Search Results:
”Quiz 2024 SAP C-ARSOR-2308: Marvelous SAP Certified Application Associate - SAP Ariba Sourcing Valid Dumps Book 🐮 Open ▷ www.pdfvce.com ◁ and search for ➥ C-ARSOR-2308 🡄 to download exam materials for free 🏑C-ARSOR-2308 Customizable Exam Mode”
-
 BlogTSA Cybersecurity Mandates for Public Transportation
BlogTSA Cybersecurity Mandates for Public Transportation…IT, OT to OT, and all traffic between OT and IT. Ordr dynamically generates segmentation and provisions segmentation policies to switches, wireless controllers, and firewalls to permit only safe and…
Blog
TSA Cybersecurity Mandates for Public Transportation
Arrive Early, Arrive Safe with Ordr
3Min Read
By Craig Hyps
The United States is constantly under attack from bad actors, including nation states and financial opportunists. Threats to critical infrastructure and services such as public transportation can have far-reaching impacts on the economy, public safety, and national security.
Following the 2021 ransomware attack on the Colonial Pipeline, the Transportation Security Administration (TSA) issued directives in 2022 to bolster security for U.S. pipelines. These directives were issued as part of an overarching executive order to protect critical infrastructure from “degradation, destruction, or malfunctioning of systems that control this infrastructure.” [Reference: National Security Memorandum on Improving Cybersecurity for Critical Infrastructure Control Systems (July 29, 2021).]
In October 2022, Security Directives 1580-21-01A, 1582-21-01A, and 1580/82-2022-01 were announced to include surface transportation systems and associated infrastructure such as passenger railroads and rail systems. In March 2023, an emergency amendment was added to extend the directives to TSA-regulated airport and aircraft operators.
What is at the core of these security directives?
In summary, the directives mandate that impacted entities such as railroad, airline, and airport owners and operators must:
- Develop a TSA-approved implementation plan that describes the specific measures taken to achieve cybersecurity outcomes; and,
- Develop a TSA-approved assessment plan that describes how the specific measures will be assessed for effectiveness.
Specific measures outlined include the following actions:
- Implement network segmentation policies and controls to ensure that the Operational Technology system can continue to safely operate in the event that an Information Technology system has been compromised;
- Implement access control measures to secure and prevent unauthorized access to Critical Cyber Systems;
- Implement continuous monitoring and detection policies and procedures to detect cybersecurity threats and correct anomalies that affect Critical Cyber System operations; and,
- Reduce the risk of exploitation of unpatched systems through the application of security patches and updates for operating systems, applications, drivers, and firmware on Critical Cyber Systems in a timely manner using a risk-based methodology.
[Reference: Security Directive 1580/82-2022-01C]
Introducing Ordr…
Ordr is a comprehensive operational technology (OT) and IT asset discovery and classification solution that helps to ensure that only trusted systems can access the network. Ordr calculates risk based on device type, model, operating system, and patch status, and continuously monitors communications for threat activity and anomalous behavior. Ordr then dynamically groups devices based on organizational requirements and automatically generates and provisions network segmentation policies.
The following table lists the four specific measures encompassed in the TSA mandates in more details and how Ordr helps to address each one.
TSA Measure Cybersecurity Measure Details Ordr Solution 1 Implement network segmentation policies and controls designed to prevent operational disruption to the Operational Technology system if the Information Technology system is compromised or vice-versa. Ordr passively discovers and classifies all OT and IT devices on the network and automatically tracks the communications of all devices including IT to IT, OT to OT, and all traffic between OT and IT. Ordr dynamically generates segmentation and provisions segmentation policies to switches, wireless controllers, and firewalls to permit only safe and authorized communications between each device regardless of its type or function. 2 Implement access control measures, including those for local and remote access, to secure and prevent unauthorized access to Critical Cyber Systems. Ordr seamlessly integrates with existing wired switches, wireless controllers, firewalls, and Network Access Control (NAC) solutions from leading vendors to implement access controls to secure and prevent unauthorized access to Critical Cyber Systems. 3 Implement continuous monitoring and detection policies and procedures that are designed to prevent, detect, and respond to cybersecurity threats and correct anomalies affecting Critical Cyber Systems. Ordr continuously monitors all device communications to establish baselines of safe behavior and automatically detects anomalies, suspicious activity, vulnerable communications, as well as internal and external threats. Ordr can dynamically respond to threats by quarantining an attack or infected system, block unauthorized or high-risk communications, or limit access to vulnerable systems. 4 Reduce the risk of exploitation of unpatched systems through the application of security patches and updates for operating systems, applications, drivers, and firmware on Critical Cyber Systems consistent with the Owner/Operator’s risk-based methodology. Ordr can directly or indirectly discover and track unpatched and vulnerable systems. As an agentless solution, Ordr does not directly apply patches, but integrates with industry leading patch management and mobile device management (MDM) solutions as well as vulnerability management solutions to verify critical systems are patched and dynamically update its risk calculation based on vulnerability and patch status. For additional information on how Ordr can accelerate compliance with TSA cybersecurity mandates for critical infrastructure to protect public transportation for airlines, railroads, rail systems, and pipelines, contact us to discuss further.
Craig Hyps
As an Ordr Fellow, Craig drives next-generation solutions that enable organizations to keep pace with the hyper-connected Internet of Things (IoT) and Operational Technology (OT) through automated classification and segmentation using ML/AI on big data platforms. Prior to joining Ordr in 2018, Craig was a 20+ year veteran with Cisco Systems defining Cisco’s policy and access control solutions including Identity Services Engine (ISE) and Software-Defined Access (SDA). He was a leading force behind its super-scaling architecture and the advancement of NAC for IoT. Craig is an active member of the IEEE 2933 Working Group focused on Trust and Identity best practices and standards for Clinical IoT. Craig is also a frequent presenter and author on the topic of Zero Trust and network segmentation for the rapidly expanding growth and convergence of IT, IoT, and OT devices.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogAre the EU and UK Ahead of the U.S. on IoT Device Security?
BlogAre the EU and UK Ahead of the U.S. on IoT Device Security?…practices for device security, the Office of Management and Budget to create guidance for agencies to meet, and require the Department of Homeland Security to publish guidance on coordinated vulnerability…
Security Strategy
Are the EU and UK Ahead of the U.S. on IoT Device Security?
4Min Read
By Corin Imai

Lawmakers in the European Union and United Kingdom have adopted device cybersecurity and privacy regulations that set the standard for asset security. What can (should) the U.S. do to catch up? What can U.S. enterprises do on their own to improve security and reduce risk? Internet of Things – Digital Transformation
Merriam-Webster’s definition of the Internet of Things (IoT) is, “the networking capability that allows information to be sent to and received from objects and devices (such as fixtures and kitchen appliances) using the Internet”. In 1999 Kevin Ashton coined the term and since then we have seen the expansive growth of IoT and while these devices have been around for decades, the regulations on these devices still remain ineffectual.
And, while IDC estimates that there will be 41.6 billion connected IoT devices, or “things,” generating 79.4 zettabytes (ZB) of data in 2025, we still are not able to properly build IoT devices with security in mind.
The United States
Recently, a bipartisan bill, the IoT Cybersecurity Improvement Act, from Reps. Will Hurd (R-Texas) and Robin Kelly (D-Ill.), along with Sens. Mark Warner (D-Va.) and Cory Gardner (R-Colo.) was passed by the House but now must go to the Senate before hitting the President’s desk. The bill took more than three years to get to the House of Representatives and in that time more than 6 billion IoT devices entered the market.
While the bill would set the minimum security standards for IoT devices connected to federal networks, it would also require the National Institute of Standards and Technology (NIST) to set best practices for device security, the Office of Management and Budget to create guidance for agencies to meet, and require the Department of Homeland Security to publish guidance on coordinated vulnerability disclosures for contractors and vendors.
The Food and Drug Administration (FDA) is trying to achieve medical device security and makes it well known on their website what they aim to accomplish:
The U.S. Food and Administration (FDA) regulates medical devices and works aggressively to reduce cybersecurity risks in what is a rapidly changing environment. It is a responsibility the Agency shares with device makers, hospitals, health care providers, patients, security researchers, and other government agencies, including the U.S. Department of Homeland Security and U.S. Department of Commerce.
The FDA provides guidance to help manufacturers design and maintain products that are cyber secure. And on behalf of patients, the FDA urges manufacturers to monitor and assess cybersecurity vulnerability risks, and to be proactive about disclosing vulnerabilities and solutions to address them.
The medical device cybersecurity guidance by the FDA was last updated in 2018. While they release a list of vulnerabilities, their guidance points organizations to the MITRE Corporation’s Medical Device Cybersecurity Regional Incident Preparedness and Response Playbook in which they were a contributor.
Much like with regulatory compliance standards around sensitive data, in the United States the individual states are leading the charge again. California and Oregon have enacted legislation that mandates that manufactures that supply IoT devices do so with “reasonable security features.” In addition to California and Oregon, eight additional states are considering legislation.
The United States is likely to not see real meaningful regulatory compliance standards for IoT devices until the impact has already hit most organizations and homes. Compare that to the European Union (EU) and what they have in place and are working to put in place.
The European Union (EU)
The EU in June of this year introduced a new cybersecurity standard for consumer IoT (ETSI EN 303 645 V2.1.1) products. With the hopes of better security practices and more manufactures adopting a security-by-design principle when developing new connected consumer products.
The standard consists of 13 provisions:
- No universal default passwords
- Implement a means to manage reports of vulnerabilities
- Keep software updated
- Securely store sensitive security parameters
- Communicate securely
- Minimize exposed attack surfaces
- Ensure software integrity
- Ensure that personal data is secure
- Make systems resilient to outages
- Examine system telemetry data
- Make it easy for users to delete user data
- Make installation and maintenance of devices easy
- Validate input data
In addition to ETSI EN 303 645 V2.1.1, the EU also explicitly addresses medical devices in the European Medical Device Regulation (EU MDR). Much like the US FDA’s UDI, it seeks to ensure high standards of quality and safety for medical devices being produced in or supplied into Europe. With the introduction of this directive, devices entering the EU will have:
- Stricter pre-market control of high-risk devices at an EU level
- The inclusion of certain aesthetic products which present the same characteristics and risk profile as equivalent medical devices
- A new risk classification system for diagnostic medical devices based on international guidance
- Improved transparency through the establishment of a comprehensive EU database of medical devices
- Device traceability through the supply chain from its manufacturer through to the final user
- An EU-wide requirement for an ‘implant card’ to be provided to patients containing information about implanted medical devices
- the reinforcement of the rules on clinical data and clinical studies on devices
- Manufacturers to collect data about the real-life use of their devices
- Improved coordination between EU Member States
And, now with Brexit, what happens with the United Kingdom (UK) come December 31, 2020 and the IoT regulatory compliance standards? While the UK remains subject to EU law, it is no longer part of the EU’s political bodies or institutions. Will the Department for Digital, Culture, Media & Sport (DCMS) serve as the governing body for IoT device security?
The United Kingdom (UK)
In June of 2020 the UK DCMS addressed the need for cybersecurity as a fundamental instrument in the building of IoT devices, they are enacting a product assurance schema to mark approved IoT devices with an assurance label or kitemark that demonstrates that the product has undergone independent testing or a robust and accredited self-assessment process. The ultimate goal would be that consumers of IoT devices would purchase approved devices, rather than those that are not, and that retailers would only sell approved devices.
DCMS has been taking forward multiple initiatives to address the matter, including:
- Publishing the Code of Practice for Consumer IoT Security
- Committing to taking forward new legislation to mandate core aspects of the Code
- Leading the development of industry standard ETSI EN 303 645
“The UK Government looks forward to continuing to work with industry and all interested stakeholders to ensure that the UK is the safest place to be online.”
While the EU and UK continue to lead the charge in regulatory compliance standards to protect citizen and resident data, it is also years ahead of the U.S. in addressing IoT device security. The fundamental issues still remain. Can we create a global culture where we put securing our data first, both from properly building IoT devices and then by holding device manufactures accountable in our procurement of devices?
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
Knowledge BaseWhat is zero trust network security?
…needs to operate. Don’t allow the device to run with open ports for services that aren’t actually necessary for the device to perform its function, and don’t allow network traffic…
What Is Zero Trust Network Security?
6Min ReadModern networks can be wild, unruly places populated by an ever-changing set of endpoints. There is no way to guarantee that a device can be trusted by default, because you can never be sure where a new device on your network originated or what’s running on it. That’s why the concept of zero trust network security is an effective replacement for outdated perimeter-based security strategies that segment trusted devices from the public Internet.
Instead of a one-and-done security check (i.e. user ID/password), zero trust security requires continuous validation for access as a user moves around a network regardless of their physical location and relationship to an organization.
Keep reading for tips on how and why to implement zero trust security, especially on networks that include unmanaged IoT devices, as well as best practices for achieving zero trust security, such as network segmentation.
What is zero trust network security?
Zero trust security is summed up as a principle of “never trust, always verify.”
In other words, a zero trust architecture means that whenever a new device appears on a network—or an existing device’s configuration changes—the device has no access to the network or the hosted resources until you have verified that the device should be granted access.
Zero trust security applies not just to devices that originate from outside a local network, but also those that appear inside it. Just because a business has a subnet that is firewalled off from the Internet—or a network running on a private IP address range—doesn’t mean that an employee could not bring an untrusted device online on that network, for example, or that an intruder who previously breached the network perimeter can’t deploy a malicious host on an internal network.
Zero trust principles and technologies
Zero trust security is founded upon several principles and practices, which help enforce the policy of not granting network access to devices until they are deemed trustworthy.
Inside and outside threats
Zero trust applies to devices regardless of whether they originate on a public or private network. You can’t rely on firewalls or private IP addresses as a way of guaranteeing that a device can be trusted. Instead, you must identify each device that exists on your network and ensure it can be trusted before you grant it access to network resources.
Least-privilege access
Determining that a device is trusted doesn’t mean granting it unfettered network access. Instead, adhere to a policy of least-privilege access, which means granting the device only the minimal access privileges it needs to operate. Don’t allow the device to run with open ports for services that aren’t actually necessary for the device to perform its function, and don’t allow network traffic among devices unless there is a reason for them to communicate with each other.
Multi-factor authentication
When you do grant access to network resources, enforcing multi-factor authentication (MFA) helps to mitigate the risk of abuse or privilege escalation by making it harder for intruders to steal or spoof access credentials. MFA is a security enhancement that allows a user to present two or more pieces of evidence when logging in to an account. These credentials fall into any of these three categories: something you know (like a password or PIN), something you have (like a smart card), or something you are (like your fingerprint). Credentials must come from two or more different categories to enhance security—so entering two or more different passwords would not be considered multi-factor.
Microsegmentation
Microsegmentation refers to the practice of granting access privileges to each device on a highly granular basis. Rather than applying blanket access-control policies to all devices of the same type, or across an entire subnet, you must adopt policies that are tailored to the individual needs of each device on the network.
By adhering to these principles, your business can put a zero trust network security into practice.
How to implement zero trust security
The previous section discussed high-level concepts that are a core part of zero trust security. Now, let’s take a look at specific practices that help in implementing a policy of zero trust.
Get visibility into the device attack surface
You can’t effectively determine access policies or assess whether devices can be trusted unless there is complete visibility into the devices that exist on your network.
Complete visibility means not only knowing where devices exist by listing IP addresses, but also establishing what each device consists of, such as:
- device make
- operating system
- location
- application/port usage
- vulnerability data
- FDA/device manufacturer alerts
It also means being able to quickly identify devices that:
- have outdated operating systems
- have FDA recalls
- are banned by governing bodies
Gaining this level of visibility requires constant scanning of your network in order to be aware of new devices as they come online, and also to know about changes to the state of existing devices. If a previously trusted device changes its IP address or opens a new port, for example, zero trust security requires you to assume the device can’t be trusted until the security of its new configuration is verified.
Identify at-risk devices
As you identify and assess the devices on the network, assign a risk score for each one. This evaluation reflects information about device details—such as which services it is running and when its software was last updated—as well as behavioral data about how the device seeks to interact with other devices.
By determining the risk level of each device, you gain a stronger sense of how much access to grant it, and whether to allow the device to access resources on a temporary or permanent basis.
Devices determined to be high-risk should be segmented entirely from the network. Those that are medium-risk may be granted access to basic services, like connectivity, but not access to protocols that could be easily abused, like telnet or SSH.
Remember, too, that risk assessment is not a one-time affair. You must continually reassess risk and recategorize the risk-status of each device if its configuration changes.
Understand device communication needs
In order to determine what level of access to grant to devices on the network, you must know each device’s purpose, and the resources it needs in order to perform its function.
With this visibility, you will know which protocols and ports to allow for each device. You can also granularly configure other endpoints each device is allowed to access.
Note, too, that just because a given port is open on a device, or it is running a particular kind of service, doesn’t mean it actually needs that port or service to be available. Don’t trust the device itself to tell you what it needs; instead, perform systematic assessments using centralized monitoring tools that provide insight into what each device requires.
Dynamically segment devices
It is not enough to apply access policies across an entire subnet or category of devices. Instead, perform microsegmentation by enforcing access policies tailored to each device, which govern the resources each device can and cannot access.
Access policies should be dynamic and updated constantly as device requirements change. For example, a device that needs to access network-attached storage in order to upload data should be granted access while the upload takes place, then have that access revoked when it is no longer necessary.
Continuous monitoring
New threats can emerge constantly, and you must monitor devices and network configuration on a constant, ongoing basis. Policies that suffice to mitigate security risks in one moment may be outdated the next.
Your ultimate goal should be to ensure that devices do only what you want them to do, only when you allow them to do it.
What are the benefits of zero trust network security?
By implementing a zero trust security policy, you gain several critical benefits:
Reduce business risk
By helping to prevent attacks that could disrupt workflows or take critical systems offline, zero trust security minimizes the overall risk to business continuity.
It also helps to defend against ransomware attacks, data theft, and other threats that can have steep financial and reputational consequences for the business.
Lower breach potential
Zero trust security ensures that devices are isolated and segmented by default. Even if attackers are able to deploy a malicious device on the network, or take control of one that is already deployed, damage is minimized if the device lacks access to network resources.
Consistency
With zero trust network security, you gain a consistent security process that applies to all devices across all components of your network. Zero trust security simplifies management by eliminating the need to enforce different policies in different contexts, or manage multiple monitoring and access-control systems.
Your end-users also benefit from consistent, streamlined security policies like multi-factor authentication, which provides an extra layer of protection even for users who fail to set secure passwords.
Getting started with zero trust
Implementing a zero trust architecture requires systematic, centralized visibility into the location and status of all devices on your network. Device information must be available in real time and updated continuously as the network changes.
While the implementation details will vary depending on specifics such as which types of devices you are managing and which software stacks are running in your network, Ordr Systems Control Engine (SCE) provides the centralized visibility you need for tracking both managed and unmanaged devices in your current environment. SCE automatically discovers and assesses each device on the network, then enforces an appropriate security policy. Ordr also automatically learns the unique communication patterns of each device in order to provide another layer of visibility into the security context of the network.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogWhite House Must Lead & Build Momentum for IoT Security
BlogWhite House Must Lead & Build Momentum for IoT Security…actors to gain access to a personal network that is relatively unprotected. Very few homes run industrial-grade security products, and are vulnerable to the tools and techniques available to most…
Security Strategy
White House Must Lead & Build Momentum for IoT Security
4Min Read
By Danelle Au

Ordr looks at the White House plan to strengthen our national cybersecurity posture and examines how, while discussing the security of consumer devices, commercial cyber assets (IoT, OT, IT) are omitted from the plan. Ordr addresses the exclusion and how enterprises can fill in the gap. The White House recently issued a memo entitled Fact Sheet: Biden-Harris Administration Delivers on Strengthening America’s Cybersecurity. The communique offers a checklist of policies, executive orders, and other steps the Biden-Harris Administration has taken to demonstrate its “relentless focus to improving the United States’ cyber defenses, building a comprehensive approach to ‘lock our digital doors’ and take aggressive action to strengthen and safeguard our nation’s cybersecurity.” It’s worth looking at the items outlined as it offers insight into the federal government’s position on the state of the nation’s cybersecurity posture.
The Fact Sheet on Strengthening America’s Cybersecurity addresses different areas of concern focused on protecting national economic interests, addressing security by design, countering ransomware threat, raising threat awareness, training more cybersecurity professionals, and preparing for a post-quantum world. The Fact Sheet’s focus policies include:
- Improving the cybersecurity of our critical infrastructure.
- Ensuring new infrastructure is smart and secure.
- Strengthening the Federal Government’s cybersecurity requirements, and raising the bar through the purchasing power of government.
- Countering ransomware attacks to protect Americans online.
- Working with allies and partners to deliver a more secure cyberspace.
- Imposing costs on and strengthening our security against malicious actors.
- Implementing internationally accepted cyber norms.
- Developing a new label to help Americans know their devices are secure.
- Building the Nation’s cyber workforce and strengthening cyber education.
- Protecting the future – from online commerce to national secrets — by developing quantum-resistant encryption.
- Developing our technological edge through the National Quantum Initiative and issuance of National Security Memorandum-10 (NSM-10) on Promoting United States Leadership in Quantum Computing While Mitigating Risks to Vulnerable Cryptographic Systems.
While the eighth policy on the list addresses a need to help make consumers more aware of the cyber-risks associated with their purchase and use of Internet of Things (IoT) devices, we note the lack of a reference to IoT security within enterprises. Here’s the full text from the Fact Sheet:
“Developing a new label to help Americans know their devices are secure. This month, we will bring together companies, associations and government partners to discuss the development of a label for Internet of Things (IoT) devices so that Americans can easily recognize which devices meet the highest cybersecurity standards to protect against hacking and other cyber vulnerabilities. By developing and rolling out a common label for products that meet U.S. Government standards and are tested by vetted and approved entities, we will help American consumers easily identify secure tech to bring into their homes. We are starting with some of the most common, and often most at-risk, technologies — routers and home cameras — to deliver the most impact, most quickly.”
Consumer and Commercial/Industrial IoT are Vulnerable
First, let me be clear that Ordr supports the efforts to help make people more aware of the risk associated with the connected devices they purchase for personal and in-home use. Often these devices collect sensitive information, or they may be a gateway for threat actors to gain access to a personal network that is relatively unprotected. Very few homes run industrial-grade security products, and are vulnerable to the tools and techniques available to most criminal hackers and hacker groups. But the same threats that put personal IoT devices at risk are present in many of the devices that populate enterprise networks.
Medical devices, industrial controls, sensors, point-of-sale systems, communications equipment, and many more Internet of Medical Things (IoMT), operational technologies (OT), IoT, and other connected devices are notoriously vulnerable to attack. Many of these devices are not built with security as a priority of their design. They operate with obsolete operating systems, rely on default (if any) passwords, and are released to market with security weaknesses. Some industry studies have found that three-quarters of all IoMT devices deployed today have at least one security vulnerability, and that half may have multiple vulnerabilities.
What’s more, the same devices that the White House wants to warn consumers about may also end up connecting to enterprise, industrial, and healthcare networks. Within minutes of deploying Ordr in these environments, our platform automatically discovers and classifies all of the devices operating on the network, and the results have been eye-opening for our customers. Vending machines, smart assistants, and gaming systems are not uncommon; but we’ve also found stranger things like parking gates, Kegerators, Pelotons, and Tesla automobiles.
The same devices that the White House wants to warn consumers about may also end up connecting to enterprise, industrial, and healthcare networks.
Many times, these devices have a legitimate reason to be operating where they are, but if IT and security operations don’t know about them, they present an unrealized risk. That is where Ordr comes in handy. By discovering and classifying every device, then drawing on the deep Ordr Data Lake to gather context and monitor its activity with a granular understanding of its purpose and normal operational patterns, Ordr can uncover vulnerabilities and detect behavioral deviations that are indicators of compromise. When that happens, Order automates policy enforcement to respond immediately to prevent or stop the spread of an attack, while maximizing operational resilience.
IoT Security for Economic Security
Some devices and systems must keep operating even while at risk, and Ordr’s enforcement of segmentation and isolation policies can ensure continued functioning even as the security team takes action to mitigate the present risk. That’s an option that is better than a “code dark” event during which non-technical staff are instructed to disconnect machines from the network altogether.
We applaud the White House’s efforts to use its bully pulpit to advance the cause of cybersecurity. We also urge the administration to continue to use its influence to help make our entire economy safer by recognizing the need to build security-by-design into every connected IoT, IoMT, and OT device. Building on the momentum of the IoT Security Improvement Act of 2020 as well as FDA guidance for IoMT security, bills like the PATCH Act and other requirements are needed to ensure connected devices are built and delivered to be secure. If labeling consumer devices is important, it must also be a priority for commercial devices as well.
Danelle Au
Danelle Au has more than 20 years of experience bringing new technologies to market. Prior to Ordr, she was CMO at Blue Hexagon, a deep learning for malware protection company, and CMO at SafeBreach where she helped build the marketing organization and and define the Breach and Attack Simulation category. Previously, she led strategy and marketing at Adallom, a cloud security company acquired by Microsoft. She was also Director, Security Solutions at Palo Alto Networks, driving growth in critical IT initiatives like virtualization, network segmentation and mobility. Danelle was co-founder of a high-speed networking chipset startup, co-author of an IP Communications Book and holds 2 U.S. Patents. She has an MSEE from UC Berkeley
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
Knowledge BaseWhat is IoMT?
…and first responders to track patient metrics outside of the hospital setting. In addition to mobile and emergency care, community IoMT also involves technologies that enable remote services. For example,…
What is IoMT?
4Min ReadThe Internet of Medical Things (IoMT) is the network of Internet-connected medical devices, hardware infrastructure, and software applications used to connect healthcare information technology. Sometimes referred to as IoT in healthcare, IoMT allows wireless and remote devices to securely communicate over the Internet to allow rapid and flexible analysis of medical data.
IoMT’s impact on the healthcare market is undeniable and irreversible. Some healthcare technology market analysts expect the IoMT market is expected to reach $861.3 billion by 2030.
The broader Internet of Things (IoT) includes the network of all Internet-connected devices, including: internet connected factory equipment, biometric cybersecurity scanners, and autonomous farming equipment. IoMT is focused specifically on healthcare and medical applications. Given the sensitivity and strict regulations around healthcare data, IoMT requires a more comprehensive security infrastructure than other IoT systems.
How is IoMT impacting healthcare?
IoMT impacts the healthcare industry in myriad ways. These changes can be seen most notably when deploying IoMT in-home, on-body, in the community, and in-hospital:
In-Hospital IoMT
Hospitals must manage the quality and supply of their medical assets over time, and they also need to understand how personnel and patients are moving throughout the premises. Healthcare professionals use IoMT sensors and other tracking systems to track all of these interactions so that administrators can get a comprehensive understanding of what is going on.
In-home IoMT
In-home IoMT allows people to transmit medical data from their home to other locations such as their primary care provider or a hospital. For instance, remote patient monitoring (RPM) is the use of medical devices to transmit metrics such as blood pressure or oxygen saturation from recently discharged patients to their hospital for review by their doctors. This can reduce hospital readmissions by catching issues before they become serious.
Telehealth—the use of communication technologies for remote healthcare services—provides further flexibility by allowing recently discharged patients to resolve minor issues by remotely connecting with their doctors.
The use of IoMT devices along with telehealth can also be useful for ongoing care outside of the patient setting. For example, personal emergency response systems (PERS) can track events—such as a fall or heart attack—to automatically call for help. PERS can provide security to at-risk people such as seniors that want to live at home without compromising their safety.
On-body IoMT
On-body IoMT is the use of wearable medical devices that are connected to remote tracking or monitoring systems. Unlike in-home IoMT, on-body IoMT can often be used outside of the home as people live their normal lives.
Consumer on-body IoMT devices are wearable devices that anyone can buy to track health metrics for both personal use and for sharing with healthcare providers. In addition to tracking a standard metric, such as heart rate, these devices can be early warning signs for more serious health conditions. For example, the Apple Watch can warn users about irregular heart rhythms.
Clinical on-body IoMT devices are like the consumer devices but afford a wider array of sensor options. For instance, glucose sensors can be worn by diabetic patients to alert them to fluctuations in glucose levels. Many of these devices can share data directly with a patient’s doctors to ensure they get fast and accurate treatment.
Community IoMT
Community IoMT is the use of IoMT devices throughout a broader town or geographic area. For example, mobility services are devices used to track patients while in transit in a vehicle. Similarly, emergency response intelligence systems are used by paramedics and first responders to track patient metrics outside of the hospital setting.
In addition to mobile and emergency care, community IoMT also involves technologies that enable remote services. For example, point of care devices can be used by healthcare providers in non-traditional medical settings such as a field hospital, and kiosks can be used to dispense medicines to people in areas with limited or no access to traditional infrastructure.
Suppliers may also use IoMT devices in logistics to help in the transport of healthcare goods or medical equipment. For instance, sensors can monitor temperature- or pressure-sensitive shipping containers to ensure that quality is maintained throughout the shipping process.
IoMT Challenges
IoMT comes with some unique legal, regulatory, technical, and privacy challenges, mainly because the IoMT ecosystem has so many stakeholders, including:
- Medical device providers
- Connectivity providers
- Original equipment manufacturers (OEM)
- Systems/software providers
- System integrators
- End users
Legal challenges
When IoMT devices generate and share data, it is not always clear who legally owns that data. For example, if a city-owned medical device captures data from a patient, stores the data in a third-party cloud application, and shares the data with a private healthcare organization … who owns the data? The city? The patient? The software provider? The healthcare organization?
There are many ways the different parties can use and share the data. The owner may have the right to destroy the data, which can be complicated in a distributed network where data is potentially replicated many times.
Regulatory challenges
Due to the sensitivity of medical data, there is significant regulation about how and where it can be used, along with specifications about how the technology should be secured. For instance, the FDA released comprehensive guidance about the Management of Cybersecurity in Medical Devices.
The European Union, the United Kingdom, and organizations such as the Association for the Advancement of Medical Instrumentation and the European Commission, released additional guidance and regulation around these devices.
However, even with all the regulations and guidance issued, 66% of respondents in the Deloitte study said they believe that the regulatory framework will not catch up with what is possible today for another five years.
Technical challenges
Given the distributed nature of IoMT infrastructure, the devices and software systems must be able to communicate securely with one another. However, the protocols and security standards for these types of integrations change constantly. This can cause compatibility issues as new technologies are introduced if older systems cannot keep up to date with these changes.
Privacy and security challenges
IoMT data typically flows through the public Internet and is exposed to more security threats than are present in a firewalled private network. This threat is compounded by the fact that the data is shared among many systems, providing multiple attack vectors.
OEMs must use industry best practices around security, and administrators should use the latest encryption protocols, using unique and complex passwords for access and validating the SSL certificates of remote systems.
Getting it right: How to secure IoMT devices
There are many variables at play in IoMT security, and there is no simple way to secure all medical devices against all types of threats. However, a basic first step is to ensure that you know which medical devices exist on your network, and the types of threats that may impact them.
Ordr recommends a zero trust network security model, in which communication among devices is controlled by strict access control and authentication to ensure traffic is coming from where you think it is. Ordr Systems Control Engine (SCE) can enable visibility and security of all your connected medical devices. Try a demo of Ordr to learn how to keep your IoMT devices—and the data they collect and share—safe and secure.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
Knowledge BaseThe Increasing Importance of Cybersecurity Asset Management
…may come and go as application instances spin up and down in response to fluctuations in demand, for instance, and cloud services may change their configurations continuously as they scale….
The Increasing Importance of Cybersecurity Asset Management
5Min ReadIn the world of cybersecurity, you can’t secure something if you don’t know it exists. That’s why cybersecurity asset management is a critical component to the foundation of cybersecurity operations across businesses of all types. By allowing your security team to maintain a real-time directory of IT assets—as well as the associated security risks—cybersecurity asset management is foundational to achieving a “whole enterprise” approach to a proactive, end-to-end, security strategy.
What is cybersecurity asset management?
Cybersecurity asset management is the process of identifying, on a continuous, real-time basis, the IT assets that your organization owns and the potential security risks or gaps that affect each one.
In this context, assets take many forms. They could be traditional devices, like PCs and servers. Or, they could be specialized IoT, IoMT, IIoT, or OT devices or software-defined resources, like a cloud-based database or a company-owned domain.
Any device, resource or service that exists within your IT estate could be subject to risks or vulnerabilities that lead to a breach of the individual resource and your network as a whole, in the event that attackers use one compromised resource as a beachhead to launch a broader attack.
Why is cybersecurity asset management important?
Cybersecurity asset management empowers your security team, as well as the overall business, with the visibility it needs to build a comprehensive security strategy that mitigates threats quickly and proactively. Such an approach delivers several key benefits:
- Cybersecurity is not a distraction: With a strong cybersecurity asset management process in place, businesses can deploy new IT services or resources without letting security become a distraction or hindrance. They can make decisions based on business priorities, confident that whichever changes they make, their cybersecurity asset management process will catch potential vulnerabilities.
- Proactive response: Cybersecurity asset management helps ensure that security teams detect threats before they evolve into serious problems. By continuously monitoring the IT estate for new deployments and risks, teams don’t have to wait until they detect an active attack in order to respond.
- Security visibility: If an attack does occur, cybersecurity asset management provides the security team with an inventory of assets and risks that it can use to gain context on what went wrong and when. Instead of having to reconstruct the state of resource deployments and configurations in order to research the origins of a breach or vulnerability, teams have an up-to-date record that they can refer to immediately.
In all of these ways, cybersecurity asset management places businesses in a stronger position to identify and react to security risks. Although cybersecurity asset management is only one component of an effective cybersecurity strategy, it’s impossible in most cases to maintain proactive security operations without cybersecurity asset management in place.
Risks associated with poor cybersecurity asset management
Lack of cybersecurity asset management, or poor implementation of it, does not merely make security operations more challenging. It creates critical risks for the overall business.
Chief among them is a higher risk of business disruptions. If essential data or systems are made unavailable by a breach, the business may not be able to operate. Not only will such disruptions harm the business’s reputation, but they also have serious financial consequences: IT downtime costs businesses $9,000 per minute on average.
Poor cybersecurity asset management also makes it difficult to maintain an continuous and accurate inventory of IT resources. Without knowing what exists where within your business’s IT estate, you are left guessing about where the most serious risks lie. Lack of certainty makes it difficult to deploy security resources efficiently or respond to issues when they arise.
Along similar lines, ineffective cybersecurity asset management undercuts security teams’ ability to operate efficiently. It’s difficult to automate security operations when you lack an accurate listing of which resources and risks exist. Instead, your team is left to find and secure devices manually, which is a poor use of time and money.
Examples of cybersecurity asset management
Because IT resources and security risks come in so many forms, cybersecurity asset management is a process that involves a variety of activities. The exact nature of cybersecurity asset management will vary from one organization to another depending on the types of resources at stake, but following are the cornerstones of the process for the typical business:
- Device discovery and protection: By identifying network endpoints and assessing each one for security vulnerabilities, teams can take immediate steps to address problems by, for example, segmenting insecure endpoints from the rest of the network.
- Vulnerability management: Cybersecurity asset management helps detect and address active vulnerabilities, such as unpatched software running on a device.
- Cloud security: Modern clouds are complex, multilayered environments that consist of a range of services and resource types. Cybersecurity asset management includes the identification of cloud resources that are vulnerable due to insecure software or lack of access control.
- Incident response: When an incident warrants further investigation, cybersecurity asset management plays a role in providing the incident response (IR) team with the information it needs to determine the root cause and remediate.
- Continuous policy enforcement: In the event that a resource violates security policies that your team has defined, cybersecurity asset management enables the rapid discovery and remediation of the problem. When new devices are added to the network that match a particular device profile with an active policy, they are automatically protected.
Remember that many of the resources described above change constantly. Network devices may come and go as application instances spin up and down in response to fluctuations in demand, for instance, and cloud services may change their configurations continuously as they scale. This is why cybersecurity asset management processes must be performed continuously and in real-time, in order to keep up to date with rapidly evolving environments.
Why prioritize cybersecurity asset management?
Historically, organizations placed little priority on cybersecurity asset management simply because the tools necessary to automate cybersecurity asset management processes didn’t exist. It wasn’t practical to maintain real-time and continuous inventories manually.
Thanks to the advent of automated resource discovery and threat identification tools, however, cybersecurity asset management now plays a major role in security operations across a variety of verticals. It’s critical not just for software and IT businesses, but for any organization that relies on software and hardware to power its operations—which virtually every business does today, given that every company is now a technology company.
In manufacturing, for instance, cybersecurity asset management helps ensure that high-value equipment, such as plant control systems, diagnostics and monitoring systems, and machine sensors, remain secure and free of threats that could disrupt operations.
Likewise, cybersecurity asset management protects healthcare organizations, which face high rates of ransomware attacks as well as vulnerabilities that may exist within specialized devices deployed as part of the Internet of Medical Things, or IoMT.
More generally, any enterprise that deploys connected devices to help manage or monitor physical infrastructure, collect business data or extend networks into spaces where conventional infrastructure can’t reach needs cybersecurity asset management to keep those devices—and, by extension, the business as a whole—secure.
How to capitalize on cybersecurity asset management
To deliver fully on its promise, cybersecurity asset management requires the implementation of multiple processes. Businesses must be able to identify, assess and address the security risks posed by devices and assets of all types while taking proactive steps to protect their devices, networks and data. They must also discover and track assets in real time, perform continuous risk assessment and immediately segment untrusted assets from the rest of the network.
The Ordr Systems Control Engine (SCE) gives organizations the tooling they need to automate cybersecurity asset management at scale. Ordr SCE provides holistic visibility and security into network-connected devices, offering a powerful solution to identify, classify and evaluate every network-connected device, then automates steps to remediate risks.
What’s more, Ordr SCE allows security and IT teams to create proactive microsegmentation policies for every class of device in order to control communications and mitigate potential risks.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogA Biomed’s Journey: From the Workbench to Connected Device Security
BlogA Biomed’s Journey: From the Workbench to Connected Device Security…needed to discover and profile IoMT, Internet of Things (IoT), and operational technology (OT) in real-time, and with the clarity that comes from access to the Ordr Data Lake with…
Healthcare Security
A Biomed’s Journey: From the Workbench to Connected Device Security
4Min Read
By Benjamin Stock

As threats to healthcare organizations increased, the role of the biomedical technician changed from one of asset management to cyber asset security. Ordr director of healthcare product management Benjamin Stock tells his biomed story and why “whole hospital cybersecurity” matters. In the late 1990s, I was just starting out in my career in tech. As an electronics engineer, I was busy designing and building circuits, installing and maintaining systems, and gaining as much experience as I could to broaden my horizons. I enjoyed the work, but things changed in late 2001, and opportunities in tech contracted dramatically. Looking for stability and a chance to apply my skills in a growth market, I moved to healthcare and became a biomedical technician with little to no understanding of the field and the rewarding experience it offered.
I thrived as a biomed. My background in electrical engineering blended well with the need to integrate and manage the influx of innovative medical technologies that hospitals were using to improve their ability to deliver positive patient outcomes. I soon earned my CBET certification, and over the coming years, progressed to a BMET 2 and then BMET 3.
ACA Changed Healthcare Cybersecurity Dynamics
Around that time, the Affordable Care Act (ACA) was passed, and with it came a push to accelerate the adoption of electronic medical records (EMR). That meant the devices I was working with were now becoming connected to the hospital network to improve workflows and reduce errors. I saw the risks that came along with that trend, so I began investigating what protections were in place to ensure patient safety and privacy. Manufacturers were frantically adapting products to meet the needs of rapidly changing care delivery strategies. These adaptations, although functional, did not take cybersecurity into account. Recognizing the danger that network-connected medical devices posed to IT networks in healthcare environments, I began working closely with security teams to help them understand these unfamiliar technologies and how they affected security and IT operations, but also impacted patient care.
Recognizing the danger that network-connected medical devices posed to IT networks in healthcare environments, I began working closely with security teams to help them understand these unfamiliar technologies and how they affected security and IT operations, but also impacted patient care.
Back then, IT management was laser-focused on protecting data and systems; patient safety was not a part of their mandate. But unlike installing or servicing a server, you can’t just take something like an infusion pump or patient monitor offline if there’s an update needed. Nothing works in a bubble in IT once it is connected to the network. There are downstream effects, security implications, and new regulatory regimes to satisfy. That meant we had to rethink our approach to the design and management of the emerging healthcare IT estate. Biomeds were now working alongside traditional IT management to address the influences of things like connected medical device inventory, patching strategies, vulnerability management, and cyber risk assessments.
The Start of Whole Hospital Cybersecurity
Looking back, it was the start of what at Ordr we call the “whole hospital” approach to protecting healthcare IT environments, and that is what attracted me to Ordr. I knew firsthand how difficult it was for Healthcare Technology Management (HTM) and IT management to discover, identify, manage, and secure their Internet of Medical Things (IoMT) devices. Traditional methods for conducting IoMT asset management (often including manual labor) are slow, inaccurate, and error prone. The result is an incomplete, moment-in-time snapshot of what devices are operating on the network and an inaccurate assessment of where the risks are.
Traditional methods for conducting IoMT asset management (often including manual labor) are slow, inaccurate, and error prone. The result is an incomplete, moment-in-time snapshot of what devices are operating on the network and an inaccurate assessment of where the risks are.
But with the Ordr whole hospital approach to healthcare IT security, CISOs have the tools needed to discover and profile IoMT, Internet of Things (IoT), and operational technology (OT) in real-time, and with the clarity that comes from access to the Ordr Data Lake with its rich library of profiles on millions of devices. The Ordr technology suite enables Biomedical Engineers/HTMs, CISOs, and IT operations managers to embrace the SEE, KNOW, SECURE philosophy of connected device security with the confidence that comes from knowing you have accurate information and precise insights for decision making—and automations to act quickly when threats arise.
Five Keys to Improving Healthcare Cybersecurity
Ordr delivers value for healthcare organizations in five important ways:
- Automating asset inventory to identify what’s connected to the hospital network. Ordr discovers and monitors every connected device in real time, understands how devices connect and communicate on the network, and provides insights to locate devices across the environment. This allows hospitals to allocate resources doing manual inventory to higher value tasks, and enables HTM and security teams to easily locate devices for maintenance or incident response.
- Know risks and vulnerabilities such as devices with outdated operating systems and vulnerabilities, complete with device risk scores. This information enables teams to know their attack surface, prioritize patching and reduce risk. It also addresses a key security gap as some devices like medical and IoT devices are typically not scanned by traditional vulnerability management solutions because of impact to operations.
- Improving collaboration between teams HTM, security, and IT teams by providing a complete picture of every device, with deep context (serial number, manufacturer, model, operating system, and more), understanding of how devices interact, device owners and device utilization. Operating from a single source of truth about assets improves hospital efficiencies.
- Detecting threats such as devices with exploits, communicating to malicious domains, or behaving abnormally. Ordr can automate workflows to assign tickets to the appropriate device owner, or create segmentation policies to limit compromised devices to “baseline” behavior.
- Demonstrate ROI not only in the context of device management and security, but by maximizing medical device utilization efficiency. By understanding how devices are being used, and when, hospitals can identify areas of over or under usage, manage maintenance schedules and optimize capital spend.
I recently recorded a webinar with more information about connected device security for healthcare organizations. If you have questions about how Ordr can help your organization compile, track, and manage its complete asset inventory in real-time, improve its security posture through the whole hospital approach, and effect better utilization of its existing medical devices, reach out and let us know.
Benjamin Stock
Benjamin Stock is the Director of Healthcare Product Management at Ordr. Previously, Ben worked as the Director of Clinical Equipment Systems and Project Support at SSM Health St. Louis, MO. With more than 15 years of experience in healthcare technology management, his wealth of knowledge in the Clinical Engineering space allows him to be a wonderful advocate for Ordr healthcare customers. Ben is also a Certified Biomedical Equipment Technician (CBET).
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogCarousel Industries and Ordr: Uncovering the IoT Surprises
BlogCarousel Industries and Ordr: Uncovering the IoT Surprises…free 30-day trial with the IoT Discovery Program. You’ll receive access to the Ordr dashboard and a zero-touch sensor that’s quick and simple to deploy. Ordr’s powerful solution and Carousel’s…
Security Strategy
Carousel Industries and Ordr: Uncovering the IoT Surprises
Hiding Within Your Network
3Min ReadBy Jason Viera

First, some straight-up pragmatism: IoT devices probably won’t get much more secure as time goes on. There’s just not enough impetus for manufacturers to add security capabilities. Couple that lack of onboard security with the fact that IoT usage is rapidly increasing, and the onus falls on IT to address the shortcomings of this evolving Internet of (Insecure) Things so new connections don’t introduce vulnerabilities.
Tools already exist to monitor and manage IoT devices but few follow Leonardo da Vinci’s time-tested premise, “Simplicity is the ultimate sophistication.” Instead, most require too much administration time and in-the-weeds configuration to make them truly effective. That leaves organizations with haphazard deployments, misconfigurations, diminished value from their tech investments, and countless IoT devices prowling the network without proper oversight.
By contrast, Ordr helps enterprises solve IoT risks with a solution that’s refreshingly sophisticated in its simplicity. Powerful and quick to deploy, Ordr hunts down IoT devices on the network, categorizes them and shows you what they are, who they’re talking to, and what they’re doing. To test its usability – its power to deliver insight into IoT activities as well as the ability to launch it quickly and use it effectively – I tried Ordr myself through their IoT Discovery Program.
Simple? Check. Deploying the Ordr sensor on my home network couldn’t have been simpler. I removed it from the box, plugged it into my network, and set up a SPAN session to send all my traffic to it. Then I grabbed some food from the kitchen. Back at my desk, sandwich in hand, I saw the sensor was already hitting security solution pay dirt.
Powerful? Definitely. Along with discovering traditional Windows devices, Ordr showed me the Raspberry Pi that I forgot was on the network and my Garmin watch, which I didn’t realize had wireless enabled. Then things got really interesting as Ordr presented information about what was happening on my network, automatically categorizing my devices and displaying flows. It revealed that my son’s machine was talking to places overseas it shouldn’t have been – and with command and control (C2) traffic, no less! I immediately remediated that issue, something I would never have known about if I hadn’t plugged Ordr into my network.
Quick? Ordr’s value became apparent right away. I didn’t fiddle around with configurations. I didn’t even have to impact my network traffic. Watching the sensor do its work was simplicity in motion and the insight I gained after just a few minutes was eye opening. Things had been happening on my network for how long without me knowing about it?
What IT organization wouldn’t want that level of visibility into their own IoT frontier?
Having real-time insight into your network is particularly important because other departments might deploy IoT devices without IT’s knowledge, often referred to as “shadow IoT.” The concept of shadow IoT isn’t about rogue employees with malicious intent. Instead, IoT – along with Operational Technology (OT) and Internet of Medical Things (IoMT) devices such as patient heart monitors, indoor air quality sensors, and automated equipment controllers – enable desirable outcomes for so many functional areas that they’re bound to wind up in your enterprise because employees think they’re doing something good. Unfortunately, the need for security never crosses their radar.
A real-world example illustrates how quickly unmanaged IoT access can turn messy. A highly secure organization working with the Department of Defense (DoD) hired a third party to conduct penetration testing. The pen test vendor was granted physical access to the building and noticed digital signage in the hallway outside the conference room reserved for their work. They got the IP address of that IoT device, discovered it was running an old, unpatched version of Linux, and obtained Microsoft Active Directory credentials into the environment. The digital signage was innocuous, intended to benefit the organization’s users, but it hadn’t been secured against intrusion.
And so, we come back to da Vinci and his penchant for simplicity. Ordr’s effectiveness is built on simplicity. You don’t have to manually sift through and categorize hundreds or thousands of IoT devices, some of which you probably didn’t expect to find. The platform does the work for you, using easily-deployed out-of-band sensors and Ordr’s powerful AI-driven database of devices, well beyond traditional Network Access Control (NAC) device discovery. Its speed stems from the ability to monitor the network in real-time, automatically assigning categories when it spots something new. Ordr solves a big Day Two challenge for enterprises struggling to keep pace with an IoT device list that’s constantly growing. In businesses where shadow IoT is hard at work, this task is even more overwhelming – and more critical.
The time to take control of your IoT environment is now. To help you get started, Carousel and Ordr are offering a free 30-day trial with the IoT Discovery Program. You’ll receive access to the Ordr dashboard and a zero-touch sensor that’s quick and simple to deploy. Ordr’s powerful solution and Carousel’s deep expertise will be behind at every step to simplify the complexities of IoT device security, and at the end of your trial you’ll receive a complete IoT Discovery Report.
What will you see when you add Ordr to your network?
Jason Viera
Jason Viera is Chief Technology Officer for Carousel Industries. As CTO, he is responsible for spearheading and shaping the vision of Carousel’s technology strategy to help innovate and cultivate new opportunities for its more than 6,000 clients. As CTO, Jason is laser-focused on continuously strengthening Carousel’s range of services and solutions and ensuring client satisfaction through the company’s engineering talent and masterfully designed solutions. Jason is the driving force behind the launch of Carousel’s Office of the CTO whose mission is to align the company’s engineering talent with customers to advance their business outcomes. Through client engagement activities, The Office is responsible for driving unbiased strategic innovation for both Carousel and its customers. Additionally, The Office vets and adds new technology solutions to its portfolio to provide further value to customers as they continue their digital transformation journey. Before serving as CTO, Jason was previously Senior Director of Infrastructure Solutions for Carousel. In this role, he worked with customers across multiple verticals to address their challenges with end-to-end architectures to meet their business and technical requirements. Prior to Carousel, he served in several engineering and leadership positions for Cisco Systems, Amgen, and Proctor & Gamble. Jason is a Tech10 Award winner, a member of the Forbes Tech Council, and is a frequent contributor to Network World, CRN, Channel Futures, and several other leading IT and business publications. Jason has over two decades of industry experience and more than a dozen industry certifications.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogCyber Insurance And Cybersecurity Controls:
BlogCyber Insurance And Cybersecurity Controls:…quickly, and the tools available to them were becoming more effective. As new threats emerged, the insurance industry struggled to keep current. Fast-forward to 2020 and, with the outbreak of…
Risk Management
Cyber Insurance And Cybersecurity Controls:
Straight Answers for a Confusing Market
5Min Read
By Danelle Au

Recent developments have caused confusion in the cyber insurance market. Ordr looks at recent trends affecting cyber insurance and security controls to offer insights and straight answers for enterprises looking to buy or renew policies. There has been a lot of confusion about the future of cyber insurance following recent statements by market makers Lloyd’s of London and Zurich Insurance Group. In late 2022, Lloyd’s informed underwriters in its syndicate that they would be required to explicitly exclude coverage for damages related to state sponsored cyberattacks. More recently Zurich CEO Mario Greco told the Financial Times, “What will become uninsurable is going to be cyber,” adding that if a threat actor “takes control of vital parts of our infrastructure” the results may be uninsurable.
Those statements, coupled with well publicized policy price increases for 2023 that are as much as three times higher than what many customers paid the year before, have fueled concerns that cyber insurance coverage may be unavailable in the near future and that many underwriters may simply get out of the business. In many ways what we are seeing is the maturation of what remains a relatively new market trying to find its footing in a dynamic threat and risk landscape. Because of that, questions and confusion are rampant, and rational answers from seasoned experts are needed. That is why Ordr recently convened the Cybertrends and the Impact on Cyberinsurance webinar with Marc Schein, national co-chair, cybersecurity center of excellence, Marsh McLennan Agency, and Jim Brady, vice president cybersecurity and risk management, and CISO at Fairview Health.
A Little History
For context, the first cyber insurance policy was written in 1997 by AIG and, according to The Insurance Journal, “Covered only third party suits arising from breaches originating from outside the company.” Optimism for the insurance industry’s first new product category in decades was high, but as underwriters began entering the market in the early 2000s, the challenges associated with an increasingly difficult threat landscape became evident. The number of threat actors, including lone wolf hackers, criminal syndicates, and state-sponsored adversaries, was growing quickly, and the tools available to them were becoming more effective. As new threats emerged, the insurance industry struggled to keep current.
Fast-forward to 2020 and, with the outbreak of Covid-19, things got bad. In the chaos of a global pandemic threat actors took advantage and began focusing on the use of ransomware. Few organizations were prepared for the attacks, and the insurance industry’s risk calculations were turned upside down. Schein said many “underwriters were paying out more in claims than they were collecting in premiums because they were unprepared for the rise in ransomware.”
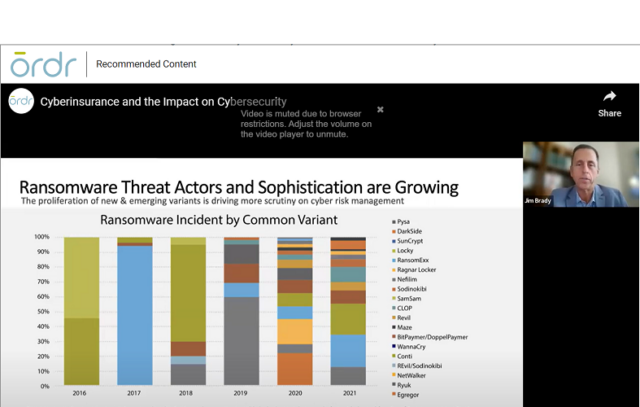
Ransomware Disruption
According to Marsh, there were 4,000 ransomware attacks per day in the U.S., and the cost to the insurance industry was $20 billion in 2021. Then, in 2022 with the outbreak of hostilities between Russia and Ukraine there was another sudden shift in the industry’s risk calculus. The potential for acts of cyberwar targeting critical infrastructure and industry, coupled with continued escalating risks for industries like healthcare, forced the insurance industry to make numerous adjustments to its risk assessments, culminating in steep premium increases along with policies and exclusions written with greater specificity.
In hindsight these changes shouldn’t come as a surprise. If anything, organizations that used cyber insurance as a major part of their risk management strategy had been getting a great deal. But as the industry has become more educated on the risks, that experience is now forcing organizations to (finally) take their own cybersecurity programs more seriously. No more cutting corners. Instead, to qualify for coverage, savvy insurers are demanding that organizations be able to demonstrate that they have complete visibility and understanding of their IT estates, and have implemented controls sufficient to protect their assets.
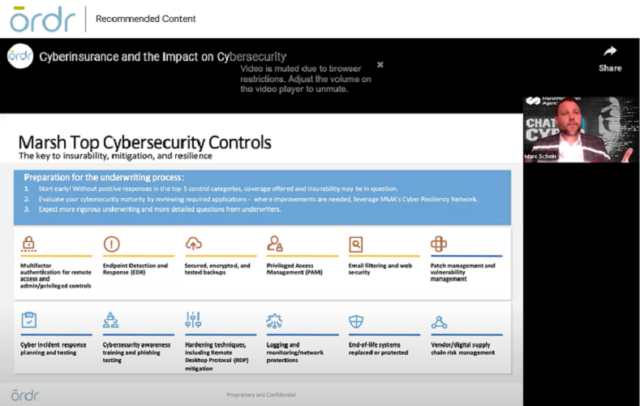
Gain Control
As an early player in cyber insurance, brokerage, risk management, and reinsurance services firm, Marsh McLennan has been a leader in its industry with a deep understanding of what it takes for customers to protect themselves from cyberthreats. The firm offers a list of twelve security controls it requires of its customers that Schein shared during the webinar–along with the caveat that a failure to demonstrate use of the first five is likely to disqualify the organization for coverage. Those twelve controls are:
- Multifactor authentication (MFA) for remote access and admin/privileged controls
- Endpoint detection and response (EDR)
- Secured, encrypted, and tested backups
- Privileged access management (PAM)
- Email filtering and web security
- Patch management and vulnerability management
- Cyber incident response planning and testing
- Cybersecurity awareness training and phishing testing
- Hardening techniques, including remote desktop protocol (RDP) mitigation
- Logging and monitoring/network protections
- End-of-life systems replaced or protected
- Vendor/digital supply chain risk management
The Marsh checklist signals a growing savvy within the industry that knows more information means more accurate risk assessments. As Robert Parisi, North American head of cyber solutions for Munich Re recently told the Wall Street Journal, “The underwriting is aggressively moving toward, ‘How can we get a deeper, more insightful look.’”
What’s missing on this checklist? In the webinar, we raised the question of why asset visibility, security, and segmentation were not included in the list of controls. In fact, the broad “endpoint detection and response”, “patch management and vulnerability management,” and “end-of-life systems replaced or protected” all require visibility into assets and the risks they bring.
Deeper Insight
That requirement for deeper insights into the customer’s risk posture can translate to an advantage for some organizations when shopping for a cyber insurance policy. The ability to provide proof of asset visibility across their entire enterprise can mean a stronger position when shopping for a policy and negotiating with potential underwriters. Brady discussed the advantages Fairview has enjoyed by “coming to the table ready to roll” with necessary controls fully documented. This includes proof the organization has gone beyond an insurer’s requirements by implementing complete asset inventory management and network segmentation to ensure the organization’s ability to quickly detect and effectively mitigate risks.
How can you even detect something bad going on [with a device] if you don’t even know you have it?”
Jim Brady Fairview Health“How can you even detect something bad going on [with a device] if you don’t even know you have it?” Brady asked, highlighting the strategic advantage of having complete device visibility across the entire network.
Good News
Schein agreed, and delivered surprisingly good news when he said, “If you are engaging better controls and you do improve your security posture, the marketplace is getting significantly better.” He then shared that, even as sharp premium increases grab headlines, 14% of Marsh’s customers enjoyed a price decrease by aggressively improving their overall security posture.
If you are engaging better controls and you do improve your security posture, the marketplace is getting significantly better.”
Marc Schein Marsh McLennan AgencyClearly, security leaders that have invested in maturing their cybersecurity program with asset management, and excellent controls at the core are reaping the benefits by not only hardening their enterprises against attacks, but by reducing their overall risk profile. Many security leaders recognize that Ordr can play a key role in that equation by giving its customers the ability to see across the entire enterprise to continuously discover and classify an organization’s complete connected device inventory. What’s more, the Ordr Data Lake ensures deep insight into every device’s risk profile with a real-time understanding of communications and operational behavior that could signal an indicator of compromise. Those insights can trigger dynamically created security policies that can be quickly enforced to prevent or contain an attack, and also give insurers confidence that they are working with a customer that takes the concept of Zero Trust seriously and employs strong risk reduction practices.
Danelle Au
Danelle Au has more than 20 years of experience bringing new technologies to market. Prior to Ordr, she was CMO at Blue Hexagon, a deep learning for malware protection company, and CMO at SafeBreach where she helped build the marketing organization and and define the Breach and Attack Simulation category. Previously, she led strategy and marketing at Adallom, a cloud security company acquired by Microsoft. She was also Director, Security Solutions at Palo Alto Networks, driving growth in critical IT initiatives like virtualization, network segmentation and mobility. Danelle was co-founder of a high-speed networking chipset startup, co-author of an IP Communications Book and holds 2 U.S. Patents. She has an MSEE from UC Berkeley
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
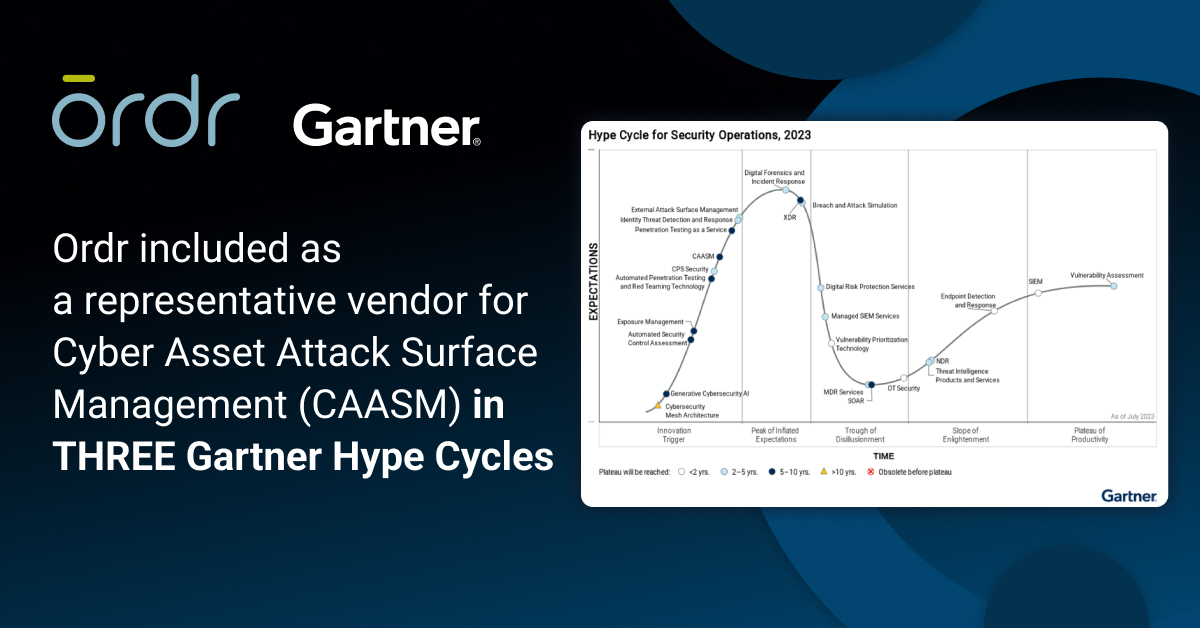 BlogWhat is Cyber Asset and Attack Surface Management?
BlogWhat is Cyber Asset and Attack Surface Management?…to detect assets containing outdated software, misconfigurations, and other vulnerabilities, CAASM tools use API integrations to connect with existing data sources of the organization. These tools then continuously monitor and…
General
What is Cyber Asset and Attack Surface Management?
3Min Read
By Danelle Au

Ordr named a representative vendor for cyber asset attack surface management (CAASM) in 3 Gartner Hype Cycle reports including Hype Cycle for Security Operations, Hype Cycle for Cyber Risk Management, and Hype Cycle for Workload and Network Security. Gartner analysts have been busy publishing several Hype Cycles recently. If you’re not familiar with the Gartner Hype Cycle, it is a graphic representation of the maturity lifecycle of new technologies, and there are several key reports to help security leaders with their strategy and investments. We are thrilled to be included as a representative vendor for Cyber Asset Attack Surface Management (CAASM) category in three Gartner Hype Cycles:
- Hype Cycle for Security Operations, 2023
- Hype Cycle for Cyber Risk Management, 2023
- Hype Cycle for Workload and Network Security, 2023
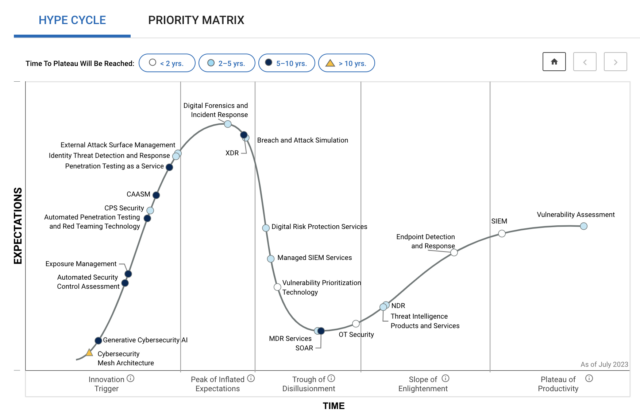
Figure 1: Gartner Hype Cycle for Security Operations, 2023 What is Cyber Asset and Attack Surface Management (CAASM)?
As described by Gartner, “Cyber Asset Attack Surface Management (CAASM) is an emerging technology that is focused on presenting a unified view of cyber assets to an IT and security team. These assets can serve as an attack vector for unauthorized users to gain access to a system to steal information or launch a cyber attack. In order to detect assets containing outdated software, misconfigurations, and other vulnerabilities, CAASM tools use API integrations to connect with existing data sources of the organization. These tools then continuously monitor and analyze detected vulnerabilities to drill down the most critical threats to the business and prioritize necessary remediation and mitigation actions for improved cyber security.”
In Ordr deployments, we don’t just aggregate data via API. We also perform our own asset discovery, via Ordr Discovery Engine and Ordr Software Inventory Collector for the most comprehensive visibility into every asset on the network.
Use Cases for Cyber Asset and Attack Surface Management
There are a number of use cases for cyber asset and attack surface management for security teams:
- Asset management – provide granular visibility across all devices (IT, Internet of Things (IoT) and operational technology (OT) assets), installed applications, SaaS and cloud workloads including detailed information about device type, manufacturer, OS version, vulnerabilities.
- Compliance assessment – during an audit, the process to provide details of assets, and the software, antivirus or applications that are running on them, can be very cumbersome if done manually. CAASM can simplify this process.
- Security gaps – identify security gaps across the network, for example, assets that should have a security endpoint agent but do not or assets that are running outdated operating systems.
- IT governance – identify shadow IT devices or assets that should not be on the network, such as gaming devices. Ordr goes a step further and can help with asset reconciliation, for example, comparing what assets we see on the network versus what is actually in the CMDB or vice versa. We can also identify devices that we discover on the network or are missing on the network in the last 24 hours.
- Vulnerability management – identify vulnerabilities associated with assets. Most CAASMs only ingest vulnerabilities from various source systems. Ordr goes further with asset risk scores and vulnerability management details from our ecosystem of integrations (via API), along with Ordr Software Inventory Collector details. Ordr delivers visibility into vulnerabilities on IoT and OT devices that are are typically blind spots for other CAASM vendors.
These use cases are all fundamental CAASM use cases. But, they are just scratching the surface of what’s possible with Ordr. Enterprise security teams deploying Ordr can also expand to deep behavioral intelligence, threat detection and segmentation for mission-critical IoT and OT assets. Because Ordr also maps communications flows for every asset, we can also support the following use cases:
- Baseline flows – the ability to baseline normal communications patterns for every device is critical to identify malicious and anomalous traffic. This can include devices communicating to the Internet, manufacturing or medical devices in the guest VLAN, or devices that are communicating to a malicious command and control domain.
- Bidirectional integrations – Any asset details that we aggregate and correlate is shared with more than 80 networking and security integrations. For example, granular asset and vulnerability details can be shared with CMMS, CMDB, SIEM and traditional vulnerability management solutions like Rapid7, Qualys and Tenable. This ensures a consistent source of truth on all assets and risks across the entire organization.
- Automated policies – Finally, with Ordr, because we have details on assets, connectivity and communications flows, we can dynamically generate proactive Zero Trust segmentation policies to secure devices (to allow only sanctioned, normal communications) or dynamically generate reactive policies to block ports, terminate sessions or move devices to different VLANs during an incident.
Check out a recent Demo Forum panel hosted by Richard Stiennon on Cyber Asset and Attack Surface Management. Ordr’s own Jeremy Haltom participated, and summarizes our value proposition.
In summary, there are many benefits to CAASM, primarily with optimizing resources via automated inventory of what’s on the network. Additionally, with the granular details on risks for every device, organizations can reduce their attack surface, improve operational efficiencies, and streamline compliance assessments. Ordr extends these benefits to even more comprehensive security capabilities, and actionable policies on existing infrastructure that can accelerate incident response by hours.
For more information on the Ordr platform, contact us.
Danelle Au
Danelle Au has more than 20 years of experience bringing new technologies to market. Prior to Ordr, she was CMO at Blue Hexagon, a deep learning for malware protection company, and CMO at SafeBreach where she helped build the marketing organization and and define the Breach and Attack Simulation category. Previously, she led strategy and marketing at Adallom, a cloud security company acquired by Microsoft. She was also Director, Security Solutions at Palo Alto Networks, driving growth in critical IT initiatives like virtualization, network segmentation and mobility. Danelle was co-founder of a high-speed networking chipset startup, co-author of an IP Communications Book and holds 2 U.S. Patents. She has an MSEE from UC Berkeley
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?