest of the vectors were split between Email, Network propagation and downloaded by other malware, which isn’t surprising
- 60% of the Ransomware cases involving direct install or installation through desktop sharing apps
- The first vector Actors are using is through the use of stolen credentials or brute force
- 42% of incidents had no financial loss and 90% of ransomware had NO loss – absurd right?! The headlines would make you feel differently.
Education Financial & Insurance Mining, Quarrying, and Oil & Gas Extraction + Utilities Frequency 1,332 incidents, 344 with confirmed data disclosure 721 incidents, 467 with confirmed data disclosure 546 incidents, 355 with confirmed data disclosure Top Patterns Social Engineering, Miscellaneous Errors and System Intrusion represent 86% of breaches Miscellaneous Errors, Basic Web Application Attacks and Social Engineering represent 81% of breaches Social Engineering, System Intrusion and Basic Web Application Attacks represent 98% of breaches Threat Actors External (80%), Internal (20%), Multiple (1%) (breaches) External (56%), Internal (44%), Multiple (1%), Partner (1%) (breaches) External (98%), Internal (2%) (breaches) Actor Motives Financial (96%), Espionage (3%), Fun (1%), Convenience (1%), Grudge (1%) (breaches) Financial (96%), Espionage (3%), Grudge (2%), Fun (1%), Ideology (1%) (breaches) Financial (78%-100%), Espionage (0%-33%) (breaches) Data Compromised Personal (61%), Credentials (51%), Other (12%), Medical (7%) (breaches) Personal (83%), Bank (33%), Credentials (32%), Other (21%) (breaches) Credentials (94%), Personal (7%), Internal (3%), Other (3%) (breaches) Top IG1 Protective Controls.
These are the CIS Controls Implementation GroupsSecurity Awareness and Skills Training (14), Access Control Management (6), Secure Configuration of Enterprise Assets and Software (4) Security Awareness and Skills Training (14), Secure Configuration of Enterprise Assets and Software (4), Access Control Management (6) Security Awareness and Skills Training (14), Access Control Management (6), Account Management (5) Also, for a stack rank on industries and their number of incidents and confirmed data disclosures, here you go:
Industry Incidents Confirmed Data Disclosures Public Administration 3,236 885 The Social Engineering pattern was responsible for over 69% of breaches in this vertical. Clearly, this industry is a favorite honey hole among the phishing fiends.The Social actions were almost exclusively Phishing with email as the vector. Information 2,935 381 If we look at only incidents, we find that this industry tends to be bombarded with DoS attacks, a trend that has been occurring ever since computers were networked, or at least since we’ve been doing this report (Figure 108). Of the incidents, DoS alone accounts for over 90% of the Hacking actions we observed, with the rest being credential-based attacks such as Brute force or the Use of stolen credentials. Professional, Scientific and Technical Services 1,892 630 Educational Services 1,332 344 Arts, Entertainment, and Recreation 7,065 109 What was a bit surprising was the high level of Medical information breached in this sector. One would typically associate medical record loss with the Healthcare industry. However, upon digging into the data a bit more, the Personal Health Information (PHI) was related to athletic programs, which fall under this vertical. Retail 725 165 Financial and Insurance 721 467 Misdelivery represents 55% of Financial sector errors. The Financial sector frequently faces Credential and Ransomware attacks from External actors Healthcare 655 472 Manufacturing 585 270 Mining, Quarrying, and Oil & Gas Extraction + Utilities 546 355 Accomodation and Food Services 69 40 Security postures and principles, such as proper network segmentation, the prevention of lateral movement, least privilege, and “never trust, always verify” have proven to be strong indicators of an organization’s ability to prevent or recover from unauthorized presence in its network environment.”
Healthcare
Frequency 655 incidents
472 with confirmed data disclosure
Top Patterns
Miscellaneous Errors, Basic Web Application Attacks and System Intrusion represent 86% of breaches
Threat Actors
- External (61%),
- Internal (39%) (breaches)
Actor Motives:
- Financial (91%)
- Fun (5%)
- Espionage (4%)
- Grudge (1%) (breaches)
Data Compromised
- Personal (66%)
- Medical (55%)
- Credentials (32%)
- Other (20%), (breaches)
Top IG1 Protective Controls:
- Security Awareness and Skills Training (14),
- Secure Configuration of Enterprise Assets and Software (4)
- Access Control Management (6)
In 2020, in the midst of the pandemic, cyber actors increased malware attacks against U.S. victims, including the healthcare and public health sector. The U.S. Secret Service noted a marked uptick in the number of ransomware attacks, ranging from small dollar to multi-million dollar ransom demands. While most organizations had adequate data backup solutions to mitigate these attacks, cyber actors shifted their focus to the exfiltration of sensitive data. These cyber actors, often organized criminal groups, proceeded to monetize the theft by threatening to publicize the data unless additional ransom was paid. The monetization of proceeds was typically enabled by cryptocurrency, in an attempt to obfuscate the destination of proceeds and hamper the ability of law enforcement to locate and apprehend those responsible for the crime.”
But, you might ask what has changed? Well, in 2020 there was a significant shift in Healthcare, where breaches were no longer Internal actors but moved to be primarily External actors. So, some good news, right? No longer is your primary threat actor your own employees!
And lastly, we found it interesting that for the second year in a row, Personal data was compromised more often than Medical. One could make the leap that Personal data can actually be used more widely than someone’s Medical data.
Manufacturing (not mining, quarrying or oil & gas)
Frequency 585 incidents
270 with confirmed data disclosure
Top Patterns
System Intrusion, Social Engineering and Basic Web Application Attacks represent 82% of breaches
Threat Actors
- External (82%),
- Internal (19%),
- Multiple (1%) (breaches)
Actor Motives
- Financial (92%)
- Espionage (6%)
- Convenience (1%)
- Grudge (1%)
- Secondary (1%) (breaches)
- Data Compromised
- Personal (66%),
- Credentials (42%),
- Other (36%),
- Payment (19%) (breaches)
Top IG1 Protective Controls
- Security Awareness and Skills Training (14)
- Access Control Management (6)
- Secure Configuration of Enterprise Assets and Software (4)
The Verizon DBIR uses organic almond milk and toilet paper – we will use the example of primed lumber and DIY tools for our examples of shortages that surround the manufacturing supply chain and implications of 2020. While facilities were shut down, you might think…cool we might get some time to relax…the answer to that was a BIG NO. Manufacturing saw ransomware as a significantly increased role in malware associated breaches (61.2%) in relation to previous years, overtaking both DoS and Phishing as the most common varieties of attacks.
How Ordr Can Help
It wouldn’t be a good vendor blog if we didn’t also mention that we are willing to help out and give you a 30 day free trial. For more information on how Ordr delivers visibility and security of all connected devices — from traditional servers, workstations and PCs to IoT, IoMT and OT devices, contact us today.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogQ&A with Tom Stafford, CTO for CDW Healthcare
BlogQ&A with Tom Stafford, CTO for CDW Healthcare…the device was tested, it could never be altered. This included the operating system on the off the shelf computer. So, the manufacturers never changed them or patch the OS…
Risk Management
Q&A with Tom Stafford, CTO for CDW Healthcare
7Min ReadBy Tom Stafford

Tom Stafford, CTO with Ordr partner CDW, works hard to educate healthcare customers on which tools to use to best optimize patient safety and hospital resources, and protect the enterprise from cyber risk. As a former hospital CIO, he knows the challenges from the inside. A little background on why I’ve agreed to do this guest QA blog for Ordr:
In my role as CTO at CDW Healthcare, I talk to former healthcare peers, in an advisory capacity, to help them protect patient safety and resources with the best cybersecurity technology solutions. Prior to joining CDW, I was CIO of Halifax Health where we deployed Ordr for our medical device security needs
I’ve been at CDW for slightly more than two years, after more than two decades in the healthcare trenches, most recently as the former CIO of Halifax Health. I decided on a different role at CDW to bring best practices and cybersecurity technologies to my CIO colleagues who are on the forefront of fighting the cyber war. If the healthcare industry could more effectively collaborate and share security expertise to mitigate cyber-attacks, we would stand a much better chance against the cyberattacker army working together against us every day!
What is your primary goal as the CTO of CDW Healthcare Division?
To bring awareness to our healthcare customers on the importance of bringing modern IT tools into healthcare organizations to optimize patient safety and hospital resources. With Ordr’s cybersecurity solution there are many ways network visibility helps hospitals beyond, of course, ransomware, but also what’s happening with device utilization, what’s happening with compliance and what’s being communicated externally. There are several important use cases we want to advise our customers about to develop a proactive plan before something bad happens.
Why is IoT and connected device monitoring and enforcement so unique for hospitals?
There’s a problem with biomed devices and it’s not going away. There will always be biomed devices that have outdated and unsupported operating systems. In the beginning, when first purchased, they were of course running mainstream and perhaps even state of the art operating systems, but now these operating systems are no longer supported by the manufacturers. As a result, O/S patches are no longer available to address vulnerabilities, even though these devices are still within their useful lifecycle and are still viable, delivering strategic care for patients and revenue to healthcare organizations.
Why weren’t patches performed on outdated operating systems on biomed devices?
Unfortunately, this is due to the biomedical industry. As a medical device design engineer for ten years, I may have helped cause the problem, although we thought it made sense the way we did it back then. We would buy an off the shelf computer and put it in a cabinet or a device we were creating, and it would run it. The computer we installed ran whatever the latest operating system was at the time. The issue back then was per the FDA 510k rules for class two, and three medical devices once the device was tested, it could never be altered. This included the operating system on the off the shelf computer. So, the manufacturers never changed them or patch the OS because they could not!
Can you patch today?
In 2016, the FDA reversed their guidelines and said you can patch devices now because it is important to upgrade operating systems. But it was a guideline, it was not a mandate. Because it was a guideline and because it is hard for biomedical manufacturing companies to transition to have a global patch program for all the devices they sell, they do not do it. And they do not want to release the product to an IT team to open it up and obviously, upgrade the operating system or patch it due to inherent risk on their part, because it might make their system not work properly.
Bottom line, the problem is going to persist because biomed devices will continue to outlast the useful life of their operating systems and CFOs do not want to replace a $4M imaging device that makes the hospital money every day only because it has a security vulnerability.
If you don’t patch what can the CISOs and security leaders to do?
They are stuck, because now they have a known vulnerability in their system, and they must do something about it. This is the reason I was introduced to Ordr.
How did you select Ordr for addressing the patching issue?
To get the security and network teams to completely agree on something was amazing.”
Our first step was to do a POC (proof of concept) by my IT security team. A few weeks later, my network and security team had a meeting with IT leadership to show the results of the POC. We were all blown away. I’ll never forget that moment because everyone was happy, even joyous which doesn’t normally happen with software in general.
To get the security and network team to completely agree on something was amazing, because normally, they have a little contention just due to their job functions where one wants data to flow, and the other one wants to control data.
Once deployed, did you meet your objective?
One of the major tenants of cyber security is to understand your landscape. And that includes all devices connected to your network. Are they patched? Or are they outdated and unsupported?“
I was amazed. Ordr worked and it worked well. We purchased Ordr originally because I knew I had a problem with older biomed devices running Windows XP. Before Ordr, our vulnerability scans would find them but then they would disappear because of their dynamic nature of how they connected to the network. And if we didn’t find them that very minute and physically locate them, we would lose sight of them. It was a real problem. We could not see and didn’t know our full landscape. And that is scary, because to me, one of the major tenets of cyber security is to understand your landscape. And that includes all devices connected to your network and their patch status. Are they patched? Or are they unsupported? It is not just your IT devices, it is anything that is connected to your network. As you know, in the last five years, that’s grown greatly with so many other things connecting now, and you still have these legacy biomed devices that are out there too.
How did you manage all the outdated and unsupported biomed devices you found?
When we fully deployed Ordr, we noticed a couple of things right away. First, we not only found all the biomed devices, but we also now had an inventory of them. And we were able to understand what operating systems they were running and could have a plan of what to do about it. At that time, we had three choices.
- Replace the device. But again, financially that might not be viable.
- Get the manufacturer to patch it, or to upgrade the operating system so it was no longer vulnerable.
- Bury it by micro segmentation. Through micro segments, you have controls around it from the internal firewall, Even though we have controls, you still need to monitor it and we used Ordr.
When I would talk to people, they understood Splunk monitors user behavior. Ordr monitors device behavior. I can now set upper or lower limits on the device itself. And if Ordr detects something odd, we can be alerted
What was the next step to managing these vulnerable devices?
If the hacker gets in and gets to an XP device, that would be the biomed device, it takes about 20 minutes for them to own that device. If the device is connected to a server, then they can own the network.”
The roadmap was moving more towards enforcement and that sat well with me. The reason why is that hackers do not attack during the day, they tend to attack at night and on weekends. At those times, depending on what hospital you’re at, you might be relying on a managed Security Operations Center (SOC), which is pretty good. Or you might be relying on your on-call staff to fight any cyber problems in the middle of night. And there’s latency in that. If the hacker somehow gets in and gets to an XP device, it takes about 20 minutes for them to own that device. If there are any servers connected to that kind of device, then they have the opportunity to own the network. Now the world turns bad quickly. To have a system that has deep understanding of proper network communication related to strategic IoMT devices and can monitor those devices 24/7and alert us when something is wrong, is great.
Next, if I could actually enforce policy, or at least send API commands from Ordr to change the policy in my firewall or my NAC, these devices could shut down communication at 3 am in milliseconds. This is much better than the time it would take the team to figure out what the problem was, based on a calls to the service. IoT and connected device security enforcement can stop a virus from propagating
What else could you do now with full visibility of your network landscape?
Device utilization is a big deal. Ordr creates custom views per departmental stakeholders. For example, the Biomed and/or Operations team could go into their Ordr view and just look at medical device utilization. Their view doesn’t allow them to see the other aspects of cyber or network information Ordr was capturing.
I like to tell the story that if a clinician wants another ultrasound device in your hospital, but your ultrasound fleet is only being utilized 30% of the time, you do not need another ultrasound, you need to improve your processes to get better utilization of your devices. And when you do this, you save money by not buying another device while improving your processes. And so that is valuable.
For some devices, Ordr was monitoring down to the battery life level. Since we all know batteries go bad, to have an alert to the Clinical Engineering team for low batteries on biomed devices is cool and important.
The next important outcome we gained is forensic device data. Ordr collecting all device data in the cloud. When we have a potential security incident, we called the security team. The team uses Ordr to determine what device was bad and see who it was talking to and how it was talking, to see if it was doing things that it should not do. We always used Ordr during any security incident as part of our incident response toolbox. And it worked well. And even the network team liked it because Ordr does an incredibly good job of showing how everything communicates, and what it is trying to communicate and what is being blocked from communication.
To sum it up, first and foremost the outdated and unsupported biomed devices are a problem that is not going away, ever! Operating systems only have a life for so long, so you need something to address the issue. With Ordr though, you get more use cases including device utilization management, forensic data and the network team gets to see how things are communicating, outside of their regular forensic toolbox. So that’s why I like Ordr.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogOrdr Security Bulletin – Volt Typhoon State-Sponsored Cyber Actor
BlogOrdr Security Bulletin – Volt Typhoon State-Sponsored Cyber Actor…Zero Trust policies. Other helpful Links: Living off the Land https://www.crowdstrike.com/cybersecurity-101/living-off-the-land-attacks-lotl/ CISA SOHO Device Manufacturer Alert https://www.cisa.gov/sites/default/files/2024-01/SbD-Alert-Security-Design-Improvements-for-SOHO-Device-Manufacturers.pdf Volt Typhoon Attack https://www.darkreading.com/cloud-security/volt-typhoon-soho-botnet-infects-us-govt-entities Router Investigation https://blog.lumen.com/routers-roasting-on-an-open-firewall-the-kv-botnet-investigation/ Detailed report by Security Scorecard https://www.securityweek.com/wp-content/uploads/2024/01/Volt-Typhoon.pdf…
Security Bulletin
Ordr Security Bulletin – Volt Typhoon State-Sponsored Cyber Actor
4Min Read
By Pandian Gnanaprakasam

Chinese state-sponsored threat actors in the VoltTyphonn group are targeting vulnerabilities in small office/home office devices to compromise enterprises. Users of the Ordr platform can find, identify, and protect at-risk assets targeted by Volt Typhoon. Authors: Pandian G, Gowri Sunder Ravi, Srinivas Loke
Summary of Advisory from FBI/CISA
Actors with malicious intentions, particularly the People’s Republic of China-backed Volt Typhoon group, are manipulating small office/home office (SOHO) routers by exploiting software vulnerabilities that manufacturers need to address through secure software engineering.
More specifically, the Volt Typhoon actors are utilizing security flaws in SOHO routers as springboards to further infiltrate U.S. critical infrastructure entities. The Cybersecurity & Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) have issued this warning due to recent and ongoing threat activities.
The FBI & CISA urge SOHO router manufacturers to incorporate security features into their products from the start, and encourage all SOHO router users to demand higher security standards from the outset.
“China’s hackers are targeting American civilian critical infrastructure, pre-positioning to cause real-world harm to American citizens and communities in the event of conflict,” said FBI Director Christopher Wray. “Volt Typhoon malware enabled China to hide as they targeted our communications, energy, transportation, and water sectors.”
One of the main vulnerabilities that Volt Typhoon has exploited is found in Cisco and NetGear routers. These routers were used by the group to route their network traffic, thus enhancing the stealth of their operations and lowering overhead costs for acquiring infrastructure.
Information about Volt Typhoon: (Also tracked as Insidious Taurus)
- Volt Typhoon is a state-sponsored actor based in China, known for its espionage and information-gathering activities. It has been active since mid-2021 and has targeted critical infrastructure organizations in the United States, spanning various sectors, including communications, manufacturing, utility, transportation, construction, maritime, government, IT, and education.
- Volt Typhoon employs a variety of tactics, techniques, and procedures (TTPs) to achieve its objectives. One of their primary strategies is the use of “living-off-the-land” techniques, which involve using built-in network administration tools to perform their objectives. This strategy allows the actor to evade detection by blending in with normal Windows system and network activities, avoiding alerts from endpoint detection and response (EDR) products, and limiting the amount of activity captured in default logging configurations.
- They also try to blend into normal network activity by routing traffic through compromised small office and home office (SOHO) network equipment, including routers, firewalls, and VPN hardware.
- Mitigation strategies against Volt Typhoon include identifying and examining the activity of compromised accounts, closing or changing credentials for compromised accounts, and implementing behavioral monitoring to detect activity that uses normal sign-in channels and system binaries.
- Of importance is the “KV-Botnet,” revealed in a report from Lumen’s Black Lotus Labs, is designed to infect end of life small-office home-office (SOHO) network devices developed by at least, but not limited to, four different vendors. It comes built with a series of stealth mechanisms and the ability to spread further into local area networks (LANs). Microsoft has confirmed that many of the devices include those manufactured by ASUS, Cisco, D-Link, NETGEAR, and Zyxel.
- Since at least February 2022, KV-Botnet has primarily infected SOHO routers like the Cisco RV320, DrayTek Vigor, and Netgear ProSafe product lines. As of mid-November, it expanded to exploit IP cameras developed by Axis Communications.
- Microsoft assesses the “Volt Typhoon campaign is pursuing development of capabilities that could disrupt critical communications infrastructure between the United States and Asia region during future crises.”
Banned Manufacturers
Section 889 of the National Defense Authorization Act (NDAA) prohibits the use of federal funds to buy certain telecommunications equipment or services from specific manufacturers. These manufacturers include:
- Huawei Technologies Company
- Hytera Communications Corporation
- ZTE Corporation
- Hangzhou Hikvision Technology Company
- Dahua Technology Company
- Any subsidiary or affiliate of these companies
Section 889 also prohibits the government from contracting with any entity that uses certain telecommunications equipment or services produced by these manufacturers. This prohibition applies to all purchases, regardless of the size of the contract or order.
How Ordr helps
See
- Ordr automatically discovers and classifies and profiles all devices based on the manufacturer, make, and model.
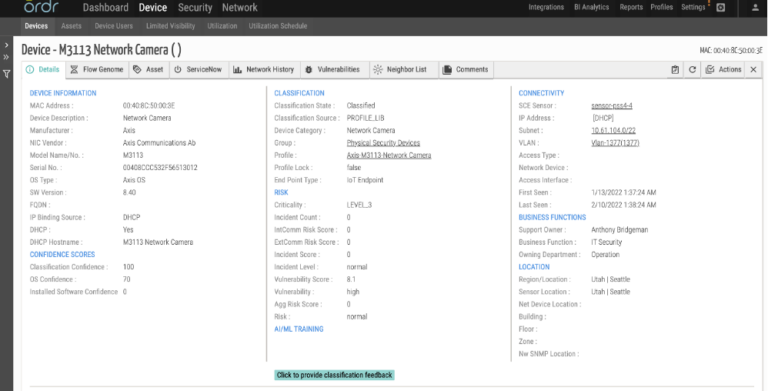
- For this attack Ordr discovers the devices known to be impacted, including those from manufacturers like Axis, Netgear, Dray Tek, D-Link, Zyxel. These devices are automatically tagged and can be easily tracked in the system.
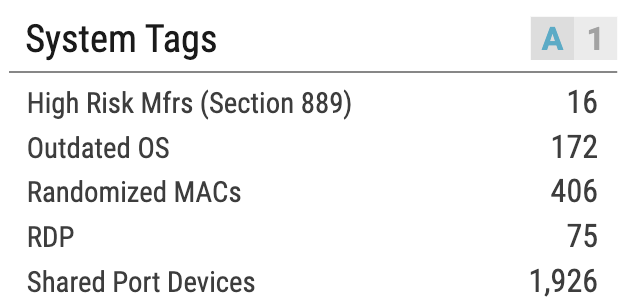
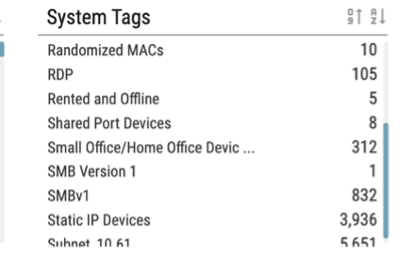
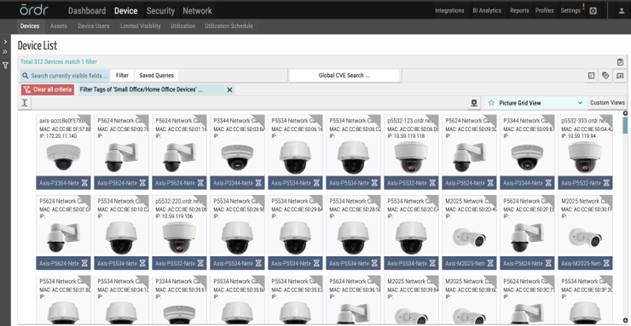
- Ordr identifies and highlights Small Office / Home Offices devices in our customer environment mentioned in the advisories and produces a device download csv/xlsx report from the reports tab for customers to easily download in addition to the ability to lookup devices directly from the tag section.
Note: Recommendations from federal agencies – Federal agencies recommend that internet-facing SOHO devices be up to date and follow guidelines mentioned in advisories from government agencies.
Know
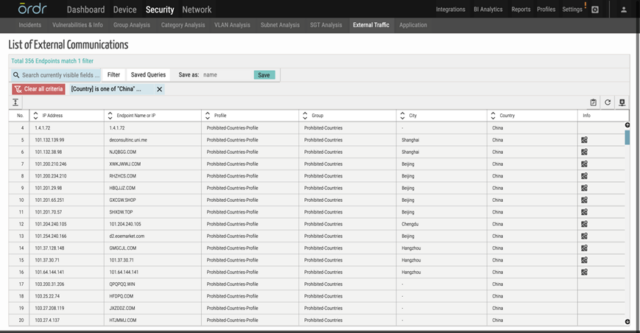
- In real-time, Ordr ‘s external IP/IOC tracks every communication to prohibited IP/URLs.
- Ordr provides in depth insights into category traffic analysis that highlights the communication patterns between devices and external entities, making it easier to see devices communicating to list of prohibited countries including China.
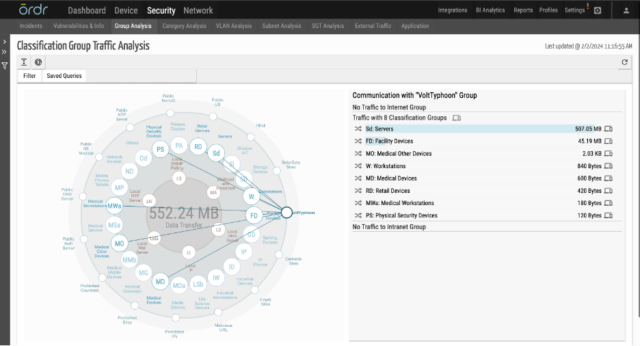
- Ordr uses a cloud-based threat intelligence platform where the list is continuously updated, and all communications are marked accordingly in the Ordr Security Threat Card.
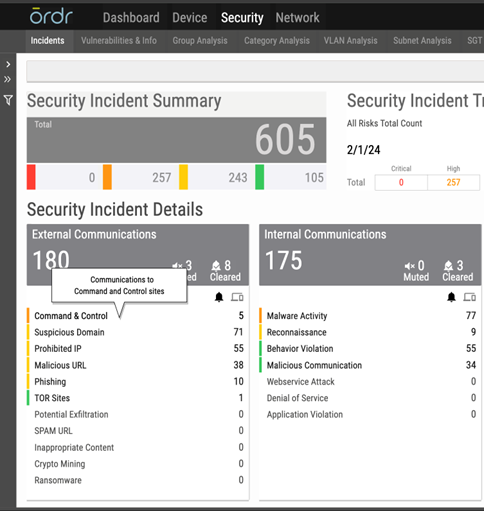
- Ordr has an IDS engine that can detect attacks originating from Volt Typhoon and generate alerts based on analysis of packets transacting over the wire.
- IDS Rule: Ordr’s network data collectors process packets for Deep packet inspection and at the same time checks for signatures and this rule that detects presence of “Volt Typhoon User Agent” and generates a high severity alarm.
- Ordr also provides the capability to baseline all the communications based on profile, location, business function, or any customized entity using our AI/ML techniques. Ordr can trigger anomalies based on any deviations observed for this traffic.
Secure
- Ordr enables segmentation of impacted devices and limiting access to only must-have communications based on Zero Trust policies.
Other helpful Links:
- Living off the Land https://www.crowdstrike.com/cybersecurity-101/living-off-the-land-attacks-lotl/
- CISA SOHO Device Manufacturer Alert https://www.cisa.gov/sites/default/files/2024-01/SbD-Alert-Security-Design-Improvements-for-SOHO-Device-Manufacturers.pdf
- Volt Typhoon Attack https://www.darkreading.com/cloud-security/volt-typhoon-soho-botnet-infects-us-govt-entities
- Router Investigation https://blog.lumen.com/routers-roasting-on-an-open-firewall-the-kv-botnet-investigation/
- Detailed report by Security Scorecard https://www.securityweek.com/wp-content/uploads/2024/01/Volt-Typhoon.pdf
- Joint Cybersecurity Advisory https://media.defense.gov/2023/May/24/2003229517/-1/-1/0/CSA_Living_off_the_Land.PDF
- Microsoft Blog https://www.microsoft.com/en-us/security/blog/2023/05/24/volt-typhoon-targets-us-critical-infrastructure-with-living-off-the-land-techniques/
- CISA Director Statement https://www.cisa.gov/news-events/news/opening-statement-cisa-director-jen-easterly
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogCyber Insurance And Cybersecurity Controls:
BlogCyber Insurance And Cybersecurity Controls:…in 2021. Then, in 2022 with the outbreak of hostilities between Russia and Ukraine there was another sudden shift in the industry’s risk calculus. The potential for acts of cyberwar…
Risk Management
Cyber Insurance And Cybersecurity Controls:
Straight Answers for a Confusing Market
5Min Read
By Danelle Au

Recent developments have caused confusion in the cyber insurance market. Ordr looks at recent trends affecting cyber insurance and security controls to offer insights and straight answers for enterprises looking to buy or renew policies. There has been a lot of confusion about the future of cyber insurance following recent statements by market makers Lloyd’s of London and Zurich Insurance Group. In late 2022, Lloyd’s informed underwriters in its syndicate that they would be required to explicitly exclude coverage for damages related to state sponsored cyberattacks. More recently Zurich CEO Mario Greco told the Financial Times, “What will become uninsurable is going to be cyber,” adding that if a threat actor “takes control of vital parts of our infrastructure” the results may be uninsurable.
Those statements, coupled with well publicized policy price increases for 2023 that are as much as three times higher than what many customers paid the year before, have fueled concerns that cyber insurance coverage may be unavailable in the near future and that many underwriters may simply get out of the business. In many ways what we are seeing is the maturation of what remains a relatively new market trying to find its footing in a dynamic threat and risk landscape. Because of that, questions and confusion are rampant, and rational answers from seasoned experts are needed. That is why Ordr recently convened the Cybertrends and the Impact on Cyberinsurance webinar with Marc Schein, national co-chair, cybersecurity center of excellence, Marsh McLennan Agency, and Jim Brady, vice president cybersecurity and risk management, and CISO at Fairview Health.
A Little History
For context, the first cyber insurance policy was written in 1997 by AIG and, according to The Insurance Journal, “Covered only third party suits arising from breaches originating from outside the company.” Optimism for the insurance industry’s first new product category in decades was high, but as underwriters began entering the market in the early 2000s, the challenges associated with an increasingly difficult threat landscape became evident. The number of threat actors, including lone wolf hackers, criminal syndicates, and state-sponsored adversaries, was growing quickly, and the tools available to them were becoming more effective. As new threats emerged, the insurance industry struggled to keep current.
Fast-forward to 2020 and, with the outbreak of Covid-19, things got bad. In the chaos of a global pandemic threat actors took advantage and began focusing on the use of ransomware. Few organizations were prepared for the attacks, and the insurance industry’s risk calculations were turned upside down. Schein said many “underwriters were paying out more in claims than they were collecting in premiums because they were unprepared for the rise in ransomware.”
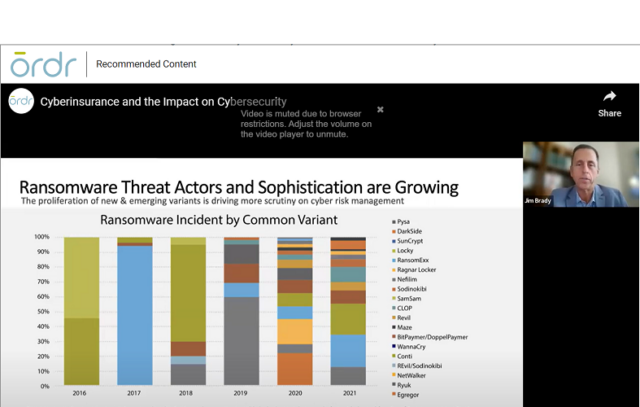
Ransomware Disruption
According to Marsh, there were 4,000 ransomware attacks per day in the U.S., and the cost to the insurance industry was $20 billion in 2021. Then, in 2022 with the outbreak of hostilities between Russia and Ukraine there was another sudden shift in the industry’s risk calculus. The potential for acts of cyberwar targeting critical infrastructure and industry, coupled with continued escalating risks for industries like healthcare, forced the insurance industry to make numerous adjustments to its risk assessments, culminating in steep premium increases along with policies and exclusions written with greater specificity.
In hindsight these changes shouldn’t come as a surprise. If anything, organizations that used cyber insurance as a major part of their risk management strategy had been getting a great deal. But as the industry has become more educated on the risks, that experience is now forcing organizations to (finally) take their own cybersecurity programs more seriously. No more cutting corners. Instead, to qualify for coverage, savvy insurers are demanding that organizations be able to demonstrate that they have complete visibility and understanding of their IT estates, and have implemented controls sufficient to protect their assets.
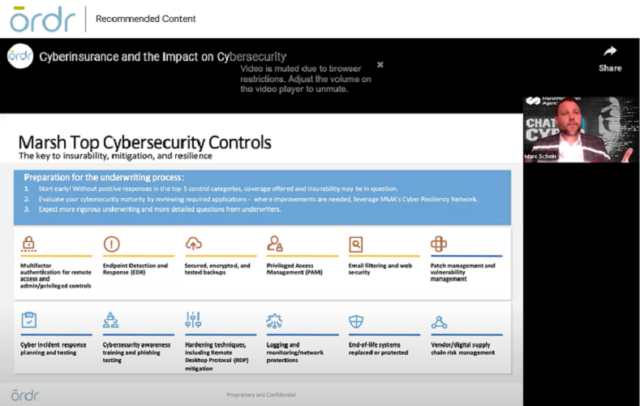
Gain Control
As an early player in cyber insurance, brokerage, risk management, and reinsurance services firm, Marsh McLennan has been a leader in its industry with a deep understanding of what it takes for customers to protect themselves from cyberthreats. The firm offers a list of twelve security controls it requires of its customers that Schein shared during the webinar–along with the caveat that a failure to demonstrate use of the first five is likely to disqualify the organization for coverage. Those twelve controls are:
- Multifactor authentication (MFA) for remote access and admin/privileged controls
- Endpoint detection and response (EDR)
- Secured, encrypted, and tested backups
- Privileged access management (PAM)
- Email filtering and web security
- Patch management and vulnerability management
- Cyber incident response planning and testing
- Cybersecurity awareness training and phishing testing
- Hardening techniques, including remote desktop protocol (RDP) mitigation
- Logging and monitoring/network protections
- End-of-life systems replaced or protected
- Vendor/digital supply chain risk management
The Marsh checklist signals a growing savvy within the industry that knows more information means more accurate risk assessments. As Robert Parisi, North American head of cyber solutions for Munich Re recently told the Wall Street Journal, “The underwriting is aggressively moving toward, ‘How can we get a deeper, more insightful look.’”
What’s missing on this checklist? In the webinar, we raised the question of why asset visibility, security, and segmentation were not included in the list of controls. In fact, the broad “endpoint detection and response”, “patch management and vulnerability management,” and “end-of-life systems replaced or protected” all require visibility into assets and the risks they bring.
Deeper Insight
That requirement for deeper insights into the customer’s risk posture can translate to an advantage for some organizations when shopping for a cyber insurance policy. The ability to provide proof of asset visibility across their entire enterprise can mean a stronger position when shopping for a policy and negotiating with potential underwriters. Brady discussed the advantages Fairview has enjoyed by “coming to the table ready to roll” with necessary controls fully documented. This includes proof the organization has gone beyond an insurer’s requirements by implementing complete asset inventory management and network segmentation to ensure the organization’s ability to quickly detect and effectively mitigate risks.
How can you even detect something bad going on [with a device] if you don’t even know you have it?”
Jim Brady Fairview Health“How can you even detect something bad going on [with a device] if you don’t even know you have it?” Brady asked, highlighting the strategic advantage of having complete device visibility across the entire network.
Good News
Schein agreed, and delivered surprisingly good news when he said, “If you are engaging better controls and you do improve your security posture, the marketplace is getting significantly better.” He then shared that, even as sharp premium increases grab headlines, 14% of Marsh’s customers enjoyed a price decrease by aggressively improving their overall security posture.
If you are engaging better controls and you do improve your security posture, the marketplace is getting significantly better.”
Marc Schein Marsh McLennan AgencyClearly, security leaders that have invested in maturing their cybersecurity program with asset management, and excellent controls at the core are reaping the benefits by not only hardening their enterprises against attacks, but by reducing their overall risk profile. Many security leaders recognize that Ordr can play a key role in that equation by giving its customers the ability to see across the entire enterprise to continuously discover and classify an organization’s complete connected device inventory. What’s more, the Ordr Data Lake ensures deep insight into every device’s risk profile with a real-time understanding of communications and operational behavior that could signal an indicator of compromise. Those insights can trigger dynamically created security policies that can be quickly enforced to prevent or contain an attack, and also give insurers confidence that they are working with a customer that takes the concept of Zero Trust seriously and employs strong risk reduction practices.
Danelle Au
Danelle Au has more than 20 years of experience bringing new technologies to market. Prior to Ordr, she was CMO at Blue Hexagon, a deep learning for malware protection company, and CMO at SafeBreach where she helped build the marketing organization and and define the Breach and Attack Simulation category. Previously, she led strategy and marketing at Adallom, a cloud security company acquired by Microsoft. She was also Director, Security Solutions at Palo Alto Networks, driving growth in critical IT initiatives like virtualization, network segmentation and mobility. Danelle was co-founder of a high-speed networking chipset startup, co-author of an IP Communications Book and holds 2 U.S. Patents. She has an MSEE from UC Berkeley
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
Knowledge BaseIoT Security: What You Need to Know
…and address the security risks posed by IoT hardware and software, and take steps to protect their devices, their networks, and their data. These steps include: proper discovery and classification…
IoT Security: What You Need To Know
7Min ReadIoT devices present great opportunities to improve business efficiency and productivity. But they also present novel challenges, such as securing the sensitive data they transmit, preventing device sabotage, targeting by threat actors, and ensuring that IoT devices don’t become part of botnets that commit malicious acts.
An organization with IoT devices on its network must make IoT security a priority. Many organizations aren’t even aware of all the devices connected to their networks. “Shadow IoT” refers to unmanaged and unseen devices—such as employees’ cell phones or smart watches, or devices set up for testing and then forgotten—connected to the network that can present a huge security risk. As many as 20% of all connected devices may be shadow IoT. This article explains what IoT security means, the main IoT security challenges businesses face today, and how to protect IoT devices against security threats.
What is IoT?
The Internet of Things, or IoT, refers to the billions of non-traditional computing devices that use the Internet to exchange data. These devices range from soil condition monitors, to Internet-connected refrigerators, to “smart” traffic lights. What they share in common is that they can monitor and/or control critical systems and have access to sensitive data.
What is IoT security?
IoT security is the proper asset inventory, visibility, and control of devices that are internet-connected to a system of computing devices, mechanical and digital machines, or objects that allow for the exchange or collection of data.
In some ways, IoT security mirrors the strategies associated with traditional network security, but the sensitivity of the data that IoT devices collect, and the systems they manage, means that the stakes of IoT security are greater. An IoT device that can shut down a power plant or collect video of a family inside its home demands greater security controls than a traditional PC or laptop.
https://youtu.be/Ip-E3mkP0dc?feature=sharedHow are IoT devices managed?
IoT security is especially challenging because IoT infrastructure consists of multiple layers, each of which must be secured. IT security teams must ensure that the software that runs on IoT devices themselves is free of vulnerabilities and is updated properly. They also must protect against vulnerabilities in the APIs that IoT devices use to communicate with each other in order. IoT networks, too, must be monitored for intrusions. Finally, the data that IoT devices collect must be stored securely, whether it is retained on the IoT devices itself, or offloaded to a data center.
It’s possible to centralize some of these security processes. For example, a security operations center (SOC) can manage IoT device identification and software updates. Other aspects of IoT security, however, such as testing APIs for vulnerabilities and ensuring that data is encrypted both at rest and in motion, require additional tools.
IoT management roles
The different responsibilities related to IoT device management generally map to different types of teams.
- IT is responsible for device deployment and general management.
- The security team focuses on managing vulnerabilities and designing IoT architectures to be resilient against attacks.
- Device end-users, too, play a role in keeping devices updated, changing default access credentials and so on.
While this division of responsibilities for IoT device management is unavoidable in most situations, it adds to the complexity of IoT security, because it requires coordination between multiple stakeholders to ensure that best practices are followed and enforced.
IoT security challenges
IoT devices are subject to inherent security challenges and vulnerabilities that, as noted above, don’t always exist on conventional hardware.
“Shadow” IoT devices
One major IoT security challenge is the risk of “shadow” devices, or devices that are connected to an IoT network but are not authorized by or known to the network owner. Shadow devices could be added to the network by users who simply don’t know any better, such as an employee who brings an IoT temperature monitor into the office. Or, they could be deployed by malicious parties, such as attackers seeking to carry out industrial espionage via unsecured conference room phones or smart televisions.
A recent whitepaper, Rise of the Machines: 2020 Enterprise of Things Adoption and Risks Report, notes that a significant percentage (10%-15%) of devices in Ordr deployments are unknown or unauthorized. The most memorable instance of this was a Tesla connected to a hospital network; after some investigation, the security teams found that the Tesla belonged to a doctor who connected to the network from his car in the parking garage.
Shadow IoT devices also are prone to infection by malware because, often, they are not properly secured. This is, in part, how botnets like Mirai and Dark_nexus have spread.
Lack of reliable software updates
Often, IoT devices are not properly updated to protect against new security vulnerabilities. First, IoT devices typically are small and deployed in remote locations. An organization may have thousands of IoT devices to manage, so it can be easy for organizations to deploy IoT devices and forget about them. Also, many IoT devices depend on users themselves to update the software, and many users don’t bother to do it, or don’t know they are supposed to do it.
API vulnerabilities
Because exchanging data over the network via application programming interface (API) is part and parcel of what IoT devices do, vulnerabilities within the APIs are a major IoT security risk. If attackers find a flaw in an API, they can use it to intercept data via Man-in-the-Middle (MITM) attacks, or take control of devices in order to launch Distributed-Denial-of-Service (DDoS) attacks.
And because there is no universal IoT API—on the contrary, there are dozens of IoT APIs from different providers, and you can also write your own—there is no single set of API vulnerabilities to track. Security teams should be aware of all potential risks in all APIs that they use.
Default passwords
Many IoT devices ship with default passwords that give users access to the software environments inside the devices. If users don’t change these passwords—which many fail to do—attackers with lists of default IoT passwords can use them to gain unauthorized access to a device and its network.
Implementation of standards
Just as there is no single IoT API, there are no unified standards to govern the design of IoT devices, the types of software they run, or how they exchange data. Instead, there is a litany of competing approaches that evolve constantly along with IoT hardware and software.
From a security perspective, this makes it more difficult to secure IoT devices because there are so many variables at play. There is no single security strategy that can protect against all threats on all IoT devices or networks.
What industries are vulnerable to IoT security threats?
The IoT security threats described above apply to any company or individual who uses an IoT device. However, the risks are particularly great in certain industries due to the potential fallout from a breach, or the sensitivity of the data that IoT devices collect:
- Healthcare: Internet of Medical Things (IoMT) devices collect personal health data and, in some cases, may even be implanted into human bodies. The harm caused by a security breach in this context could be enormous.
- Hospitality: While 76 percent of hospitality companies have IoT initiatives, security risks posed by IoT are a top concern for them, due to the damage to their brands’ reputation that could result from an attack.
- Government: When governments rely on IoT devices to collect data or control physical infrastructure—such as dams or highways—attackers may breach their IoT networks in order to access privileged information or disable critical systems.
- Manufacturing: A breach in a manufacturer’s IoT network could disrupt operations, leading to downtime and significant financial loss.
- Retail: IoT devices can help retailers protect against theft, manage inventory and more. But unsecured IoT devices may also allow attackers to steal customers’ information or disrupt critical business systems.
- Transportation: Transportation networks that rely on IoT devices can be easily crippled by a breach of those devices. If buses require IoT devices to operate, or a plane relies on the IoT to navigate, security problems with those devices may lead to critical damage.
How to protect IoT systems and devices
Many stakeholders play a role in guaranteeing IoT security. Device manufacturers must design device hardware to be resistant against attack. Software developers must write secure code to run on the devices. Engineers who deploy and manage IoT devices must take steps to mitigate security risks. End-users who access data or systems via the IoT must keep the devices secure and avoid giving access to unauthorized users.
While the roles of each of these groups in IoT security vary, they can all use a common set of guidelines to help assess and address potential IoT security issues.
Discovery
All stakeholders should strive to discover unauthorized devices that appear on an IoT network. These include ephemeral assets that may go offline at any time and then reappear in a new physical and network location. It is vital to have accurate information in order to understand and classify these devices.
Understand behavior
Once a security team discovers all devices on an IoT network, it needs to know the intended role of each device in order to interpret and predict the device’s behavior patterns: which kinds of data it will generate, when it will come online and go offline and so on. Look for anomalies within these patterns to identify potential breaches.
Risk assessment
Not all IoT devices pose the same level of risk. A medical device that controls a patient’s heart is higher-risk than an IoT device that controls a lamp. To assess risk accurately, stakeholders must develop risk profiles for each device on their networks. Then, they can prioritize security incidents appropriately, and know which devices to update first when a security vulnerability is announced for a device they manage.
Generate policies
Following the identification and classification of all devices on the network, IT and security teams can establish segmentation policies to protect high-risk, vulnerable, or mission-critical devices from the rest of the network. Segmentation policies also can control how each device communicates, manage access to other resources on the network, and ensure that every new device is evaluated and secured in real time.
IoT security: final thoughts
In order to capitalize on the benefits of IoT devices, organizations must acknowledge and address the security risks posed by IoT hardware and software, and take steps to protect their devices, their networks, and their data.
These steps include: proper discovery and classification of all IoT devices on a network; continuously tracking device behavior; performing risk assessment; and segmenting vulnerable and mission-critical devices from others.
The Ordr asset inventory management platform gives organizations the power to enable visibility and security of their network-connected devices, with a simple and powerful solution to identify, classify, profile the behavior and risk and automate action for every network-connected device in the enterprise. One of the differentiated actions with Ordr is that security and IT teams can proactively create microsegmentation policies to only allow sanctioned communications for every class of device
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogCyber Attacks in Smart Buildings
BlogCyber Attacks in Smart Buildings…of operation, and underutilization. Compare usage across facilities to for better distribution Identify offline devices and bring them back into service Understand the usage patterns and adjust schedules Make better-informed…
Risk Management
Cyber Attacks in Smart Buildings
The Threat Is Here
6Min Read
By Pandian Gnanaprakasam

Smart buildings and smart cities deliver great benefits for citizens. Unfortunately, they are popular targets for threat actors. To protect networks, facilities, and people you must understand the challenges and adopt new cybersecurity techniques. Smart Cities and connected buildings offer tremendous benefits yet the question of their security is becoming increasingly crucial. The stakes are all the more important as intelligent building management systems are not limited to home automation, their reach also extends to the controls of the building safety system. In conducting a telemetry survey of 40,000 smart buildings, anti-virus firm Kasperky found that 37.8% of them had already been the target of a cyber attacks. And that was only during the first half of 2019.
Connected buildings typically combine sensors and controllers to monitor and automate the operation of various systems, such as building access, elevator, ventilation, electricity and more. Everything is centralized on a single machine, most often a simple PC connected to the Internet, and therefore as vulnerable as any personal computer. Connected buildings can be offices, houses or residential buildings, but also hospitals, shopping centers, public transport or even prisons.
Attacks are becoming more sophisticated and spreading
Attacks have been detected all over the world, with a higher rate in Western Europe, India, China, and Brazil. Kaspersky investigated the source of the attacks, revealing statistics that are similar to those for industrial systems. Nearly a quarter of intrusions come from the web, while removable drives and email software are each responsible for 10% of incidents. “Although these numbers are relatively low compared to the threat landscape, their impact should not be underestimated,” said Kirill Kruglov, a cyber security researcher at Kaspersky.
Kaspersky noted that most attacks do not specifically target connected buildings and infect all types of networks. Buildings can, therefore, be victims of the same problems as individuals, with spyware (11.3% of detections), computer worms (10.8%), phishing (7.8%) or the risk of see the files taken hostage by ransomware (4% of detections). Buildings are also vulnerable to other threats, which are not detectable by the security software, such as denial of service attacks.
Businesses are facing a worrying growth of cyber threats in 2019.
Cyber-attacks are becoming more sophisticated and are forcing IT professionals to equip themselves with computer security solutions and even smart automated systems that can quickly detect attacks. The best systems must also deploy strategies to guard against these cyber threats holistically equipment, training, recruitment of dedicated technical teams, etc. Considering the valuable assets out there we feel cyber threats against businesses will intensify in the future.
Increased Attack Sophistication: Multiplication of Attacks on Connected Objects
Attacks against Connected Objects (IoT) have multiplied throughout 2018, an increase of more than 200% compared to 2017. While everyone wants devices to be interconnected and connected to the Internet, strong growth in the number of weakly secured connected objects, suggests a very sharp rise in cyber attacks over the next few years.
Cyber criminals take control of connected objects in order to create large networks of Botnets to launch Denial of Service (DDoS) attacks. The United States, for the moment, is the first victim of hackers with more than 46% of global botnets from US-based IP addresses followed by China at 13%.
Protecting Yourself Proactively
Some IoT security solutions just identify problems and signal alarms. This does not alleviate the overworked IT and Security Staff dealing with the increasing threat of cyber attacks on smart buildings. At Ordr, we provide protection proactively. We see the objects and inventory the assets and then we take it a step forward with automated policy generation and automated remedial action using A.I. and machine learning. Ordr also protects a smart building before a potential attack by monitoring all device communications and detecting any anomalies and any behavior that seems unusual.
Be Proactive
The only way to protect yourself is to arm yourself with diligence. Most cyber-attacks of this type come from human errors within an organization, such as an employee opening an infected file or downloading malicious software. For this reason, our intelligent Ordr system is here to face the sophisticated attacks by:
- Detecting anomalies, preventing and isolating attack attempts, segmenting networks when necessary and diligently monitoring the flow of traffic.
- What’s unique is that Ordr policy becomes smarter over time and establishes policies to maintain security and order.
The bad guys can leverage A.I. We take it a step further
In some cases, hackers can use malware and try to mimic the normal behavior of a network in order to spread to more machines, while avoiding detection. Malware enriched by artificial intelligence will be able to infest much faster information systems, able to adapt their behavior according to their environment.
Traditionally, attackers maintain communications with compromised systems using command and control servers. If the malware can use artificial intelligence to autonomously determine how to mimic normal behavior while they are moving, for example by detecting and using local identifiers, attackers no longer need a command server and control, and the malware becomes much more difficult to detect.
The combination applied by Ordr’s automation and artificial intelligence system is the ideal combination to streamline and strengthen a cyber security defense line against sophisticated AI attacks.
ORDR offers specific ways to in this part to face sophisticated attacks as we use machine learning to inspect and baseline the behavior of our growing catalog of devices. Our SCE automatically and continuously detects flows, learns, adapts and expands our data lake. The policy generation is what really differentiates us from the competition as we close the loop of detection, learning, policy and implementation.
Ordr’s ability to learn and adapt
In the future, companies will increasingly connect IoT devices to their networks. To protect themselves and strengthen their defense, particularly as it relates to smart building attacks, we recommend enterprises to consider Ordr’s proactive protection system. The platform is built from the ground up to ensure full security and automated policy generation to protect from the coming attacks on smart buildings.
Automation involves a range of skills such as process automation, test automation, security automation. Security automation is designed to reduce risks, operational errors and solve cybersecurity problems. Threats often come from abnormal use of the data. Security tasks are often prone to errors when processing large volumes of data and creating fast, reliable, and accurate solutions. The ORDR system is fast, dynamic and leverages automation and machine learning to go beyond incident reports. We do feel that the number of ransomware injected into a system by cybercriminals is exponentially greater than the threat detection measures taken by businesses.
Cyber security teams are flooded with alarms and alerts around the clock. We dont want to add to the process and instead fix things automatically. Delayed investigations can lead to devastating data breaches if there is a sub-optimal response to the detection of the threat and relying on manual intervention will not scale.
Ordr’s system allows IT managers to focus on complex types of attacks as attacks become more sophisticated. Along the way ORDR policy becomes smarter and establishes policies so that a human being is not forced to do so.
Identify & Classify
Ordr Systems Control Engine (SCE) is the only purpose-built solution that fully maps every microscopic device detail and its context – the device flow genome – at massive scale, using machine learning to completely and continuously inspect and baseline the behavior of every device. Ordr detects exposed vulnerabilities and delivers intricate risk scores for priority attention and mitigation. All in real-time, all-the-time, delivered in a simple dashboard.
- Discovers every device in your environment.
- Tracks risk scores to focus attention on high-risk devices.
- Maintains a real-time database and tracks changes.
- Integrates with management and workflow tools.
Regulation
Ordr Systems Control Engine monitors and analyzes all device communications, and delivers real-time communications flow analytics. Regulate flow and behavior by device type, group, location, function, application, the control is yours. Ordr SCE automatically detects anomalous behavior including out of flow communication, unusual data and application usage, and off baseline cadence and activity. And it’s real-time, so any new connected systems are immediately regulated when connected.
- Analyzes all device communications 24×7.
- Learns correct behaviors and creates conversation maps.
- Group systems by type, location, function, application.
- Anomaly detection prevents and isolates attempted attacks.
Figure 2: Connected Smart Building
Source: Ordr
Secure
The Ordr SCE architecture is unique in its ability to process enormous quantities of data in real-time, using sophisticated AI to deliver closed-loop security, automatically generating policies for each class of device. The Ordr SCE is integrated with the exisiting network and security infrastructure management tools to implement policies directly and automatically. There is no need to upgrade your network. This is truly no-touch, agent-less protection for business-critical assets.
- Micro-segmentation per NIST
- Access control policy generation
- Full integration with existing NAC solutions
- Program firewalls, wired/wireless access network
System Utilization
Ordr gives you in-depth insight into what’s happening with your systems. High capital and fleet equipment needs to be used efficiently for maximum ROI. Ordr gathers detailed utilization information across the entire enterprise, giving you intelligence about detailed device usage, usage type, hours of operation, and underutilization.
- Compare usage across facilities to for better distribution
- Identify offline devices and bring them back into service
- Understand the usage patterns and adjust schedules
- Make better-informed purchasing decisions
The Ordr Systems Control Engine: Why stop at visibility?
Ordr has developed a smart system than can see everything that is connected to the network and quickly deploy policies to protect the network. The Ordr Systems Control Engine goes beyond what competitors do in that we offer behavioral profiling, flow monitoring, and integrated risk management. Instead of just “blacklisting” non compliant devices, Ordr takes it a step forward “whitelisting” connected devices, providing compliance, and true policy enforcement. Hospitals, shopping centers, public transport, and connected smart buildings will be under attack. Proactive protection is needed and with Ordr, you’re in control.
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
Knowledge BaseA Complete Guide to CIS Critical Security Controls
…into resource and expertise specific sections, an organization is given the option of choosing the best fit for their infrastructure. Why use CIS Controls for Security and Compliance? The CIS…
A Complete Guide to CIS Critical Security Controls
6Min ReadThe major crux faced by IT security professionals across the industry today is that threats evolve at the same speed as technology. Technology is vital to business, especially as more professionals work outside the standard office environment, and that creates additional vulnerabilities. The CIS 20 Critical Security Controls framework is so widely used, that there are several different ways to reference them:
- CIS CSC
- CIS 20
- CCS CSC
- SANS Top 20
- CAG 20
The key to mitigating risk is having a solid security foundation on which to build industry or business specific security protocols. The CIS 20 Critical Security Controls (CSC) are that foundation.
What are the CIS 20 Critical Security Controls?
The CSC are a security foundation of actionable best practices developed by the Center for Internet Security (CIS) and the SANS Institute. Knowledge is garnered from a wide array of security professionals, condensed and clarified by industry experts, and presented in a format that can be adapted by any organization to counter the leading forms of cyber attack and protect data assets.
These basic principles allow IT professionals to respond swiftly and effectively against growing security concerns, which allows organizations to reduce cybersecurity risks.
How do the CIS 20 apply to your organization?
All organizations must navigate the deep and complex waters that are risk and compliance. Industry standards often define the specific dive level an organization has to make into those murky depths, but they rarely indicate how. The CIS Critical Security Controls are a set of best practices that recommend how to combat the most common cybersecurity threats, and are applicable to all organizations.
The CSC are broken into three implementation groups, each set of controls being a progression based upon an organization’s needs:- Basic implementation is applying controls 1 – 6, and is advised for all organizations. These six controls can be implemented with conservative resources, and will provide a basic level of protection that even the smallest of organizations can utilize.
- Foundational implementation is applying the basic controls and controls 7 – 16, and is advised for mid-level organizations that have more resources and cybersecurity professionals to implement security measures.
- Organizational implementation is applying all 20 security controls, and is intended for developed organizations that have rich resources and robust cybersecurity expertise.
By segmenting the controls into resource and expertise specific sections, an organization is given the option of choosing the best fit for their infrastructure.
Why use CIS Controls for Security and Compliance?
The CIS top 20 Critical Security Controls are an evolution of worldwide knowledge from IT professionals that are arm-deep in security each and every day. The results of using the CSC are phenomenal; studies have shown that 85% of cyberattacks can be thwarted by using just the basic implementation of CSC. Using the organizational implementation of all 20 Critical Security Controls has a staggering 97% success rate. By using these outlined best practices, an organization will have a strong security base that has already proven its worth. A base that is perfect for building in any additional industry specific security requirements.
How do the CIS Critical Security Controls work with other standards?
The CSC are cross-compatible because they are effective best-practices that encompass a large threat range. Industry specific standards and security framework ideologies are growing and evolving with technology, and the CSC helps organizations keep up with the ever changing security environment.
For example, the California Consumer Privacy Act (CCPA) and General Data Protection Act (GDPR) require organizations to maintain reasonable security to protect consumers’ private data. In addition, the IoT Cybersecurity Act requires connected devices to meet a minimum level of cybersecurity. Using the CIS Top 20 Critical Security Controls allows an organization to meet these thresholds.
Also, the CSC maps well to other well known security standards:
- National Institute of Standards and Technology (NIST)
- International Organization for Standardization (ISO)
- Payment Card Industry Data Security Standard (PCI-DSS)
- Health Insurance Portability and Accountability Act (HIPAA)
- Control Objectives for Information and Related Technologies (COBIT)
- Federal Information Security Modernization Act of 2014 (FISMA)
- NERC Critical Infrastructure Protection Standards (NERC CIP)
- Federal Financial Institutions Examinations Council (FFIEC)
- Department of Homeland Security Continuous Diagnostics and Mitigation (DHS CDM)
- National Security Agency Manageable Network Plan Guide (NSA Network Infrastructure Security Guide)
- Data Security and Protection Toolkit Standard (NHS DSP Toolkit)
The CSC are beneficial aids for organizations that need to meet these complex industry standards or regulations.
An overview of the CIS Controls
Basic CIS Controls
The basic level of implementation is applying controls 1 – 6, and is considered the minimum amount of security that all organizations should use to be ready against cyber attacks.
Control 1: Inventory and Control of Hardware Assets
Knowing who and what is using the network is key to preventing unauthorized access. This includes maintaining a detailed inventory via both active and passive discovery and using access controls. An in-depth view of all the devices that use an organization’s network provides a first line of defense.
Control 2: Inventory and Control of Software Assets
Software needs to be inventoried and monitored in a way that allows the organization to see what’s been installed, who did the installing, and what the software is doing. Implementing authorization lists, installation rights, and integrity management are a must. Just like hardware assets, software can be used as a vulnerable point of entry into the protected network.
Control 3: Continuous Vulnerability Management
Security risks need to be identified before they result in an actual breach. The network should be scanned for weak points, which can then be quickly remediated. For the testing to be most effective, keep up-to-date on vulnerability advances.
Control 4: Controlled Use of Administrative Privileges
Inventory of service accounts, administrative credentials, and adequate password requirements need to be fundamental. Administrative accounts must be safeguarded to prevent them being used by attackers.
Control 5: Secure Configuration for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers
Update default configurations and automate processes that manage them. Configuration management is necessary to lock-down unnecessary risks that attackers can exploit.
Control 6: Maintenance, Monitoring, and Analysis of Audit Logs
Logging will give an organization the ability to see all the activity of the network and provide pertinent details in the case of a breach. It also allows for the creation of alerts.
Foundational CIS Controls
The foundational level of implementation is also applying controls 7 – 16, and is considered appropriate for mid-level organizations that need to protect systems beyond basic needs.
Control 7: Email and Web Browser Protections
Numerous threats are directly related to email systems and web browsers. If they aren’t safe, the network isn’t either.
Control 8: Malware Defenses
Malware is used for everything from identity theft to corporate espionage. Antivirus software and malware prevention mitigates the risk to users and the organization.
Control 9: Limitation and Control of Network Ports, Protocols, and Services
Firewalls, port scans, and separation of critical services can reduce the available avenues open to attackers. Sharp focus here can prevent unauthorized access.
Control 10: Data Recovery Capabilities
Some forms of cyber attack, like ransomware, directly target data. Backups prevent losing data and give a benchmark for data comparison if data integrity is in question after a security breach.
Control 11: Secure Configuration for Network Devices, such as Firewalls, Routers, and Switches
Encryption and advanced authentication methods are good starting points. Shielding network devices from improper access, shields the network and its data.
Control 12: Boundary Defense
An organization must control flow through the boundary using monitoring and analysis. Tight management of perimeter defenses keeps out unauthorized users and keeps in sensitive data.
Control 13: Data Protection
Data protection is complex and requires a multi-prong focus. Use managerial controls, procedures, and technology to ensure data is accessed only where authorized, is controlled, and maintains integrity.
Control 14: Controlled Access Based on the Need to Know
Classify data, segment based on that classification, and control the access based on what users/systems need to use that level of data. This prevents both internal and external unauthorized access to data.
Control 15: Wireless Access Control
Wireless access is a common area of risk for many organizations, and controls are necessary to mitigate as much risk as possible. Implementing protocols around SSID and broadcasting levels, guest networks, and monitoring the wireless network are ways to combat attacks.
Control 16: Account Monitoring and Control
Attackers using valid credentials is a concern that must be addressed. Two factor authentication and managing the account life cycle are common recommendations.
Organizational CIS Controls
The organizational level of implementation is applying all 20 CIS controls. It is considered appropriate for well-developed organizations that have more complex security needs and have the necessary resources/capabilities required for implementation.
Control 17: Implement a Security Awareness and Training Program
Users are an important piece of the cybersecurity puzzle. Refreshing users about security practices and new attacks to be wary of can be key to preventing breaches.
Control 18: Application Software Security
Keep applications current, use only trusted components, and harden applications where possible to prevent vulnerabilities. In-house applications should be accessed for security and kept within maintenance limits. Do not allow applications to provide a backdoor into the system.
Control 19: Incident Response and Management
Always be prepared by planning for possible incidents and testing where possible. Don’t leave the response measures unplanned until something actually happens.
Control 20: Penetration Tests and Red Team Exercises
Identify points of breach and remediate as they are found. Keep testing and remediations evolving as the attack vectors change.
How to implement CIS Controls
The CIS Top 20 Critical Security Controls are actionable best practices that organizations can use to protect themselves in an ever-changing technology environment. In order to successfully implement the CSC controls, organizations have to move forward against security risks by taking proper action to protect organizational devices, networks, and data.
This includes taking steps to implement proper discovery methods and ensuring the correct classifications of all devices on an organization’s network. In addition, an organization needs to continuously track device behavior and segment vulnerable devices. Risk assessment should be performed, as well, to ensure that security standards are being met.
The Ordr Systems Control Engine (SCE) gives organizations the power to enable visibility and security of their network-connected devices, with a simple and powerful solution to identify, classify, profile the behavior and risk, and automate action for every network-connected device in the enterprise.
One of the differentiated actions with Ordr SCE is that security and IT teams have access to dynamically generated segmentation policies to only allow sanctioned communications for every class of device.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 Blog9 Cybersecurity Predictions For 2022
Blog9 Cybersecurity Predictions For 2022…COVID-19 pandemic brought telehealth and telemedicine into the mainstream, and they are not going away even after the threat of the virus abates. For most healthcare organizations, the popularity of…
Last year, we shared a number of cybersecurity predictions, most of which either played out as described or are trending that way, with results that remain to be seen. In one instance Ordr CEO Greg Murphy predicted that, “Someone in the U.S. will die as the result of a ransomware attack, resulting in increased push for cybersecurity regulations in healthcare and increased cybersecurity budgets.” Tragically, according to a lawsuit filed in September of last year, that prediction came true.
This year, we asked a number of Ordr cybersecurity experts what they saw unfolding for the next eleven months and are sharing nine of the more interesting responses.
-
Ransomware attacks will continue to increase (Pandian Gnanaprakasam)
The impacts of double extortion and crimeware-as-a-service will continue to plague businesses worldwide. The number of victims will triple, increasing from 20% to 50%, while the number of companies that pay a ransom to recover their data will increase from 10% to 30%.
Cybercriminals will drive these increases through more aggressive tactics, including data destruction, sensitive data leaks, DDoS campaigns, targeting and breaching high-profile organizations (including wealthy families), and disrupting business operations to force enterprises to pay. We will also see a concerning increase in the use of killware in attacks that once were used to sow only ransomware.
-
Organizations will adopt a more holistic security strategy to address a shift from traditional endpoints as IoT, IoMT, and OT devices converge in the enterprise network. (Bryan Gillson)
Recent attacks (i.e., Colonial Pipeline) show us that we are not thinking about cyber resilience and as a result, in the case of thousands of industrial and healthcare breaches, we see loss of services (patients diverted, pipelines shut down). This happened even though the IoT/OT infrastructure was not attacked nor compromised.
This will prompt organizations to recognize that what is needed is to embrace a whole-of-enterprise approach to security that encompasses cloud-to-ground visibility, and analysis and control of all connected assets (from traditional IT to vulnerable IoT, IoMT or OT) in order to enable true cyber resilience.
-
Third party/Supply chain attacks will continue to increase (Brad LaPorte)
2022 will be the Year of the Supply Chain Attack. Already up 430% since 2019, the growth of these types of attacks will increase exponentially and become the #1 global attack vector. As more enterprises adopt more mature cybersecurity practices, criminals will go upstream to weaker targets that can maximize their blast radius and give them an impactful one-to-many attack ratio. Historically, attacks have been spray-and-pray; now, they will become more surgical as supply chain attacks become weapons of mass disruption.
-
Attackers will begin using AI to infect multiple organizations at a massive scale (Srinivas Loke)
It has taken a few decades, but adoption of automation solutions such as AI, ML, and DL has gone mainstream and worldwide. This is great news for cyber defenders, as Gartner finds “33% of technology providers plan to invest $1 Million or more in AI within two years.” The cybersecurity industry is leading the way on this trend, but easy access to open-source AI tools is both a blessing and curse. Cybercriminals have access to the same resources, and the resulting threat is multiplied by strong ideological and financial incentives to use them. This will accelerate the ability of threat actors to conduct targeted, automated attacks at a massive scale. The war of the machines is on the horizon.
-
Attackers are going straight to recruiting insiders for advanced attacks (Danelle Au)
Organizations have focused (rightly so) on shoring up their identity and access management capabilities, and deploying multi-factor authentication within their networks. These solutions have made it harder for attackers to bypass defenses—and so attackers are going directly to insiders. With the promise of a cut of the haul in exchange for access, ransomware gangs are bypassing traditional methods and are instead working to recruit insiders to use their privileged access to install malware directly. The tactics being used by these attackers are similar to HUMINT espionage and recruitment programs. Unfortunately, this means that every security leader now needs to consider insider-originated malware as part of their ransomware protection strategy.
-
Laws or sanctions won’t make a big dent in stopping ransomware and cyberattacks (Greg Murphy)
Over the last several years, the urgency in dealing with ransomware and other advanced attacks at the legislative level has grown, as illustrated with bills like Warren-Ross, a 30-country meeting led by the Biden administration to address the threat of ransomware, and efforts by the FBI to crack down on ransomware gangs. However, political and legislative efforts won’t make a difference as long as cybercrime makes sense economically, and as long as Russia has no incentive to bring threat actors to justice. One possible—though controversial—way to reduce these advanced attacks is to eliminate the anonymity associated with cryptocurrency payments. Without an easy way to pay ransom, these attacks will decrease. Additionally, more scrutiny is needed on cyber insurance, as this practice facilitates easy payments for threat actors, and has the adverse effect of fueling more cyberattacks.
-
Security teams should expect significant Zero Day vulnerabilities (Pandian Gnanaprakasam)
Software development has roared forward for decades without enough thought given to security implications, and we’re suffering the consequences. That was evident to security teams in 2021 with the emergence of vulnerabilities like PrintNightmare in Q2/3, and Log4j in Q4. Similar revelations will continue throughout 2022 and beyond with the evolution and use of malicious, automated scanners leveraging tools like Cobalt Strike to find and exploit new vulnerabilities. In response, software developers should emphasize security best practices, especially when working with open-source software. Manufacturers should also disclose their software bill of materials (SBOM)–nested inventory for software, a list of ingredients that make up software components–to better inform customers and users of the possible security implications of using their products.
-
Telehealth and telemedicine are here to stay. And healthcare organizations need to keep those systems secure. (Darrell Kesti)
The COVID-19 pandemic brought telehealth and telemedicine into the mainstream, and they are not going away even after the threat of the virus abates. For most healthcare organizations, the popularity of telehealth visits versus physical visits will be dependent on insurance providers, and whether they will pay the same amount for virtual versus physical visits. In the UK, telehealth visits are gaining in popularity because of the reduced number of physicians and the long wait time when it comes to scheduling visits. From a cybersecurity perspective, a lot of telehealth/telemedicine environments connect directly from the patient to the specific telehealth vendor, and therefore there is a lack of security visibility into these visits. That needs to change for the sake of patient and organizational safety.
In the U.S., Mayo Clinic began offering hospital-at-home care for patients with non-life-threatening conditionsduring the pandemic, and saw success from the strategy; not just for patients but also for freeing up space in the hospital. With Omicron and future variants being inevitable, expect that these will also be included in telehealth and telemedicine at-home care, with corresponding medical devices that also need to be secured.
-
Cloud infrastructure will be one of the leading attack vectors in 2022. (Brad LaPorte)
Everything is moving to the cloud—including cybercriminals. According to Gartner, by 2023, 70% of all enterprise workloads will be deployed in cloud infrastructure and platform services, up from 40% in 2020. Through 2025, more than 99% of cloud breaches will have a root cause of preventable misconfigurations or mistakes by end users. In addition, 96% of third-party container applications deployed in cloud infrastructure contain known vulnerabilities. And 63% of third-party code templates used in building cloud infrastructure contained insecure configurations. Threat actors know this, and they are working hard to take advantage. To say that cloud security needs to be a top priority is the understatement of the year.
Those are our thoughts on what’s in store for the cybersecurity landscape in 2022. We’d love to hear yours.
Danelle Au
Danelle Au has more than 20 years of experience bringing new technologies to market. Prior to Ordr, she was CMO at Blue Hexagon, a deep learning for malware protection company, and CMO at SafeBreach where she helped build the marketing organization and and define the Breach and Attack Simulation category. Previously, she led strategy and marketing at Adallom, a cloud security company acquired by Microsoft. She was also Director, Security Solutions at Palo Alto Networks, driving growth in critical IT initiatives like virtualization, network segmentation and mobility. Danelle was co-founder of a high-speed networking chipset startup, co-author of an IP Communications Book and holds 2 U.S. Patents. She has an MSEE from UC Berkeley
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
-
 BlogStories from the Field – The Convergence of IT and OT
BlogStories from the Field – The Convergence of IT and OT…a Bachelor of Science in Electrical and Computer Engineering from the University of Minnesota, Duluth. Interested in Learning More? Subscribe today to stay informed and get regular updates from Ordr…
Security Strategy
Stories from the Field – The Convergence of IT and OT
5Min Read
By Darrell Kesti

The convergence of IT and OT makes it important to have visibility and security for all connected assets because business operations are at risk. Stories from the field on Iot and OT security challenges that enterprises face. Ordr has one of the most robust channel partner programs in the market, and I often meet with our partners to understand not only what opportunities they’re working on, but also address any questions they have about our products.
In a conversation with Steven Dastoor of CITON recently, we spoke about the convergence of IT and OT environments, and how it was important to have visibility and security for IT (IoT) and OT devices. The Colonial Pipeline attack demonstrated that the security of IT systems is just as important as OT, because when your billing system goes down, your business operations are impacted even if the ransomware did not hit the OT systems.
We discussed best practices and specifically the recommendations outlined in the September 2020 Microsoft Digital Defense Report on securing IoT/OT Networks.
The convergence of IT and OT makes it important to have visibility and security for all connected assets because business operations are at risk. This was illustrated in dramatic fashion when Colonial Pipeline’s IT system in admin was hit, and OT systems were affected. These were great recommendations by Microsoft. Here’s how Ordr maps to them:
Reducing exposure of IoT/OT devices
Beyond discovering and classifying all connected devices– from traditional servers, workstations and PCs to IoT, IoMT and OT devices. Ordr profiles device behavior and risks, and then automates appropriate action. In addition, there are visual representations of your network and associated risk. You can view this at the device group level easily to see all devices with communications to the internet in our Ordr Traffic Analysis connectivity map, or at the individual device level in our Ordr Flow Genome. We also integrate threat intelligence from multiple sources, enriching the Ordr Data Lake with data on emerging threats, domains associated with phishing sites, Command and Control (C2) infrastructure etc. We can also map “good behavior,” and flag and alert on any anomalies or new traffic patterns we have never seen before. This good behavior can be shared with other tools like the firewalls, switch infrastructure too, to create zero trust policies that only allow a device access and communication flows it needs. Anything else is automatically blocked based on the dynamically generated policies.
Mitigating risks
Ordr has a number of capabilities to first identify devices that are high-risks. These include devices with weak passwords and certificates, running outdated operating systems, or with vulnerabilities. Ordr also includes an integrated Threat Detection Engine that detects exploits and active threats, in addition to machine-learning models that alerts on anomalous traffic. Ordr helps validate security-based workflows like red teaming.
In addition, once vulnerable or compromised devices are identified, we can deliver rapid response to remediate and mitigate risks. We dynamically generate policies to save security teams time on manually writing policies individually for VLANs, SGTs, internal Firewall rules. In addition, organizations globally, use Ordr to triage events during the incident response (IR) process, often through enriching their Security Information Event Management (SIEM) solution.
Implement Zero Trust IoT/OT strategies
In order to create the appropriate Zero Trust policies, it is important to not only identify devices but also what they are doing in the network, and be able to create policies that align to business needs. This is one of Ordr’s biggest differentiators– creation of Zero Trust policies and the ability to be able to enforce them across existing networking and security infrastructure such as Aruba ClearPass, Cisco ISE, FortiManager/FortiGate, FortiNAC, CheckPoint, etc…
Centralize asset/configuration/patch management (IT, IoT, and OT)
Ordr delivers real-time asset inventory of every device. As we discover devices on the network, we can push and pull information from tools like ServiceNow or other CMDB/IT Asset Management tools to ensure the devices we see are cataloged by the business. We can keep asset management systems continuously up-to-date about systems that are not being tracked. We see this a lot where Ordr detects devices on the network that do not exist in the Asset Management tool, and also devices that are still in the Asset Management system as Active, but not deployed or online in the environment.
Ordr also works with vulnerability management tools like Tenable and Rapid7 to deliver vulnerability insights into devices that may not previously have been scanned for CVEs.
Convergence of IT and OT
We are a bridge between these teams, as we give them a data set they can both work with, from their unique perspective. I am working with a manufacturer right now where we are delivering visibility and security of their OT and IT networks. Because there aren’t “air-gapped” networks anymore, the IT security team was concerned about exactly what was connected. We found a number of OT Workstations running Windows XP, not part of IT as they are Siemens control systems, But the IT team was using Remote Access (RDP) to connect to them remotely for work. This is similar to how threat actors infiltrated the water treatment plant in Florida. Ordr was able to map out what specific devices are allowed to be part of remote work and remote access, limiting the attack surface. It is a great story of IT and OT coming together to ensure the security and availability of these systems.
Continuously monitor for unusual or unauthorized behavior
The Ordr platform includes a machine learning engine that baselines and maps every single device communications. This baseline allows us to understand what is “normal behavior” and alert on unusual behavior.
Ordr also monitors all devices that use supervisory protocols like SSH, telnet, ftp, etc., associates them with user names, correlates them with the network they logged in from (corporate or guest), and maintains an accurate access record for each and every device as well as each and every user.
Plan for Incident response
We are a critical product for Security Operations Centers (SOCs) and Cyber Security Incident Response Teams (CSIRTs) and should be a tool used in diagnostics. When an incident occurs, Ordr provides the context for the device and details about what it is communicating with. We can also provide insights on communications to C2 sites retrospectively. Finally, we empower SOCs and incident response teams by creating security policies to quickly lock down or isolate a device, block threats through NGFW policies, ACL blocks, quarantine VLAN assignment, port shutdown, or session termination–either directly to firewalls, existing switches, wireless controllers, or via NAC platform.
For example, when the SolarWinds vulnerability hit, we had a customer reach out and ask: “Can you give me an inventory of all of my SolarWinds devices, and where they are in the network”? We did it in two clicks. We also monitored the customer’s environment to see if there were any communications to SolarWinds domains.
Remember third parties
We can monitor third party connections. We see this all the time in healthcare where a third party, like Siemens, is connecting to do remote support on a device, like an MRI. We see the communications coming in from the Netherlands, generally over traditional management protocols like Telnet, SSH, HTTPS, and RDP. We can track the source/destination of this traffic, as well as have the time stamps for when it is occurring. We can then create Zero Trust policies to lock down these management ports, but still allow the third party access that is needed.
Ready to achieve total visibility into what’s on your network? Request a free Ordr sensor today and you’ll be able to see what connected devices are on your network in minutes!
Darrell Kesti
Darrell is VP Sales at Ordr. He joined Ordr as one of the original Account Executives in October of 2018 to help launch the field organization. In his prior role as Ordr’s Director of Healthcare Sales, Darrell drove significant growth in healthcare sales and helped position Ordr as the leader in connected device security. Darrell has had over 20+ years of Sales Leadership, Account Management, and Field Engineering experience supporting customers and partners while with leading security and networking organizations – ForeScout Technologies, FireEye, Mandiant, F5 Networks, and Secure Computing Corporation. Darrell earned a Bachelor of Science in Electrical and Computer Engineering from the University of Minnesota, Duluth.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?