
Cisco
Ordr’s deep integrations across the Cisco portfolio adds visibility and insights needed to manage and secure the wide range of connected devices in today’s environments.
”Quiz 2024 SAP C-ARSOR-2308: Marvelous SAP Certified Application Associate - SAP Ariba Sourcing Valid Dumps Book 🐮 Open ▷ www.pdfvce.com ◁ and search for ➥ C-ARSOR-2308 🡄 to download exam materials for free 🏑C-ARSOR-2308 Customizable Exam Mode”
…THE ABOVE LIMITATION AND EXCLUSIONS MAY NOT APPLY TO YOU. Indemnity. You agree to indemnify and hold Ordr, its affiliates, officers, agents, employees, and partners harmless for and against any…
Last Updated: September 27, 2022
PLEASE NOTE THAT YOUR USE OF AND ACCESS TO OUR WEBSITE (DEFINED BELOW) ARE SUBJECT TO THE FOLLOWING TERMS; IF YOU DO NOT AGREE TO ALL OF THE FOLLOWING, YOU MAY NOT USE OR ACCESS THE WEBSITE IN ANY MANNER.
Welcome to Ordr, Inc.’s website. Please read on to learn the rules and restrictions that govern your use of our website(s) (the “Website”). If you have any questions, comments, or concerns regarding these terms or the Website, please contact us at info@ordr.net.
These Terms of Use (the “Terms”) are a binding contract between you and Ordr, Inc. (“Ordr,” “we” and “us”). You must agree to and accept all of the Terms, or you don’t have the right to use the Website. If you use the Website in any way, you agree to all of these Terms, and these Terms will remain in effect while you use the Website. These Terms include the provisions in this document, as well as those in the Ordr Privacy Policy.
We are constantly trying to improve our Website, so these Terms may need to change along with the Website. We reserve the right to change the Terms at any time, but if we do, we will bring it to your attention by placing a notice on the Website, and/or by sending you an email and/or by some other means.
If you don’t agree with the new Terms, you are free to reject them; unfortunately, that means you will no longer be able to use the Website. If you use the Website in any way after a change to the Terms is effective, that means you agree to all of the changes.
Except for changes by us as described here, no other amendment or modification of these Terms will be effective unless in writing and signed by both you and us.
Ordr takes the privacy of its users very seriously. For the current Ordr Privacy Policy Is posted on the www.ordr.net.
The Children’s Online Privacy Protection Act (“COPPA”) requires that online service providers obtain parental consent before they knowingly collect personally identifiable information online from children who are under 13. We do not knowingly collect or solicit personally identifiable information from children under 13; if you are a child under 13, please do not attempt to use the Website or send any personal information about yourself to us. If we learn we have collected personal information from a child under 13, we will delete that information as quickly as possible. If you believe that a child under 13 may have provided us personal information, please contact us at info@ordr.net.
You represent and warrant that you are of legal age to form a binding contract (or if not, you’ve received your parent’s or guardian’s permission to use the Website and gotten your parent or guardian to agree to these Terms on your behalf). If you’re agreeing to these Terms on behalf of an organization or entity, you represent and warrant that you are authorized to agree to these Terms on that organization or entity’s behalf and bind them to these Terms (in which case, the references to “you” and “your” in these Terms, except for in this sentence, refer to that organization or entity).
You will only use the Website for your own internal, personal, non- commercial use, and not on behalf of or for the benefit of any third party, and only in a manner that complies with all laws that apply to you. If your use of the Website is prohibited by applicable laws, then you aren’t authorized to use the Website. We can’t and won’t be responsible for your using the Website in a way that breaks the law.
Your use of the Website is subject to the fact that You represent, warrant, and agree that You will not contribute any Content or User Submission (each of those terms is defined below) or otherwise use the Website or interact with the Website in a manner that:
(a) Infringes or violates the intellectual property rights or any other rights of anyone else (including Ordr);
(b) Violates any law or regulation;
(c) Is harmful, fraudulent, deceptive, threatening, harassing, defamatory, obscene, or otherwise objectionable;
(d) Violates the security of any computer network, or cracks any passwords or security encryption codes;
(e) Runs Maillist, Listserv, any form of auto-responder or “spam” on the Website, or any processes that run or are activated while you are not logged into the Website, or that otherwise interfere with the proper working of the Website (including by placing an unreasonable load on the Website infrastructure);
(f) “Crawls,” “scrapes,” or “spiders” any page, data or portion of or relating to the Website or Content (through use of manual or automated means);
(g) Copies or stores any significant portion of the Content and/or share, post or distribute any significant portion of the Content elsewhere;
(h) Decompiles, reverse engineers, or otherwise attempts to obtain the source code or underlying ideas or information of or relating to the Website.
A violation of any of the foregoing is grounds for termination of your right to use or access the Website.
The materials displayed or performed or available on or through the Website, including, but not limited to, text, graphics, data, articles, photos, images, illustrations, user submissions, and so forth (all of the foregoing, the “Content”) are protected by copyright and/or other intellectual property laws. You promise to abide by all copyright notices, trademark rules, information, and restrictions contained in any Content you access through the Website, and you won’t use, copy, reproduce, modify, translate, publish, broadcast, transmit, distribute, perform, upload, display, license, sell or otherwise exploit for any purpose any Content not owned by you, (i) without the prior consent of the owner of that Content or (ii) in a way that violates someone else’s (including Ordr’s) rights.
You understand that Ordr owns the Website. You won’t modify, publish, transmit, participate in the transfer or sale of, reproduce (except as expressly provided in this Section), creative derivative works based on, or otherwise exploit any of the Website.
The Website may allow you to copy or download certain Content; please remember that just because this functionality exists, doesn’t mean that all the restrictions above don’t apply—they do!
You access all information and content posted or transmitted through the Website at your own risk, and we aren’t liable for any errors or omissions in that information or content or for any damages or loss you might suffer in connection with it. We cannot control and have no duty to take any action regarding how you may interpret and use the Content or what actions you may take as a result of having been exposed to the Content, and you hereby release us from all liability for you having acquired or not acquired Content through the Website. We can’t guarantee the identity of any users with whom you interact in using the Website and are not responsible for which users gain access to the Website.
You are responsible for all Content you provide, in any manner, via the Website, and you represent and warrant you have all rights necessary to do so, in the manner in which you provide it. You are responsible for all your activity in connection with the Website.
The Website may contain links or connections to third party websites or services that are not owned or controlled by Ordr. When you access third party websites or use third party services, you accept that there are risks in doing so, and that Ordr is not responsible for such risks. We encourage you to be aware when you leave the Website and to read the terms and conditions and privacy policy of each third party website or service that you visit or utilize.
Ordr has no control over, and assumes no responsibility for, the content, accuracy, privacy policies, or practices of or opinions expressed in any third party websites or by any third party that you interact with or find through the Website. In addition, Ordr will not and cannot monitor, verify, censor or edit the content of any third party site or service.
By using the Website, you release and hold us harmless from any and all liability arising from your use of any third party website or service.
If there is a dispute between users of the Website, or between users and any third party, you agree that Ordr is under no obligation to become involved. In the event that you have a dispute with one or more other users, you release Ordr, its officers, employees, agents, and successors from claims, demands, and damages of every kind or nature, known or unknown, suspected or unsuspected, disclosed or undisclosed, arising out of or in any way related to such disputes and/or our Website. If you are a California resident, you shall and hereby do waive California Civil Code Section 1542, which says: “A general release does not extend to claims which the creditor does not know or suspect to exist in his favor at the time of executing the release, which, if known by him must have materially affected his settlement with the debtor.”
We are always trying to improve the Website, so it may change over time. We may suspend or discontinue any part of the Website, or we may introduce new features or impose limits on certain features or restrict access to parts or all of the Website. We’ll try to give you notice when we make a material change to the Website that would adversely affect you, but this isn’t always practical. Similarly, we reserve the right to remove any Content from the Website at any time, for any reason (including, but not limited to, if someone alleges you contributed that Content in violation of these Terms), in our sole discretion, and without notice.
You’re free to do that at any time, by contacting us at info@ordr.net; please refer to our Privacy Policy, as well as these Terms of Use, to understand how we treat information you provide to us after you have stopped using our Website.
Ordr is also free to terminate (or suspend access to) your use of the Website for any reason in our discretion, including your breach of these Terms. Ordr has the sole right to decide whether you are in violation of any of the restrictions set forth in these Terms.
Provisions that, by their nature, should survive termination of these Terms shall survive termination. By way of example, all of the following will survive termination: any obligation you have to indemnify us, any limitations on our liability, any terms regarding ownership or intellectual property rights, and terms regarding disputes between us.
Warranty Disclaimer. Ordr does not make any representations or warranties concerning any content contained in or accessed through the Website, and we will not be responsible or liable for the accuracy, copyright compliance, legality, or decency of material contained in or accessed through the Website. We make no representations or warranties regarding suggestions or recommendations of services or products offered or purchased through the Website. Services purchased or offered (whether or not following such recommendations and suggestions) through the Website are provided “AS IS” and without any warranty of any kind from Ordr or others (unless, with respect to such others only, provided expressly and unambiguously in writing by a designated third party for a specific product). THE WEBSITE AND CONTENT ARE PROVIDED ON AN “AS-IS” BASIS, WITHOUT WARRANTIES OR ANY KIND, EITHER EXPRESS OR IMPLIED, INCLUDING, WITHOUT LIMITATION, IMPLIED WARRANTIES OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE, NON-INFRINGEMENT, OR THAT USE OF THE WEBSITE WILL BE UNINTERRUPTED OR ERROR-FREE. SOME STATES DO NOT ALLOW LIMITATIONS ON HOW LONG AN IMPLIED WARRANTY LASTS, SO THE ABOVE LIMITATIONS MAY NOT APPLY TO YOU.
Limitation of Liability. TO THE FULLEST EXTENT ALLOWED BY APPLICABLE LAW, UNDER NO CIRCUMSTANCES AND UNDER NO LEGAL THEORY (INCLUDING, WITHOUT LIMITATION, TORT, CONTRACT, STRICT LIABILITY, OR OTHERWISE) SHALL ORDR BE LIABLE TO YOU OR TO ANY OTHER PERSON FOR (A) ANY INDIRECT, SPECIAL, INCIDENTAL, OR CONSEQUENTIAL DAMAGES OF ANY KIND, INCLUDING DAMAGES FOR LOST PROFITS, LOSS OF GOODWILL, WORK STOPPAGE, ACCURACY OF RESULTS, OR COMPUTER FAILURE OR MALFUNCTION, OR (B) ANY AMOUNT, IN THE AGGREGATE, IN EXCESS OF THE GREATER OF (I) $100 OR (II) THE AMOUNTS PAID BY YOU TO ORDR IN CONNECTION WITH THE WEBSITE IN THE TWELVE (12) MONTH PERIOD PRECEDING THIS APPLICABLE CLAIM, OR (III) ANY MATTER BEYOND OUR REASONABLE CONTROL. SOME STATES DO NOT ALLOW THE EXCLUSION OR LIMITATION OF CERTAIN DAMAGES, SO THE ABOVE LIMITATION AND EXCLUSIONS MAY NOT APPLY TO YOU.
Indemnity. You agree to indemnify and hold Ordr, its affiliates, officers, agents, employees, and partners harmless for and against any and all claims, liabilities, damages (actual and consequential), losses and expenses (including attorneys’ fees) arising from or in any way related to any third party claims relating to (a) your use of the Website (including any actions taken by a third party on your behalf or at your direction), and (b) your violation of these Terms. In the event of such a claim, suit, or action (“Claim”), we will attempt to provide notice of the Claim to the contact information we have for you (provided that failure to deliver such notice shall not eliminate or reduce your indemnification obligations hereunder).
Assignment. You may not assign, delegate or transfer these Terms or your rights or obligations hereunder, in any way (by operation of law or otherwise) without Ordr’s prior written consent. We may transfer, assign, or delegate these Terms and our rights and obligations without consent.
Choice of Law; Arbitration. These Terms are governed by and will be construed under the laws of the State of California, without regard to the conflicts of laws provisions thereof. Any dispute arising from or relating to the subject matter of these Terms shall be finally settled in San Francisco County, California, in English, in accordance with the Streamlined Arbitration Rules and Procedures of Judicial Arbitration and Mediation Services, Inc. (“JAMS”) then in effect, by one commercial arbitrator with substantial experience in resolving intellectual property and commercial contract disputes, who shall be selected from the appropriate list of JAMS arbitrators in accordance with the Arbitration Rules and Procedures of JAMS. Judgment upon the award rendered by such arbitrator may be entered in any court of competent jurisdiction. Notwithstanding the
foregoing obligation to arbitrate disputes, each party shall have the right to pursue injunctive or other equitable relief at any time, from any court of competent jurisdiction. For all purposes of this Agreement, the parties consent to exclusive jurisdiction and venue in the state or federal courts located in, respectively, Santa Clara County, California, or the Northern District of California.
Miscellaneous. You will be responsible for paying withholding, filing, and reporting all taxes, duties, and other governmental assessments associated with your activity in connection with the Website, provided that Ordr may, in its sole discretion do any of the foregoing on your behalf or for itself as it sees fit. The failure of either you or us to exercise, in any way, any right herein shall not be deemed a waiver of any further rights hereunder. If any provision of this Agreement is found to be unenforceable or invalid, that provision will be limited or eliminated, to the minimum extent necessary, so that these Terms shall otherwise remain in full force and effect and enforceable. You and Ordr agree that these Terms are the complete and exclusive statement of the mutual understanding between you and Ordr, and that it supersedes and cancels all previous written and oral agreements, communications and other understandings relating to the subject matter of these Terms, and that all modifications to these Terms must be in a writing signed by both parties (except as otherwise provided herein). No agency, partnership, joint venture, or employment is created as a result of these Terms and you do not have any authority of any kind to bind Ordr in any respect whatsoever. You and Ordr agree there are no third party beneficiaries intended under this Agreement.
…and function, and assess each device for risk. It analyzes device communications to learn behaviors and creates device baselines to determine what communications the device requires for normal operations. From…
Cybersecurity attacks are an ever present concern—a hydra that spawns new heads after each known head is vanquished. One of those newly spawned nightmares is trying to protect Internet of Things (IoT), Internet of Medical Things (IoMT), and Operational Technology (OT) devices as they become network enabled and part of the bigger cybersecurity picture. This is something that traditional cybersecurity tools aren’t built to handle.
These devices are used in many industries—healthcare, financial services, transportation, manufacturing, and education, just to name a few. IoT, IoMT, and OT devices, as well as traditional systems and resources, must be protected by a thorough plan. The National Institute of Standards and Technology Cybersecurity Framework (NIST CSF) helps your organization build a solution customized to fit your business and needs.
The NIST Cybersecurity Framework is a technology neutral security structure built upon cutting-edge global standards, existing guidelines, and developed practices that is capable of evolving to meet business requirements and keep up with technological advancement. The NIST Cybersecurity Framework is intended as a complement to an organization’s existing cybersecurity strategy and risk management plan. It provides the means to continue with current policies and procedures, while also discovering areas of potential improvement, better means of communication, and/or increased industry alignment.
The NIST Cybersecurity Framework Core can be used by any sector with any infrastructure because it is adaptable, flexible, and based on business-driven implementation. The NIST Cybersecurity Framework is a top-ranked structural foundation on which a company can build the cybersecurity program best suited to their unique business profile.
The Core breaks the controls and practices into five service lanes to be addressed concurrently:
The NIST Cybersecurity Framework is built upon tried-and-true practices, so you can apply proven solutions to real problems by leveraging the framework for guidance. It enhances compliance with industry standards and regulations, as well as helps mitigate vulnerabilities by exposing previously unseen risk.
The framework also aids with zeroing in on a company’s true risks, increasing both efficiency and resource management. In addition, the NIST Cybersecurity Framework (CSF) refines asset management to ensure the company maintains accurate inventory.
While security teams understand the threat landscape and cybersecurity needs, stakeholders and other company teams don’t have this detailed understanding. NIST CSF bridges the gap between IT and business departments by laying a reasonable path that focuses on specific outcomes. The framework enhances conversations with these groups and helps explain why certain actions and resources are necessary to achieve a fully mature cybersecurity solution.
The five core functions of the NIST Cybersecurity Framework allow for a company to start at any point. Whether your company is using cutting edge cybertech or relying on legacy systems, there are benefits to be reaped by employing the framework.
When applying NIST CSF, a practitioner should leverage the framework against a controlset outlined by the NIST publication they are attempting to adhere to. For example, 800-53 rev5 (Security and Privacy Controls for Information Systems and Organizations) are often used as the core set of standards for healthcare organizations as it helps in protection of personally identifiable information (PII). The control spreadsheet outlines a list of controls or control enhancements outlined by the control text column (that is to say, ‘do i have this control?’). Often controls are satisfied by technologies you have or need to have in your environment. A solution such as Ordr could help meet the requirements of CM-8 (System Component Inventory) and satisfy PM-5 (System Inventory) requirements. These controls speak directly to the framework.
Let’s take an example for 800-53 mapped to the CSF for ID.AM-1: Physical devices and systems within the organization are inventoried. To satisfy this functional category and subcategory you need controls CM-8 and PM-5. As you see, to satisfy the CSF you need to first decide what publication you would like to adhere to. 800-53 is popular but others may be relevant to your organization and contain similar control maps.
The Core framework divides security activities into five high-level functions that include Identify, Protect, Detect, Respond, and Recover. As a whole, these functions provide a company with the means of managing risks by organizing all pertinent information, addressing potential threats, and continuously learning from previous ventures.
Identify is the NIST Cybersecurity Framework function that brings together business context, critical support functions and resources, and risk management. The goal of Identify is to define the critical business landscape for your organization so adequate protection can be implemented around it. Organizations should also consider all processes, procedures, and policies that revolve around the organization’s compliance regulation, legal considerations, risk factors, operational requirements, and environment.
This includes the following recommended tasks:
Your organization should employ a platform that allows for passive discovery with in-depth details, agentless software tracking, and data flow monitoring. Ideally, this includes support of connected devices such as IoT, IoMT, and OT devices. This platform will be capable of providing relevant information to assist the risk management process, such as risk scores per device. The platform also should be able to identify and manage devices and/or communications that involve regulated data, such as payment card industry (PCI) data or medical information protected by HIPAA such as protected health information (PHI).
Consider a solution that can monitor incidents and risk for both traditional devices and IoT devices. The solution should be able to detect anomalies and network intrusions, as well as bad URL/site connections, with detailed trend analysis. A platform such as Ordr also provides a risk score to assist with prioritization, and should be capable of both scheduled and ad-hoc reporting.
The Protect function is about safeguarding to prevent, limit, or contain any impacts from potential cybersecurity incidents. It’s a crucial piece of ensuring the continued delivery of vital services.
This includes the following tasks:
A good solution should employ artificial intelligence (AI) that can establish baseline communication behavior and transform the baseline into security policies that are device specific, such as limiting traffic to only approved systems to reduce the IoT/IoMT/OT attack surface. As an example, microsegmentation policy can be created to limit IoT/IoMT/OT device communications such as restricting external communications as well as communications with internal systems not required for normal operations. A security platform such as Ordr can continuously monitor all communication and detect devices trying to connect to malicious sites, unauthorized networks, or receive malicious communications. Such a solution also provides domain separation between environments by creating and enforcing microsegmentation policy. Choose a solution that can track an asset’s SDLC as it relates to cybersecurity.
Another capability to look for in a solution is the ability to integrate security intel feeds as well as integration with a vulnerability management platform. Security intel feeds provide insights into known vulnerabilities and associated risk with the ability to identify impact to your environment. Vulnerability management capabilities will help to ensure that remediation and mitigation tasks can be coordinated and tracked across teams as you look to reduce or eliminate risk. Ordr’s offering is capable of integrating security intel feed data to identify connected devices with known vulnerabilities. The solution also provides native vulnerability management capabilities as well as the ability to integrate with other 3rd party vulnerability management tools.
Detect is the section of the NIST Cybersecurity Framework that focuses on the development and implementation of capabilities, tasks, and activities required to identify incidents precipitated by a cybersecurity event. This functionality enables the organization to discover cybersecurity incidents quickly and efficiently.
Consider these tasks:
Choose a platform that provides the ability to detect malicious activity as well as a security dashboard based on a consolidated view of events, which can be further enhanced with criticality and MITRE kill chain step data. Your organization also can benefit from a platform that can provide real-time alerts filtered by security event types so specific staff can be notified, based on the affected asset. A high-quality solution should be capable of detecting and logging device moves, adds, and changes.
Ordr continuously monitors the network and employs intrusion detection capabilities to identify known malicious attack traffic. In addition the solution creates a baseline of normal behavior for each connected device and will detect abnormal deviations. With these capabilities Ordr can identify active threats, attempts to exploit vulnerabilities, and indications of compromise. Your platform should work with security information and event management (SIEM) and IT assessment management (ITAM) products so it can seamlessly integrate with existing workflows and procedures.
The Respond function of the NIST Cybersecurity Framework revolves around containing the impact of a potential cybersecurity event. It includes development and implementation of necessary activities to take action once a cybersecurity event has been detected.
Such recommended tasks include:
Ordr takes pride in being an ideal solution, as our platform uses automation to accelerate your response to an incident with the ability to create and apply next-generation firewall (NGFW) policies, quarantine VLAN assignment, access control list blocks, session termination, and port shutdown with a single click of a button. Ordr also provides details on the physical and network location for each device in the event that a technician needs to physically remove a device from the network or apply a patch by accessing the device directly.
The ability to recover from an incident needs to be both timely and effective. The quicker system restoration is performed and operations returned to normal, the less impact the cyber incident has on your organization.
The NIST Cybersecurity Framework recommends these steps:
Recovery is highly dependent on the circumstances of the attack, the attack method, and the level of complexity in the findings. Ordr’s ability identify the network and physical location of a device can aid in the system restoration process by enabling staff to quickly locate a device impacted by a cyber event that may need to be updated or reimaged. Ordr can also quickly move a quarantined device back to its normal network environment once upgrades, patches, or other remediation methods have been applied.
The NIST Cybersecurity Framework uses five specific service lanes that should be handled concurrently. The NIST Cybersecurity Framework is highly effective and can be used by any size organization in any industry.
The Identify function determines the who, what, when, and where of the cybersecurity configuration, while the Protect function employs safeguards and protects critical assets. Once you’ve dealt with the Detect function that monitors the network and roots out trouble, the Respond function launches the policies and procedures to combat an active cybersystem attack. Finally, Recovery involves the necessary activities to bring the system back to normal.
Ordr helps organizations extend the NIST Cybersecurity Framework to cover all of your assets, including IoT/IoMT/OT devices. With Ordr, you can rapidly inventory all assets in the domain, automatically classify them based on type and function, and assess each device for risk. It analyzes device communications to learn behaviors and creates device baselines to determine what communications the device requires for normal operations. From this baseline, Ordr can detect malicious activity and create policies to quickly stop active threats and quarantine compromised devices without disrupting the device, network, or enterprise operations. Ordr also uses device baselines to proactively improve protection via microsegmentation to logically segregate devices from non-essential areas.
To learn more about how Ordr aligns to the NIST framework, download this report.
Subscribe today to stay informed and get regular updates from Ordr Cloud

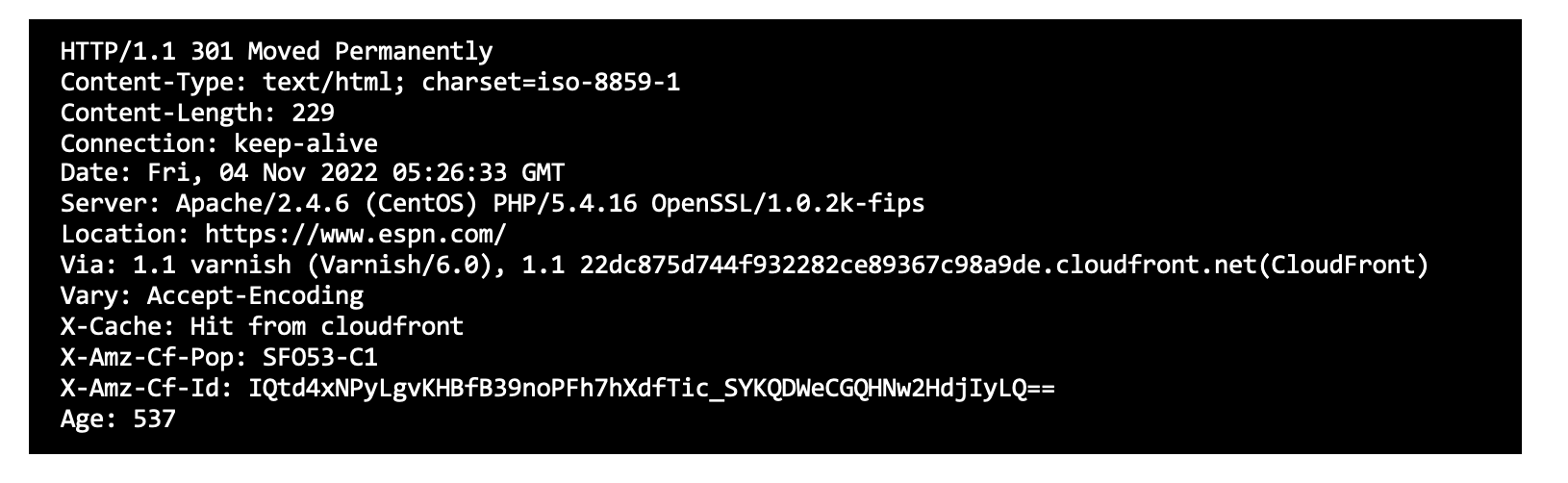
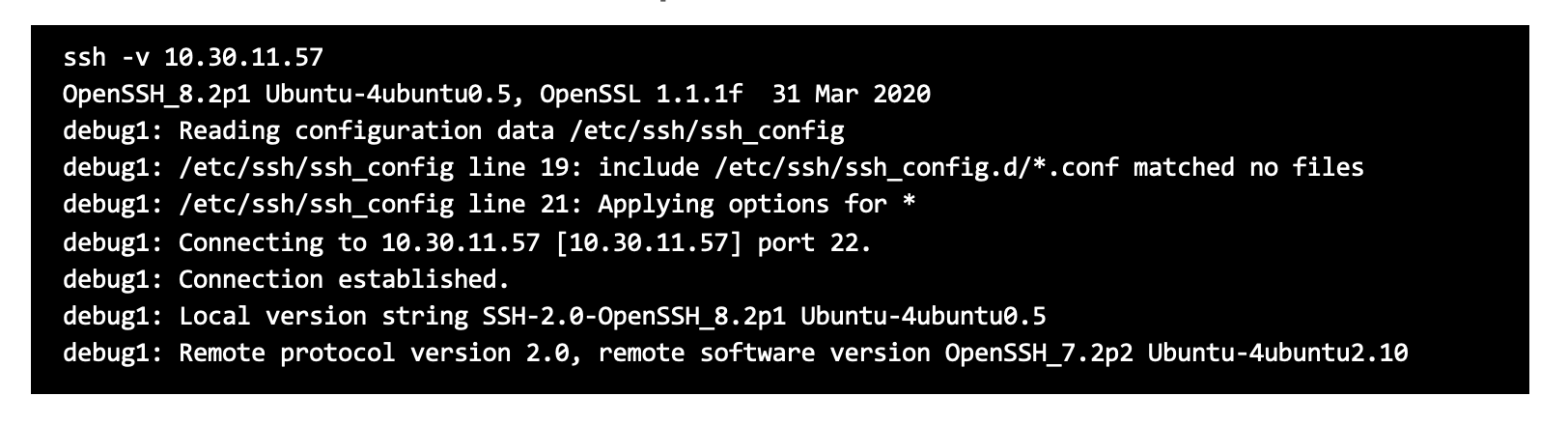
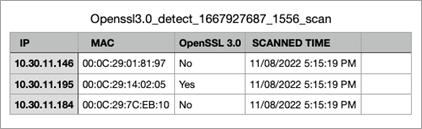
…as a precursor before finding out about the OpenSSL version. Example screenshots of detecting Open SSL that is built into the Ordr scanner. Sample SSL command Sample SSH command Packet…
Risk Management

By Pandian Gnanaprakasam

(Updated on November 10th with new Ordr capabilities)
On October 26th, OpenSSL Project a critical vulnerability associated with OpenSSL versions 3.0 and higher. The version released on November 1st — OpenSSL version 3.0.7 —addresses this vulnerability.
These vulnerabilities were downgraded from critical to as high (CVSS score 8.8 from 9.0) on November 1st.
Here is what you need to know about this critical vulnerability:
What is OpenSSL?
OpenSSL is a widely used open-source cryptography utility implemented to keep secure the web traffic exchange between a client and server. It is used to generate public and private keys, install SSL/TLS certificates, verify certificate information, and provide encryption.
Most web servers across the internet and within Intranets use SSL certificates to secure connections and the website being browsed. These certificates are traditionally generated by OpenSSL.
How concerned should we be about this vulnerability?
OpenSSL can be misused if the vulnerable version is in use. The good news is that this vulnerability impacts a very specific version of OpenSSL and patching quickly will address any associated risks.
A flaw in OpenSSL has previously affected businesses. In April 2014, OpenSSL’s Heartbleed flaw was discovered. Numerous web servers, including those running popular websites like Yahoo, included it. Security teams rushed to apply updates because the vulnerability was simple to exploit.
How is this OpenSSL vulnerability exploited?
Both CVE-2022-3602 and CVE-2022-3786 vulnerabilities are prone to buffer overflow attacks that can perform RCE (Remote Code Execution) or expose contents of the memory that contains private keys or proprietary information.
The chances of these vulnerabilities getting abused are low because one of the conditions is a malformed certificate signed by a trusted CA.
The issue lies in the verification process of certificates that OpenSSL performs for certificate-based authentication. The exploitation of the vulnerabilities could allow an attacker to launch a Denial of Service (DoS) or even a Remote Code Execution attack.
Patches for the two weaknesses found in OpenSSL v3.0.0 to v3.06 have now been released.
Which OpenSSL versions are vulnerable?
CRITICAL Severity: This affects common configurations, which are also likely to be exploitable. Among these are significant disclosures of server memory (potentially revealing user information), vulnerabilities that are easily exploitable to compromise server private keys remotely, or situations where remote code execution is possible. We will keep these issues private and release a new version of all supported versions as soon as possible.
HIGH Severity: This includes issues that are of a lower risk than critical, perhaps due to affecting fewer common configurations or which are less likely to be exploitable. These issues will be kept private and will trigger a new release of all supported versions. We will attempt to keep the time these issues are private to a minimum; our aim would be no longer than a month, where this is something under our control.
Is the Ordr platform impacted by the OpenSSL vulnerability?
Ordr has reviewed our usage of OpenSSL. This vulnerability does not impact Ordr as we do not use the impacted version.
How Ordr can help?
Ordr has added two new capabilities:
A new scanner that will detect versions of the OpenSSL that are vulnerable.
New IPS signatures that can detect exploits of this OpenSSL vulnerability
Sample SSL command
Sample SSH command
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Subscribe today to stay informed and get regular updates from Ordr Cloud

…Command and Control (C&C) server and a connection could be used to download malware such as ransomware to a device and orchestrate the spread across an environment. Malicious Russian Site…
Security Bulletin

By Pandian Gnanaprakasam

As the war in Ukraine broke out in late Feb, security teams around the globe took notice. Russia has long been a focus in the fight against cybercrime, and their aggression raised concerns to new levels with fears that cyberattacks could increase with a focus on the US and other western countries. On March 21, 2022, President Biden confirmed the rising concerns with a statement warning of a potential increase in Russian cyber activity targeting the US, allies, and partners. As organizations across the globe were taking steps to improve cyber defenses, we heard from many of our customers asking what Ordr could do to help improve security, threat prevention, and the ability to monitor their environments. A primary requirement was the ability to identify devices in their environments that had communications with potentially malicious Russian sites.
By continuously analyzing network data, Ordr uncovers all connected device communications within an organization as well as communications to external sites. We also assess the risk for these communications and provide that insight to every customer in our UI. To make these insights a little easier to access, we created a focused report that our customers could run to get a quick view of the exact flow level details of medical devices communicating with Russian sites and assess the risk. You can learn more about the report in this video:
While our customers could collect some of this data from various tools across their environment, only Ordr combines communication insights with device context. This triangulation methodology from multiple sources helps them understand the risk of communication and provides them with the details needed to pinpoint the device at risk and quickly craft the proper response to eliminate the threat.
Ordr’s continuous analysis of network data and the report highlighting communications to Russia is available to all Ordr customers, providing necessary details to help them understand and quickly respond to potential threats. We also wanted to share our insights beyond Ordr’s customers to help others understand the potential risk to their environment.
The threats uncovered below focus on medical devices; however, these threats are not limited to just medical devices or the healthcare industry. Attackers target connected devices in all industries, including manufacturing, financial services, retail, and utilities. Attacks not only target medical devices but also operational technology (OT) devices such as HVAC systems, elevator controls, and connected cameras that are common across all industries. Many of these devices are critical to business operations even if it seems there is no direct connection, and a successful breach could have a significant impact. For example, an attack that takes an HVAC system offline could create unsafe conditions in the emergency ward and hamper patient care.
Before getting into the details of our findings, here’s an extremely brief overview of how Ordr works and some of the details we uncover for each device:
Ordr analyzes data collected from multiple points in the network to discover every connected device. We also uncover details to accurately classify every device and identify devices with vulnerabilities and potential threats. With our approach to collecting and analyzing network data we provide granular device insights without the need for agents or scanning and no impact on device operations.
Ordr insights help customers understand the exact devices connected in their environment, how those devices fit into the organization, and their potential risk. Ordr device details include:
Ordr also uncovers internal and external communication insights for each device by analyzing network data. This post focuses specifically with devices communicating with Russian sites but could also be used to identify communications with other restricted or high-risk countries. Ordr insights specific to devices communicating with external sites include:
For the insights that follow, the Ordr platform performed deep analysis on data aggregated and anonymized from 50 large health care chains, each consisting of multiple hospitals. The details below focus on medical devices used in healthcare settings such as infusion pumps, patient monitors, EEG/ECG, MRI/CT scanners, X-Rays, ultrasounds, medical gateways, medical workstations running medical apps, medical servers used to process and store patient data, and other connected device in the clinical setting delivering patient care. As mentioned previously, these threats are not limited to healthcare devices or the healthcare industry.
The goal of this analysis is to shed light on the potential threats so that organizations across all industries can be better prepared and take proper steps to secure their environments.
NOTE ON METHODOLOGY
The first analysis highlights Russian domains that were identified for sustaining the highest levels of traffic into and out of the organizations we analyzed. While these domains may look somewhat benign, each may have the potential to be used to distribute malware or perform other malicious activities. Many of these sites are known to generate intrusive online ads and collect personal information. Device communications to any of these domains should be scrutinized to determine if communication is required and expected.
The next analysis identifies device types that have communications with the largest number of Russian URLs. Many of these devices perform critical functions in healthcare environments and we can infer these types of devices are top targets for attackers.
The following medical device types have communications with the least number of Russian URLs compared the devices listed above. Like the devices above, many of these devices provide critical functions in healthcare environments and although they communicate with fewer Russian URLs, this activity should still be scrutinized to determine if communications are required and expected.
Focus using our analysis on individual devices, the following details highlight the device types with the most amount of data received from Russian sites per device. Even if outbound communication is blocked by a firewall, the fact that these devices are receiving this volume of data from Russian sites should be of concern, and communication should be scrutinized to determine if communications are required and expected.
Device Category (Received bytes per device)
Since a single organization may have multiple units of each device, we aggregated and analyzed device data to highlight the device categories with the most amount of data received from Russian sites. As with the other categories these devices provide critical functions in healthcare environments.
Since a single organization may have multiple units of each device, we aggregated and analyzed device data to highlight the device categories with the most amount of data transmitted to Russian sites. These devices provide critical functions in healthcare environments and are also found in the list above, highlighting device categories receiving the most data from Russian sites.
Looking at the types of Russian sites communicating with the device data we analyzed, the following shows the distribution of site categories communicating with medical devices. As with the Top Russian Domains by Traffic analysis above, many of these categories may look benign; however, each may have the potential to be used to distribute malware or perform other malicious activities.
Looking at the reputation score of destination URLs, the following chart highlights device types and the reputation of the Russian sites they communicate with. Sites with a low reputation score (e.g., 10) are determined to be very suspicious with a high probability of being malicious. As an example, these sites could host a Command and Control (C&C) server and a connection could be used to download malware such as ransomware to a device and orchestrate the spread across an environment.
The site counter.yadro.ru is a known malicious site advertisement that has had several reports in the past of downloading malware. The following device types analyzed had frequent transactions with this site.
Here is a list of the offenders by device type with the number of URLs they are reaching out to.
The following analysis highlights the top Russian cities with the most traffic to and from the devices we analyzed. Since attackers commonly use techniques to obscure their details, it is not always easy to determine the exact location of malicious activity. However, by analyzing the site IP address, it can be possible to provide insight and an approximation of the potential location.
Identifying potentially malicious activity and understanding risk is a critical first step to protecting any environment. Ordr customers regularly generate and review their detailed reports showing devices in their environment that have communicated with Russian sites. That report not only identifies these communications but also provides detailed analysis to help customers understand and address the potential risk in their environments.
Ordr also helps customers eliminate risk by dynamically generating policies for enforcement across their existing security and network infrastructure. Ordr has Integrations with leading firewall vendors and can automatically push policies to limit the sites with which devices are allowed to communicate. Examples might be manufacturer maintenance, software update, and services such as image enhancements for medical imaging.
If a device is already infected and spreading malware, Ordr can quickly push policies to switches or wireless controllers to isolate them and stop the spread of the attack. Ordr can also push proactive zero-trust policies to switches or wireless controllers, allowing only a pre-determined set of devices and flows to and from any medical device.
If you want to learn more about the Ordr solution, the insights we provide to uncover the risk of Russian communications, and how you can improve the security for your connected devices, reach out for a personalized demo.
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Subscribe today to stay informed and get regular updates from Ordr Cloud

…needed education about the unique threats to connected devices, and we were competing for attention in the cybersecurity space with hundreds of companies, each claiming to have something new and…
Company News

By Pandian Gnanaprakasam

Today Ordr announced our Series C funding; another injection of capital that allows us to continue investing in our company and build it to last. On this occasion, I can’t help but look back and reflect on a journey that began in 2015 when Sheausong Yang and I–the founding team–had a vision to build a security platform that would give organizations the ability to see and secure every connected device in their network.
Our idea was new then, and it wasn’t easy getting people to understand the problem at first. Even as organizations were increasingly adding unmanaged connected devices to enterprise IT environments, there was confusion over what was classified as internet of things (IoT) or operational technology (OT). Many organizations we encountered thought we were talking about consumer technologies, like then-new smart speakers, and not the millions of medical devices, industrial controls, building management systems, and other equipment like surveillance cameras, phones, printers and vending machines that were often connecting simultaneously to enterprise networks and the public internet.
Because an entrepreneur’s journey is hard, often with ups and downs, it’s important to find partners who believe in the vision, the team, and are willing to give the support needed to work things out and solve big problems. We were fortunate to find such a believer in Peter Wagner, founding partner at Wing Venture Capital. Peter believed in the Ordr founding team and our ability to design the right solution to the problem. We also trusted Peter as a partner in our journey. Dominic Orr, former president of Aruba Networks; Pankaj Patel, former executive vice president and chief development officer at Cisco Systems; Dan Warmenhoven, former CEO of NetApp; and Prakash Bhalerao, veteran chief executive and angel investor also became believers in our vision and invested in our seed round as well.
What was not well-known when we started, but something that Peter, Dominic, Pankaj, Dan, and Prakash grasped, was how difficult it was to discover and secure IoT devices in enterprise environments. In fact, it was nearly impossible. These devices were often connected and unmanaged, operating outside the view of IT management and security tools, and given the proliferation rate at which they were connecting, the problem was getting worse. A specialized security solution was needed, and so we set out to build one. At the same time, the industry needed education about the unique threats to connected devices, and we were competing for attention in the cybersecurity space with hundreds of companies, each claiming to have something new and better, even if only a few really did.
Every strong structure starts with a solid foundation. Our approach to connected device security would be built on data and analytics. Specifically, building a massive data lake populated with the details of as many device types as possible, and using behavioral analytics to build security models for each. Achieving our vision required studying breaches to understand their characteristics and communication patterns, and continuously comparing what we learned with the typical behavior of every single device in the network. Employing behavioral analytics was the only way to monitor complex communication patterns and adapt to the ever-changing strategies of threat actors.
Artificial intelligence (AI) and machine learning (ML) require massive amounts of data to solve hard problems. Rather than rely on second-order metadata, the Ordr Data Lake would be populated with accurate, correlated device details collected directly from the source. This was no easy task. You need to have grit, and shortcuts taken at this stage will haunt you throughout the lifetime of the product. We knew once we had the data we could harness it to solve hard problems, take on the challenges ahead, and build a platform for connected device security.
Fast forward to 2022 and the Ordr Data Lake has millions of device profiles; a number that grows as new devices are released and connected to environments across the globe. To enrich our data lake with new details and insights, we do a full, real-time packet capture across our customers’ environments to feed our platform with an accurate and continuous input of every connection, every flow, and every change. Analysis of that data is real-time too. It has to be. When someone asks for the current weather, it does no good to give the temperature from earlier in the day. Real-time analysis is critical in security and provides a precise assessment so accurate decisions can be made. In security, the game is rapid detection and remediation; guesswork is unacceptable.
Other key innovations have been part of the evolution of our platform. Data correlation, normalization, compression and organization is critical to storing and harnessing the massive amounts of data we collect and analyze without requiring hundreds of servers and zettabytes of disk storage. For those who are counting, one zettabyte is one billion terabytes. Thanks to our intelligent data compression, we can secure an entire large-scale hospital with just a few servers as our analytics backend. For context, the average hospital maintains an inventory of more than 100,000 total devices of which at least 10-15 thousand are in clinical care as internet of medical things (IoMT) devices, as well as IoT and OT associated with administration, communications, facilities management, and other essential functions–not to mention all the stranger things that find their way onto enterprise networks.
Behavior-based identity analytics is another key innovation for Ordr, and is used to establish multifactor authentication on agentless, unmanaged devices. Triangulation of factors such as a device’s OS vulnerabilities, communication patterns across the enterprise, communications patterns to external sites, and the reputation score of destination sites, are all analyzed to minimize false-positives and ensure a high level of confidence when unique indicators of compromise (IOC) are identified.
Countless hours of hard work, determination, and creativity were behind the effort that turned our vision into a proof-of-concept, and then, a working product. From that point, our vision, the strength of our team, and the potential of our technology helped us secure Series A funding, led by Alex Doll of Ten Eleven Ventures and joined by Unusual Ventures. With Series A we were able to build our team, establish our brand, and go to market. After Series B, led by Dharmesh Thakkar of Battery Ventures, and with investments from Kaiser Permanente Ventures and Mayo Clinic, Ordr was established as a force in healthcare and positioned for expansion into other verticals, like manufacturing, financial services, smart cities, and government. At this point, we began expanding into visibility and security for every connected device. To secure any device, you need visibility into every device in the network.
When the pandemic struck in early 2020, the strength, resilience, and flexibility of our company were put to the test. The growth of nearly every organization was impacted at this time, but our healthcare customers in particular faced tremendous challenges. We stepped up to explore new ways to deliver value with our platform. Leveraging our core discovery and analytics capabilities, our customers found value in the ability to locate existing device inventory and understand real-time device utilization.
As an example, the Ordr platform enabled customers to keep track of critical devices such as ventilators, ensuring they were deployed to maximal efficiency to deal with the surge of COVID patients. Not only did the Ordr platform keep hospitals safe during this time, it also helped them run efficiently, ensuring they could continue to deliver critical healthcare services. That built goodwill and, when the pandemic eased, our customers adopted our platform enterprise-wide and recommended us to their peers in the industry. It was a key moment for the growth of our business.
As the world slowly returns to some semblance of normalcy, our Series C funding sets us up for our next phase of expansion on our journey to build an unrivaled security franchise. The Ordr Data Lake is growing rapidly, and now includes millions of device profiles, helping us to discover, identify, and classify every device in a customer’s environment with accurate, granular detail.
Within minutes of deploying Ordr in an environment, the data we analyze populates our UI with every connected device discovered, classifying each by manufacturer and model. Each device includes a picture for easy identification, along with a detailed description of attributes that include the device’s OS, vulnerabilities, connectivity details, flow data, applications installed, and logged users. Visualization in our platform is world-class and gets raves from our customers thanks to the tremendous “design thinking” effort we put into our UI/UX to achieve excellent aesthetics in support of usability.
On top of that, we add data and insights from a wide variety of enterprise tools to enrich our analysis. With more than 70 integrations, our data lake quickly provides accurate context for the operational status, as well as security posture, of every device in an organization.
Another critical strength of the Ordr platform is its ability to identify and respond to active attacks, including zero-day threats, and enable teams to stop them quickly with automation and orchestration. To get to “zero-day” attack detection requires behavioral baselines–something that must be done within minutes–to identify unique, malicious, abnormal behaviors. Since most connected devices operate within narrow behavioral parameters, our extensive data lake allows us to detect IOCs with a high degree of speed and accuracy.
Once malicious activity is identified, we leverage our deep knowledge of each device and its exact connectivity under normal operations to dynamically generate zero trust policies to isolate any misbehaving, potentially compromised device. These policies can be reviewed by security teams and, with a single click in our UI, policies are enforced with existing security and network infrastructure. With Ordr, response times are reduced from hours or days down to minutes to stop the spread of an attack. No other connected device security solution provides a complete map of all the devices, their connectivity in the enterprise, and their flow level context in real time, 24×7. We achieved this by building interfaces with every single network infrastructure vendor out there–a daunting task indeed.
From the start, our mission has been to help enterprise organizations see, know, and secure every connected device everywhere. We continue to innovate to deliver on that mission and provide our customers and partners with the most accurate, complete, and easy to consume device knowledgebase on the planet with meticulous device classifying, profiling, and cataloging.
What’s more, all of our data is available to partners through open APIs. In fact, Ordr is the only platform that has complete device intelligence that includes network and flow-level context with deep accuracy. Today, Ordr is well-positioned to be the supplier of choice of device intelligence to evolving Open XDR frameworks, providing open-source data to enable the correlation of information and delivery of the best possible service to the customers.
There are many more innovations and opportunities ahead for Ordr. With our world-class investors, dynamic board of directors, experienced management team, and passionate employees, we look ahead with laser focus to meeting the needs of our customers and helping them see, know, and secure every connected device that is critical to their business. Stay tuned, we’re off to write the industry’s next chapter on connected device security–and beyond.
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Subscribe today to stay informed and get regular updates from Ordr Cloud
…best practices for organizations to follow to manage that risk. These frameworks consist of assessment, monitoring, preventative, and response activities to help security teams identify and resolve current issues and…
Protecting data from cyber attacks has only grown more complicated over the years: the number of cyber crimes committed per year has massively grown. In 2021, the number of security breaches reached 1,862. How do organizations prevent the risk of cyber attack?
Many countries and industries have devised their own sets of cybersecurity best practices for organizations to follow to manage that risk. These frameworks consist of assessment, monitoring, preventative, and response activities to help security teams identify and resolve current issues and constantly scan for new threats. In some cases, these frameworks have even been signed into law.
In this article, you’ll learn what those cybersecurity frameworks are, how they are categorized, and determine which of the most common frameworks might help your organization achieve its security goals.
Cybersecurity frameworks are systems and standards that guide security programs and help leaders mitigate cyber risks in their organizations. These frameworks act as a shared language across regions and industries, allowing consumers and businesses to make informed decisions about the companies they place their trust in. No matter the industry, organizations that adopt cyber security frameworks have committed to maintaining a high degree of security around the data they gather and store, as well as the services they provide. Likewise, when a threat arises, they should have a clear plan to take action.
In many cases, implementing certain cybersecurity frameworks is necessary to comply with state, national, and international regulations. Abiding by accepted frameworks shows that organizations are taking concrete steps to decrease their exposure to vulnerabilities that hackers can exploit on their networks, applications, or devices. In practice, cybersecurity frameworks can take on several different forms.
There are three types of cybersecurity frameworks distinguished by their function:
Control frameworks
Control frameworks are foundational security strategies. They help teams:
Program frameworks
Program frameworks strengthen an organization’s overarching security practices by:
Risk frameworks
As the name implies, risk frameworks are designed specifically to minimize risks. They include:
Together, control, program, and risk frameworks serve as a comprehensive barrier — not only to current cyber threats but risks that may arise in the future as well.
Since there isn’t any one “right” framework to follow, implementing cybersecurity frameworks can be daunting. Let’s explore eight of the most common frameworks to give you inspiration for the types of frameworks that could fit your organization’s security goals.
The NIST Framework for Improving Critical Infrastructure Cybersecurity, known as the “NIST Cybersecurity Framework,” or “NIST CSF” was created to safeguard commercial, energy, and defense utilities. However, its core principles can help any organization follow the basic pattern of cyber defense: identify, protect, detect, respond, and recover.
The NIST framework consists of a series of steps to protect an organization’s data (in transit and at rest), detect risks, respond to threats, and recover assets if needed. It also prompts security teams to conduct root cause analysis of any vulnerabilities they uncover in the process. Originally, the NIST framework was designed to cover traditional IT-managed systems. But organizations are applying the NIST framework to any IoT, IoMT, OT or other connected devices under their purview.
While NIST compliance is voluntary, it’s required for any organization doing business with federal government agencies. For that reason, many enterprise-level organizations in the U.S. have adopted the NIST framework in conjunction with the Cybersecurity Enhancement Act of 2014.
The Center for Internet Security (CIS) Critical Security Controls framework is best for organizations wanting to ease into a cybersecurity framework. The 20 CIS controls are constantly updated by volunteer experts who hold various industrial, academic, and government roles. Controls are divided into three groups: basics, foundational, and organizational. Security teams should implement the basics first and then move on to the foundational and organizational controls.
CIS also has benchmarks that work in conjunction with its controls. They are set according to other existing standards like NIST or HIPAA, and are split into two levels: security essentials that don’t affect performance, and advanced protocols that may affect performance. Again, this distinction enables security teams to break up their work into more manageable chunks, getting controls implemented faster and more efficiently.
CIS frameworks are meant to calibrate IT services, products, and devices, as well as prepare organizations to tackle other, more complex and demanding frameworks.
International Standards Organization (ISO) frameworks are international standards for cybersecurity. As part of the 27K ISO framework, organizations must design and implement an information security (InfoSec) management program dedicated to mitigating identified threats and patching vulnerabilities.
27001 and 27002 ISO frameworks are notoriously demanding. They have over 100 coherent and comprehensive controls that organizations struggle to follow without an ongoing risk management process.
But many organizations need to adopt at least ISO 27001 for legal reasons. To be considered ISO 27001-compliant, organizations must demonstrate that they adhere to the “PDCA Cycle” to an external auditor. The PDCA Cycle is a business management method that focuses on four steps: Plan, Do, Check, and Act:
Any organization that has a financial services arm or handles particularly sensitive data, such as medical records, should consider implementing the ISO 27001 protocol.
Systems and Organization Controls 2 dictates how organizations protect their data from unauthorized access, security incidents, and other vulnerabilities. Today, most organizations store this information on the cloud, so SOC 2 was formed specifically to protect sensitive data used in cloud-based applications and connected devices.
The SOC 2 framework requires that customer data is managed and stored based on 5 Trust Services criteria:
Unlike other frameworks, SOC 2 has some flexibility — organizations can determine attestation reports and controls on their own. These reports and controls are then distributed to and evaluated by independent CPA auditors.
While achieving SOC 2 compliance isn’t necessary, it establishes trust with service providers and their customers. Modern procurement teams often look for SOC 2 compliance when evaluating new vendors. Any B2B SaaS organization should strongly consider achieving compliance with this framework.
The European Union’s GDPR is consumer and data privacy legislation, not a cybersecurity framework. However, this law requires that organizations use “appropriate technical and organizational measures” to secure processed personal data — something that applies to many organizations, especially those in the healthcare sector.
All organizations with patients in the EU must prove that they are GDPR-compliant under the accountability principle. That means they’ve instituted technical measures to adhere to the GDPR law, can explain how those measures work, and demonstrate their effectiveness whenever requested. Examples of those measures include:
The goal of GDPR is to provide consumers with more control over how their personal data is handled and disseminated by companies, particularly in a marketing context. Putting consumers in the driver’s seat makes it more difficult for organizations to mislead consumers with deliberately confusing or vague information.
The EU takes GDPR rules very seriously and will fine organizations that fail to comply with GDPR up to 4% of their global revenue.
The Cybersecurity Maturity Model Certification (CCMC) is a unified standard for implementing cybersecurity across defense industrial base contractors. The CMMC model was built to prevent U.S. Department of Defense (DoD) information leakage.
Before a contractor can start any government contracts, they must pass certain CMMC certifications. Currently, this applies to over 300,000 companies in the supply chain.
There are five levels to the CMMC certification paradigm. Each reflects the reliability of a company’s cybersecurity infrastructure to safeguard sensitive government information like federal contact information and unclassified documents. Contractors must pass an audit conducted by third-party assessors to achieve each certification.
Organizations that abide by the NIST framework will be in good shape, as submitting an NIST 800-171 assessment to the DoD’s Supplier Performance Risk System is the first step in achieving CMMC certification. Post- NIST assessment, many enterprises enlist the help of an accredited third-party auditor to perform a gap analysis. They can pinpoint any major missing protocols prior to taking the full CMMC assessment.
Organizations also have a chance to remedy any issues that are spotted in a CMMC assessment 90 days after the evaluation is complete. If your organization is successful, it will be awarded a 3-year CMMC certification.
Like GDPR, FISMA is U.S. legislation that defines a framework of guidelines and standards to protect government information and operations. FISMA was signed into law in 2002 and requires compliance from state agencies that administer federal programs or organizations that hold a contract with the U.S. government. FISMA compliance is especially crucial for healthcare organizations: many patients receive care through Medicare and Medicaid programs, which are government programs that must be protected. Non-compliance with FISMA can lead to a loss of federal funding, reputational damage, and even indictment for potential government hearings.
FISMA has similar controls to the NIST framework, requiring federal contractors to:
Organizations that work with the federal government, and even those in the private sector, should stay up to date with FISMA standards and keep a record of the ways in which they comply with the law. Data should be classified according to the level of sensitivity whenever it’s created or stored. Organizations should also take steps to encrypt that data automatically.
The Cyber Essentials scheme is designed to show an organization has a minimum level of protection in cyber security through annual assessments to maintain certification. The Cyber Essentials and Cyber Essentials Plus certifications help organizations avoid weaknesses and address vulnerabilities to prevent exploits.
Both assessments are rooted in five major controls that show organizations are committed to preventing cyber crime. Those controls include:
Organizations that want to bid for UK central government contracts must have the Cyber Essentials certification at minimum.
Cyber security is of utmost concern to all organizations: hospitals, IP-enabled manufacturing systems, and Interactive Teller Machines are collecting more data than ever before, making rock-solid security protocols a necessity — not a nice to have.
Implementing cyber security frameworks can seem daunting, especially without the right tools. Organizations need a security solution particularly designed for their unique security needs, and that’s where Ordr comes into play. Ordr makes connected device security simple through automated asset discovery, identification of vulnerabilities and risk, and dynamically created policy to improve protection.
Organizations that use Ordr get visibility into what is connected to their network in real time, allowing security teams to find and eliminate vulnerabilities proactively. Plus, Ordr can dynamically create policy to respond to active threats or proactively improve security to protect your organization, data, and patients.
Subscribe today to stay informed and get regular updates from Ordr Cloud

…communications to only enable access required for their role. We recommend the following approach to secure every connected device. Download our Maturity Guide for connected device security for more details: …
Security Strategy

By Benjamin Stock

Before medical device manufacturers are able to release a product to market, they are subject to Food and Drug Administration (FDA) reviews to evaluate the safety and effectiveness of these devices. Since 2014, those evaluations have included medical device security guidance, with a subsequent update in 2018. Now, with the explosive growth of connected devices used by hospitals and healthcare providers and a growing number of cyberattacks that have crippled healthcare services, the FDA recently released draft guidelines requiring that devices comprising the Internet of Medical Things (IoMT) meet more stringent cybersecurity standards.
“Cybersecurity in Medical Devices: Quality System Considerations and Content of Premarket Submissions,” is a 45-page document that deals with security design, vulnerability disclosures, Software Bill of Materials (SBOMs), and other documentation requirements that will have to be addressed by medical device manufacturers before their new devices can gain FDA premarket approval.
In general, this is a step in the right direction for the FDA. Security needs to be built into the design of medical devices. At the same time, because medical devices have longer lifecycles than typical IT devices, it also means that it may be a while years before new devices falling under this new guidance are deployed. Because of the risks inherent with existing medical devices, healthcare organizations need to take action to secure legacy devices now.
New medical device applicants are advised to submit “a plan to monitor, identify, and address, as appropriate, in a reasonable time, postmarket cybersecurity vulnerabilities, and exploits.”
They are also asked to “design, develop, and maintain processes and procedures to provide a reasonable assurance that the device and related systems are cybersecure.” This includes making patches available “on a reasonably justified regular cycle,” and for newfound critical vulnerabilities, “as soon as possible out of cycle.”
Finally, manufacturers must provide the FDA with “a Software Bill of Materials,” including any open-source or other software their devices use. This is one of the new changes in the FDA guidance— a complete SBOM requirement instead a Cybersecurity Bill of Materials (CBOM), as outlined in the 2018 guidance.
Note that even with a manufacturer-provided SBOM, when a zero vulnerability like Log4J or OpenSSL is discovered, it is almost impossible to find out the real composition of the packages and the dependent libraries that was pulled into each package when the software was built and shipped. Sometimes, the manufacturer may have customized and configured functionality and those additional details aren’t released.
Therefore, as the FDA determines the format for manufacturer SBOMs, it is important to ensure that these SBOM declarations are detailed enough to include each and every piece of library that is included in the build. With this FDA mandate, if manufacturers release an SBOM that is accurate and complete, along with configuration settings, Ordr (and our vulnerability matching engine) can immediately assess the risk of these vulnerabilities and understand the exposure and exploitability.
The new security requirements came into effect when the $1.7 trillion federal omnibus spending bill (the 2023 Consolidated Appropriations Act) was signed by President Joe Biden on December 29, 2022.
Section 3305 of the spending bill — “Ensuring cybersecurity of medical devices”— is an amendment to the Federal Food, Drug, and Cosmetic Act. It took effect 90 days after the Act became law, and with its new authority, the FDA has given manufacturers six months — until Oct. 1, 2023 — to comply with the new regulations. The new law also requires the FDA to update its medical device cybersecurity guidance at least every two years.
Security of medical devices is a shared responsibility. While the FDA mandate can ensure security for a device before it is released to the market, the day-to-day management and security of devices post FDA approvals is the responsibility of healthcare providers and requires a solution like Ordr. Ordr not only maintains an accurate device inventory and monitors devices for vulnerabilities and threats but also delivers device utilization details to optimize operations.
In addition, medical devices are expensive, and a complete upgrade to new devices that adhere to the new guidelines is not operationally feasible or cost effective. Ordr can ensure existing devices (pre-2022 devices) or devices with outdated operating systems in the network can be secured via Zero Trust segmentation policies to restrict access and communications to only enable access required for their role.
We recommend the following approach to secure every connected device. Download our Maturity Guide for connected device security for more details:
With regard to the new 2022 FDA mandate, Ordr can ingest SBOMs as manufacturers make them available, to enable easy visibility across the entire organization. Ordr Software Inventory Collector can complement manufacturer SBOMs by identifying applications for devices running Windows, iOS, and Linux operating systems.
The Ordr platform is trusted by the world’s leading healthcare delivery organizations. Schedule a demo with our product experts to see how we can secure your connected devices.
Benjamin Stock is the Director of Healthcare Product Management at Ordr. Previously, Ben worked as the Director of Clinical Equipment Systems and Project Support at SSM Health St. Louis, MO. With more than 15 years of experience in healthcare technology management, his wealth of knowledge in the Clinical Engineering space allows him to be a wonderful advocate for Ordr healthcare customers. Ben is also a Certified Biomedical Equipment Technician (CBET).
Subscribe today to stay informed and get regular updates from Ordr Cloud
…trusted components, and harden applications where possible to prevent vulnerabilities. In-house applications should be accessed for security and kept within maintenance limits. Do not allow applications to provide a backdoor…
The major crux faced by IT security professionals across the industry today is that threats evolve at the same speed as technology. Technology is vital to business, especially as more professionals work outside the standard office environment, and that creates additional vulnerabilities. The CIS 20 Critical Security Controls framework is so widely used, that there are several different ways to reference them:
The key to mitigating risk is having a solid security foundation on which to build industry or business specific security protocols. The CIS 20 Critical Security Controls (CSC) are that foundation.
The CSC are a security foundation of actionable best practices developed by the Center for Internet Security (CIS) and the SANS Institute. Knowledge is garnered from a wide array of security professionals, condensed and clarified by industry experts, and presented in a format that can be adapted by any organization to counter the leading forms of cyber attack and protect data assets.
These basic principles allow IT professionals to respond swiftly and effectively against growing security concerns, which allows organizations to reduce cybersecurity risks.
All organizations must navigate the deep and complex waters that are risk and compliance. Industry standards often define the specific dive level an organization has to make into those murky depths, but they rarely indicate how. The CIS Critical Security Controls are a set of best practices that recommend how to combat the most common cybersecurity threats, and are applicable to all organizations.
The CSC are broken into three implementation groups, each set of controls being a progression based upon an organization’s needs:
By segmenting the controls into resource and expertise specific sections, an organization is given the option of choosing the best fit for their infrastructure.
The CIS top 20 Critical Security Controls are an evolution of worldwide knowledge from IT professionals that are arm-deep in security each and every day. The results of using the CSC are phenomenal; studies have shown that 85% of cyberattacks can be thwarted by using just the basic implementation of CSC. Using the organizational implementation of all 20 Critical Security Controls has a staggering 97% success rate. By using these outlined best practices, an organization will have a strong security base that has already proven its worth. A base that is perfect for building in any additional industry specific security requirements.
The CSC are cross-compatible because they are effective best-practices that encompass a large threat range. Industry specific standards and security framework ideologies are growing and evolving with technology, and the CSC helps organizations keep up with the ever changing security environment.
For example, the California Consumer Privacy Act (CCPA) and General Data Protection Act (GDPR) require organizations to maintain reasonable security to protect consumers’ private data. In addition, the IoT Cybersecurity Act requires connected devices to meet a minimum level of cybersecurity. Using the CIS Top 20 Critical Security Controls allows an organization to meet these thresholds.
Also, the CSC maps well to other well known security standards:
The CSC are beneficial aids for organizations that need to meet these complex industry standards or regulations.
The basic level of implementation is applying controls 1 – 6, and is considered the minimum amount of security that all organizations should use to be ready against cyber attacks.
Knowing who and what is using the network is key to preventing unauthorized access. This includes maintaining a detailed inventory via both active and passive discovery and using access controls. An in-depth view of all the devices that use an organization’s network provides a first line of defense.
Software needs to be inventoried and monitored in a way that allows the organization to see what’s been installed, who did the installing, and what the software is doing. Implementing authorization lists, installation rights, and integrity management are a must. Just like hardware assets, software can be used as a vulnerable point of entry into the protected network.
Security risks need to be identified before they result in an actual breach. The network should be scanned for weak points, which can then be quickly remediated. For the testing to be most effective, keep up-to-date on vulnerability advances.
Inventory of service accounts, administrative credentials, and adequate password requirements need to be fundamental. Administrative accounts must be safeguarded to prevent them being used by attackers.
Update default configurations and automate processes that manage them. Configuration management is necessary to lock-down unnecessary risks that attackers can exploit.
Logging will give an organization the ability to see all the activity of the network and provide pertinent details in the case of a breach. It also allows for the creation of alerts.
The foundational level of implementation is also applying controls 7 – 16, and is considered appropriate for mid-level organizations that need to protect systems beyond basic needs.
Numerous threats are directly related to email systems and web browsers. If they aren’t safe, the network isn’t either.
Malware is used for everything from identity theft to corporate espionage. Antivirus software and malware prevention mitigates the risk to users and the organization.
Firewalls, port scans, and separation of critical services can reduce the available avenues open to attackers. Sharp focus here can prevent unauthorized access.
Some forms of cyber attack, like ransomware, directly target data. Backups prevent losing data and give a benchmark for data comparison if data integrity is in question after a security breach.
Encryption and advanced authentication methods are good starting points. Shielding network devices from improper access, shields the network and its data.
An organization must control flow through the boundary using monitoring and analysis. Tight management of perimeter defenses keeps out unauthorized users and keeps in sensitive data.
Data protection is complex and requires a multi-prong focus. Use managerial controls, procedures, and technology to ensure data is accessed only where authorized, is controlled, and maintains integrity.
Classify data, segment based on that classification, and control the access based on what users/systems need to use that level of data. This prevents both internal and external unauthorized access to data.
Wireless access is a common area of risk for many organizations, and controls are necessary to mitigate as much risk as possible. Implementing protocols around SSID and broadcasting levels, guest networks, and monitoring the wireless network are ways to combat attacks.
Attackers using valid credentials is a concern that must be addressed. Two factor authentication and managing the account life cycle are common recommendations.
The organizational level of implementation is applying all 20 CIS controls. It is considered appropriate for well-developed organizations that have more complex security needs and have the necessary resources/capabilities required for implementation.
Users are an important piece of the cybersecurity puzzle. Refreshing users about security practices and new attacks to be wary of can be key to preventing breaches.
Keep applications current, use only trusted components, and harden applications where possible to prevent vulnerabilities. In-house applications should be accessed for security and kept within maintenance limits. Do not allow applications to provide a backdoor into the system.
Always be prepared by planning for possible incidents and testing where possible. Don’t leave the response measures unplanned until something actually happens.
Identify points of breach and remediate as they are found. Keep testing and remediations evolving as the attack vectors change.
The CIS Top 20 Critical Security Controls are actionable best practices that organizations can use to protect themselves in an ever-changing technology environment. In order to successfully implement the CSC controls, organizations have to move forward against security risks by taking proper action to protect organizational devices, networks, and data.
This includes taking steps to implement proper discovery methods and ensuring the correct classifications of all devices on an organization’s network. In addition, an organization needs to continuously track device behavior and segment vulnerable devices. Risk assessment should be performed, as well, to ensure that security standards are being met.
The Ordr Systems Control Engine (SCE) gives organizations the power to enable visibility and security of their network-connected devices, with a simple and powerful solution to identify, classify, profile the behavior and risk, and automate action for every network-connected device in the enterprise.
One of the differentiated actions with Ordr SCE is that security and IT teams have access to dynamically generated segmentation policies to only allow sanctioned communications for every class of device.
Subscribe today to stay informed and get regular updates from Ordr Cloud
…with Fortigate and FortiNAC solutions. Read More Fortinet Fortinet and Ordr have partnered to deliver an industry-leading IoT and unmanaged device security solution by integrating FortiManager, FortiGate and FortiNAC with…
See, know and secure every managed and unmanaged asset, from IT, IoT, IoMT, OT, to users, applications, SaaS and cloud, in any environment.
The OrdrAI Asset Intelligence Platform has been designed to be modular, and enable a building block approach to address your cybersecurity maturity – from asset visiblity all the way to Zero Trust.
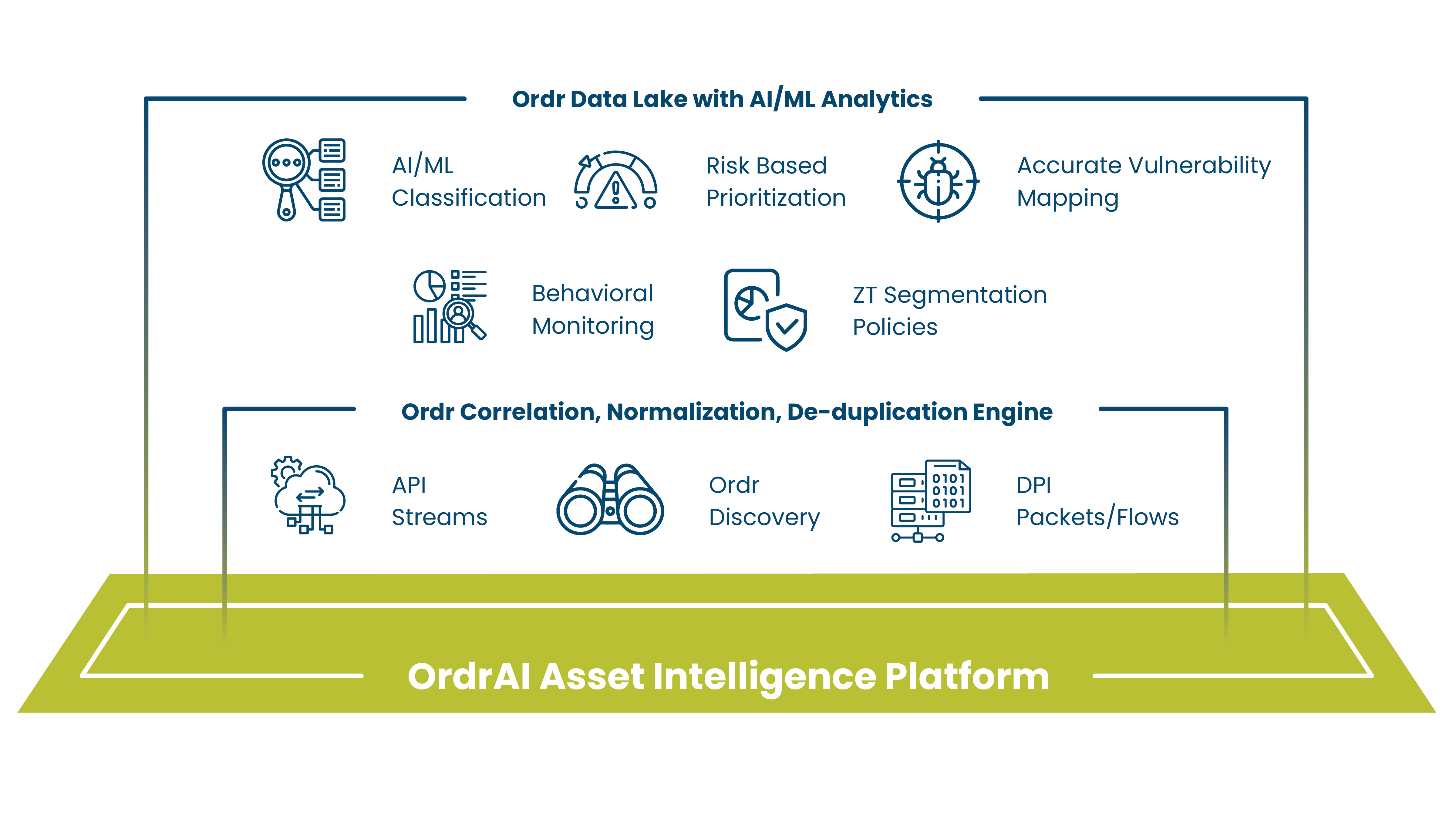
Gain visibility for your entire asset attack surface. Prioritize vulnerabilities, identify gaps and reduce your exposure.
MINIMIZE YOUR ATTACK SURFACEAdvanced threat detection, behavioral intelligence and segmentation for mission-critical IT, IOT, OT, IOMT assets.
UNLOCK ASSET THREAT PROTECTIONAddress your entire asset management journey
EXPLORE WHY ORDR FOR TOTAL ASSET SECURITYAsset Visibility and Management
Security Issues and Coverage Gaps
Vulnerability Prioritization and Management
Threat And Anomaly Detection
Segmentation and NAC Acceleration
Regulatory Frameworks
Enrich CMDB and security operations with real-time, automated hardware and software inventory, granular asset details, connectivity, device flows and more.
AUTOMATE VISIBILITY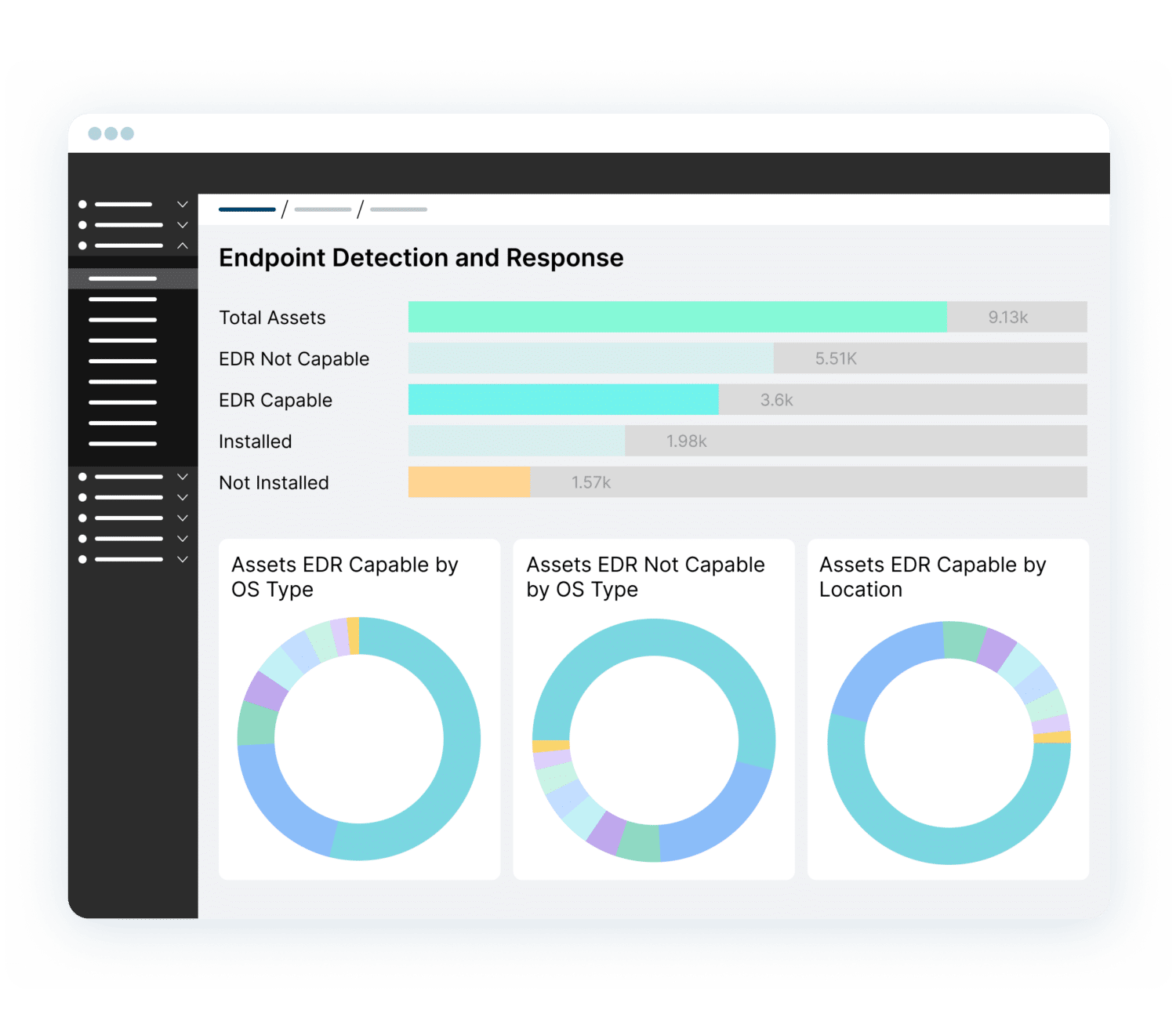
Improve your security hygiene by surfacing security gaps such as devices with outdated OS, or missing EDR/MDM agents.
PINPOINT SECURITY GAPSReduce risks by prioritizing vulnerabilities based on organizational impact. Automate remediation, assign to the right owner and track progress.
MINIMIZE SECURITY RISKS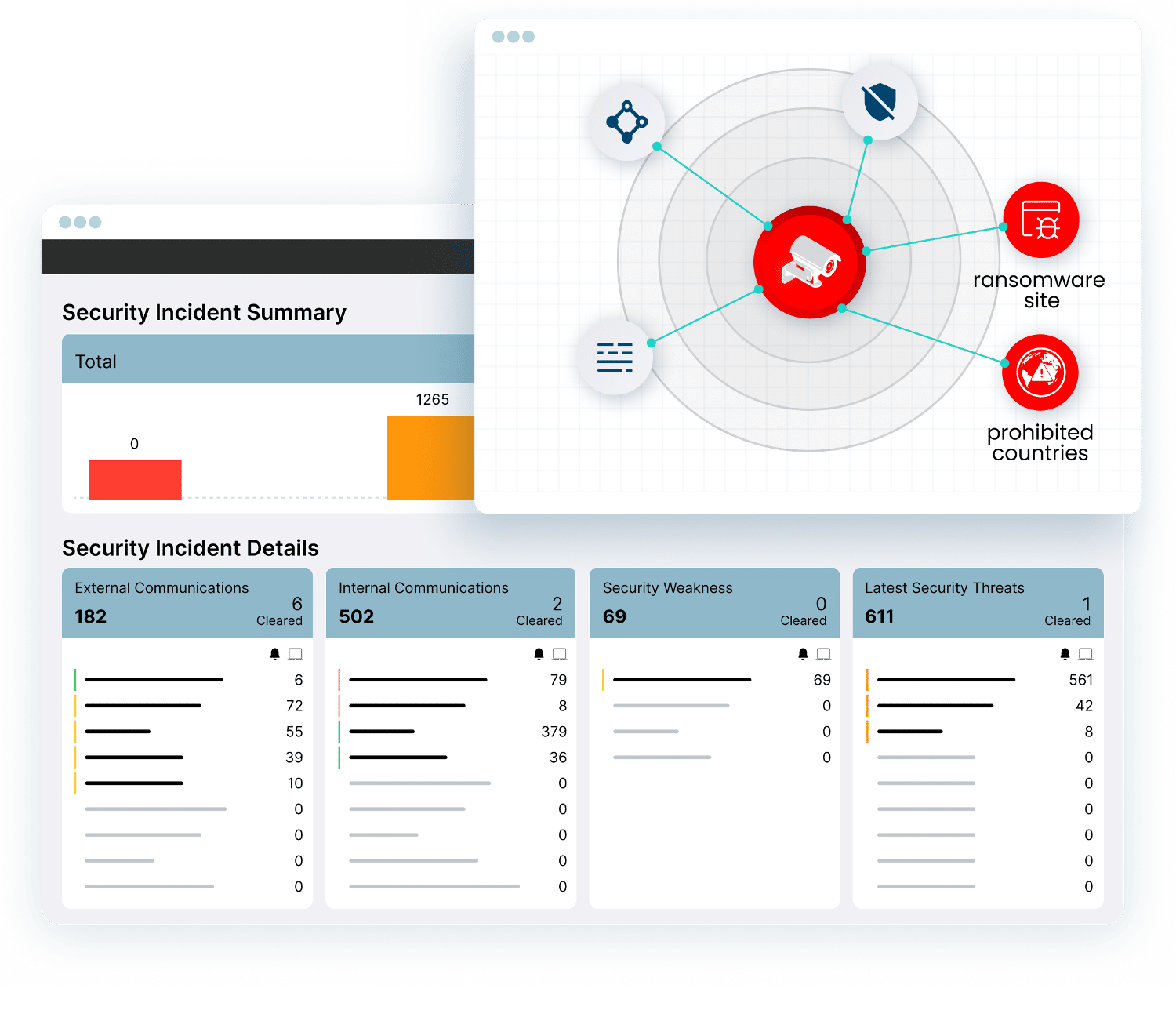
Reduce dwell time. Detect and quarantine devices with exploits, risky communications, anomalous behavior.
ACCELERATE RESPONSE
Accelerate NAC projects with asset context and automated policies. Implement Zero Trust segmentation for mission-critical devices.
ENHANCE SEGMENTATION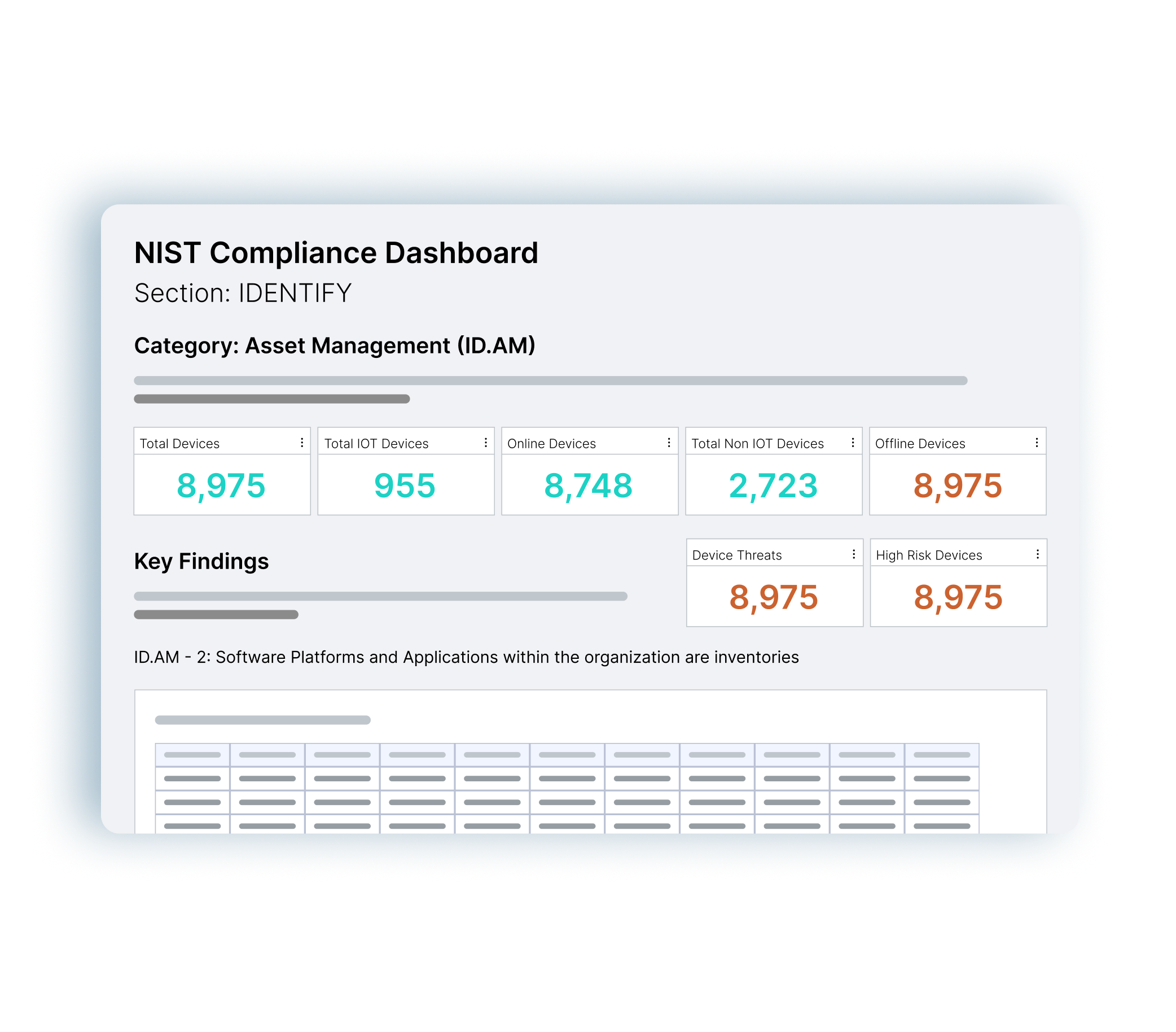
Simplify NIST, CIS Controls, CMMC, Cyber Essentials and NHS DSP Toolkit audits with asset data and reporting at your fingertips.
ENSURE COMPLIANCESeamlessly connect to hundreds of networking and security tools via API. Enrich your security tools with Ordr asset data, and automate response and segmentation policies on firewalls, switches, NAC.
SEE ALL TECHNOLOGY PARTNERSIntegration between Ordr and CrowdStrike ensures the security of all managed and unmanaged devices with comprehensive device visibility, detailed vulnerability insights, an understanding of risk, and the ability to enforce policy to mitigate active threats and improve security across all connected devices
Ordr analyzes network flow data to automatically discover and classify every connected device, profile behavior, and identify active threats. Security telemetry from the CrowdStrike Falcon platform, is shared with Ordr to enhance device insights, and provide a centralized, deep understanding of each device and its associated risk. Ordr uses multiple factors to calculate risk for each device based on business context, asset criticality, vulnerabilities, and overall threat details. With additional device data from the Falcon platform, Ordr provides a highly accurate risk score for each device. By continuously synchronizing device risk scores with CrowdStrike’s enriched security data, Ordr enables teams with an up-to-date view of risk to help them focus on the most critical devices.
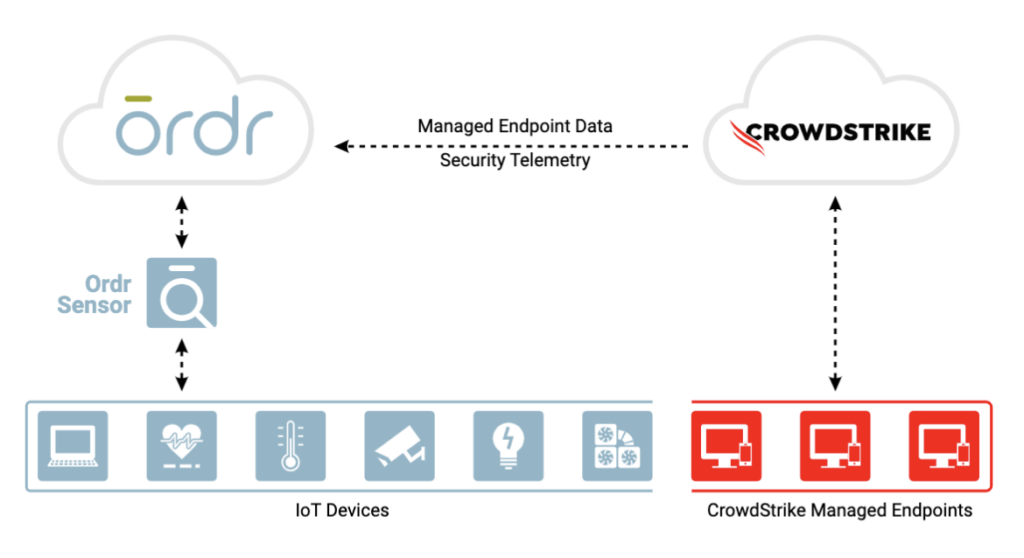
Gain complete device visibility
Minimize risk with better insights
Remediate faster
A basic tenet of network security and regulatory compliance is that “You cannot secure what you cannot see.” Gigamon and Ordr have teamed to deliver unsurpassed visibility and control into every thing connected to your network.
The Gigamon Visibility and Analytics Fabric (VAF) optimizes data collection of all north-south and east-west traffic across branch, campus, data center and cloud. Collected data is delivered to Ordr for analysis to ensure comprehensive device classification and visibility into all device communications. Integration with Gigamon VAF also eliminates concerns of SPAN security and potential impact to network infrastructure with “yet another SPAN port or session.”
By integrating with Gigamon VAF, customers can significantly reduce the number of Ordr sensors required to comprehensively discover and monitor every network-connected device, simplifying your network and security monitoring architecture.
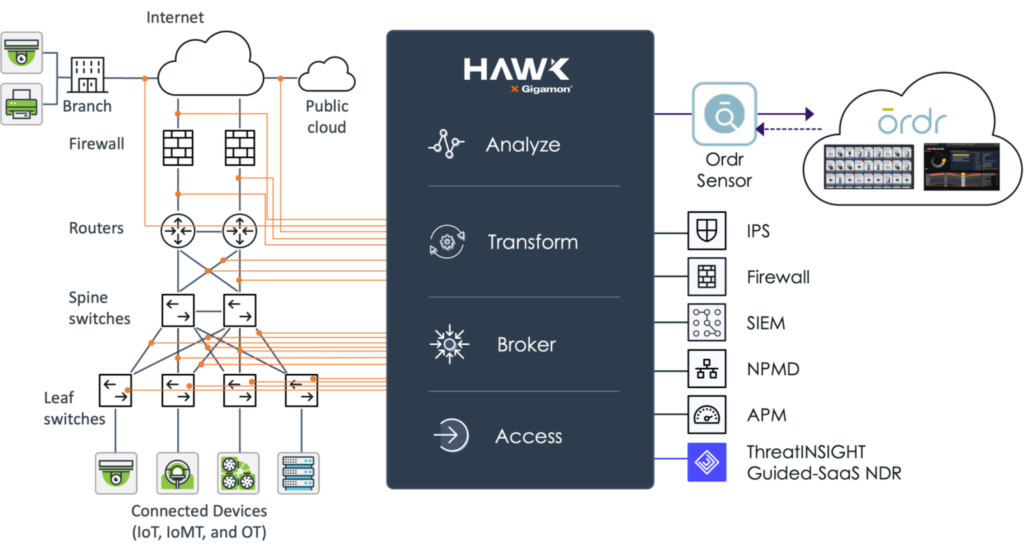
Fortinet and Ordr have partnered to deliver an industry-leading IoT and unmanaged device security solution by integrating FortiManager, FortiGate and FortiNAC with Ordr Systems Control Engine (SCE)
Automated Visibility and Security of All Connected Devices
Ordr SCE automatically creates a complete asset inventory, identifies and prioritizes asset risk, and tracks and risk-rates asset communications patterns. Ordr transmits this critical security context to Fortinet FortiGate, FortiManager, and FortiNAC, allowing administrators to create and apply firewall and NAC policies using business-relevant groups, classifications, and device names, while understanding the full risk profile and impact of each change. Ordr further reduces administrative costs by automatically updating asset groupings as devices join and leave the network, as well as by creating and transmitting security policies directly to FortiGate and FortiManager for enforcement.
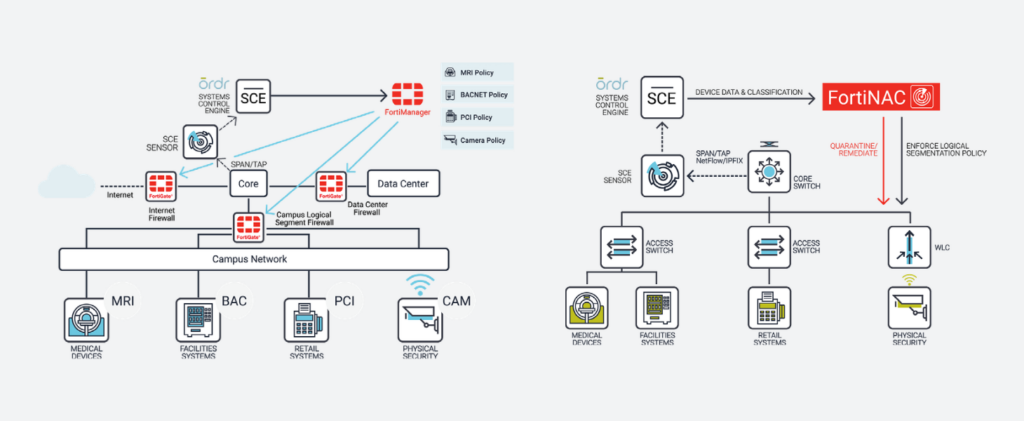
With the integration, joint customers can now:
Ordr works with Rapid7 to seamlessly discover all connected assets including IoT, IoMT, and OT devices. The joint solution enables Rapid7 to perform the right scan at the right time regardless of the device type, location, criticality or role within the organization. Many vulnerable IoT/OT devices discovered by Rapid7 cannot be patched or updated. Ordr automates the application of compensating controls to safeguard these devices by sending protection policies directly to firewalls, switches, wireless, or NAC systems. Similarly, infected devices can be quickly isolated through existing network and security devices.
The integration with Ordr and Rapid7 InsightVM provide ongoing bi-directional synchronization for managing vulnerabilities with rich device context. Ordr discovers every connected device, profiles device behaviors and risks, and automates remediation responses. Rapid7 InsightVM provides visibility into the vulnerabilities and clarity on how those vulnerabilities translate into business risk. Combining Ordr’s unique device intelligence with Rapid7’s advanced vulnerability intelligence provides organizations with the ultimate solution to efficiently manage risks while reducing service disruption and time to remediate.
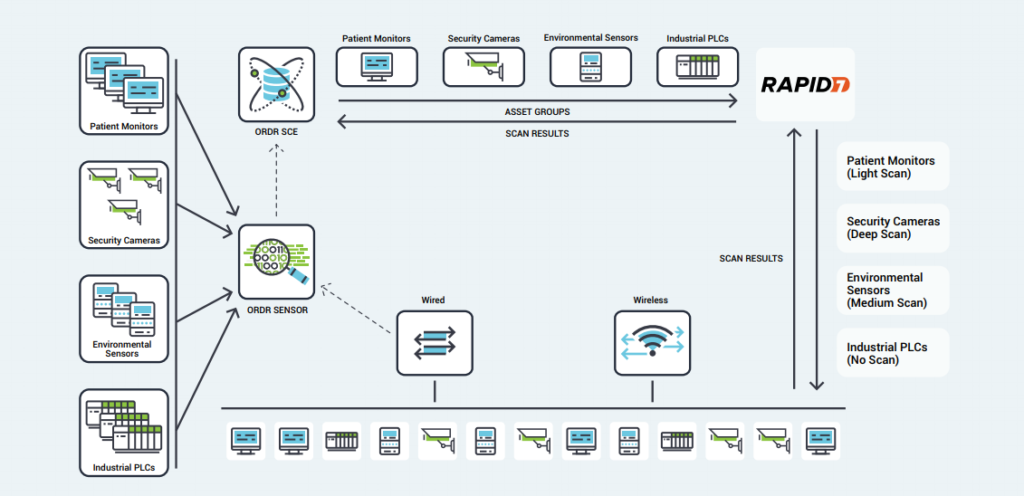
Explore how OrdrAI CAASM+ strengthens essential security measures by detecting gaps in security controls, evaluating security posture, and revealing asset exposures across all digital assets.
LEARN MORE ABOUT CAASM+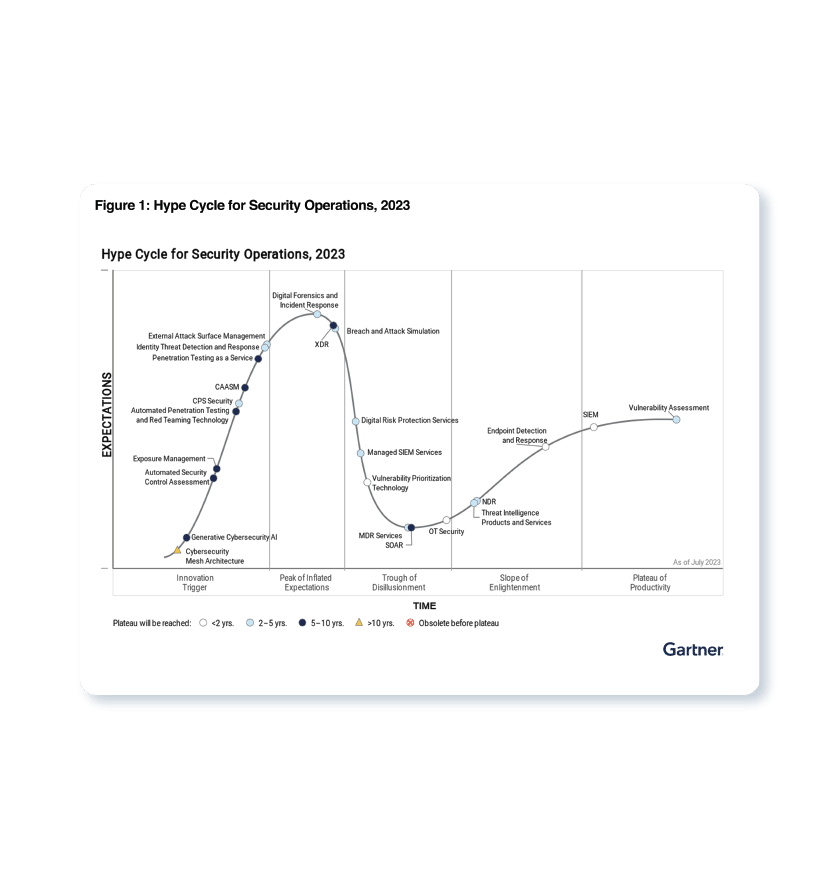
…hyper-connected healthcare enterprise, the quantity and heterogeneity of IoT devices creates a complex and increasingly untenable reality for healthcare technology, IT and security organizations. Leaders struggle to understand exactly what’s…
Connected devices in healthcare—often referred to as the Internet of Medical Things (IoMT)—represent one of the fastest-growing sectors of the IoT market, and is predicted to reach $176 billion by 2026.
To monitor, manage, and protect Internet of Things (IoT) devices in healthcare you must first understand the multiple ways in which IoMT devices are used. While the most popular example of IoT in healthcare is remote patient monitoring—meaning IoMT devices that collect patient data such as heart rate and body temperature—there are many other examples of IoT in the healthcare industry.
Here’s a look at 10 ways IoT is changing healthcare, as well as how the use of IoT devices for medical purposes impacts IoT security.
IoT devices offer a number of new opportunities for healthcare professionals to monitor patients, as well as for patients to monitor themselves. By extension, the variety of wearable IoT devices provide an array of benefits and challenges, for healthcare providers and their patients alike.
Remote patient monitoring is the most common application of IoT devices for healthcare. IoT devices can automatically collect health metrics like heart rate, blood pressure, temperature, and more from patients who are not physically present in a healthcare facility, eliminating the need for patients to travel to the providers, or for patients to collect it themselves.
When an IoT device collects patient data, it forwards the data to a software application where healthcare professionals and/or patients can view it. Algorithms may be used to analyze the data in order to recommend treatments or generate alerts. For example, an IoT sensor that detects a patient’s unusually low heart rate may generate an alert so that healthcare professionals can intervene.
A major challenge with remote patient monitoring devices is ensuring that the highly personal data that these IoT devices collect is secure and private.
For the more than 30 million Americans with diabetes, glucose monitoring has traditionally been difficult. Not only is it inconvenient to have to check glucose levels and manually record results, but doing so reports a patient’s glucose levels only at the exact time the test is provided. If levels fluctuate widely, periodic testing may not be sufficient to detect a problem.
IoT devices can help address these challenges by providing continuous, automatic monitoring of glucose levels in patients. Glucose monitoring devices eliminate the need to keep records manually, and they can alert patients when glucose levels are problematic.
Challenges include designing an IoT device for glucose monitoring that:
a. Is small enough to monitor continuously without causing a disruption to patients
b. Does not consume so much electricity that it needs to be recharged frequently.
These are not insurmountable challenges, however, and devices that address them promise to revolutionize the way patients handle glucose monitoring.
Like glucose, monitoring heart rates can be challenging, even for patients who are present in healthcare facilities. Periodic heart rate checks don’t guard against rapid fluctuations in heart rates, and conventional devices for continuous cardiac monitoring used in hospitals require patients to be attached to wired machines constantly, impairing their mobility.
Today, a variety of small IoT devices are available for heart rate monitoring, freeing patients to move around as they like while ensuring that their hearts are monitored continuously. Guaranteeing ultra-accurate results remains somewhat of a challenge, but most modern devices can deliver accuracy rates of about 90 percent or better.
Traditionally, there hasn’t been a good way to ensure that providers and patients inside a healthcare facility washed their hands properly in order to minimize the risk of spreading contagion.
Today, many hospitals and other health care operations use IoT devices to remind people to sanitize their hands when they enter hospital rooms. The devices can even give instructions on how best to sanitize to mitigate a particular risk for a particular patient.
A major shortcoming is that these devices can only remind people to clean their hands; they can’t do it for them. Still, research suggests that these devices can reduce infection rates by more than 60 percent in hospitals.
Information about depression symptoms and patients’ general mood is another type of data that has traditionally been difficult to collect continuously. Healthcare providers might periodically ask patients how they are feeling, but were unable to anticipate sudden mood swings. And, often, patients don’t accurately report their feelings.
“Mood-aware” IoT devices can address these challenges. By collecting and analyzing data such as heart rate and blood pressure, devices can infer information about a patient’s mental state. Advanced IoT devices for mood monitoring can even track data such as the movement of a patient’s eyes.
The key challenge here is that metrics like these can’t predict depression symptoms or other causes for concern with complete accuracy. But neither can a traditional in-person mental assessment.
In order to treat Parkinson’s patients most effectively, healthcare providers must be able to assess how the severity of their symptoms fluctuate through the day.
IoT sensors promise to make this task much easier by continuously collecting data about Parkinson’s symptoms. At the same time, the devices give patients the freedom to go about their lives in their own homes, instead of having to spend extended periods in a hospital for observation.
While wearable devices like those described above remain the most commonly used type of IoT device in healthcare, there are devices that go beyond monitoring to actually providing treatment, or even “living” in or on the patient. Examples include the following.
Conditions such as asthma or COPD often involve attacks that come on suddenly, with little warning. IoT-connected inhalers can help patients by monitoring the frequency of attacks, as well as collecting data from the environment to help healthcare providers understand what triggered an attack.
In addition, connected inhalers can alert patients when they leave inhalers at home, placing them at risk of suffering an attack without their inhaler present, or when they use the inhaler improperly.
Collecting data from inside the human body is typically a messy and highly disruptive affair. No no enjoys having a camera or probe stuck into their digestive tract, for example.
With ingestible sensors, it’s possible to collect information from digestive and other systems in a much less invasive way. They provide insights into stomach PH levels, for instance, or help pinpoint the source of internal bleeding.
These devices must be small enough to be swallowed easily. They must also be able to dissolve or pass through the human body cleanly on their own. Several companies are hard at work on ingestible sensors that meet these criteria.
Smart contact lenses provide another opportunity for collecting healthcare data in a passive, non-intrusive way. They could also, incidentally, include microcameras that allow wearers effectively to take pictures with their eyes, which is probably why companies like Google have patented connected contact lenses.
Whether they’re used to improve health outcomes or for other purposes, smart lenses promise to turn human eyes into a powerful tool for digital interactions.
By deploying small Internet-connected robots inside the human body, surgeons can perform complex procedures that would be difficult to manage using human hands. At the same time, robotic surgeries performed by small IoT devices can reduce the size of incisions required to perform surgery, leading to a less invasive process, and faster healing for patients.
These devices must be small enough and reliable enough to perform surgeries with minimal disruption. They must also be able to interpret complex conditions inside bodies in order to make the right decisions about how to proceed during a surgery. But IoT robots are already being used for surgery, showing that these challenges can be adequately addressed.
In order to make the most of IoT for healthcare, critical security challenges must be addressed.
Above all, IoT device developers, managers and healthcare providers must ensure that they adequately secure data collected by IoT devices. Much of the data collected by medical devices qualifies as protected health information under HIPAA and similar regulations. As a result, IoT devices could be used as gateways for stealing sensitive data if not properly secured. Indeed, 82 percent of healthcare organizations report having experienced attacks against their IoT devices.
Developing secure IoT hardware and software is one step in addressing this challenge. Equally important, however, is ensuring that IoT devices in healthcare are managed properly in order to protect against data from unmonitored devices falling into the wrong hands. A patient monitoring device that has an older version of software or firmware, or a device that is not properly decommissioned after it is no longer needed, for example, could offer attackers an opportunity to infiltrate a network or steal protected health information.
Proper discovery and classification of all IoT devices on a healthcare provider’s network helps guard against this risk. Once IoT device networks are properly identified, classified, regulated, and secured, managers can track device behavior to identify anomalies, perform risk assessments and segment vulnerable from mission-critical devices.
In a hyper-connected healthcare enterprise, the quantity and heterogeneity of IoT devices creates a complex and increasingly untenable reality for healthcare technology, IT and security organizations. Leaders struggle to understand exactly what’s connected to the network, what it’s doing, and how to regulate and protect it all.
Ordr Systems Control Engine (SCE) can enable visibility, and security of all of your connected medical devices. It can identify, classify, profile behavior and risk, and secure all medical and IoT assets in your healthcare organization. Once you understand the behavior and communications of every connected device, you can proactively secure them using microsegmentation policies enforced on your existing network and security infrastructure, without touching or modifying the devices. You can even use Ordr to maximize the utilization of all of your connected medical devices.
Ordr offers superior ransomware protection across the kill chain starting with comprehensive visibility into devices and risks (including complete details about devices, with granular insights—such as make, model, serial number, and network location). Our solution is capable of illuminating network blind spots by monitoring for east-west lateral movement and identifying attacker exploit tools. Our machine learning engine can baseline communication patterns to recognize an attack in progress, such as C2 communications. Finally, automated policies allow security teams to take action rapidly.
Subscribe today to stay informed and get regular updates from Ordr Cloud