Search Results:
”Quiz 2024 SAP C-ARSOR-2308: Marvelous SAP Certified Application Associate - SAP Ariba Sourcing Valid Dumps Book 🐮 Open ▷ www.pdfvce.com ◁ and search for ➥ C-ARSOR-2308 🡄 to download exam materials for free 🏑C-ARSOR-2308 Customizable Exam Mode”
-
 BlogUK Bill Signals Growing Awareness of IoT Security Risks
BlogUK Bill Signals Growing Awareness of IoT Security Risks…Sonos and Alexas, Kegerators, and many more unmanaged, consumer devices connected to corporate networks and healthcare environments—often for legitimate purposes and operations. Alexa devices, for instance, are being used as…
Risk Management
UK Bill Signals Growing Awareness of IoT Security Risks
3Min Read
By Danelle Au

A new UK cybersecurity law, the Secure Equipment Act of 2021, signals a growing awareness of the risks posed by IoT and other devices to enterprises. Learn what’s in the Act, what it means for cybersecurity preparedness, and how Ordr helps UK organizations comply with the new law. Awareness and concern over security implications associated with the flood of connected devices hitting the market is growing worldwide, and governments are taking notice. Here in the U.S., it started after it was discovered that internet-connected security cameras made in China, and in common use at Department of Defense facilities, were sending data back to their manufacturers. That prompted Congress to take targeted action prohibiting the purchase of communications gear made in China. The Secure Equipment Act of 2021 was signed into law on November 11, 2021.
But unsecure IoT and Internet-connected devices aren’t a problem limited to products made overseas. The journal EE Times recently reported that the security of connected devices is a major concern, and that manufacturers of such products are not reporting known issues and vulnerabilities with their goods.

New UK Bill Aims to Protect Consumers
Now, a new law being considered in the UK seems intended to protect consumers from the threats associated with unsecure connected devices. The Product Security and Telecommunications Infrastructure (PSTI) Bill is expected to become law sometime in 2022 and would establish new rules for Internet-connected devices made and marketed to consumers. PSTI would prohibit universal default passwords, ensure transparency related to known security flaws and what actions are being taken to mitigate them, and require the creation of better public reporting systems for discovered vulnerabilities.
Industry research, current events, and laws like PSTI show that personal and enterprise security have never been more vulnerable and intertwined. Vulnerabilities in Internet-connected devices don’t just put consumer data at risk, but also put corporate and government enterprise integrity in jeopardy. While PSTI is focused on the consumer-grade IoT market, we know many such devices make their way onto corporate and government networks.
Consumer Devices are Connecting to Commercial, Government Networks
Ordr’s own research has found devices like Pelotons, Sonos and Alexas, Kegerators, and many more unmanaged, consumer devices connected to corporate networks and healthcare environments—often for legitimate purposes and operations. Alexa devices, for instance, are being used as substitutes for the nurse call button, turning on lights and TVs with a voice command. Pelotons are being adopted for physical therapy. Imagine if those devices were to become compromised after connecting to a hospital’s IT infrastructure.
In Ordr’s view, legislation like PTSI should be expanded to cover an even broader array of devices, including those designed specifically for the enterprise as well as the consumer. Enterprise devices, and even medical devices, share many of the same vulnerabilities. Instead of merely requiring transparency, PTSI should mandate designing security into IoT products, ensuring secure protocols and technologies are used for key functions.
More Awareness, Security Needed
PTSI will help make consumer devices safer, but beyond safer passwords and vulnerability management, organizations still need to consider additional security best practices, such as:
- Maintaining a real-time inventory of devices: You can’t protect what you don’t know about. Security starts with real-time visibility of exactly what you have in your network and how those components are communicating in the network.
- Monitoring device behaviors for suspicious communications: Devices have deterministic functions. By using machine learning to baseline what behaviors are normal, you can then identify abnormal device behavior that may be an early indication of an attack.
- Tracking who is using your devices: By tracking and associating devices to users, you can identify compromised devices and also potential account misuse.
- Implementing Zero Trust segmentation for vulnerable devices that cannot be patched: Zero Trust segmentation policies can keep these devices in operations by allowing “normal communications” required for its function, while limiting exposure.
We believe PSTI is a good start, but much more remains to be done to make all internet-connected devices, and the people and organizations that use and rely on them, safe.
Danelle Au
Danelle Au has more than 20 years of experience bringing new technologies to market. Prior to Ordr, she was CMO at Blue Hexagon, a deep learning for malware protection company, and CMO at SafeBreach where she helped build the marketing organization and and define the Breach and Attack Simulation category. Previously, she led strategy and marketing at Adallom, a cloud security company acquired by Microsoft. She was also Director, Security Solutions at Palo Alto Networks, driving growth in critical IT initiatives like virtualization, network segmentation and mobility. Danelle was co-founder of a high-speed networking chipset startup, co-author of an IP Communications Book and holds 2 U.S. Patents. She has an MSEE from UC Berkeley
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 NewsOrdr Partners with Sodexo on Managed Cybersecurity Service
NewsOrdr Partners with Sodexo on Managed Cybersecurity Service…up-to-date inventory of all assets – and help locate devices for maintenance and patching. Actionable Risk Insights – Understand vulnerabilities and clinical risks to the healthcare environment, prioritize risks and…
Ordr Partners with Sodexo on Managed Cybersecurity Service
For Connected Devices in Healthcare
3Min ReadSanta Clara, CA – November 9th, 2022 – Ordr, the leader in connected device security, announced today that it has partnered with Sodexo Healthcare Technology Management to deliver a managed HTM and cybersecurity solution that combines the strengths of Ordr’s connected device security platform with Sodexo’s healthcare technology management services expertise. The combined solution — Sodexo Managed HTM Cybersecurity services built on the Ordr platform — delivers the people, process, and technology that healthcare technology management (HTM) teams need to mitigate risks and secure all connected healthcare devices.
In healthcare facilities, connected devices, including Internet of Medical Things (IoMT), have transformed care delivery and are used every day by providers and staff to deliver high-quality, efficient, life-saving medical care. However, while providers depend on the ever-increasing number of connected devices to deliver care, these devices create challenges and complexity for the HTM and IT users responsible for operating and securing them.
At scale, it can be difficult to accurately identify and classify these devices, understand their specific vulnerabilities and risks, determine whether they are available for maintenance, or to locate them for patching. Without strong security protections, unprotected devices can provide an opening for attackers to breach a system or spread ransomware. Addressing security and compliance is especially challenging because these devices often run outdated operating systems and because FDA or manufacturer guidelines may preclude updates.
“Visibility and security of medical devices is critical for healthcare organizations. HTM users need to be able to discover, profile and manage risks associated with these devices. With attacks such as ransomware increasing, it is important to be able to prioritize issues that have the highest impact when it comes to mitigating risks,” said Jim Hyman, CEO of Ordr. “The combination of the Ordr technology with Sodexo’s expertise and deep knowledge of the healthcare environment, will enable HTM teams to securely manage their connected medical devices and improve operational efficiencies.”
The Ordr platform, with successful deployments across hundreds of leading healthcare facilities, can discover and secure everything connected – from traditional servers, workstations, and PCs, to IoT, IoMT, and OT devices. Ordr Clinical Defender is optimized for HTM teams to automate the discovery and inventory of medical devices, accelerate day-to-day tasks, identify and prioritize medical device vulnerabilities, and drive operational efficiencies with device utilization insights.
“Successfully managing today’s expansive healthcare networks requires best-in-class technology that delivers real-time device, utilization and risk insights along with guidance on how to optimize security and performance,” added JT Surgener, Senior Vice President, Technical Services, Sodexo Healthcare. “Through the Ordr and Sodexo managed services offering, organizations will gain access to a powerful, yet easy-to-use healthcare device security platform – along with leading HTM and cybersecurity services, that will help them drive to greater efficiencies and security.”
Sodexo Healthcare Technology Management (HTM) services are tailored to specific hospitals or healthcare systems. Sodexo’s services help optimize medical equipment inventory, advise on equipment replacement and purchases, and provide on-site maintenance and repair.
Key benefits of the Sodexo’s Managed HTM Cybersecurity Solution include:
- Strategic Insights, Guidance, And Expertise – Sodexo’s highly skilled and motivated technical team integrates with local healthcare teams to solve problems, provide solutions, and continually find innovative ways to maximize assets to ensure smooth and effective patient care.
- Best-In-Class Tailored Solution – The Sodexo solution combines decades of HTM service delivery expertise with Ordr’s leading connected device security platform. The combined service helps healthcare providers of all sizes drive performance, efficiency, and security.
- Comprehensive Visibility – Discover and profile every connected device in an environment, with granular details that help maintain an accurate, up-to-date inventory of all assets – and help locate devices for maintenance and patching.
- Actionable Risk Insights – Understand vulnerabilities and clinical risks to the healthcare environment, prioritize risks and actions, and continuously monitor for threats.
- Improved Cyber Response – Improve incident response to stop active attacks, while accelerating efforts to improve overall security posture. Tailored recommendations and dynamically generated policies support segmentation and zero trust efforts.
Sodexo’s Managed HTM Cybersecurity Solution leveraging Ordr is available now. For more information on how you can gain insights and control over the connected devices on your healthcare network, contact Sodexo.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogKLAS Names Ordr Market Leader in Healthcare IoT Security
BlogKLAS Names Ordr Market Leader in Healthcare IoT Security…our journey and contributed to our release. “COVID-19 has forced healthcare organizations to double-down on prioritizing security while balancing other organizational priorities and needs. CIOs need to find ways to…
Company News
KLAS Names Ordr Market Leader in Healthcare IoT Security
2Min Read
By Danelle Au

Healthcare has been one of the key verticals for Ordr since our inception as CloudPost Networks. Over the last couple of years, we’ve helped many healthcare organizations address visibiity and security for their unmanaged and IoT devices. In turn, we’ve worked with our customers to evolve our solution and address new use cases.
As a result, we’re grateful and proud to have been named a market leader (with the highest market share) in the new KLAS Research report, Decision Insights: Healthcare IoT Security for the second year in a row. If you’re not familiar with KLAS Research, they are a healthcare IT data and insights company. One of the most unusual aspects of KLAS Research is that they actually interview real clients with questions such as “Are customers happy with a vendor’s products and with customer service?” “Do they have a positive impression of their vendor?” “Do they think their organization has benefited from adopting the vendor’s software?” KLAS is lauded in the industry for their accurate, honest and impartial research.
Market Leader for Second Straight Year
The KLAS Healthcare IoT Security Report defined the following as key capabilities for an IoT Security solution.
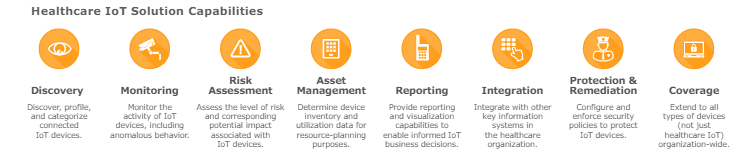
In addition, KLAS spoke to more than 51 customers on which vendors were being selected and why. They had this to say in their report, “ Ordr, who has contracted with some of the largest health systems, has continued to be one of the market leaders in terms of wins and considerations for the second straight year, resulting in their current leading market share.”
KLAS also noted that we were praised by customers for:
- The breadth and number of devices Ordr can detect;
- The highly granular visibility the solution provides;
- Ordr’s culture of “flexibility and willingness to partner;”
- Strong technology integrations that help drive value with the solution; and,
- High customer satisfaction.
We thank all healthcare organizations who participated in the KLAS interviews. We’re excited to continue our growth with our customers, helping to discover, profile and secure connected devices. Thank you to two of our customer advisory board members Skip Rollins and Jeff Vinson, who supported us throughout our journey and contributed to our release.
“COVID-19 has forced healthcare organizations to double-down on prioritizing security while balancing other organizational priorities and needs. CIOs need to find ways to support the business,” said Skip Rollins, CIO, Freeman Health. “Ordr is a tool we lean on not only for visibility and security of unmanaged and IoT devices, but for device utilization insights. Details about how often a device is being used helps us to optimize device allocation and support procurement decisions.”
“Most healthcare organizations don’t realize that a vending machine may be connected to the same network as a critical life-saving device like a ventilator,” said Jeffrey Vinson, CISO, Harris Health. “We have partnered with Ordr because the company provides the most comprehensive IoT security solution that goes beyond simple device inventory. Ordr discovers all connected devices, helps us identify risks and malicious behaviors in devices, and can automatically generate segmentation policies to secure high-risk devices.”
We are excited to continue our growth with our customers, helping to discover, profile and secure connected devices.
Danelle Au
Danelle Au has more than 20 years of experience bringing new technologies to market. Prior to Ordr, she was CMO at Blue Hexagon, a deep learning for malware protection company, and CMO at SafeBreach where she helped build the marketing organization and and define the Breach and Attack Simulation category. Previously, she led strategy and marketing at Adallom, a cloud security company acquired by Microsoft. She was also Director, Security Solutions at Palo Alto Networks, driving growth in critical IT initiatives like virtualization, network segmentation and mobility. Danelle was co-founder of a high-speed networking chipset startup, co-author of an IP Communications Book and holds 2 U.S. Patents. She has an MSEE from UC Berkeley
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogOrdr is Good Medicine for CISOs
BlogOrdr is Good Medicine for CISOs…were compiled well before former Uber CISO Joe Sullivan’s controversial conviction on charges he hindered a federal investigation into a data breach at the ride-sharing company. Given the range and…
General
Ordr is Good Medicine for CISOs
3Min Read
By Darrell Kesti

The challenges of cyber asset attack surface management (CAASM) and enterprise protection mean that stress and burnout are a major concern for chief information security officers (CISOs), according to a recent study by Heidrick & Struggles. Ordr simplifies CAASM and relieves the stress. Did you catch the recent news that stress and burnout are the primary concerns for most chief information security officers (CISOs) these days? That was the result of a recent study conducted by the executive search firm Heidrick & Struggles as reported by CNBC last month. The survey found stress (59%) and burnout (48%) were identified as the top two personal risks by 327 CISOs from around the globe. Those results were compiled well before former Uber CISO Joe Sullivan’s controversial conviction on charges he hindered a federal investigation into a data breach at the ride-sharing company. Given the range and passion of opinions other CISOs have expressed in response to that case, it’s likely that stress is on the rise.
Scapegoats and Sacrificial Lambs
It’s not that surprising to learn that CISOs are under stress. They are responsible for keeping networks and data safe from a relentless onslaught of attacks from threat actors, and from data breaches that are a result of simple human error. If you spend any amount of time talking with members of the CISO community, as I do, you’ll hear the common complaint that they must manage high expectations and low budgets. You’re also likely to hear a lot of gallows humor involving scapegoats and sacrificial lambs.
I’m sympathetic to a CISO’s plight. In Ordr’s corner of the cybersecurity world, we deal with connected devices of the sort that make up the Internet of things (IoT), Internet of medical things (IoMT), and operational technologies (OT) that are the backbone of industrial and critical infrastructure enterprises. In that world, the pace of change and growth is astounding; it’s impossible to keep up. Consider the following statistics:
- By 2025 there may be as many as 83 billion connected devices active in commercial networks by 2024 (Juniper Research).
- At that time there will be more than 150,000 devices connecting to networks every minute (IDC).
- The average hospital IT infrastructure includes more than 100,000 connected devices, including more than 15,000 IoMT devices dedicated to critical care, and between 10-15 IoMT devices per bed.
Those are big numbers, and they only represent the devices a CISO knows about. There may also be hundreds more unmanaged devices connecting to their networks, enlarging the enterprise’s attack surface, and increasing the chances of a data breach. That’s because you can’t protect what you can’t see. And when vending machines, smart assistants, aquariums, Kegerators, Teslas, Pelotons, and any number of other stranger things decide to make themselves at home on the network, stress rises along with risk.
Just What the Doctor Ordr’ed
Ordr is aware of these trends, and we have just what the doctor ordered to ease the burden that they cause on both the CISO’s enterprise and psyche. Our platform excels at looking across the network to locate and identify each device. Within minutes, Ordr discovers, locates, and automatically classifies all the device assets that are operating on your network, including devices you knew you had, devices you forgot you had, devices you thought you lost, and the ones that you weren’t expecting. In addition to complete devices discovery, Ordr’s feature set is designed to make a CISO’s job easier, including:
- Automated asset inventory synchronized with your CMMS or CMDB.
- Continuous risk assessment uncovering vulnerabilities and risky communications.
- Vulnerability management to help with remediation and mitigation tasks.
- Improved incident response with dynamically created policies to stop attacks.
- Accelerated Zero Trust with dynamically created policies for NAC and segmentation.
- Simplified compliance with detailed reports and documentation to help with auditors and assessments.
And because the Ordr Data Lake is already populated with detailed information on millions of individual device types, every device we find is automatically and accurately profiled, and its communications patterns baselined and monitored. That’s important because connected devices operate in narrow, deterministic ways. Any deviation from normal can be considered as an indicator of compromise, and when Ordr detects a threat, we arm your teams with contextual insights and policies so you can take the right action, quickly. That protects your network by preventing attacks, containing threats, and enabling operational resilience by isolating mission-critical devices that need to remain in service.
You can’t protect what you can’t see. And when vending machines, smart assistants, aquariums, Kegerators, Teslas, Pelotons, and any number of other stranger things decide to make themselves at home on the network, stress rises along with risk.
The CISO’s team also benefits from these features. The ability to automate asset inventory, locate devices easily, and generate security policies on any networking or security infrastructure reduces human errors and frees IT and security personnel to focus on more strategic tasks. This can help CISOs ensure higher job satisfaction, reduce stress, and increase retention for his or her team.
A CISO’s Peace of Mind
Whether you are protecting a hospital, industrial facility, financial services firm, or any other enterprise that relies on a vast constellation of connected devices, Ordr is good medicine. When Ordr is at work a CISO has a little more peace of mind, reducing the stress that comes with being an organization’s Cyber Incident Scapegoat Offering. If you want more information about the Ordr connected device security platform, or if you’d like a demo, reach out and let us know.
Darrell Kesti
Darrell is VP Sales at Ordr. He joined Ordr as one of the original Account Executives in October of 2018 to help launch the field organization. In his prior role as Ordr’s Director of Healthcare Sales, Darrell drove significant growth in healthcare sales and helped position Ordr as the leader in connected device security. Darrell has had over 20+ years of Sales Leadership, Account Management, and Field Engineering experience supporting customers and partners while with leading security and networking organizations – ForeScout Technologies, FireEye, Mandiant, F5 Networks, and Secure Computing Corporation. Darrell earned a Bachelor of Science in Electrical and Computer Engineering from the University of Minnesota, Duluth.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogThe Unique Security Challenges of Cyber-Physical Systems
BlogThe Unique Security Challenges of Cyber-Physical Systems…vulnerabilities, normal communications patterns, and other essential context that allows you to set policy. A Potent Combination for CPS Protection That combination of insight and capability supports automated responses whenever…
Risk Management
The Unique Security Challenges of Cyber-Physical Systems
Require New Security Tools
3Min Read
By Bryan Gillson

New tools are needed for cyber-physical systems (CPS) security. Ordr explores the tools and capabilities that are needed to address CPS security and how to manage the risks associated with connected devices like IT, IoT, and OT. Ordr’s See, Know, Secure Approach to Connected Device Security is Ideal for CPS Protection
As IT estates and their attack surfaces grow in complexity, cyber-physical systems (CPS) are getting more attention from cyber security professionals. Because organizations across all verticals are adopting CPS to run operations more efficiently, connected devices are becoming more and more abundant. Some reports predict the number of Internet of Things (IoT), Internet of Medical Things (IoMT), Industrial Internet of Things (IIoT) and other emerging specialized (XIoT) devices that populate sprawling corporate networks will exceed 24 billion by 2030. Those devices represent a critical interface between traditional IT and the hyper-connected sensors, controls, and other operational technologies (OT) comprising CPS these days.
Our own Chris Westphal blogged about cyber-physical systems recently, offering some background on what they are and identifying some of the security challenges associated with protecting them. A newly updated report by Gartner, 3 Initial Steps to Address Unsecure Cyber-Physical Systems, goes into more detail to help organizations struggling to understand their CPS infrastructure and establish a strategy to keep their CPS secure.
Threat Actors are Aggressive
The report makes it clear that threat actors are aggressively exploiting vulnerabilities inherent with CPS technologies and the threat to those organizations unprepared to defend them. In fact, Microsoft recently uncovered a “a sophisticated attack campaign” targeting IoT devices, while other new security research suggests malware targeting IoT devices has increased 700% since 2020.
As IT and OT converge, cybersecurity leaders need to identify their attack surface across both environments. Gartner’s report cites examples of attacks against organizations in healthcare, critical infrastructure, manufacturing, and public utilities illustrate the risks beyond cyber with potential impact to individuals, public safety and economic stability, and serve as a warning to organizations relying on traditional IT security approaches. The report’s author, Gartner analyst Kattell Thielemann, puts it this way:
“Business-led Internet of Things or converged OT-IT projects have largely underestimated or ignored security and safety risks. Security and risk management leaders must go beyond data security by embracing cyber-physical system security efforts, or they will soon be overwhelmed by new threats.”
Business-led Internet of Things or converged OT-IT projects have largely underestimated or ignored security and safety risks. Security and risk management leaders must go beyond data security by embracing cyber-physical system security efforts, or they will soon be overwhelmed by new threats.”
A Strategic CPS Security Foundation
That dire warning comes with the promise that, by taking the time to understand CPS infrastructure from a risk management perspective, CSOs, CISOs, and other security leaders can implement effective strategies for protecting those systems. Formulating a CPS security strategy starts by:
- Prioritizing discovery of all elements of the CPS environment;
- Anchoring security goals and policies based on insights derived from device data and industry-specific requirements like regulations and threat intelligence; and,
- Focusing on building maturity into the strategy based on an evolving Zero Trust approach.
Here at Ordr we call it a “See, Know, Secure” model for protecting connected devices, and the capabilities enabled by our platform dovetail well with the needs of organizations with CPS infrastructure. That’s because Ordr quickly discovers all CPS elements operating in the network, including those that were previously unknown or that connect and disconnect outside the control of IT management. This discovery happens in real-time, so there are never any blind spots.
Once discovered, we classify, map communications, analyze behavior, and assign a risk score to each device based on the data in the Ordr Data Lake—the industry’s most complete library of connected device intelligence. Our data lake is populated with millions of individual device profiles, including rich detail on each. We know their deterministic operational parameters, disclosed vulnerabilities, normal communications patterns, and other essential context that allows you to set policy.
A Potent Combination for CPS Protection
That combination of insight and capability supports automated responses whenever indicators of compromise are detected; and that means your network security gaps are identified and closed. Whether a CPS device is the vector, target, or in the path of an attack, Ordr can detect it and either stop it or help contain the spread.
The speed, complexity, and unique technical challenges endemic to cyber-physical systems operations means that legacy security tools and strategies are severely limited when applied to CPS infrastructure. Gartner recommends that CPS security “focus on safety, reliability, resilience, adaptability, and privacy.”
The Ordr platform is ideally suited to address these challenges. Learn about best practices to secure cyber physical systems to help you better grasp the complexities and establish a CPS security strategy that meets the needs specific to your organization.
Bryan Gillson
Bryan joined Ordr in November 2019 after spending six years as VP Strategic Alliances at Ionic Security. At Ionic, Bryan initiated and managed business relationships with system integrators such as Accenture, Deloitte, and PwC, and closed OEM partnerships with vendors in the CASB, virtualization, and data protection sectors. Previously, Bryan led product management and business operations for Symantec’s encryption products and information protection groups after integrating the acquisitions of both PGP Corporation and GuardianEdge. Prior to Symantec, Bryan led the business development team at PGP Corp. and was a VP in Merrill Lynch’s Technology Investment Banking group.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogSegmentation Done Right – Part 2: Seeking a Better Way
BlogSegmentation Done Right – Part 2: Seeking a Better Way…logical segments. Micro-segmentation divides networks down to the workload level and then defines specific security controls and policies for these specific segments and workloads. It’s a more granular and logical…
Security Strategy
Segmentation Done Right – Part 2: Seeking a Better Way
3Min Read
By Pandian Gnanaprakasam

Device segmentation is essential for protecting at-risk devices (and the networks they attach to) from cyberattack. Ordr gives you a comprehensive, step by step guide to implement connected asset segmentation for your enterprise security strategy. Segmentation Done Right – Part 2 of 3
Segmentation is a good thing, and there are many use cases for segmentation done the right way. What tools then do we implement to get started with segmentation, and are there some pitfalls to avoid? The idea is simple, but one doesn’t want to design cost and complexity into the equation from the start. A flexible yet granular segmentation system with ample room to grow is what you need.
The traditional way of doing segmentation was to use the perimeter firewall—one side was trusted and safe, and on the outside was the big bad world. With many intrusions, however, a small breach means the damage is difficult to contain. Take it a step further, and one can deploy multiple virtual networks, or VLANs, to further segment and create various “safety zones” inside the network, then leverage routers and Layer 3 switches to control access between the virtual segments.
Dynamic Applications vs. Traditional Methods
Using VLANs is pretty intuitive—place all things of a particular type into the same virtual segment. But VLANs are manually intensive—each new device must be manually categorized and assigned the correct VLAN. Each new group needs its own VLAN and a painful call to the IT desk to allocate a new VLAN across the enterprise, each with its own unique IP address space. And don’t forget the VLAN boundaries. ACL policies need to be consistently deployed at each of the routers and L3 switches to control the flow between VLANs, or else what was the reason for creating new VLANs in the first place?
Furthermore, the world of applications is dynamic, so boundaries can’t be so rigid. When one creates and deploys a new application using an Auto Scaling group, which contains a collection of Amazon EC2 instances, an IP address is dynamically assigned. Frequently this application will need to move around various network segments. If one applies a rigid approach to segmentation, there will be too many strict routing rules to navigate since traffic is only allowed when information is on a pre-defined list. Moving around is hampered, and a permissible list has to be updated continuously manually. In today’s environment, network ports are dynamic, DHCP is dynamic, applications are active, and we think segmentation should be flexible and smart.
Let us go back to the middle school example from last week. Students in their classrooms can further represent segmentation. Grades and different classrooms separate children, and each class has a teacher. Typically, (or in some cases hopefully) the children are expected not to interact with each other during lessons and only interact with the teacher. Likewise, when you have a class of IoT devices, rarely do these devices need to communicate or talk to each other. If anything, one MRI machine talking to another or sharing a snack should not happen.
So if this orderly communication between a teacher and student makes sense in a classroom or “segment,” then why do we lump similar devices such as cameras, X-Ray machines, or workstations together into their respective segment, VLAN or subnet with the notion that they are protected? These devices should talk to a central master and externally to get a patch once in a while, but not each other. If one device is compromised, there goes the notion of protection via segmentation. If junior in class catches the flu, other students in the same class are likely to get sick, too. Likewise, if a workstation is compromised and it’s in the same VLAN with other workstations, how does one contain the damage?
Traditional segmentation often places all sorts of devices of a general category into the same group/segment, and any infection of one will quickly spread to the rest. At Ordr, we segment smartly and take it further with micro-segmentation. We can group and segment things logically, and we can control the flow between the logical segments. Micro-segmentation divides networks down to the workload level and then defines specific security controls and policies for these specific segments and workloads. It’s a more granular and logical approach than physical segmentation via physical firewalls, making it easier for network and security administrators.
If a device becomes infected, we can contain the damage and not let it spill over, thus help you regulate and protect precious assets and information. Next week we will discuss segmentation automation and how one can generate clear policies using observed behavior. Be smart and control the flow between segments and do segmentation in an Ordr’ly way.
Read Segmentation Done Right – Part 3: Take Control.
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogDiscovery and Segmentation: Keys to IoT Strategy Success
BlogDiscovery and Segmentation: Keys to IoT Strategy Success…and to ensuring your IoT initiative does what you want it to do—with no unpleasant surprises. Ordr Core Ordr Core gives us the ability to open a customer’s eyes to…
Security Strategy
Discovery and Segmentation: Keys to IoT Strategy Success
3Min ReadBy Jason Malacko

Guest blog by Jason Malacko, Director Architecture – Security at Logicalis US
When you’re in the business of helping companies integrate and consume sophisticated technology, you learn that, behind all the questions related to how it works, there are two primary concerns: that it will be simple to use, and that it will deliver its promised value… fast.
At Logicalis we strive to make the complex simple. We recognize that our customers are too busy using technology and don’t want to worry about whether a service or application will be reliable or difficult. That’s why they hire us, after all. So, whether it’s a healthcare organization, manufacturer, state or local government agency, or whatever it is that your organization does, we approach every project as though we are architects of change for our customers, building a technology solution that doesn’t befuddle, but that inspires.
Internet of Things
Recently we’ve been using a lot of connected devices in the solutions we’re designing for our customers. The internet of things (IoT) includes a lot of wonderful tools that make operating a business more efficient and effective.
Think about a typical hospital, for example, and you get a sense of the ways IoT supports a mission of healing. Environmental controls keep temperatures where they need to be in every setting, and that air quality is always excellent. Building and security controls make sure people can get to where they need to go quickly, and that only authorized people are allowed in sensitive spaces; that video cameras keep a constant watch on the premises; and that lighting is on at the right level when it needs to be, and off when a space is vacant. There are devices that facilitate communications, IT operations, administrative duties. And, of course, there are a host of medical devices used to treat and monitor patients, provide therapy, and otherwise support medical staff as they care for the sick and injured.
All of these devices have important roles, but from a security and management perspective, they have to be treated very differently. Ordr has proven to be a valuable member of our partner network, supporting our top-down approach to IoT utilization in pursuit of this ideal.
When beginning a customer engagement, we’ve found that about ten percent of an organization’s devices are out of view of IT operations management. That means there are dozens or possibly hundreds of attack vectors somewhere in the network. It also helps to explain why only 26 percent of companies have launched an IoT initiative they consider to have been a success. That makes device discovery a critical first step in understanding, managing, and protecting the network, and to ensuring your IoT initiative does what you want it to do—with no unpleasant surprises.
Ordr Core
Ordr Core gives us the ability to open a customer’s eyes to the level of risk they didn’t realize they had, but it’s only the first step. Complete device discovery means we can begin the process of assessing risk, identifying device behavior, and categorizing each device’s purpose in the network. From there we can reconcile each device’s role, and implement policy automation to ensure proper device use as well as to implement a critical part of the IoT strategy: segmentation.
Device segmentation is an underappreciated aspect of IoT management and security. Done right, segmentation is about more than simply making sure certain categories of devices are on the right VLAN; it’s about aligning IoT use with security and business objectives. If all you’re doing to put segmentation into effect is grouping like assets—say, keeping medical devices, environmental controls, and facilities management equipment on their own VLANs—you may still be leaving your network vulnerable to attack and, once inside, allowing adversarial elements to quickly move laterally within the network.
Ordr Core excels as a tool that give our engineers the ability to work closely with our customers, show them their level of risk, and bring complex technical solutions with a reliance on IoT into alignment with their needs. When we’re able to do that, it gives our team and the customer confidence that our design will be simple to use, and that it will deliver its promised value… fast.
Want to experience Ordr in your network, request a free sensor here.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogUnderstanding IoT Adoption and Risks
BlogUnderstanding IoT Adoption and Risks…person in the U.S. Fast forward to 2020 and the IoT market has exploded. From connected cars and video cameras to smart virtual assistants and HVAC systems, the IoT market…

The first step to gaining the upper hand on cyberthreats is understanding IoT adoption trends and the security risks they pose. The second step? Acquiring the tools needed to discover, monitor, and protect your connected devices in real-time. In 2015, former Cisco research David Evans calculated how many devices were being added every second. At the time, an average of 127 new things were being connected to the Internet every second. 328 million things were being connected every month, approximately one for each person in the U.S.
Fast forward to 2020 and the IoT market has exploded. From connected cars and video cameras to smart virtual assistants and HVAC systems, the IoT market is now expected to grow to 31 billion connected devices by 2020 and 75 billion devices by 2025.
With so many devices proliferating, security and risk professionals need to be much more aware of the expansion of their attack surface. Each device represents a new attack vector for cyber attackers. The recent spate of vulnerabilities that impact IoT recently, from Ripple20 to SIGRed, demonstrates the importance of securing these devices.
But what types of risks should enterprises expect to find in their environment? How best should they protect themselves?
Today, we’re excited to release the inaugural Rise of the Machines: 2020 Enterprise Adoption and Risk Report. We examined more than 5 million unmanaged, IoT, and IoMT devices in Ordr customer deployments across a variety of verticals including healthcare, life sciences, retail and manufacturing, between June 2019 and June 2020. Ordr strongly believes in the importance of sharing this type of data with the global security communitiy to better understand IoT risks and secure their organization.
Among the report’s most interesting findings were the frequent discovery of consumer-grade shadow IoT devices on the network such as Amazon Alexas and Echos.
We love the perspective that Zeus Kerravala, founder and Principal Analyst at ZK Research provided, “In some of my recent research around enterprise IoT security I’ve found that more than 51% of IT teams are unaware of what types of devices are touching their network. But perhaps what is more disconcerting is that the other 49% often times find themselves guessing or using a ‘Frankenstein’d’ solution to provide visibility into their network security, which will almost always create security issues. Shadow IoT is becoming a real security challenge, as It’s not enough to have the visibility into what is touching your network, but you need a solution like Ordr’s that allows for you to resolve the issues in a scalable automated fashion.”
Highlights from Ordr deployments include the following:
- 15-19 percent of deployments had IoT devices running on legacy operating systems Windows 7 (or older). Since it is often not economical to take these critical systems out of service, these devices need to be properly segmented.
- 20 percent of deployments had PCI-DSS violations where IoT devices with credit card information were on the same subnet or VLAN as a tablet, printer, copier, or video surveillance camera.
- 86 percent of healthcare deployments had more than 10 FDA recalls against their medical IoT devices, meaning the medical device is defective, poses a health risk, or both.
- 95 percent of healthcare deployments had Amazon Alexa and Echo devices active in their environment alongside other hospital surveillance equipment. Voice assistants can unknowingly eavesdrop and record conversations and may put the organization at risk of a HIPAA violation.
- 75 percent of healthcare deployments had VLAN violations where medical devices were connected to the same VLAN and subnet as other non-medical devices.
There are real risks and threats posed by IoT, IoMT, and other connected devices if not accounted for and properly managed. One cannot fix what one cannot see, and with IoT, the discovery and classification is the very first step. Once security and networking have high fidelity visibility into unmanaged and IoT devices, then they need to understand device behavior, perform risk assessment and segment vulnerable and mission-critical devices.
Danelle Au
Danelle Au has more than 20 years of experience bringing new technologies to market. Prior to Ordr, she was CMO at Blue Hexagon, a deep learning for malware protection company, and CMO at SafeBreach where she helped build the marketing organization and and define the Breach and Attack Simulation category. Previously, she led strategy and marketing at Adallom, a cloud security company acquired by Microsoft. She was also Director, Security Solutions at Palo Alto Networks, driving growth in critical IT initiatives like virtualization, network segmentation and mobility. Danelle was co-founder of a high-speed networking chipset startup, co-author of an IP Communications Book and holds 2 U.S. Patents. She has an MSEE from UC Berkeley
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogWhy Ordr? Why Now?
BlogWhy Ordr? Why Now?…in healthcare. Previously he was the CTO for Imprivata, and prior to that VP and CTO at Sutter Health, a 26 hospital network in Northern California. Prior to Sutter, Wes…

Wes Wright tells the inside story of why he joined Ordr as the company’s first Chief Healthcare Officer at a crucial time for the industry, his early experiences with connected device security solution, and how Ordr helped him address security needs prior to becoming part of the Ordr team. I just joined Ordr as Chief Healthcare Officer and, as is often the case in life, there’s a story, personal and professional, behind my new adventure here.
A little more than seven years ago, while I was CTO at Sutter Health, a friend from my days as CIO at Seattle Children’s Hospital called and told me about a technology he really wanted to get my opinion on. It was an innovative new product aimed at keeping connected devices secure—a growing problem for healthcare environments. Since I was just a few hours from Silicon Valley, I drove out to find out more.
That’s when I met Gnanaprakasam Pandian, one of Ordr’s co-founders. Pandian proceeded to show me v1 of Ordr and I was floored. In more than 20 years in healthcare IT and security, I had never, ever, been able to get complete visibility on everything that was on any of the networks I managed. And from conversations with my colleagues and peers I knew I was not alone; nobody could.
Sure, I could see all my PCs, printers, routers, switches and other traditional IT and back-office gear; I could even manage them fairly efficiently with the right set of tools, but my vulnerability scanners kept reminding me that there were things connected to my network that were just out of view. Yes, I might have a MAC or IP address, but no clear understanding of what the associated device was, where it was, or how it was behaving. That’s the kind of stuff that keeps a CIO or CISO up at night.
My network managers had told me not to worry about it. They would try to assuage my fears by telling me those unknown configuration items were probably just biomedical devices, not real IT equipment. Yes, they were operating on the network, but they were someone else’s problem. Their advice was meant to reassure me, but I couldn’t shake the feeling of dread.
Ordr Visibility and Security Capabilities
I described my experience with Pandian, and he showed me that, with the Ordr platform, he could tell me exactly what devices all those MAC and IP addresses were assigned to. Not only that, but Ordr could also tell me if any of those devices had associated ECRI notices, vulnerabilities, recalls, and other insights invaluable to understanding a hospital’s security posture. The visibility alone would have been enough to give me the confidence to get a full night’s sleep, but the depth and device intelligence Ordr provided was invaluable to a CISO.
Then Pandian showed me how Ordr could learn and establish a baseline for all these devices– establishing what is “normal behavior”, and then automatically generating VLAN, ACL, and Firewall policies for network and security engineers to review and execute. This functionality delivered “Zero Trust policies” — enabling only the normal communications required for its function–and was thanks to the machine learning (ML) artificial intelligence (AI) that Ordr’s other founder, Sheausong Yang, brought to the platform. And because it is ML driven, Ordr has been learning about device behavior for a long time and has a precise understanding of what constitutes abnormal activity—and what to do about it.
As impressed as I was at the demonstration, it was still a demonstration. And while I am not from Missouri, I am fond of the state’s motto: “Show Me”. So, I asked Pandian if he would be willing to bring Ordr to my organization’s operational environment. I wanted to see how the platform would perform with my stuff, and, oh boy, did it ever perform. I was amazed at the level of device intelligence I was getting out of Ordr, and I wasn’t the only one. I had my security team with me, and their faces lit up.
Seven Years Later
That was seven years ago. Today, with 61 million individual device profiles (with 1000 attributes each) now populating the Ordr Data Lake, it is now the leading asset visibility and security platform used by healthcare organizations everywhere.
Because of that experience, Sutter engaged Ordr for a trial and we began putting the platform through its paces and working with the company’s engineers. Alas, I left Sutter to take on the CTO role at Imprivata, and did not get through the PoV process before I left. Pandian and I had discussed the possibility of joining Ordr then, but the timing wasn’t quite right. I did join the company’s advisory board, however. As it turns out, that was the best scenario for both parties.
While I had extensive experience as a healthcare CIO and CTO, Ordr is much more than just a healthcare security platform and I don’t think I would have been able to do what the company needed at that point in its growth. In fact, I remember one of my first meetings “on the vendor side” listening to people talk about TAM, SAM, and SOM. I made a mental note thinking, “I’d better meet these people. They seem important!”
Today, I think I’m much better prepared to work with my friends and colleagues in the healthcare field and to use those conversations to help Ordr continue to evolve its market leading device security platform. That’s why I decided to join the Ordr team now.
I am eager and excited for this next chapter to unfold, and I hope that it involves you.
Wes Wright
Chief Healthcare Officer
Wes is responsible for driving Ordr’s engagements in healthcare. Previously he was the CTO for Imprivata, and prior to that VP and CTO at Sutter Health, a 26 hospital network in Northern California. Prior to Sutter, Wes was CTO and then CIO at Seattle Childrens’, which, to this day, he says was his most gratifying work experience.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogBD Vulnerabilities for Pyxis and Synapsys Product Lines
BlogBD Vulnerabilities for Pyxis and Synapsys Product Lines…security teams to proactively segment the impacted BD devices, and to set Zero Trust security policies specific to each. In the event that a device is compromised, and we detect…
Security Bulletin
BD Vulnerabilities for Pyxis and Synapsys Product Lines
CISA Advisory on Taking Action
3Min Read
By Darrell Kesti

CISA recently issued security advisories highlighting vulnerabilities associated with connected devices made by medical technology firm Becton, Dickinson & Co. (BD). The advisories follow disclosures BD made to CISA about security flaws in the company’s Pyxis and Synapsys product lines. The Cyber & Infrastructure Security Agency (CISA) recently issued two security advisories highlighting vulnerabilities associated with connected devices made by medical technology firm Becton, Dickinson & Co. (BD). The advisories follow disclosures BD made to CISA, and describe security flaws in the company’s Pyxis and Synapsys product lines.

Among the vulnerabilities described in the advisories are the use of default and shared credentials in the Pyxis products and “insufficient” session expiration for the Synapsys informatics platform. Both flaws could leave the devices vulnerable to exploitation by threat actors who could then gain access to sensitive patient protected health information (PHI) or even affect the delivery of correct treatment.
Device Vulnerabilities Put Network and Patient Safety at Risk
The disclosure of these security flaws by BD, and the subsequent advisories issued by CISA, underscores the risk to both network and patient security when vulnerable internet of medical things (IoMT) devices are deployed within healthcare environments. Even when such devices must remain in service and cannot be patched, allowing them to continue operation without taking steps to mitigate their associated risks should be regarded as a dereliction of duty.
In this current case, BD recommends a number of steps to close the now-known security gaps, including:
-
Limit physical access to only authorized personnel;
-
Tightly control management of system passwords provided to authorized users;
-
Monitor and log network traffic attempting to reach the affected products for suspicious activity;
-
Isolate affected products in a secure VLAN or behind firewalls with restricted access that only permits communication with trusted hosts in other networks when needed; and,
-
Work with your local BD support team to ensure that patching and virus definitions are up to date. The BD Remote Support Services Solution for automated patching and virus definition management is an available solution for customer accounts.
From an IT and security operations standpoint, these steps may be difficult for hospitals and other healthcare delivery organizations (HDOs), especially in larger organizations with no means for effecting proper asset management. This leaves questions like: Does my organization have these devices in inventory and where are they located? What software versions are installed? Are they in use and unable to be taken out of service?
Ordr can answer these questions and easily address the recommendations by BD above.
See, Know, Secure, Every Connected Device
Our See, Know, Secure approach to connected device security means our customers can find and identify all the BD connected assets—as well as other connected devices operating in the network—within minutes of deployment. Once Ordr has discovered the devices, their specific make, model, and other operational data are identified, the BD products that are impacted by this vulnerability can be monitored for any anomalous behavior that could be an indicator of compromise (IOC).
Ordr can identify which BD devices are being accessed by which user, and track which users were logged into a specific device, at what time, duration and more.
Ordr also enables security teams to proactively segment the impacted BD devices, and to set Zero Trust security policies specific to each. In the event that a device is compromised, and we detect anomalies such as a suspicious communications pattern or other operations outside of defined parameters—our segmentation policies limit an attack’s potential “blast radius” by isolating affected devices and network segments, and allowing security teams to take mitigating actions within minutes of a breach.
Ordr Can Help Secure Your Devices and Environment
With studies suggesting that as many as three-quarters of all connected medical devices currently in service contain at least one security vulnerability, and that half may contain two or more, it is critically important for hospitals and HDOs to do what is necessary to gain the upper-hand on connected device inventory, management, and security. For more information about how the Ordr can assist in this endeavor, please visit our site to learn more about our asset inventory management and security platform, or contact us with questions specific to your organization’s situation.
Darrell Kesti
Darrell is VP Sales at Ordr. He joined Ordr as one of the original Account Executives in October of 2018 to help launch the field organization. In his prior role as Ordr’s Director of Healthcare Sales, Darrell drove significant growth in healthcare sales and helped position Ordr as the leader in connected device security. Darrell has had over 20+ years of Sales Leadership, Account Management, and Field Engineering experience supporting customers and partners while with leading security and networking organizations – ForeScout Technologies, FireEye, Mandiant, F5 Networks, and Secure Computing Corporation. Darrell earned a Bachelor of Science in Electrical and Computer Engineering from the University of Minnesota, Duluth.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-