-
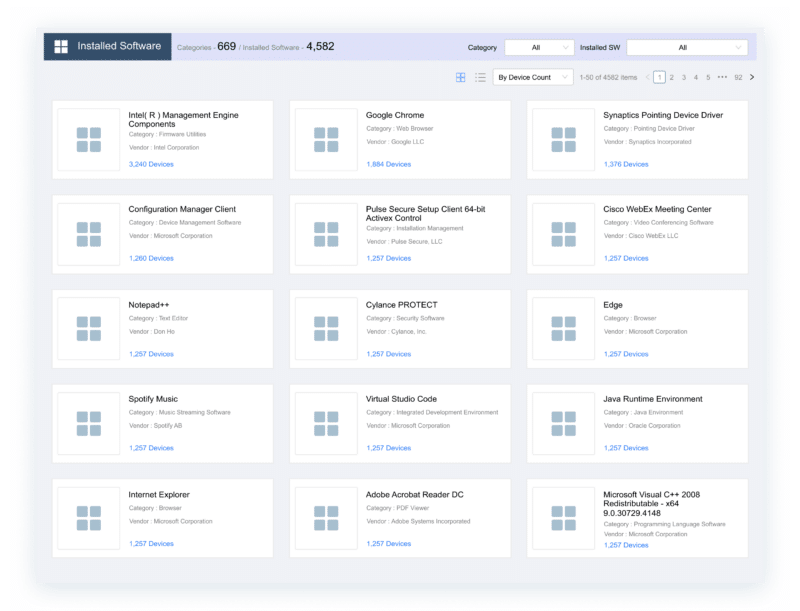
 PagesOrdrAI CAASM+
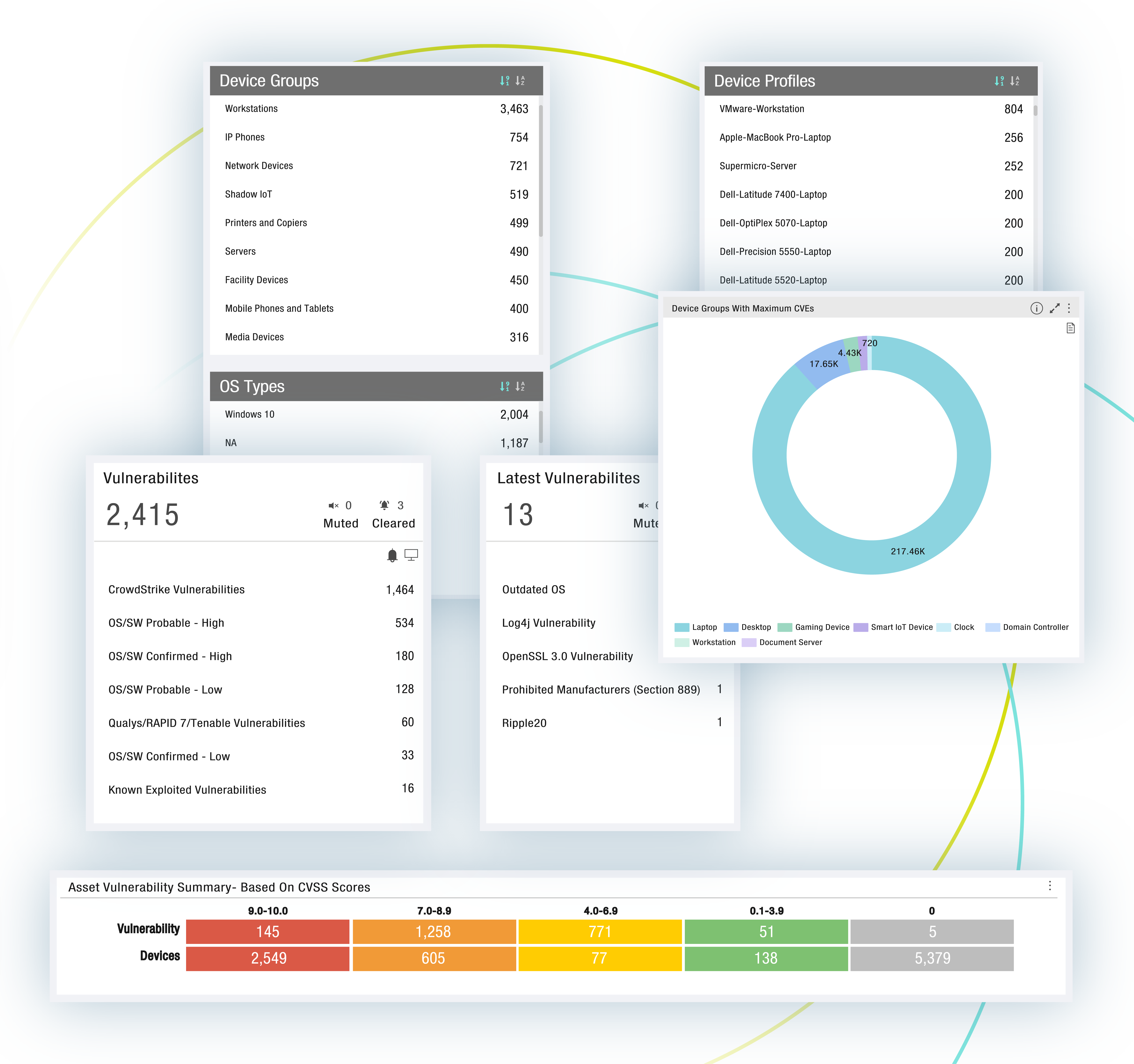
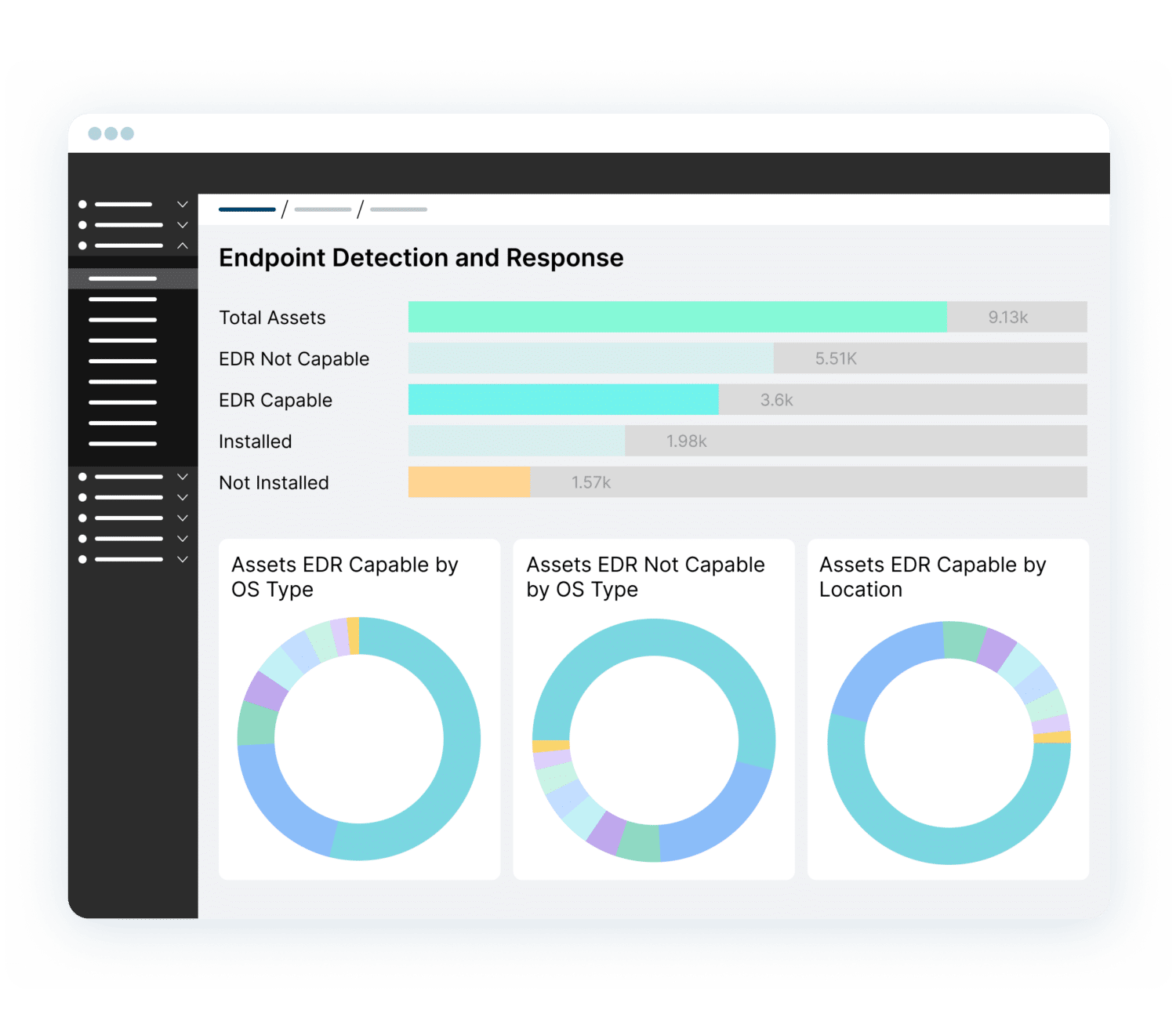
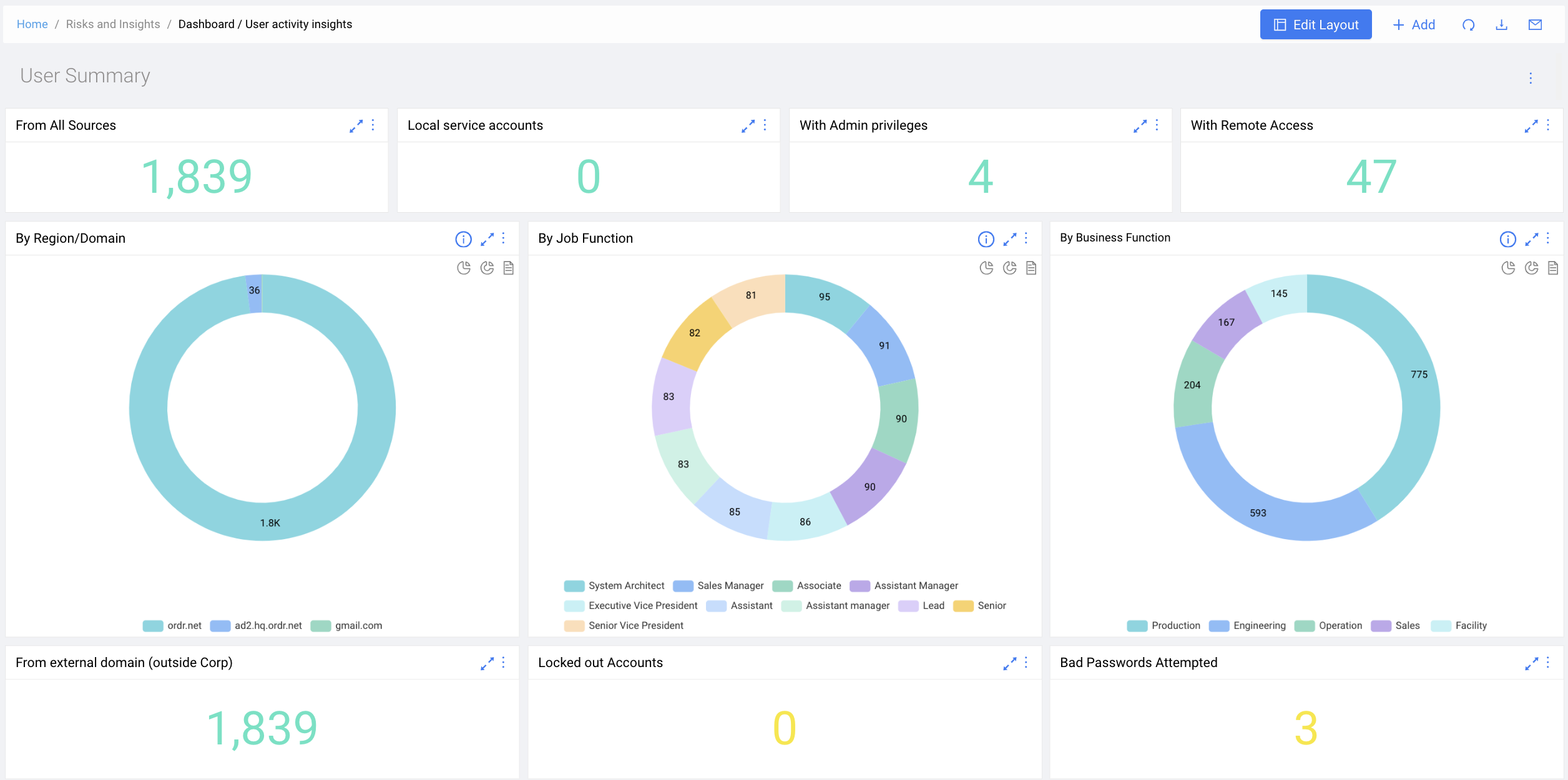
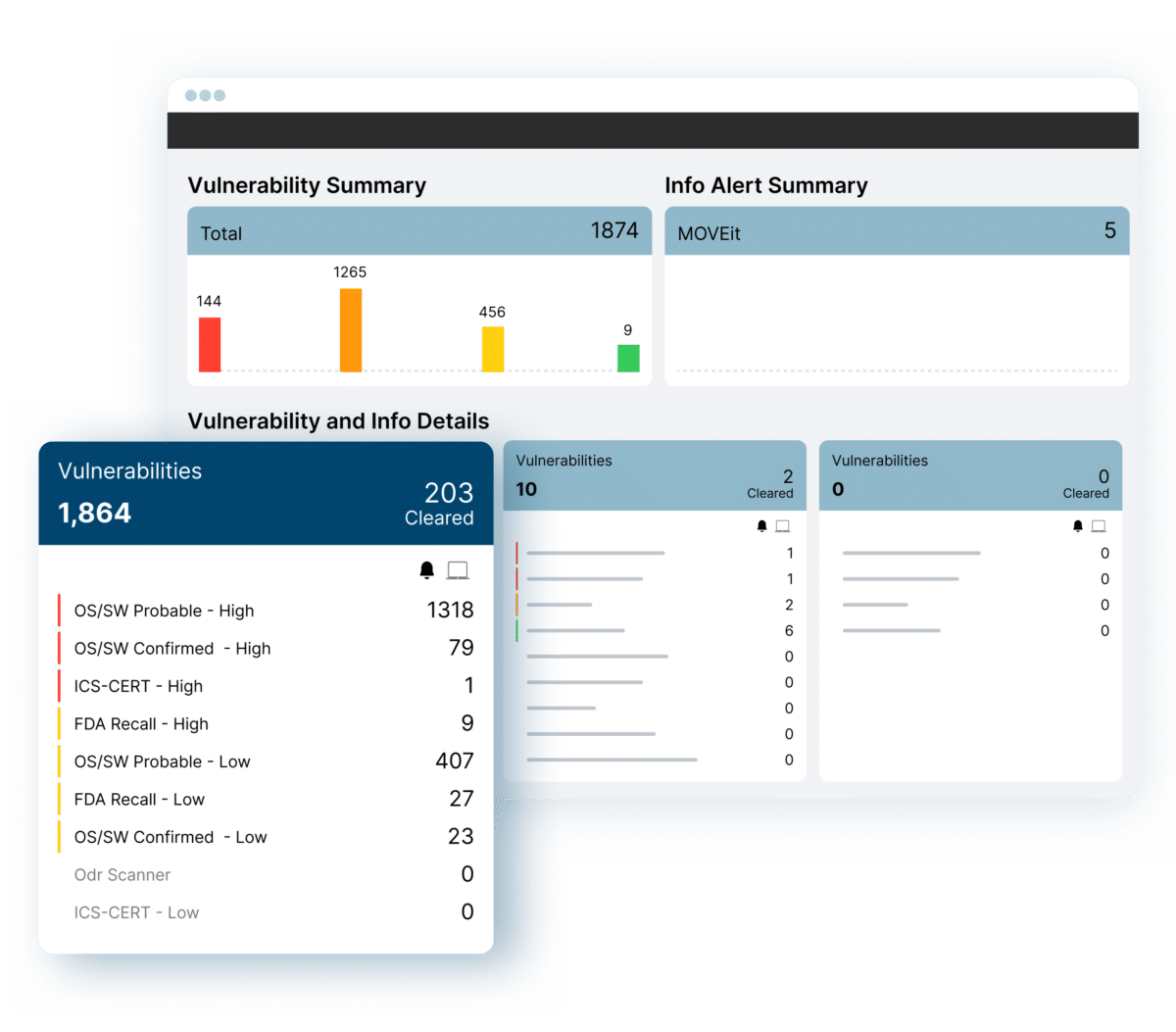
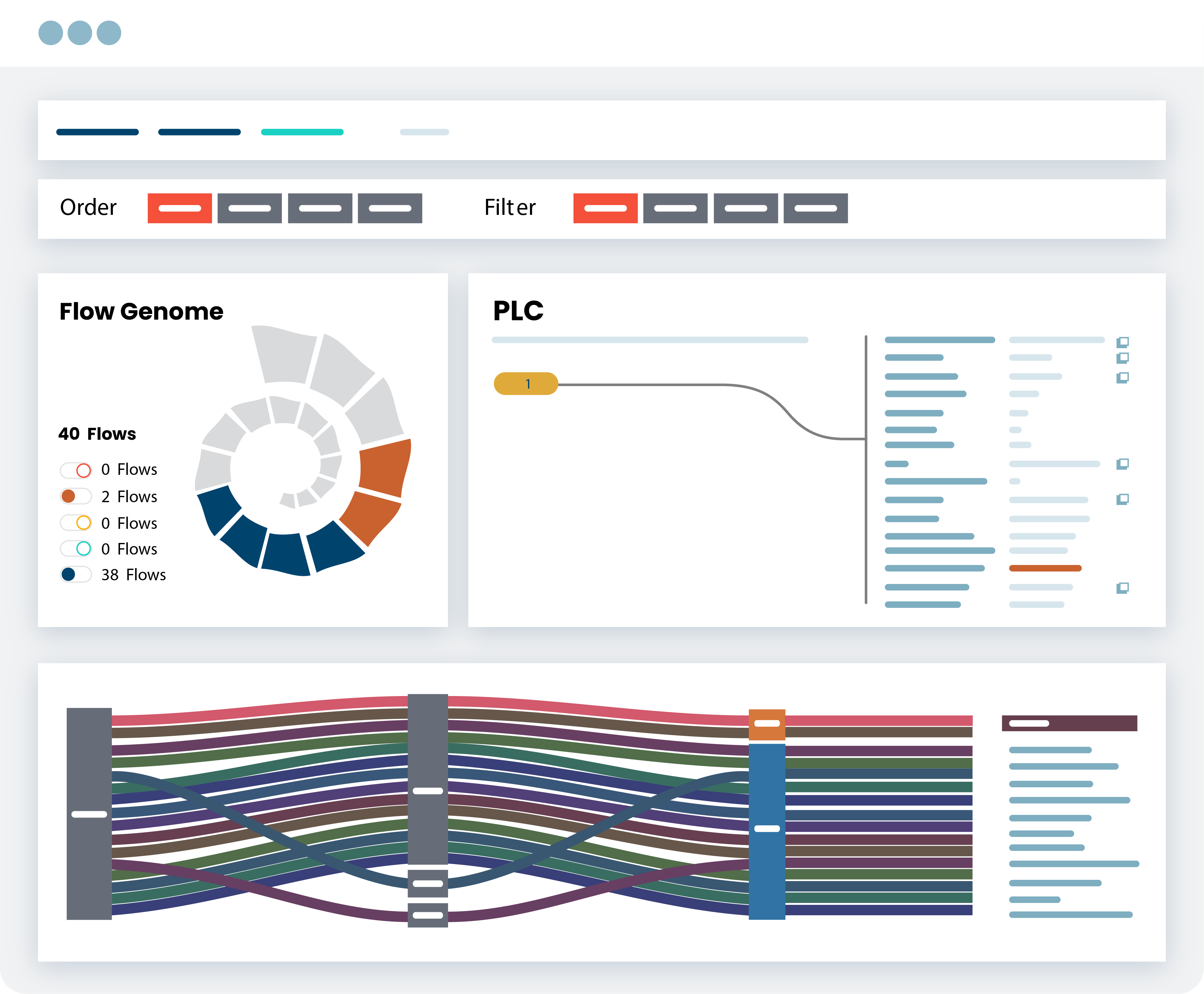
PagesOrdrAI CAASM+…and user activities. Asset Graph and Intelligent Analytics Powerful asset graph, AI-enhanced analytics and customizable dashboards to gain actionable insights into security posture, gaps and risks. Query With Natural Language…
-
 BlogDemocratizing IoT Security Together With Our Partners
BlogDemocratizing IoT Security Together With Our Partners…includes a complete kit – Ordr Core and zero touch provisioning sensor– to discover and classify IoT (and shadow IoT) devices in the enterprise. The IoT Discovery Program is so…
-
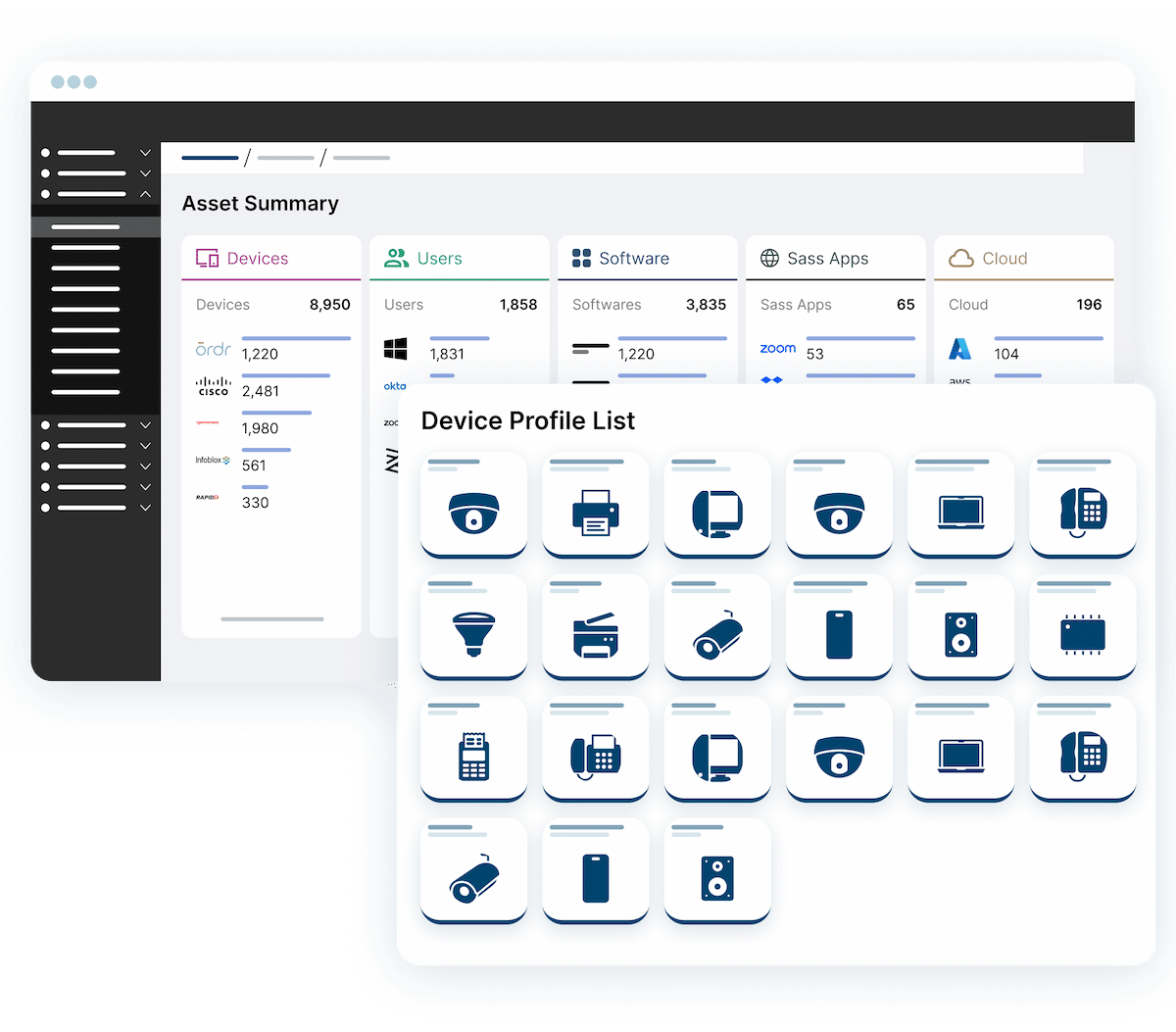
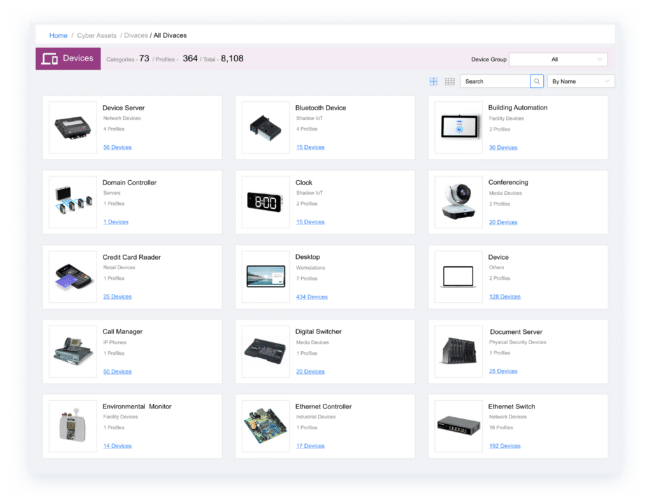
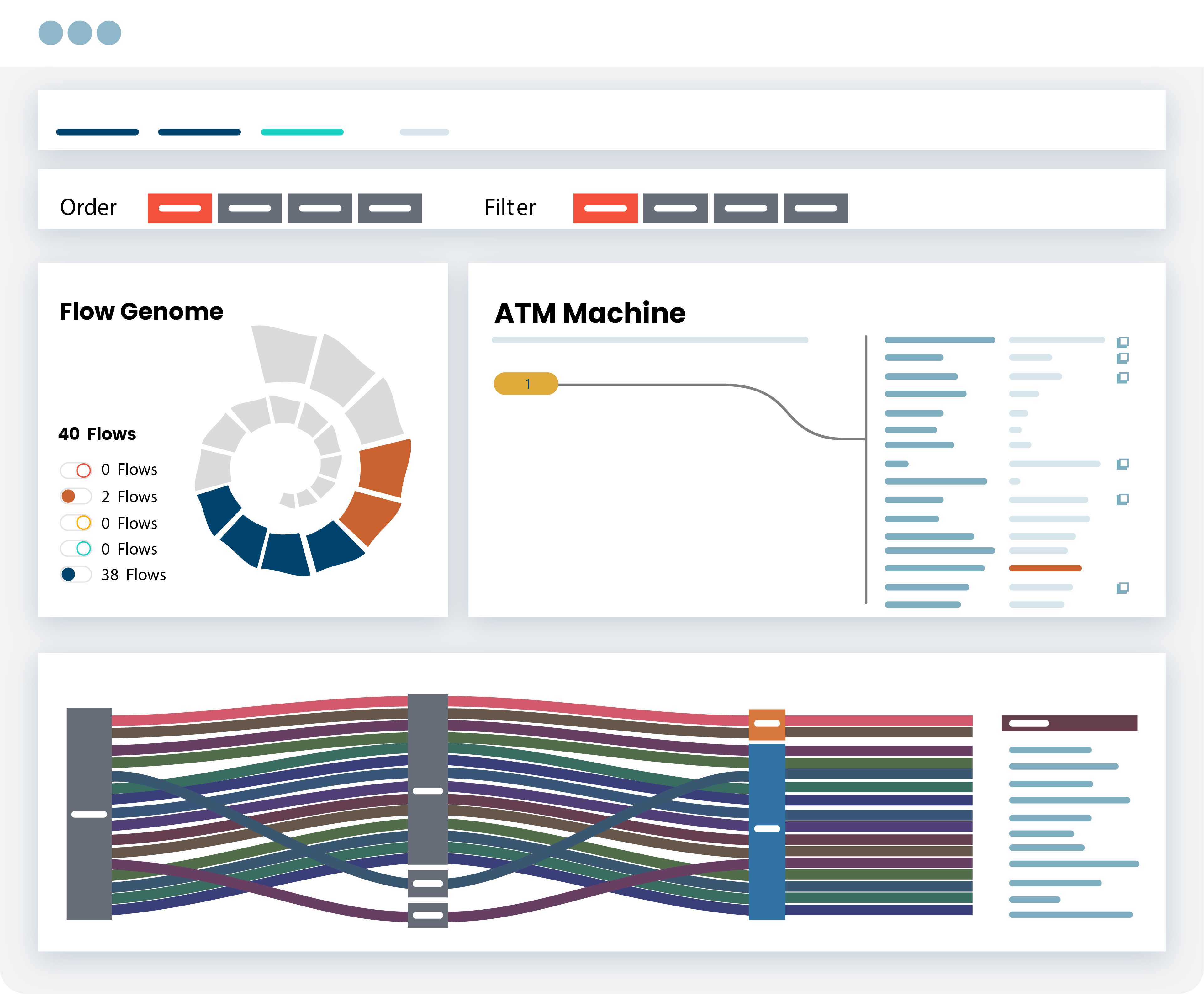
PagesAsset Visibility and Management
Real-Time Asset Visibility And Management Eliminate the need for manual methods and fine tuning with automated, real-time visibility and insights for every asset. REQUEST A DEMO hours a week spent…
-
 BlogWelcome René Bonvanie, our new Executive Chairman of the Board
BlogWelcome René Bonvanie, our new Executive Chairman of the Board…journey. With the alarming increase in cybercrime, organizations are looking not only for visibility and insights on connected devices, but a complete set of security features to protect and respond…
-
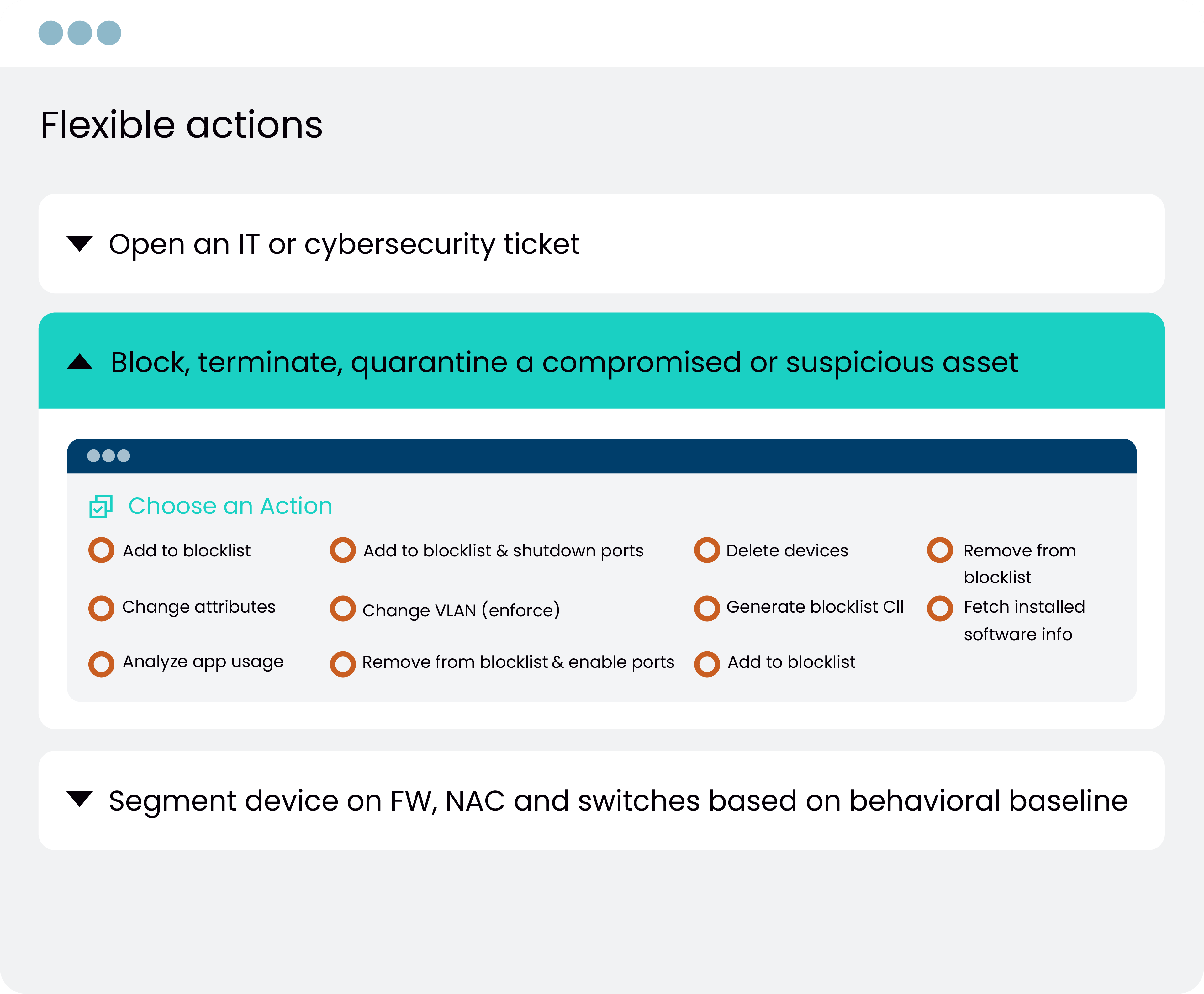
 BlogSegmentation Done Right – Part 3: Take Control
BlogSegmentation Done Right – Part 3: Take Control…business needs flexibly. Blacklist with micro-segmentation, we do that too. We give you the tools to do segmentation right and we give you the smarts to take control. Read Segmentation…
-
![[Part 2] Medical Device Security: Building an ROI-Based Business Case](https://ordr.net/wp-content/uploads/2020/10/Part-2-Medical-Device-Security-1.webp) Blog[Part 2] Medical Device Security: Building an ROI-Based Business Case
Blog[Part 2] Medical Device Security: Building an ROI-Based Business Case…include medical device security, and have disjointed governance and sponsorship policies. Technical: Typical IT network tools do not work for medical device security purposes, and without passively scanning them as…
-
 BlogThe IT Cold War – U.S. & China
BlogThe IT Cold War – U.S. & China…image recognition and deep-learning software SenseTime – facial, text, and image recognition, object detection, medical image analysis, and more Yitu Technologies – facial and speech recognition, natural language processing, and…
-
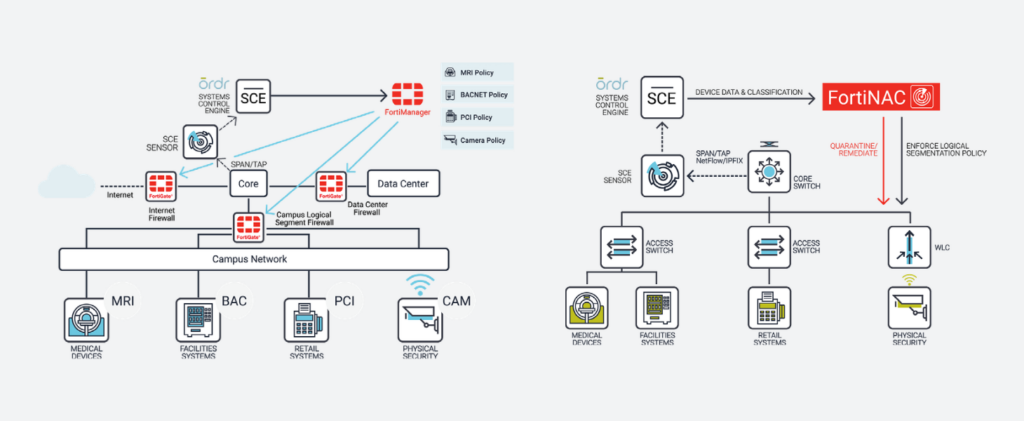
 IntegrationsFortinet
IntegrationsFortinet…this critical security context to Fortinet FortiGate, FortiManager, and FortiNAC, allowing administrators to create and apply firewall and NAC policies using business-relevant groups, classifications, and device names, while understanding the…
-
PagesManufacturing
…systems, to ensure uninterrupted manufacturing operations. SEE Granular Visibility For Your Entire Manufacturing Organization IT and OT convergence can impact visibility into the attack surface. Ordr delivers complete visibility into…
-
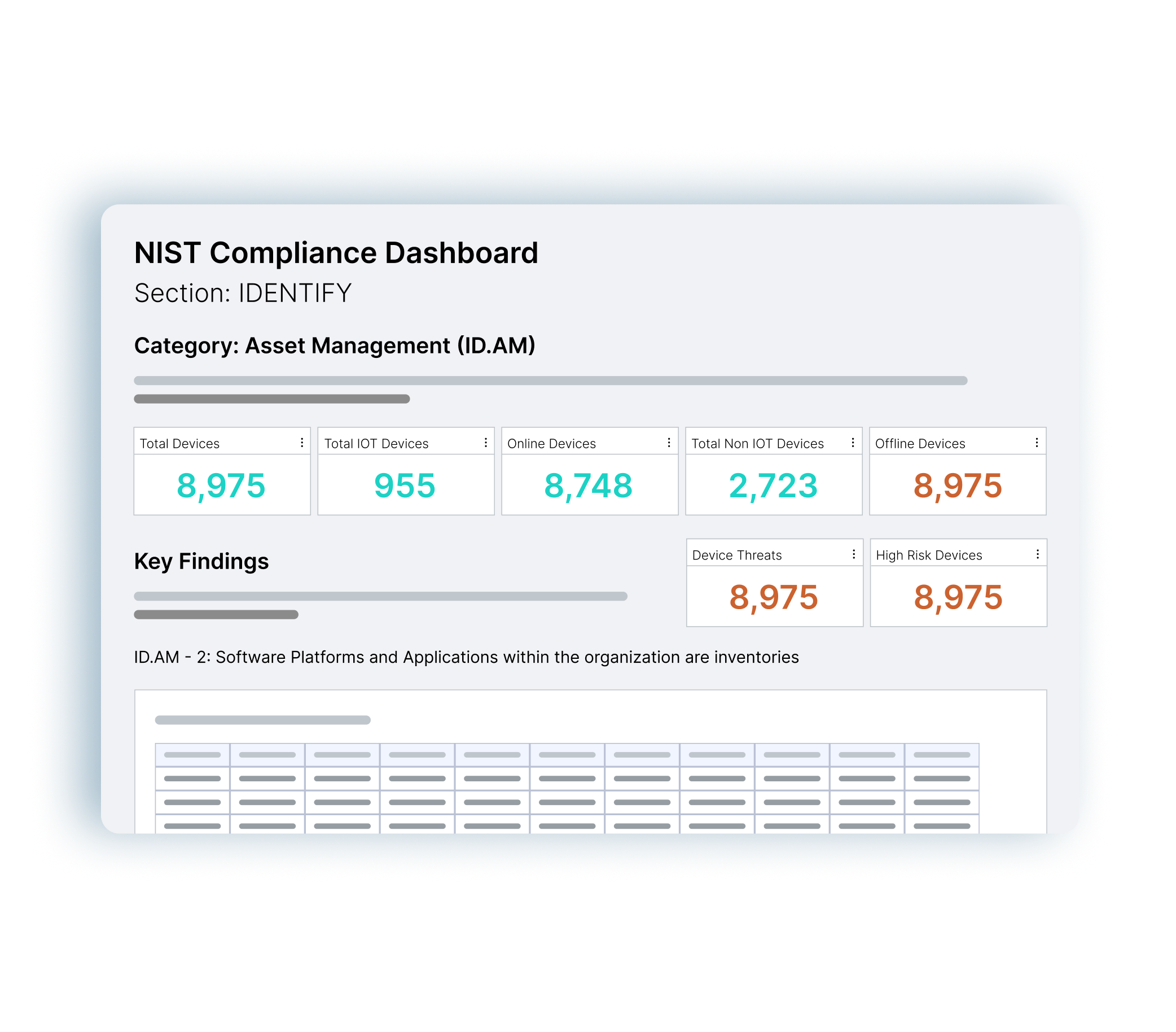
PagesRegulatory Frameworks
…SOLVE FOR TODAY AND TOMORROW Audit and Compliance Reporting Maintain compliance effortlessly by generating reports and comprehensive asset insights for standards like NIST, CIS Controls, Cyber Essentials, DSP Toolkit,…