Search Results:
”Quiz 2024 SAP C-ARSOR-2308: Marvelous SAP Certified Application Associate - SAP Ariba Sourcing Valid Dumps Book 🐮 Open ▷ www.pdfvce.com ◁ and search for ➥ C-ARSOR-2308 🡄 to download exam materials for free 🏑C-ARSOR-2308 Customizable Exam Mode”
-
 BlogSeeing is Not Enough: Cyber Asset and Attack Surface Management Use Cases
BlogSeeing is Not Enough: Cyber Asset and Attack Surface Management Use Cases…for all assets to streamline and automate workflows by creating ITSM tickets with ITSM, SIEM, and SOC systems. Audit and Compliance Reporting: Addressing compliance can be an expensive and time-consuming…
Blog
Seeing is Not Enough: Cyber Asset and Attack Surface Management Use Cases
4Min Read
By Monica Armand
We recently launched our OrdrAI CAASM+ solution, driven by the broad need from our enterprise customers for a platform that unifies asset data for complete visibility and deep context on every asset in their network. CAASM, first defined by Gartner, means “cyber asset and attack surface management,” and is about the increasing need to identify the growing security and management challenges with network connected assets, including devices, users, installed applications, cloud workloads, and SaaS applications.
With the explosive growth of assets (in both volume and diversity) and the corresponding expansion of the attack surface, both security and IT teams find themselves grappling with numerous challenges: from effectively managing asset inventory to pinpointing risks and exposures and ensuring compliance with regulatory requirements.
Recognizing the need for a complete solution to address these pain points, Ordr developed CAASM+ with the belief that merely seeing an organization’s entire asset inventory is not enough. What they truly need is comprehensive, accurate asset visibility coupled with in-depth asset context to tackle critical security and IT use cases head-on. To deliver a CAASM solution that fulfils these use cases, Ordr maintains three fundamental beliefs regarding asset and attack surface management:
- Completeness Asset Discovery: Discovering and classifying every asset on the network, including IoT and OT, and eliminating blind spots is essential functionality for a CAASM solution. These critical assets comprise about 40% of most networks, and most organizations cannot discover or classify them effectively. High level insights about IoT or OT devices and manufacturers are not enough; details about what software is running, where it’s connected, and what it is doing in the network is important.
- High Fidelity Asset Data: The days of “more data is better data” are over. What is important is that a security team has high quality data they can rely on for patching, remediation, and incident response. This means automating the process of correlation, normalization, and deduplication (especially for ephemeral devices) to deliver a single source of trusted asset truth.
- Deep Context and Classification: Finally, a CAASM solution must have granular context and classification to reveal security gaps and vulnerabilities, and prioritize risks based on business impact. Without granular details and classification, organizations can’t align business and technical contexts to build a security strategy that prioritizes their team’s resources on the most critical tasks.
This is what sets CAASM+ apart from other CAASM solutions. Because of our foundation of complete, high-quality, and granular asset data, we provide organizations across all industries with an asset visibility and security solution that solves their most critical asset management use cases. Below we will get into what you can expect from CAASM+ and the top use cases it addresses. In the next several weeks we will publish a series of blogs that dive deeper into each of these so that you can understand why they are important and how Ordr addresses them.
Asset Visibility and Management: Complete and accurate data is foundational for CAASM. By eliminating the need for manual methods and fine-tuning, Ordr CAASM+ provides comprehensive asset oversight with automated inventory capabilities and uncovers hidden gaps in asset management. Ordr addresses critical asset visibility and management challenges that security teams face in their environments such as:
- Automated asset inventory;
- CMDB reconciliation;
- SBOM reporting; and,
- Asset ownership and user insights.
Identify Security Gaps and Coverage Issues: While security teams invest a lot in their security tools each year, determining if their assets are secure and identifying gaps is time-consuming and complex. Ordr CAASM+ simplifies this process by consolidating data from various sources, like vulnerability scanners and endpoint tools, to create a comprehensive cyber asset inventory and then compares tool coverage against this inventory. This improves endpoint security by detecting and addressing endpoint security coverage gaps such as missing EDR and MDM agents. Security teams can use natural language search to easily reveal gaps and continuously monitor for issues like:
- Endpoints missing critical security controls like EDR or MDM;
- Assets banned by the federal government;
- Assets running out-of-date software; and,
- Assets with weak, default, or no passwords.
Vulnerability Prioritization and Management: Identifying and prioritizing critical vulnerabilities puts a heavy burden on security teams. Ordr CAASM+ alleviates this challenge by providing a unified platform for end-to-end vulnerability management, enabling teams to identify, investigate, and prioritize vulnerabilities efficiently. Ordr automatically cross-references data with vulnerability databases, ensuring a comprehensive and up-to-date overview of vulnerabilities across the network. Ordr’s AI/ML mapping and correlation engine and Software Inventory Collector align technical and business priorities, reducing alert fatigue and providing a prioritized list of top risks. Ordr CAASM+ empowers teams to:
- Minimize cyber risk by discovering and understanding the full vulnerability landscape (including IT, OT, IoT, and IoMT).
- Simplify risk prioritization and vulnerability remediation based on asset risk scores tailored to the organization’s risk profile, ensuring that teams can focus on vulnerabilities posing the greatest threat to the business.
- Automate remediation workflows with ITSM workflows that are assigned to the right device owner.
Accelerate Incident Response: Time is critical for incident response teams, and having a centralized asset “database” to analyze incidents is invaluable. Ordr CAASM+ empowers incident response and security teams to act decisively and effectively with complete asset visibility and deep asset context. Sharing this context with SIEM/SOC results in faster and more informed incident response. Ordr CAASM+ also enriches IT tools and incident response data with the most comprehensive, accurate, and trusted insights for all assets to streamline and automate workflows by creating ITSM tickets with ITSM, SIEM, and SOC systems.
Audit and Compliance Reporting: Addressing compliance can be an expensive and time-consuming process, especially because regulations are constantly changing. Ordr’s automated asset inventory and deep asset insights enable teams to easily address and demonstrate compliance for industry and regulatory frameworks with customized dashboard and reports to meet compliance frameworks, including NIST, CIS Controls, Cyber Essentials, DSP Toolkit, CMMC, SOC2, PCI-DSS, and more.
By prioritizing complete asset visibility, high-fidelity data, and deep context, Ordr CAASM+ empowers organizations to address critical asset management challenges, from asset visibility and management, to vulnerability prioritization, incident response, and audit/compliance reporting. Follow along as we explore these benefits and explain how our product effectively addresses each specific use case. If you are ready to learn how CAASM+ can help your organization reduce your attack surface, schedule a personalized demo today.

Monica Armand
Monica is a key member of the Ordr product marketing team, dedicated to linking customers with Ordr products that empower action and diminish asset risk. With prior experience in launching enterprise cybersecurity products across multiple domains—including application security, identity management, and asset management—Monica is deeply committed to introducing innovative technologies that not only solve customer challenges but also facilitate decisive action.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogA Primer on Responding to Ransomware for Users of IoT and IoMT
BlogA Primer on Responding to Ransomware for Users of IoT and IoMT…and technology strategy , the Ordr platform is designed to give you full visibility into all the devices connected to your network, understand their purpose and operation, and automate management…
Healthcare Security
A Primer on Responding to Ransomware for Users of IoT and IoMT
4Min ReadBy Jeff Horne

You are under the constant threat of a ransomware attack, but how do you prepare and react for an incident? Ordr offers you a primer on responding to ransomware attacks for users of IoT, IoMT, OT, and other connected devices and assets. The COVID-19 pandemic is one of those black swan events that is beyond the scope of normal contingency planning and has unpredictable, long-lasting, and highly disruptive consequences. Yet amid the chaos, one thing has been completely predictable: malicious actors quickly exploiting the panic.
Not long after emergency orders were issued and the healthcare industry was preparing for the first wave of patients infected by coronavirus, malicious actors were already bombarding healthcare workers with phishing emails weaponized with ransomware, and exploiting vulnerable remote desktop systems deployed by hospitals to enable a remote workforce and then installing ransomware on hospital systems.
Ransomware is one of the more insidious attacks that can be unleashed by malicious actors. It usually enters an organization through phishing attacks or vulnerable systems deployed on a network’s perimeter. Once the ransomware gains a foothold, the infection spreads through common exploits or open shares, moving laterally from machine to machine and encrypting important data. Then, once the important data is encrypted, the attackers display a message to pay a ransom or else the data will be lost forever; that is followed by instructions for transferring money to the attackers via untraceable cryptocurrency. In most ransomware cases, the requested ransom amount increases over time in an attempt to lure companies to act fast and pay a lower ransom payment. UCSF was recently targeted by the Netwalker ransomware and paid $1.14M to recover their data.
Hospitals and other healthcare organizations are especially susceptible because many of their mission-critical, internet-connected devices—including medical devices—run vulnerable operating systems that cannot be patched. Some examples include nursing station that have to interact with legacy systems that, in turn, have out of date operating system requirements; or expensive imaging equipment which runs on unsupported and unpatchable versions of WindowsXP. Our Rise of the Machines: 2020 Enterprise Risk and Adoption Report found that 15-19 percent of deployments had IoT devices running on legacy operating systems Windows 7 (or older).
By some estimates there are nearly 650 million IoT and IoMT devices operating in the healthcare industry right now, and 82% of healthcare organizations using IoT/IoMT devices have had those devices attacked.
When a ransomware attack happens:
- Don’t Panic: If you can isolate infected machines, do it quickly. Stop the spread of ransomware by isolating those machines from the network and protecting systems with important information. It is much easier to deal with a few infected machines versus thousands, so identifying and stopping the spread of ransomware should be the primary goal after it has entered the network.
- Research: Ransomware has been around for a long time. Some variants have been well-studied, and free decryption programs are available to defeat them. Once you know what variant of ransomware has hit your network, you may learn that the keys to decrypt your data are easily available and that your infection turns out to be little more than a nuisance. However, newer variants are more virulent, and use sophisticated algorithms that can’t be decrypted.
- Respond: Having assessed your situation and taken the appropriate action to limit the damage, you may still find that your important data is encrypted. This is where the question, “Should I pay the ransom?” comes into play and you have decisions to make. Some points to consider:
- How valuable is your lost data and can you do without it?
- Do you have that data backed up and archived?
- Does losing the data affected by the ransomware put the life of your business at risk?
- Follow the Advisory on Potential Sanctions Risks for Facilitating Ransomware Payments by the U.S. Department of the Treasury to make sure that you are not facilitating payment if, “there is a reason to believe the cyber actor demanding ransomware payment may be sanctioned or otherwise have a sanctions nexus.” This could potentially result in an assessed fine.
- No Guarantees: One major point to consider if you decide to pay the ransom is that, after doing so there is no guarantee of recovery. Keep in mind that attackers are criminals. They may execute an attack campaign, scoop up quick payouts, and then abandon their victims in order to leave a cold trail for investigators. The systems they’ve set up for transferring payment may not work as intended. Or, they may have never intended to cooperate with anyone who made payment in the first place.
Of course, the best thing you can do to respond to a ransomware attack is to take proactive, mitigating actions. Working with trained security experts to assess vulnerabilities, close security gaps, train employees, and put written incident plan in place specific to your organization, and of course having a robust backup strategy for important information before an attack occurs is your best course of action. There are many antivirus and backup tools out there that can prevent or limit the damage of a ransomware or other malware attack.
For organizations that have adopted IoT as a part of their infrastructure and technology strategy , the Ordr platform is designed to give you full visibility into all the devices connected to your network, understand their purpose and operation, and automate management and security policies to ensure maximal protection for even the most sensitive and mission critical equipment. In a worst-case scenario, Ordr can facilitate the rapid isolation and protection of infected devices.
If you have questions about your situation, or need a partner with the skills and expertise to help protect your IoT assets, let us know. We work with a number of excellent integrators and managed security providers who specialize in protecting healthcare and other industries that are heavily invested in the use of connected devices.
Jeff Horne
Jeff Horne is currently the CSO at Ordr where he is responsible for security direction both within Ordr products and internal security. Prior to Ordr Jeff was the VP of Information Security for Optiv where he was responsible for all Security Operations, Governance Risk and Compliance, Endpoint, Internal Incident Response, Physical Security, and Employee Security Awareness groups. Before Optiv Jeff was the Senior Director of Information Security for SpaceX where he was responsible for the overall security strategy of SpaceX and managing the Information Security, Compliance (ITAR), Security Operations, and Physical Security groups. Previous to SpaceX Jeff was the Vice President of R&D and Chief Architect for Accuvant LABS where he managed teams of researchers and consultants specializing in reverse engineering, malicious code, incident response, breach analysis, and vulnerability assessment. Prior to Accuvant Jeff was the Director of Threat Research at Webroot Software where he led several teams of malware researchers, reverse engineers, and a development organization specializing in creating anti-malware functionality and detection signatures for all Webroot products. Jeff began his career as a Vulnerability Researcher at Internet Security Systems where he was responsible for vulnerability discovery, exploit creation, IDS evasion research, and behavioral detection of malware. Jeff is well known for his insight in interviews for numerous news channels and publications, speaking roles at various security conferences, as well as authoring several vulnerability disclosures and patents.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogClosing the Door to Cyber Vulnerabilities at Hospitals
BlogClosing the Door to Cyber Vulnerabilities at Hospitals…were unable to review patients’ medical history or transmit laboratory and pharmacy orders. Unable to restore services and unable to pay a ransom, Princeton Hospital resorted to using paper records. And with…
Healthcare Security
Closing the Door to Cyber Vulnerabilities at Hospitals
5Min Read
By Pandian Gnanaprakasam

Healthcare’s recent and profound digital transformation, with new medical devices, digital services, and applications comes with a high cost of increased cyber risk as networks and attack surfaces become larger and more complex. The health sector has been undergoing a profound digital transformation in recent years. New digital technologies have allowed for important improvements in all the processes of the sector, from medical follow-ups and preventive care to improved diagnosis and patient services. The sector has also seen major improvements to its connected network, administrative and financial systems. The day-to-day life of hospitals is increasingly punctuated by digital technology and more devices are becoming smart and connected. Consider the MRI scanner, insulin pumps or other important assets that are all digitally interconnected. These devices can communicate information on their operating status, provide detailed information on patients and in some devices can even be operated remotely.
Digital transformation affects all sectors, all organizations, both public and private. Healthcare facilities are no exception, especially in terms of cyber security. This transformation of connectivity in hospitals has unfortunately been accompanied by a sharp increase in threats and risks on all the processes involved. Hackers often favor health care institutions because they know that their security investments are not necessarily prioritized and remain lower than for other industries. With hacks at hospitals, the sector can be impacted as a whole as patient confidence decreases and regulatory fines increase. We focus on vulnerabilities in this article, what it is, and how the medical industry should think about risk and some potential ways to isolate, measure and reduce vulnerabilities.
In hospitals, connected objects are everywhere while confidential patient data is becoming digitized across the board. While the rapid development of digitization and connectivity provides for improved efficiency and quality of care, the industry is now wrestling with the increase in threats and the potential risk of information breaches at these hospitals. Sensitive patient information is what cyber attackers are often after. Just recently in October, the FBI issued a warning that ransomware attacks are becoming “more targeted, sophisticated and costly, even as the overall frequency of attacks remains consistent.”
Framing Vulnerabilities at Hospitals
A vulnerability is essentially a fault or a weakness in an environment that can make the collective system unstable. This amounts to leaving, for example, a house unlocked, a door left open, a checklist incomplete. As a result, this “door” can potentially be used by hackers to access the system.
We often find vulnerabilities on computers but the weakness of vulnerabilities can be increasingly found in many other connected devices. In essence, anything that is “coded” can potentially contain vulnerabilities: including firmware, hypervisors, operating systems, libraries, and software. Vulnerabilities may also appear in the way a network or system has been configured. Once a vulnerability exists, a hacker can exploit this weakness for malicious purposes, causing damage to an organization. Every organization today faces attacks from multiple vectors and overall protection and risk management include thoroughly understanding a system’s vulnerabilities.
At hospitals, medical devices themselves can often be the source of vulnerabilities. A study of 24 hospitals in nine countries (EMEA) found that more than half of the hospitals surveyed used standard passwords (ie default settings) to secure their valuable assets. Data is what is often the target for hackers at hospitals and it’s a constant battle to close opened doors and to risk manage vulnerabilities.
What are hackers after? Patient data can be quite valuable and a medical record can sell for $20 to $300 on the darknet, fetching multiples more than credit card data. Hackers also want to create harm and demand ransom in return. Some hospitals have seen had their patient schedule pirated. Scammers in one instance contacted patients to tell them that their consultation was canceled and showed them a different contact number to reschedule an appointment. It can get worse. In 2016, 114,000 patients by a pharmaceutical company were contacted following the detection of a cyber security breach on an insulin pump model. The control box had a vulnerability that, if it had been exploited, could have allowed the patient to inject a potentially lethal dose of insulin.
Vigilance is Needed
Hospitals have to deal with many security issues and if anything the the number of incidents seem to be on the rise. This is happening while devices being connected to the hospital network is growing at +20% per year.
- Theft of scanned records containing medical history, test results, and ongoing treatments.
- Misuse of social security and financial data of patients.
- Partial or total interruption of access to databases.
- Partial or total destruction of the information contained in the databases.
Not Easy for Hospitals
It can be particularly difficult for hospitals to close the door on vulnerabilities. Oftentimes, hospitals are working under regulatory constraints, too many disparate systems and limited overall security and network visibility. Hospitals also have to deal with the lack of resources, training, multiple remote site, and branches. While the headquarters and data centers can be fortified, hackers are all too aware that a remote, unprotected connected site can be an easy on-ramp to the overall healthcare system, exposing yet another key vulnerability.
Cyber Risks and the Consequences Doth Direct and Indirect
Cyber criminals are ingenious and use many methods: phishing, hacking passwords, to get into hospital networks to reach sensitive and profitable data held by hospitals and major healthcare systems. Our next article dives deeper into specific methods of how the bad guys can get in a hospital system. What is alarming is that often times, the bad buys are already in, patiently waiting to exploit vulnerabilities.
Lost Time and Asset Utilization
The goal of hackers is to slow down or paralyze the health facility’s activities until ransom payment and these cyber-extortions can provide considerable financial gains. Think not just of WannaCry but even PetyaWrap which caused Princeton Community Hospital to stop functioning. Doctors were unable to review patients’ medical history or transmit laboratory and pharmacy orders. Unable to restore services and unable to pay a ransom, Princeton Hospital resorted to using paper records. And with little choice left the hospital subsequently scrapped and rebuilt its entire network.
Cyber criminals benefit from the fact that medical equipment such as MRI, X-ray machines, scanners and other diagnostic equipment do not always benefit from optimal security, even though they are almost always connected and used often. This oversight can create security loopholes and encourages intrusions into the systems. Taking a system offline can be a big issue as oftentimes hospitals lease expensive equipment to maximize their usage.
Hidden in the Dark
Highly targeted and sophisticated, the focused on hospitals are often the result of structured groups. These attackers are patient, often lurking undetected waiting to exploit a vulnerability. The goal of the attacker is to discreetly maintain access for as long as possible in order to capture strategic information in a timely manner. In some instances it can be years before an attacker surfaces.
Thinking about Proactive Protection
Businesses need cost-effective, easy-to-deploy solutions that can continually show them who and what is connected to all parts of their networks. The other critical element to consider is the ability to identify any vulnerabilities and apply remedial action proactively. Ideally, the security system will be able to regulate flow and behavior by device type, group, location, function, application, the control is yours.
Many products today will ring the alarm that something is wrong, adding to a whole list of alarms that go off in a day at a hospital. A few will take the next necessary step forward providing automated remediation and loop learning. What we recommend is a system that can quickly provide holistic visibility and the ability to detect exposed vulnerabilities and delivers intricate risk scores for priority attention and mitigation.
Increasingly threats will become sophisticated and automated smart enough to find the key vulnerabilities in a network. Remediation should likewise follow suit and will need to be more sophisticated and automated while leveraging machine learning and AI. The goal of this intelligent system is to deal proactively with any type of vulnerability and limit the damage before it occurs, protecting the hospital’s important business critical assets and closing the door on cyber vulnerabilities.
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogDetect & Defend Against Chrome Vulnerabilities Using OrdrAI
BlogDetect & Defend Against Chrome Vulnerabilities Using OrdrAI…so far in 2024 and four in May alone! To mitigate these threats users are strongly advised to update their Chrome browser to version 125.0.6422.112/.113 for Windows and macOS, and…
Blog
Detect & Defend Against Chrome Vulnerabilities Using OrdrAI
Ordr Security Bulletin
< 1Min Read
By Pandian Gnanaprakasam
This security bulletin written with support from Ordr senior product manager Derek Loomis
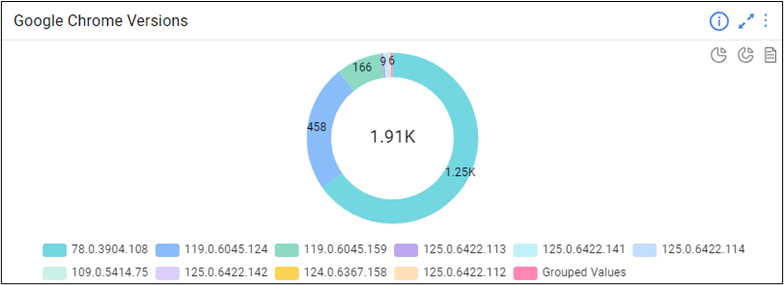
Google Chrome has experienced eight zero-day exploits so far in 2024 and four in May alone! To mitigate these threats users are strongly advised to update their Chrome browser to version 125.0.6422.112/.113 for Windows and macOS, and version 125.0.6422.112 for Linux.
Similarly, users of Chromium-based browsers such as Microsoft Edge, Brave, Opera, and Vivaldi are urged to apply the available fixes promptly. Additionally, CISA has acknowledged active exploitation of CVE-2024-5274 and requested that users patch the flaw before June 18, 2024. It’s crucial for administrators to enable application vulnerability policies and consider setting the severity to high, blocking user access to work data until the app is updated.
Attackers may exploit these vulnerabilities by delivering a maliciously crafted webpage through SMS, email, or messaging platforms, convincing victims to tap the link and initiate the exploit. A successful attack could grant attackers access to sensitive data or deliver phishing sites or malware to the vulnerable device, posing a critical risk to enterprise security postures that rely heavily on mobile devices accessing sensitive cloud data.
OrdrAI CAASM+ (Cyber Asset Attack Surface Management) accelerates the remediation of these threats by providing software version information so you don’t have to wait for vulnerability scans to complete. The most recent zero-day exploits are so serious, the U.S. government has warned federal employees to apply emergency updates or stop using Chrome altogether. Deadlines for updates exist for both June 3rd and June 6th. As with all zero-day vulnerabilities, time-to-remediation is crucial, and OrdrAI enables you to act quickly to secure your assets.
Vulnerability Details:
CVE-ID Severity Details Exploitability Score Vector NVD Published Date CVE-2024-5274 8.8 Type Confusion in V8 in Google Chrome prior to 125.0.6422.112 allowed a remote attacker to execute arbitrary code inside a sandbox via a crafted HTML page. 2.8 CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H 05/28/2024 CVE-2024-4671 9.6 Use after free in Visuals in Google Chrome prior to 124.0.6367.201 allowed a remote attacker who had compromised the renderer process to potentially perform a sandbox escape via a crafted HTML page. 2.8 CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:C/C:H/I:H/A:H 05/14/2024 CVE-2024-4761 8.8 Out of bounds write in V8 in Google Chrome prior to 124.0.6367.207 allowed a remote attacker to perform an out of bounds memory write via a crafted HTML page 2.8 CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H 05/14/2024 CVE-2024-4947 8.8 Type Confusion in V8 in Google Chrome prior to 125.0.6422.60 allowed a remote attacker to execute arbitrary code inside a sandbox via a crafted HTML page. 2.8 CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H 05/15/2024 CVE-2024-2886 Awaiting Analysis Use after free in WebCodecs in Google Chrome prior to 123.0.6312.86 allowed a remote attacker to perform arbitrary read/write via a crafted HTML page. Awaiting Analysis Awaiting Analysis 03/26/2024 CVE-2024-2887 Awaiting Analysis Type Confusion in WebAssembly in Google Chrome prior to 123.0.6312.86 allowed a remote attacker to execute arbitrary code via a crafted HTML page. Awaiting Analysis Awaiting Analysis 03/26/2024 CVE-2024-3159 8.8 Out of bounds memory access in V8 in Google Chrome prior to 123.0.6312.105 allowed a remote attacker to perform arbitrary read/write via a crafted HTML page 2.8 CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H 04/06/2024 CVE-2024-0519 8.8 Out of bounds memory access in V8 in Google Chrome prior to 120.0.6099.224 allowed a remote attacker to potentially exploit heap corruption via a crafted HTML page. 2.8 CVSS:3.1/AV:N/AC:L/PR:N/UI:R/S:U/C:H/I:H/A:H 01/16/2024 Source: CVE Details
Google Chrome May Vulnerabilities- CVE-2024-5274 (type confusion in V8 JavaScript and WebAssembly engine)
- CVE-2024-4671 (use-after-free in Visuals)
- CVE-2024-4761 (out-of-bounds write in V8)
- CVE-2024-4947 (type confusion in V8)
Other Google Chrome 2024 Zero-Days
- CVE-2024-2886 (UAF issue in WebCodecs)
- Demonstrated at March hacking contest Pwn2Own Vancouver 2024
- CVE-2024-2887 (type-confusion issue in WebAssembly)
- Demonstrated at March hacking contest Pwn2Own Vancouver 2024
- CVE-2024-3159 (out-of-bounds memory access in V8)
- Demonstrated at March hacking contest Pwn2Own Vancouver 2024
- CVE-2024-0519 (out-of-bounds memory access in Chrome JavaScript engine)
How OrdrAI Helps
OrdrAI CAASM+ integrates with your existing infrastructure utilizing API calls to gather software information from numerous vendors. Further, Ordr’s lightweight, patented script and primary data source, Software Inventory Collector, delivers a high-fidelity software inventory. Then, OrdrAI CAASM+ provides out-of-the-box dashboards to continuously monitor your environment. Correlating all these data sources Ordr provides comprehensive and accurate deduplicated asset visibility, thus preventing exposures.
History shows Google Chrome’s recent streak of zero days will repeat itself. Web Browers, Adobe, and Java products have historically been at the top of the list of most vulnerable third-party software. But with OrdrAI CAASM+ you can track all browser versions in your environment.
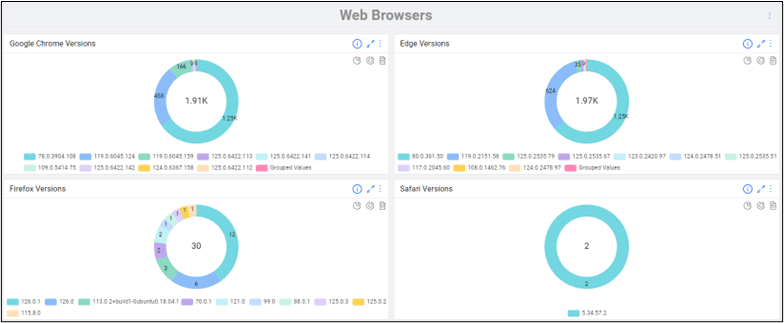
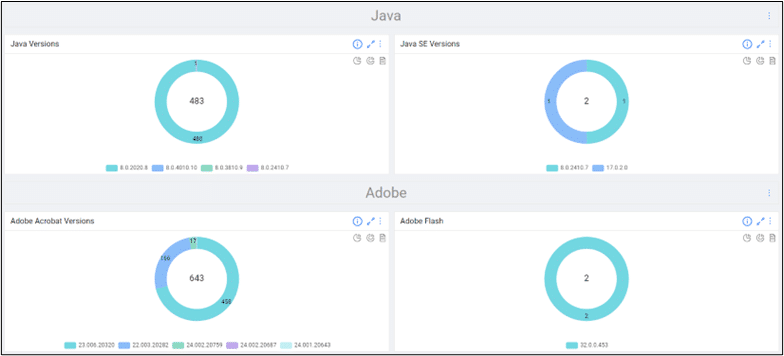
Ordr’s out-of-the-box comprehensive software inventory allows your remediation teams to define scope and begin remediation in just a few clicks, and Identify and track devices with out-of-date browser versions in your environment. With a simple search, you can then add this as a widget and dig deeper into these devices for remediation, identifying the blast radius in case these vulnerabilities are exploited.

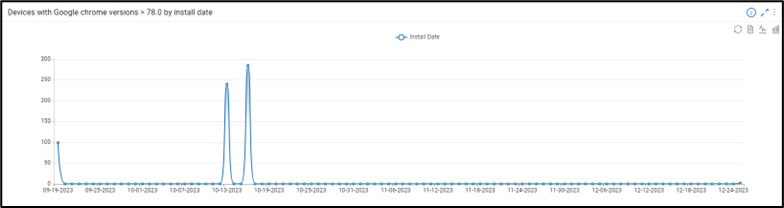
You can also track updates or installation of new browsers based on version number correlated with Install date/Update time.
Customers can also get a detailed view of the blast radius via the “Asset Graph” feature, identifying devices, users, and applications associated with a vulnerable asset.
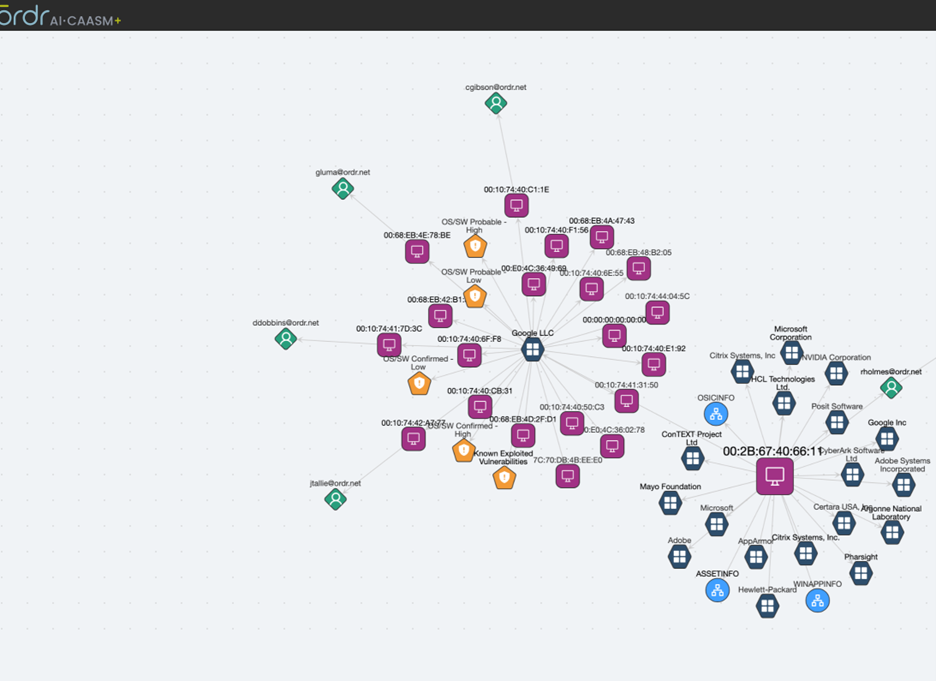
OrdrAI lets you assign a variety of actions to appropriate remediation teams to patch out of date devices.
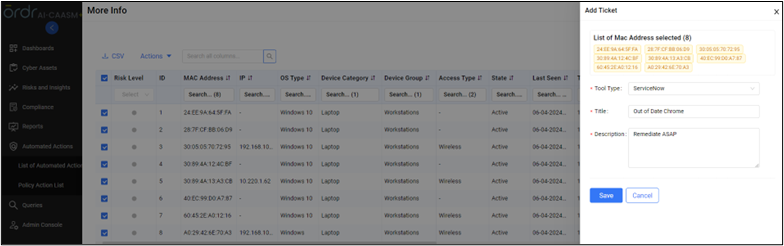
Actions Supported by OrdrAI CAASM+
OrdrAI CAASM+ allows easy management of vulnerabilities, including assignments and status of the vulnerabilities thanks to deep integration with vulnerability management tools like ServiceNow VR module, providing real-time status updates based on reconciled data.
Furthermore, OrdrAI CAASM+ delivers vital capabilities, like muting or removing a vulnerability from the system when information is not available or is hidden from publicly available dashboards. This is usually done when admins are not ready to patch and are waiting for validation from the manufacturer. OrdrAI also lets you assign vulnerabilities to individual users along with priority and due date. All this information can be shared with CMDB or any other asset management vendors.
Finally, OrdrAI CAASM+ reduces time-to-remediation and risk to the organization with the help of Integration with messaging/collaboration tools and ticketing systems and providing a range of asset specific actions.
OrdrAI CAASM+ is your single source of truth, enabling your teams act with confidence. Contact us for more information.
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogOrdr Included in Forrester Microsegmentation Landscape Report
BlogOrdr Included in Forrester Microsegmentation Landscape Report…Because today’s enterprise IT infrastructures are sprawling, comprising diverse systems and devices, and always in flux, network segmentation—and microsegmentation—is vital to protecting the full spectrum of assets that an organization…
Blog
Ordr Included in Forrester Microsegmentation Landscape Report
4Min Read
By Danelle Au
From the start, one of the key features of the Ordr platform has been our ability to discover and classify assets at a granular level, pinpoint asset risks and threats, and accelerate segmentation. That is an important part of establishing a Zero Trust architecture for any organization serious about maximizing security and operational resilience. Because today’s enterprise IT infrastructures are sprawling, comprising diverse systems and devices, and always in flux, network segmentation—and microsegmentation—is vital to protecting the full spectrum of assets that an organization relies on to carry out its mission.
A Maturing Market
As more cybersecurity tools are evolved and developed to address microsegmentation, the market is attracting the attention of users who need those capabilities, and analysts whose expertise is sought to help guide the market. One analyst group leading the way is Forrester Research, and we are thrilled to be included in the Q2 Forrester Research Microsegmentation Solutions Landscape research report as a representative vendor.
The number of tools available for addressing the need for microsegmentation is growing, as you’d expect when a critical need is identified, and pioneering vendors like Ordr show the way. We work hard to provide the best possible solution for microsegmentation through our OrdrAI asset intelligence platform and OrdrAI Protect, and so it is gratifying to be recognized by a respected technology analyst firm like Forrester.
Addressing Core Needs
Authored by principal research analyst David Holmes with contributions from VP and research director Joseph Blankenship, associate project manager Lok Sze Sung, and practice director Michael Belden, the Microsegmentation Solutions Landscape report defines the core value of microsegmentation as helping organizations with the following
- Secure critical and important resources. The best way to quantify microsegmentation as a business benefit is to accept that some level of resource isolation is a cybersecurity requirement, and then compare the cost of a microsegmentation solution to the cost of resegmenting a network or architecture. Limiting lateral movement reduces the impact of cybersecurity incidents since they involve fewer systems and get access to less data.
[In Ordr deployments, critical infrastructure and industrial operators often have deep investments in supervisory control and data acquisition (SCADA), industrial control systems (ICS), and other operational technologies (OT) with service lives that may be measured in decades. Likewise, modern healthcare facility networks are an amalgam of medical technologies, building controls, traditional IT, and even consumer devices. Keeping those systems in service—while protecting them from imperiling threats—is essential.]
- Defend against ransomware. While many organizations are proactive about Zero Trust, an enterprise typically seeks a microsegmentation solution after a cybersecurity incident like ransomware has already done its damage. These organizations are looking to prevent future attacks from being as destructive. Quantifying the benefit for ransomware victims is as easy as subtracting the cost of the solution from the cost of the actual breach, including the ransom.
[Ordr helps defend against ransomware attacks by identifying assets behaving outside of normal baselines, or by identifying those with vulnerabilities that can be exploited. Ordr also can generate proactive segmentation policies based on business needs to stop lateral movement, enforced on existing infrastructure like switches, wireless LAN controllers, firewalls and NAC. And should an attack succeed in getting through, Ordr can also quarantine a compromised device, keeping it isolated until the threat can be remediated.]
- Achieve compliance imperatives. Occasionally, microsegmentation can be used to meet a specific business imperative or compliance mandate separate from Zero Trust. For instance, it can assist in identifying data for GDPR. Customers with strict security requirements can insist that you use microsegmentation to protect their data within your systems.
[By providing a complete asset inventory, Ordr can accelerate compliance initiatives. Ordr pre-defined reports like NIST can help accelerate compliance initiatives, while segmentation limits the scope of compliance.
Our asset risk scores are based on what the asset is, the most up-to-date data and threat intelligence, vulnerabilities, hotfixes and more , Ordr enables security teams to close risk gaps that could result in security incidents triggering enforcement under regulations like HIPAA, GDPR, and other data security and privacy regimes.]
Addressing Zero Trust
Forrester says that microsegmentation tools emerged as one of the first technologies to address Zero Trust security architectures when that philosophy was defined (by Forrester) more than 15 years ago. According to Forrester, one of the most important Zero Trust implementation trends involving microsegmentation is:
Main Trend: Organizations are finally getting serious about Zero Trust. Some, proactively, are implementing microsegmentation as part of a Zero Trust strategy or initiative. Others are implementing it because they got hit by ransomware and are trying to avoid it again. But all of them are doing Zero Trust with microsegmentation.
Ordr Microsegmentation Benefits
Importantly, Forrester has highlighted how Ordr demonstrates key abilities like the capacity to discover assets across the full enterprise, including on-premises legacy technologies, cloud and hybrid infrastructure, industrial environments populated with operational technologies, and other enterprises with heterogeneous network configurations.
Holmes says, “You can use microsegmentation solutions to secure critical and important resources, defend against ransomware, and achieve compliance imperatives. But to realize these benefits, you’ll first have to select from a diverse set of vendors that vary by size, type of offering, geography, and use case differentiation.”
Ordr Takes Microsegmentation Further
That is true, but Ordr goes a step further. To gain the full potential of microsegmentation requires a platform that can discover assets, ingest data, and deliver precise risk analysis in real-time. That is the power of OrdrAI–and the advantage of the Ordr Data Lake, which is unrivaled in its scope and rich detail, containing in-depth profiles of millions of individual asset types. With OrdrAI organizations can assign an accurate risk score to every asset in the network, baseline normal operations and accurately identify risky behavior, then automatically enforce security policies, including microsegmentation, to prevent, contain, and limit the damage of cyberattacks.
The good news is that you don’t have to wait for that future to arrive if you are struggling with complex networks, visibility gaps, and technologies that are impossible to discover and monitor using traditional tools. OrdrAI has already established a stellar record and reputation with a growing client list that includes top organizations in healthcare, manufacturing, critical infrastructure, financial services, education, and government and smart cities. You can find more information about the OrdrAI asset intelligence platform here, and learn more about our segmentation capabilities here, or contact us directly with questions about the OrdrAI platform, or your specific challenges.
Want to learn more about how Ordr helps you simplify segmentation? Attend our webinar on May 14th with our expert Craig Hyps.
Danelle Au
Danelle Au has more than 20 years of experience bringing new technologies to market. Prior to Ordr, she was CMO at Blue Hexagon, a deep learning for malware protection company, and CMO at SafeBreach where she helped build the marketing organization and and define the Breach and Attack Simulation category. Previously, she led strategy and marketing at Adallom, a cloud security company acquired by Microsoft. She was also Director, Security Solutions at Palo Alto Networks, driving growth in critical IT initiatives like virtualization, network segmentation and mobility. Danelle was co-founder of a high-speed networking chipset startup, co-author of an IP Communications Book and holds 2 U.S. Patents. She has an MSEE from UC Berkeley
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogApplication & User Control
BlogApplication & User Control…level. On applications, we have the capability to track applications and any device or workstation that uses that specific application. Specifically, command applications such as SSH flows between machines are closely…

From major customer wins in key industries, to new hires, technical innovations, and product advancements, hear perspective from Ordr co-founder and chief product officer Gnanaprakasam Pandian about what Ordr accomplished in 2022 and what to expect from us in 2023. Part VI of VI on Control
Who, What and For Real?
With all the antics and the daily drama, it’s not easy keeping up with the Kardashians. Kim, Kourtney, Khloe, how do you keep up with everything they do? An oftentimes, it is quite unexpected what they do. Thinking about the Kardashians made me empathize with the hospital IT staff who have the unenviable task of keeping tabs of all the users and applications that are crisscrossing a major healthcare network. How do we easily keep track of everything without multiple systems that need to be stitched together?
When thousands of people are moving about in and out of a hospital, understanding what each and every user is doing is not easy. The problem is made more difficult since not all users are created equal and access for some people to certain devices is allowed but access to others is not. An MRI machine, for example, some medical personal are allowed to use it but some people are not. Easy stuff right with access control, right? But it can get complicated.
User profiles are often set up via an Active Directory yet sometimes a user can be created locally on the fly so it’s important to discern the difference between the two as this can be a big area of potential security weakness. Sometimes, profiles are created as users log in to a device and just add more new users, forgetting to delete the user if the session was a one-timer. For real, this happens more than you think. It helps to be contextually aware to understand not just who has access, but when the login occurred, and how long a session for a particular medical device lasted. A user provisioned on a CT scanner can potentially have access to the entire patient record database in a hospital. Think about that, the least protected device is potentially the gateway to the most valuable data.
Access and Convenience via Applications
Who doesn’t love apps that give users access with convenience? In hospitals and other enterprises for that matter, mission-critical business applications are used to come in and out of the network helping to drive overall productivity with the added convenience of remote use. Doctors use mobile applications all the time and it’s important from a security point of view that an organization understands what devices were accessed and whether or not it was done so appropriately via the corporate network or inadvertently by the guest network. Sometimes we see credentials shared across multiple users so it is important to safeguard how many people are claiming to be an admin for example.
In the application kingdom, there are supervisory protocols like TELNET (port 23), FTP (port 21), SSH (port 22), SNMP (161) and others that are usually used by system administrators. As an example, SSH enables an administrator to securely connect to a remote server and perform necessary operations on that server. These supervisory applications are routinely used by admins to operate, debug, transfer data and fix things on the servers. And these applications are used in all Operating Systems including Microsoft Windows.
Understanding applications is one thing but what’s also important is to understand the flow and what is actually happening in a session. If there is a regular port 22 session with a known regular device that is fine but shouldn’t someone proactively ring the alarm if the SSH session comes from a different or even worse from an unknown un-authorized person? And wouldn’t it be helpful to know which stations are performing how many sessions to quickly understand any abnormal behavior?
Stealing the Keys
The problem in relying on supervisory commands to operate critical devices can leave you vulnerable if by chance the credentials are stolen. If this occurs, then brace yourself as anything can happen. Hackers can change code, manipulate machines, it can be quite the issue so if anything, the faster the detection, the more damage can be contained.
Application control is essential and it is important to quickly see something that looks out of the normal behavior as this can be an early sign of malicious behavior. If there are specific pediatric centric applications, take the necessary step to see who and when it is accessing and for what purpose. Is a medical device being accessed too often? It may not be just a utilization issue but rather an indication that something is off.
Take Control
The Ordr system control engine has the ability to track every user and every application, all the time. It’s one holistic platform for all your visibility needs. We can provide the insight into each medical machine, and tell you who logs in, when the machine was used and for how long. That’s helping you take control. We can further map specific devices to specific users to provide the granular detail helping you to take proactive security to the next level.
On applications, we have the capability to track applications and any device or workstation that uses that specific application. Specifically, command applications such as SSH flows between machines are closely monitored and we can show you all the secure shell sessions of any device at any point in time. Keeping track of the countless users and applications is not easy but we can make it easier in an AI-based system that keeps learning and gets smarter with each use. Now only if we can automate Kylie Jenner’s jet setting whereabouts.
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 NewsOrdr Announces Expanded Partnership With Fortinet
NewsOrdr Announces Expanded Partnership With Fortinet…automatically creates a complete asset inventory, identifies and prioritizes asset risk, and tracks and risk-rates asset communications patterns. Ordr transmits this critical security context to Fortinet FortiGate, FortiManager, and FortiNAC,…
Ordr Announces Expanded Partnership With Fortinet
To Deliver Industry-Leading Security Across Network-Connected Devices
3Min ReadSANTA CLARA, Calif., February 10, 2021 — Ordr, the leader in security for all connected devices, today announced that the company has expanded its partnership with Fortinet, a global leader in broad, integrated and automated cybersecurity solutions, to deliver an industry-leading integrated solution to address the security challenges posed by widespread IoT and unmanaged devices. The integration of Ordr Systems Control Engine (SCE) with the Fortinet Security Fabric, including FortiManager, FortiGate, and FortiNAC, through the Fortinet Open Fabric Ecosystem, dramatically reduces the time and effort needed for customers to create and maintain a complete and detailed asset inventory, determine safe communication patterns, and create effective, business-relevant firewall policies. This integration also enables NAC segmentation policies that automatically update as devices are added, removed, and move around the network.
As the number of connected devices on corporate networks—from critical business infrastructure such as IP-enable physical security devices to consumer devices such as smart speakers—has grown exponentially, they have become lucrative targets for attack. A majority of IoT devices, including critical and expensive systems like MRIs, commonly run legacy software that lack anti-malware and patch management support and are thus an inherent risk to an organization. The only way to reduce threat exposure is to first identify every connected device and its risk, then proactively apply protection policies through firewall rules or NAC policies that permit only necessary and safe communications.
Ordr SCE automatically creates a complete asset inventory, identifies and prioritizes asset risk, and tracks and risk-rates asset communications patterns. Ordr transmits this critical security context to Fortinet FortiGate, FortiManager, and FortiNAC, allowing administrators to create and apply firewall and NAC policies using business-relevant groups, classifications, and device names, while understanding the full risk profile and impact of each change. Ordr further reduces administrative costs by automatically updating asset groupings as devices join and leave the network, as well as by creating and transmitting security policies directly to FortiGate and FortiManager for enforcement.
Benefits:
- Discover and inventory every connected network asset, including the massive volume of IoT and unmanaged devices, and make available across the Fortinet Security Fabric, from endpoint to edge, through FortiNAC, FortiManager, and FortiGate
- Establish comprehensive security controls that restrict IoT devices to known-good network behaviors
- Manage firewall and NAC policies using business-relevant context such as device type, manufacturer, location, risk, and function rather than IP addresses
- Automate updates of firewall groups and address info to ensure consistent policy enforcement regardless of device location, VLAN, or IP assignment, thus drastically reducing operational costs and downtime
- Protect critical devices with automated, zone-based segmentation and microsegmentation within zones
Ordr also incorporates additional network intelligence from FortiGate deployments. Ordr SCE can consume network traffic information, wireless device context, and other data, in some cases eliminating the need for an Ordr sensor in remote offices. Ordr SCE also correlates threat information with FortiGate, clearing alerts when suspect traffic has been blocked by the firewall.
“Fortinet is a leader in enterprise security and today’s announcement bolsters our customers’ ability to discover and inventory every connected device, including the massive volume of IoT and unmanaged devices on a typical network,” said Bryan Gillson, VP of Business Development at Ordr. “It is now easier than ever for customers to establish and automate comprehensive security controls that restrict the behaviors of connected devices. It’s also easier to manage firewall and NAC policies using business-relevant context such as device type, manufacturer, location, and function, rather than manually checking IP addresses.”
“FortiGate Next-Generation Firewalls enhance Ordr’s visibility across the infrastructure by sending flow data to a centralized Ordr sensor,” said John Maddison, EVP of products and CMO at Fortinet. “This extends the visibility in remote and lateral communications to improve overall infrastructure visibility, enhance anomaly detection, and increase the efficacy of FortiGate zone-based segmentation and FortiNAC access control policies. FortiGate NGFWs can also reduce incident response efforts by informing Ordr when malicious traffic is dropped at the firewall.”
“With just a few clicks, administrators can create business-relevant segmentation policies in FortiGate NGFWs that ensure devices of a specific type and role only connect over approved communication channels with necessary destinations—all specific to the organization,” said Josh King, Director of Security Solutions at Carousel Industries, an Ordr partner whose team of more than 1,300 IT professionals provide IT, security, cloud and managed services to thousands of businesses. “This drastically reduces operational costs and downtime, which is essential for companies across all verticals – including healthcare, manufacturing, life sciences, financial services and retail.”
To learn more about how to discover all network-connected devices and automate network segmentation workflows, visit https://ordr.net/partners/fortinet/
About Ordr
Ordr makes it easy to secure every connected device, from traditional IT devices to newer and more vulnerable IoT, IoMT, and OT. Ordr Systems Control Engine uses deep packet inspection and advanced machine learning to discover every device, profile its risk and behavior, map all communications and protect it with automated policies. Organizations worldwide trust Ordr to provide real-time asset inventory, address risk and compliance and accelerate IT initiatives. Ordr is backed by top investors including Battery Ventures, Wing, and TenEleven Ventures. For more information, visit www.ordr.net and follow Ordr on Twitter and LinkedIn.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
Knowledge BaseWhat is Ryuk Ransomware?
…a big factor in the cybersecurity picture, and everyone needs to understand and fulfill their part in order for the organization to have robust security. Defining risk management and accounting…
What is Ryuk Ransomware?
6Min ReadRansomware is unlikely to go away any time soon, and the Ryuk ransomware family is a particularly nasty version of this tech. Ryuk ransomware has been around since 2018, and it continues to be a viable threat due to its evolving nature—particularly attacking large organizations in a variety of industries. If attackers think your organization could be vulnerable and/or an easy payday, you may find yourself under attack.
Understanding Ryuk ransomware is the best way to determine the necessary tools to protect yourself against it, and will help you formulate the policies and procedures vital to defend your organization. Furthermore, the more you know, the better educated you’ll be at choosing the best security solution for your organization.
Definition of Ryuk Ransomware
Ryuk is a ransomware family that targets large companies, typically with Microsoft Windows operating system, and encrypts data to hold it hostage until a ransom is paid. In more technical terms, Ryuk ransomware is a human-operated ransomware family that uses AES-256–based file encryption to encrypt all files on the targeted systems, except for those with the .dll, .lnk, .hrmlog, .ini, and .exe extension, appending the .ryk extension to the newly encrypted files. Ryuk is considered to be a unique ransomware family because of continued human involvement throughout the attack, specifically, the group behind this ransomware uses manual hacking technique and open-source tools to move laterally through the network
Most ransomware attacks use a “spray and pray” approach, in which they hit multiple targets at once and hope for infiltration. Ryuk uses targeted attacks; it is an advanced persistent threat (APT) with human threat actors active in the network for an extended period of time. The network is infiltrated, with a prolonged period of data collection and network activity.
Ryuk continues to evolve. While still advanced with human involvement, that human interaction is no longer required for lateral movement. The newest strains of Ryuk are capable of auto-propagation through systems, once loaded into the network, using worm-like techniques. Because Ryuak doesn’t check to see if a system is already infected, it continues to re-infect systems, which makes the ransomware family that much more dangerous.
How Does Ryuk Attack?
Ryuk has been used to target organizations in several different industries, including hospitals, governmental institutions, and news outlets. It’s used to “big game hunt”—an organization is specifically chosen before the attack. The victims are typically larger organizations with multiple or high-value critical assets because of the increased chances of the ransom being paid.
Delivery
Part of what makes Ryuk so dangerous is it’s absolutely benign-looking delivery system: a common Microsoft Word document. The document is attached to a basic phishing email, often sent from a spoofed legitimate source. But, the document has a Emotet trojan downloader hidden in the macros, and it cleverly tricks a user into enabling macros in order to view the document. This then lets Ryuk launch the attack against the system.
Once the Emotet trojan is let loose, it downloads additional malware to install Trickbot onto the system. Trickbot is spyware that can collect the necessary credentials for the attackers to successfully move through the infected systems without hindrance.
Execution
Once the attackers have the credentials, they recon the network and systems to determine whether or not the organization is worth attacking. During this espionage, the threat actors do extensive mapping of the systems and identify which critical assets to target during the attack.
As part of this initial phase, Trickbot modules allow the malware to gain Remote Desktop Protocol (RDP) credentials via brute-force attack and create service user accounts on authentication servers on the network. This results in a faster and less detectable final deployment of the encryption. Once recon and set up is finished, the Ryuk encryption is deployed on the critical asset targets.
Evasion
Many security solutions use registered signatures to scan for known threats. Ryuk ransomware is stealthy—it creates mutations of the original variant so it registers as a previously unseen threat. By mutating to a new variant, it doesn’t flag as a known threat. This constant evolution is a key reason for a more robust security solution—there are more factors than just looking for known security flags.
Data Collection
The attack targets are always what the organization would consider critical assets. However, what each organization considered critical assets isn’t the same across the board—depending on the industry, this could be protected customer data, patient charts, student transcripts, or an OT network. Ryuk’s goal is to target what would best cripple your organization because that increases the chances of you paying the ransom.
Ryuk encrypts the system in such a way that the organization can determine exactly what’s been encrypted, yet leave you still capable of digitally paying the ransom. Ryuk has been known to partially encrypt some files, which prevents decrypting the files with anything other than the designated key. This puts your decryption attempts at a high risk of causing file corruption.
How to Detect Ryuk Ransomware
Detecting ransomware like Ryuk requires a robust security solution like Ordr. Ordr integrates with Active Directory to tie devices with users, and ensure all access is valid, which can be used to detect any Ryuk-created service accounts as they appear on the network. Ordr also monitors for exploits, attacker tools and reconnaissance network scans with an integrated threat detection engine, and uses known behavioral baselines to detect unusual or suspicious traffic, which could flag Ryuk’s internal lateral movement before encryption deployment. The behavioral baseline capabilities can also track RDP activity, and if any suspicious activity is detected, Ordr can immediately obtain a list of infected assets and track down infection roots.
Furthermore, Ordr can proactively reduce the attack surface in ransomware attacks by using its discovery process to profile what devices connect to your organization’s network. High-risk devices can then be properly segmented. Ordr also offers retrospective security to look back at anomalous communications by devices in the network to newly discovered indicators of compromise.
Ways to Prevent a Ryuk Attack
Preventing a Ryuk ransomware attack can be accomplished by having a strong security solution that is foundational sound, tested often, and is continuously improved using an iterative approach. Your organization should also have a plan in place for handling an attack in progress once it has already infiltrated and been detected.
1. Focus on the basics and drill often
Fully define your organization’s attack profile. Understand what could make you a target by discovering and classifying every asset in your network, identifying the risks they bring, and determining which are critical assets to protect. Ensure the proper protections are in place for those assets. Keep patches updated and use enhanced security practices like multifactor authentication and microsegmenation.
2. Have a plan
Develop policies and procedures that embrace security methodologies and ensure that all teams are aware of how to best protect the network. People are a big factor in the cybersecurity picture, and everyone needs to understand and fulfill their part in order for the organization to have robust security. Defining risk management and accounting for any federal, state, or industry compliance standards is an absolute must.
3. Improve security continuously
As technology develops and new threats enter the threat landscape, it’s critical that security evolves over time to remain effective. Mitigate risk where possible, and document and patch vulnerabilities as they’re encountered. Ensure that you have a security solution that can detect known threats as well as behavioral anomalies that may provide early indicators of an attack in progress. Inspect external traffic communications to the Internet as well as East West traffic to detect lateral movement.
Keep improving over time. Operational readiness is key to handling any cyberattack, and it should include the input of not only security, but also key decision makers, as they provide a unique perspective in regards to risk.
4. Implement Zero Trust
Zero Trust is a very effective security methodology that’s best suited to the newly evolved threat landscape. It relies on the principle of least privilege and helps keep user access at safe levels, and it embraces microsegmentation, which can be a critical facet when trying to shut down an attack in progress. Additionally, Zero Trust prevents standard users from installing applications—that’s an important hurdle to place in front of a Ryuk ransomware attack.
The Path to Better Security
The increase of complexity in the threat landscape will only grow, and it is up to your organization to put a solution in place that can expand to meet the needs that will come from threat expansion. The insidious malware family of Ryuk ransomware is an advanced, persistent threat that can seem overwhelming, especially since you deal with mutated, worn-like propagation capabilities and a human-operated attacker. The human element in the Ryuk ransomware makes it extremely formidable, as does its combining with Emotet and Trickbot to infiltrate and take over the network. But you can detect and halt a Ryuk ransomware attack with the right advanced solution.
Using an advanced security solution like Ordr gives your organization the necessary arsenal, such as microsegmentation, Zero Trust, internal lateral movement tracking, and much more.
Ordr gives you full visibility into all the devices connected to your network, helps you understand their purpose and operation, and automates management and security policies to ensure maximal protection. Should you fall under attack, Ordr can help you rapidly isolate and protect infected devices.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogWhere IoT Plays a Role in Critical Infrastructure
BlogWhere IoT Plays a Role in Critical Infrastructure…Standard Application Layer Protocols [T869], to communicate with controllers and download modified control logic. Use of vendor engineering software and Program Downloads [T843]. Modifying Control Logic [T833] and Parameters [T836]…
Security Bulletin
Where IoT Plays a Role in Critical Infrastructure
NSA & CISA Alert (AA20-205A)
4Min Read
By Corin Imai

NSA and CISA warned that threat actors are leveraging vulnerabilities in OT and other connected devices to compromise the networks of critical infrastructure operators (Alert AA20-205A). Ordr can find affected devices and help mitigate the threat. Overview:
On July 23, the National Security Agency (NSA) along with the Cybersecurity and Infrastructure Security Agency (CISA) urged all DoD, NSS, DIB, and U.S. critical infrastructure facilities take immediate actions to secure their Operational Technologies (OT) assets. The alert was issued because in the past few months, threat actors have leveraged internet connected devices to exploit critical infrastructure. OT and IoT devices and systems are designed for ease-of-use rather than with security in mind and thus don’t have the means to detect or mitigate malicious activity. The design of these devices and systems combined with the data that they transmit and share via the internet, make them easily exploitable.
“…civilian infrastructure makes attractive targets for foreign powers attempting to do harm to US interests”
Some of the observed Tactics, Techniques, and Procedures (TTPs) as defined by the MITRE ATT&CK framework are:
- Spearphishing [T1192] to obtain initial access to the organization’s information technology (IT) network before pivoting to the OT network.
- Deployment of commodity ransomware to Encrypt Data for Impact [T1486] on both networks.
- Connecting to Internet Accessible PLCs [T883] requiring no authentication for initial access.
- Utilizing Commonly Used Ports [T885] and Standard Application Layer Protocols [T869], to communicate with controllers and download modified control logic.
- Use of vendor engineering software and Program Downloads [T843].
- Modifying Control Logic [T833] and Parameters [T836] on PLCs.
While Alert AA20-205A discusses OT specifically, IoT is also relevant in this alert, because the alert tackles the 16 “critical infrastructure” sectors as defined by CISA:
Bolded below are the 9 critical infrastructure sectors that are largely impacted by IoT
- Chemical
- Commercial Facilities
- Communications
- Critical Manufacturing
- Dams
- Defense Industrial Base
- Emergency Services
- Energy
- Financial Services
- Food and Agriculture
- Government Facilities
- Healthcare and Public Health
- Information Technology
- Nuclear Reactors, Materials, and Waste
- Transportation Systems
- Water and Wastewater Systems
How Ordr can help:
“At this time of heightened tensions, it is critical that asset owners and operators of critical infrastructure take the following immediate steps to ensure resilience and safety of US systems should a time of crisis emerge in the near term.”
With our comprehensive IoT security platform, Ordr can help organizations address the following recommended steps as outlined in NSA & CISA Alert AA20-205A:
- Harden Your Network
- Create and Accurate “As-operated” Network Map Immediately
- Understand and Evaluate Cyber-risk on “As-operated” Assets
- Implement a Continuous and Vigilant System Monitoring Program
- Exercise your Incident Response Plan
Harden Your Network
Hardening your network starts with visibility into what is actually on your network. With the most comprehensive platform for discovering, profiling, and automating action for connected devices, we passively discover high-fidelity context on every connected device, including; make, model, operating system, firmware, version, location, and application/port usage. This device context is enriched with threat intelligence, vulnerability data, FDA/device manufacturer alerts, and incorporated into our data lake. Organizations then have granular, high-fidelity classification into every device in their network for identification of outdated operating systems, FDA recalls, and devices banned by the U.S Commerce Department. This device context can be integrated with asset management systems.
Using Ordr Flow Genome, we leverage real-time machine learning to profile every device, and visualize and baseline every device’s communications. This allows organizations to have a deep understanding of behavior insights like identifying anomalous or suspicious behaviors, such as communications to external malicious domains, lateral movement of malware/trojans and more. We do this through our security engines that scan for activity on infected machines.
This allows organizations to address the following hardening requirements:
- Identify devices using weak passwords and ciphers – clear text transfer of passwords, default or manufacturer passwords, shared drives, weak ciphers, etc.
- Identify devices that connect to business, telecommunications, or wireless networks – clearly separate devices into managed, unmanaged, and how devices enter the network.
- Closely scrutinize and track devices that are internet-accessible – closely scrutinize outbound connections to internet especially from mission critical devices like PLCs etc., and rate those connections with respect to the reputation of the sites they are reaching out to.
- Closely scrutinize and track devices that have remote management services – extract all administrative protocol interactions like SSH, rlogin, and more to closely monitor manufacturer based remote debugging sessions using protocols like RDP.
Create and Accurate “As-operated” Network Map Immediately
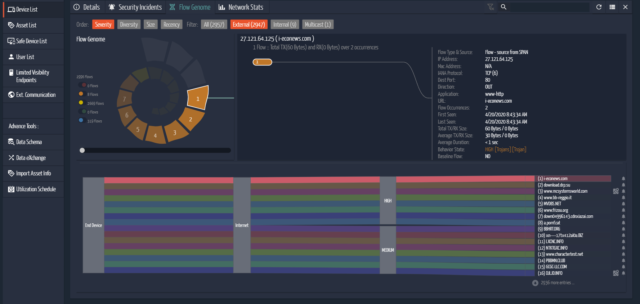
Ordr Flow Genome provides the most comprehensive profiling of every device communications patterns. We are also able to extract the latest authentication information via Active Directory/LDAP, WinRM/WMI and Kerberos to identify device users so organizations can locate devices associated with a specific owner, or identify the most recent authenticated login to a device. Our constellation map also provides a visual network topology view of where these devices are relative to network VLANs and subnets, allowing organizations to quickly address the “network map” requirement,
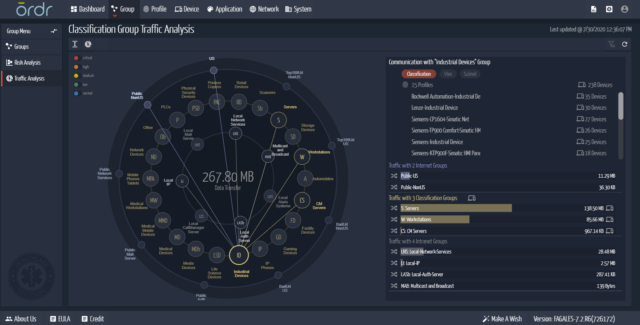
Understand and Evaluate Cyber-risk on “As-operated” Assets
The Ordr dashboard provides flexibility in searching for and investigating the risks outlined by NSA and CISA. This includes using our device inventory and context to identify devices that have been called out by:
- Vendor or technical advisories
- CISA advisories
- CVE vulnerabilities databases
- National vulnerability databases
More importantly, Ordr has the capability to automatically segment and isolate any device that is impacted by vulnerabilities, with one touch of a button. These policies can be enforced on any security or networking infrastructure.
Implement a Continuous and Vigilant System Monitoring Program
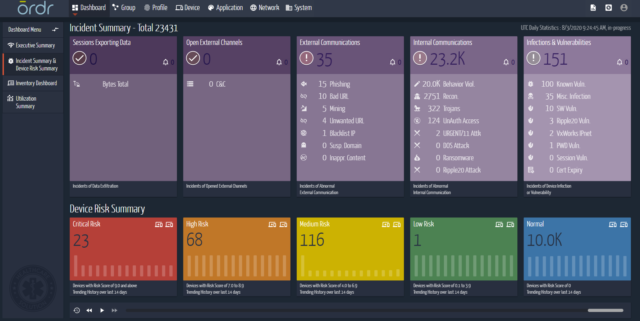
Through the Ordr Incident Summary & Device Risk Summary, we can visually show the continuous discovery and monitoring of devices, highlight any new risks to those devices (ie. Ripple20), alert based on severity, and create action for segmentation.
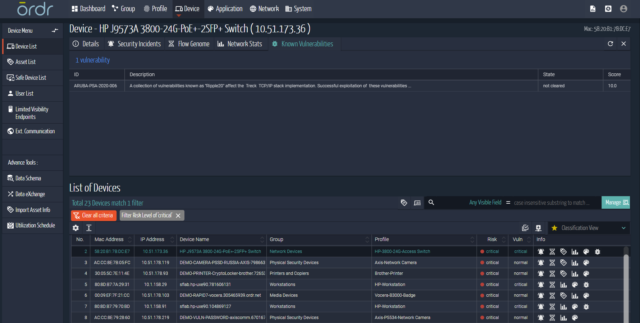
Exercise your Incident Response Plan
We automate the appropriate responses for security and networking teams. These include the automated creation and enforcement of segmentation policies or alerting and triggering a specific security or operational workflow. We also integrate with enforcement points (like switches, CISCO ISE, CPPM, controllers, etc.) to quarantine, blacklist, shutdown or enforce an ACL.
- Proactive Segmentation – Unlike users, devices should only communicate with specific systems. Ordr dynamically create policies to allow only appropriate device communications. These policies can be automatically enforced on existing infrastructure — firewalls, switches, NAC and wireless LAN controllers.
- Operational Actions – when a new or unknown device is discovered, we can trigger a centralized workflow with a CMMS or CMDB to ensure proper inventory, authentication, and routing to the right device owners.
- Security and Incident Response Actions – in the event of a security incident, or if devices have triggered an alert (known vulnerability, weak cipher, weak certificate, active threat, or malicious/suspicious behaviors) we can initiate an incident response workflow in a SIEM or SOAR, or automatically segment the impacted device.
To learn more about how Ordr can help your organization, schedule a demo.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogHow Ordr Maps to the CMMC
BlogHow Ordr Maps to the CMMC…of compliance associated with NIST 800-171. CMMC will become a requirement designed to permit only businesses with a valid CMMC certification to bid on and win contracts with the US…

Recently Ordr spent time talking to our clients about the Cybersecurity Maturity Model Certification (CMMC): what it is, why it’s important, and how they can prepare for it as it relates to the world of devices and IoT. Ordr is the leader in IoT cybersecurity, ranging from mid-market businesses to large enterprises; many of whom offer services to the Department of Defense (DoD). Because of this, it is incumbent on us to know how the CMMC will apply to our clients infrastructure and to be able to help our clients achieve certification. We realize, and educate our clients that the DoD’s new CMMC isn’t just another framework.
To help our forward-looking clients meet future CMMC requirements, Ordr is already working to map the security controls that IoT and device components require against the CMMC checklist. In order to plan for the CMMC, it is crucial that our clients and potential clients understand how IoT and device configurations are being considered as part of this new maturity model.
First let’s break down what CMMC is. In the Fall of 2020, the U.S. Government will begin requiring organizations to become compliant with CMMC. This is being done primarily to help more organizations fix low rates of compliance associated with NIST 800-171. CMMC will become a requirement designed to permit only businesses with a valid CMMC certification to bid on and win contracts with the US Government. The U.S. Department of Defense (DoD) obviously recognizes that all contractors are not alike, and is using the modifications of the CMMC and its “levels” to make this compliance endeavor more palatable for a broader swath of potential contracting organizations. The CMMC is a tiered model that has the potential to impact every business in the Defense Industrial Base (DIB). To be sure, this is no “small” endeavor.
Soon – contractors in the DoD supply chain will need to be evaluated against this maturity model by a third-party auditor. CMMC contains seventeen capability domains, each of which encompasses a different area of security. Each of these domains will be evaluated on a level from one to five — five being the most mature — and the organization will be assigned an overall CMMC level based on their evaluation results.
CMMC is a big deal for DIB companies because the level that an organization achieves will determine which DoD contracts they’re eligible to bid on and win. Get a 5, the world is your oyster; get a 1 and it limits your available opportunities.
For sure CMMC is daunting. The capability domains outlined in CMMC are very broad, and entail everything from physical security to personnel security to asset management and essentially any other applicable security control that the government can think of. That sounds nearly impossible, and it certainly could be, but in reality CMMC happened to help organizations understand the complexity and breadth of achieving a true security posture. Hopefully CMMC will help mitigate some of the pencil whipping and box checking security failures that have plagued contractors in the past.
Because CMMC is broad, it is critical that any organization wanting to compete and win lucrative contracts heed the call to ensure they consider their IoT/OT security vulnerabilities, as well as their other security controls and programs. Modern exploits and attacks usually cross IT/OT infrastructures at some point. After all, everything is “connected” today. This means that without IoT visibility and accountability the entire network is potentially threatened, and the CMMC auditors know that.
There are very few CMMC domains that don’t apply to IoT network devices. Asset discovery, threat detection, incident response are part of any intelligent or complete response package. One can easily see why they are integral to the CMMC requirements.
While CMMC has many other requirements, much of what it mandates can be summed up pretty simply. Here are a few basic considerations that can help set your organization on the right track to achieving CMMC compliance specifically related to your IoT/OT network devices.
1) Do you have visibility, access, analytics or even the capability to understand IoT devices?
You can’t defend what you don’t cannot see. And you cannot defend any enterprise if you don’t know about the totality of devices or “assets” in a network. Ordr works with organizations to gain that visibility into their IT and IoT networks. In doing this our systems help your team understand how those assets communicate and are connected to each other.
Without that insight and knowledge, it’s impossible to prioritize risks, detect active threats already operating in your environment, or prove that your security posture is strong enough and doing its job. All of those things are key to CMMC compliance across a variety of domains. Being candid, it is impossible to fully secure your networks without having IoT/OT network device visibility.
2) How resilient is your overall IoT/IT network architecture?
CMMC focuses on building a stronger cybersecurity posture in DoD supply chain contractors, and as part of that, CMMC requires an organization to detail how they have built a strong overall approach for securing all network connected devices.
Part of having a sound security posture is to make sure that all devices only communicate with the internet as intended. Stronger network segmentation improves security. Ordr makes network segmentation easy by using ML/AI-assisted automation..
3) Can you identify and remediate IoT/OT device vulnerabilities in your network?
Key CMMC requirements focus on identifying and addressing vulnerabilities across all devices and infrastructure components. For networks with IoT/OT devcies, that could mean CVEs, malfunctioning devices, or the presence of unauthorized ports or rogue applications. CMMC requires that you’re able to detect and prioritize vulnerabilities like this. If your organization cannot do this, you will have a hard time achieving higher levels of compliance. Ordr shines in this area and can rapidly enable this action.
4) Can you detect exploits with all your IoT/OT devices?
IoT and device threats are a very different animal than detecting threats that target legacy IT systems and endpoints. Typically, embedded IoT/ICS devices do not support agents and may not be visible to your IT teams or tools. Because of this gap in security, your organization may be required to incorporate IoT and device aware analytics to detect abnormal machine behavior that could help identify an attack.
This is not an area where current IT approaches can be used in the IoT/OT device environment. The requirements for these unmanaged devices are very different.
Lastly, Ordr can be deployed to help avoid the pain and cost of an extended audit. Like every other federal certification requirement, a 3rd party is going to audit your company for compliance, and that will include your IoT devices, device security controls and asset inventory. Think about this from a financial perspective. With auditors, time is money. If an organization pays an auditor an hourly rate of $300 per hour – the longer it takes the auditor to review and understand your environment, including all the IoT devices, the more billable hours and costs you will accumulate. To minimize the time and costs, it makes sense to have an accurate inventory and full visibility of every asset, including IoT devices, before the auditors arrive. With auditors, nothing exists unless it is documented. Ask Ordr to assist with preparing for your CMMC and FISMA audits.
To see how Ordr maps to CMMC in our White Paper.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?