Search Results:
”Quiz 2024 SAP C-ARSOR-2308: Marvelous SAP Certified Application Associate - SAP Ariba Sourcing Valid Dumps Book 🐮 Open ▷ www.pdfvce.com ◁ and search for ➥ C-ARSOR-2308 🡄 to download exam materials for free 🏑C-ARSOR-2308 Customizable Exam Mode”
-
 BlogNAME:WRECK Unlikely An Initial Compromise
BlogNAME:WRECK Unlikely An Initial Compromise…security researchers at JSOF and Forescout. This research is arguably an extension of the previous Ripple20 and AMNESIA:33 research as much like Ripple20 the NAME:WRECK vulnerabilities are found in commonly…
Security Bulletin
NAME:WRECK Unlikely An Initial Compromise
But Here is What You Should Know
6Min ReadBy Jeff Horne

NAME:WRECK is the short name for a collection of nine DNS based vulnerabilities discovered by the security researchers at JSOF and Forescout. This research is arguably an extension of the previous Ripple20 and AMNESIA:33 research as much like Ripple20 the NAME:WRECK vulnerabilities are found in commonly used TCP/IP stacks utilized by potentially millions of IoT devices. Several DNS vulnerabilities were discovered in the previous Ripple20 and AMNESIA:33 research with the vulnerable IP stacks being: Treck TCP/IP, uIP, PicoTCP, FreeBSD, IPNet, NetX and Nucleus NET, however these newly reported Name:Wreck vulnerabilities are inFreeBSD, IPNet, Nucleus NET, and NetX. TheTrech, uIP, PicoTCP, vulnerabilities were disclosed as part of the Ripple20 and Amnesia:33 research papers.
What are TCP/IP stacks?
TCP/IP stacks are common network libraries that allow devices with limited hardware resources to communicate over the network. These device focused TCP/IP stacks are usually found in IoT devices, which typically lack the resources to run the more demanding types of software that are common on PCs or servers. These vulnerable network libraries consequently are in widespread use, and likely places millions of devices at risk. Those devices represent a broad category of IoT use cases, from Industrial Control Systems (ICS), to healthcare equipment and beyond.
What are the effects of NAME:WRECK?
The most serious NAME:WRECK vulnerabilities disclosed are the remote-code execution attacks, in which threat actors take control of an affected device in order to harvest private data from the device or run malicious software on it and gain access to the network its connected to. That being said, exploitation of these vulnerabilities are made more difficult by the fact that it would require a malicious actor to either take control of a DNS server utilized by a vulnerable device or utilize a man-in-the-middle (MITM) style attack where communication to a legitimate DNS server is intercepted and manipulated with malicious intent. This exploitation difficulty does not change the fact that these TCP/IP stacks are vulnerable, but given the complexities of compromising a DNS server or setting up a MITM attack it does lessen the probability of these vulnerabilities being utilized by attackers.The following table displays a number of common vulnerabilities and exposures (CVE) that correspond to specific types of attacks and risks that have emerged from NAME:WRECK.
CVEs that correspond to NAME:WRECK
CVE ID Stack Description Affected Feature Potential Impact CVSSv3.1 Score 2020-7461 FreeBSD In FreeBSD 12.1-STABLE before r365010, 11.4-STABLE before r365011, 12.1-RELEASE before p9, 11.4-RELEASE before p3, and 11.3-RELEASE before p13, dhclient(8) fails to handle certain malformed input related to handling of DHCP option 119 resulting a heap overflow. The heap overflow could in principle be exploited to achieve remote code execution. The affected process runs with reduced privileges in a Capsicum sandbox, limiting the immediate impact of an exploit. Message Compression RCE 7.7 2016-20009 IPnet ** UNSUPPORTED WHEN ASSIGNED ** A DNS client stack-based buffer overflow in ipdnsc_decode_name() affects Wind River VxWorks 6.5 through 7. NOTE: This vulnerability only affects products that are no longer supported by the maintainer. Message Compression RCE 9.8 2020-15795 Nucleus NET The DNS domain name label parsing functionality does not properly validate the names in DNS responses. The parsing of malformed responses could result in a write past the end of an allocated structure. An attacker with a privileged position in the network could leverage this vulnerability to execute code in the context of the current process or cause a denial-of-service condition. Domain name label parsing RCE 8.1 2020-27009 Nucleus NET The DNS domain name record decompression functionality does not properly validate the pointer offset values. The parsing of malformed responses could result in a write past the end of an allocated structure. An attacker with a privileged position in the network could leverage this vulnerability to execute code in the context of the current process or cause a denial-of-service condition. Message Compression RCE 8.1 2020-27736 Nucleus NET The DNS domain name label parsing functionality does not properly validate the name in DNS responses. The parsing of malformed responses could result in a read past the end of an allocated structure. An attacker with a privileged position in the network could leverage this vulnerability to cause a denial-of-service condition. Domain name label parsing DoS 6.5 2020-27737 Nucleus NET The DNS response parsing functionality does not properly validate various length and counts of the records. The parsing of malformed responses could result in a read past the end of an allocated structure. An attacker with a privileged position in the network could leverage this vulnerability to cause a denial-of-service condition. Domain name label parsing DoS 6.5 2020-27738 Nucleus NET The DNS domain name record decompression functionality does not properly validate the pointer offset values. The parsing of malformed responses could result in a read access past the end of an allocated structure. An attacker with a privileged position in the network could leverage this vulnerability cause a denial-of-service condition. Message Compression DoS 6.5 2021-25677 Nucleus NET The DNS client does not properly randomize DNS transaction ID (TXID) and UDP port numbers, allowing attackers to perform DNS cache poisoning/spoofing attacks. Transaction ID DNS cache poisoning 5.3 Yet to be Assigned NetX In the DNS resolver component, functions do not check that the compression pointer does not equal the same offset currently being parsed, which could lead to an infinite loop. In the function. The pointer can also point forward and there is no out-of–bounds check on the packet buffer. Message Compression DoS 6.5 The effects of NAME:WRECK could include; stealing data or allowing a malicious actor to gain access to a network that a IoT device running a vulnerable TCP/IP stack is connected to through the RCE vulnerabilities. Or attackers use NAME:WRECK disclosed DoS vulnerabilities they could use it to disrupt operations through effectively disabling vulnerable IoT devices which could lead to downtime and significant financial loss. The list of potential attack scenarios could go on. The takeaway is that NAME:WRECK affects a large amount of devices in the IoT ecosystem.
Identifying devices vulnerable to NAME:WRECK
Currently the Ordr engineering team is working on functionality within our active scanning feature to utilize Internet Control Message Protocol (ICMP) “pings” to be able to identify IoT devices utilizing these vulnerable TCP/IP stacks. We plan to quickly have this feature included and rolled out to all Ordr customers this week.
Unfortunately accurately identifying IoT devices utilizing these vulnerable TCP/IP stacks is extremely difficult to do by passively listening to the network alone. It may be possible to detect some of these vulnerable TCP/IP stacks by listening to certain events like DHCP handshakes which include option data in a specific order, which could be used to identify vulnerable TCP/IP stacks DHCP implementation, but that would require IoT devices to be setup to use DHCP or some special configuration and circumstances that could lead to misdetection. Therefore, active scanning devices for vulnerable TCP/IP stacks is the preferred method of accurate detection.
However, for critical devices in regulated industries like healthcare and manufacturing, the active scanning technique is not a preferred method so as to not interfere with their mission critical operations. Ordr has passive scanning methods to accurately identify these devices and could create exclusion lists if the customer chooses to apply active scanning methods on customer class IoT devices to identify these vulnerabilities.
How to detect NAME:WRECK
Currently there are no known exploits for the NAME:WRECK vulnerabilities. The Ordr security team is actively monitoring the security communities for any proof-of-concept (PoC) exploits, or malicious actors that maybe creating exploits for these vulnerabilities. If that happens the Ordr security team will release network detection signatures for the known PoC or malicious NAME:WRECK exploits.
How to protect vulnerable devices from NAME:WRECK
Although identifying devices that are impacted by NAME:WRECK and patching them is an obvious step for responding to the NAME:WRECK vulnerabilities, organizations must take broader steps to ensure that their networks are hardened against threats like NAME:WRECK. That includes embracing the principles of Zero Trust security to help ensure that your network will be resilient against undiscovered vulnerabilities, regardless of which form they take.When applying the Zero Trust concept to devices, it means that networks are configured in such a way that, whenever a new device appears on a network, or an existing device’s configuration changes, the device has no access to the network or the hosted resources until a security administrator has verified that the device should be granted access.
In addition, network administrators should adhere to several other best practices associated with Zero Trust:
- Do not rely on firewalls or private IP addresses to establish which devices are “safe.” Instead, identify each device that exists on a network and ensure that it can be trusted before you grant it access to network resources.
- Implement least-privilege access. Grant devices only the minimal access privileges they need to operate.
- Use Multi-Factor Authentication (MFA). MFA is a security enhancement that requires a user to present two or more pieces of evidence when logging in to an account.
- Implement microsegmentation. Grant access privileges to each device on a highly granular basis, rather than assigning broad access rights. Policies are tailored to the individual needs of each device on the network.
Proactive protection of IoT devices with Ordr
The NAME:WRECK vulnerabilities highlight the risk of having IoT and unmanaged devices, even when they run software that has been used and trusted for decades – proving the need again for proactive protection and deep visibility.
Organizations globally, use Ordr to protect their network and devices from vulnerabilities like NAME:WRECK by discovering all network-connected devices, identifying vulnerable assets impacted by NAME:WRECK and other CVEs, detecting and flagging anomalous behavior using a built-in intrusion detection engine, and then using these device insights to proactively protect devices from vulnerabilities by dynamically generating policies and enforcing them on next-generation firewalls or NAC solutions.
Jeff Horne
Jeff Horne is currently the CSO at Ordr where he is responsible for security direction both within Ordr products and internal security. Prior to Ordr Jeff was the VP of Information Security for Optiv where he was responsible for all Security Operations, Governance Risk and Compliance, Endpoint, Internal Incident Response, Physical Security, and Employee Security Awareness groups. Before Optiv Jeff was the Senior Director of Information Security for SpaceX where he was responsible for the overall security strategy of SpaceX and managing the Information Security, Compliance (ITAR), Security Operations, and Physical Security groups. Previous to SpaceX Jeff was the Vice President of R&D and Chief Architect for Accuvant LABS where he managed teams of researchers and consultants specializing in reverse engineering, malicious code, incident response, breach analysis, and vulnerability assessment. Prior to Accuvant Jeff was the Director of Threat Research at Webroot Software where he led several teams of malware researchers, reverse engineers, and a development organization specializing in creating anti-malware functionality and detection signatures for all Webroot products. Jeff began his career as a Vulnerability Researcher at Internet Security Systems where he was responsible for vulnerability discovery, exploit creation, IDS evasion research, and behavioral detection of malware. Jeff is well known for his insight in interviews for numerous news channels and publications, speaking roles at various security conferences, as well as authoring several vulnerability disclosures and patents.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
Knowledge BaseHow to Detect Ransomware
…to track users’ access to the devices, applications, and systems on the network. Command and Control Once the command and control phase has been reached, the attackers are communicating with…
How to Detect Ransomware
8Min ReadIt’s no secret that there are cyber criminals out there who are after your company’s critical assets, but now you have to be concerned with your data not only being exfiltrated and sold—you have to worry about losing them entirely if you can’t or won’t pay a ransom..
Once upon a time, firewalls were a viable way to protect assets, but companies can’t rely anymore on the moat keeping the castle safe. It’s too easy to get the keys to the gate, especially with the extended enterprise – cloud, SaaS and remote work.
An astounding 70% of ransomware attacks succeed in encrypting a company’s data. This is due to how quickly ransomware can infect a system. Microsoft’s research determined that 97% of ransomware attacks infect the intended target within four hours. As if that isn’t disturbing enough, more advanced ransomware infections can infiltrate and assume control of a system in less than 45 seconds.
What is Ransomware?
Ransomware is a type of malware that loads itself into your system, spreads like wildfire, locks down files and data via encryption, and then holds it hostage for ransom. It has surged to the forefront as one of the most popular cyberattack methods, and now companies must contend with even more advanced tactics from cyberattackers utilizing Ransomware-as-a-Service.
Ransomware has many avenues into your organization. It can arrive in an infected attachment, which attacks your system once the attachment has been downloaded. Ransomware also can infect via an executable file, an infected website, a fake ad that a user interacts with, or even an infected chat message that contains a clickable link. It can even hide inside of a macro in a Word document.
One of the most common ways to launch ransomware attacks is via phishing. Phishing is still done via email, but it’s now also done with voice calls (vishing) and SMS (smishing). Adversaries also deploy different methods, such as hitting a smaller selection of targets (spear fishing), even executives specifically (whaling). It’s a complex environment with highly believable messages, emails, or phone calls. Social media even plays a part—everyone has seen those “Getting to Know You” posts, which are often really just fronts for obtaining your details that are helpful in stealing your information for their own nefarious purposes.
Ransomware Attacks: What Have We Learned?
Ransomware has definitely made its presence known: a new organization finds itself in battle with ransomware roughly every 11 seconds. Analyzing past attacks and their outcomes allows us to measure the impact of ransomware and evolve protections used against them.
Colonial Pipeline Attack
In May 2021, the Colonial Pipeline was attacked by a group known as DarkSide. The group entered the systems via a stolen set of credentials for the Colonial Pipeline’s VPN. Within two hours, Darkside stole roughly 100 gigabytes of data and deployed the ransomware as they exited. The ransomware made itself known the following day, and Colonial Pipeline was forced to shut down its pipeline OT network because their IT systems including billing and accounting were down.
The impact of this attack was substantial. The airline industry had a jet fuel shortage. The fear of gasoline shortages incited panic in six eastern states. Gas prices spiked, affecting consumers. And then there was the $4.4 million ransom that Colonial Pipeline paid. The Department of Justice recovered roughly $2.3 million of that ransom, but Colonial Pipeline was out the rest of the funds, in addition to the cost of being completely shut down for six days.
This attack displays the importance of using a multi-layered approach. Once DarkSide breached the gate (the VPN), they went unchecked. It’s essential to monitor the network for ransomware, inspect traffic, and implement additional checks, like multi-factor authentication, to protect against this type of attack.
JBS Incident
The JBS attack was the second major one that affected U.S. infrastructure in May 2021; this attack was perpetrated by REvil, a Russian-based ransomware-as-a-service organization. In addition to shutting down services, it’s believed that sensitive customer data also was stolen. The company deemed it had no choice but to pay the $11 million ransom to protect their customers.
This incident had a global impact. It shutdown cattle slaughtering in all US plants for a full day, which caused food supply disruption and increased food prices. Some Australia and Canada operations were disrupted, as well.
The details of this attack haven’t been released, but it was deemed to be highly sophisticated.
Zero Day Attack On Kaseya
In July of 2021, REvil used Kaseya’s virtual system administrators (VSA) to disperse ransomware to Kaseya’s customer base. Because many of Kaseya’s customers are managed service providers (MSP), the ransomware was further dispersed to their customers. It was one of the largest ransomware sprees in history.
The impact of this attack was extensive. Over 22 countries were affected, with roughly a million individual systems having been put at risk in a wide range of industries. It’d be impossible to list every single effect of such a widespread attack, but it provided a great example of why efficient, effective cybersecurity is necessary.
The Kaseya attack shows us that prevention won’t always work. Because there was no barrier to entry, discovering lateral movement would be the best chance of containing damage in situations like this. Complete east-west traffic monitoring would be the best way to detect such an attack. It also demonstrates the importance of microsegmentation and a Zero Trust cybersecurity strategy, which in this case would’ve allowed the organization to shut down the affected area and prevented the infection from spreading.
Detecting Ransomware
Ransomware is an issue that every organization faces. It’s essential to detect ransomware before it has encrypted your organization’s files, because then it’s too late to take effective action.
Ransomware can be detected at various stages of the cyber kill chain:
Reconnaissance
In this stage, the attackers focus on checking out your organization’s systems. This could be looking for viable breach opportunities by scanning ports or networks, or collecting information about the system and/or users.
In order to detect ransomware in the reconnaissance stage, your system must be capable of detecting any network or port scans that are performed. Ordr supports the ability to detect reconnaissance attacks.
Weaponization
Weaponization refers to applying various techniques to the code after reconnaissance so it’s capable of evading memory-, network-, and/or file-based cyber defense measures employed by the targeted network. For example, attackers may make the payload look like a simple PDF or hide it inside a benign-looking word document.
To combat this effectively, it’s essential to stay updated on patches and security updates. Also, employ a solution, like Ordr’s platform, that utilizes a variety of threat intelligence and security sources, as well as AI and DPI, to identify the high-risk devices on the network that may be targeted. Ordr can dynamically generate segmentation policies for devices that run outdated operating systems that cannot be patched.
Delivery
This is the kill chain stage that’s concerned with loading the ransomware into your organization’s system. It could be via an email containing an infected attachment or plugging in a compromised USB drive. Or, it could be gaining credentials or assistance from an employee through social engineering, or using a traffic distribution system (TDS) to redirect traffic from a legitimate website to a malicious website.
Device security is effective here, because if a device can be seen as compromised, it can be quarantined. Along that same line, if microsegmentation is used, the small section of the network where the ransomware is initially deployed can be locked down to prevent compromising the rest of the network. Other applicable protections include adequate change management and application whitelisting. Ordr can dynamically create the appropriate microsegmentation policies based on business risks.
Exploitation
Exploitation is where the ransomware actually launches itself on the victim machine. Typically, this is done one of two ways: exploit kit or specific, targeted exploitation. The difference is whether or not the threat actors have a known vulnerability to exploit. If the vulnerability is known in advance, it’ll be specifically targeted.
Using secure passwords, security patching, and continuous network monitoring can help thwart ransomware’s ability to successfully exploit your system. It’s essential to make the network harder to exploit and also slow down anything that does manage to get into the system. The Ordr platform includes an integrated threat detection system that can identify exploits and attacker tools, such as Cobalt Strike or Eternal Blue.
Installation and Lateral Movement
Once the initial infection is in, the installation phase is where the infection begins to disseminate itself within the network. Sometimes the ransomware needs to make an external C2 communication in order to complete this, but other types of ransomware begin lateral movement on their own. The ransomware targets files in the system and any accessible backups.
To successfully combat ransomware, a system should monitor for these C2 communications so an attack can be isolated. It’s also necessary to monitor traffic, especially with regard to east-west lateral movement. Ordr uses machine learning to baseline the normal communication patterns for a device; as a result, lateral movement or anomalous communications to a C2 site will trigger alerts. Ordr also integrates with Active Directory to track users’ access to the devices, applications, and systems on the network.
Command and Control
Once the command and control phase has been reached, the attackers are communicating with the attacker domain (C2). They are in the network and very likely have already started the process of encrypting data and/or exfiltrating it for extortion purposes. The attackers are now in control and issue the ransom demand.
Actions on Objectives
At this point, the ransomware provides the instructions for paying the ransom. Whether your data is actually returned after paying the ransom is another story.
Best Practices for Ransomware Detection
Ransomware comes in many different shapes and sizes, and often strikes with an unknown advantage. For this reason, your organization’s cybersecurity should be armed with both prevention and detection. The following best practices can help arm your cybersecurity solution:
1. Focus on basic cybersecurity hygiene
Cybersecurity technology constantly evolves, but there are basic practices that can help your organization mitigate the impact of ransomware. Examples of this include conducting regular vulnerability scans and having a regular patch schedule. Ordr gives you a strong cybersecurity solution that helps you follow such best practices—having detailed info about each device’s make, model, serial number, location in the network identifies vulnerable devices, and mapping every device communication patterns is critical to establish a baseline so you can identify when an attack is happening.
2. Establish process and compliance procedures
Ransomware affects an organization as a whole, and any processes and procedures need to be known and followed by the organization as whole. Important stakeholders and key decision makers should be involved in this process. For example, during a ransomware attack, who is going to negotiate with the attacker? What is the criteria for deciding when you’re going to pay a ransom?
3. Prioritize continuous improvement
Ransomware becomes smarter and more intricate all the time and can explode from a threat to a crisis in the blink of an eye. A static system of protection isn’t viable for long, so your organization needs to continuously improve cybersecurity. Identify vulnerabilities and security weaknesses so you can correct them before an unfriendly source reveals them for you. Ordr’s platform helps automate continuous improvement and is agentless so you can effortlessly have state-of-the-art protection at your fingertips. Ordr sensors deploy across the network, so while most organizations focus on north-south threat detection, our platform also performs east-west traffic analyses to detect lateral movement—a major blind spot for enterprises.
4. Implement zero trust
Zero trust is a revolutionary take on cybersecurity that states nothing should be trusted and everything must be verified. Zero trust is highly effective against cyberattackers, and helps protect your organization from ransomware and other cyber incidents.
Where to Go From Here
Ransomware is an ever present threat that needs to be caught early in the cyber kill chain to prevent significant damage to your organization’s systems. The key to this is identifying devices that are at risk prior to the attack and locking them down. During an attack, it’s critical to determine what device has been compromised, where that device is located in the network and what it’s communicating to. From there, rapid mitigation can be employed to contain the infection. Finally, retrospective analysis provides the ability to identify potentially infected devices or systems when new indicators of compromise emerge, allowing you to identify security systems that are being bypassed.
Ordr offers superior ransomware protection across the kill chain starting with comprehensive visibility into devices and risks (including complete details about devices, with granular insights—such as make, model, serial number, and network location). Our solution is capable of illuminating network blind spots by monitoring for east-west lateral movement and identifying attacker exploit tools. Our machine learning engine can baseline communication patterns to recognize an attack in progress, such as C2 communications. Finally, automated policies allow security teams to take action rapidly.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogThe Impact of Digital Transformation on the Security of Connected Devices
BlogThe Impact of Digital Transformation on the Security of Connected Devices…devices and using them as a platform for attacks, including data exfiltration after establishing communications with command-and-control servers in Russia. Digital Supply Chain Security Digital supply chains that allow for…
Integration
The Impact of Digital Transformation on the Security of Connected Devices
6Min Read
By Pandian Gnanaprakasam

The rapid proliferation of connected devices is expanding the enterprise’s attack surface and security risk profile. Ordr co-founder and CPO Pandian Gnanaprakasam addresses the impacts digital transformation has on connected device security. Today’s tech-dependent enterprises are no strangers to change. Our customers’ experiences demonstrate that familiarity daily. Whether they operate in healthcare, financial services, manufacturing, education, or government, they must contend with a constantly evolving infrastructure within their organizations, and constantly evolving threats from the outside. On top of that are the regulations and evolving business standards and practices that influence day-to-day operations.
Embracing digital transformation for all its benefits means buckling in for a bumpy ride—bumpier for some industries than others. Digital transformation expands an organization’s capabilities and opportunities, but it takes effort. In healthcare, for example, I recently stumbled on an interesting digital transformation report stating that only 16% of healthcare providers are in the “win zone,” meeting their transformation goals and driving sustainable change. The average across other industries is over 30%. That figure may be discouraging, but it is absolutely understandable, and organizations in healthcare as well as other industries can learn a lot from the experiences of their peers.
High Risks, Big Rewards
Using technology to improve patient care and operations sounds simple, but it is a complex endeavor that takes herculean effort. The pandemic briefly diverted attention away from long-term planning, but most health delivery organizations (HDOs) and other enterprises are back to addressing their plans and priorities. They are beginning to switch back from being reactive to a proactive mode. And with good reason.
Although high stakes, high costs, and risk aversion have discouraged many in the healthcare industry and beyond from fully embracing digital transformation, the rewards are too great to ignore. And the threats, expectations and competition all organizations face are not standing still. Done well, digital transformation delivers benefits that outweigh the risks and so, for those that have been reluctant to act, the time to embrace digital transformation is now.
What’s Fueling this New Wave of Transformation?
Over the years, every organization I have worked with—no matter how big or small—boils down their core priorities to three essential goals:
- Protecting people and the network
- Preserving service availability
- Improving operational efficiency
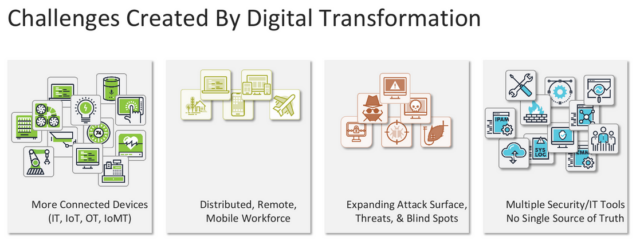
Those goals never change, even when the tools and strategies for achieving them do. And what’s more, they are transferable to other contexts as well: keeping manufacturing equipment operational and staff safe on the shop floor, preserving service availability for financial transactions, maintaining the operational efficiency of constituent services, etc. Consistent with these goals, here are some key initiatives and capabilities that are driving this new wave of transformation and pushing the boundaries of operational potential.
- Remote workforce support (i.e., work from home);
- Remote facility, branch, and clinic operations;
- Contractor and equipment maintenance support and outsourcing;
- Data center transformation and migration to hybrid cloud;
- Digital supply chain enablement; and,
- Mergers and acquisitions.
These use cases show how, more and more, connected devices are integral to fulfilling an organization’s mission. And as the inventory of connected devices expands—including the Internet of Things (IoT), Internet of Medical Things (IoMT), operational technologies (OT), mobile, and other devices—those deployments reflect the evolution of the technology. Assets that were once under tight control, on-premises and behind the firewall, are now expanding and connecting beyond traditional boundaries, across multiple network dimensions, and outside of the view and control of IT.
Here are some examples:
- Access from Any Device – IT, IoT, IoMT, OT, IoXT.
- Access from Anywhere – remote sites, remote workers, telemedicine.
- Deployed Anywhere – private and public cloud, virtualized data centers.
- Modern Apps/Mobile Apps – XaaS, training, collaboration, any device-anywhere-any deployment support.
- Ecosystem – third party apps, supply chain access, mergers and acquisitions.
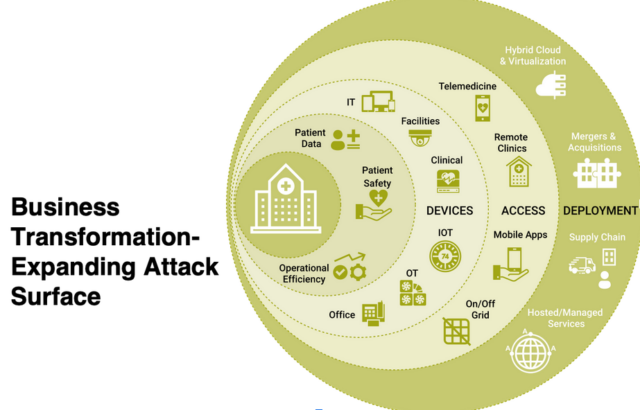
What Keeps the CXOs Up at Night?
IT leaders tasked with driving new digital transformation initiatives understand that success goes well beyond merely integrating new technologies and getting them up and running. Enjoying the multitude of benefits that can follow the completion of a technology refresh comes with many elements contributing to the pucker factor that keeps a CXO awake at night. An expanded and expanding attack surface is at the heart of this unease. Acknowledging that fact, and the factors that play into those concerns, is the first step in planning for and addressing them during the transformation process, rather than promising yourself that you’ll “get to it eventually.” Some pucker factors are reflected in several troubling trends.
Surge in Ransomware Attacks
Ransomware attacks are now more frequent, sophisticated, and severe than ever—and getting worse. Attackers know that many organizations will pay huge ransoms because costs associated with downtime and operational disruption may be even higher than what attackers demand. In healthcare, disruptions caused by ransomware can have life and death consequences.
Prevention is the best way to deal with the ransomware threat, but old school methods simply don’t work. Prevention demands accurate and timely detection, and response automation that can block an attack from progressing to its target destination. You need a way to detect ransomware early, before it has encrypted your organization’s files, because then it’s too late to take effective action.
State-Sponsored Attacks
Adversarial nation states have become adept at using the ambiguity of cyberwarfare to launch attacks on critical infrastructure and economic targets, as well as organizations that hold valuable intellectual property. The tools and methods developed for these campaigns are rarely confined to a limited set of organizations either, as sowing chaos is part of the strategy.
For example, the U.S. Cybersecurity and Infrastructure Security Agency (CISA), along with the FBI and Treasury Department issued a joint advisory about North Korean Maui ransomware targeting the healthcare industry. Similarly, Russian threat actors have been hard at work compromising connected devices and using them as a platform for attacks, including data exfiltration after establishing communications with command-and-control servers in Russia.
Digital Supply Chain Security
Digital supply chains that allow for remote and automated service between organizations have been a boon for operational efficiency—and for threat actors able to compromise those connections for their own ends. The SolarWinds Orion attack targeting U.S. federal agencies and commercial enterprises illustrated how damaging supply chain attacks can be.
Vulnerable SolarWinds servers sitting inside agency and corporate networks, operating with privileged access to IT systems, proved to be a gold mine for hackers to exploit and get whatever data they need, including high level state and military secrets.
Shadow IoT
One big security challenge faced by enterprises today is the presence of connected devices on their networks operating outside the view of IT security and operations. Known as “shadow IoT,” these devices epitomize the mantra you can’t protect what you can’t see. A recent Five Fifty report by McKinsey highlights the risk of the proliferation of devices connecting to the network as shadow IoT (such as the infamous hack of a casino using a connected aquarium thermometer as the vector of attack) and lack of readiness for most organizations.
Often these systems operate with outdated OSes, are unpatched, and unmanaged. Without proper onboarding—or a security platform able to detect, identify, profile, and monitor any device that connects to the network—any organization with shadow IoT operating within its IT estate is at risk of an attack.
How Ordr Helps Enable Secure Digital Transformation
Ordr’s mantra from the beginning has been to enable our customers to SEE, KNOW, and SECURE every device that is connected to their organization. To do this, we establish the most comprehensive and accurate single source of connected device truth in the Ordr Data Lake for each of our customers. This starts with automatically discovering and accurately classifying every connected device because you can’t secure what you can’t see.
From this foundation of visibility Ordr provides a complete view of the connected device attack surface including how devices are connected and communicating, which devices are vulnerable, and the unique risk each device represents in the environment.
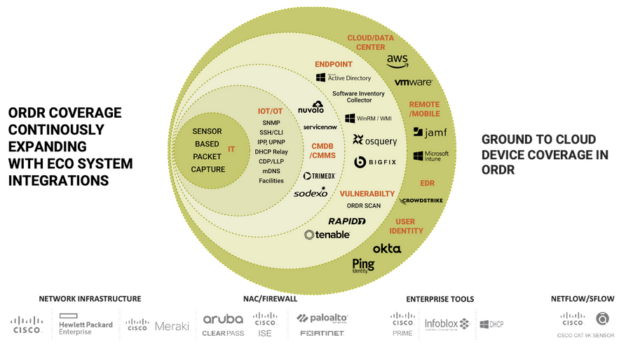
Integrations across the security, networking, and IT ecosystem are integral to the Ordr solution. These integrations enhance the already rich view Ordr has of connected devices by centralizing additional data points and device details. A good example of this are the recent integrations with Mobile Device Management (MDM) and Endpoint Detection and Response (EDR) platforms in the recent Ordr 8.2 release.
Integrations also enable Ordr to enrich the tools and workflows used every day and improve how teams manage and secure devices. An example here is the recent integration with the ServiceNow Service Graph Connector to help customers ensure the data in their CMDB is complete, up to date, and accurate. Another example is how Ordr device insights are used to optimize vulnerability scanning with Qualys.
Integrations also help teams take action to address vulnerabilities, respond to active threats, proactively improve protections, and ultimately reduce risk. Ordr automates the creation of security policies and enforces those policies by integrating with a customer’s existing security and network infrastructure. With this approach Ordr customers are able to quickly block attacks, quarantine compromises devices, segment vulnerable devices, and accelerate Zero Trust projects to proactively improve security.
We continue to drive innovations across the Ordr platform and expand with integrations across the security, networking, and IT ecosystem to provide our customers with a single source of truth for all their connected devices. Reach out for a demo and to learn how Ordr can help you SEE, KNOW, and SECURE, all your connected devices.
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogQ&A with Tom Stafford, CTO for CDW Healthcare
BlogQ&A with Tom Stafford, CTO for CDW HealthcareRisk Management 7Min Read By Tom Stafford Tom Stafford, CTO with Ordr partner CDW, works hard to educate healthcare customers on which tools to use to best optimize patient safety…
Risk Management
Q&A with Tom Stafford, CTO for CDW Healthcare
7Min ReadBy Tom Stafford

Tom Stafford, CTO with Ordr partner CDW, works hard to educate healthcare customers on which tools to use to best optimize patient safety and hospital resources, and protect the enterprise from cyber risk. As a former hospital CIO, he knows the challenges from the inside. A little background on why I’ve agreed to do this guest QA blog for Ordr:
In my role as CTO at CDW Healthcare, I talk to former healthcare peers, in an advisory capacity, to help them protect patient safety and resources with the best cybersecurity technology solutions. Prior to joining CDW, I was CIO of Halifax Health where we deployed Ordr for our medical device security needs
I’ve been at CDW for slightly more than two years, after more than two decades in the healthcare trenches, most recently as the former CIO of Halifax Health. I decided on a different role at CDW to bring best practices and cybersecurity technologies to my CIO colleagues who are on the forefront of fighting the cyber war. If the healthcare industry could more effectively collaborate and share security expertise to mitigate cyber-attacks, we would stand a much better chance against the cyberattacker army working together against us every day!
What is your primary goal as the CTO of CDW Healthcare Division?
To bring awareness to our healthcare customers on the importance of bringing modern IT tools into healthcare organizations to optimize patient safety and hospital resources. With Ordr’s cybersecurity solution there are many ways network visibility helps hospitals beyond, of course, ransomware, but also what’s happening with device utilization, what’s happening with compliance and what’s being communicated externally. There are several important use cases we want to advise our customers about to develop a proactive plan before something bad happens.
Why is IoT and connected device monitoring and enforcement so unique for hospitals?
There’s a problem with biomed devices and it’s not going away. There will always be biomed devices that have outdated and unsupported operating systems. In the beginning, when first purchased, they were of course running mainstream and perhaps even state of the art operating systems, but now these operating systems are no longer supported by the manufacturers. As a result, O/S patches are no longer available to address vulnerabilities, even though these devices are still within their useful lifecycle and are still viable, delivering strategic care for patients and revenue to healthcare organizations.
Why weren’t patches performed on outdated operating systems on biomed devices?
Unfortunately, this is due to the biomedical industry. As a medical device design engineer for ten years, I may have helped cause the problem, although we thought it made sense the way we did it back then. We would buy an off the shelf computer and put it in a cabinet or a device we were creating, and it would run it. The computer we installed ran whatever the latest operating system was at the time. The issue back then was per the FDA 510k rules for class two, and three medical devices once the device was tested, it could never be altered. This included the operating system on the off the shelf computer. So, the manufacturers never changed them or patch the OS because they could not!
Can you patch today?
In 2016, the FDA reversed their guidelines and said you can patch devices now because it is important to upgrade operating systems. But it was a guideline, it was not a mandate. Because it was a guideline and because it is hard for biomedical manufacturing companies to transition to have a global patch program for all the devices they sell, they do not do it. And they do not want to release the product to an IT team to open it up and obviously, upgrade the operating system or patch it due to inherent risk on their part, because it might make their system not work properly.
Bottom line, the problem is going to persist because biomed devices will continue to outlast the useful life of their operating systems and CFOs do not want to replace a $4M imaging device that makes the hospital money every day only because it has a security vulnerability.
If you don’t patch what can the CISOs and security leaders to do?
They are stuck, because now they have a known vulnerability in their system, and they must do something about it. This is the reason I was introduced to Ordr.
How did you select Ordr for addressing the patching issue?
To get the security and network teams to completely agree on something was amazing.”
Our first step was to do a POC (proof of concept) by my IT security team. A few weeks later, my network and security team had a meeting with IT leadership to show the results of the POC. We were all blown away. I’ll never forget that moment because everyone was happy, even joyous which doesn’t normally happen with software in general.
To get the security and network team to completely agree on something was amazing, because normally, they have a little contention just due to their job functions where one wants data to flow, and the other one wants to control data.
Once deployed, did you meet your objective?
One of the major tenants of cyber security is to understand your landscape. And that includes all devices connected to your network. Are they patched? Or are they outdated and unsupported?“
I was amazed. Ordr worked and it worked well. We purchased Ordr originally because I knew I had a problem with older biomed devices running Windows XP. Before Ordr, our vulnerability scans would find them but then they would disappear because of their dynamic nature of how they connected to the network. And if we didn’t find them that very minute and physically locate them, we would lose sight of them. It was a real problem. We could not see and didn’t know our full landscape. And that is scary, because to me, one of the major tenets of cyber security is to understand your landscape. And that includes all devices connected to your network and their patch status. Are they patched? Or are they unsupported? It is not just your IT devices, it is anything that is connected to your network. As you know, in the last five years, that’s grown greatly with so many other things connecting now, and you still have these legacy biomed devices that are out there too.
How did you manage all the outdated and unsupported biomed devices you found?
When we fully deployed Ordr, we noticed a couple of things right away. First, we not only found all the biomed devices, but we also now had an inventory of them. And we were able to understand what operating systems they were running and could have a plan of what to do about it. At that time, we had three choices.
- Replace the device. But again, financially that might not be viable.
- Get the manufacturer to patch it, or to upgrade the operating system so it was no longer vulnerable.
- Bury it by micro segmentation. Through micro segments, you have controls around it from the internal firewall, Even though we have controls, you still need to monitor it and we used Ordr.
When I would talk to people, they understood Splunk monitors user behavior. Ordr monitors device behavior. I can now set upper or lower limits on the device itself. And if Ordr detects something odd, we can be alerted
What was the next step to managing these vulnerable devices?
If the hacker gets in and gets to an XP device, that would be the biomed device, it takes about 20 minutes for them to own that device. If the device is connected to a server, then they can own the network.”
The roadmap was moving more towards enforcement and that sat well with me. The reason why is that hackers do not attack during the day, they tend to attack at night and on weekends. At those times, depending on what hospital you’re at, you might be relying on a managed Security Operations Center (SOC), which is pretty good. Or you might be relying on your on-call staff to fight any cyber problems in the middle of night. And there’s latency in that. If the hacker somehow gets in and gets to an XP device, it takes about 20 minutes for them to own that device. If there are any servers connected to that kind of device, then they have the opportunity to own the network. Now the world turns bad quickly. To have a system that has deep understanding of proper network communication related to strategic IoMT devices and can monitor those devices 24/7and alert us when something is wrong, is great.
Next, if I could actually enforce policy, or at least send API commands from Ordr to change the policy in my firewall or my NAC, these devices could shut down communication at 3 am in milliseconds. This is much better than the time it would take the team to figure out what the problem was, based on a calls to the service. IoT and connected device security enforcement can stop a virus from propagating
What else could you do now with full visibility of your network landscape?
Device utilization is a big deal. Ordr creates custom views per departmental stakeholders. For example, the Biomed and/or Operations team could go into their Ordr view and just look at medical device utilization. Their view doesn’t allow them to see the other aspects of cyber or network information Ordr was capturing.
I like to tell the story that if a clinician wants another ultrasound device in your hospital, but your ultrasound fleet is only being utilized 30% of the time, you do not need another ultrasound, you need to improve your processes to get better utilization of your devices. And when you do this, you save money by not buying another device while improving your processes. And so that is valuable.
For some devices, Ordr was monitoring down to the battery life level. Since we all know batteries go bad, to have an alert to the Clinical Engineering team for low batteries on biomed devices is cool and important.
The next important outcome we gained is forensic device data. Ordr collecting all device data in the cloud. When we have a potential security incident, we called the security team. The team uses Ordr to determine what device was bad and see who it was talking to and how it was talking, to see if it was doing things that it should not do. We always used Ordr during any security incident as part of our incident response toolbox. And it worked well. And even the network team liked it because Ordr does an incredibly good job of showing how everything communicates, and what it is trying to communicate and what is being blocked from communication.
To sum it up, first and foremost the outdated and unsupported biomed devices are a problem that is not going away, ever! Operating systems only have a life for so long, so you need something to address the issue. With Ordr though, you get more use cases including device utilization management, forensic data and the network team gets to see how things are communicating, outside of their regular forensic toolbox. So that’s why I like Ordr.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogOrdr Security Bulletin: Defeating Black Basta with OrdrAI
BlogOrdr Security Bulletin: Defeating Black Basta with OrdrAI…to have a close affiliation with the Conti ransomware group because of the similarities in their approach to creating malware, leak sites, and communication for payment negotiation and data recovery….
Blog
Ordr Security Bulletin: Defeating Black Basta with OrdrAI
6Min Read
By Pandian Gnanaprakasam
This security bulletin written with support from Ordr security research analyst Gowri Sunder Ravi
Ransomware attacks have become a critical threat to the healthcare industry, impacting patient care, data security, and disrupting operational continuity. The recent attack on UnitedHealth’s Change Healthcare subsidiary in February 2024 brought to light how attractive the healthcare industry and its data are to hackers. The ALPHV/BlackCat group was behind this attack and received a Bitcoin payment worth $22 million to restore affected data. Another notable threat group targeting the healthcare sector is the Black Basta ransomware gang.
Black Basta has targeted over 500 organizations in the past two years, and healthcare industries are no exception. A joint advisory was issued by the Federal Bureau of Investigation (FBI), Cybersecurity and Infrastructure Security Agency (CISA), Department of Health and Human Services (HHS), and Multi-State Information Sharing and Analysis Center (MS-ISAC) detailing the Black Basta threat.
Insights from the Advisory
The alert was issued after a ransomware attack hit major healthcare provider Ascension, affecting the critical services and systems of 140 hospitals in 19 states. Black Basta is regarded as a ransomware-as-a-service (RaaS) operator, and the group’s attacks have impacted more than 500 organizations and critical infrastructure operators in North America, Europe, and Australia between April 2022 and May 2024 according to the joint advisory. Black Basta has encrypted and stolen data from 12 of 16 critical infrastructure sectors, including the Healthcare and Public Health (HPH) sector.
Like many other members of the ransomware family, Black Basta exploits known vulnerabilities or uses phishing methods to gain initial access. Moreover, the advisory revealed that since February 2024 the group has exploited critical vulnerabilities in the ConnectWise ScreenConnect remote desktop software management application. Similarly, researchers from Trend Micro have linked Black Basta in exploiting CVE-2024-1709, a critical vulnerability with a CVSS score of 10.
Recommendations for Healthcare Organizations:
All organizations and cybersecurity professionals should implement effective cybersecurity measures that align with the Cross-Sector Cybersecurity Performance Goals (CPGs) developed by CISA and NIST. The mitigation tips include the following:
- Update firmware, software, and operating systems to the latest versions as soon as they are released.
- Install modern anti-malware software and update signatures where needed.
- Implement phishing-resistant multi-factor authentication (MFA) across a wide range of services.
- Always validate the URL of the link by hovering the cursor over the link and check if it matches the link’s text.
- Healthcare organizations should ensure that electronic public healthcare information (ePHI) is secured and compliant with HIPAA.
- Organizations must identify their critical business assets by using active scans, passive processes, or a combination of both.
- Identify, evaluate, and prioritize vulnerabilities across the environment so they can be dealt with appropriately within time. For prioritizing vulnerabilities, use the Common Vulnerability Scoring System (CVSS), which helps decide which vulnerabilities to prioritize.
CISA and NIST also recommend continuous testing of the security program to ensure its optimal performance against the MITRE ATT&CK techniques.
Black Basta – An Overview
Black Basta is a notorious ransomware variant and Ransomware-as-a-Service (RaaS) operator that first appeared in early 2022. According to Malwarebytes, the group was linked with 28 of the 373 confirmed ransomware attacks carried out in April 2024. BlackBasta is believed to have a close affiliation with the Conti ransomware group because of the similarities in their approach to creating malware, leak sites, and communication for payment negotiation and data recovery.
Black Basta has targeted organizations across the globe, including a recent attack on the Toronto Public Library, Canada’s largest public library system, disrupting library services, including access to digital resources, patron information, and other essential functions.

(Image source: hhs.gov)
The group’s primary targets are the English-speaking “Five Eyes” countries of Australia, Canada, New Zealand, United Kingdom, and United States, suggesting a possible political agenda in addition to seeking financial gain. Black Basta use a variety of tools and remote access methods to execute their attacks and exfiltrate data, including Qakbot, SystemBC, Mimikatz, CobaltStrike, and Rclone.
The group employs the double extortion tactic, encrypting the victims’ data, and threatening to publish it online if their demands aren’t met. In early campaigns, Black Basta used email or spear phishing methods to get initial access to a target organization and deploy ransomware on their devices. The gang has also used other techniques to deploy ransomware, like disabling the compromised system DNS to complicate the recovery process and deploying ransomware that targets Linux-based VMware ESXi Virtual Machines (VMs). They have a public leak website where they publish data about their victims and samples of stolen data to create pressure to pay ransom.
Despite its success and widespread impact, Black Basta maintains a low profile, operating similarly to private threat groups like Conti, TA505, and Evil Corp. The group’s modus operandi is to conduct a careful assessment of an intended target before conducting a focused attack. This sets them apart from threat actors that conduct broader, less selective campaigns.
How Ordr Helps
Organizations are increasingly exposed to cyber threats like ransomware attacks without even knowing about them, mainly because the enterprise attack surface continues to expand making it challenging for security teams to correlate asset data across multiple sources to identify security gaps, prioritize vulnerabilities, and remediate threats. Fortunately, OrdrAI Protect and the recently launched OrdrAI CAASM+ solutions provide comprehensive and accurate deduplicated asset visibility, thus preventing exposures.
SEE:
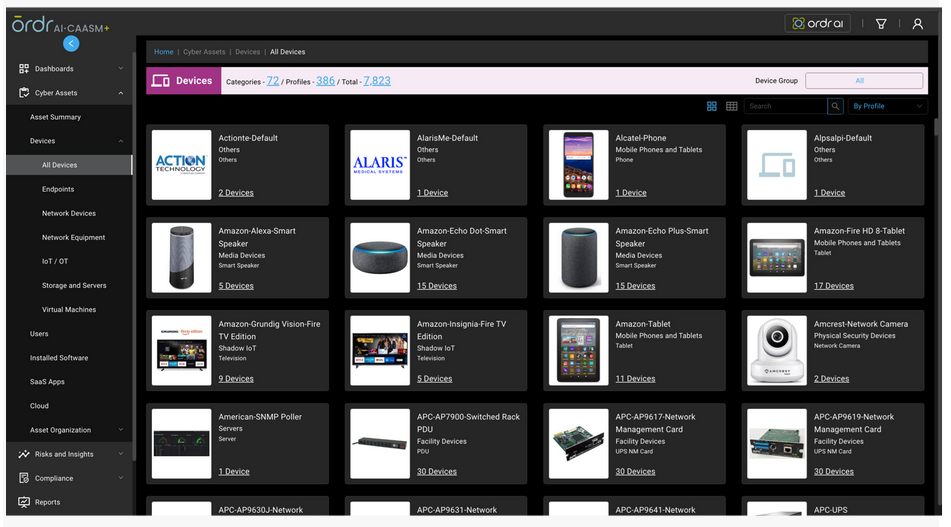
OrdrAI automatically discovers, classifies, and profiles all devices based on the manufacturer, make, and model, while providing a granular view of data flows and asset attributes associated with all the devices in your environment.
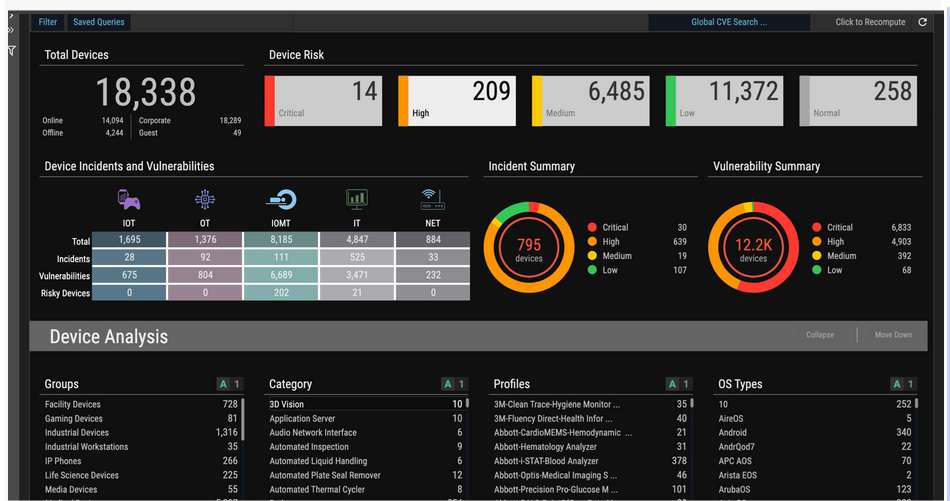

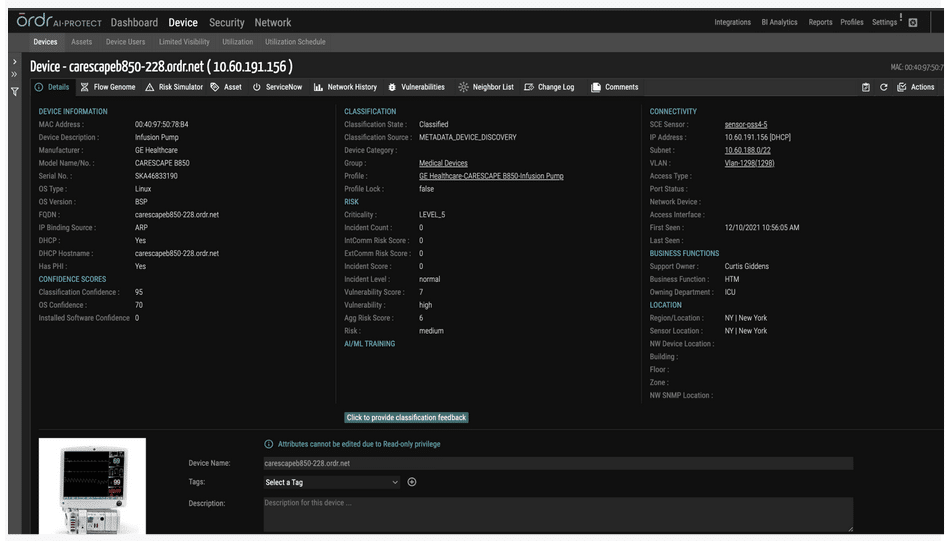
OrdrAI correlates and deduplicates all asset data (Including users, installed applications, IoT and IoMT, OT, cloud services, and more) across multiple sources, then classifies and profiles all devices based on the manufacturer, make, model, and other information pulled from integration sources.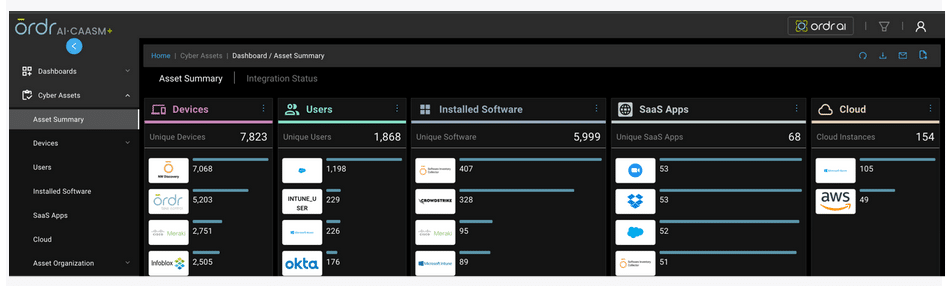

KNOW:
OrdrAI ‘s external IP/IOC detects and tracks asset communication to prohibited IP/URLs in real-time:
- Ordr provides in-depth insights into category traffic analysis that highlights the communication patterns between devices and external entities, making it easier to identify devices communicating to a list of prohibited countries or any group of IPs that customers want to monitor that are associated with popular threat actors.
- Ordr uses a continuously updated cloud-based threat intelligence platform, and all communications are marked accordingly in the Ordr Security Threat Card.
- Ordr has an IDS engine that can detect attacks associated with techniques used by Black Basta and generate alerts based on analysis of packets transacting over the wire.
- Ordr also provides the capability to baseline all communications based on profile, location, business function, or any customized entity using our AI/ML techniques.
- Ordr detects anomalies based on any deviations observed for this traffic.
OrdrAI uses multiple methods to collect and deduplicate the vulnerability data from multiple sources and provide an easy way to manage the vulnerabilities.
- Conducts analyses based on data collected using passive and active techniques, make, model, manufacturer, OS, and from integration with vulnerability assessment systems like Rapid7, Tenable, and Qualys. This works for assets that can withstand scan and are scanned regularly.
- OrdrAI Software Inventory Collector is a lightweight script that detects based on KB/HF correlation instead of scanning the asset for vulnerabilities. This works great for assets that cannot withstand scans, and for assets that are not updated regularly.
- OrdrAI uses known exploitable vulnerability (KEV) data and the Exploit Prediction Scoring System (EPSS) to provide additional context to the vulnerabilities based on the real-world data.
- OrdrAI provides additional context to assets with vulnerabilities, including normalizing risks based on classification, allowing users to modify risk scores based on asset criticality.
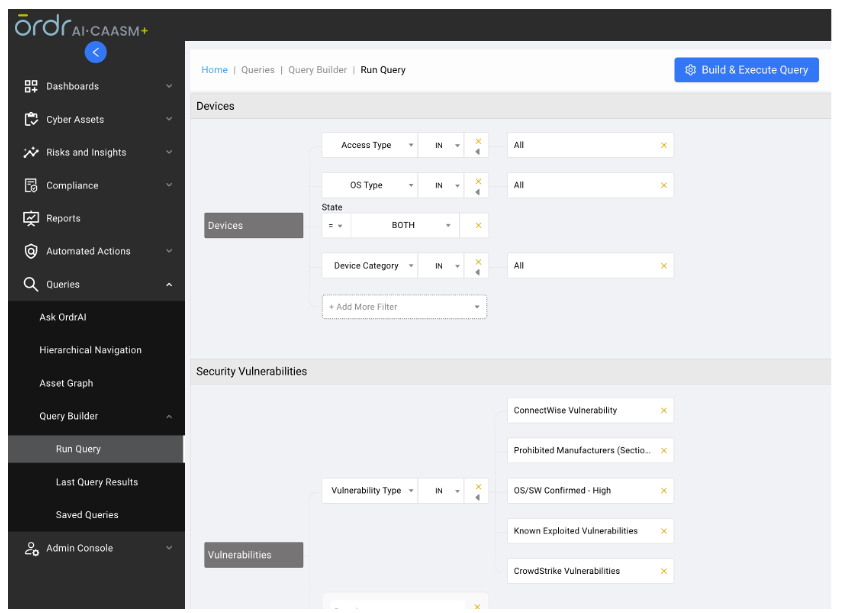
Based on vulnerability info collected by these methods, OrdrAI customers can get an accurate assessment of risks in their environment, including:
- Risk summary that dashboard delivers a high-level risk map of the organization making it easy for security teams to track gaps and vulnerabilities in their environment.
- A clear view of security gaps present in the organization via a “Security Control Gaps” dashboard highlighting devices without EDR Installed, MDM Installed, and devices not scanned by vulnerability scanners.
- A vulnerability dashboard that provides a complete “state of the union” on vulnerabilities affecting the organization.
- Compliance dashboards that provide a snapshot of non-compliant assets present in your environment.
- A query builder for creating custom dashboards or querying information based on customer needs.
- Ask OrdrAI for instant info on assets, vulnerabilities, coverage gaps, and user risk.

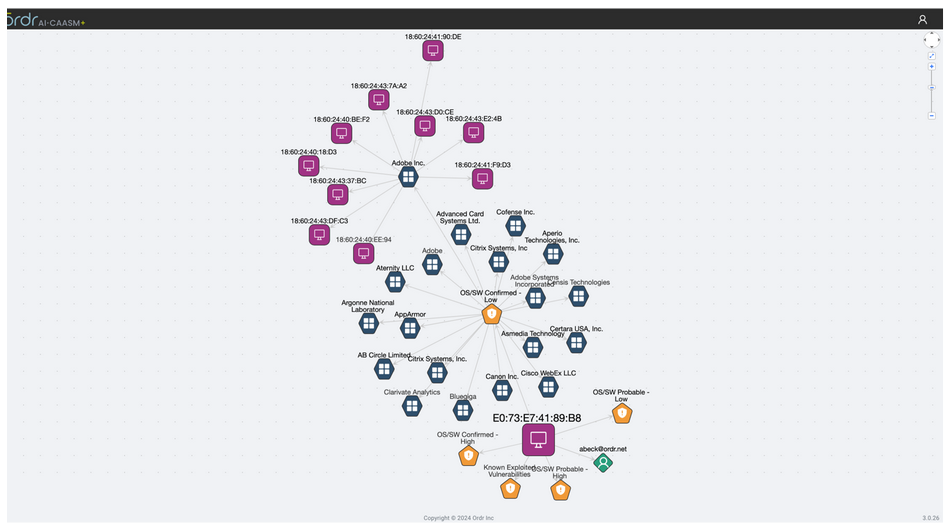
Customers can also get a detailed view of the blast radius via the “Asset Graph” feature, identifying devices, users, and applications associated with a vulnerable asset.
SECURE:
OrdrAI allows easy management of vulnerabilities, including assignments and status of the vulnerabilities, thanks to deep integration with vulnerability management tools like ServiceNow VR module, providing real-time status updates based on reconciled data. That delivers vital capabilities, including:
- Muting or removing a vulnerability from the system when information is not available or is hidden from publicly available dashboards. This is usually done when admins are not ready to patch and are waiting for validation from the manufacturer.
- Ability to assign vulnerabilities to individual users along with priority and due date. All this information can be shared with CMDB or any other asset management vendors.
- OrdrAI Protect also allows you to clear and mute incidents in addition to vulnerability related actions.
OrdrAI supports a variety of additional actions like
- Network based enforcement for reactive rapid threat containment (Change VLAN, Shutdown Port, Integrate with Firewall) for quarantining affected devices and limiting communications over certain protocols.This automation works with almost any networking, switch, or wireless controller vendor.
- Integration with ticketing system, messaging, and collaboration tools.
- Ordr segmentation add-on to enable segmentation of impacted devices, limiting access to only must-have communications based on Zero Trust policies.
Are you ready to learn more about Ordr products and how they can reduce the likelihood of ransomware attacks? Schedule a demo now!
Helpful links:
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
Knowledge BaseThe Healthcare Industry Is at Risk
…complete asset inventory is critical to progress from “detect” to “response”. For example, the ability to identify the device being compromised, where it is connected (physical and network location), and…
The Healthcare Industry Is at Risk
8Min ReadProtecting healthcare data from cyber attacks would be easy if organizations only had to worry about a few types of attacks, or if attempted breaches were rare.
Unfortunately, that’s not the case. Cyber attacks that target healthcare data and systems occur at a dizzying rate and come in many forms. The sheer volume of sensitive and diverse data–including Protected Health Information (PHI)–that healthcare organizations manage make it even more challenging to defend healthcare data and systems against cyber attack risks.
Establishing a plan to mitigate the risk of healthcare cyber attacks, and responding effectively when they occur, is critical for any organization that operates in the healthcare sector. This article offers guidance on how to manage cyber attack risks in healthcare by detailing common types of cyber risks and attacks, then explaining best practices for protecting systems and data.
Why the healthcare sector is at risk for cyber attacks
Cyber attacks occur in every industry and sector. However, healthcare organizations are at special risk, largely due to the fact that the information they produce and manage is a particularly alluring target for attackers.
Patient information often includes data, like treatment history information, that is unchangeable and can’t be erased or updated following a breach, meaning it holds special value. In fact, a single breach of a hospital or doctor office’s network could expose hundreds of thousands of individual records. This makes healthcare cyber attacks an especially lucrative activity for hackers. This helps explain why attacks that target the healthcare industry reached an all-time high in 2021 and have continued to climb since.
Another reason why the healthcare sector is targeted is because of the high propensity to pay a ransom. There is a zero sum choice between paying a ransom to a cyberattacker or risking patient lives by not being able to deliver healthcare services. In 2021, 61% of respondents to a Sophos healthcare study reported that they paid ransoms; this is a higher rate than any other sector. Additionally, with the continued focus on the pandemic and patient care, users can also be distracted, leaving systems unprotected or unknowingly clicking on a phishing email. This can make healthcare organizations more vulnerable and easier to target.
On top of this, PHI and other information stored by healthcare organizations is subject to special data privacy regulations, defined by the Health Insurance Portability and Accountability Act (HIPAA) and other regulatory laws. As a result, the impact of a breach in this industry can be especially grave. Other types of businesses may suffer financial harm or disruptions to their operations due to attacks, but they typically don’t face the steep consequences that apply in the case of healthcare cyber attacks.
The cost of cyber attacks
Due to regulatory consequences as well as a variety of other factors, the cost of a breach that impacts a healthcare business can be especially steep.
Fines assessed by the federal government for HIPAA violations amount to millions of dollars per year. Disruptions to hospital services can bring revenue to a halt, leading to losses of hundreds of thousands of dollars per day. Healthcare organizations that fail to deliver promised patient services, or can’t uphold standard safety and security procedures due to cyber attacks may also face lawsuits, further increasing the cost of a breach. And the harm caused by an attack to a hospital’s reputation may cause patients to seek care elsewhere, leading to a loss of future revenue.
When you add up these various costs, it’s easy to understand why the total financial fallout of cyber attacks is 9.44 million dollars, according to the latest data from IBM. And that’s just the average cost. In some cases, the cost of individual cyber incidents involving healthcare organizations in recent years have exceeded 100 million dollars.
Fortunately, as healthcare providers know better than anyone else, an ounce of prevention equals a pound of cure. By investing in cyber attack prevention, it’s possible to avoid the steep financial fallout of cyber attacks that target the healthcare industry.
To read a complete maturity guide on implementing connected device security for healthcare, please download the report here.
Preventing cyber risks
Attack prevention starts with understanding the types of systems that are at risk, as well as the specific types of attacks that may affect them.
In the context of healthcare, connected devices tend to be an especially easy target. Connected devices include Internet of Medical Things (IoMT) such as infusion pumps and patient monitors for patient care, or Internet of Things (IoT) such as HVAC systems and elevator control systems for hospital operations. Healthcare organizations typically manage tens of thousands or hundreds of thousands of devices like these that can increase the attack surface. These devices cannot be protected by conventional endpoint security tools like antivirus or endpoint security software. This means that they often represent low-hanging fruit for attackers looking to breach a hospital’s network.
Even if the devices themselves don’t contain sensitive data, they may connect to other devices or systems that do. That means attackers can use them as a “beachhead” where they gain initial access to internal resources, then execute other exploits.
Exacerbating the cyber risks that connected devices bring is the fact that many medical devices have long operational life cycles, and therefore run on outdated software which means that security updates are no longer available. Due to FDA regulations, it may also not be possible to apply updates to some medical devices; some medical device manufacturers also do not always offer software updates to address vulnerabilities. When devices run on outdated software, threat actors can easily exploit any vulnerabilities that are present.
Securing these connected devices, then, is crucial for healthcare organizations. The first step is to discover and classify what devices are actually connected to the network. This includes visibility into what the device is, what other devices or systems it is communicating with, and where it is connected. This granular visibility is critical to identify devices with risks and vulnerabilities. By baselining what is normal behavior for devices, organizations can quickly pinpoint anomalies that may be an early indication of an attack in progress. Finally, segmentation can mitigate risks for devices that are mission-critical, or those that are running outdated operating systems that cannot be patched.
Types of cyber threats
There are many types of specific cyber threats for healthcare organizations to manage. Each attack involves different techniques and different types of risks; therefore,each type requires different defense methodologies.
Ransomware
Ransomware is a type of threat that occurs when attackers plant malware, or malicious software, inside a company’s network. The malware encrypts important data, and attackers demand ransom in exchange for decrypting it.
Unless victims have access to a backup of their data, they are forced to choose between paying the ransom or suffering permanent data loss. Either way, the affected organization is likely to suffer a delay in operations: either while waiting for data to be decrypted or developing workarounds to restore operations in the absence of the lost data.
If ransomware attackers gain access to sensitive data like PHI, the incident could be considered a breach of healthcare regulations. Laws like HIPAA require public disclosure of these types of breaches. They may also lead to fines, especially if regulators determine that the breach occurred because the business failed to adhere to cybersecurity best practices.
Antivirus tools that can detect and block malware help to prevent ransomware attacks. Other best practices include monitoring the use of privileged protocols such as RDP and Telnet, and segmenting the network to prevent lateral movement. Creating regular data backups ensures that organizations can recover ransomed data quickly without paying the attackers.
When a ransomware attack occurs, the connected device security best practices described earlier, such as gaining complete asset inventory is critical to progress from “detect” to “response”. For example, the ability to identify the device being compromised, where it is connected (physical and network location), and whether security policies or compensating controls can be applied is crucial for security and operations teams responding to the ransomware attack.
Data breaches
A data breach is any type of incident in which sensitive information is exposed to unauthorized parties. Like ransomware attacks, data breaches can lead to regulatory fines. They can also disrupt organization operations, cause a loss of revenue, and ultimately harm the company’s reputation. This is an especially serious risk in the healthcare industry, where establishing patient trust is a paramount priority for organizations.
To prevent data breaches, organizations must securely store data. In addition to encrypting sensitive information, organizations should enforce strict access controls that grant data access rights only to the specific parties or individuals who need it. For example, one doctor should not be able to view information for patients receiving care from a different doctor.
Phishing, social engineering and Business Email Compromise
Phishing is the use of social engineering techniques to trick an organization’s employees into handing over sensitive information.
There are multiple types of phishing attacks. The most common type utilizes email to target employees with messages requesting passwords or access keys. In other cases, attackers might target executives or managers in what are known as spear phishing attacks. Social media, SMS messages, and even videoconferencing can also be used to carry out phishing.
If attackers successfully gain access to sensitive credentials via phishing attacks, they can execute more sophisticated attacks like a Business Email Compromise (BEC). In a BEC, hackers use a company’s email system to launch further attacks against the organization, its patients, or its partners. This is done through impersonating insiders at the company using their official email accounts. For example, attackers could use a doctor’s email account to ask the doctor’s patients to send them financial information. Since patients are likely to place special trust in their doctor, an attack like this has a higher chance of success than an ordinary phishing or social engineering attack.
Protecting against phishing threats starts with educating employees to identify and report phishing attacks to security teams, rather than responding to malicious messages. Software that automatically scans email and other systems for evidence of phishing can also help to mitigate this type of threat.
Insider threats
An insider threat is any type of risk to data or systems that is caused by insiders, like employees of the organization.
Some insider threats involve malicious actors, such as disgruntled employees who exfiltrate sensitive data to harm the organization. But insider threats can also result from complacency: employees don’t actively follow security best practices. Sometimes, insider threats happen when well-intentioned employees make mistakes, such as forgetting to encrypt a sensitive file.
Insider threat mitigation requires the implementation of security controls that limit access rights to the minimum privileges necessary to do their job. Training employees to be vigilant against malicious or complacent insider threats is also a best practice.
DDoS attacks
In a Distributed Denial-of-Service (DDoS) attack, attackers flood a network, service, or server with illegitimate traffic or requests in order to make the system unusable for legitimate users. Although DDoS attacks don’t typically lead to data exposure or loss, they do disrupt operations, which causes lost revenue and harms the organization’s reputation.
Since a DDoS attack could be launched from any device, securing connected network assets is critical for preventing DDoS attacks. Deploying special services that can detect and block DDoS attacks quickly can help mitigate this risk.
Mitigate Your Cyber Risks
Cyber attacks that target the healthcare industry come in many forms, and they can have particularly grave consequences given the volume and sensitivity of healthcare data. The fact that healthcare organizations constitute particularly lucrative targets for hackers only exacerbates the cybersecurity challenges that this industry faces.
To protect against these threats, it’s critical for healthcare organizations to invest in processes and tools that can protect all of their assets–including not just traditional IT resources like servers, but also connect devices–from all categories of cyber threat.
Ordr’s platform for discovering and securing devices is designed to do just that. By automatically identifying all devices connected to your network and informing you of potential security risks, Ordr helps you stay a step ahead of attackers and provides comprehensive visibility into threats no matter where they lurk on your network. Ordr can also automate responses, such as dynamically generating policies to block ports, terminate sessions or segment devices to mitigate risks. In an industry where small-scale breaches can quickly turn into multi-million dollar attacks, the value of protecting your network with Ordr can’t be understated.
To read a complete maturity guide on implementing connected device security for healthcare, please download the report here.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
Knowledge BaseGuide to OT Security
…of bodily injury to workers, financial loss, and brand damage. Safety and availability go hand-in-hand in the OT space. And the security level of the IT network that communicates with…
Guide to OT Security
6Min ReadIn the legacy environment, operational technology (OT) security was heavily reliant on an ”air-gap” configuration, also known as the Purdue Model. OT systems weren’t exposed to the Internet or any internal networks. With the fourth revolution of industry ongoing, this configuration is no longer a viable option for manufacturing industries.
In today’s rapidly changing manufacturing environment and because of digital transformation, OT networks are now connected to IT networks and cloud. OT security now has to consider the wholistic needs of securing both the manufacturing floor and the ‘carpeted IT environment” from cyber attacks. In fact, analysis of recent cyber attacks against manufacturing environments show that the majority of threats are entering through the IT network and devices. As a result, OT and IT security must converge to work together in order to efficiently and comprehensively cover both networks.
What is OT Security?
OT is the use of hardware and software to monitor, maintain, and control the safe operation of manufacturing assets and processes. OT security is about protecting these devices, including Distributed Control Systems (DCS), Supervisory Control and Data Acquisition (SCADA) networks, Programmable Logic Controllers (PLC), and Remoted Processing Units (RPU) that are common in the industrial sectors and for maintaining cyber resiliency.
When OT wasn’t exposed to the IT networks, Internet or the cloud, securing the OT environment that was largely isolated was simpler. Now, OT is part of the same environment IT and facing a threat landscape similar to IT.
OT Security and IT Security Converge
OT and IT are fundamentally different, so it’s no surprise that the previous security measures for OT didn’t include considerations for traditional IT security. The most relevant difference between the two is OT security focuses on securing assets that are part of the manufacturing facilities and process, rather than the digital assets and data of IT security. While OT security is centered around cyber resilience and keeping equipment and processes safe, IT security’s goal is to preserve confidentiality and data integrity.
Both types of security share the same goal of availability, but availability is a much higher priority for the OT sphere. If the components of the OT environment can’t run because they’ve been compromised by a cyberattack, this impacts the business. Consider the possible ramifications of a cyberattack immediately halting a manufacturing process without warning—physical damage to equipment, risk of bodily injury to workers, financial loss, and brand damage. Safety and availability go hand-in-hand in the OT space. And the security level of the IT network that communicates with the OT network directly affects the OT network’s safety and availability.
While the goals of IT security and OT security are different, and traditionally have followed different paths, converging IT and OT security into a cohesive whole has become the new normal. For example, the Colonial Pipeline attack forced 5,550 miles of pipeline to shut down for several days due to a ransomware attack. This ransomware attack on IT systems resulted in an OT impact even though the OT devices weren’t initially targeted. The shutdown was a precaution because the affected IT systems impacted billing.
In addition to the connection to traditional IT networks, the Industrial Internet of Things (IIoT) also factors into the convergence. Smart devices deployed in various industrial environments have helped create the need for IT/OT convergence. Even compliance is converging—any and all networks must be secure and meet a certain compliance threshold. The OT sphere is subject to its own regulations, creating a blending of needs to satisfy compliance frameworks.
IT security and OT security are bound together in the threat landscape because there’s no longer a distinct separation of OT and IT networks. This has led to development of viable OT security solutions that can provide asset visibility into the devices on the OT/IT converged network, monitor for threats and vulnerabilities, implement network segmentation, and maintain compliance while offering scalability.
Importance of OT Security Solutions
OT security is an absolute must. It’s key to securing water treatment, waste management, utilities, manufacturing, and transportation facilities . A cyberattack that results in an OT security incident could have drastic and dire consequences for the company and the public at large. In order to operate safely and maintain optimal availability, a OT security solution should be implemented and maintained.
Visibility and Device Discovery in OT and IT
Asset discovery should be able to passively collect all necessary information on both IT and OT assets for the converged OT/IT network. Taking it a step further, continued visibility into what these discovered devices are communicating with provides a baseline of observed behaviors. This baseline on traffic visibility between OT, IT, and IIoT devices delivers actionable intelligence that can be used to identify anomalies, such as devices communicating outside of baseline to a malicious domain that may be indicative of a cyberattack in progress. Security starts with enterprise-wide visibility to all assets, including their vulnerabilities and behavior coalesced into a single source of truth.
Monitoring
A central OT security tool with monitoring allows a continuous analysis of OT network behavior. Using network behaviors as a guideline helps the system determine friend from foe, and reveals security insights that are critical to evolving measures on the network over time, such as vulnerabilities and weak passwords or certificates. Monitoring also provides logging, reporting, and event management. Because many OT networks are comprised of critical assets, continuous monitoring helps provide enhanced security for those assets.
Control and Compliance
IT/OT convergence has rendered the Purdue Model of layered segmentation inviable. Devices need to be able to communicate, which requires a more flexible version of network segmentation. OT security solutions today provide a modern version of segmentation and control zones. In addition, OT security solutions offer a more secure interface using a multifactor authentication method to implement appropriate user access, and methodical threat detection and remediation, including automated quarantine.
Capabilities of a Strong OT Security Solution
A strong OT security solution should provide detailed asset management, dynamic network segmentation, continuous threat assessment and vulnerability management, assist compliance and governance, and scale to meet business needs.
Identify and Classify Assets
A key piece of asset management is continuous, real-time discovery that doesn’t impact operations. It should provide granular classification of OT, IT, IIoT, and unmanaged devices with comprehensive details. Using visibility across the various network topologies will help illustrate the cyberattack threat surface and designate non-compliant assets. Detailed asset management lowers the number of vulnerable entry points available to threat actors.
Segment the Network
The CrashOverride attack in 2016 manipulated systems that relied upon the “air-gap” concept practiced in the Purdue model by infiltrating the gapped network. As attackers’ methods advance, so too must security practices to prevent incidents. A strong OT security solution delivers dynamic and automated network segmentation with layered zone controls. Using micro-segmentation policies on existing infrastructure limits devices’ ability to communicate, ensuring only authorized devices can do so.
Continuous Behavioral MonitoringThreat/Vulnerability Detection
Continuous monitoring of the behavior or communication flows of devices offers a window into what’s “normal” in the network. Combining behavioral anomalies with threat detection policy-based rules alerts system administrators of an attack before it begins or is in early stages. For example, an early indication of a ransomware attack might be application anomalies, such as SMB or RDP traffic from a targeted and vulnerable device. With continuous monitoring and behavioral analytics, this type of attack would be discovered before damage occurs.
Compliance
OT compliance is always a pivotal concern and consists of a variety of frameworks and regulations. For compliance adherence, an OT security solution should provide in-depth inventory that pertains to ‘where and how’ sensitive regulatory information is stored. Identify devices running legacy systems, as well as devices that are potentially vulnerable, have expired certificates, or display anomalous behaviors. Vulnerable devices must be segmented and only interact with authorized devices and systems. With so many compliance caveats, a strong OT security solution helps facilitate and manage all these moving pieces.
Cyber Resilience and Scalability
OT must have high availability or cyber resilience to prevent financial ramifications or safety concerns. As business requirements change or capacity limits are reached, a solution must be able to expand to accommodate the change in needs. It should be easy to add new devices and sensors to a network without risking an interruption in productivity or system/device availability. Similarly, OT security solutions need to scale as the OT environment scales. Security policies that are in place to secure assets should be applied to new devices as they come onto the network.
Don’t Skip Over OT Security
The convergence of OT and IT has revolutionized OT security into more robust, complex requirements. While it’s beneficial that IT networks communicating with previously “air-gapped” OT networks have expanded the reach of the OT network significantly, it also increases the risk involved and introduces additional compliance concerns. Most cyber threats that affect OT systems enter through the IT space. The traditional Purdue Model can’t keep up with the advances in the cyber threat landscape, which have led to more dynamic and versatile OT security solutions that can protect valuable IT and OT assets, and can deliver segmentation inline with business needs.
In order to provide an adequate level of protection, an OT security solution must be able to work within the IT space and truly bring the IT and OT networks together into one cohesive “single source of truth” system.
Ordr provides a scalable solution to cover the entirety of the newly converged OT-IT network model that includes all the key components:
- Real-time asset management for OT and IT, including agentless and zero touch discovery
- Comprehensive traffic visibility and analytics for every single asset
- Behavioral and policy-based threat detection and remediation
- Dynamic network segmentation tied to business objectives
- Layered control zones
- Governance and compliance capabilities
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogCyber Attacks in Smart Buildings
BlogCyber Attacks in Smart Buildings…and control, and the malware becomes much more difficult to detect. The combination applied by Ordr’s automation and artificial intelligence system is the ideal combination to streamline and strengthen a…
Risk Management
Cyber Attacks in Smart Buildings
The Threat Is Here
6Min Read
By Pandian Gnanaprakasam

Smart buildings and smart cities deliver great benefits for citizens. Unfortunately, they are popular targets for threat actors. To protect networks, facilities, and people you must understand the challenges and adopt new cybersecurity techniques. Smart Cities and connected buildings offer tremendous benefits yet the question of their security is becoming increasingly crucial. The stakes are all the more important as intelligent building management systems are not limited to home automation, their reach also extends to the controls of the building safety system. In conducting a telemetry survey of 40,000 smart buildings, anti-virus firm Kasperky found that 37.8% of them had already been the target of a cyber attacks. And that was only during the first half of 2019.
Connected buildings typically combine sensors and controllers to monitor and automate the operation of various systems, such as building access, elevator, ventilation, electricity and more. Everything is centralized on a single machine, most often a simple PC connected to the Internet, and therefore as vulnerable as any personal computer. Connected buildings can be offices, houses or residential buildings, but also hospitals, shopping centers, public transport or even prisons.
Attacks are becoming more sophisticated and spreading
Attacks have been detected all over the world, with a higher rate in Western Europe, India, China, and Brazil. Kaspersky investigated the source of the attacks, revealing statistics that are similar to those for industrial systems. Nearly a quarter of intrusions come from the web, while removable drives and email software are each responsible for 10% of incidents. “Although these numbers are relatively low compared to the threat landscape, their impact should not be underestimated,” said Kirill Kruglov, a cyber security researcher at Kaspersky.
Kaspersky noted that most attacks do not specifically target connected buildings and infect all types of networks. Buildings can, therefore, be victims of the same problems as individuals, with spyware (11.3% of detections), computer worms (10.8%), phishing (7.8%) or the risk of see the files taken hostage by ransomware (4% of detections). Buildings are also vulnerable to other threats, which are not detectable by the security software, such as denial of service attacks.
Businesses are facing a worrying growth of cyber threats in 2019.
Cyber-attacks are becoming more sophisticated and are forcing IT professionals to equip themselves with computer security solutions and even smart automated systems that can quickly detect attacks. The best systems must also deploy strategies to guard against these cyber threats holistically equipment, training, recruitment of dedicated technical teams, etc. Considering the valuable assets out there we feel cyber threats against businesses will intensify in the future.
Increased Attack Sophistication: Multiplication of Attacks on Connected Objects
Attacks against Connected Objects (IoT) have multiplied throughout 2018, an increase of more than 200% compared to 2017. While everyone wants devices to be interconnected and connected to the Internet, strong growth in the number of weakly secured connected objects, suggests a very sharp rise in cyber attacks over the next few years.
Cyber criminals take control of connected objects in order to create large networks of Botnets to launch Denial of Service (DDoS) attacks. The United States, for the moment, is the first victim of hackers with more than 46% of global botnets from US-based IP addresses followed by China at 13%.
Protecting Yourself Proactively
Some IoT security solutions just identify problems and signal alarms. This does not alleviate the overworked IT and Security Staff dealing with the increasing threat of cyber attacks on smart buildings. At Ordr, we provide protection proactively. We see the objects and inventory the assets and then we take it a step forward with automated policy generation and automated remedial action using A.I. and machine learning. Ordr also protects a smart building before a potential attack by monitoring all device communications and detecting any anomalies and any behavior that seems unusual.
Be Proactive
The only way to protect yourself is to arm yourself with diligence. Most cyber-attacks of this type come from human errors within an organization, such as an employee opening an infected file or downloading malicious software. For this reason, our intelligent Ordr system is here to face the sophisticated attacks by:
- Detecting anomalies, preventing and isolating attack attempts, segmenting networks when necessary and diligently monitoring the flow of traffic.
- What’s unique is that Ordr policy becomes smarter over time and establishes policies to maintain security and order.
The bad guys can leverage A.I. We take it a step further
In some cases, hackers can use malware and try to mimic the normal behavior of a network in order to spread to more machines, while avoiding detection. Malware enriched by artificial intelligence will be able to infest much faster information systems, able to adapt their behavior according to their environment.
Traditionally, attackers maintain communications with compromised systems using command and control servers. If the malware can use artificial intelligence to autonomously determine how to mimic normal behavior while they are moving, for example by detecting and using local identifiers, attackers no longer need a command server and control, and the malware becomes much more difficult to detect.
The combination applied by Ordr’s automation and artificial intelligence system is the ideal combination to streamline and strengthen a cyber security defense line against sophisticated AI attacks.
ORDR offers specific ways to in this part to face sophisticated attacks as we use machine learning to inspect and baseline the behavior of our growing catalog of devices. Our SCE automatically and continuously detects flows, learns, adapts and expands our data lake. The policy generation is what really differentiates us from the competition as we close the loop of detection, learning, policy and implementation.
Ordr’s ability to learn and adapt
In the future, companies will increasingly connect IoT devices to their networks. To protect themselves and strengthen their defense, particularly as it relates to smart building attacks, we recommend enterprises to consider Ordr’s proactive protection system. The platform is built from the ground up to ensure full security and automated policy generation to protect from the coming attacks on smart buildings.
Automation involves a range of skills such as process automation, test automation, security automation. Security automation is designed to reduce risks, operational errors and solve cybersecurity problems. Threats often come from abnormal use of the data. Security tasks are often prone to errors when processing large volumes of data and creating fast, reliable, and accurate solutions. The ORDR system is fast, dynamic and leverages automation and machine learning to go beyond incident reports. We do feel that the number of ransomware injected into a system by cybercriminals is exponentially greater than the threat detection measures taken by businesses.
Cyber security teams are flooded with alarms and alerts around the clock. We dont want to add to the process and instead fix things automatically. Delayed investigations can lead to devastating data breaches if there is a sub-optimal response to the detection of the threat and relying on manual intervention will not scale.
Ordr’s system allows IT managers to focus on complex types of attacks as attacks become more sophisticated. Along the way ORDR policy becomes smarter and establishes policies so that a human being is not forced to do so.
Identify & Classify
Ordr Systems Control Engine (SCE) is the only purpose-built solution that fully maps every microscopic device detail and its context – the device flow genome – at massive scale, using machine learning to completely and continuously inspect and baseline the behavior of every device. Ordr detects exposed vulnerabilities and delivers intricate risk scores for priority attention and mitigation. All in real-time, all-the-time, delivered in a simple dashboard.
- Discovers every device in your environment.
- Tracks risk scores to focus attention on high-risk devices.
- Maintains a real-time database and tracks changes.
- Integrates with management and workflow tools.
Regulation
Ordr Systems Control Engine monitors and analyzes all device communications, and delivers real-time communications flow analytics. Regulate flow and behavior by device type, group, location, function, application, the control is yours. Ordr SCE automatically detects anomalous behavior including out of flow communication, unusual data and application usage, and off baseline cadence and activity. And it’s real-time, so any new connected systems are immediately regulated when connected.
- Analyzes all device communications 24×7.
- Learns correct behaviors and creates conversation maps.
- Group systems by type, location, function, application.
- Anomaly detection prevents and isolates attempted attacks.
Figure 2: Connected Smart Building
Source: Ordr
Secure
The Ordr SCE architecture is unique in its ability to process enormous quantities of data in real-time, using sophisticated AI to deliver closed-loop security, automatically generating policies for each class of device. The Ordr SCE is integrated with the exisiting network and security infrastructure management tools to implement policies directly and automatically. There is no need to upgrade your network. This is truly no-touch, agent-less protection for business-critical assets.
- Micro-segmentation per NIST
- Access control policy generation
- Full integration with existing NAC solutions
- Program firewalls, wired/wireless access network
System Utilization
Ordr gives you in-depth insight into what’s happening with your systems. High capital and fleet equipment needs to be used efficiently for maximum ROI. Ordr gathers detailed utilization information across the entire enterprise, giving you intelligence about detailed device usage, usage type, hours of operation, and underutilization.
- Compare usage across facilities to for better distribution
- Identify offline devices and bring them back into service
- Understand the usage patterns and adjust schedules
- Make better-informed purchasing decisions
The Ordr Systems Control Engine: Why stop at visibility?
Ordr has developed a smart system than can see everything that is connected to the network and quickly deploy policies to protect the network. The Ordr Systems Control Engine goes beyond what competitors do in that we offer behavioral profiling, flow monitoring, and integrated risk management. Instead of just “blacklisting” non compliant devices, Ordr takes it a step forward “whitelisting” connected devices, providing compliance, and true policy enforcement. Hospitals, shopping centers, public transport, and connected smart buildings will be under attack. Proactive protection is needed and with Ordr, you’re in control.
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogOrdr Security Bulletin – Volt Typhoon State-Sponsored Cyber Actor
BlogOrdr Security Bulletin – Volt Typhoon State-Sponsored Cyber Actor…Zero Trust policies. Other helpful Links: Living off the Land https://www.crowdstrike.com/cybersecurity-101/living-off-the-land-attacks-lotl/ CISA SOHO Device Manufacturer Alert https://www.cisa.gov/sites/default/files/2024-01/SbD-Alert-Security-Design-Improvements-for-SOHO-Device-Manufacturers.pdf Volt Typhoon Attack https://www.darkreading.com/cloud-security/volt-typhoon-soho-botnet-infects-us-govt-entities Router Investigation https://blog.lumen.com/routers-roasting-on-an-open-firewall-the-kv-botnet-investigation/ Detailed report by Security Scorecard https://www.securityweek.com/wp-content/uploads/2024/01/Volt-Typhoon.pdf…
Security Bulletin
Ordr Security Bulletin – Volt Typhoon State-Sponsored Cyber Actor
4Min Read
By Pandian Gnanaprakasam

Chinese state-sponsored threat actors in the VoltTyphonn group are targeting vulnerabilities in small office/home office devices to compromise enterprises. Users of the Ordr platform can find, identify, and protect at-risk assets targeted by Volt Typhoon. Authors: Pandian G, Gowri Sunder Ravi, Srinivas Loke
Summary of Advisory from FBI/CISA
Actors with malicious intentions, particularly the People’s Republic of China-backed Volt Typhoon group, are manipulating small office/home office (SOHO) routers by exploiting software vulnerabilities that manufacturers need to address through secure software engineering.
More specifically, the Volt Typhoon actors are utilizing security flaws in SOHO routers as springboards to further infiltrate U.S. critical infrastructure entities. The Cybersecurity & Infrastructure Security Agency (CISA) and the Federal Bureau of Investigation (FBI) have issued this warning due to recent and ongoing threat activities.
The FBI & CISA urge SOHO router manufacturers to incorporate security features into their products from the start, and encourage all SOHO router users to demand higher security standards from the outset.
“China’s hackers are targeting American civilian critical infrastructure, pre-positioning to cause real-world harm to American citizens and communities in the event of conflict,” said FBI Director Christopher Wray. “Volt Typhoon malware enabled China to hide as they targeted our communications, energy, transportation, and water sectors.”
One of the main vulnerabilities that Volt Typhoon has exploited is found in Cisco and NetGear routers. These routers were used by the group to route their network traffic, thus enhancing the stealth of their operations and lowering overhead costs for acquiring infrastructure.
Information about Volt Typhoon: (Also tracked as Insidious Taurus)
- Volt Typhoon is a state-sponsored actor based in China, known for its espionage and information-gathering activities. It has been active since mid-2021 and has targeted critical infrastructure organizations in the United States, spanning various sectors, including communications, manufacturing, utility, transportation, construction, maritime, government, IT, and education.
- Volt Typhoon employs a variety of tactics, techniques, and procedures (TTPs) to achieve its objectives. One of their primary strategies is the use of “living-off-the-land” techniques, which involve using built-in network administration tools to perform their objectives. This strategy allows the actor to evade detection by blending in with normal Windows system and network activities, avoiding alerts from endpoint detection and response (EDR) products, and limiting the amount of activity captured in default logging configurations.
- They also try to blend into normal network activity by routing traffic through compromised small office and home office (SOHO) network equipment, including routers, firewalls, and VPN hardware.
- Mitigation strategies against Volt Typhoon include identifying and examining the activity of compromised accounts, closing or changing credentials for compromised accounts, and implementing behavioral monitoring to detect activity that uses normal sign-in channels and system binaries.
- Of importance is the “KV-Botnet,” revealed in a report from Lumen’s Black Lotus Labs, is designed to infect end of life small-office home-office (SOHO) network devices developed by at least, but not limited to, four different vendors. It comes built with a series of stealth mechanisms and the ability to spread further into local area networks (LANs). Microsoft has confirmed that many of the devices include those manufactured by ASUS, Cisco, D-Link, NETGEAR, and Zyxel.
- Since at least February 2022, KV-Botnet has primarily infected SOHO routers like the Cisco RV320, DrayTek Vigor, and Netgear ProSafe product lines. As of mid-November, it expanded to exploit IP cameras developed by Axis Communications.
- Microsoft assesses the “Volt Typhoon campaign is pursuing development of capabilities that could disrupt critical communications infrastructure between the United States and Asia region during future crises.”
Banned Manufacturers
Section 889 of the National Defense Authorization Act (NDAA) prohibits the use of federal funds to buy certain telecommunications equipment or services from specific manufacturers. These manufacturers include:
- Huawei Technologies Company
- Hytera Communications Corporation
- ZTE Corporation
- Hangzhou Hikvision Technology Company
- Dahua Technology Company
- Any subsidiary or affiliate of these companies
Section 889 also prohibits the government from contracting with any entity that uses certain telecommunications equipment or services produced by these manufacturers. This prohibition applies to all purchases, regardless of the size of the contract or order.
How Ordr helps
See
- Ordr automatically discovers and classifies and profiles all devices based on the manufacturer, make, and model.
- For this attack Ordr discovers the devices known to be impacted, including those from manufacturers like Axis, Netgear, Dray Tek, D-Link, Zyxel. These devices are automatically tagged and can be easily tracked in the system.
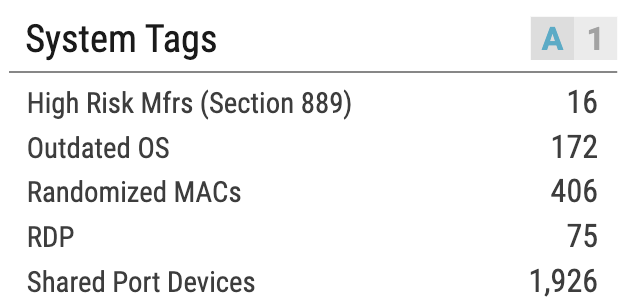
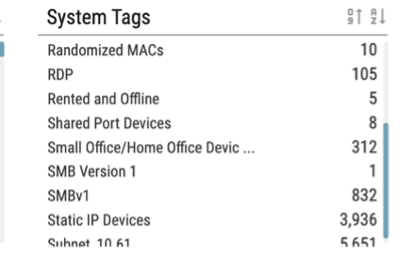
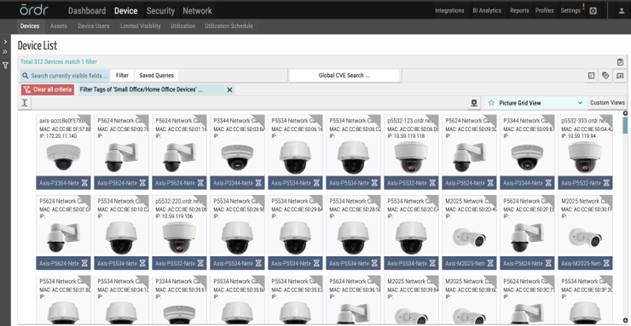
- Ordr identifies and highlights Small Office / Home Offices devices in our customer environment mentioned in the advisories and produces a device download csv/xlsx report from the reports tab for customers to easily download in addition to the ability to lookup devices directly from the tag section.
Note: Recommendations from federal agencies – Federal agencies recommend that internet-facing SOHO devices be up to date and follow guidelines mentioned in advisories from government agencies.
Know
- In real-time, Ordr ‘s external IP/IOC tracks every communication to prohibited IP/URLs.
- Ordr provides in depth insights into category traffic analysis that highlights the communication patterns between devices and external entities, making it easier to see devices communicating to list of prohibited countries including China.
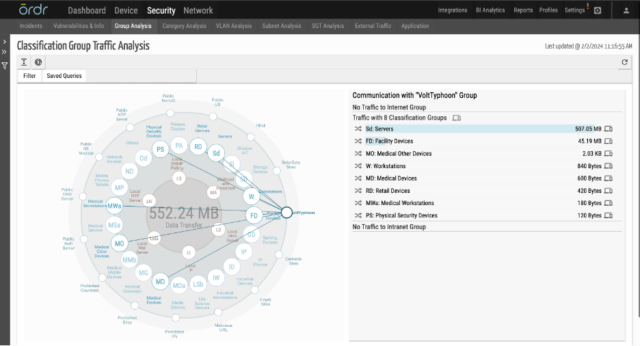
- Ordr uses a cloud-based threat intelligence platform where the list is continuously updated, and all communications are marked accordingly in the Ordr Security Threat Card.
- Ordr has an IDS engine that can detect attacks originating from Volt Typhoon and generate alerts based on analysis of packets transacting over the wire.
- IDS Rule: Ordr’s network data collectors process packets for Deep packet inspection and at the same time checks for signatures and this rule that detects presence of “Volt Typhoon User Agent” and generates a high severity alarm.
- Ordr also provides the capability to baseline all the communications based on profile, location, business function, or any customized entity using our AI/ML techniques. Ordr can trigger anomalies based on any deviations observed for this traffic.
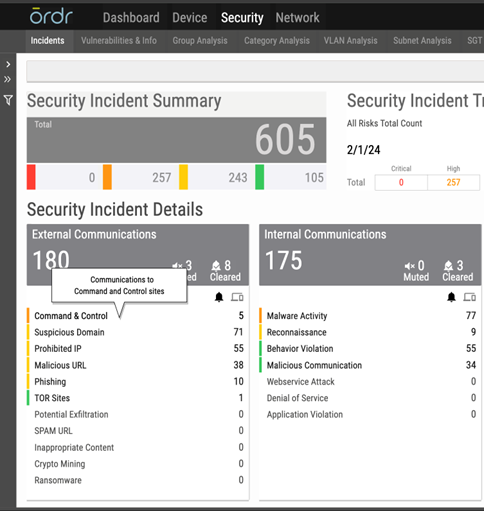
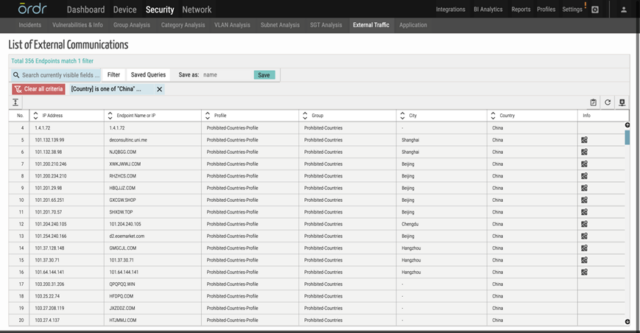
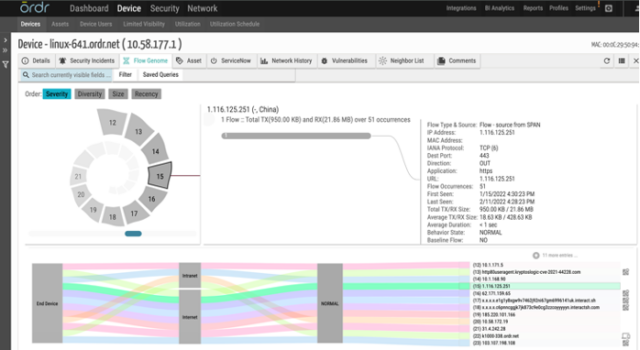
Secure
- Ordr enables segmentation of impacted devices and limiting access to only must-have communications based on Zero Trust policies.
Other helpful Links:
- Living off the Land https://www.crowdstrike.com/cybersecurity-101/living-off-the-land-attacks-lotl/
- CISA SOHO Device Manufacturer Alert https://www.cisa.gov/sites/default/files/2024-01/SbD-Alert-Security-Design-Improvements-for-SOHO-Device-Manufacturers.pdf
- Volt Typhoon Attack https://www.darkreading.com/cloud-security/volt-typhoon-soho-botnet-infects-us-govt-entities
- Router Investigation https://blog.lumen.com/routers-roasting-on-an-open-firewall-the-kv-botnet-investigation/
- Detailed report by Security Scorecard https://www.securityweek.com/wp-content/uploads/2024/01/Volt-Typhoon.pdf
- Joint Cybersecurity Advisory https://media.defense.gov/2023/May/24/2003229517/-1/-1/0/CSA_Living_off_the_Land.PDF
- Microsoft Blog https://www.microsoft.com/en-us/security/blog/2023/05/24/volt-typhoon-targets-us-critical-infrastructure-with-living-off-the-land-techniques/
- CISA Director Statement https://www.cisa.gov/news-events/news/opening-statement-cisa-director-jen-easterly
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogTop 10 Risks of Not Getting Your CMDB In Order and How That Changes Today
BlogTop 10 Risks of Not Getting Your CMDB In Order and How That Changes Today…organization. We are proud to offer the Service Graph Connector for Ordr to help customers achieve the comprehensive and accurate asset inventory they need to simplify workflows, improve security, and…
General
Top 10 Risks of Not Getting Your CMDB In Order and How That Changes Today
5Min Read
By Pandian Gnanaprakasam

What are the top ten risks of not getting your CMDB in order? How do those risks affect enterprise cybersecurity? And how can new tools and techniques that deliver real-time device discovery and analytics help you to change your situation? Great news! Ordr just announced the availability of the Service Graph Connector for Ordr in the ServiceNow Store. This integration is exciting for our customers, who can now maintain an up-to-date system of record for all assets so organizations can operate efficiently, react quickly, and manage risks more effectively.
Service Graph Connector for Ordr now available in the ServiceNow Store
Ordr provides the most comprehensive, accurate, real-time inventory of connected assets as a single source of truth. As the threat surface continuously evolves and expands, it is critical to ensure asset inventories are complete and provide the context to address risk proactively and reactively. With ServiceNow and Ordr’s bidirectional integration, Ordr’s device, network, and risk context are combined with the business context of ServiceNow. And the new Service Graph Connector for Ordr makes the integration more manageable and robust.
You now get a robust, most comprehensive, accurate real-time inventory of connected assets—from traditional IT to IoT, IoMT, and OT — and their risks in the ServiceNow Configuration Management Database (CMDB) to optimize enterprise-wide workflows and assess and manage risks.
Top Ten Security Risks of Incomplete and Outdated Asset Inventories
As given below, there are significant entry points that cybercriminals can exploit. With the combination of Ordr and ServiceNow, security and IT teams can identify and mitigate the following asset risks.
- Banned Equipment (Section 889)
To protect national security, the federal government bans products manufactured by prohibited companies such as Kaspersky, Huawei, and Hikvision. These banned products can have vulnerabilities if exploited, resulting in the loss of intellectual property. The mandate covers new procurement and requires reporting within one business day if any prohibited asset is discovered in inventory.
- Unauthorized Devices
Every unauthorized device that bypasses IT and operational tools and connects to a corporate network will expand the attack surface and could introduce significant risk. When the flash news of new vulnerabilities impacting corporate tools is announced, tracking all those instances of the compromised device can be challenging. This can include devices used in production and increasingly non-production or POV (Proof of Value) environments. The combination of Ordr and ServiceNow can proactively detect devices that can access other corporate servers and other precious devices and remove them from the network after the trial period.
- Orphaned/Missing Devices
Maintaining good asset hygiene is always a best practice for improving security posture. It is critical to ensure that all assets registered and recorded by the procurement team are tracked and compared against all the devices connecting to the network. Any gaps should be reconciled proactively before it results in security concerns.
- Manufacturer Recall / FDA Recall
Manufacturers may issue recall notices and security bulletins for significant vulnerabilities discovered. This is prevalent in regulated industries with mission-critical medical and industrial equipment devices. Similarly, from a federal regulation perspective, there can be recalls for sensitive equipment such as medical devices. Ordr can collate all recall announcements from multiple sources and tag all devices impacted; this context can be shared with ServiceNow.
- Default Credentials
Business groups typically install IoT devices such as cameras in batches. The person responsible for the installation is usually not technical and often needs to gain knowledge or experience to change default passwords. It is unrealistic, if not impossible, to have a process to choose multiple unique passwords for physical security cameras when hundreds to thousands are going up in the ceiling. Think of the risk when hundreds of devices default to “Password1”. These passwords are not rotated periodically using over-the-air methods, like a password policy that enforces periodic password changes for laptops and desktops. An asset management system that combines the Ordr “default password discovery” feature with ServiceNow CMDB can alert administrators to update the credentials associated with these devices.
- Rogue Wireless/Switches that are bridging traffic to the internet (5G/LTE/Guest Wi-Fi)
Unauthorized devices usually connect to a corporate open port and a set of devices using a daisy chain mechanism. Suppose the consumer-grade switches/routers come with LTE or link to the Guest Wi-Fi network. In this case, taking corporate data and exfiltrating without going through all the border controls exercised by firewalls becomes easier. It is a vast attack surface. Even when a good asset management and visibility solution is implemented, one needs a sophisticated tool to understand this daisy chain mechanism throughout the network to keep an exact list of these devices and implement a solution to eliminate them. An asset management system must integrate with a sophisticated visibility tool to detect and eliminate these daisy chain devices; this is why the Ordr and ServiceNow integration is so powerful.
- Non-Compliant Devices
When a corporate Antivirus (AV)/Endpoint Detection Response (EDR) policy mandates that all IT endpoints (e.g., laptops, mobile, desktops) need to have a robust agent/software installed, it is not easy to audit all the devices and pull a list of those that do not have the required software installed. One step further than that is how challenging it is to ensure all those EDR agents are continuously running and receiving updates periodically to detect and thwart the latest attacks.Expired Certificates: We have all experienced how frantic it is to fix a certificate issue when a critical server stops working with expired certs. With a good asset management strategy, corporate IT can track all certificate expirations and implement a plan to address them periodically. Both these insights are readily available with Ordr and can be shared with ServiceNow.
- Local User Accounts without Domain Joins
All users accessing a system must be part of Windows Active Directory (AD), if possible. This is especially critical in the case of older Windows machines that usually have a lot of unpatched vulnerabilities. Even if the device is part of the domain controller, sometimes operators can create local users on these machines. This practice must be watched closely, and a list of all locally-made user accounts must be extracted and reported continuously. When hackers create local user accounts and leave them dormant for later exploitation, it is easy to identify and remove those inactive accounts and fix the machines with malware infections.
- End-of-Life / Outdated OS
Assets running end-of-life and outdated operating systems pose a significant risk to the organization. The first step is to identify these end-of-life devices. This can be a struggle without a solution like Ordr and ServiceNow that not only delivers accurate real-time inventory but now extends visibility to IoT, IoMT, and OT devices that often have longer operating cycles than traditional IT endpoints.Note that upgrading all devices running end-of-life or outdated OS is a logical way to address potential risks. But upgrading these devices in regulated industries such as healthcare, manufacturing, and banking might not be possible due to backward compatibility issues. In some cases, an update to a device will trigger the need to re-certify the device with federal regulators. For all these cases, it is prudent to have a segmentation strategy to isolate outdated and at-risk devices from other parts of your environment, which could get be easily accomplished with Ordr’s behavioral baselining and automated Zero Trust policies.
- Unpatched Devices Vulnerable to Exploitation
This is the most important reason one should embark on an asset management strategy to get an accurate view of all connected devices and their associated details. An asset management strategy must include identifying operating system (OS) versions and patch levels for each connected device. This makes it easy to highlight the exact CVEs (Common Vulnerabilities and Exposures) that are still open and vulnerable that a potential hacker could exploit. Having this list as a work item and tracking how the patching for these devices is progressing is one of the most foundational aspects of cyber security an organization can initiate.
Asset Management Aligned to Risk Reduction
An incomplete and inaccurate asset inventory poses many risks. The risks can extend from non-compliance to safety and regulatory concerns. On top of that, add the problems of security breaches, which can cause high financial and reputation costs to organizations.
Understanding your attack surface by implementing a robust asset management strategy that identifies and closely tracks vulnerabilities and threats from the entire asset universe of IT, OT, IoT, ICS, BMS, and IoMT (Internet of Medical Things) will minimize the risk imposed on an organization. We are proud to offer the Service Graph Connector for Ordr to help customers achieve the comprehensive and accurate asset inventory they need to simplify workflows, improve security, and accelerate incident response.
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
- Banned Equipment (Section 889)