Search Results:
”Role of Huawei H19-431_V1.0 Exam Questions in Getting the Highest-Paid Job 💆 Search for { H19-431_V1.0 } and download exam materials for free through [ www.pdfvce.com ] 🏸Premium H19-431_V1.0 Files”
-
 BlogSolving IoT Security Challenges with Behavioral Analytics
BlogSolving IoT Security Challenges with Behavioral Analytics…virtually impossible to ensure agent compatibility with the myriad combinations of connected device hardware, software, and firmware. Agents impact performance in the best case and completely disable devices in the…
Security Strategy
Solving IoT Security Challenges with Behavioral Analytics
7Min Read
By Pandian Gnanaprakasam

Behavioral analytics are vital to understanding the IT estate, and detecting/preventing threats. Ordr’s own Gnanaprakasam Pandian describes why complete asset discovery, accurate operational data ingestion, and real-time behavioral analytics are key to threat detection and prevention. Organizations spend more than ever on security, yet the rate and impact of attacks continue to grow. Is a positive or negative security model the right approach to address today’s concerns, specifically to protect IoT devices?
SPOILER ALERT: you need a hybrid model based on behavioral analytics.
Traditional approaches to cybersecurity simply can’t keep pace with attackers becoming increasingly specialized, organized, and sophisticated. Security leaders and practitioners know that a new approach to security is needed, but navigating the myriad buzzwords and claims about artificial intelligence (AI), machine learning (ML), and behavioral analytics can be challenging. With that in mind, I want to explain how and why a new approach using behavioral analytics (including AI/ML analytics algorithms) solves real-world security problems today.
The Negative Security Model
A negative security model will “allow everything” by default while attempting to identify the “bad.” This approach is a mainstay of security tools such as antivirus software or IDS/IPS and has dominated cybersecurity for most of its brief history.
Just as credit card companies use rules and known attributes to identify fraud, negative security controls use rules and signatures to identify known threats previously seen in the wild. When the threat is seen again, security tools can detect and block the malicious traffic, malware, exploit, URL, etc.
Negative security controls are good at identifying known threats. However, tools using these controls can only identify and block what they are told to block. A signature must exist, or a tool must be configured to block malicious activity. Ongoing care and feeding are required to keep tools up to date with the latest signatures and configurations to detect and stop threats.
A negative security model alone is essentially defenseless against widespread zero-days such as the recent Log4j vulnerability, which impacted thousands of enterprise products and created massive exposure for virtually every modern organization.
Depending entirely on negative controls for threats has some serious limitations, and organizations need both negative and positive controls to protect their assets and environments.
The Positive Security Model
A positive security model is the opposite of a negative security model and works by defining allowed actions. Instead of defining a blocklist of “bad” actions, the positive security model defines what is “good” or allowed. Think of positive security as the doorman at an invitation-only party as a simple analogy. Instead of identifying and blocking “bad” attendees, the positive security doorman uses the guest list to define who should be let in.
A network firewall is a classic example of a positive security tool. Only specific, required network ports are open, while all other ports and traffic are denied by default.
A tool using the positive security model can address the shortcomings of a tool using the negative security model by providing a far more proactive approach to security. Instead of constantly chasing the “bad,” a positive model focuses on what applications, users, and devices need to do their job. Everything else is flagged or blocked. It doesn’t matter if an attacker targets a zero-day vulnerability – anything that doesn’t match the “good” list or vastly differs from normal activity will be denied.
As a simple example, attackers often gain initial access to an environment by using phishing emails to get a user to click a link or open an attachment. The attacker can easily evade negative security controls by altering a URL or malware payload. As controls become more sophisticated, so do attackers by changing their tools and methodologies.
Once on a user’s device, the attacker will target other assets in the environment in an attempt to move laterally, often using protocols such as SMBv1 or RDP. Since this movement is outside the norms of valid activity, positive security controls can recognize and deny the abnormal behavior without prior knowledge of the methods used or the specific threat.
Blending Security Models With Behavioral Analytics
To meet today’s security challenges, a blend of negative and positive controls is essential. More importantly, behavioral analytics must be applied to enable a positive security model, control an organization’s complex communication patterns and address security challenges in ways never possible before.
Positive security is more complicated than simply allowing communications or opening ports on a firewall. Instead of focusing on individual traits or indicators, positive security requires understanding the more complicated world of behavior.
Consider the different scenarios of medical devices in a research facility, outpatient care, and a critical care environment. Some of the devices may be similar in make and model; however, their use and criticality in each environment will dictate different requirements, priorities, and risk tolerance.
A system needs awareness of a device’s purpose, the services or assets it needs to access, and how similar devices in the environment behave to provide the right level of protection.
In recent years, anomaly detection and behavioral analytics have been hot topics in security but have delivered mixed results. The ultimate goal for successful solutions today is to leverage behavioral analytics for truly reliable and valuable insights. For that, we need to cover three essentials.
1. Get all the right data from the best sources
Instead of simply identifying specific behavior as abnormal, the goal of positive security is to enforce controls that keep devices and data safe while ensuring each device can function in the environment as needed. Positive security requires a deep understanding of what each device is, its role, purpose, and communication patterns. To get this level of deep understanding requires large amounts of ground truth data. Arguably, the network provides the most accurate and reliable source of data needed to understand this level of detail.
An agent-based approach will result in blind spots across the exploding population of unmanaged devices that include IoT, IoMT, OT, and other connected devices. Agents are notoriously painful to manage, and for many unmanaged devices, agents are either not available or difficult to develop. It’s virtually impossible to ensure agent compatibility with the myriad combinations of connected device hardware, software, and firmware. Agents impact performance in the best case and completely disable devices in the worst case.
Understanding device behavior requires a “show me, don’t tell me” approach, and looking at device communication flows over the network provides the best source of truth.
To quote Batman, “It’s not who you are underneath, it’s what you do that defines you.”
Normal behavior informs the positive security model for a specific device profile, and normal behavior can be determined by baselining communications flows and understanding the systems it communicates with. With this understanding, policies can align with a zero trust framework limiting device communications to the required systems and nothing else.
Ordr collects and analyzes network data to create a baseline of normal behavior, and map communication flows for every device. The baseline for each device is automatically tuned, updated, and compared to the device’s historical behavior and similar devices in the environment. Device flow information is enriched with device context, threat insights (threat intelligence, third-party vulnerability databases, and reputation data), network data (from switches, routers, and wireless controllers), and additional data (IPAM, DNS, CMDB, Active Directory) as we continuously analyze the activity of every device. All of this data is collated into the Ordr Data Lake and continuously analyzed to identify any changes in behavior.
2. Organize the data for effective analysis
We need to know every device’s “what, where, and why.” An algorithm won’t magically generate needed answers from massive amounts of data. Getting valuable insights requires organizing data hierarchically with relationships properly established.
Is the device a patient monitor, a security camera, or a printer?
Where is the device located, and why does it behave the way it does?
What data and systems does the device serve, and what does it require?
Ordr organizes data to see the interrelationships between devices, the network, and how data flows in all directions to answer these questions. Ultimately, all this context is organized in terms of the device itself. While analyzing hundreds of thousands of records may still be required, analyzing organized data is far more manageable and focused than iterating over massive amounts of data.
Analyzing organized data enables focus on specific types of devices and behaviors to uncover valuable security insights. Analyzing organized data can be used to learn how patient monitors behave as a generic device and a specific model of monitor. We can understand how other similar devices in the network behave to identify unique traits and specific needs in each organization.
Analyzing organized data can help answer important questions that drastically change a security team’s ability to respond to an event. For example, when a hospital sees a malicious outbound DNS request, there may be no need for action if the request is from a visitor’s laptop on the guest network. On the other hand, it would cause serious concern if the malicious request came from a hospital-owned infusion pump. Ordr provides these insights by properly organizing and analyzing data.
3. Understanding and explaining behavior
Once we know where to look, we need to understand what we see in terms of behavior on the network. Having partial information for security is not helpful, and this is where most cybersecurity behavioral analysis attempts fall short. If a security tool can’t explain in detail what was detected, an analyst has to do the work to understand what happened. A tool that generates anomalies it can’t explain will quickly drown security analysts in work or, more likely, cause them to miss critical events. It’s not enough to say a learning algorithm triggered an alert. More context is required to instill confidence and to ensure priority for action.
Ordr analyzes network data to create a baseline of behavior for each device in an environment. That baseline is then combined and analyzed with the baseline of other devices. With this approach, Ordr identifies activity outside of normal behavior for the device, its cohorts in the environment, or similar devices deployed globally.
Additional details such as the specific device, physical location, internal and external connections, and communication information are critical to ensure that incident response teams have enough detail. Proving this detail in an easy-to-understand, graphical way with the flexibility to customize the view is critical for any AI-based tool to be useful.
Analysis to uncover attribution and explainability is complicated. Making this easy for security teams is one of the essential traits of Ordr. The image below shows the enormous scale of analysis needed for a single Ordr customer deployment.
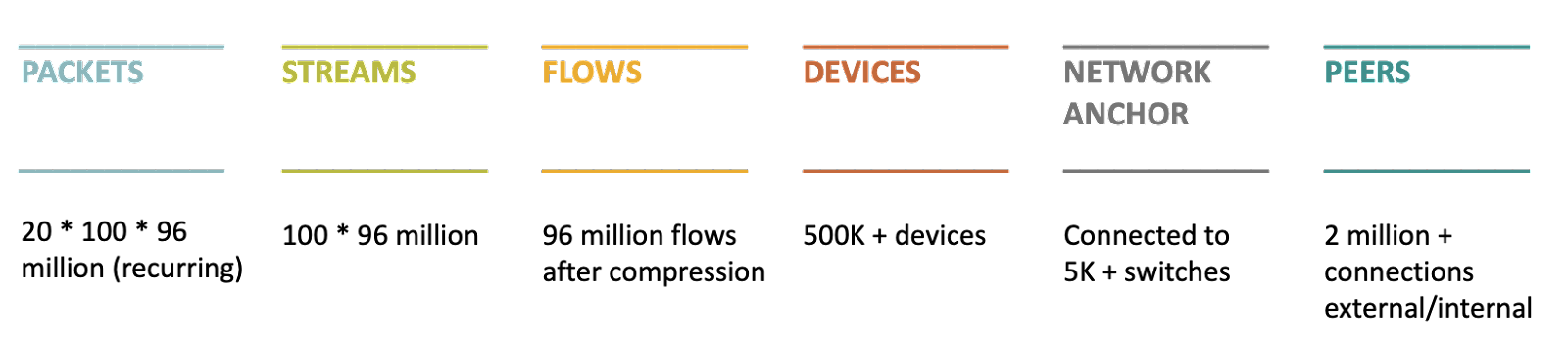
Ordr ultimately rolls behavior up to the device level. The center of the diagram above highlights the Ordr database of behavioral patterns for over 500,000 devices.
Understanding the behavior of these devices requires the analysis of 96 million network flows. However, to truly perform attribution and achieve understanding, we need to analyze the 100 streams that make up each flow and the packets that make up each stream. This essential task is where the analysis gets complex, and most behavioral analysis systems fall short.
To achieve positive controls, we must understand and use automation to control behavior. There are too many devices and network segments for security teams to understand the complexities of each one. Instead, security tools must understand and control behaviors in the same set-it-and-forget-it way that traditional firewalls control network ports.
Providing this level of simplicity to security teams requires a new type of analysis and a new type of security solution. One that we at Ordr continue to build and optimize.
Ordr’s Unique Approach to IoT Security
While most behavioral analytics solutions have failed to live up to the hype, Ordr provides actionable and practical answers to secure your connected devices without creating new headaches for users or security teams.
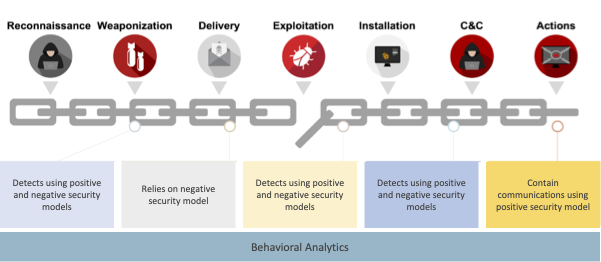
To illustrate, consider blending the positive and negative security models along with behavioral analytics to detect the multiple stages of a ransomware attack kill chain. In most instances, Indicators of Compromise (IoCs) are not available immediately after detecting an attack in the wild. In these cases, a positive security model compliments a negative security model by providing greater insight into a potential problem in the network and the attack timeline. Once IoCs are defined, they can be validated using the negative security model.
The screenshot below shows the detection of stages of the kill chain using different security models.
If you have thoughts or questions about this blog, or simply want to learn more about Ordr, reach out to the team for a deep dive discussion.
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
Knowledge BaseThe Healthcare Industry Is at Risk
…data from IBM. And that’s just the average cost. In some cases, the cost of individual cyber incidents involving healthcare organizations in recent years have exceeded 100 million dollars. Fortunately, as…
The Healthcare Industry Is at Risk
8Min ReadProtecting healthcare data from cyber attacks would be easy if organizations only had to worry about a few types of attacks, or if attempted breaches were rare.
Unfortunately, that’s not the case. Cyber attacks that target healthcare data and systems occur at a dizzying rate and come in many forms. The sheer volume of sensitive and diverse data–including Protected Health Information (PHI)–that healthcare organizations manage make it even more challenging to defend healthcare data and systems against cyber attack risks.
Establishing a plan to mitigate the risk of healthcare cyber attacks, and responding effectively when they occur, is critical for any organization that operates in the healthcare sector. This article offers guidance on how to manage cyber attack risks in healthcare by detailing common types of cyber risks and attacks, then explaining best practices for protecting systems and data.
Why the healthcare sector is at risk for cyber attacks
Cyber attacks occur in every industry and sector. However, healthcare organizations are at special risk, largely due to the fact that the information they produce and manage is a particularly alluring target for attackers.
Patient information often includes data, like treatment history information, that is unchangeable and can’t be erased or updated following a breach, meaning it holds special value. In fact, a single breach of a hospital or doctor office’s network could expose hundreds of thousands of individual records. This makes healthcare cyber attacks an especially lucrative activity for hackers. This helps explain why attacks that target the healthcare industry reached an all-time high in 2021 and have continued to climb since.
Another reason why the healthcare sector is targeted is because of the high propensity to pay a ransom. There is a zero sum choice between paying a ransom to a cyberattacker or risking patient lives by not being able to deliver healthcare services. In 2021, 61% of respondents to a Sophos healthcare study reported that they paid ransoms; this is a higher rate than any other sector. Additionally, with the continued focus on the pandemic and patient care, users can also be distracted, leaving systems unprotected or unknowingly clicking on a phishing email. This can make healthcare organizations more vulnerable and easier to target.
On top of this, PHI and other information stored by healthcare organizations is subject to special data privacy regulations, defined by the Health Insurance Portability and Accountability Act (HIPAA) and other regulatory laws. As a result, the impact of a breach in this industry can be especially grave. Other types of businesses may suffer financial harm or disruptions to their operations due to attacks, but they typically don’t face the steep consequences that apply in the case of healthcare cyber attacks.
The cost of cyber attacks
Due to regulatory consequences as well as a variety of other factors, the cost of a breach that impacts a healthcare business can be especially steep.
Fines assessed by the federal government for HIPAA violations amount to millions of dollars per year. Disruptions to hospital services can bring revenue to a halt, leading to losses of hundreds of thousands of dollars per day. Healthcare organizations that fail to deliver promised patient services, or can’t uphold standard safety and security procedures due to cyber attacks may also face lawsuits, further increasing the cost of a breach. And the harm caused by an attack to a hospital’s reputation may cause patients to seek care elsewhere, leading to a loss of future revenue.
When you add up these various costs, it’s easy to understand why the total financial fallout of cyber attacks is 9.44 million dollars, according to the latest data from IBM. And that’s just the average cost. In some cases, the cost of individual cyber incidents involving healthcare organizations in recent years have exceeded 100 million dollars.
Fortunately, as healthcare providers know better than anyone else, an ounce of prevention equals a pound of cure. By investing in cyber attack prevention, it’s possible to avoid the steep financial fallout of cyber attacks that target the healthcare industry.
To read a complete maturity guide on implementing connected device security for healthcare, please download the report here.
Preventing cyber risks
Attack prevention starts with understanding the types of systems that are at risk, as well as the specific types of attacks that may affect them.
In the context of healthcare, connected devices tend to be an especially easy target. Connected devices include Internet of Medical Things (IoMT) such as infusion pumps and patient monitors for patient care, or Internet of Things (IoT) such as HVAC systems and elevator control systems for hospital operations. Healthcare organizations typically manage tens of thousands or hundreds of thousands of devices like these that can increase the attack surface. These devices cannot be protected by conventional endpoint security tools like antivirus or endpoint security software. This means that they often represent low-hanging fruit for attackers looking to breach a hospital’s network.
Even if the devices themselves don’t contain sensitive data, they may connect to other devices or systems that do. That means attackers can use them as a “beachhead” where they gain initial access to internal resources, then execute other exploits.
Exacerbating the cyber risks that connected devices bring is the fact that many medical devices have long operational life cycles, and therefore run on outdated software which means that security updates are no longer available. Due to FDA regulations, it may also not be possible to apply updates to some medical devices; some medical device manufacturers also do not always offer software updates to address vulnerabilities. When devices run on outdated software, threat actors can easily exploit any vulnerabilities that are present.
Securing these connected devices, then, is crucial for healthcare organizations. The first step is to discover and classify what devices are actually connected to the network. This includes visibility into what the device is, what other devices or systems it is communicating with, and where it is connected. This granular visibility is critical to identify devices with risks and vulnerabilities. By baselining what is normal behavior for devices, organizations can quickly pinpoint anomalies that may be an early indication of an attack in progress. Finally, segmentation can mitigate risks for devices that are mission-critical, or those that are running outdated operating systems that cannot be patched.
Types of cyber threats
There are many types of specific cyber threats for healthcare organizations to manage. Each attack involves different techniques and different types of risks; therefore,each type requires different defense methodologies.
Ransomware
Ransomware is a type of threat that occurs when attackers plant malware, or malicious software, inside a company’s network. The malware encrypts important data, and attackers demand ransom in exchange for decrypting it.
Unless victims have access to a backup of their data, they are forced to choose between paying the ransom or suffering permanent data loss. Either way, the affected organization is likely to suffer a delay in operations: either while waiting for data to be decrypted or developing workarounds to restore operations in the absence of the lost data.
If ransomware attackers gain access to sensitive data like PHI, the incident could be considered a breach of healthcare regulations. Laws like HIPAA require public disclosure of these types of breaches. They may also lead to fines, especially if regulators determine that the breach occurred because the business failed to adhere to cybersecurity best practices.
Antivirus tools that can detect and block malware help to prevent ransomware attacks. Other best practices include monitoring the use of privileged protocols such as RDP and Telnet, and segmenting the network to prevent lateral movement. Creating regular data backups ensures that organizations can recover ransomed data quickly without paying the attackers.
When a ransomware attack occurs, the connected device security best practices described earlier, such as gaining complete asset inventory is critical to progress from “detect” to “response”. For example, the ability to identify the device being compromised, where it is connected (physical and network location), and whether security policies or compensating controls can be applied is crucial for security and operations teams responding to the ransomware attack.
Data breaches
A data breach is any type of incident in which sensitive information is exposed to unauthorized parties. Like ransomware attacks, data breaches can lead to regulatory fines. They can also disrupt organization operations, cause a loss of revenue, and ultimately harm the company’s reputation. This is an especially serious risk in the healthcare industry, where establishing patient trust is a paramount priority for organizations.
To prevent data breaches, organizations must securely store data. In addition to encrypting sensitive information, organizations should enforce strict access controls that grant data access rights only to the specific parties or individuals who need it. For example, one doctor should not be able to view information for patients receiving care from a different doctor.
Phishing, social engineering and Business Email Compromise
Phishing is the use of social engineering techniques to trick an organization’s employees into handing over sensitive information.
There are multiple types of phishing attacks. The most common type utilizes email to target employees with messages requesting passwords or access keys. In other cases, attackers might target executives or managers in what are known as spear phishing attacks. Social media, SMS messages, and even videoconferencing can also be used to carry out phishing.
If attackers successfully gain access to sensitive credentials via phishing attacks, they can execute more sophisticated attacks like a Business Email Compromise (BEC). In a BEC, hackers use a company’s email system to launch further attacks against the organization, its patients, or its partners. This is done through impersonating insiders at the company using their official email accounts. For example, attackers could use a doctor’s email account to ask the doctor’s patients to send them financial information. Since patients are likely to place special trust in their doctor, an attack like this has a higher chance of success than an ordinary phishing or social engineering attack.
Protecting against phishing threats starts with educating employees to identify and report phishing attacks to security teams, rather than responding to malicious messages. Software that automatically scans email and other systems for evidence of phishing can also help to mitigate this type of threat.
Insider threats
An insider threat is any type of risk to data or systems that is caused by insiders, like employees of the organization.
Some insider threats involve malicious actors, such as disgruntled employees who exfiltrate sensitive data to harm the organization. But insider threats can also result from complacency: employees don’t actively follow security best practices. Sometimes, insider threats happen when well-intentioned employees make mistakes, such as forgetting to encrypt a sensitive file.
Insider threat mitigation requires the implementation of security controls that limit access rights to the minimum privileges necessary to do their job. Training employees to be vigilant against malicious or complacent insider threats is also a best practice.
DDoS attacks
In a Distributed Denial-of-Service (DDoS) attack, attackers flood a network, service, or server with illegitimate traffic or requests in order to make the system unusable for legitimate users. Although DDoS attacks don’t typically lead to data exposure or loss, they do disrupt operations, which causes lost revenue and harms the organization’s reputation.
Since a DDoS attack could be launched from any device, securing connected network assets is critical for preventing DDoS attacks. Deploying special services that can detect and block DDoS attacks quickly can help mitigate this risk.
Mitigate Your Cyber Risks
Cyber attacks that target the healthcare industry come in many forms, and they can have particularly grave consequences given the volume and sensitivity of healthcare data. The fact that healthcare organizations constitute particularly lucrative targets for hackers only exacerbates the cybersecurity challenges that this industry faces.
To protect against these threats, it’s critical for healthcare organizations to invest in processes and tools that can protect all of their assets–including not just traditional IT resources like servers, but also connect devices–from all categories of cyber threat.
Ordr’s platform for discovering and securing devices is designed to do just that. By automatically identifying all devices connected to your network and informing you of potential security risks, Ordr helps you stay a step ahead of attackers and provides comprehensive visibility into threats no matter where they lurk on your network. Ordr can also automate responses, such as dynamically generating policies to block ports, terminate sessions or segment devices to mitigate risks. In an industry where small-scale breaches can quickly turn into multi-million dollar attacks, the value of protecting your network with Ordr can’t be understated.
To read a complete maturity guide on implementing connected device security for healthcare, please download the report here.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogOrdr’s Innovation Journey: From Seed to Shining C
BlogOrdr’s Innovation Journey: From Seed to Shining C…of the Unexpected When the pandemic struck in early 2020, the strength, resilience, and flexibility of our company were put to the test. The growth of nearly every organization was…
Company News
Ordr’s Innovation Journey: From Seed to Shining C
7Min Read
By Pandian Gnanaprakasam

Ordr closed $40 million in C-round venture funding. Here’s how we got there, and how we intend to invest the new capital. That includes R&D, continuous improvement of the Ordr platform, expanding our talented team, and attacking new markets in need of a better way to protect their enterprises. Today Ordr announced our Series C funding; another injection of capital that allows us to continue investing in our company and build it to last. On this occasion, I can’t help but look back and reflect on a journey that began in 2015 when Sheausong Yang and I–the founding team–had a vision to build a security platform that would give organizations the ability to see and secure every connected device in their network.
Our idea was new then, and it wasn’t easy getting people to understand the problem at first. Even as organizations were increasingly adding unmanaged connected devices to enterprise IT environments, there was confusion over what was classified as internet of things (IoT) or operational technology (OT). Many organizations we encountered thought we were talking about consumer technologies, like then-new smart speakers, and not the millions of medical devices, industrial controls, building management systems, and other equipment like surveillance cameras, phones, printers and vending machines that were often connecting simultaneously to enterprise networks and the public internet.
The Entrepreneur’s Dream
Because an entrepreneur’s journey is hard, often with ups and downs, it’s important to find partners who believe in the vision, the team, and are willing to give the support needed to work things out and solve big problems. We were fortunate to find such a believer in Peter Wagner, founding partner at Wing Venture Capital. Peter believed in the Ordr founding team and our ability to design the right solution to the problem. We also trusted Peter as a partner in our journey. Dominic Orr, former president of Aruba Networks; Pankaj Patel, former executive vice president and chief development officer at Cisco Systems; Dan Warmenhoven, former CEO of NetApp; and Prakash Bhalerao, veteran chief executive and angel investor also became believers in our vision and invested in our seed round as well.
What was not well-known when we started, but something that Peter, Dominic, Pankaj, Dan, and Prakash grasped, was how difficult it was to discover and secure IoT devices in enterprise environments. In fact, it was nearly impossible. These devices were often connected and unmanaged, operating outside the view of IT management and security tools, and given the proliferation rate at which they were connecting, the problem was getting worse. A specialized security solution was needed, and so we set out to build one. At the same time, the industry needed education about the unique threats to connected devices, and we were competing for attention in the cybersecurity space with hundreds of companies, each claiming to have something new and better, even if only a few really did.
A Foundation of Data
Every strong structure starts with a solid foundation. Our approach to connected device security would be built on data and analytics. Specifically, building a massive data lake populated with the details of as many device types as possible, and using behavioral analytics to build security models for each. Achieving our vision required studying breaches to understand their characteristics and communication patterns, and continuously comparing what we learned with the typical behavior of every single device in the network. Employing behavioral analytics was the only way to monitor complex communication patterns and adapt to the ever-changing strategies of threat actors.
Artificial intelligence (AI) and machine learning (ML) require massive amounts of data to solve hard problems. Rather than rely on second-order metadata, the Ordr Data Lake would be populated with accurate, correlated device details collected directly from the source. This was no easy task. You need to have grit, and shortcuts taken at this stage will haunt you throughout the lifetime of the product. We knew once we had the data we could harness it to solve hard problems, take on the challenges ahead, and build a platform for connected device security.
Fast forward to 2022 and the Ordr Data Lake has millions of device profiles; a number that grows as new devices are released and connected to environments across the globe. To enrich our data lake with new details and insights, we do a full, real-time packet capture across our customers’ environments to feed our platform with an accurate and continuous input of every connection, every flow, and every change. Analysis of that data is real-time too. It has to be. When someone asks for the current weather, it does no good to give the temperature from earlier in the day. Real-time analysis is critical in security and provides a precise assessment so accurate decisions can be made. In security, the game is rapid detection and remediation; guesswork is unacceptable.
Innovative Approaches to Problem Solving
Other key innovations have been part of the evolution of our platform. Data correlation, normalization, compression and organization is critical to storing and harnessing the massive amounts of data we collect and analyze without requiring hundreds of servers and zettabytes of disk storage. For those who are counting, one zettabyte is one billion terabytes. Thanks to our intelligent data compression, we can secure an entire large-scale hospital with just a few servers as our analytics backend. For context, the average hospital maintains an inventory of more than 100,000 total devices of which at least 10-15 thousand are in clinical care as internet of medical things (IoMT) devices, as well as IoT and OT associated with administration, communications, facilities management, and other essential functions–not to mention all the stranger things that find their way onto enterprise networks.
Behavior-based identity analytics is another key innovation for Ordr, and is used to establish multifactor authentication on agentless, unmanaged devices. Triangulation of factors such as a device’s OS vulnerabilities, communication patterns across the enterprise, communications patterns to external sites, and the reputation score of destination sites, are all analyzed to minimize false-positives and ensure a high level of confidence when unique indicators of compromise (IOC) are identified.
Countless hours of hard work, determination, and creativity were behind the effort that turned our vision into a proof-of-concept, and then, a working product. From that point, our vision, the strength of our team, and the potential of our technology helped us secure Series A funding, led by Alex Doll of Ten Eleven Ventures and joined by Unusual Ventures. With Series A we were able to build our team, establish our brand, and go to market. After Series B, led by Dharmesh Thakkar of Battery Ventures, and with investments from Kaiser Permanente Ventures and Mayo Clinic, Ordr was established as a force in healthcare and positioned for expansion into other verticals, like manufacturing, financial services, smart cities, and government. At this point, we began expanding into visibility and security for every connected device. To secure any device, you need visibility into every device in the network.
Flexibility in the Face of the Unexpected
When the pandemic struck in early 2020, the strength, resilience, and flexibility of our company were put to the test. The growth of nearly every organization was impacted at this time, but our healthcare customers in particular faced tremendous challenges. We stepped up to explore new ways to deliver value with our platform. Leveraging our core discovery and analytics capabilities, our customers found value in the ability to locate existing device inventory and understand real-time device utilization.
As an example, the Ordr platform enabled customers to keep track of critical devices such as ventilators, ensuring they were deployed to maximal efficiency to deal with the surge of COVID patients. Not only did the Ordr platform keep hospitals safe during this time, it also helped them run efficiently, ensuring they could continue to deliver critical healthcare services. That built goodwill and, when the pandemic eased, our customers adopted our platform enterprise-wide and recommended us to their peers in the industry. It was a key moment for the growth of our business.
Building an Unrivaled Franchise
As the world slowly returns to some semblance of normalcy, our Series C funding sets us up for our next phase of expansion on our journey to build an unrivaled security franchise. The Ordr Data Lake is growing rapidly, and now includes millions of device profiles, helping us to discover, identify, and classify every device in a customer’s environment with accurate, granular detail.
Within minutes of deploying Ordr in an environment, the data we analyze populates our UI with every connected device discovered, classifying each by manufacturer and model. Each device includes a picture for easy identification, along with a detailed description of attributes that include the device’s OS, vulnerabilities, connectivity details, flow data, applications installed, and logged users. Visualization in our platform is world-class and gets raves from our customers thanks to the tremendous “design thinking” effort we put into our UI/UX to achieve excellent aesthetics in support of usability.
On top of that, we add data and insights from a wide variety of enterprise tools to enrich our analysis. With more than 70 integrations, our data lake quickly provides accurate context for the operational status, as well as security posture, of every device in an organization.
Fast, Accurate, Dynamic, Automatic
Another critical strength of the Ordr platform is its ability to identify and respond to active attacks, including zero-day threats, and enable teams to stop them quickly with automation and orchestration. To get to “zero-day” attack detection requires behavioral baselines–something that must be done within minutes–to identify unique, malicious, abnormal behaviors. Since most connected devices operate within narrow behavioral parameters, our extensive data lake allows us to detect IOCs with a high degree of speed and accuracy.
Once malicious activity is identified, we leverage our deep knowledge of each device and its exact connectivity under normal operations to dynamically generate zero trust policies to isolate any misbehaving, potentially compromised device. These policies can be reviewed by security teams and, with a single click in our UI, policies are enforced with existing security and network infrastructure. With Ordr, response times are reduced from hours or days down to minutes to stop the spread of an attack. No other connected device security solution provides a complete map of all the devices, their connectivity in the enterprise, and their flow level context in real time, 24×7. We achieved this by building interfaces with every single network infrastructure vendor out there–a daunting task indeed.
The Next Chapter
From the start, our mission has been to help enterprise organizations see, know, and secure every connected device everywhere. We continue to innovate to deliver on that mission and provide our customers and partners with the most accurate, complete, and easy to consume device knowledgebase on the planet with meticulous device classifying, profiling, and cataloging.
What’s more, all of our data is available to partners through open APIs. In fact, Ordr is the only platform that has complete device intelligence that includes network and flow-level context with deep accuracy. Today, Ordr is well-positioned to be the supplier of choice of device intelligence to evolving Open XDR frameworks, providing open-source data to enable the correlation of information and delivery of the best possible service to the customers.
There are many more innovations and opportunities ahead for Ordr. With our world-class investors, dynamic board of directors, experienced management team, and passionate employees, we look ahead with laser focus to meeting the needs of our customers and helping them see, know, and secure every connected device that is critical to their business. Stay tuned, we’re off to write the industry’s next chapter on connected device security–and beyond.
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogTop 10 Risks of Not Getting Your CMDB In Order and How That Changes Today
BlogTop 10 Risks of Not Getting Your CMDB In Order and How That Changes Today…With ServiceNow and Ordr’s bidirectional integration, Ordr’s device, network, and risk context are combined with the business context of ServiceNow. And the new Service Graph Connector for Ordr makes the…
General
Top 10 Risks of Not Getting Your CMDB In Order and How That Changes Today
5Min Read
By Pandian Gnanaprakasam

What are the top ten risks of not getting your CMDB in order? How do those risks affect enterprise cybersecurity? And how can new tools and techniques that deliver real-time device discovery and analytics help you to change your situation? Great news! Ordr just announced the availability of the Service Graph Connector for Ordr in the ServiceNow Store. This integration is exciting for our customers, who can now maintain an up-to-date system of record for all assets so organizations can operate efficiently, react quickly, and manage risks more effectively.
Service Graph Connector for Ordr now available in the ServiceNow Store
Ordr provides the most comprehensive, accurate, real-time inventory of connected assets as a single source of truth. As the threat surface continuously evolves and expands, it is critical to ensure asset inventories are complete and provide the context to address risk proactively and reactively. With ServiceNow and Ordr’s bidirectional integration, Ordr’s device, network, and risk context are combined with the business context of ServiceNow. And the new Service Graph Connector for Ordr makes the integration more manageable and robust.
You now get a robust, most comprehensive, accurate real-time inventory of connected assets—from traditional IT to IoT, IoMT, and OT — and their risks in the ServiceNow Configuration Management Database (CMDB) to optimize enterprise-wide workflows and assess and manage risks.
Top Ten Security Risks of Incomplete and Outdated Asset Inventories
As given below, there are significant entry points that cybercriminals can exploit. With the combination of Ordr and ServiceNow, security and IT teams can identify and mitigate the following asset risks.
- Banned Equipment (Section 889)
To protect national security, the federal government bans products manufactured by prohibited companies such as Kaspersky, Huawei, and Hikvision. These banned products can have vulnerabilities if exploited, resulting in the loss of intellectual property. The mandate covers new procurement and requires reporting within one business day if any prohibited asset is discovered in inventory.
- Unauthorized Devices
Every unauthorized device that bypasses IT and operational tools and connects to a corporate network will expand the attack surface and could introduce significant risk. When the flash news of new vulnerabilities impacting corporate tools is announced, tracking all those instances of the compromised device can be challenging. This can include devices used in production and increasingly non-production or POV (Proof of Value) environments. The combination of Ordr and ServiceNow can proactively detect devices that can access other corporate servers and other precious devices and remove them from the network after the trial period.
- Orphaned/Missing Devices
Maintaining good asset hygiene is always a best practice for improving security posture. It is critical to ensure that all assets registered and recorded by the procurement team are tracked and compared against all the devices connecting to the network. Any gaps should be reconciled proactively before it results in security concerns.
- Manufacturer Recall / FDA Recall
Manufacturers may issue recall notices and security bulletins for significant vulnerabilities discovered. This is prevalent in regulated industries with mission-critical medical and industrial equipment devices. Similarly, from a federal regulation perspective, there can be recalls for sensitive equipment such as medical devices. Ordr can collate all recall announcements from multiple sources and tag all devices impacted; this context can be shared with ServiceNow.
- Default Credentials
Business groups typically install IoT devices such as cameras in batches. The person responsible for the installation is usually not technical and often needs to gain knowledge or experience to change default passwords. It is unrealistic, if not impossible, to have a process to choose multiple unique passwords for physical security cameras when hundreds to thousands are going up in the ceiling. Think of the risk when hundreds of devices default to “Password1”. These passwords are not rotated periodically using over-the-air methods, like a password policy that enforces periodic password changes for laptops and desktops. An asset management system that combines the Ordr “default password discovery” feature with ServiceNow CMDB can alert administrators to update the credentials associated with these devices.
- Rogue Wireless/Switches that are bridging traffic to the internet (5G/LTE/Guest Wi-Fi)
Unauthorized devices usually connect to a corporate open port and a set of devices using a daisy chain mechanism. Suppose the consumer-grade switches/routers come with LTE or link to the Guest Wi-Fi network. In this case, taking corporate data and exfiltrating without going through all the border controls exercised by firewalls becomes easier. It is a vast attack surface. Even when a good asset management and visibility solution is implemented, one needs a sophisticated tool to understand this daisy chain mechanism throughout the network to keep an exact list of these devices and implement a solution to eliminate them. An asset management system must integrate with a sophisticated visibility tool to detect and eliminate these daisy chain devices; this is why the Ordr and ServiceNow integration is so powerful.
- Non-Compliant Devices
When a corporate Antivirus (AV)/Endpoint Detection Response (EDR) policy mandates that all IT endpoints (e.g., laptops, mobile, desktops) need to have a robust agent/software installed, it is not easy to audit all the devices and pull a list of those that do not have the required software installed. One step further than that is how challenging it is to ensure all those EDR agents are continuously running and receiving updates periodically to detect and thwart the latest attacks.Expired Certificates: We have all experienced how frantic it is to fix a certificate issue when a critical server stops working with expired certs. With a good asset management strategy, corporate IT can track all certificate expirations and implement a plan to address them periodically. Both these insights are readily available with Ordr and can be shared with ServiceNow.
- Local User Accounts without Domain Joins
All users accessing a system must be part of Windows Active Directory (AD), if possible. This is especially critical in the case of older Windows machines that usually have a lot of unpatched vulnerabilities. Even if the device is part of the domain controller, sometimes operators can create local users on these machines. This practice must be watched closely, and a list of all locally-made user accounts must be extracted and reported continuously. When hackers create local user accounts and leave them dormant for later exploitation, it is easy to identify and remove those inactive accounts and fix the machines with malware infections.
- End-of-Life / Outdated OS
Assets running end-of-life and outdated operating systems pose a significant risk to the organization. The first step is to identify these end-of-life devices. This can be a struggle without a solution like Ordr and ServiceNow that not only delivers accurate real-time inventory but now extends visibility to IoT, IoMT, and OT devices that often have longer operating cycles than traditional IT endpoints.Note that upgrading all devices running end-of-life or outdated OS is a logical way to address potential risks. But upgrading these devices in regulated industries such as healthcare, manufacturing, and banking might not be possible due to backward compatibility issues. In some cases, an update to a device will trigger the need to re-certify the device with federal regulators. For all these cases, it is prudent to have a segmentation strategy to isolate outdated and at-risk devices from other parts of your environment, which could get be easily accomplished with Ordr’s behavioral baselining and automated Zero Trust policies.
- Unpatched Devices Vulnerable to Exploitation
This is the most important reason one should embark on an asset management strategy to get an accurate view of all connected devices and their associated details. An asset management strategy must include identifying operating system (OS) versions and patch levels for each connected device. This makes it easy to highlight the exact CVEs (Common Vulnerabilities and Exposures) that are still open and vulnerable that a potential hacker could exploit. Having this list as a work item and tracking how the patching for these devices is progressing is one of the most foundational aspects of cyber security an organization can initiate.
Asset Management Aligned to Risk Reduction
An incomplete and inaccurate asset inventory poses many risks. The risks can extend from non-compliance to safety and regulatory concerns. On top of that, add the problems of security breaches, which can cause high financial and reputation costs to organizations.
Understanding your attack surface by implementing a robust asset management strategy that identifies and closely tracks vulnerabilities and threats from the entire asset universe of IT, OT, IoT, ICS, BMS, and IoMT (Internet of Medical Things) will minimize the risk imposed on an organization. We are proud to offer the Service Graph Connector for Ordr to help customers achieve the comprehensive and accurate asset inventory they need to simplify workflows, improve security, and accelerate incident response.
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
- Banned Equipment (Section 889)
-
PagesIntegrations
…inventory, identifies and prioritizes asset risk, and tracks and risk-rates asset communications patterns. Ordr transmits this critical security context to Fortinet FortiGate, FortiManager, and FortiNAC, allowing administrators to create and…
- PLATFORM
- INTEGRATIONS
Enable Faster ROI With Ordr Integrations
Ordr integrates with 180+ security, networking, infrastructure, IT, and clinical solutions to unify device details, enrich device context, and extend the value of your existing investments.
Aruba
With Ordr and HPE Aruba ClearPass Policy Manager (CPPM), organizations can quickly gain complete visibility into every connected device and deploy segmentation to proactively protect and reactively respond and mitigate threats. This includes Zero Trust policy enforcement and microsegmentation to isolate groups or individual devices from non-essential access while protecting them from attack and compromise on existing networking and security infrastructure
How it works
The integrated Ordr SCE and HPE Aruba CPPM solution makes it easy to get rich visibility for IoT and unmanaged devices and to simplify segmentation projects. The solution provides detailed classification and context for every connected device, automatically groups devices into CPPM policy groups for role-based access and facilitates software-defined segmentation to provide more precise controls for every IoT device in the network. By providing continuous, multi-level security monitoring of all device communications, Ordr SCE detects anomalous behavior and shares this information with ClearPass to implement network access control based on vulnerability, threat, and risk ratings. Ordr SCE also integrates with HPE Aruba CPPM to streamline the process of containing threats based on the organization’s access policy such as blocking unauthorized devices, quarantining them, or limiting their network access.
Benefits
- Automating IoT inventory discovery, classification, and categorization, and sharing detailed device context with ClearPass
- Providing rich analytics about the behavior of all devices that guides segmentation design, streamlines the segmentation implementation, and audits the result to assure accuracy and effectiveness
- Quickly contain threats and protect at-risk devices
- Accelerating ClearPass deployments with powerful yet easy-to-use tools that provide accurate device information and automate steps that are traditionally error-prone and labor intensive
CrowdStrike
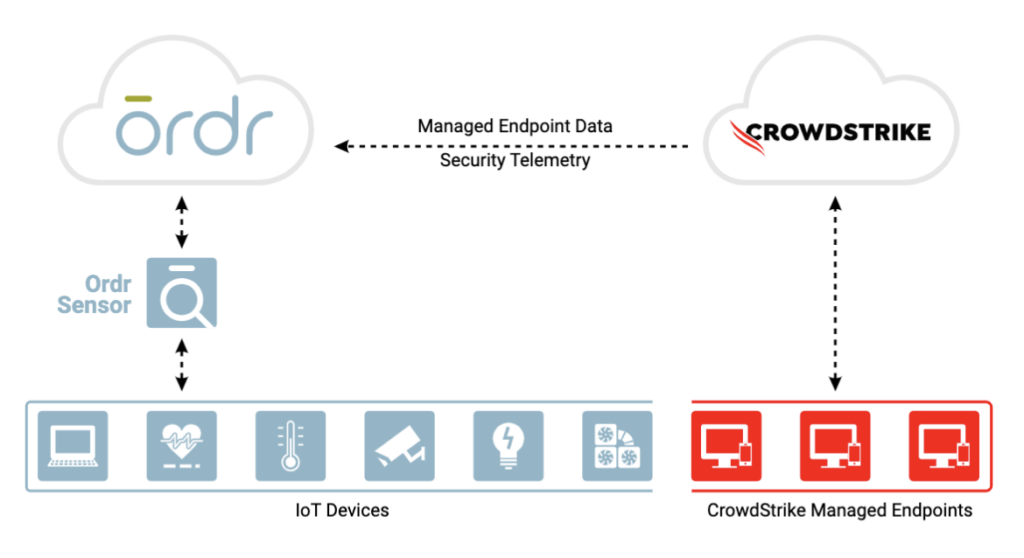
Integration between Ordr and CrowdStrike ensures the security of all managed and unmanaged devices with comprehensive device visibility, detailed vulnerability insights, an understanding of risk, and the ability to enforce policy to mitigate active threats and improve security across all connected devices
How it works
Ordr analyzes network flow data to automatically discover and classify every connected device, profile behavior, and identify active threats. Security telemetry from the CrowdStrike Falcon platform, is shared with Ordr to enhance device insights, and provide a centralized, deep understanding of each device and its associated risk. Ordr uses multiple factors to calculate risk for each device based on business context, asset criticality, vulnerabilities, and overall threat details. With additional device data from the Falcon platform, Ordr provides a highly accurate risk score for each device. By continuously synchronizing device risk scores with CrowdStrike’s enriched security data, Ordr enables teams with an up-to-date view of risk to help them focus on the most critical devices.
Benefits
Gain complete device visibility
- See into all devices – agentless and agent-based
- Track both online and offline devices continuously
- Identify unmanaged devices without CrowdStrike agent for compliance
Minimize risk with better insights
- Improve Ordr risk score accuracy with supplemental event data from CrowdStrike
Remediate faster
- Improve threat detection and incident response time with a combination of Ordr endpoint flow & CrowdStrike process data
- Block/quarantine/segment managed endpoints in Ordr for rapid remediation via the network
Fortinet
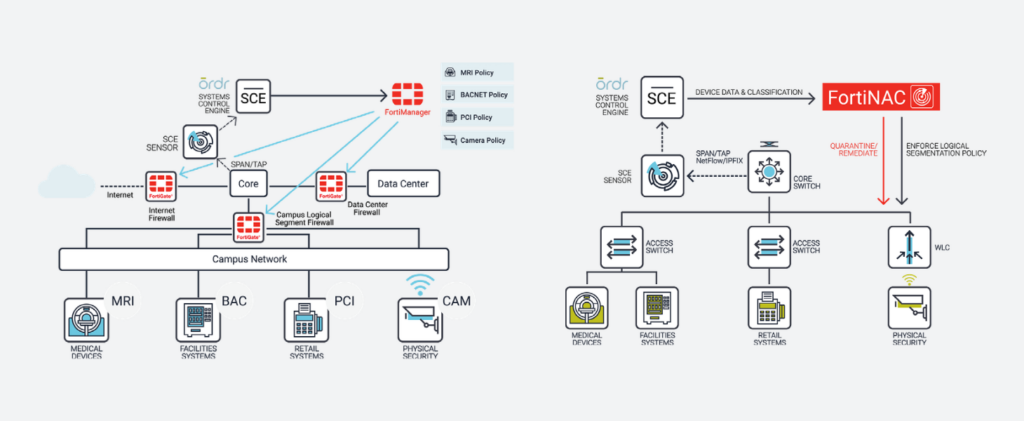
Fortinet and Ordr have partnered to deliver an industry-leading IoT and unmanaged device security solution by integrating FortiManager, FortiGate and FortiNAC with Ordr Systems Control Engine (SCE)
How it works
Automated Visibility and Security of All Connected Devices
Ordr SCE automatically creates a complete asset inventory, identifies and prioritizes asset risk, and tracks and risk-rates asset communications patterns. Ordr transmits this critical security context to Fortinet FortiGate, FortiManager, and FortiNAC, allowing administrators to create and apply firewall and NAC policies using business-relevant groups, classifications, and device names, while understanding the full risk profile and impact of each change. Ordr further reduces administrative costs by automatically updating asset groupings as devices join and leave the network, as well as by creating and transmitting security policies directly to FortiGate and FortiManager for enforcement.
Benefits
With the integration, joint customers can now:
- Discover and inventory every connected network asset, including the massive volume of IoT and unmanaged devices, and make available across the Fortinet Security Fabric, from endpoint to edge, through FortiNAC, FortiManager, and FortiGate
- Establish comprehensive security controls that restrict IoT devices to known-good network behaviors
- Manage firewall and NAC policies using business-relevant context such as device type, manufacturer, location, risk, and function rather than IP addresses
- Automate updates of firewall groups and address info to ensure consistent policy enforcement regardless of device location, VLAN, or IP assignment, thus drastically reducing operational costs and downtime
- Protect critical devices with automated, zone-based segmentation and microsegmentation within zones
SentinelOne
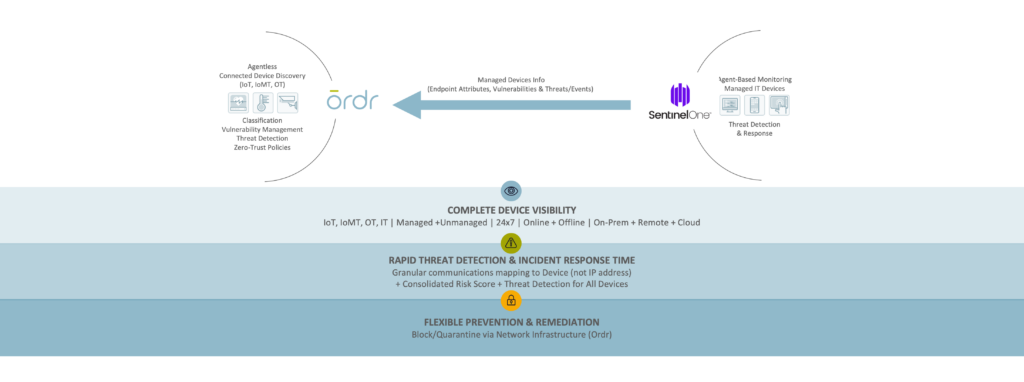
Ordr integration with SentinelOne enables collection of managed device data, vulnerabilities and threat insights for comprehensive device visibility and a better understanding of risk.
How It Works
Ordr discovers and secures every connected device—from traditional IT to new or vulnerable IoT, IoMT, and OT devices. With the SentinelOne integration, Ordr collects managed device data, vulnerabilities, and threat insights from the Singularity Platform delivering comprehensive device visibility, a better understanding of risk, and the ability to enforce policy to mitigate active threats and improve security across all connected devices.
Benefits
Gain Complete Device Visibility
- See granular details for all agentless and agent-based devices.
- Track both online and offline devices continuously.
- Identify unmanaged devices without the SentinelOne agent to meet compliance requirements.
Minimize Risk with Extended Insights
- Improve risk score accuracy with supplemental event data from SentinelOne.
Remediate Faster
- Improve threat detection and incident response with combined Ordr endpoint flow and SentinelOne process data.
- Block/quarantine/segment managed endpoints in Ordr for rapid remediation via the network.
Gigamon
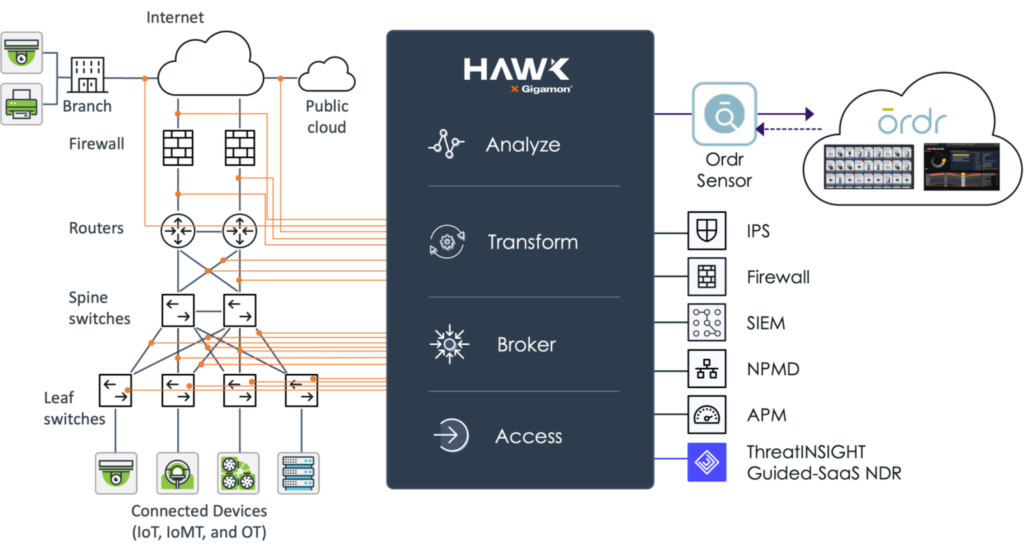
A basic tenet of network security and regulatory compliance is that “You cannot secure what you cannot see.” Gigamon and Ordr have teamed to deliver unsurpassed visibility and control into every thing connected to your network.
How It Works
The Gigamon Visibility and Analytics Fabric (VAF) optimizes data collection of all north-south and east-west traffic across branch, campus, data center and cloud. Collected data is delivered to Ordr for analysis to ensure comprehensive device classification and visibility into all device communications. Integration with Gigamon VAF also eliminates concerns of SPAN security and potential impact to network infrastructure with “yet another SPAN port or session.”
By integrating with Gigamon VAF, customers can significantly reduce the number of Ordr sensors required to comprehensively discover and monitor every network-connected device, simplifying your network and security monitoring architecture.
Benefits
- Real-time asset inventory – Ordr continuously analyzes device traffic sent from Gigamon to passively discover an automatically classify every device connected to the network to help you maintain an up-to-date and accurate inventory.
- Connected device risk – using the traffic captured and optimized by Gigamon Hawk, Ordr calculates device risk scores and uncovers connected devices with risk such as outdated operating systems, unpatched software, weak passwords, and manufacturer recalls. Ordr also maps and baselines device communications to identify risk and stop attacks.
- Accelerate Zero Trust – working together, Gigamon and Ordr can map and baseline all IT, IoT and other device communications. Ordr can then dynamically create Zero Trust policies to simplify and accelerate NAC and segmentation projects. These policies can be enforced with popular security and network devices to integrate with existing infrastructure tools.
Palo Alto Networks
Rapid7
Ordr works with Rapid7 to seamlessly discover all connected assets including IoT, IoMT, and OT devices. The joint solution enables Rapid7 to perform the right scan at the right time regardless of the device type, location, criticality or role within the organization. Many vulnerable IoT/OT devices discovered by Rapid7 cannot be patched or updated. Ordr automates the application of compensating controls to safeguard these devices by sending protection policies directly to firewalls, switches, wireless, or NAC systems. Similarly, infected devices can be quickly isolated through existing network and security devices.
How It Works
The integration with Ordr and Rapid7 InsightVM provide ongoing bi-directional synchronization for managing vulnerabilities with rich device context. Ordr discovers every connected device, profiles device behaviors and risks, and automates remediation responses. Rapid7 InsightVM provides visibility into the vulnerabilities and clarity on how those vulnerabilities translate into business risk. Combining Ordr’s unique device intelligence with Rapid7’s advanced vulnerability intelligence provides organizations with the ultimate solution to efficiently manage risks while reducing service disruption and time to remediate.
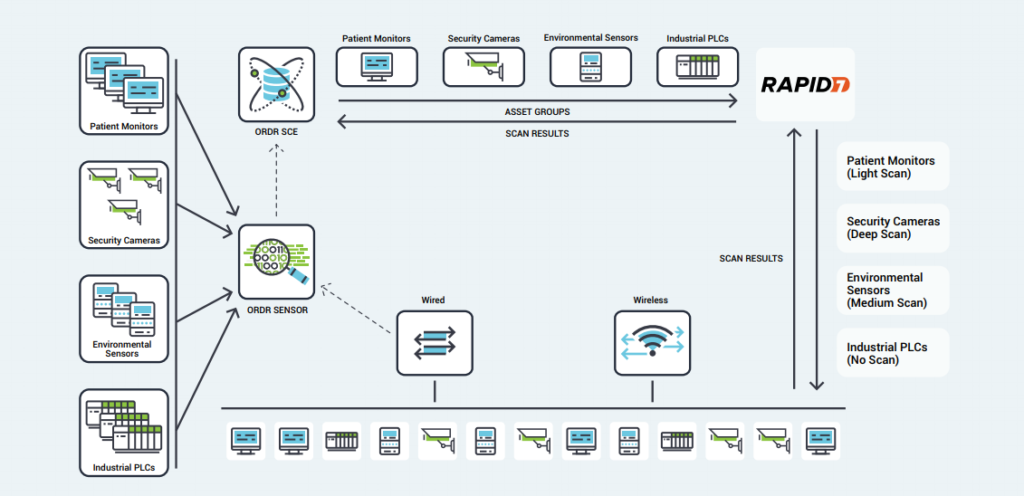
Benefits
- Comprehensive Coverage – Ordr’s identification and classification of lightweight, agentless devices allows administrators to quickly exclude specific IoT devices or categories from active Rapid7 scans, opening network segments to vulnerability scanning that had previously been excluded.
- Optimized Scanning – Using Ordr’s detailed insight into device types, scan sensitivity, and their critical role within the organization, Rapid7 scans can be tailored to each device.
- Proactive Protection – Rather than blocking or quarantining critical IoT devices after infection, Ordr’s segmentation policies create barriers that protect vulnerable devices while still enabling essential services.
- Smart Scheduling – Ordr tracks utilization patterns for critical devices, allowing administrators to schedule vulnerability scans for times when devices are not in use, minimizing disruption and operational risk.
Splunk
Ordr integration with Splunk allows you to leverage Ordr’s rich device data to create alerts, reports, and custom analyses. Ordr transmits security alerts, device information, and other critical information. Splunk ingests the feed for better event management.
VMware
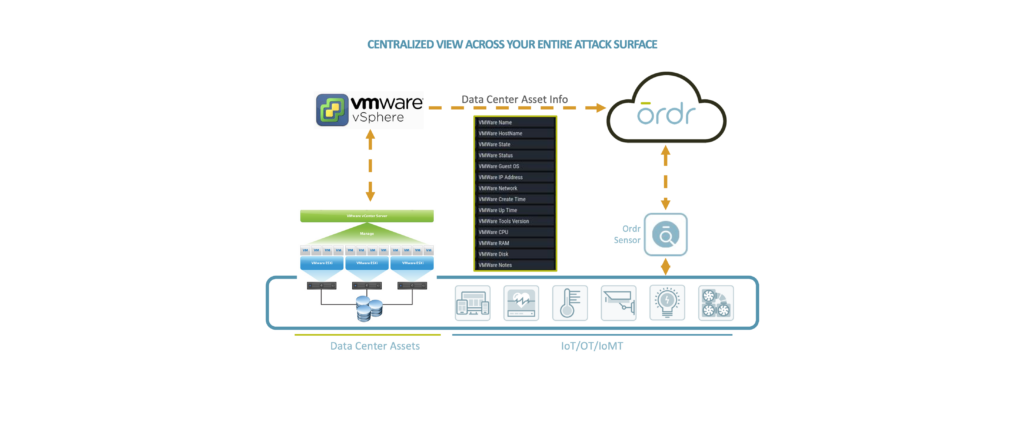
Ordr leverages the vSphere API, which provides access to server management, virtual machine provisioning, monitoring, and more. Ordr collects datacenter asset details including the servers (hosts), individual virtual machines (guests), operating systems, shared compute resources (CPU, memory, disk), status, and compatibility.
The extended visibility to VMware workloads running in public, private, and hybrid cloud environments delivers a ‘whole hospital’ or ‘whole enterprise’ approach to security ensuring that no device or connection remains unknown.
Microsoft
Ordr integrates with multiple Microsoft solutions to enhance device context and improve risk insights to keep your organization secure.
Ready to Get Started?
-
Knowledge Base10 Internet of Things (IoT) Healthcare Examples
10 INTERNET OF THINGS (IoT) HEALTHCARE EXAMPLES 6Min Read 10 INTERNET OF THINGS (IoT) HEALTHCARE EXAMPLES, AND WHY THEIR SECURITY MATTERS Connected devices in healthcare—often referred to as the Internet…
10 INTERNET OF THINGS (IoT) HEALTHCARE EXAMPLES
6Min Read10 INTERNET OF THINGS (IoT) HEALTHCARE EXAMPLES, AND WHY THEIR SECURITY MATTERS
Connected devices in healthcare—often referred to as the Internet of Medical Things (IoMT)—represent one of the fastest-growing sectors of the IoT market, and is predicted to reach $176 billion by 2026.
To monitor, manage, and protect Internet of Things (IoT) devices in healthcare you must first understand the multiple ways in which IoMT devices are used. While the most popular example of IoT in healthcare is remote patient monitoring—meaning IoMT devices that collect patient data such as heart rate and body temperature—there are many other examples of IoT in the healthcare industry.
Here’s a look at 10 ways IoT is changing healthcare, as well as how the use of IoT devices for medical purposes impacts IoT security.
Healthcare monitoring devices
IoT devices offer a number of new opportunities for healthcare professionals to monitor patients, as well as for patients to monitor themselves. By extension, the variety of wearable IoT devices provide an array of benefits and challenges, for healthcare providers and their patients alike.
1. Remote patient monitoring
Remote patient monitoring is the most common application of IoT devices for healthcare. IoT devices can automatically collect health metrics like heart rate, blood pressure, temperature, and more from patients who are not physically present in a healthcare facility, eliminating the need for patients to travel to the providers, or for patients to collect it themselves.
When an IoT device collects patient data, it forwards the data to a software application where healthcare professionals and/or patients can view it. Algorithms may be used to analyze the data in order to recommend treatments or generate alerts. For example, an IoT sensor that detects a patient’s unusually low heart rate may generate an alert so that healthcare professionals can intervene.
A major challenge with remote patient monitoring devices is ensuring that the highly personal data that these IoT devices collect is secure and private.
2. Glucose monitoring
For the more than 30 million Americans with diabetes, glucose monitoring has traditionally been difficult. Not only is it inconvenient to have to check glucose levels and manually record results, but doing so reports a patient’s glucose levels only at the exact time the test is provided. If levels fluctuate widely, periodic testing may not be sufficient to detect a problem.
IoT devices can help address these challenges by providing continuous, automatic monitoring of glucose levels in patients. Glucose monitoring devices eliminate the need to keep records manually, and they can alert patients when glucose levels are problematic.
Challenges include designing an IoT device for glucose monitoring that:
a. Is small enough to monitor continuously without causing a disruption to patients
b. Does not consume so much electricity that it needs to be recharged frequently.These are not insurmountable challenges, however, and devices that address them promise to revolutionize the way patients handle glucose monitoring.
3. Heart-rate monitoring
Like glucose, monitoring heart rates can be challenging, even for patients who are present in healthcare facilities. Periodic heart rate checks don’t guard against rapid fluctuations in heart rates, and conventional devices for continuous cardiac monitoring used in hospitals require patients to be attached to wired machines constantly, impairing their mobility.
Today, a variety of small IoT devices are available for heart rate monitoring, freeing patients to move around as they like while ensuring that their hearts are monitored continuously. Guaranteeing ultra-accurate results remains somewhat of a challenge, but most modern devices can deliver accuracy rates of about 90 percent or better.
4. Hand hygiene monitoring
Traditionally, there hasn’t been a good way to ensure that providers and patients inside a healthcare facility washed their hands properly in order to minimize the risk of spreading contagion.
Today, many hospitals and other health care operations use IoT devices to remind people to sanitize their hands when they enter hospital rooms. The devices can even give instructions on how best to sanitize to mitigate a particular risk for a particular patient.
A major shortcoming is that these devices can only remind people to clean their hands; they can’t do it for them. Still, research suggests that these devices can reduce infection rates by more than 60 percent in hospitals.
5. Depression and mood monitoring
Information about depression symptoms and patients’ general mood is another type of data that has traditionally been difficult to collect continuously. Healthcare providers might periodically ask patients how they are feeling, but were unable to anticipate sudden mood swings. And, often, patients don’t accurately report their feelings.
“Mood-aware” IoT devices can address these challenges. By collecting and analyzing data such as heart rate and blood pressure, devices can infer information about a patient’s mental state. Advanced IoT devices for mood monitoring can even track data such as the movement of a patient’s eyes.
The key challenge here is that metrics like these can’t predict depression symptoms or other causes for concern with complete accuracy. But neither can a traditional in-person mental assessment.
6. Parkinson’s disease monitoring
In order to treat Parkinson’s patients most effectively, healthcare providers must be able to assess how the severity of their symptoms fluctuate through the day.
IoT sensors promise to make this task much easier by continuously collecting data about Parkinson’s symptoms. At the same time, the devices give patients the freedom to go about their lives in their own homes, instead of having to spend extended periods in a hospital for observation.
Other examples of IoT/IoMT
While wearable devices like those described above remain the most commonly used type of IoT device in healthcare, there are devices that go beyond monitoring to actually providing treatment, or even “living” in or on the patient. Examples include the following.
7. Connected inhalers
Conditions such as asthma or COPD often involve attacks that come on suddenly, with little warning. IoT-connected inhalers can help patients by monitoring the frequency of attacks, as well as collecting data from the environment to help healthcare providers understand what triggered an attack.
In addition, connected inhalers can alert patients when they leave inhalers at home, placing them at risk of suffering an attack without their inhaler present, or when they use the inhaler improperly.
8. Ingestible sensors
Collecting data from inside the human body is typically a messy and highly disruptive affair. No no enjoys having a camera or probe stuck into their digestive tract, for example.
With ingestible sensors, it’s possible to collect information from digestive and other systems in a much less invasive way. They provide insights into stomach PH levels, for instance, or help pinpoint the source of internal bleeding.
These devices must be small enough to be swallowed easily. They must also be able to dissolve or pass through the human body cleanly on their own. Several companies are hard at work on ingestible sensors that meet these criteria.
9. Connected contact lenses
Smart contact lenses provide another opportunity for collecting healthcare data in a passive, non-intrusive way. They could also, incidentally, include microcameras that allow wearers effectively to take pictures with their eyes, which is probably why companies like Google have patented connected contact lenses.
Whether they’re used to improve health outcomes or for other purposes, smart lenses promise to turn human eyes into a powerful tool for digital interactions.
10. Robotic surgery
By deploying small Internet-connected robots inside the human body, surgeons can perform complex procedures that would be difficult to manage using human hands. At the same time, robotic surgeries performed by small IoT devices can reduce the size of incisions required to perform surgery, leading to a less invasive process, and faster healing for patients.
These devices must be small enough and reliable enough to perform surgeries with minimal disruption. They must also be able to interpret complex conditions inside bodies in order to make the right decisions about how to proceed during a surgery. But IoT robots are already being used for surgery, showing that these challenges can be adequately addressed.
Why security matters for IoT in healthcare
In order to make the most of IoT for healthcare, critical security challenges must be addressed.
Above all, IoT device developers, managers and healthcare providers must ensure that they adequately secure data collected by IoT devices. Much of the data collected by medical devices qualifies as protected health information under HIPAA and similar regulations. As a result, IoT devices could be used as gateways for stealing sensitive data if not properly secured. Indeed, 82 percent of healthcare organizations report having experienced attacks against their IoT devices.
Developing secure IoT hardware and software is one step in addressing this challenge. Equally important, however, is ensuring that IoT devices in healthcare are managed properly in order to protect against data from unmonitored devices falling into the wrong hands. A patient monitoring device that has an older version of software or firmware, or a device that is not properly decommissioned after it is no longer needed, for example, could offer attackers an opportunity to infiltrate a network or steal protected health information.
Proper discovery and classification of all IoT devices on a healthcare provider’s network helps guard against this risk. Once IoT device networks are properly identified, classified, regulated, and secured, managers can track device behavior to identify anomalies, perform risk assessments and segment vulnerable from mission-critical devices.
Ordr can help
In a hyper-connected healthcare enterprise, the quantity and heterogeneity of IoT devices creates a complex and increasingly untenable reality for healthcare technology, IT and security organizations. Leaders struggle to understand exactly what’s connected to the network, what it’s doing, and how to regulate and protect it all.
Ordr Systems Control Engine (SCE) can enable visibility, and security of all of your connected medical devices. It can identify, classify, profile behavior and risk, and secure all medical and IoT assets in your healthcare organization. Once you understand the behavior and communications of every connected device, you can proactively secure them using microsegmentation policies enforced on your existing network and security infrastructure, without touching or modifying the devices. You can even use Ordr to maximize the utilization of all of your connected medical devices.
Ordr offers superior ransomware protection across the kill chain starting with comprehensive visibility into devices and risks (including complete details about devices, with granular insights—such as make, model, serial number, and network location). Our solution is capable of illuminating network blind spots by monitoring for east-west lateral movement and identifying attacker exploit tools. Our machine learning engine can baseline communication patterns to recognize an attack in progress, such as C2 communications. Finally, automated policies allow security teams to take action rapidly.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
Knowledge BaseHow to Detect Ransomware
…initial infection is in, the installation phase is where the infection begins to disseminate itself within the network. Sometimes the ransomware needs to make an external C2 communication in order…
How to Detect Ransomware
8Min ReadIt’s no secret that there are cyber criminals out there who are after your company’s critical assets, but now you have to be concerned with your data not only being exfiltrated and sold—you have to worry about losing them entirely if you can’t or won’t pay a ransom..
Once upon a time, firewalls were a viable way to protect assets, but companies can’t rely anymore on the moat keeping the castle safe. It’s too easy to get the keys to the gate, especially with the extended enterprise – cloud, SaaS and remote work.
An astounding 70% of ransomware attacks succeed in encrypting a company’s data. This is due to how quickly ransomware can infect a system. Microsoft’s research determined that 97% of ransomware attacks infect the intended target within four hours. As if that isn’t disturbing enough, more advanced ransomware infections can infiltrate and assume control of a system in less than 45 seconds.
What is Ransomware?
Ransomware is a type of malware that loads itself into your system, spreads like wildfire, locks down files and data via encryption, and then holds it hostage for ransom. It has surged to the forefront as one of the most popular cyberattack methods, and now companies must contend with even more advanced tactics from cyberattackers utilizing Ransomware-as-a-Service.
Ransomware has many avenues into your organization. It can arrive in an infected attachment, which attacks your system once the attachment has been downloaded. Ransomware also can infect via an executable file, an infected website, a fake ad that a user interacts with, or even an infected chat message that contains a clickable link. It can even hide inside of a macro in a Word document.
One of the most common ways to launch ransomware attacks is via phishing. Phishing is still done via email, but it’s now also done with voice calls (vishing) and SMS (smishing). Adversaries also deploy different methods, such as hitting a smaller selection of targets (spear fishing), even executives specifically (whaling). It’s a complex environment with highly believable messages, emails, or phone calls. Social media even plays a part—everyone has seen those “Getting to Know You” posts, which are often really just fronts for obtaining your details that are helpful in stealing your information for their own nefarious purposes.
Ransomware Attacks: What Have We Learned?
Ransomware has definitely made its presence known: a new organization finds itself in battle with ransomware roughly every 11 seconds. Analyzing past attacks and their outcomes allows us to measure the impact of ransomware and evolve protections used against them.
Colonial Pipeline Attack
In May 2021, the Colonial Pipeline was attacked by a group known as DarkSide. The group entered the systems via a stolen set of credentials for the Colonial Pipeline’s VPN. Within two hours, Darkside stole roughly 100 gigabytes of data and deployed the ransomware as they exited. The ransomware made itself known the following day, and Colonial Pipeline was forced to shut down its pipeline OT network because their IT systems including billing and accounting were down.
The impact of this attack was substantial. The airline industry had a jet fuel shortage. The fear of gasoline shortages incited panic in six eastern states. Gas prices spiked, affecting consumers. And then there was the $4.4 million ransom that Colonial Pipeline paid. The Department of Justice recovered roughly $2.3 million of that ransom, but Colonial Pipeline was out the rest of the funds, in addition to the cost of being completely shut down for six days.
This attack displays the importance of using a multi-layered approach. Once DarkSide breached the gate (the VPN), they went unchecked. It’s essential to monitor the network for ransomware, inspect traffic, and implement additional checks, like multi-factor authentication, to protect against this type of attack.
JBS Incident
The JBS attack was the second major one that affected U.S. infrastructure in May 2021; this attack was perpetrated by REvil, a Russian-based ransomware-as-a-service organization. In addition to shutting down services, it’s believed that sensitive customer data also was stolen. The company deemed it had no choice but to pay the $11 million ransom to protect their customers.
This incident had a global impact. It shutdown cattle slaughtering in all US plants for a full day, which caused food supply disruption and increased food prices. Some Australia and Canada operations were disrupted, as well.
The details of this attack haven’t been released, but it was deemed to be highly sophisticated.
Zero Day Attack On Kaseya
In July of 2021, REvil used Kaseya’s virtual system administrators (VSA) to disperse ransomware to Kaseya’s customer base. Because many of Kaseya’s customers are managed service providers (MSP), the ransomware was further dispersed to their customers. It was one of the largest ransomware sprees in history.
The impact of this attack was extensive. Over 22 countries were affected, with roughly a million individual systems having been put at risk in a wide range of industries. It’d be impossible to list every single effect of such a widespread attack, but it provided a great example of why efficient, effective cybersecurity is necessary.
The Kaseya attack shows us that prevention won’t always work. Because there was no barrier to entry, discovering lateral movement would be the best chance of containing damage in situations like this. Complete east-west traffic monitoring would be the best way to detect such an attack. It also demonstrates the importance of microsegmentation and a Zero Trust cybersecurity strategy, which in this case would’ve allowed the organization to shut down the affected area and prevented the infection from spreading.
Detecting Ransomware
Ransomware is an issue that every organization faces. It’s essential to detect ransomware before it has encrypted your organization’s files, because then it’s too late to take effective action.
Ransomware can be detected at various stages of the cyber kill chain:
Reconnaissance
In this stage, the attackers focus on checking out your organization’s systems. This could be looking for viable breach opportunities by scanning ports or networks, or collecting information about the system and/or users.
In order to detect ransomware in the reconnaissance stage, your system must be capable of detecting any network or port scans that are performed. Ordr supports the ability to detect reconnaissance attacks.
Weaponization
Weaponization refers to applying various techniques to the code after reconnaissance so it’s capable of evading memory-, network-, and/or file-based cyber defense measures employed by the targeted network. For example, attackers may make the payload look like a simple PDF or hide it inside a benign-looking word document.
To combat this effectively, it’s essential to stay updated on patches and security updates. Also, employ a solution, like Ordr’s platform, that utilizes a variety of threat intelligence and security sources, as well as AI and DPI, to identify the high-risk devices on the network that may be targeted. Ordr can dynamically generate segmentation policies for devices that run outdated operating systems that cannot be patched.
Delivery
This is the kill chain stage that’s concerned with loading the ransomware into your organization’s system. It could be via an email containing an infected attachment or plugging in a compromised USB drive. Or, it could be gaining credentials or assistance from an employee through social engineering, or using a traffic distribution system (TDS) to redirect traffic from a legitimate website to a malicious website.
Device security is effective here, because if a device can be seen as compromised, it can be quarantined. Along that same line, if microsegmentation is used, the small section of the network where the ransomware is initially deployed can be locked down to prevent compromising the rest of the network. Other applicable protections include adequate change management and application whitelisting. Ordr can dynamically create the appropriate microsegmentation policies based on business risks.
Exploitation
Exploitation is where the ransomware actually launches itself on the victim machine. Typically, this is done one of two ways: exploit kit or specific, targeted exploitation. The difference is whether or not the threat actors have a known vulnerability to exploit. If the vulnerability is known in advance, it’ll be specifically targeted.
Using secure passwords, security patching, and continuous network monitoring can help thwart ransomware’s ability to successfully exploit your system. It’s essential to make the network harder to exploit and also slow down anything that does manage to get into the system. The Ordr platform includes an integrated threat detection system that can identify exploits and attacker tools, such as Cobalt Strike or Eternal Blue.
Installation and Lateral Movement
Once the initial infection is in, the installation phase is where the infection begins to disseminate itself within the network. Sometimes the ransomware needs to make an external C2 communication in order to complete this, but other types of ransomware begin lateral movement on their own. The ransomware targets files in the system and any accessible backups.
To successfully combat ransomware, a system should monitor for these C2 communications so an attack can be isolated. It’s also necessary to monitor traffic, especially with regard to east-west lateral movement. Ordr uses machine learning to baseline the normal communication patterns for a device; as a result, lateral movement or anomalous communications to a C2 site will trigger alerts. Ordr also integrates with Active Directory to track users’ access to the devices, applications, and systems on the network.
Command and Control
Once the command and control phase has been reached, the attackers are communicating with the attacker domain (C2). They are in the network and very likely have already started the process of encrypting data and/or exfiltrating it for extortion purposes. The attackers are now in control and issue the ransom demand.
Actions on Objectives
At this point, the ransomware provides the instructions for paying the ransom. Whether your data is actually returned after paying the ransom is another story.
Best Practices for Ransomware Detection
Ransomware comes in many different shapes and sizes, and often strikes with an unknown advantage. For this reason, your organization’s cybersecurity should be armed with both prevention and detection. The following best practices can help arm your cybersecurity solution:
1. Focus on basic cybersecurity hygiene
Cybersecurity technology constantly evolves, but there are basic practices that can help your organization mitigate the impact of ransomware. Examples of this include conducting regular vulnerability scans and having a regular patch schedule. Ordr gives you a strong cybersecurity solution that helps you follow such best practices—having detailed info about each device’s make, model, serial number, location in the network identifies vulnerable devices, and mapping every device communication patterns is critical to establish a baseline so you can identify when an attack is happening.
2. Establish process and compliance procedures
Ransomware affects an organization as a whole, and any processes and procedures need to be known and followed by the organization as whole. Important stakeholders and key decision makers should be involved in this process. For example, during a ransomware attack, who is going to negotiate with the attacker? What is the criteria for deciding when you’re going to pay a ransom?
3. Prioritize continuous improvement
Ransomware becomes smarter and more intricate all the time and can explode from a threat to a crisis in the blink of an eye. A static system of protection isn’t viable for long, so your organization needs to continuously improve cybersecurity. Identify vulnerabilities and security weaknesses so you can correct them before an unfriendly source reveals them for you. Ordr’s platform helps automate continuous improvement and is agentless so you can effortlessly have state-of-the-art protection at your fingertips. Ordr sensors deploy across the network, so while most organizations focus on north-south threat detection, our platform also performs east-west traffic analyses to detect lateral movement—a major blind spot for enterprises.
4. Implement zero trust
Zero trust is a revolutionary take on cybersecurity that states nothing should be trusted and everything must be verified. Zero trust is highly effective against cyberattackers, and helps protect your organization from ransomware and other cyber incidents.
Where to Go From Here
Ransomware is an ever present threat that needs to be caught early in the cyber kill chain to prevent significant damage to your organization’s systems. The key to this is identifying devices that are at risk prior to the attack and locking them down. During an attack, it’s critical to determine what device has been compromised, where that device is located in the network and what it’s communicating to. From there, rapid mitigation can be employed to contain the infection. Finally, retrospective analysis provides the ability to identify potentially infected devices or systems when new indicators of compromise emerge, allowing you to identify security systems that are being bypassed.
Ordr offers superior ransomware protection across the kill chain starting with comprehensive visibility into devices and risks (including complete details about devices, with granular insights—such as make, model, serial number, and network location). Our solution is capable of illuminating network blind spots by monitoring for east-west lateral movement and identifying attacker exploit tools. Our machine learning engine can baseline communication patterns to recognize an attack in progress, such as C2 communications. Finally, automated policies allow security teams to take action rapidly.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
PagesTechnology
…the value of your existing investments. Cisco Ordr’s deep integrations across the Cisco portfolio adds visibility and insights needed to manage and secure the wide range of connected devices in…
- PARTNERS
- TECHNOLOGY
Enable Faster ROI With Ordr Technology Integration Partners
Ordr integrates with 180+ security, networking, infrastructure, IT, and clinical solutions to unify device details, enrich device context, and extend the value of your existing investments.

Aruba
With Ordr and HPE Aruba ClearPass Policy Manager (CPPM), organizations can quickly gain complete visibility into every connected device and deploy segmentation to proactively protect and reactively respond and mitigate threats. This includes Zero Trust policy enforcement and microsegmentation to isolate groups or individual devices from non-essential access while protecting them from attack and compromise on existing networking and security infrastructure
How it works
The integrated Ordr SCE and HPE Aruba CPPM solution makes it easy to get rich visibility for IoT and unmanaged devices and to simplify segmentation projects. The solution provides detailed classification and context for every connected device, automatically groups devices into CPPM policy groups for role-based access and facilitates software-defined segmentation to provide more precise controls for every IoT device in the network. By providing continuous, multi-level security monitoring of all device communications, Ordr SCE detects anomalous behavior and shares this information with ClearPass to implement network access control based on vulnerability, threat, and risk ratings. Ordr SCE also integrates with HPE Aruba CPPM to streamline the process of containing threats based on the organization’s access policy such as blocking unauthorized devices, quarantining them, or limiting their network access.
Benefits
- Automating IoT inventory discovery, classification, and categorization, and sharing detailed device context with ClearPass
- Providing rich analytics about the behavior of all devices that guides segmentation design, streamlines the segmentation implementation, and audits the result to assure accuracy and effectiveness
- Quickly contain threats and protect at-risk devices
- Accelerating ClearPass deployments with powerful yet easy-to-use tools that provide accurate device information and automate steps that are traditionally error-prone and labor intensive
CrowdStrike
Integration between Ordr and CrowdStrike ensures the security of all managed and unmanaged devices with comprehensive device visibility, detailed vulnerability insights, an understanding of risk, and the ability to enforce policy to mitigate active threats and improve security across all connected devices
How it works
Ordr analyzes network flow data to automatically discover and classify every connected device, profile behavior, and identify active threats. Security telemetry from the CrowdStrike Falcon platform, is shared with Ordr to enhance device insights, and provide a centralized, deep understanding of each device and its associated risk. Ordr uses multiple factors to calculate risk for each device based on business context, asset criticality, vulnerabilities, and overall threat details. With additional device data from the Falcon platform, Ordr provides a highly accurate risk score for each device. By continuously synchronizing device risk scores with CrowdStrike’s enriched security data, Ordr enables teams with an up-to-date view of risk to help them focus on the most critical devices.

Benefits
Gain complete device visibility
- See into all devices – agentless and agent-based
- Track both online and offline devices continuously
- Identify unmanaged devices without CrowdStrike agent for compliance
Minimize risk with better insights
- Improve Ordr risk score accuracy with supplemental event data from CrowdStrike
Remediate faster
- Improve threat detection and incident response time with a combination of Ordr endpoint flow & CrowdStrike process data
- Block/quarantine/segment managed endpoints in Ordr for rapid remediation via the network
Fortinet
Fortinet and Ordr have partnered to deliver an industry-leading IoT and unmanaged device security solution by integrating FortiManager, FortiGate and FortiNAC with Ordr Systems Control Engine (SCE)
How it works
Automated Visibility and Security of All Connected Devices
Ordr SCE automatically creates a complete asset inventory, identifies and prioritizes asset risk, and tracks and risk-rates asset communications patterns. Ordr transmits this critical security context to Fortinet FortiGate, FortiManager, and FortiNAC, allowing administrators to create and apply firewall and NAC policies using business-relevant groups, classifications, and device names, while understanding the full risk profile and impact of each change. Ordr further reduces administrative costs by automatically updating asset groupings as devices join and leave the network, as well as by creating and transmitting security policies directly to FortiGate and FortiManager for enforcement.

Benefits
With the integration, joint customers can now:
- Discover and inventory every connected network asset, including the massive volume of IoT and unmanaged devices, and make available across the Fortinet Security Fabric, from endpoint to edge, through FortiNAC, FortiManager, and FortiGate
- Establish comprehensive security controls that restrict IoT devices to known-good network behaviors
- Manage firewall and NAC policies using business-relevant context such as device type, manufacturer, location, risk, and function rather than IP addresses
- Automate updates of firewall groups and address info to ensure consistent policy enforcement regardless of device location, VLAN, or IP assignment, thus drastically reducing operational costs and downtime
- Protect critical devices with automated, zone-based segmentation and microsegmentation within zones
SentinelOne
Ordr integration with SentinelOne enables collection of managed device data, vulnerabilities and threat insights for comprehensive device visibility and a better understanding of risk.
How It Works
Ordr discovers and secures every connected device—from traditional IT to new or vulnerable IoT, IoMT, and OT devices. With the SentinelOne integration, Ordr collects managed device data, vulnerabilities, and threat insights from the Singularity Platform delivering comprehensive device visibility, a better understanding of risk, and the ability to enforce policy to mitigate active threats and improve security across all connected devices.

Benefits
Gain Complete Device Visibility
- See granular details for all agentless and agent-based devices.
- Track both online and offline devices continuously.
- Identify unmanaged devices without the SentinelOne agent to meet compliance requirements.
Minimize Risk with Extended Insights
- Improve risk score accuracy with supplemental event data from SentinelOne.
Remediate Faster
- Improve threat detection and incident response with combined Ordr endpoint flow and SentinelOne process data.
- Block/quarantine/segment managed endpoints in Ordr for rapid remediation via the network.
Gigamon
A basic tenet of network security and regulatory compliance is that “You cannot secure what you cannot see.” Gigamon and Ordr have teamed to deliver unsurpassed visibility and control into every thing connected to your network.
How It Works
The Gigamon Visibility and Analytics Fabric (VAF) optimizes data collection of all north-south and east-west traffic across branch, campus, data center and cloud. Collected data is delivered to Ordr for analysis to ensure comprehensive device classification and visibility into all device communications. Integration with Gigamon VAF also eliminates concerns of SPAN security and potential impact to network infrastructure with “yet another SPAN port or session.”
By integrating with Gigamon VAF, customers can significantly reduce the number of Ordr sensors required to comprehensively discover and monitor every network-connected device, simplifying your network and security monitoring architecture.

Benefits
- Real-time asset inventory – Ordr continuously analyzes device traffic sent from Gigamon to passively discover an automatically classify every device connected to the network to help you maintain an up-to-date and accurate inventory.
- Connected device risk – using the traffic captured and optimized by Gigamon Hawk, Ordr calculates device risk scores and uncovers connected devices with risk such as outdated operating systems, unpatched software, weak passwords, and manufacturer recalls. Ordr also maps and baselines device communications to identify risk and stop attacks.
- Accelerate Zero Trust – working together, Gigamon and Ordr can map and baseline all IT, IoT and other device communications. Ordr can then dynamically create Zero Trust policies to simplify and accelerate NAC and segmentation projects. These policies can be enforced with popular security and network devices to integrate with existing infrastructure tools.
Palo Alto Networks
Rapid7
Ordr works with Rapid7 to seamlessly discover all connected assets including IoT, IoMT, and OT devices. The joint solution enables Rapid7 to perform the right scan at the right time regardless of the device type, location, criticality or role within the organization. Many vulnerable IoT/OT devices discovered by Rapid7 cannot be patched or updated. Ordr automates the application of compensating controls to safeguard these devices by sending protection policies directly to firewalls, switches, wireless, or NAC systems. Similarly, infected devices can be quickly isolated through existing network and security devices.
How It Works
The integration with Ordr and Rapid7 InsightVM provide ongoing bi-directional synchronization for managing vulnerabilities with rich device context. Ordr discovers every connected device, profiles device behaviors and risks, and automates remediation responses. Rapid7 InsightVM provides visibility into the vulnerabilities and clarity on how those vulnerabilities translate into business risk. Combining Ordr’s unique device intelligence with Rapid7’s advanced vulnerability intelligence provides organizations with the ultimate solution to efficiently manage risks while reducing service disruption and time to remediate.

Benefits
- Comprehensive Coverage – Ordr’s identification and classification of lightweight, agentless devices allows administrators to quickly exclude specific IoT devices or categories from active Rapid7 scans, opening network segments to vulnerability scanning that had previously been excluded.
- Optimized Scanning – Using Ordr’s detailed insight into device types, scan sensitivity, and their critical role within the organization, Rapid7 scans can be tailored to each device.
- Proactive Protection – Rather than blocking or quarantining critical IoT devices after infection, Ordr’s segmentation policies create barriers that protect vulnerable devices while still enabling essential services.
- Smart Scheduling – Ordr tracks utilization patterns for critical devices, allowing administrators to schedule vulnerability scans for times when devices are not in use, minimizing disruption and operational risk.
Splunk
Ordr integration with Splunk allows you to leverage Ordr’s rich device data to create alerts, reports, and custom analyses. Ordr transmits security alerts, device information, and other critical information. Splunk ingests the feed for better event management.
VMware
Ordr leverages the vSphere API, which provides access to server management, virtual machine provisioning, monitoring, and more. Ordr collects datacenter asset details including the servers (hosts), individual virtual machines (guests), operating systems, shared compute resources (CPU, memory, disk), status, and compatibility.
The extended visibility to VMware workloads running in public, private, and hybrid cloud environments delivers a ‘whole hospital’ or ‘whole enterprise’ approach to security ensuring that no device or connection remains unknown.

Microsoft
Ordr integrates with multiple Microsoft solutions to enhance device context and improve risk insights to keep your organization secure.
Ready to Get Started?
-
 BlogNAME:WRECK Unlikely An Initial Compromise
BlogNAME:WRECK Unlikely An Initial Compromise…security researchers at JSOF and Forescout. This research is arguably an extension of the previous Ripple20 and AMNESIA:33 research as much like Ripple20 the NAME:WRECK vulnerabilities are found in commonly…
Security Bulletin
NAME:WRECK Unlikely An Initial Compromise
But Here is What You Should Know
6Min ReadBy Jeff Horne

NAME:WRECK is the short name for a collection of nine DNS based vulnerabilities discovered by the security researchers at JSOF and Forescout. This research is arguably an extension of the previous Ripple20 and AMNESIA:33 research as much like Ripple20 the NAME:WRECK vulnerabilities are found in commonly used TCP/IP stacks utilized by potentially millions of IoT devices. Several DNS vulnerabilities were discovered in the previous Ripple20 and AMNESIA:33 research with the vulnerable IP stacks being: Treck TCP/IP, uIP, PicoTCP, FreeBSD, IPNet, NetX and Nucleus NET, however these newly reported Name:Wreck vulnerabilities are inFreeBSD, IPNet, Nucleus NET, and NetX. TheTrech, uIP, PicoTCP, vulnerabilities were disclosed as part of the Ripple20 and Amnesia:33 research papers.
What are TCP/IP stacks?
TCP/IP stacks are common network libraries that allow devices with limited hardware resources to communicate over the network. These device focused TCP/IP stacks are usually found in IoT devices, which typically lack the resources to run the more demanding types of software that are common on PCs or servers. These vulnerable network libraries consequently are in widespread use, and likely places millions of devices at risk. Those devices represent a broad category of IoT use cases, from Industrial Control Systems (ICS), to healthcare equipment and beyond.
What are the effects of NAME:WRECK?
The most serious NAME:WRECK vulnerabilities disclosed are the remote-code execution attacks, in which threat actors take control of an affected device in order to harvest private data from the device or run malicious software on it and gain access to the network its connected to. That being said, exploitation of these vulnerabilities are made more difficult by the fact that it would require a malicious actor to either take control of a DNS server utilized by a vulnerable device or utilize a man-in-the-middle (MITM) style attack where communication to a legitimate DNS server is intercepted and manipulated with malicious intent. This exploitation difficulty does not change the fact that these TCP/IP stacks are vulnerable, but given the complexities of compromising a DNS server or setting up a MITM attack it does lessen the probability of these vulnerabilities being utilized by attackers.
The following table displays a number of common vulnerabilities and exposures (CVE) that correspond to specific types of attacks and risks that have emerged from NAME:WRECK.
CVEs that correspond to NAME:WRECK
CVE ID Stack Description Affected Feature Potential Impact CVSSv3.1 Score 2020-7461 FreeBSD In FreeBSD 12.1-STABLE before r365010, 11.4-STABLE before r365011, 12.1-RELEASE before p9, 11.4-RELEASE before p3, and 11.3-RELEASE before p13, dhclient(8) fails to handle certain malformed input related to handling of DHCP option 119 resulting a heap overflow. The heap overflow could in principle be exploited to achieve remote code execution. The affected process runs with reduced privileges in a Capsicum sandbox, limiting the immediate impact of an exploit. Message Compression RCE 7.7 2016-20009 IPnet ** UNSUPPORTED WHEN ASSIGNED ** A DNS client stack-based buffer overflow in ipdnsc_decode_name() affects Wind River VxWorks 6.5 through 7. NOTE: This vulnerability only affects products that are no longer supported by the maintainer. Message Compression RCE 9.8 2020-15795 Nucleus NET The DNS domain name label parsing functionality does not properly validate the names in DNS responses. The parsing of malformed responses could result in a write past the end of an allocated structure. An attacker with a privileged position in the network could leverage this vulnerability to execute code in the context of the current process or cause a denial-of-service condition. Domain name label parsing RCE 8.1 2020-27009 Nucleus NET The DNS domain name record decompression functionality does not properly validate the pointer offset values. The parsing of malformed responses could result in a write past the end of an allocated structure. An attacker with a privileged position in the network could leverage this vulnerability to execute code in the context of the current process or cause a denial-of-service condition. Message Compression RCE 8.1 2020-27736 Nucleus NET The DNS domain name label parsing functionality does not properly validate the name in DNS responses. The parsing of malformed responses could result in a read past the end of an allocated structure. An attacker with a privileged position in the network could leverage this vulnerability to cause a denial-of-service condition. Domain name label parsing DoS 6.5 2020-27737 Nucleus NET The DNS response parsing functionality does not properly validate various length and counts of the records. The parsing of malformed responses could result in a read past the end of an allocated structure. An attacker with a privileged position in the network could leverage this vulnerability to cause a denial-of-service condition. Domain name label parsing DoS 6.5 2020-27738 Nucleus NET The DNS domain name record decompression functionality does not properly validate the pointer offset values. The parsing of malformed responses could result in a read access past the end of an allocated structure. An attacker with a privileged position in the network could leverage this vulnerability cause a denial-of-service condition. Message Compression DoS 6.5 2021-25677 Nucleus NET The DNS client does not properly randomize DNS transaction ID (TXID) and UDP port numbers, allowing attackers to perform DNS cache poisoning/spoofing attacks. Transaction ID DNS cache poisoning 5.3 Yet to be Assigned NetX In the DNS resolver component, functions do not check that the compression pointer does not equal the same offset currently being parsed, which could lead to an infinite loop. In the function. The pointer can also point forward and there is no out-of–bounds check on the packet buffer. Message Compression DoS 6.5 The effects of NAME:WRECK could include; stealing data or allowing a malicious actor to gain access to a network that a IoT device running a vulnerable TCP/IP stack is connected to through the RCE vulnerabilities. Or attackers use NAME:WRECK disclosed DoS vulnerabilities they could use it to disrupt operations through effectively disabling vulnerable IoT devices which could lead to downtime and significant financial loss. The list of potential attack scenarios could go on. The takeaway is that NAME:WRECK affects a large amount of devices in the IoT ecosystem.
Identifying devices vulnerable to NAME:WRECK
Currently the Ordr engineering team is working on functionality within our active scanning feature to utilize Internet Control Message Protocol (ICMP) “pings” to be able to identify IoT devices utilizing these vulnerable TCP/IP stacks. We plan to quickly have this feature included and rolled out to all Ordr customers this week.
Unfortunately accurately identifying IoT devices utilizing these vulnerable TCP/IP stacks is extremely difficult to do by passively listening to the network alone. It may be possible to detect some of these vulnerable TCP/IP stacks by listening to certain events like DHCP handshakes which include option data in a specific order, which could be used to identify vulnerable TCP/IP stacks DHCP implementation, but that would require IoT devices to be setup to use DHCP or some special configuration and circumstances that could lead to misdetection. Therefore, active scanning devices for vulnerable TCP/IP stacks is the preferred method of accurate detection.
However, for critical devices in regulated industries like healthcare and manufacturing, the active scanning technique is not a preferred method so as to not interfere with their mission critical operations. Ordr has passive scanning methods to accurately identify these devices and could create exclusion lists if the customer chooses to apply active scanning methods on customer class IoT devices to identify these vulnerabilities.
How to detect NAME:WRECK
Currently there are no known exploits for the NAME:WRECK vulnerabilities. The Ordr security team is actively monitoring the security communities for any proof-of-concept (PoC) exploits, or malicious actors that maybe creating exploits for these vulnerabilities. If that happens the Ordr security team will release network detection signatures for the known PoC or malicious NAME:WRECK exploits.
How to protect vulnerable devices from NAME:WRECK
Although identifying devices that are impacted by NAME:WRECK and patching them is an obvious step for responding to the NAME:WRECK vulnerabilities, organizations must take broader steps to ensure that their networks are hardened against threats like NAME:WRECK. That includes embracing the principles of Zero Trust security to help ensure that your network will be resilient against undiscovered vulnerabilities, regardless of which form they take.
When applying the Zero Trust concept to devices, it means that networks are configured in such a way that, whenever a new device appears on a network, or an existing device’s configuration changes, the device has no access to the network or the hosted resources until a security administrator has verified that the device should be granted access.
In addition, network administrators should adhere to several other best practices associated with Zero Trust:
- Do not rely on firewalls or private IP addresses to establish which devices are “safe.” Instead, identify each device that exists on a network and ensure that it can be trusted before you grant it access to network resources.
- Implement least-privilege access. Grant devices only the minimal access privileges they need to operate.
- Use Multi-Factor Authentication (MFA). MFA is a security enhancement that requires a user to present two or more pieces of evidence when logging in to an account.
- Implement microsegmentation. Grant access privileges to each device on a highly granular basis, rather than assigning broad access rights. Policies are tailored to the individual needs of each device on the network.
Proactive protection of IoT devices with Ordr
The NAME:WRECK vulnerabilities highlight the risk of having IoT and unmanaged devices, even when they run software that has been used and trusted for decades – proving the need again for proactive protection and deep visibility.
Organizations globally, use Ordr to protect their network and devices from vulnerabilities like NAME:WRECK by discovering all network-connected devices, identifying vulnerable assets impacted by NAME:WRECK and other CVEs, detecting and flagging anomalous behavior using a built-in intrusion detection engine, and then using these device insights to proactively protect devices from vulnerabilities by dynamically generating policies and enforcing them on next-generation firewalls or NAC solutions.
Jeff Horne
Jeff Horne is currently the CSO at Ordr where he is responsible for security direction both within Ordr products and internal security. Prior to Ordr Jeff was the VP of Information Security for Optiv where he was responsible for all Security Operations, Governance Risk and Compliance, Endpoint, Internal Incident Response, Physical Security, and Employee Security Awareness groups. Before Optiv Jeff was the Senior Director of Information Security for SpaceX where he was responsible for the overall security strategy of SpaceX and managing the Information Security, Compliance (ITAR), Security Operations, and Physical Security groups. Previous to SpaceX Jeff was the Vice President of R&D and Chief Architect for Accuvant LABS where he managed teams of researchers and consultants specializing in reverse engineering, malicious code, incident response, breach analysis, and vulnerability assessment. Prior to Accuvant Jeff was the Director of Threat Research at Webroot Software where he led several teams of malware researchers, reverse engineers, and a development organization specializing in creating anti-malware functionality and detection signatures for all Webroot products. Jeff began his career as a Vulnerability Researcher at Internet Security Systems where he was responsible for vulnerability discovery, exploit creation, IDS evasion research, and behavioral detection of malware. Jeff is well known for his insight in interviews for numerous news channels and publications, speaking roles at various security conferences, as well as authoring several vulnerability disclosures and patents.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogThe Impact of Digital Transformation on the Security of Connected Devices
BlogThe Impact of Digital Transformation on the Security of Connected Devices…of connected devices expands—including the Internet of Things (IoT), Internet of Medical Things (IoMT), operational technologies (OT), mobile, and other devices—those deployments reflect the evolution of the technology. Assets that…
Integration
The Impact of Digital Transformation on the Security of Connected Devices
6Min Read
By Pandian Gnanaprakasam

The rapid proliferation of connected devices is expanding the enterprise’s attack surface and security risk profile. Ordr co-founder and CPO Pandian Gnanaprakasam addresses the impacts digital transformation has on connected device security. Today’s tech-dependent enterprises are no strangers to change. Our customers’ experiences demonstrate that familiarity daily. Whether they operate in healthcare, financial services, manufacturing, education, or government, they must contend with a constantly evolving infrastructure within their organizations, and constantly evolving threats from the outside. On top of that are the regulations and evolving business standards and practices that influence day-to-day operations.
Embracing digital transformation for all its benefits means buckling in for a bumpy ride—bumpier for some industries than others. Digital transformation expands an organization’s capabilities and opportunities, but it takes effort. In healthcare, for example, I recently stumbled on an interesting digital transformation report stating that only 16% of healthcare providers are in the “win zone,” meeting their transformation goals and driving sustainable change. The average across other industries is over 30%. That figure may be discouraging, but it is absolutely understandable, and organizations in healthcare as well as other industries can learn a lot from the experiences of their peers.
High Risks, Big Rewards
Using technology to improve patient care and operations sounds simple, but it is a complex endeavor that takes herculean effort. The pandemic briefly diverted attention away from long-term planning, but most health delivery organizations (HDOs) and other enterprises are back to addressing their plans and priorities. They are beginning to switch back from being reactive to a proactive mode. And with good reason.
Although high stakes, high costs, and risk aversion have discouraged many in the healthcare industry and beyond from fully embracing digital transformation, the rewards are too great to ignore. And the threats, expectations and competition all organizations face are not standing still. Done well, digital transformation delivers benefits that outweigh the risks and so, for those that have been reluctant to act, the time to embrace digital transformation is now.
What’s Fueling this New Wave of Transformation?
Over the years, every organization I have worked with—no matter how big or small—boils down their core priorities to three essential goals:
- Protecting people and the network
- Preserving service availability
- Improving operational efficiency
Those goals never change, even when the tools and strategies for achieving them do. And what’s more, they are transferable to other contexts as well: keeping manufacturing equipment operational and staff safe on the shop floor, preserving service availability for financial transactions, maintaining the operational efficiency of constituent services, etc. Consistent with these goals, here are some key initiatives and capabilities that are driving this new wave of transformation and pushing the boundaries of operational potential.
- Remote workforce support (i.e., work from home);
- Remote facility, branch, and clinic operations;
- Contractor and equipment maintenance support and outsourcing;
- Data center transformation and migration to hybrid cloud;
- Digital supply chain enablement; and,
- Mergers and acquisitions.
These use cases show how, more and more, connected devices are integral to fulfilling an organization’s mission. And as the inventory of connected devices expands—including the Internet of Things (IoT), Internet of Medical Things (IoMT), operational technologies (OT), mobile, and other devices—those deployments reflect the evolution of the technology. Assets that were once under tight control, on-premises and behind the firewall, are now expanding and connecting beyond traditional boundaries, across multiple network dimensions, and outside of the view and control of IT.
Here are some examples:
- Access from Any Device – IT, IoT, IoMT, OT, IoXT.
- Access from Anywhere – remote sites, remote workers, telemedicine.
- Deployed Anywhere – private and public cloud, virtualized data centers.
- Modern Apps/Mobile Apps – XaaS, training, collaboration, any device-anywhere-any deployment support.
- Ecosystem – third party apps, supply chain access, mergers and acquisitions.
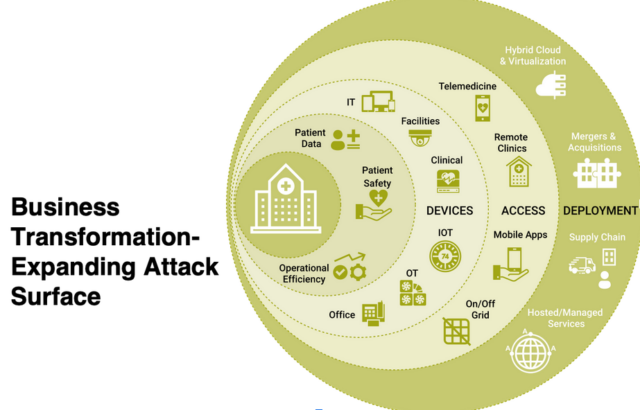
What Keeps the CXOs Up at Night?
IT leaders tasked with driving new digital transformation initiatives understand that success goes well beyond merely integrating new technologies and getting them up and running. Enjoying the multitude of benefits that can follow the completion of a technology refresh comes with many elements contributing to the pucker factor that keeps a CXO awake at night. An expanded and expanding attack surface is at the heart of this unease. Acknowledging that fact, and the factors that play into those concerns, is the first step in planning for and addressing them during the transformation process, rather than promising yourself that you’ll “get to it eventually.” Some pucker factors are reflected in several troubling trends.
Surge in Ransomware Attacks
Ransomware attacks are now more frequent, sophisticated, and severe than ever—and getting worse. Attackers know that many organizations will pay huge ransoms because costs associated with downtime and operational disruption may be even higher than what attackers demand. In healthcare, disruptions caused by ransomware can have life and death consequences.
Prevention is the best way to deal with the ransomware threat, but old school methods simply don’t work. Prevention demands accurate and timely detection, and response automation that can block an attack from progressing to its target destination. You need a way to detect ransomware early, before it has encrypted your organization’s files, because then it’s too late to take effective action.
State-Sponsored Attacks
Adversarial nation states have become adept at using the ambiguity of cyberwarfare to launch attacks on critical infrastructure and economic targets, as well as organizations that hold valuable intellectual property. The tools and methods developed for these campaigns are rarely confined to a limited set of organizations either, as sowing chaos is part of the strategy.
For example, the U.S. Cybersecurity and Infrastructure Security Agency (CISA), along with the FBI and Treasury Department issued a joint advisory about North Korean Maui ransomware targeting the healthcare industry. Similarly, Russian threat actors have been hard at work compromising connected devices and using them as a platform for attacks, including data exfiltration after establishing communications with command-and-control servers in Russia.
Digital Supply Chain Security
Digital supply chains that allow for remote and automated service between organizations have been a boon for operational efficiency—and for threat actors able to compromise those connections for their own ends. The SolarWinds Orion attack targeting U.S. federal agencies and commercial enterprises illustrated how damaging supply chain attacks can be.
Vulnerable SolarWinds servers sitting inside agency and corporate networks, operating with privileged access to IT systems, proved to be a gold mine for hackers to exploit and get whatever data they need, including high level state and military secrets.
Shadow IoT
One big security challenge faced by enterprises today is the presence of connected devices on their networks operating outside the view of IT security and operations. Known as “shadow IoT,” these devices epitomize the mantra you can’t protect what you can’t see. A recent Five Fifty report by McKinsey highlights the risk of the proliferation of devices connecting to the network as shadow IoT (such as the infamous hack of a casino using a connected aquarium thermometer as the vector of attack) and lack of readiness for most organizations.
Often these systems operate with outdated OSes, are unpatched, and unmanaged. Without proper onboarding—or a security platform able to detect, identify, profile, and monitor any device that connects to the network—any organization with shadow IoT operating within its IT estate is at risk of an attack.
How Ordr Helps Enable Secure Digital Transformation
Ordr’s mantra from the beginning has been to enable our customers to SEE, KNOW, and SECURE every device that is connected to their organization. To do this, we establish the most comprehensive and accurate single source of connected device truth in the Ordr Data Lake for each of our customers. This starts with automatically discovering and accurately classifying every connected device because you can’t secure what you can’t see.
From this foundation of visibility Ordr provides a complete view of the connected device attack surface including how devices are connected and communicating, which devices are vulnerable, and the unique risk each device represents in the environment.
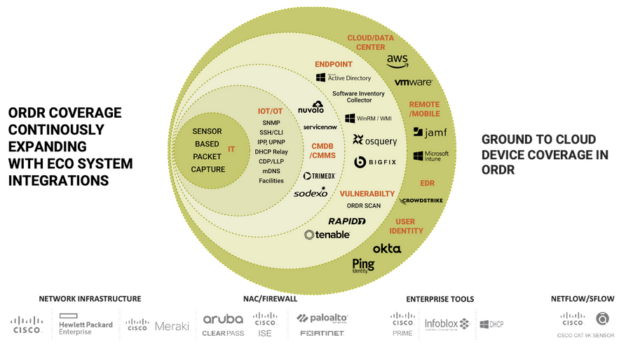
Integrations across the security, networking, and IT ecosystem are integral to the Ordr solution. These integrations enhance the already rich view Ordr has of connected devices by centralizing additional data points and device details. A good example of this are the recent integrations with Mobile Device Management (MDM) and Endpoint Detection and Response (EDR) platforms in the recent Ordr 8.2 release.
Integrations also enable Ordr to enrich the tools and workflows used every day and improve how teams manage and secure devices. An example here is the recent integration with the ServiceNow Service Graph Connector to help customers ensure the data in their CMDB is complete, up to date, and accurate. Another example is how Ordr device insights are used to optimize vulnerability scanning with Qualys.
Integrations also help teams take action to address vulnerabilities, respond to active threats, proactively improve protections, and ultimately reduce risk. Ordr automates the creation of security policies and enforces those policies by integrating with a customer’s existing security and network infrastructure. With this approach Ordr customers are able to quickly block attacks, quarantine compromises devices, segment vulnerable devices, and accelerate Zero Trust projects to proactively improve security.
We continue to drive innovations across the Ordr platform and expand with integrations across the security, networking, and IT ecosystem to provide our customers with a single source of truth for all their connected devices. Reach out for a demo and to learn how Ordr can help you SEE, KNOW, and SECURE, all your connected devices.
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?